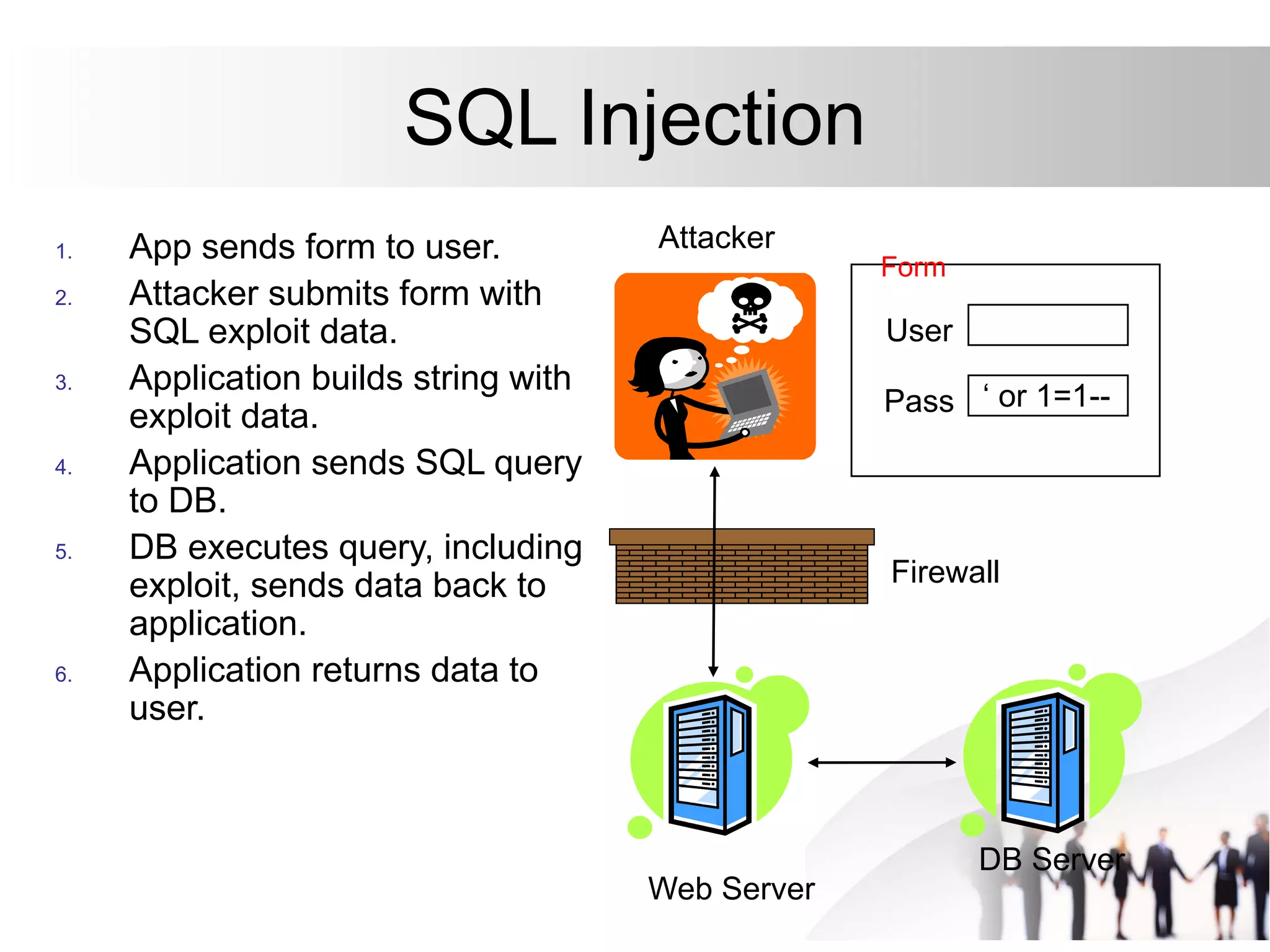
