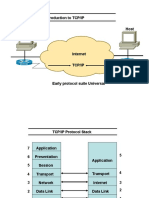
TCP/IP Protocol Suite
HTTP SMTP DNS RTP
Distributed
applications User
Reliable
stream TCP UDP datagram
service service
Best-effort
IP (ICMP, ARP)
connectionless
packet transfer
Network Network Network
Interface 1 Interface 2 Interface 3
8.2 The Internet Protocol
• Provides best effort, connectionless packet
delivery
– motivated by need to keep routers simple and by
adaptibility to failure of network elements
– packets may be lost, out of order, or even duplicated
– higher layer protocols must deal with these, if
necessary
1
� IP Packet Header (Fig8.4)
0 4 8 16 19 24 31
Version IHL Type of Service Total Length
Identification Flags Fragment Offset
Time to Live Protocol Header Checksum
Source IP Address
Destination IP Address
Options Padding
z Minimum 20 bytes
z Up to 40 bytes in options fields
Version: current IP version is 4.
Identification, Flags, and Fragment Offset: used for fragmentation and
reassembly (More on this shortly).
Time to live (TTL): number of hops packet is allowed to traverse in the network.
Each router along the path to the destination decrements this value by one.
If the value reaches zero before the packet reaches the destination, the router
discards the packet and sends an error message back to the source.
Protocol: specifies upper-layer protocol that is to receive IP data at the destination.
Examples include TCP (protocol = 6), UDP (protocol = 17), and ICMP (protocol = 1).
Header checksum: verifies the integrity of the IP header.
Source IP address and destination IP address: contain the addresses of the
source and destination hosts.
2
� IP Addressing
• Each host on Internet has unique 32 bit IP address
• Each address has two parts: netid and hostid
• A separate address is required for each physical
connection of a host to a network; “multi-homed”
hosts
• Dotted-Decimal Notation:
int1.int2.int3.int4 where intj = integer value of jth
octet
IP address of 10000000 10000111 01000100
00000101
is 128.135.68.5 in dotted-decimal notation
Classful Addresses
Class A 7 bits 24 bits
0 netid hostid
• 126 networks with up to 16 million hosts 1.0.0.0 to
127.255.255.255
Class B
14 bits 16 bits
1 0 netid hostid
• 16,382 networks with up to 64,000 hosts 128.0.0.0 to
191.255.255.255
Class C 22 bits 8 bits
1 1 0 netid hostid
• 2 million networks with up to 254 hosts 192.0.0.0 to
223.255.255.255
3
�Class D 28 bits
1 1 1 0 multicast address
224.0.0.0 to
239.255.255.255
• Up to 250 million multicast groups at the
same time
• Permanent group addresses
– All systems in LAN; All routers in LAN;
– All OSPF routers on LAN; All designated OSPF
routers on a LAN, etc.
• Temporary groups addresses created as
needed
• Special multicast routers
Reserved Host IDs (all 0s &
1s)
Internet address used to refer to network has hostid set to all 0s
this host
0 0 0 0 0 0 (used when
booting up)
Broadcast address has hostid set to all 1s
broadcast on
1 1 1 1 1 1 local network
broadcast on
netid 1 1 1 1 1 1 1 distant
network
4
� Private IP Addresses
• Specific ranges of IP addresses set aside
for use in private networks (RFC 1918)
• Use restricted to private internets; routers
in public Internet discard packets with
these addresses
• Range 1: 10.0.0.0 to 10.255.255.255
• Range 2: 172.16.0.0 to 172.31.255.255
• Range 3: 192.168.0.0 to 192.168.255.255
• Network Address Translation (NAT) used
to convert between private & global IP
addresses
Example of IP Addressing
128.135.40.1 128.140.5.40
Interface Interface H
H Address is Address is
128.135.10.2 128.140.5.35
Network Network
R
128.135.0.0 128.140.0.0
H H
H
128.135.10.20 128.135.10.21
128.140.5.36
Address with host ID=all 0s refers to the network
R = router
Address with host ID=all 1s refers to a broadcast packet H = host
5
� Subnet Addressing
• Subnet addressing introduces another
hierarchical level
• Transparent to remote networks
• Simplifies management of multiplicity of LANs
• Masking used to find subnet number
Original
1 0 Net ID Host ID
address
Subnetted
address 1 0 Net ID Subnet ID Host ID
Subnetting Example
• Organization has Class B address (16 host ID
bits) with network ID: 150.100.0.0
• Create subnets with up to 100 hosts each
– 7 bits sufficient for each subnet
– 16-7=9 bits for subnet ID
• Apply subnet mask to IP addresses to find
corresponding subnet
– Example: Find subnet for 150.100.12.176
