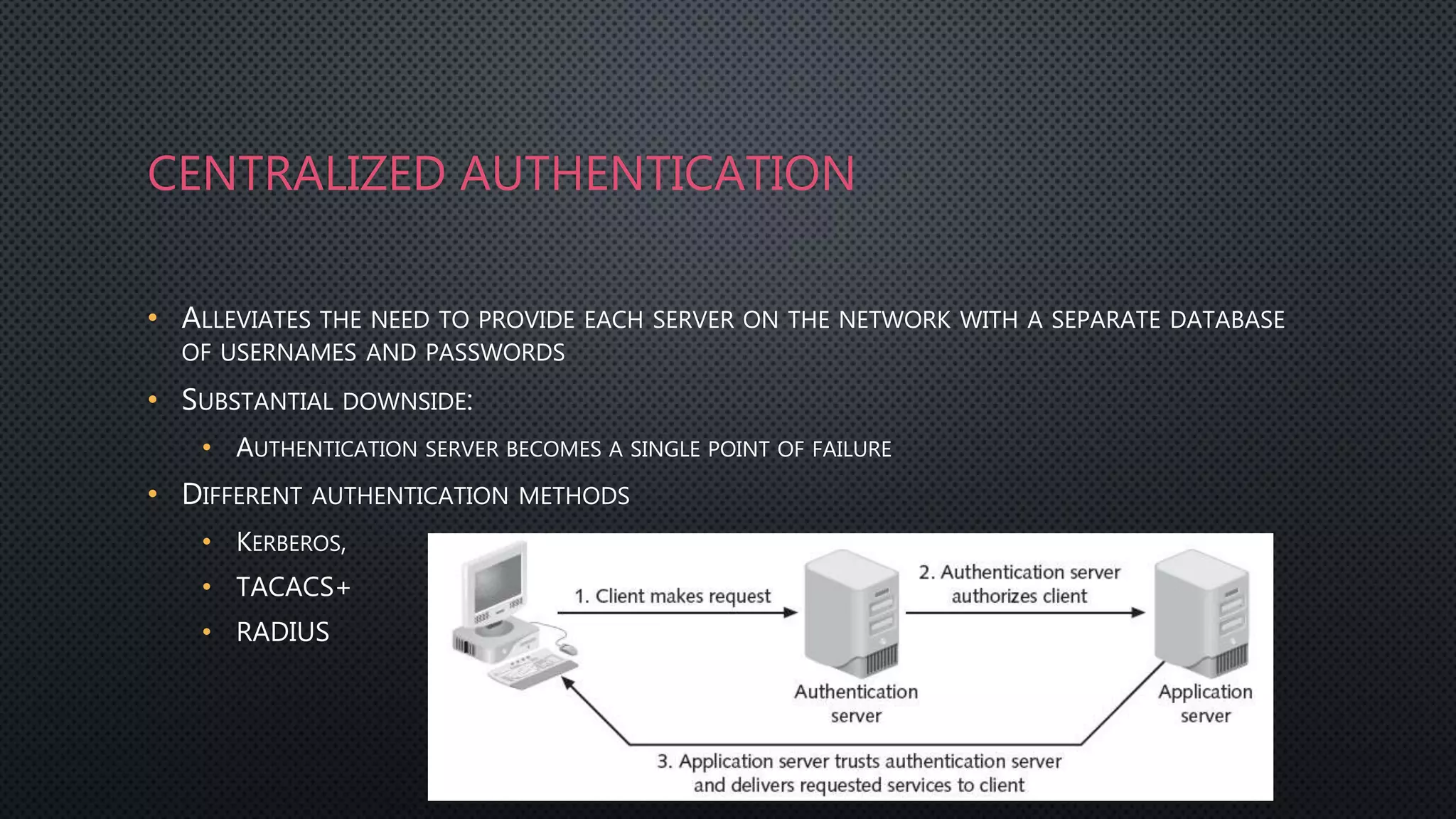
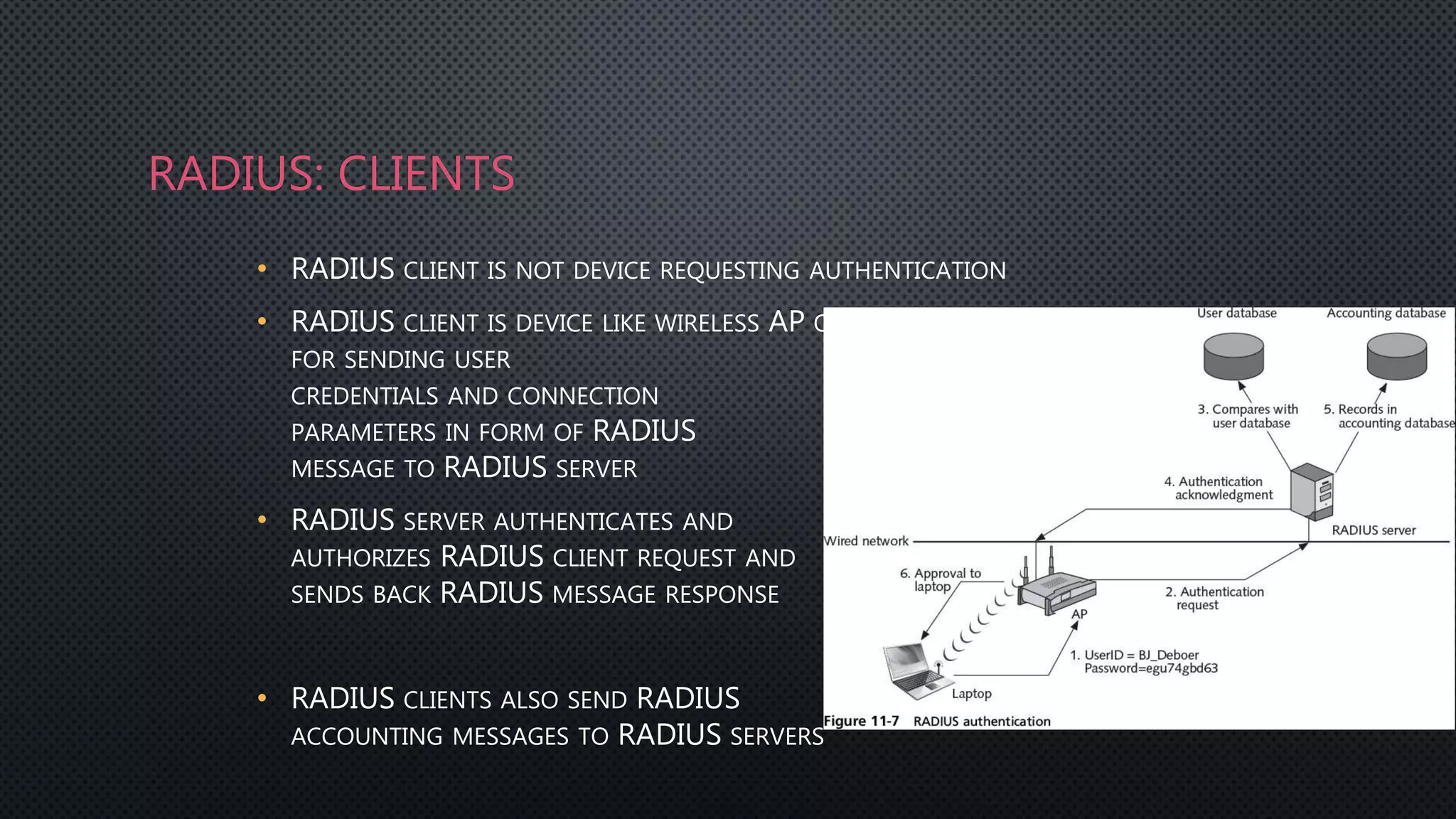
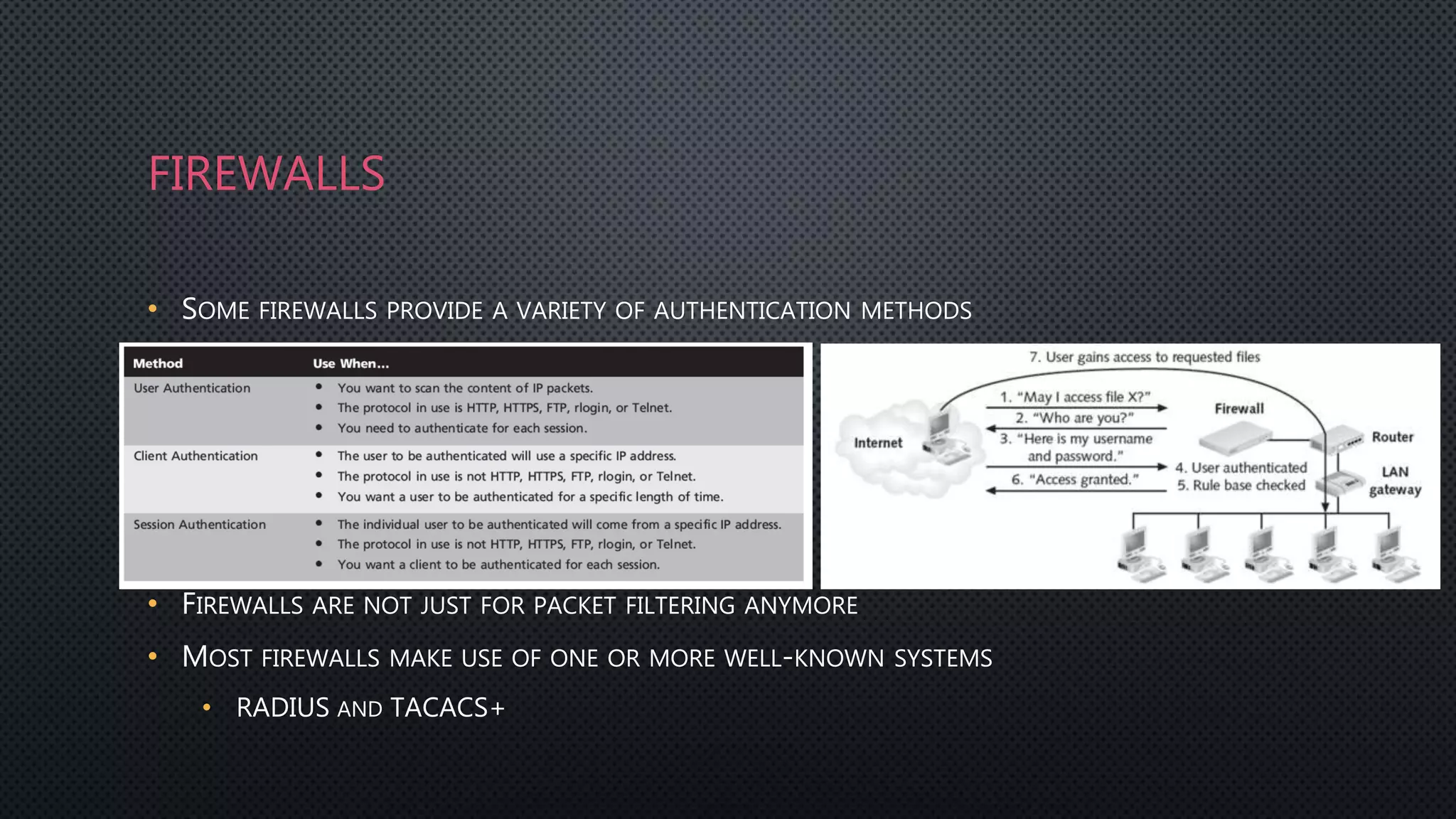
