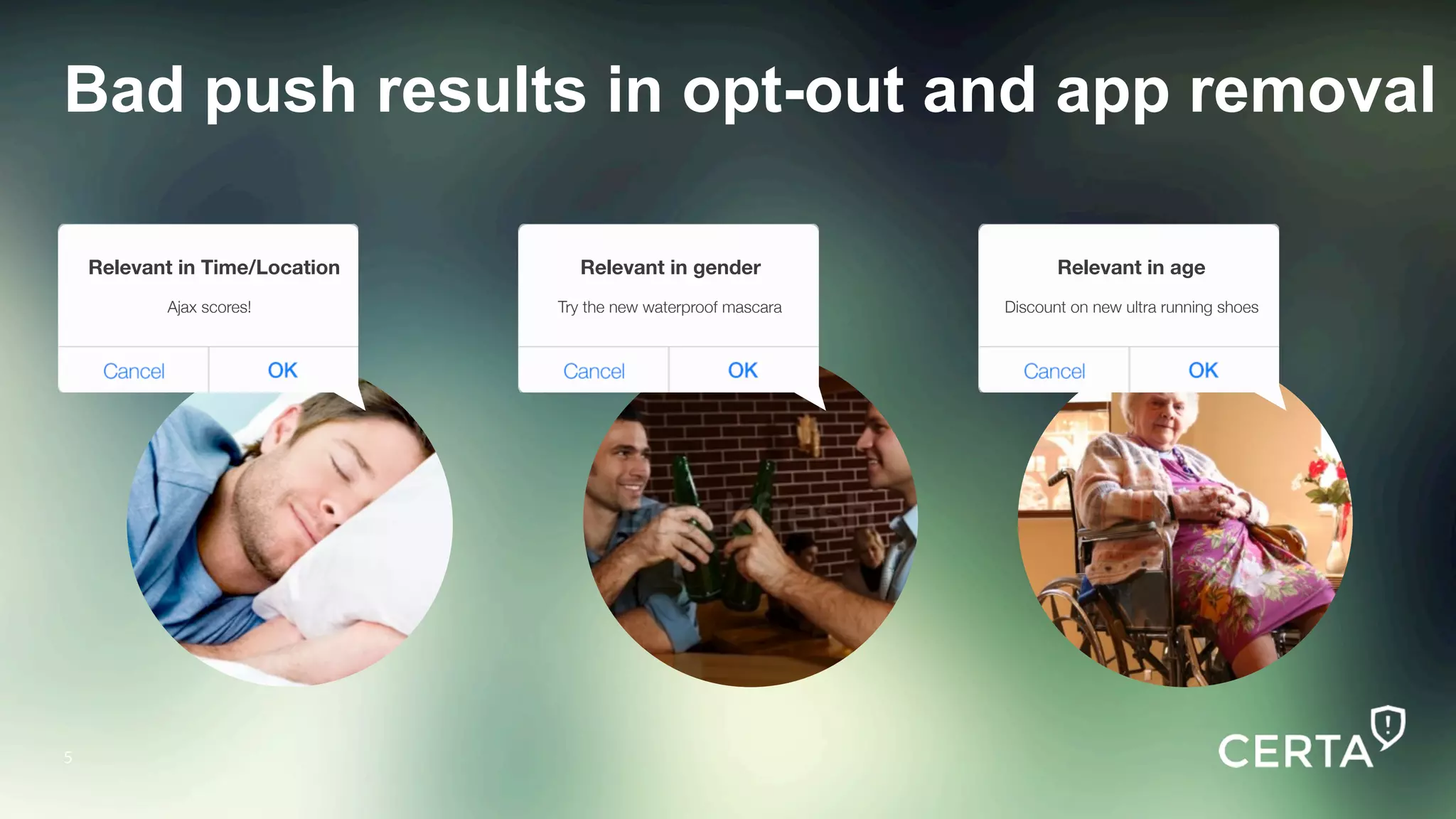
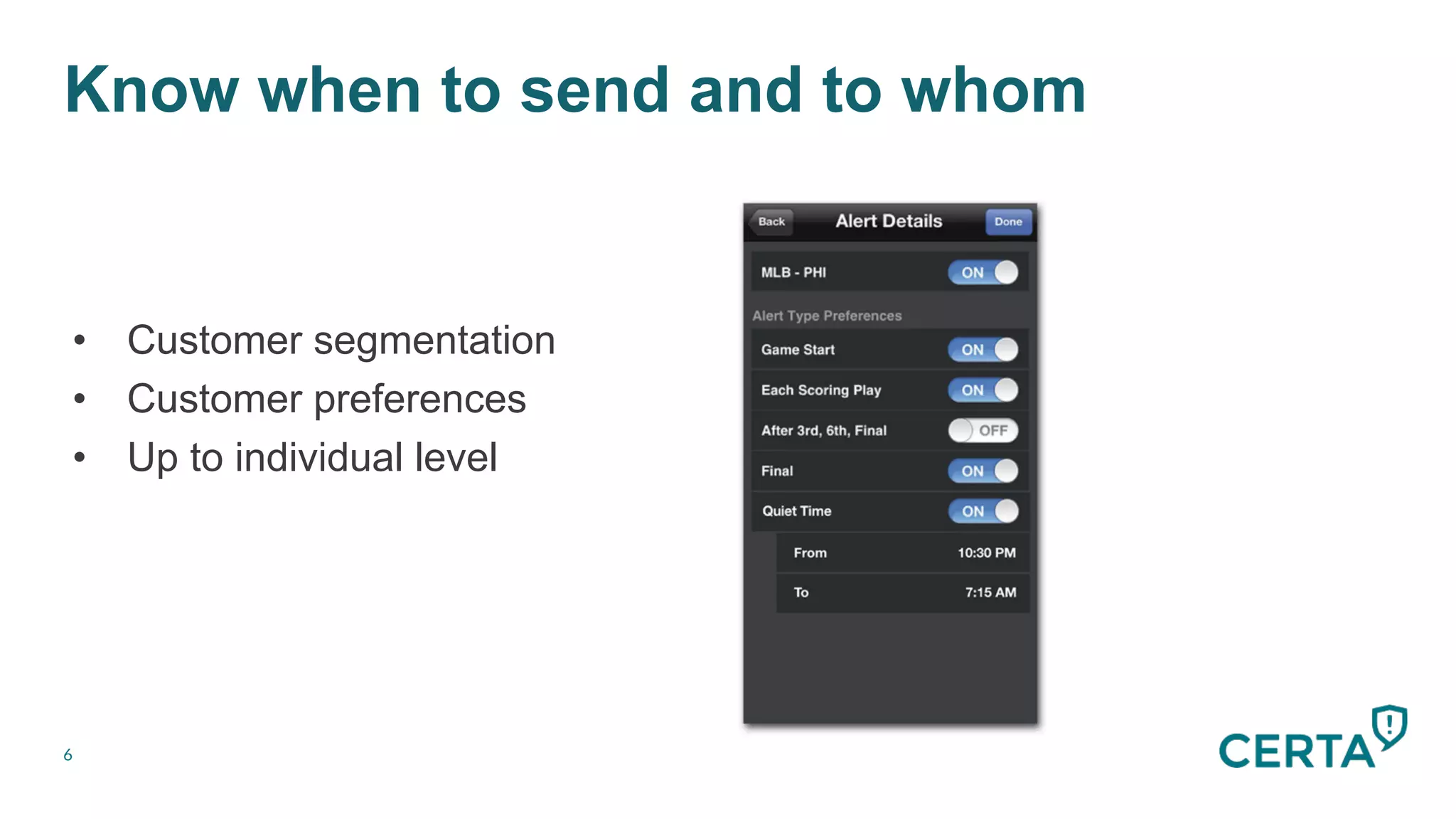
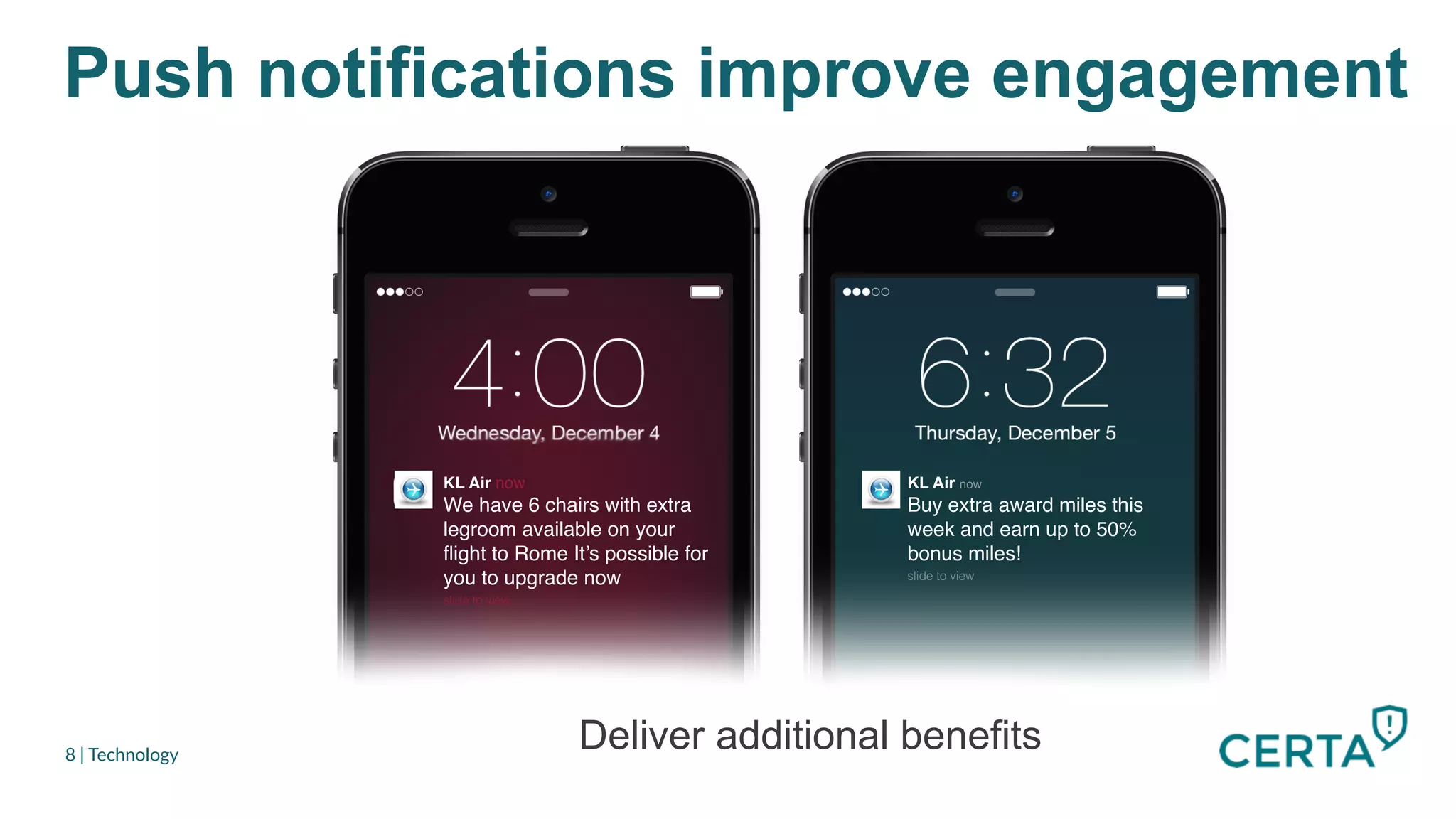
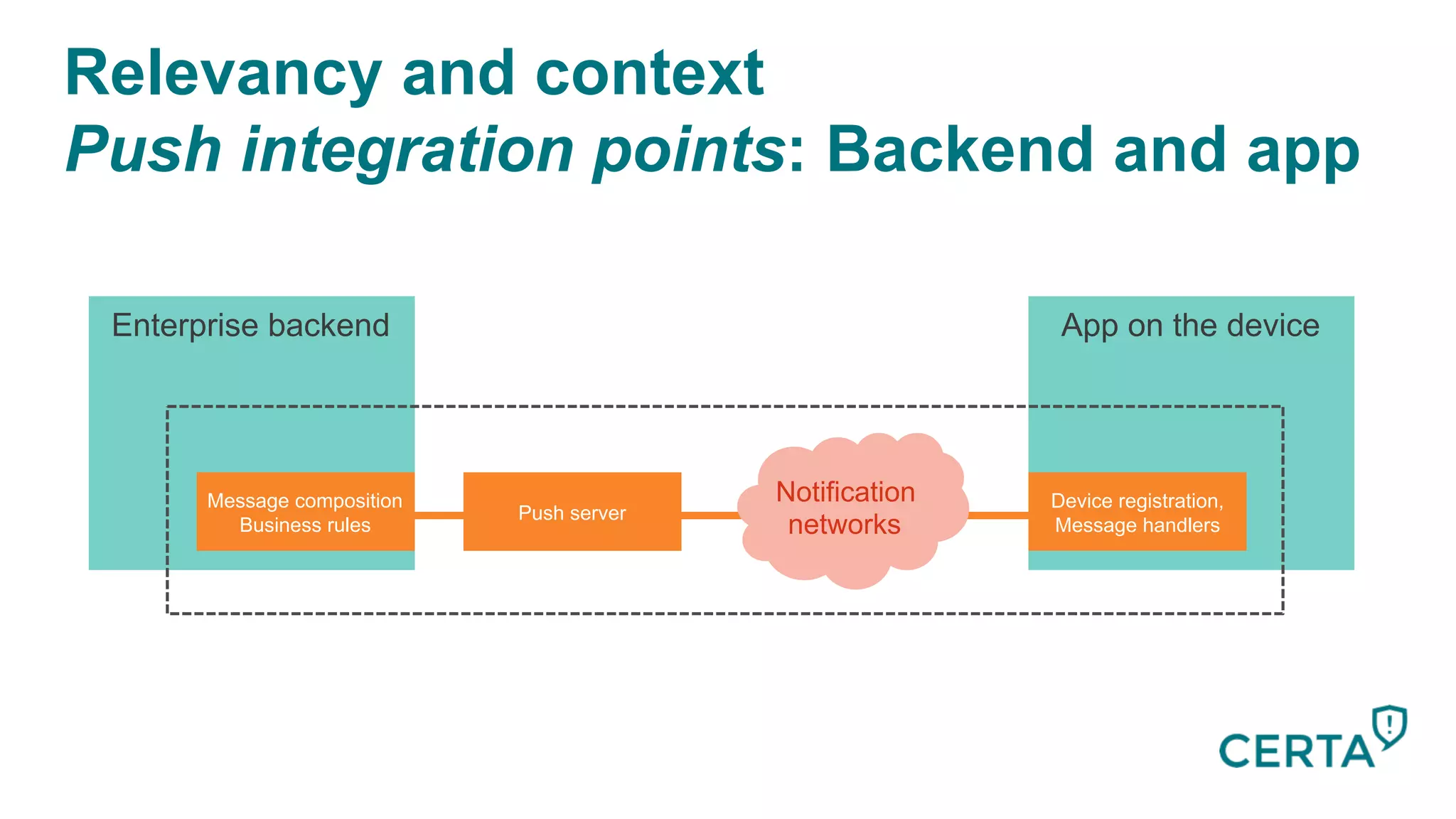
