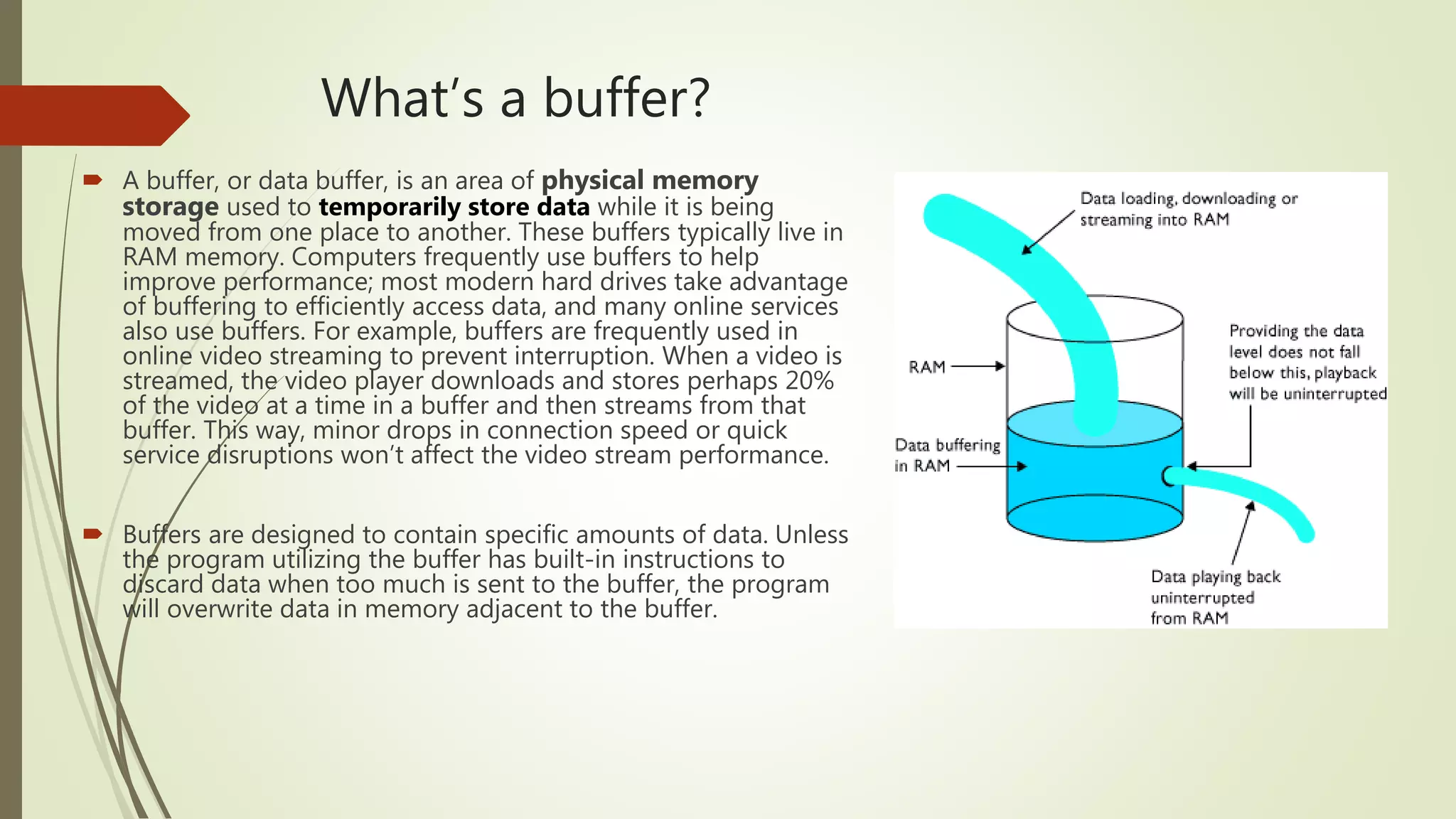
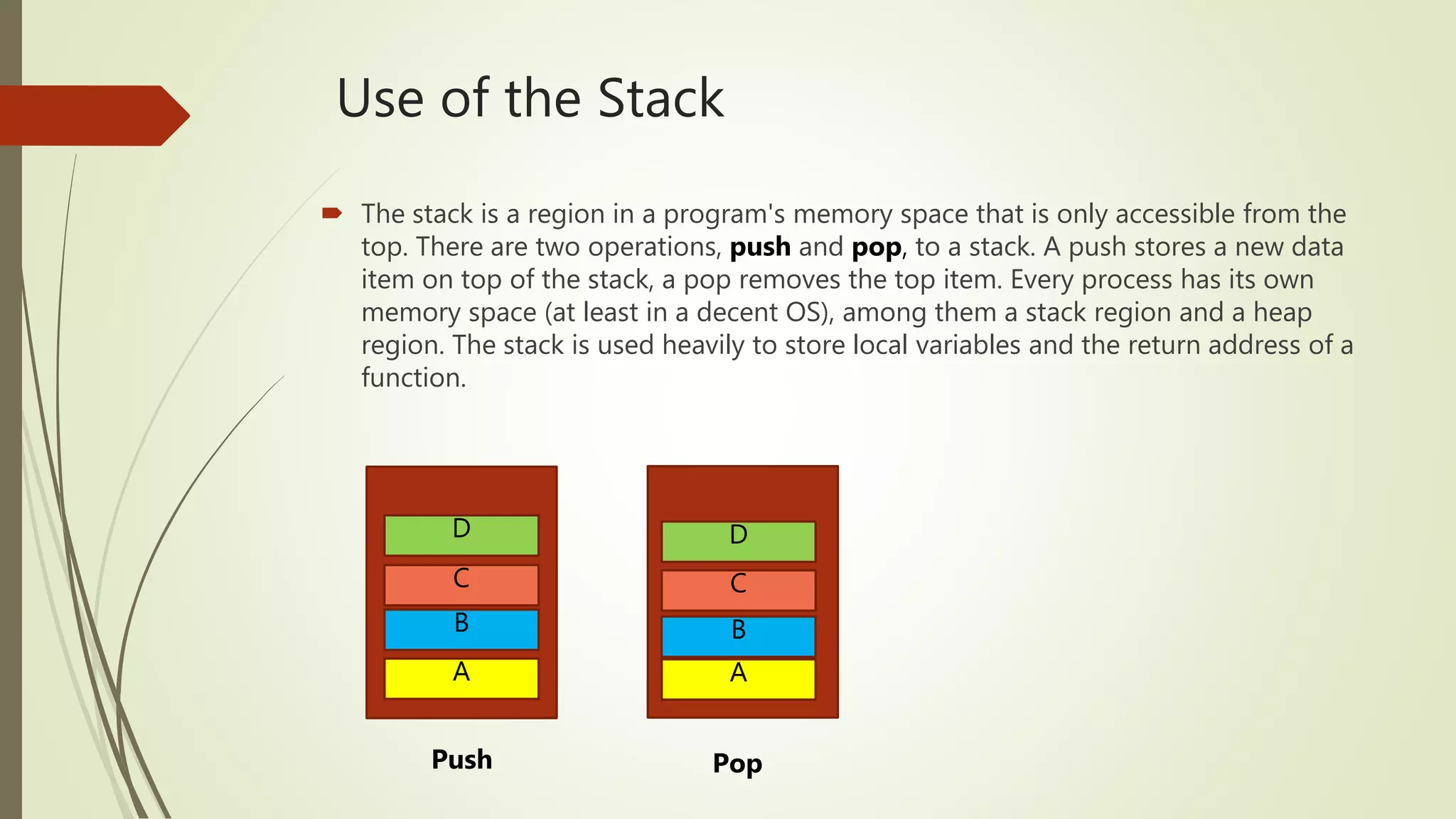
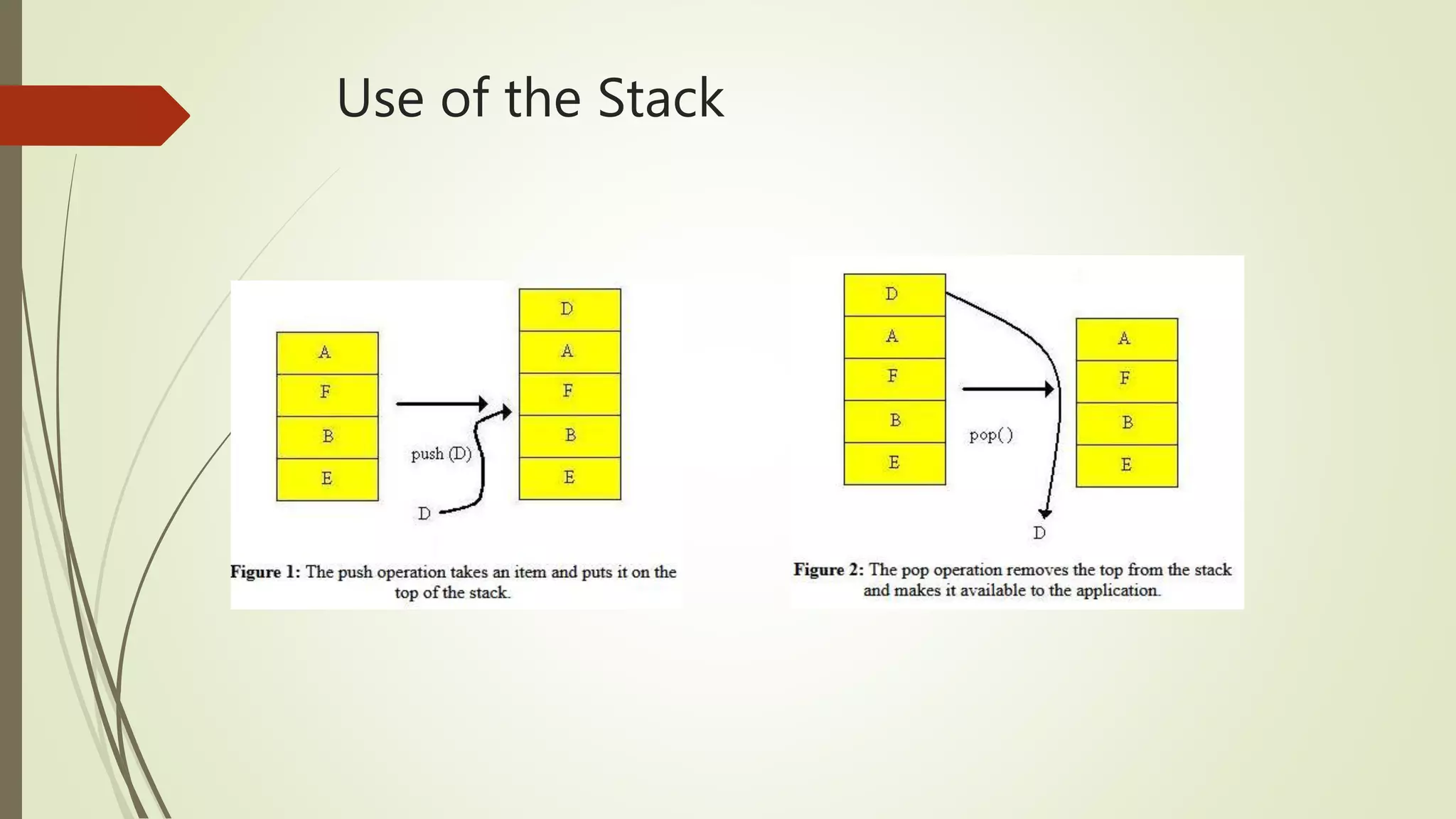
