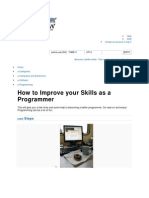
Architecture of the UNIX
user programs
user Level kernel Level
trap
libraries
system call interface
file subsystem buffer cache
character block device drivers
kernel Level hardware Level
process control subsystem
inter-process communication scheduler
memory management
hardware control
�System Calls
Provide an interface between a process an d the operating system. Generally availabl e as assembly-language instructions UNIX system calls maybe invoked directly from a C or C++ program System calls for modern Microsoft Window s platforms are part of the Win32 applicati on programmer interface (API), which is av ailable for use by all the compilers written for Microsoft Windows
�Process States and Transition
User mode running
Interrupt, Interrupt return Zombie exi t Sys call return interrupt Return to user Ready
Kernel mode running preempt sleep Reschedule process
Sleep in memory Ready to run in memoryEnough Created Wake-up memory
fork
Swap out
Swap out
Swap in
Not enough memory
Sleep, Swapped Ready to Run, Swapped Wake-up
3
�Kernel data structure Process Table
Process Identification Process State Scheduling parameter
The process priority, user-mode scheduling priority, recent CPU utilization, and amount od of time spent sleeping
Signal State
Signal pending delivery, signal mask, and summary of signal actions
Timer : Real-time timer and CPU-utilization counters Event Descriptor Realted Process Ids Serveral User IDs & Group IDs : uid, euid, gid, egid
�Kernel data structure u area
Pointer to Process Table Timer : spent in kernel and user mode Signal Handler The control terminal Error Return value I/O parameters Current directory and Current root User File Descriptor table Limit fields restrict the size of process and the size of a file it can
write
Permission modes field masks mode setting on the files the process creats.
�Process Control
Control of Process Context
fork : create a new process exit : terminate process execution wait : allow parent process to synchronize its execution with the exit of a child process exec : invoke a new program brk : allocate more memory dynamically signal : inform asynchronous event
�Process Creation
Process Creation
the only way to create a new process in UNIX is fork
parent process : the process that invokes the fork child process : the newly created process
Process 0 is the only process not created via fork
fork system call
pid = fork(); pid : to parent, the child process ID to child process, 0
�Sequence of Operations for fork
1. It allocates a slot in process table for the new process
2. It assigns a unique ID number to the child process
3. It makes a logical copy of the context of the parent process. Since certain portion of process, such as the text region, may be shared between processes, the kernel can sometimes increment a region reference count instead of copying the region to a new physical location in memory 4. It increments file and inode table counters for files associated with the process. 5. It returns the ID number of child process to the parent process, and a 0 value to the child process.
8
�Signals
Informs the occurrence of asynchronous event.
from process to process : kill system call. from kernel to process internally. 64 Signals
Treatment of Signals
How the kernel sends a signal to a process. How the process handles a signal How a process controls its reaction to the signal
�How to Send a Signal to Process
Send a Signal
sets a bit in the signal field in process table entry. process can remember different type of signal. process can not remember how many signals it receives of particular type. u area contains an array of signal-handler fields. kernel stores the address of the user-function in the field.
Check for Signal
about to return from kernel mode to user mode enters or leaves the sleep state at a suitably low scheduling priority.
Handle Signals
only when returns from kernel mode to user mode
10
�Handling Signals
Handling Signals
kernel handles signals in the context of the process that received signals. process must run to handle signals exit(default action) ignores signals executes a particular user function
Three Cases
signal System call
specify special action to take on receipt of certain signal oldfunction = signal(signum, function);
signum : signal number function : the address of function to invoke on receipt of signal
0 : exit 1 : ignore
oldgunction : the most recently specified to call to signum
11
�Algorithm for Handling Signal
1. determines signal type 2. turns off signal bit in the process table entry 3. if receives a signal to ignore
continues as if the signal has never occurred.
4. If signal handling function is set to its default value,
kernel dumps core image for signals that imply something is wrong with process and exit kernel does not dump core for signals that do not imply error.
5. If receives a signal to catch,
accesses the user saved register context, and find the program counter and stack pointer clears the signal handler field in u area( undesirable side-effects ) kernel creates a new stack frame and writes a program counter and stack pointer from user saved register context kernel changes the user register context: program counter to the address of signal catcher function, and stack pointer to account for the growth of the user stack.
12
�Source Code for a Program that Catches Signals
#include <signal.h> main() { extern catcher(); signal(SIGINT, catcher); kill(0,SIGINT); } catcher() { }
Address of kill system call : 10c Address of catcher : 104
13
�Sending Signals from Processes
kill system call
kill(pid,signum)
pid : set of processes to receive the signals signum : signal number being sent
pid and processes
if pid > 0, to the process with process ID pid. If pid == 0. to all processes in the senders process group. If pid == -1, to all processes whose real user ID is equal to effective user ID of senders. If sending process has effective user ID of super user, sends the signal all processes except process 0 and 1. If pid < 0 and pid != -1, to all processes in the process group equal to the absolute value of pid.
Failure
if the sending process does not have effective user ID of super user, or its real user ID or effective user ID do not match the real or effective user ID of the receiving process.
14
�Sample Use of setpgrp
#include <signal.h> main() { register int i;
Kernel sends the signal to the 5 even processes that did not reset their process group 5 odd processes continue to loop
setpgrp(); for(i=0; i<10; i++) { if (fork()==0) { /* child proc */ if ( i & 1 ) setpgrp(); printf(pid=%d pgrp=%d\n, getpid(), getppid()); pause(); } } kill(0,SIGINT); }
15
�Process Termination
exit system call
process terminate by exit system call
enters the zombie status relinquish resources. dismantles its context except for its slot in the process table.
exit(status);
status : the value returned to parent process
call exit explicitly or implicitly(by startup routine) at the end of program. kernel may invoke internally on receipt of uncaught signals. In this case, the value of status is the signal number.
16
�Awaiting Process Termination
wait system call
synchronize its execution with the termination of a child process pid = wait(stat_addr);
pid : process id of the zombie child process
stat_addr : address of an integer to contain the exit status of the child
17
�Algorithm for Awaiting Process Termination
1. 2. 3. 4. searches the zombie child process If no children, return error if finds zombie children, extracts PID number and exit code adds accumulated time the child process executes in the user and kernel mode to the fields in u area 5. Release process table slot
18
�Algorithm for Wait
algorithm wait input : address of variables to store status of exiting process output : child ID, child exit code { if (waiting process has no child process) return(error); for(;;) { if (waiting process has zombie child) { pick arbitrary zombie child; add child CPU usage to parent; free child process table entry; return(childID,child exit code); } if (process has no child process) return(error); sleep at interruptible priority(event child process exits); } }
19
�Processes in UNIX System
User Process
most processes on typical system associated with users at a terminal not associated with any users do system-wide functions administration and control of networks, execution of timedependent activities, line printer spooling, and so on run at user mode and make system calls to access system service like user process execute only in kernel mode process 0 spawns kernel process, such as page-reclaiming process vhand, and then becomes the swapper process extremely powerful, not flexible
20
Daemon Process
Kernel Process