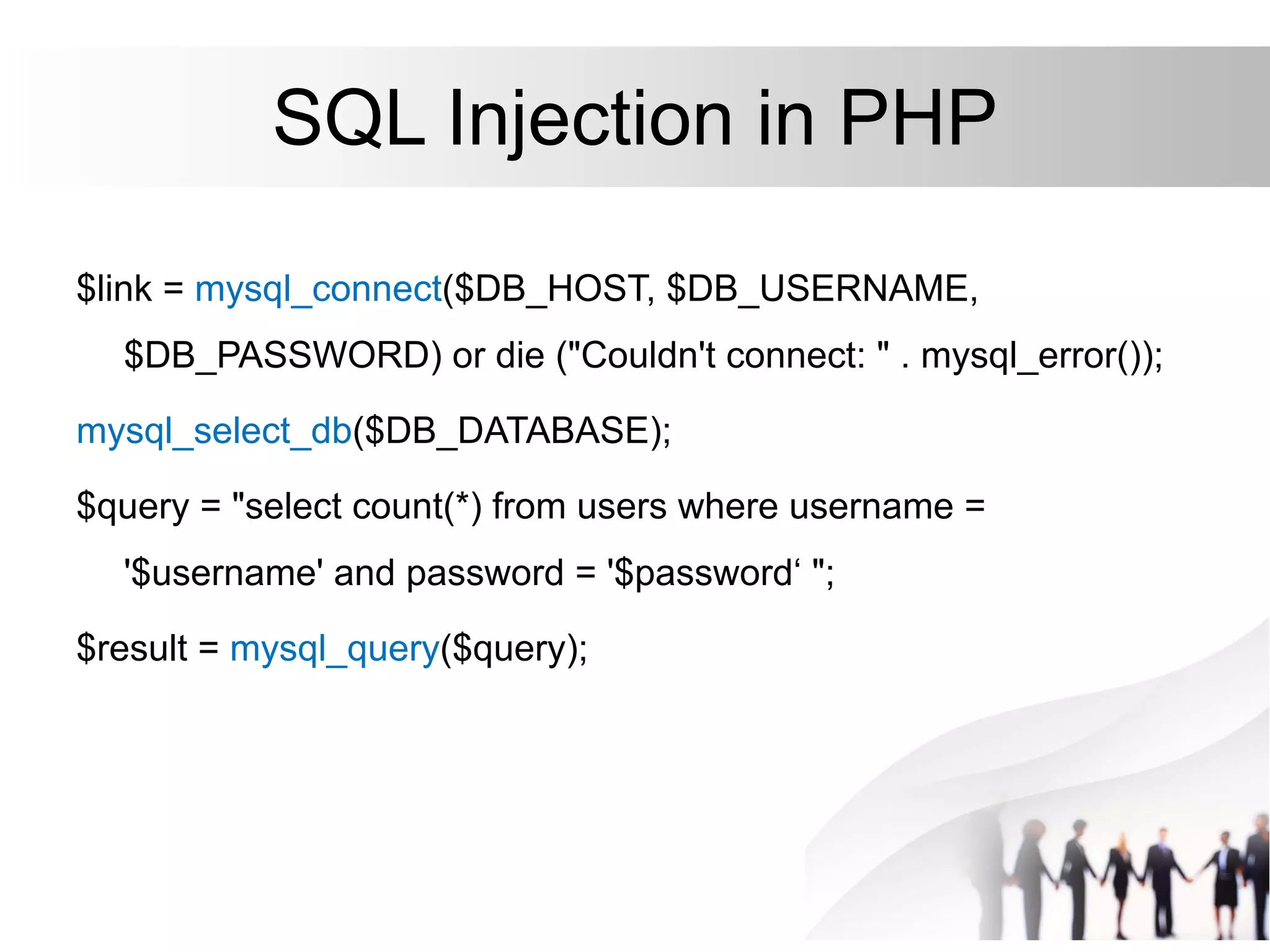