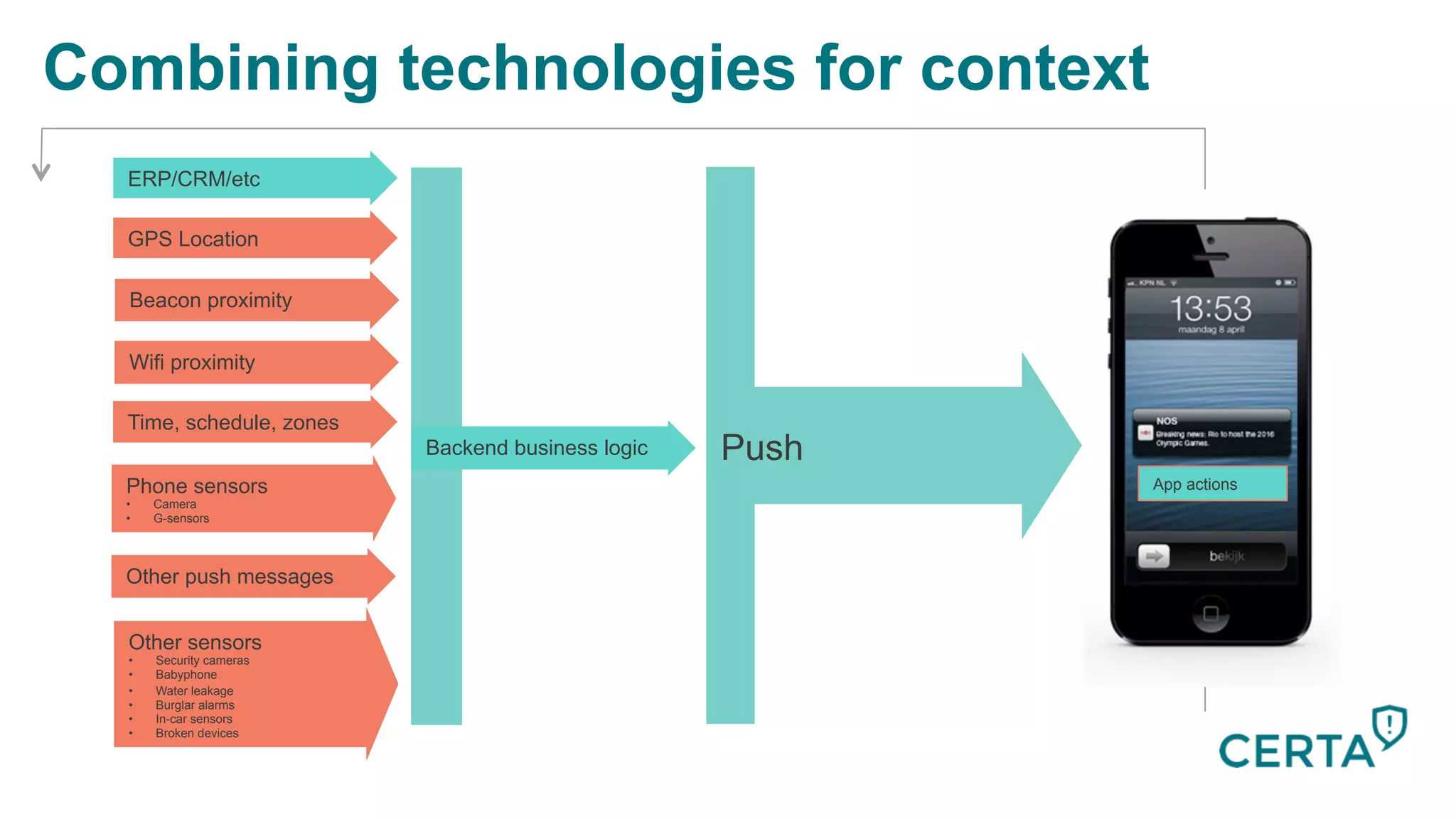
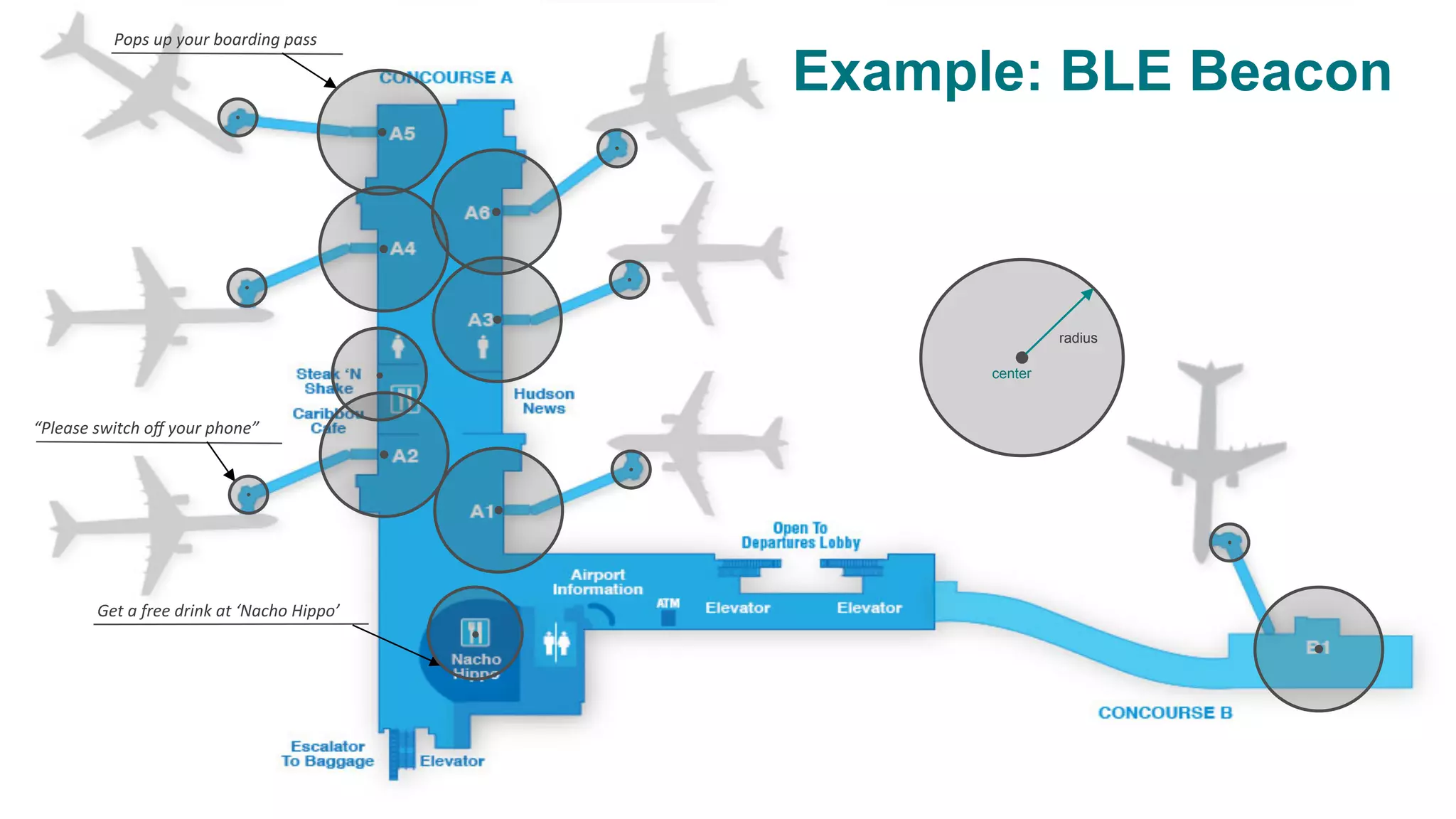
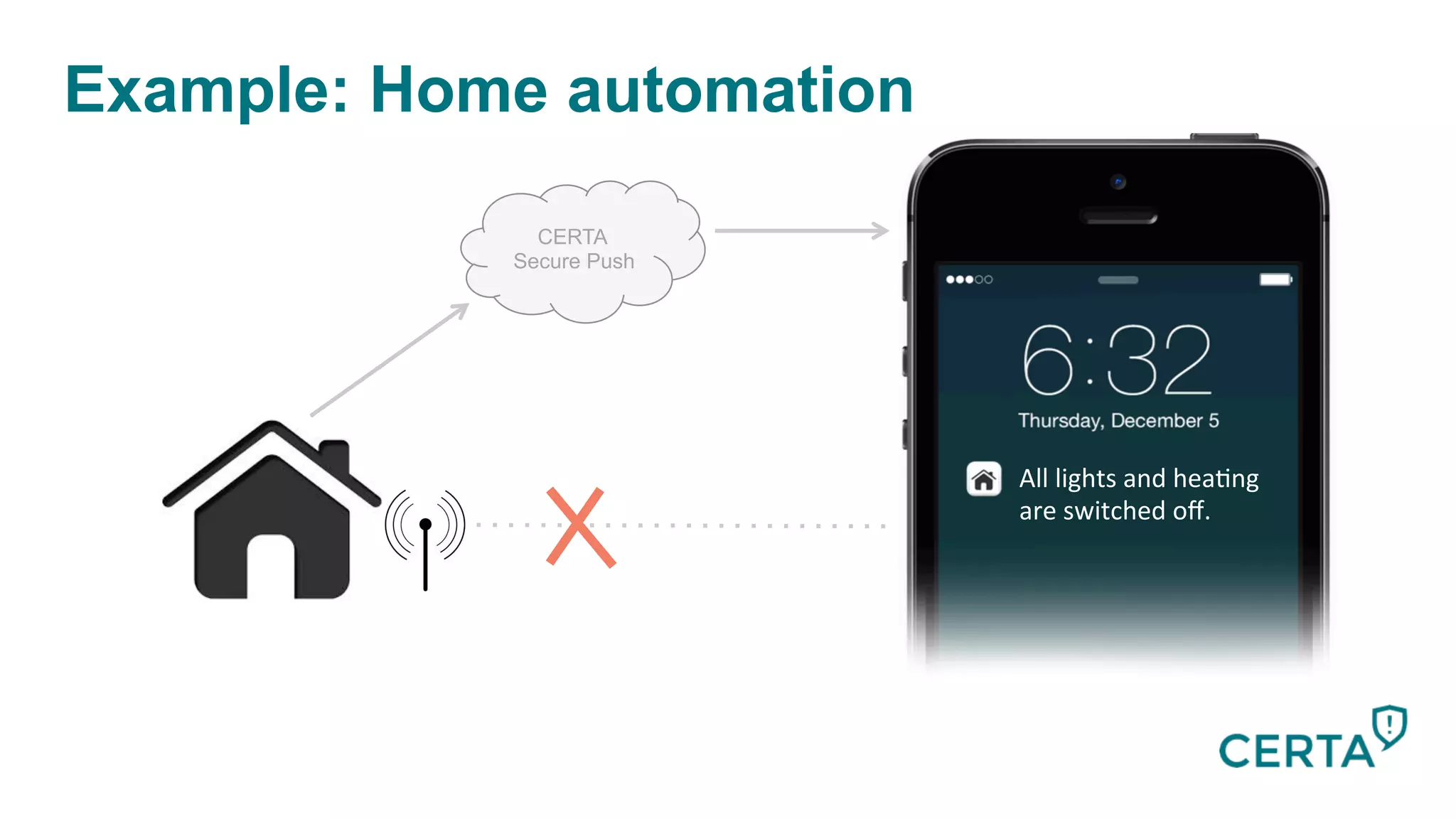