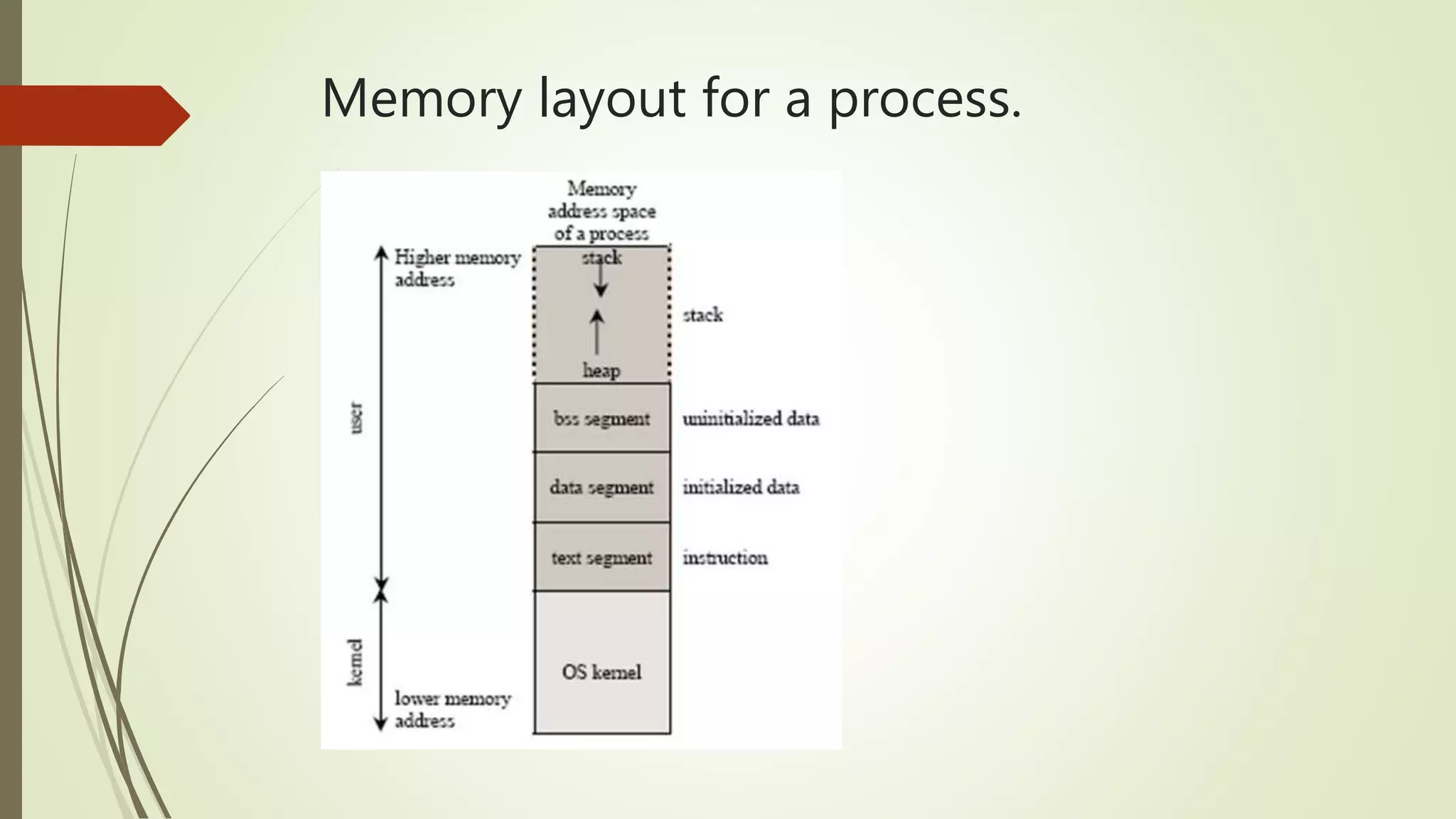
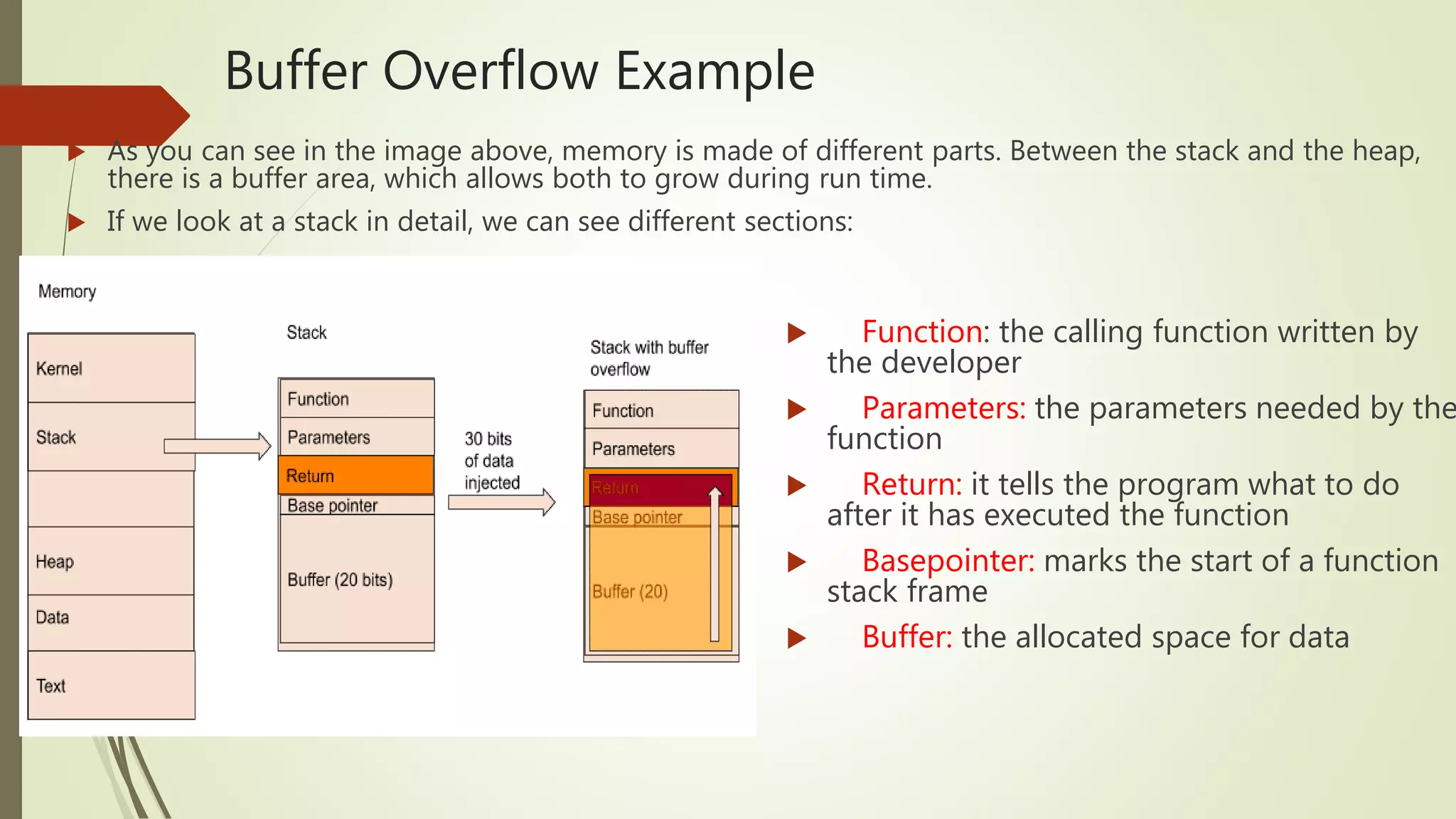
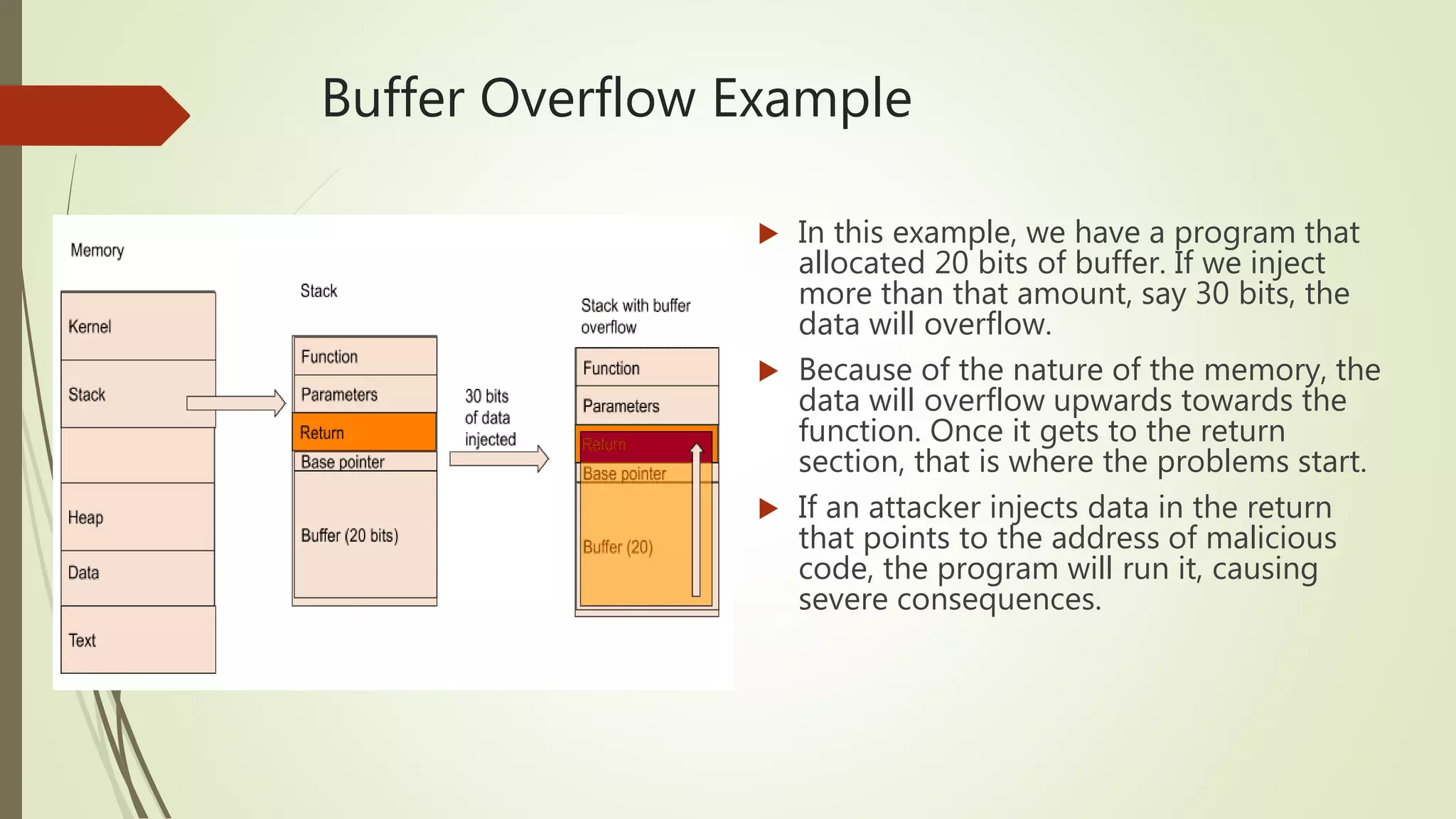