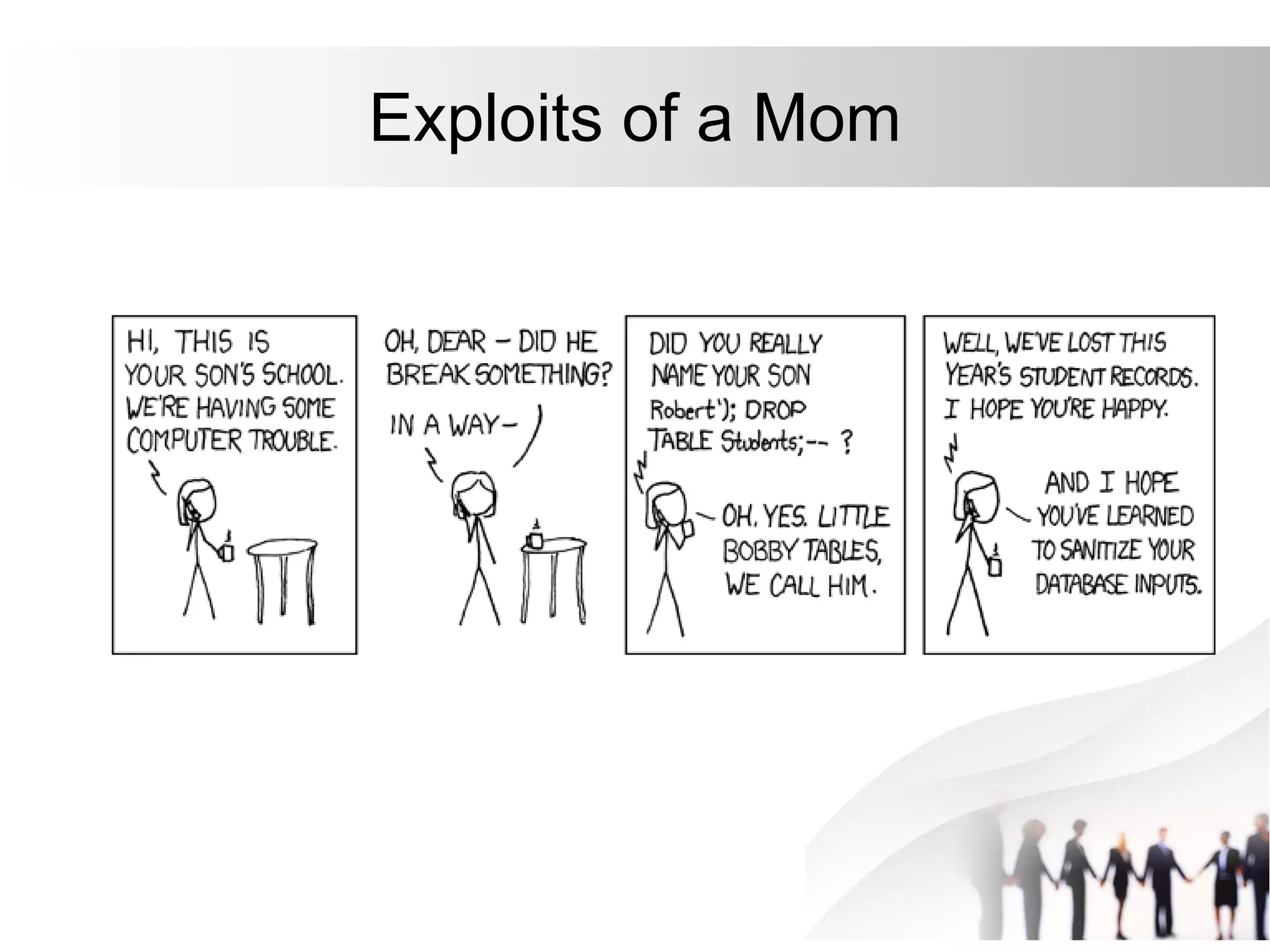