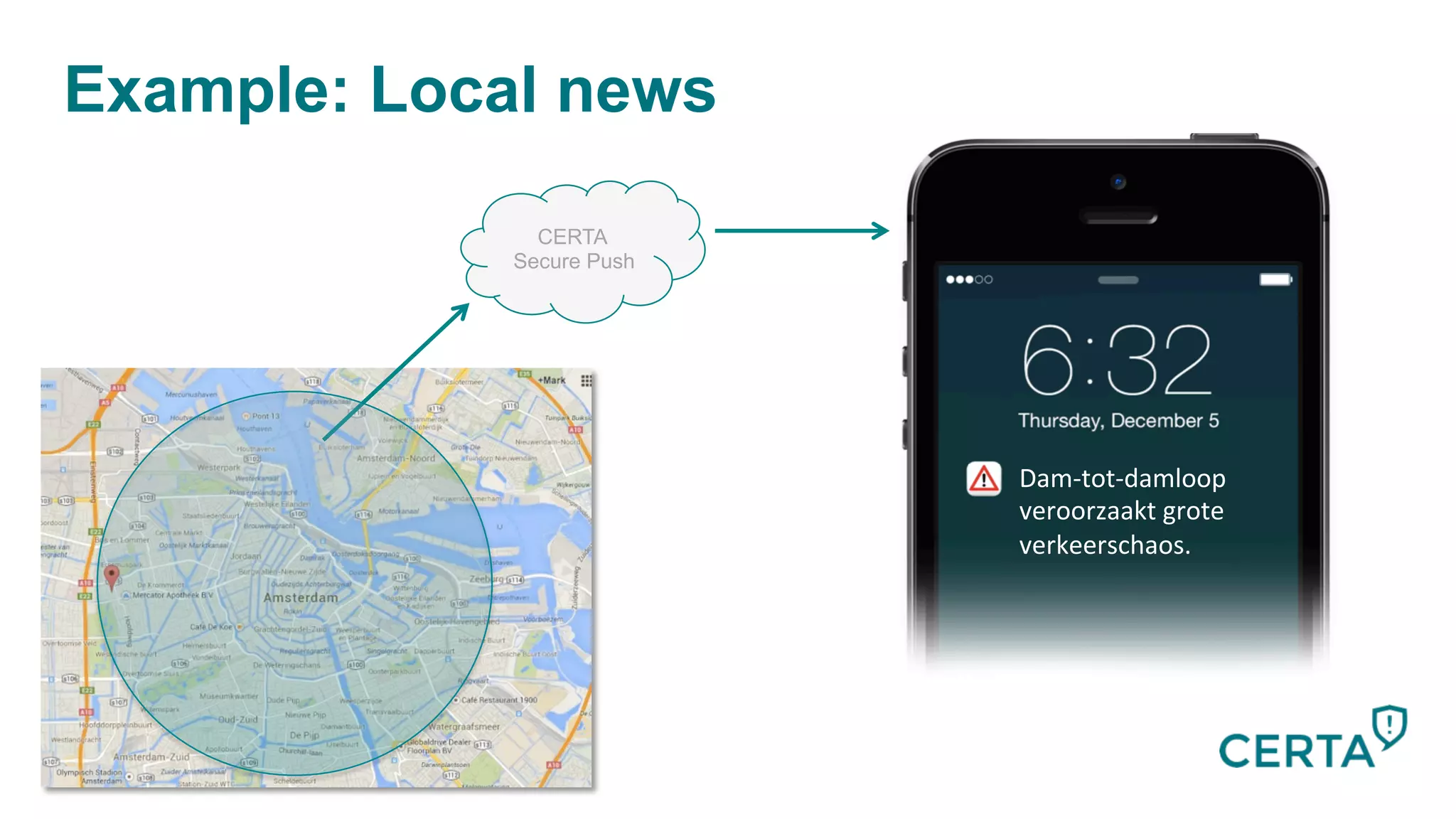
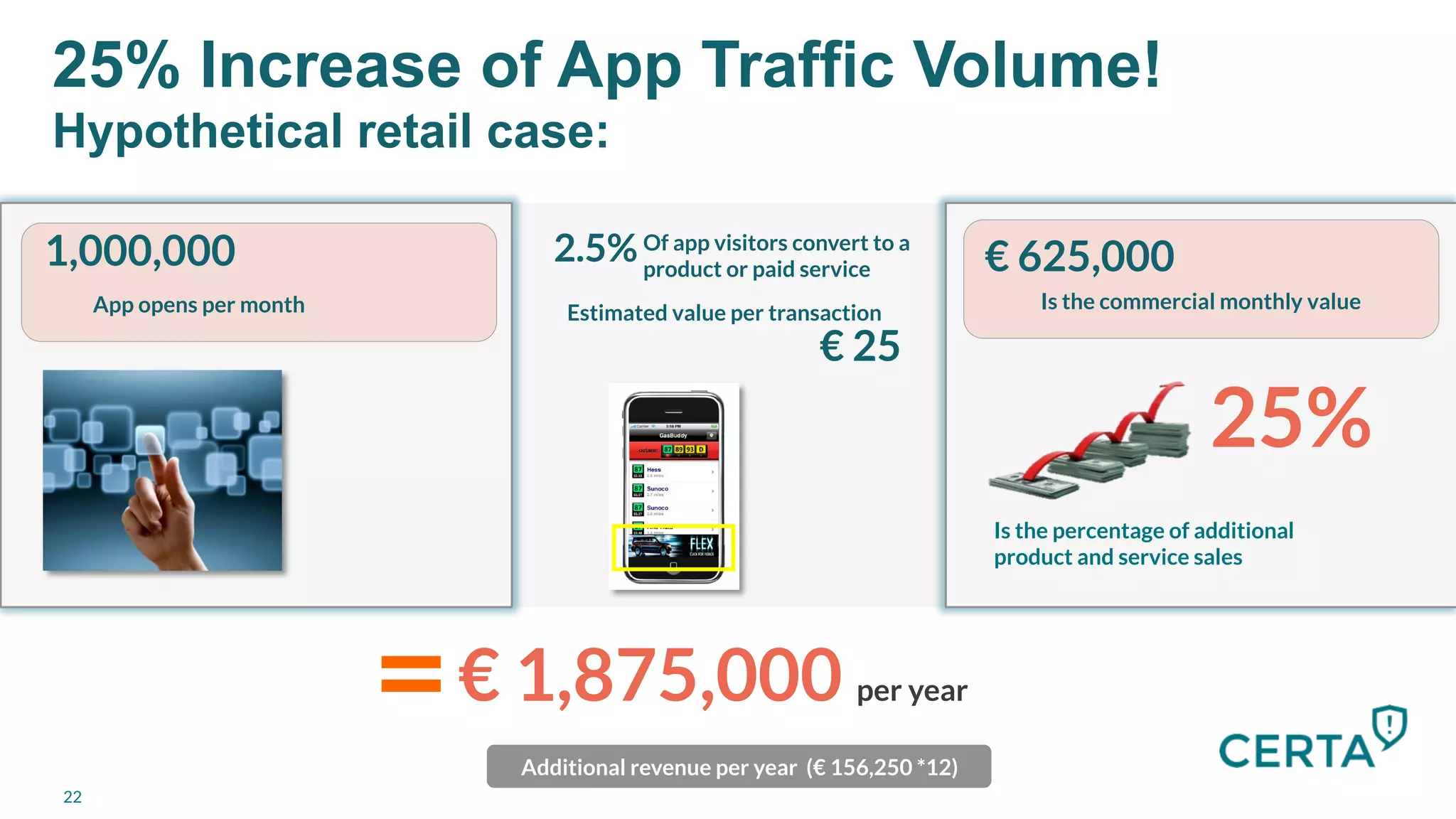
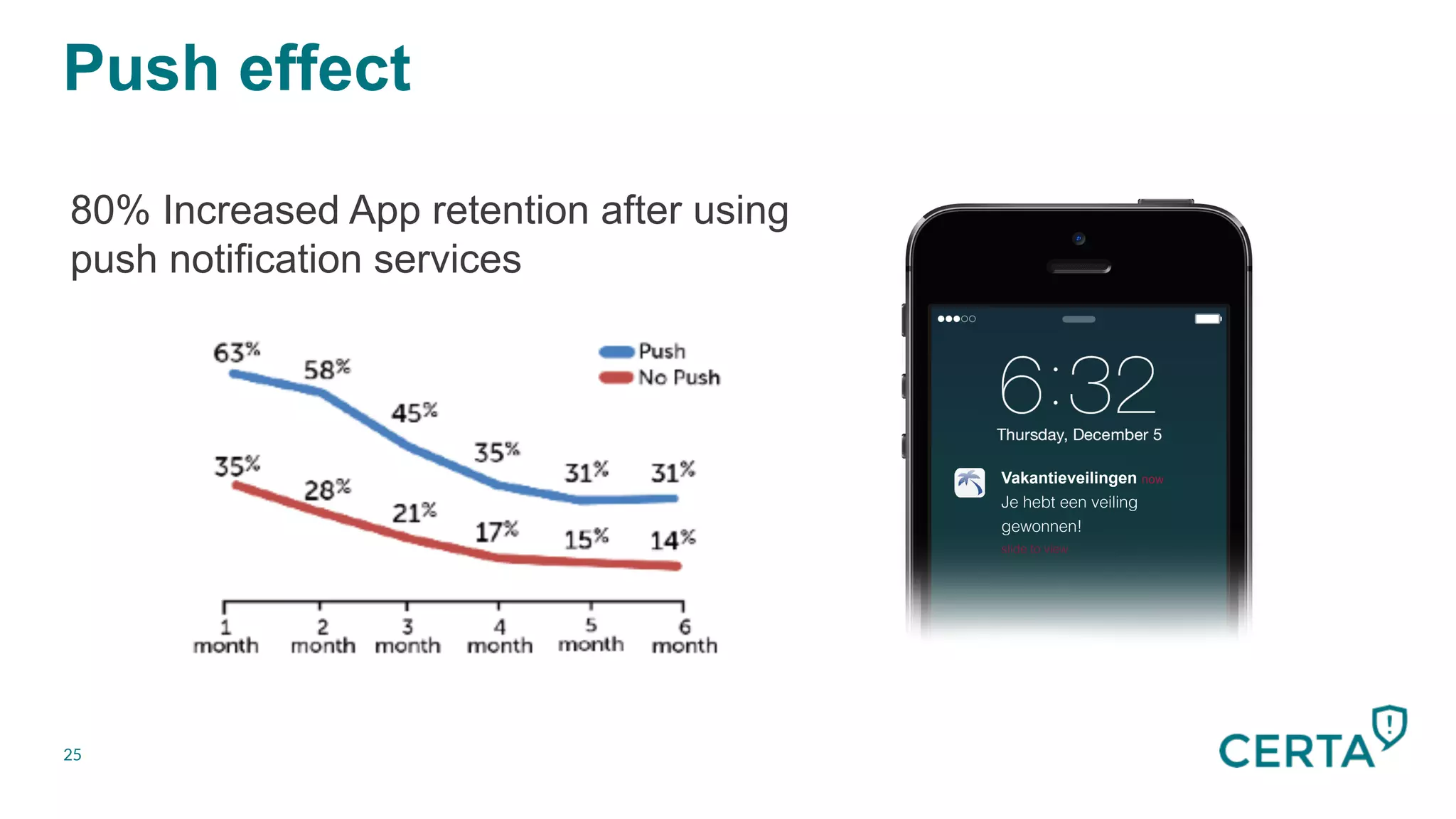
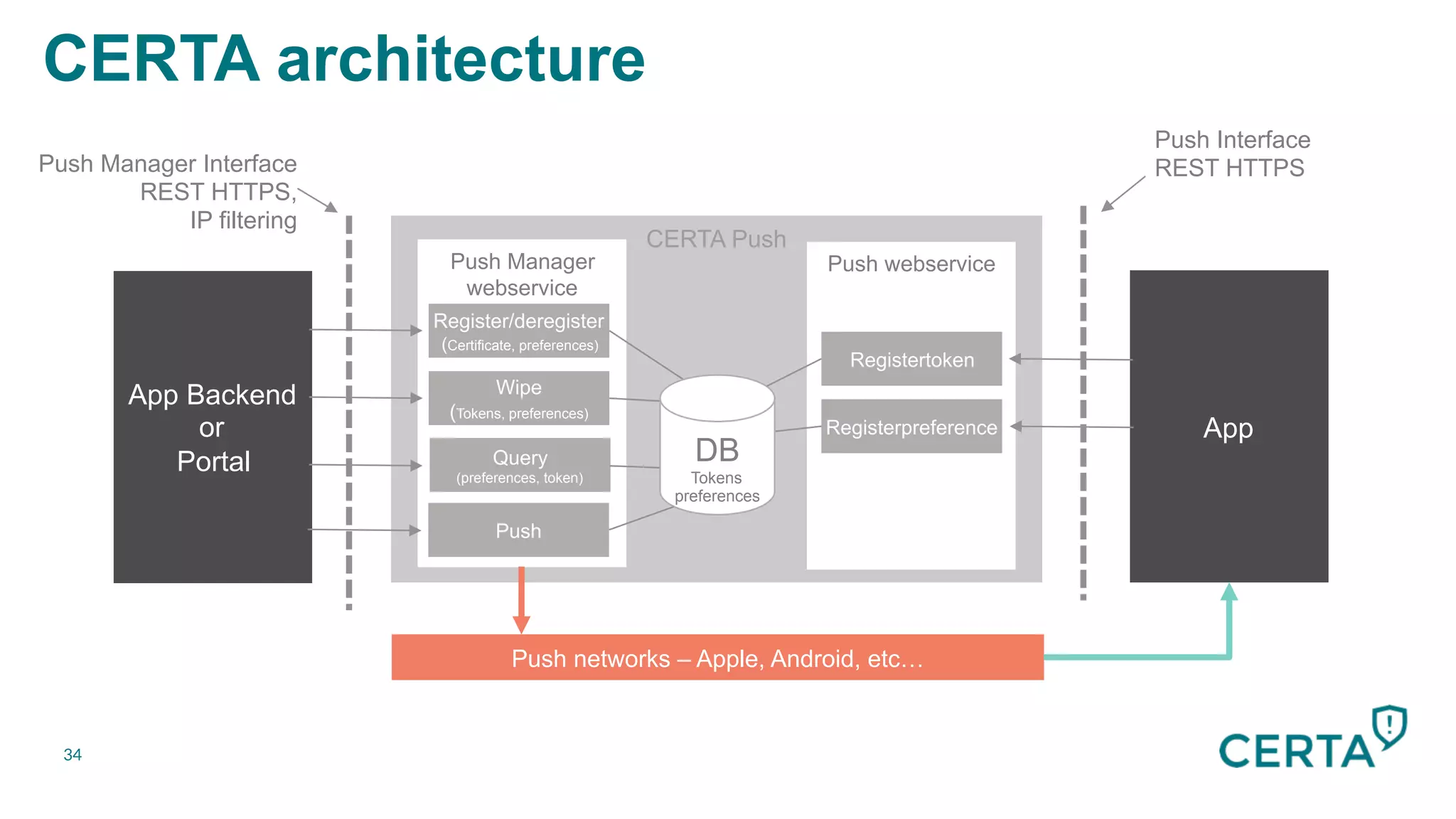