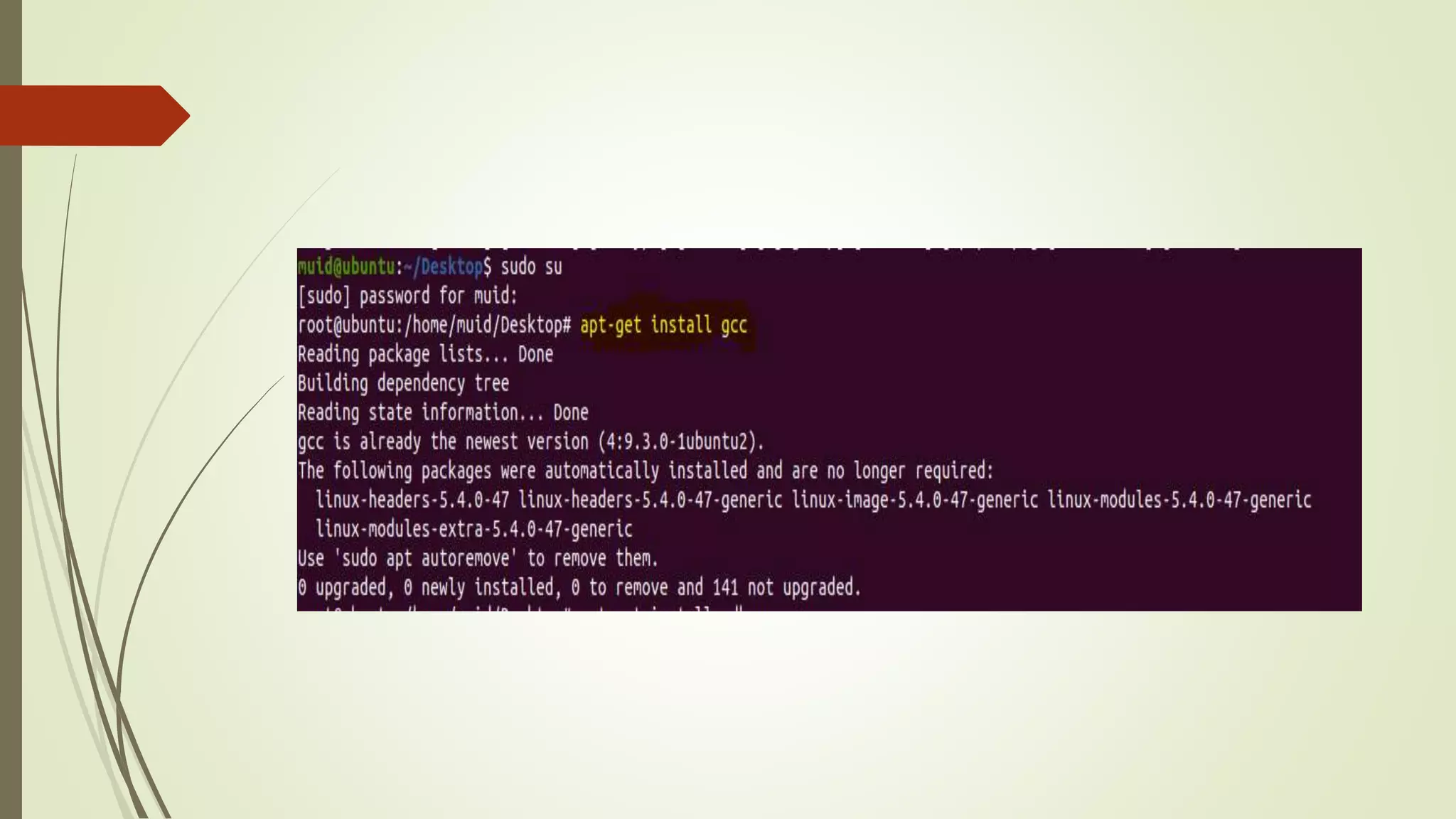
This document covers the concept of buffer overflow, a vulnerability that occurs when a program writes more data to a buffer than it can hold, potentially allowing attackers to overwrite adjacent memory. It discusses who is vulnerable, methods of exploitation, various types of buffer overflow attacks, and protective measures like address space randomization and data execution prevention. Additionally, it emphasizes the importance of using programming languages with built-in protections against such vulnerabilities.