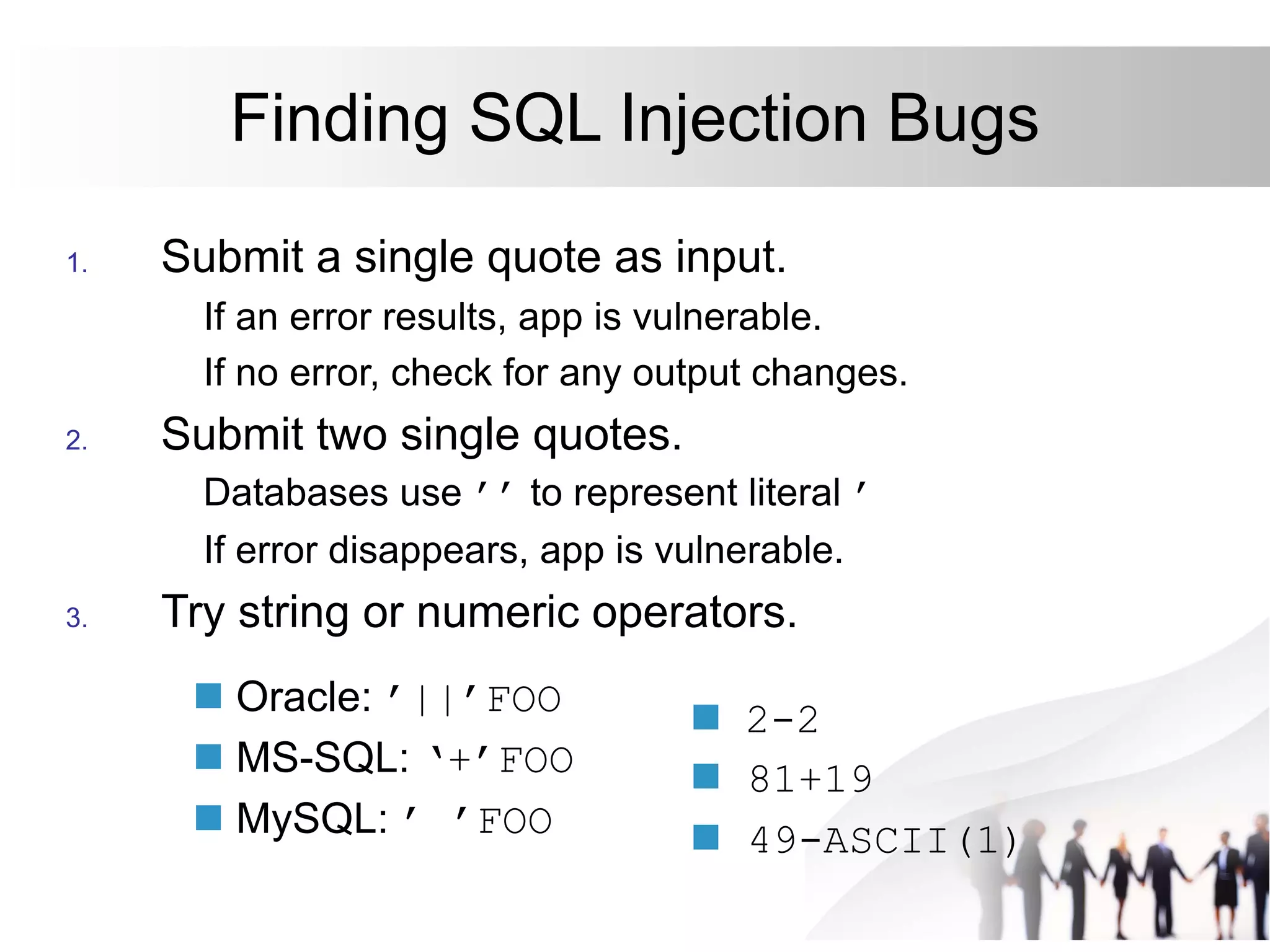