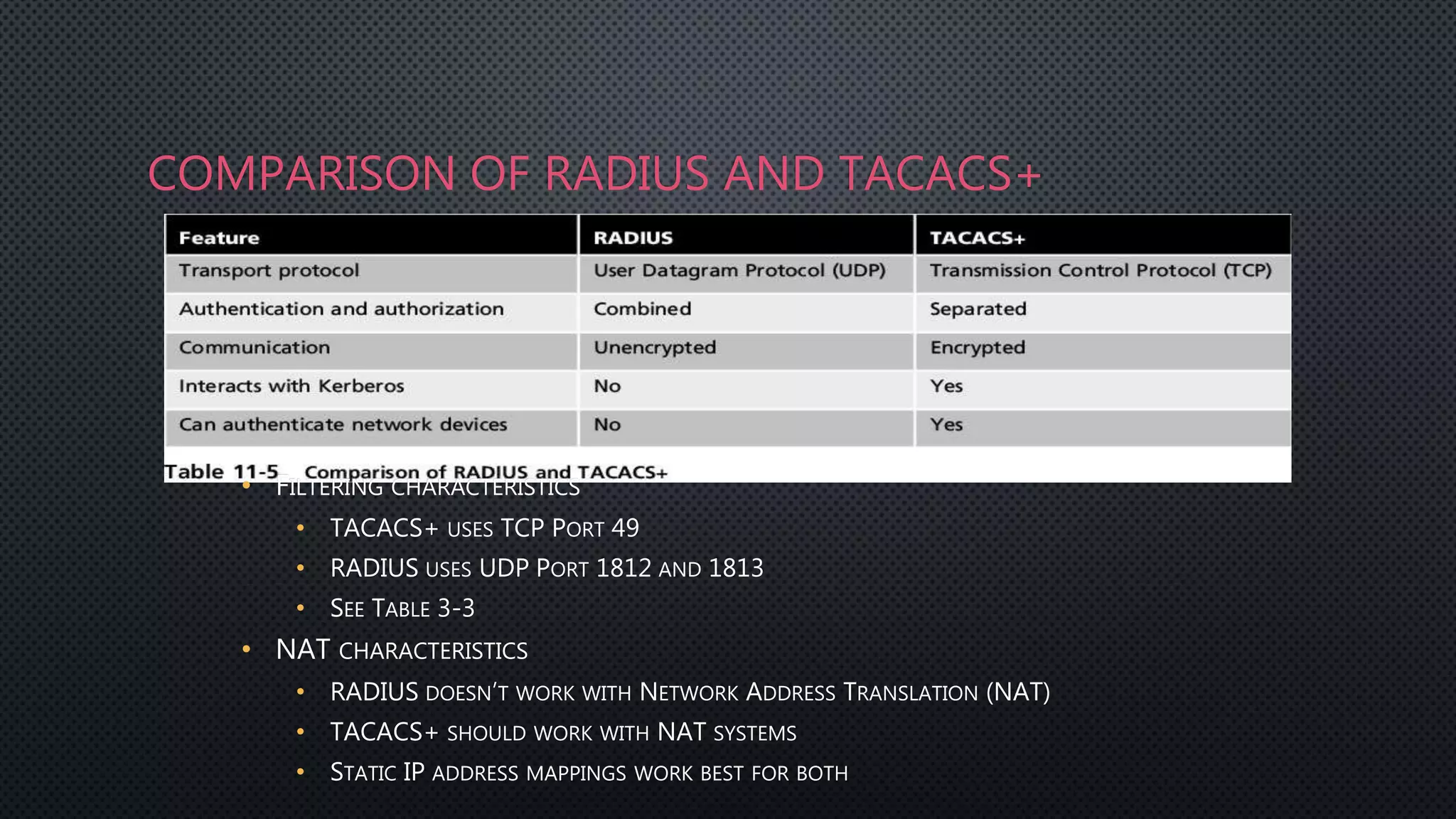
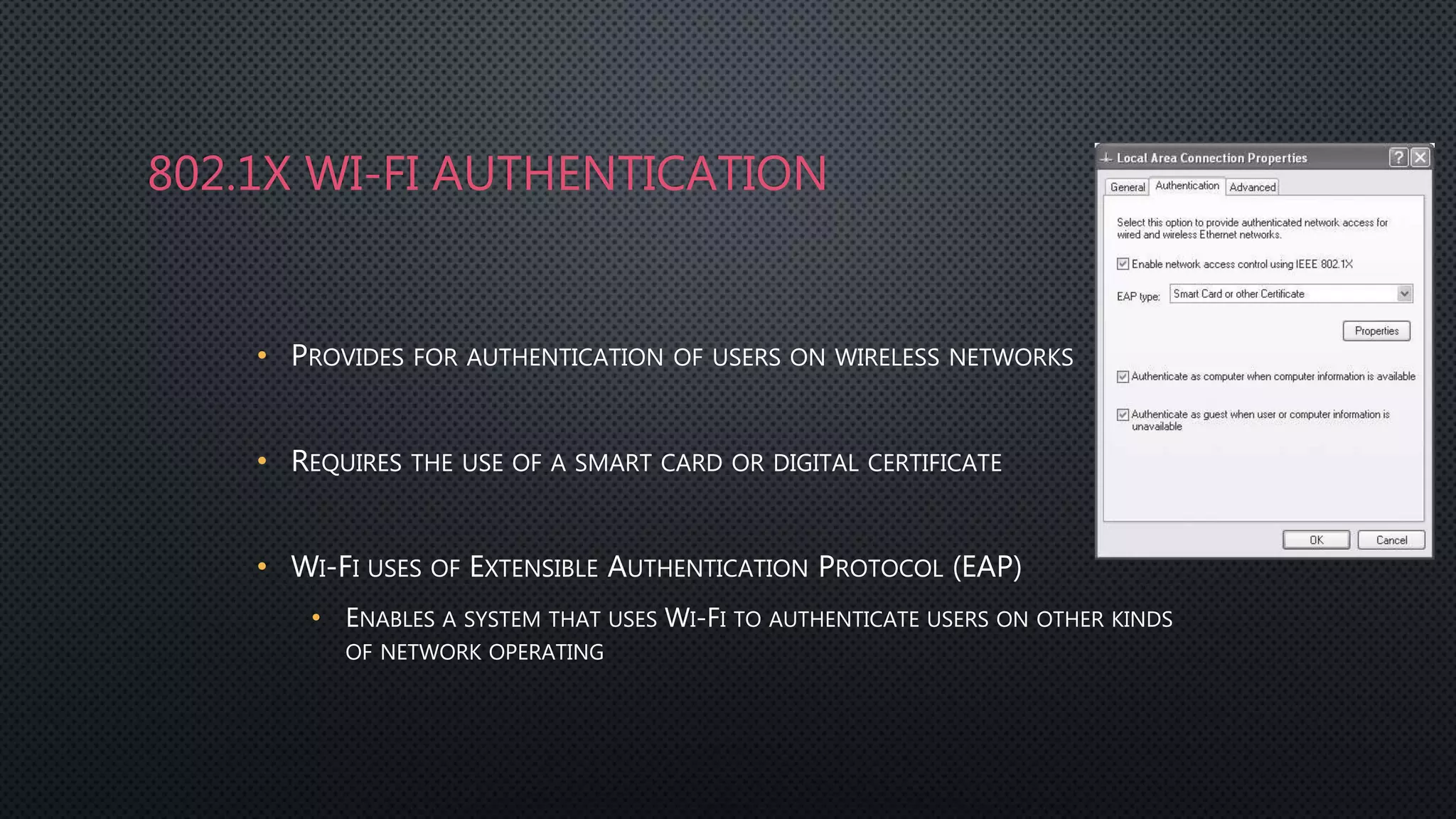
Authentication is the process of verifying a user's identity by requiring them to provide credentials like a password or certificate. Common authentication methods include centralized authentication services like RADIUS, TACACS+, and Kerberos which verify credentials on a network authentication server. Firewalls can integrate with these authentication servers to provide user authentication and authorization when accessing the network.