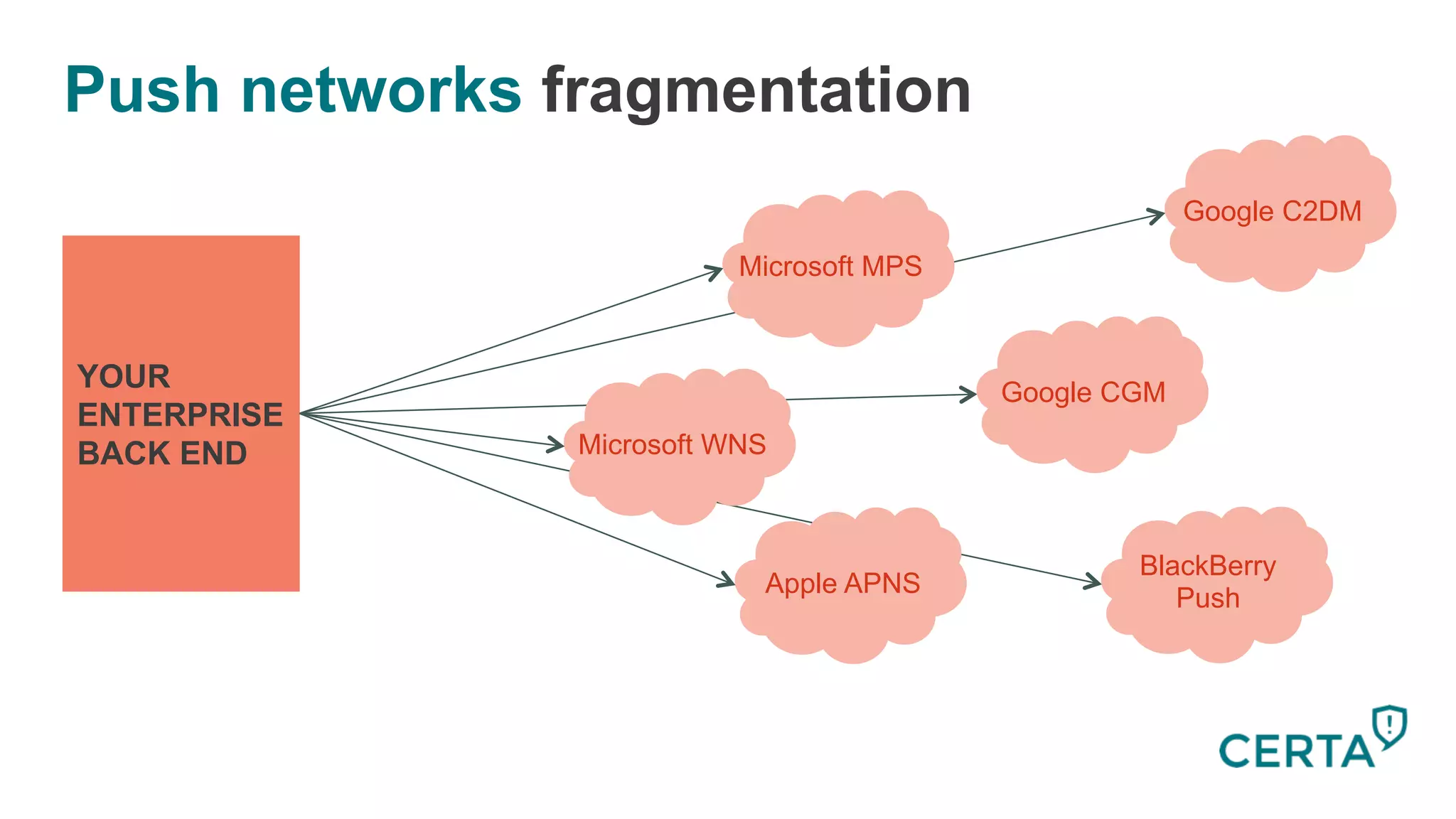
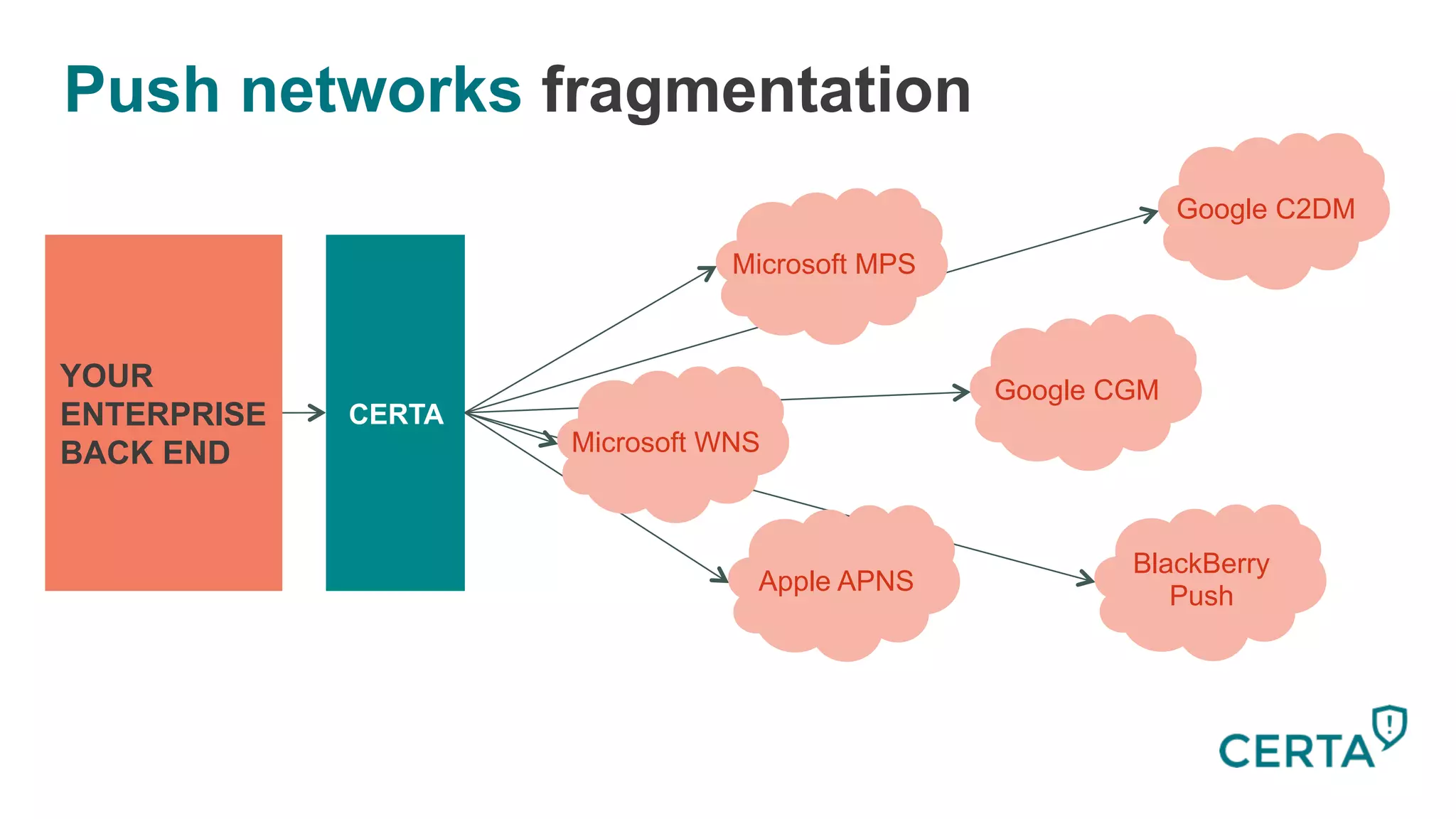
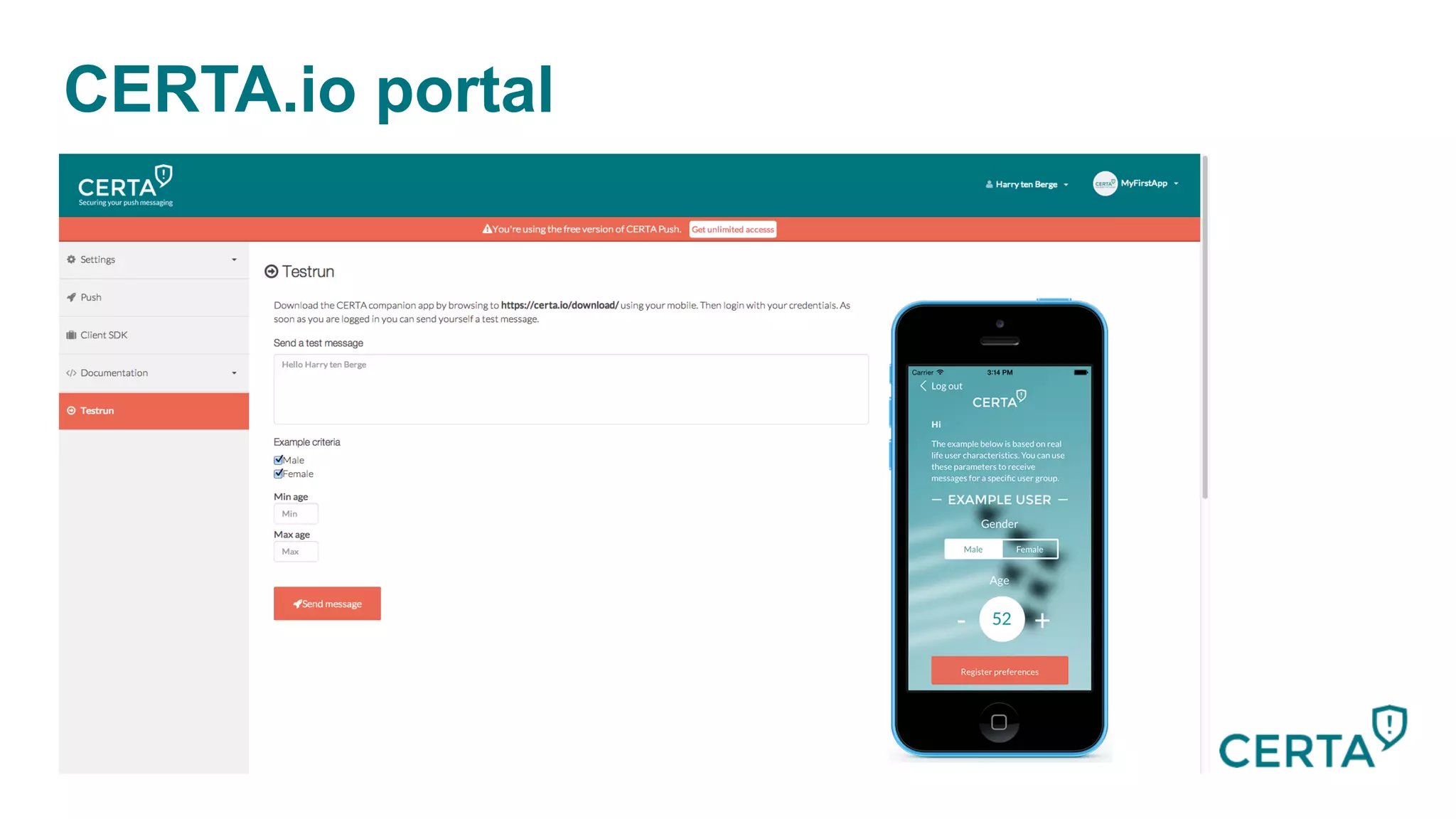