– IP add = 10010110 01100100 00001100 10110000
– Mask = 11111111 11111111 11111111 10000000
– AND = 10010110 01100100 00001100 10000000
– Subnet = 150.100.12.128
– Subnet address used by routers within organization
6
� Subnet Example
H1 H2
150.100.12.154 150.100.12.176
150.100.12.128
150.100.12.129
150.100.0.1
R1
To the rest of H3 H4
the Internet 150.100.12.4
150.100.12.24 150.100.12.55
150.100.12.0
150.100.12.1
R2 H5
150.100.15.54 150.100.15.11
150.100.15.0
Routing with Subnetworks
• IP layer in hosts and routers maintain a routing
table
• Originating host: To send an IP packet, consult
routing table
– If destination host is in same network, send packet
directly using appropriate network interface
– Otherwise, send packet indirectly; typically, routing
table indicates a default router
• Router: Examine IP destination address in
arriving packet
– If dest IP address not own, router consults routing
table to determine next-hop and associated network
interface & forwards packet
7
� Routing Table
• Each row in routing table • Routing table search
contains: order & action
– Destination IP address – Complete destination
address; send as per
– IP address of next-hop
next-hop & G flag
router
– Destination network ID;
– Physical address
send as per next-hop &
– Statistics information G flag
– Flags – Default router entry;
• H=1 (0) indicates route is
send as per next-hop
to a host (network)
• G=1 (0) indicates route is – Declare packet
to a router (directly undeliverable; send
connected destination) ICMP “host unreachable
error” packet to
originating host
Example: Host H5 sends
packet to host H2
H1 H2
150.100.12.154 150.100.12.176
150.100.12.128
150.100.12.129
150.100.0.1
R1
To the rest of H3 H4
the Internet 150.100.12.4
150.100.12.24 150.100.12.55
150.100.12.0
150.100.12.1
R2 H5
150.100.15.54 150.100.15.11
Routing Table at H5
150.100.15.0
Destination Next-Hop Flags Net I/F
127.0.0.1 127.0.0.1 H lo0 150.100.12.176
default 150.100.15.54 G emd0
150.100.15.0 150.100.15.11 emd0
8
� Example: Host H5 sends
packet to host H2
H1 H2
150.100.12.154 150.100.12.176
150.100.12.128
150.100.12.129
150.100.0.1
R1
To the rest of H3 H4
the Internet 150.100.12.4
150.100.12.24 150.100.12.55
150.100.12.0
150.100.12.1
150.100.12.176
R2 H5
Routing Table at R2
150.100.15.54 150.100.15.11
Destination Next-Hop Flags Net I/F
150.100.15.0
127.0.0.1 127.0.0.1 H lo0
default 150.100.12.4 G emd0
150.100.15.0 150.100.15.54 emd1
150.100.12.0 150.100.12.1 emd0
Example: Host H5 sends
packet to host H2
H1 H2
150.100.12.154 150.100.12.176
150.100.12.128
150.100.12.129 150.100.12.176
150.100.0.1
R1
To the rest of H3 H4
the Internet 150.100.12.4
150.100.12.24 150.100.12.55
150.100.12.0
150.100.12.1
R2 H5
Routing Table at R1
150.100.15.54 150.100.15.11
Destination Next-Hop Flags Net I/F
150.100.15.0
127.0.0.1 127.0.0.1 H lo0
150.100.12.176 150.100.12.176 emd0
150.100.12.0 150.100.12.4 emd1
150.100.15.0 150.100.12.1 G emd1
9
� IP Address Problems
• In the 1990, two problems became apparent
– IP addresses were being exhausted
– IP routing tables were growing very large
• IP Address Exhaustion
– Class A, B, and C address structure inefficient
• Class B too large for most organizations, but future proof
• Class C too small
• Rate of class B allocation implied exhaustion by 1994
• IP routing table size
– Growth in number of networks in Internet reflected in # of table
entries
• From 1991 to 1995, routing tables doubled in size every 10 months
• Stress on router processing power and memory allocation
• Short-term solution:
• Classless Interdomain Routing (CIDR), RFC 1518
• New allocation policy (RFC 2050)
• Private IP Addresses set aside for intranets
• Long-term solution: IPv6 with much bigger address space
Supernetting
• Summarize a contiguous group of class C
addresses using variable-length mask
• Example: 150.158.16.0/20
– IP Address (150.158.16.0) & mask length (20)
– IP add = 10010110 10011110 00010000 00000000
– Mask = 11111111 11111111 11110000 00000000
– Contains 16 Class C blocks:
– From 10010110 10011110 00010000 00000000
– i.e. 150.158.16.0
– Up to 10010110 10011110 00011111 00000000
– i.e. 150.158.31.0
10
� Classless Inter-Domain Routing
• CIDR deals with Routing Table Explosion Problem
– Networks represented by prefix and mask
– Pre-CIDR: Network with range of 16 contiguous class C blocks