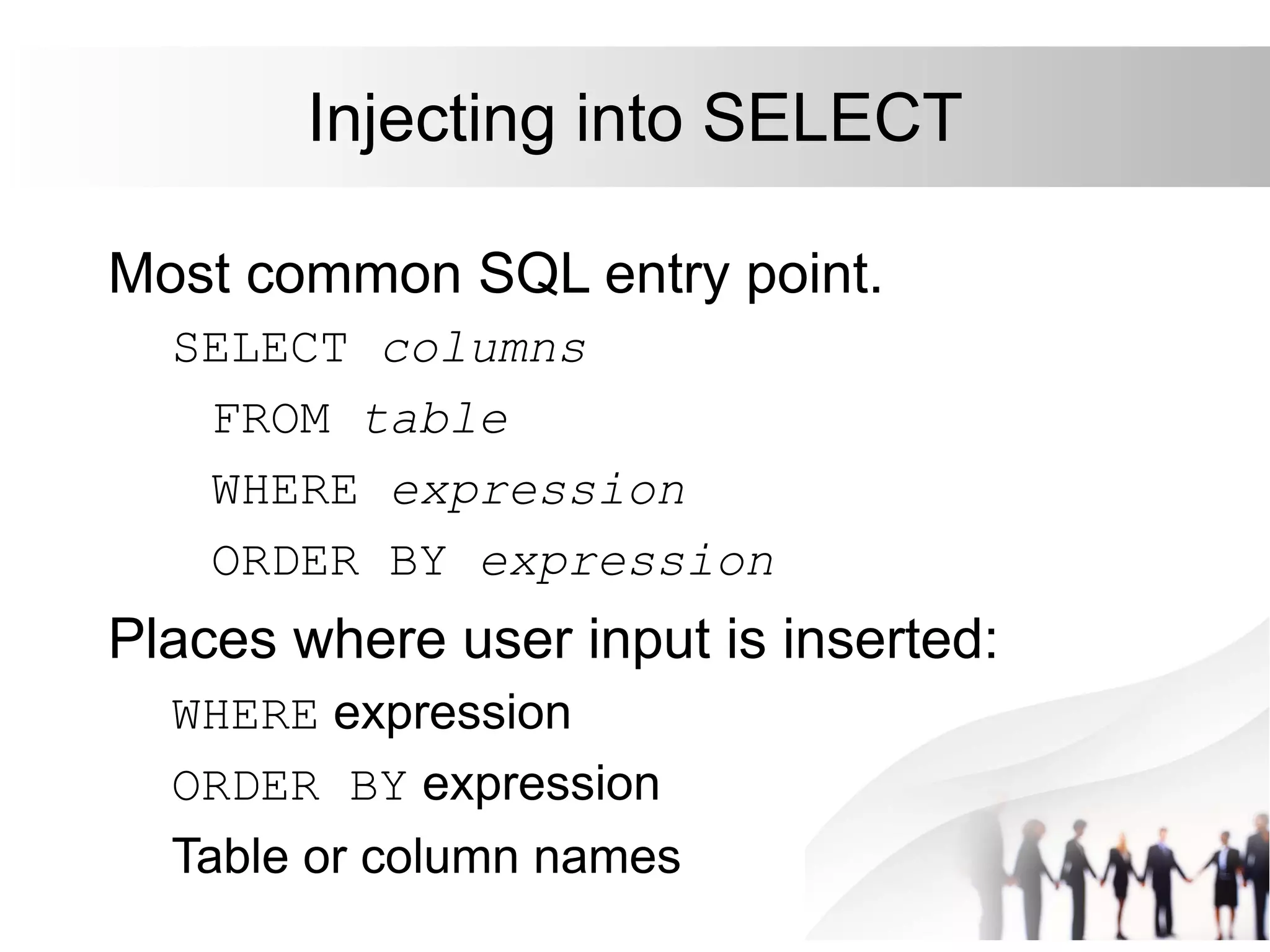
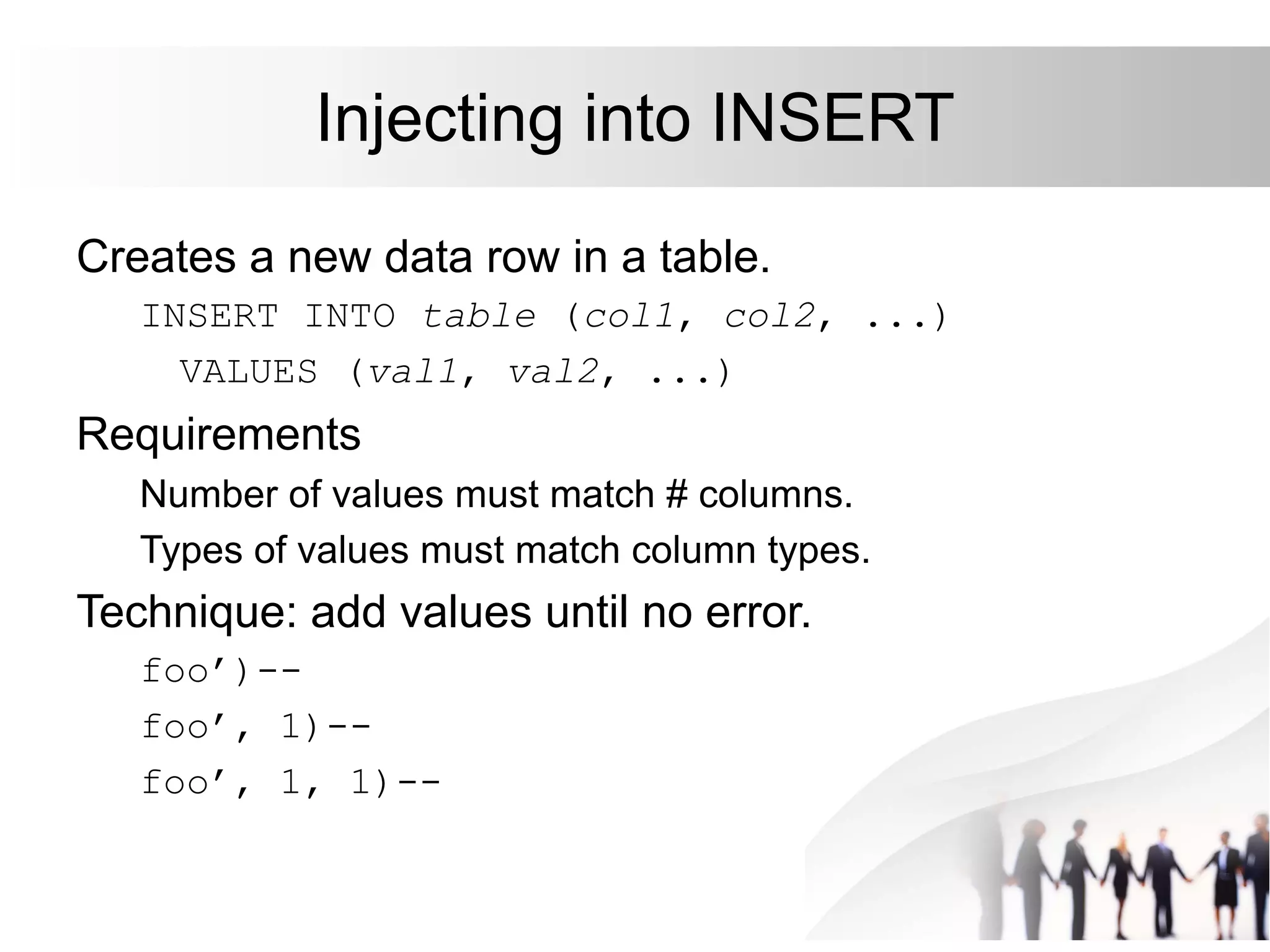