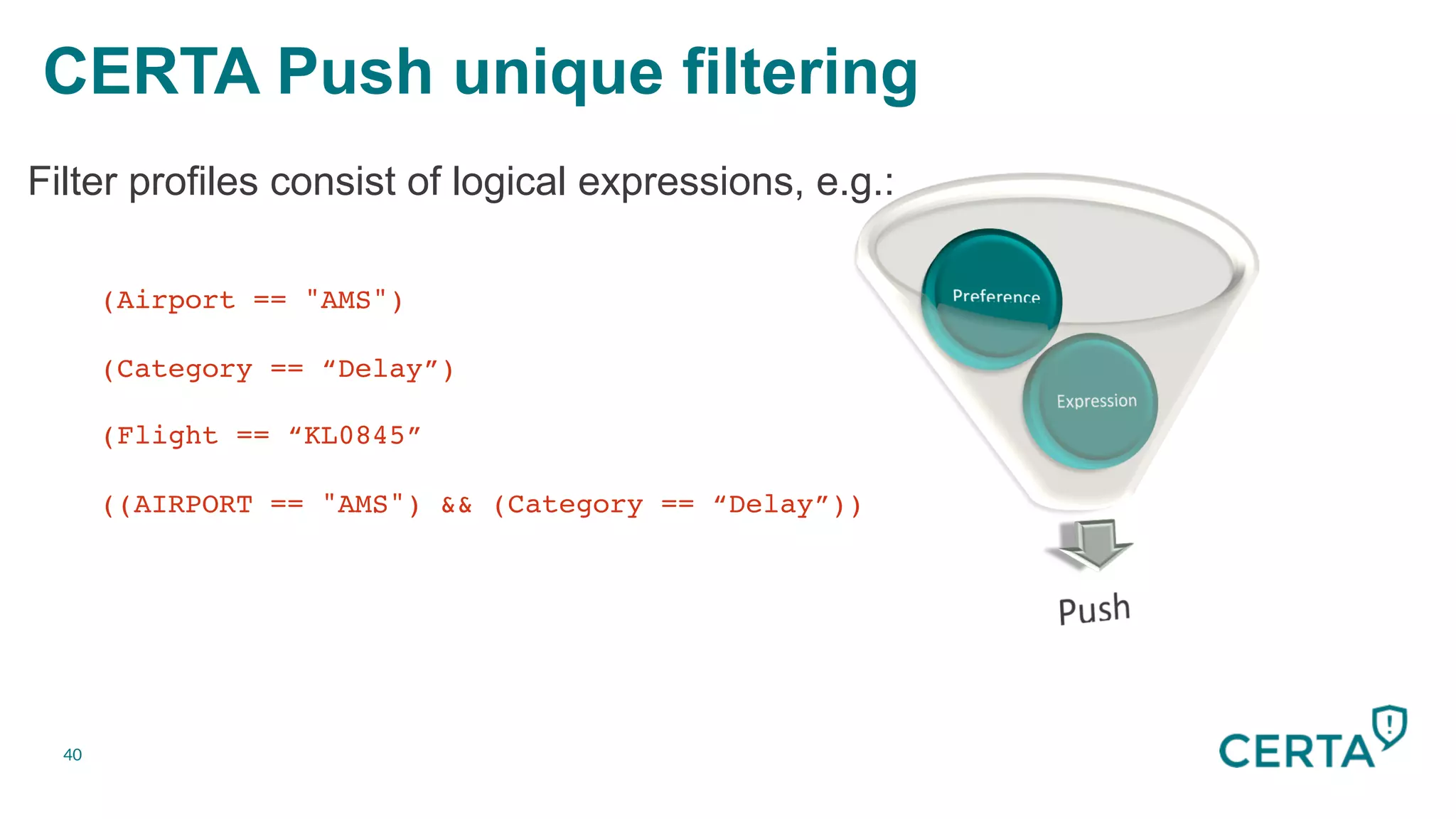
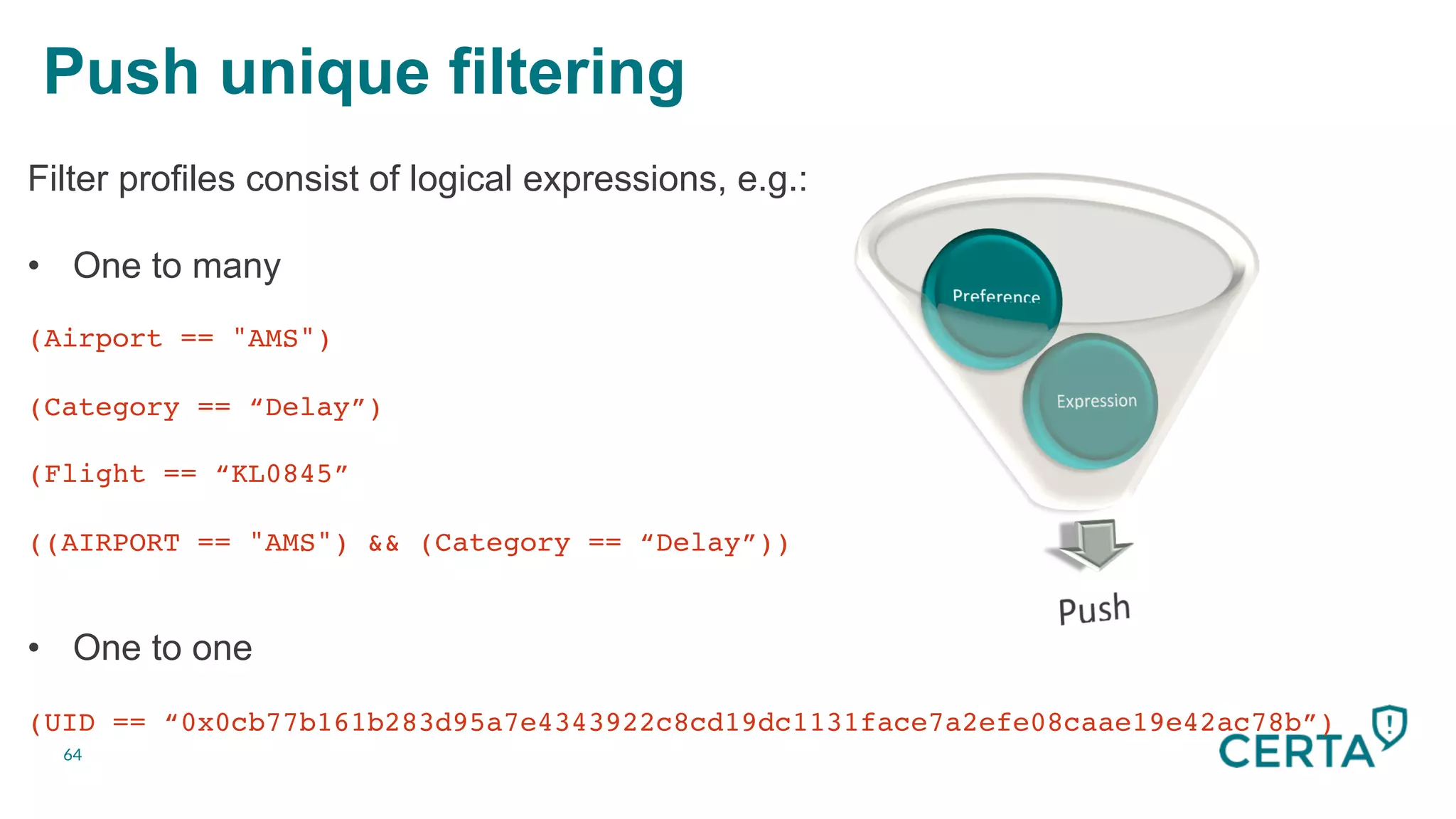
The document discusses the integration and effectiveness of push notifications in mobile marketing, highlighting their role in increasing user engagement and revenue. It emphasizes the importance of relevance, customer segmentation, and timing when sending push notifications, as well as the necessity of incorporating these notifications into broader marketing strategies. Additionally, legal and security considerations regarding data privacy and protection in the context of push notifications are addressed.