requires 16 entries
– Post-CIDR: Network with range of 16 contiguous class C
blocks requires 1 entry
• Solution: Route according to prefix of address, not class
– Routing table entry has <IP address, network mask>
– Example: 192.32.136.0/21
– 11000000 00100000 10001000 00000001 min address
– 11111111 11111111 11111--- -------- mask
– 11000000 00100000 10001--- -------- IP prefix
– 11000000 00100000 10001111 11111110 max address
– 11111111 11111111 11111--- -------- mask
– 11000000 00100000 10001--- -------- same IP prefix
Longest Prefix Match
• CIDR impacts routing & forwarding
• Routing tables and routing protocols must carry IP address
and mask
• Multiple entries may match a given IP destination address
• Example: Routing table may contain
– 205.100.0.0/22 which corresponds to a given supernet
– 205.100.0.0/20 which results from aggregation of a larger
number of destinations into a supernet
– Packet must be routed using the more specific route, that
is, the longest prefix match
• Several fast longest-prefix matching algorithms are available
11
� Address Resolution Protocol
Although IP address identifies a host, the packet is physically
delivered by an underlying network (e.g., Ethernet) which
uses its own physical address (MAC address in Ethernet).
How to map an IP address to a physical address?
H1 wants to learn physical address of H3 -> broadcasts an ARP request
H1 H2 H3 H4
150.100.76.20 150.100.76.21 150.100.76.22 150.100.76.23
ARP request (what is the MAC address of 150.100.76.22?)
Every host receives the request, but only H3 reply with its physical address
H1 H2 H3 H4
ARP response (my MAC address is 08:00:5a:3b:94)
Fragmentation and
Reassembly
• Identification identifies a particular packet
• Flags = (unused, don’t fragment/DF, more fragment/MF)
• Fragment offset identifies the location of a fragment within a packet
Reassemble
at destination
Source Router Destination
Fragment
at source Fragment
IP IP
at router
Network Network
12
� Example: Fragmenting a Packet
• A packet is to be forwarded to a network with MTU of 576
bytes. The packet has an IP header of 20 bytes and a data
part of 1484 bytes. and of each fragment.
• Maximum data length per fragment = 576 - 20 = 556 bytes.
• We set maximum data length to 552 bytes to get multiple of 8.
Total Id MF Fragment
Length Offset
Original 1504 x 0 0
packet
Fragment 1 572 x 1 0
Fragment 2 572 x 1 69
Fragment 3 400 x 0 138
Internet Control Message Protocol
(ICMP)
• RFC 792; Encapsulated in IP packet (protocl type = 1)
• Handles error and control messages
• If router cannot deliver or forward a packet, it sends an ICMP
“host unreachable” message to the source
• If router receives packet that should have been sent to
another router, it sends an ICMP “redirect” message to the
sender; Sender modifies its routing table
• ICMP “router discovery” messages allow host to learn about
routers in its network and to initialize and update its routing
tables
• ICMP echo request and reply facilitate diagnostic and used in
“ping”
13
� ICMP Basic Error Message
Format
0 8 16 31
Type Code Checksum
Unused
IP header and 64 bits of original datagram
• Type of message: some examples
– 0 Network Unreachable; 3 Port Unreachable
– 1 Host Unreachable 4 Fragmentation needed
– 2 Protocol Unreachable 5 Source route failed
– 11 Time-exceeded, code=0 if TTL exceeded
• Code: purpose of message
• IP header & 64 bits of original datagram
– To match ICMP message with original data in IP packet
8.4 User Datagram Protocol
• Best effort datagram service
• Multiplexing enables sharing of IP datagram service
• Simple transmitter & receiver
– Connectionless: no handshaking & no connection state
– Low header overhead
– No flow control, no error control, no congestion control
– UDP datagrams can be lost or out-of-order
• Applications
– multimedia (e.g. RTP)
– network services (e.g. DNS, RIP, SNMP)
14
� UDP Datagram
0 16 31
• Source and destination port
Source Port Destination Port
numbers
UDP Length UDP Checksum – Client ports are ephemeral
– Server ports are well-known
Data – Max number is 65,535
• UDP length
– Total number of bytes in
0-255 datagram (including header)
– Well-known ports – 8 bytes ≤ length ≤ 65,535
256-1023 • UDP Checksum
– Less well-known ports – Optionally detects errors in
UDP datagram
1024-65536
– Ephemeral client ports
15