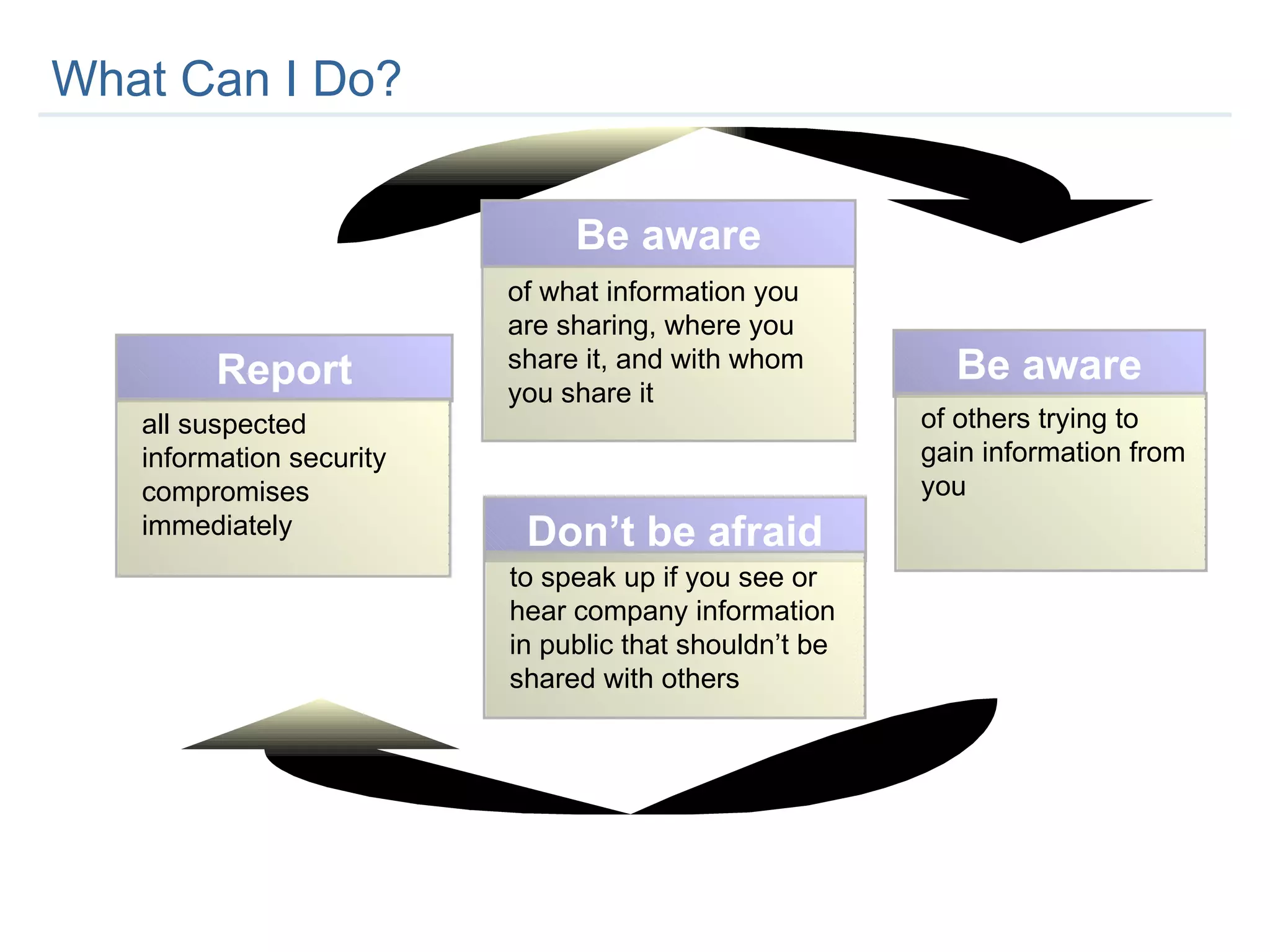
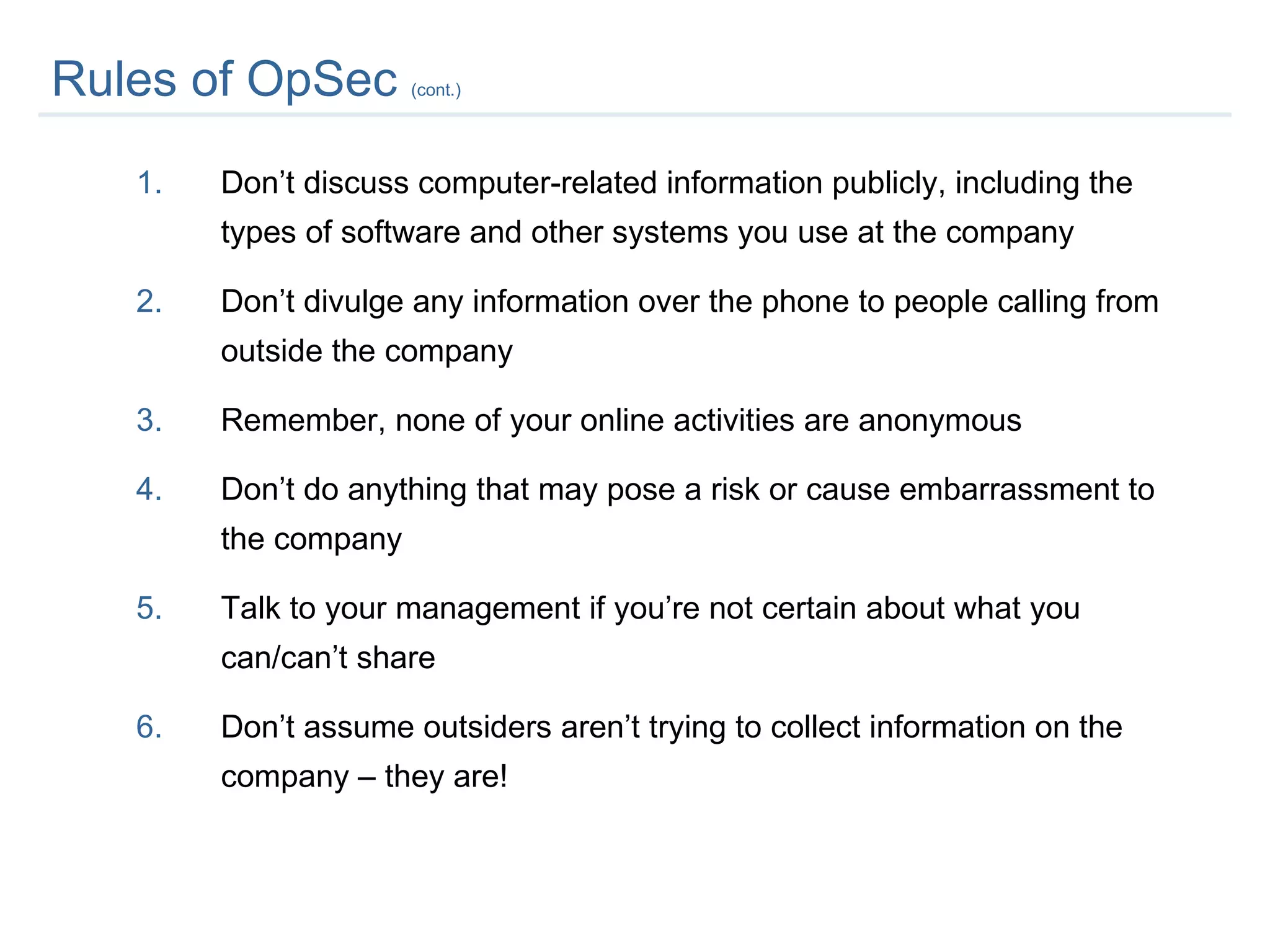
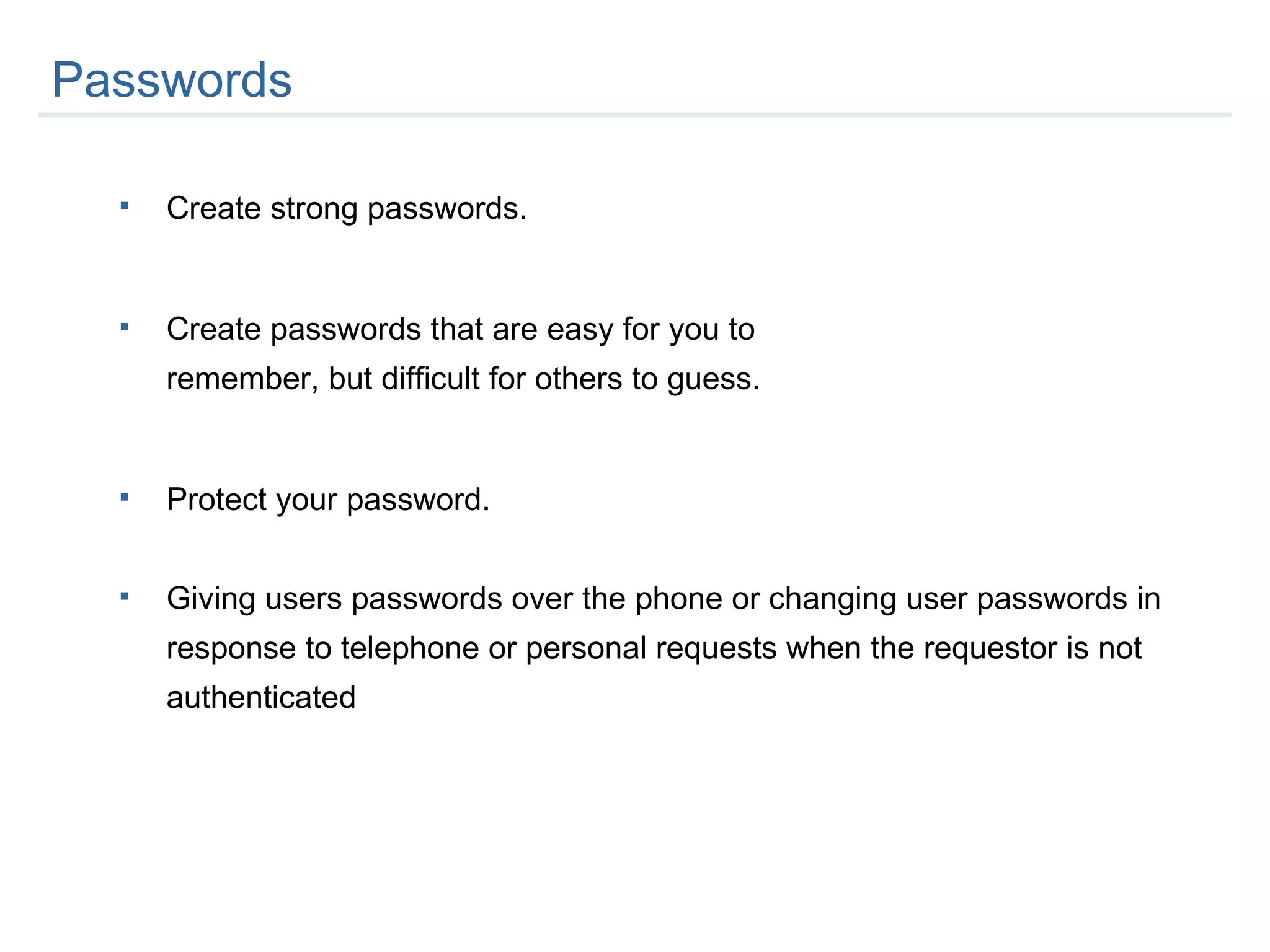
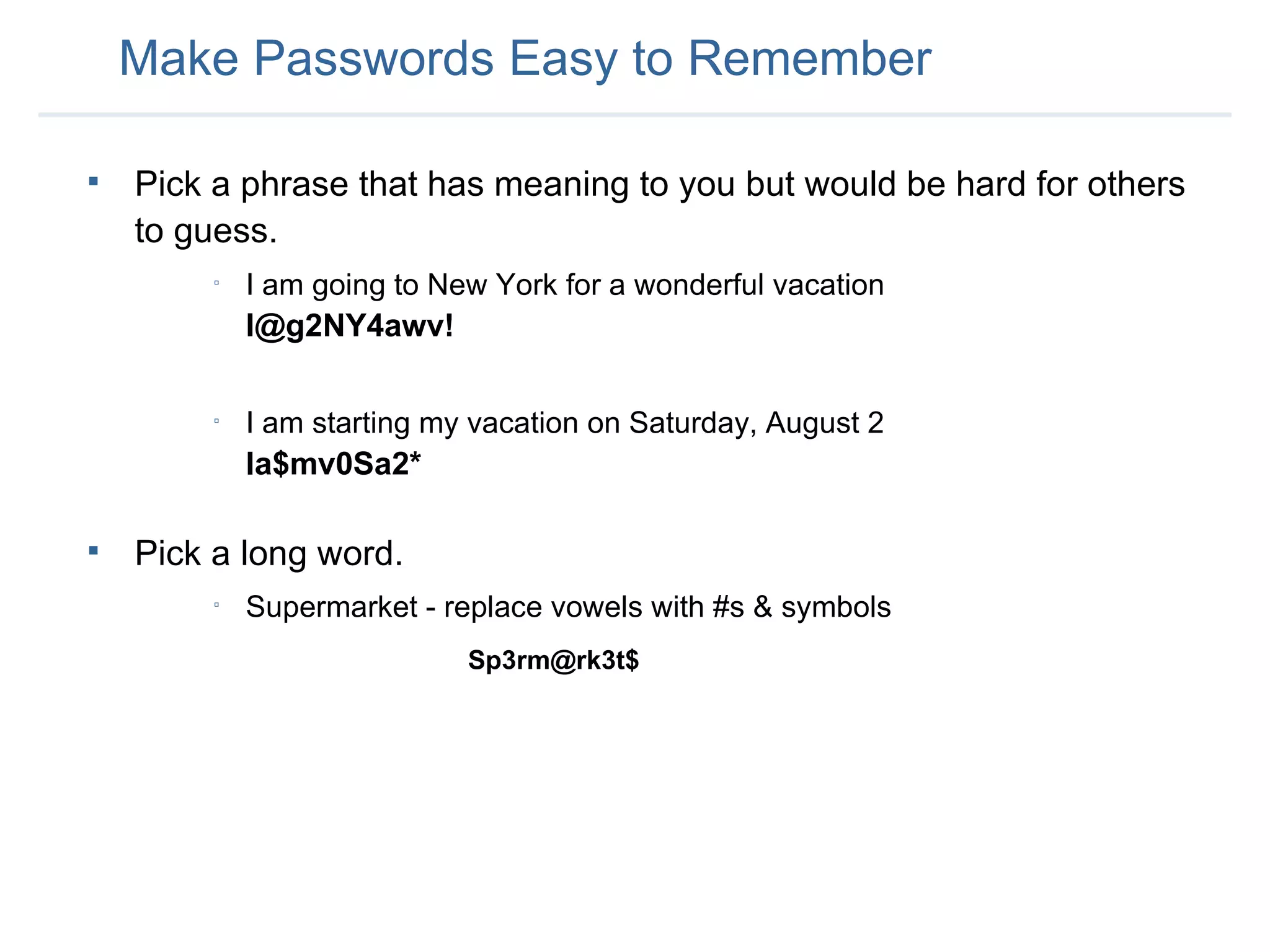
The document provides an overview of an employee information security awareness training. It summarizes key topics covered in the training including identifying security risks, developing good security practices, protecting classified and sensitive company information, securing workstations and mobile devices, safe email practices, and guarding against social engineering. It emphasizes the importance of protecting company information and passwords at all times.