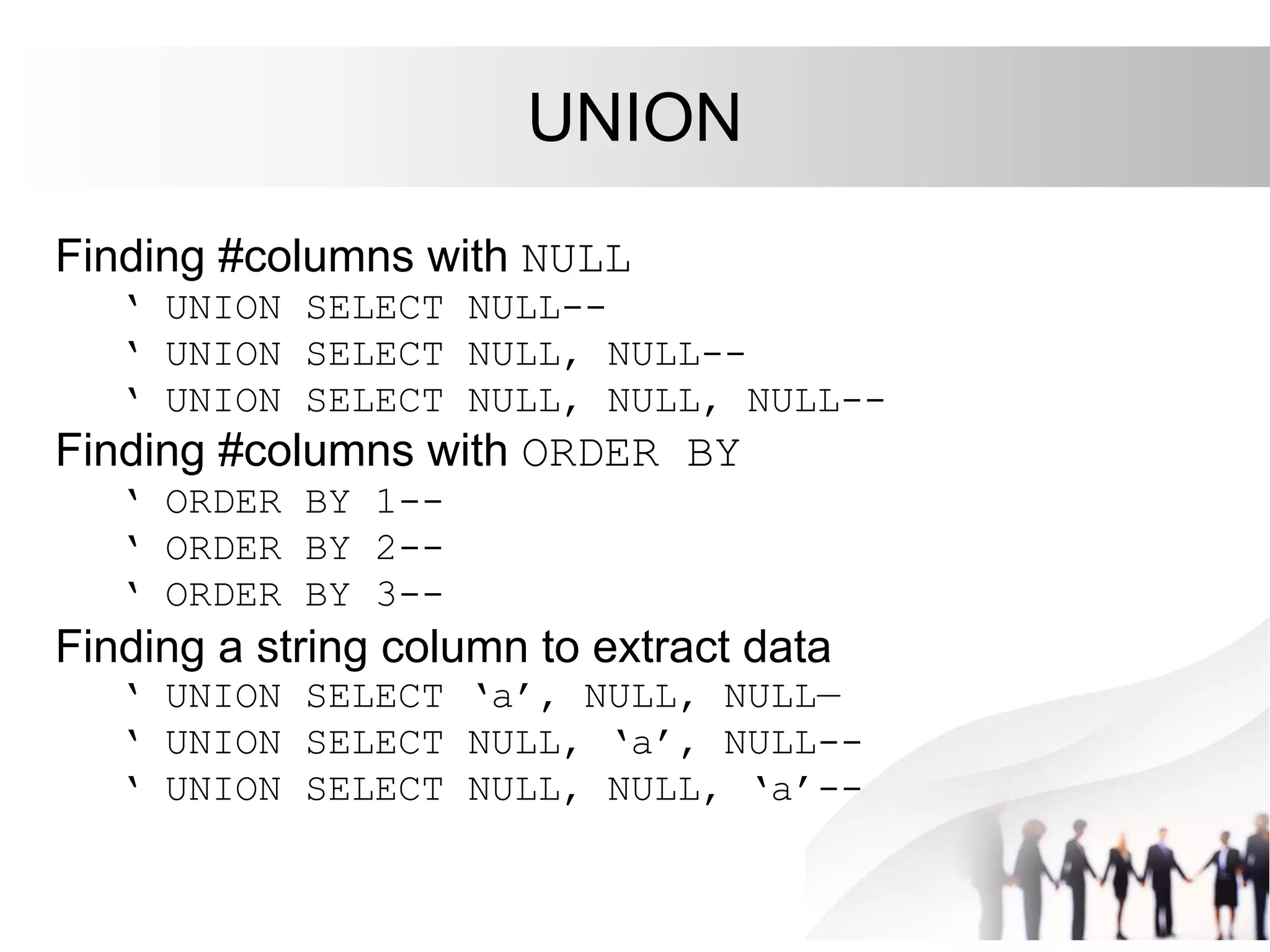
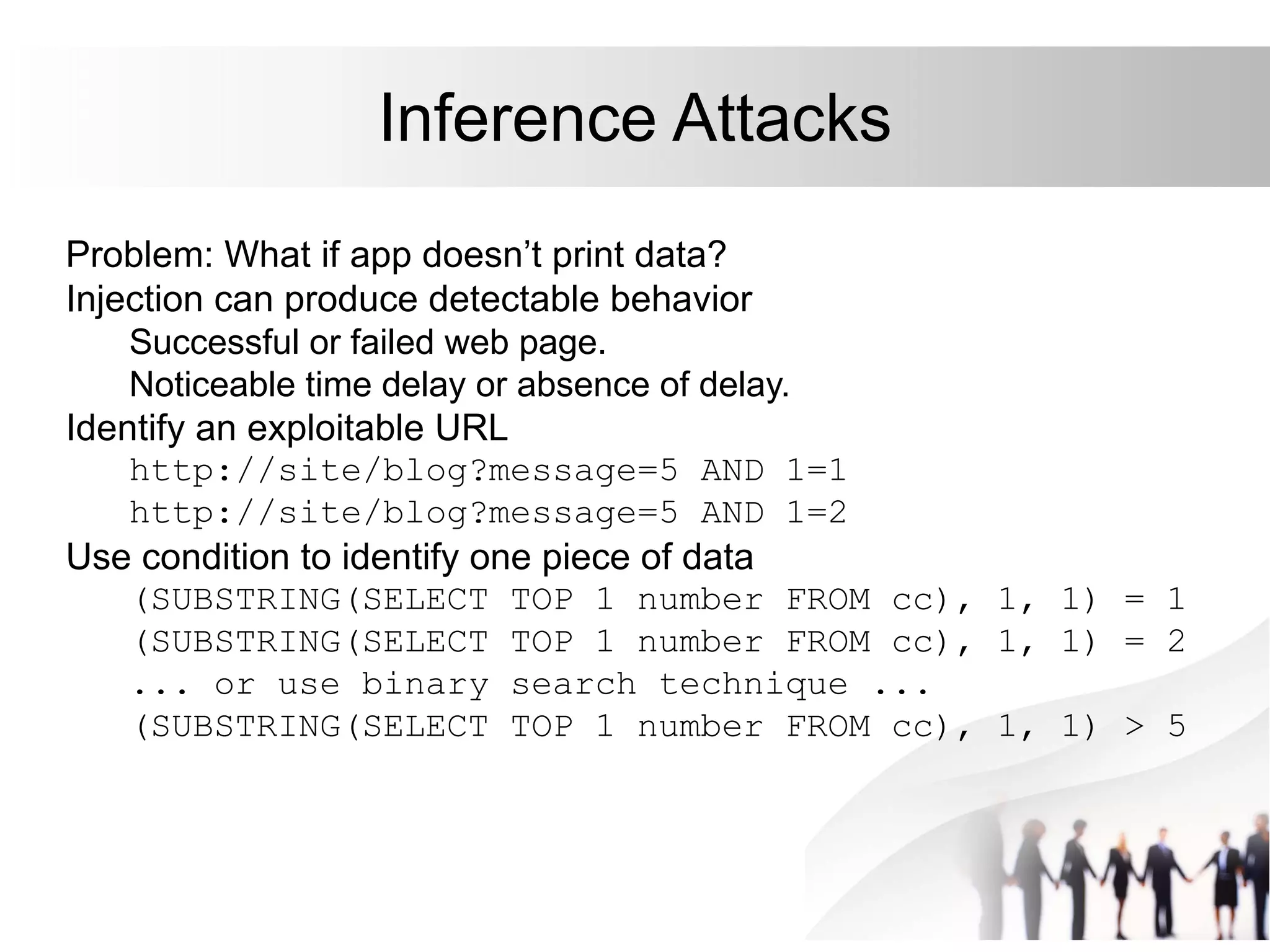
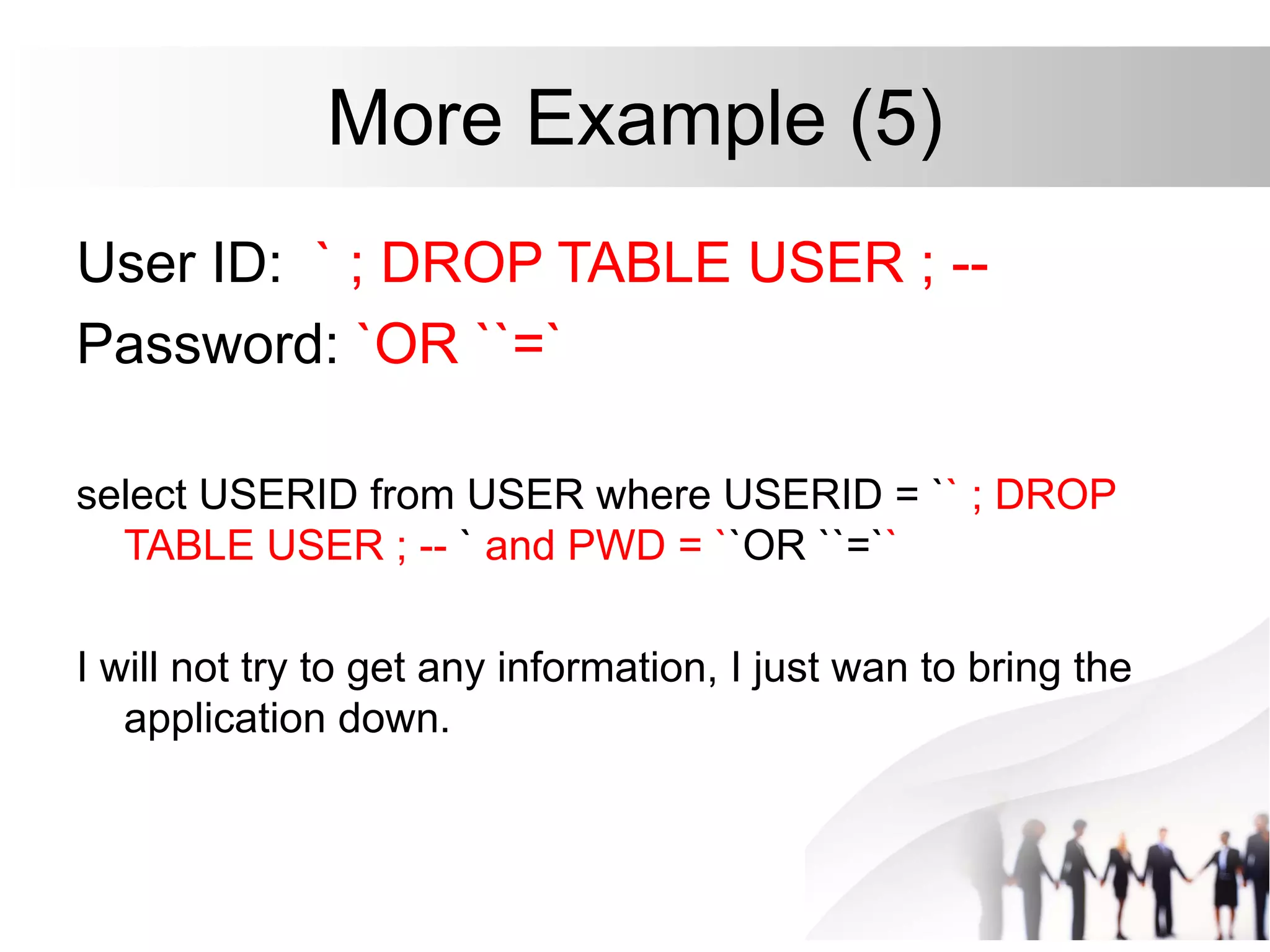
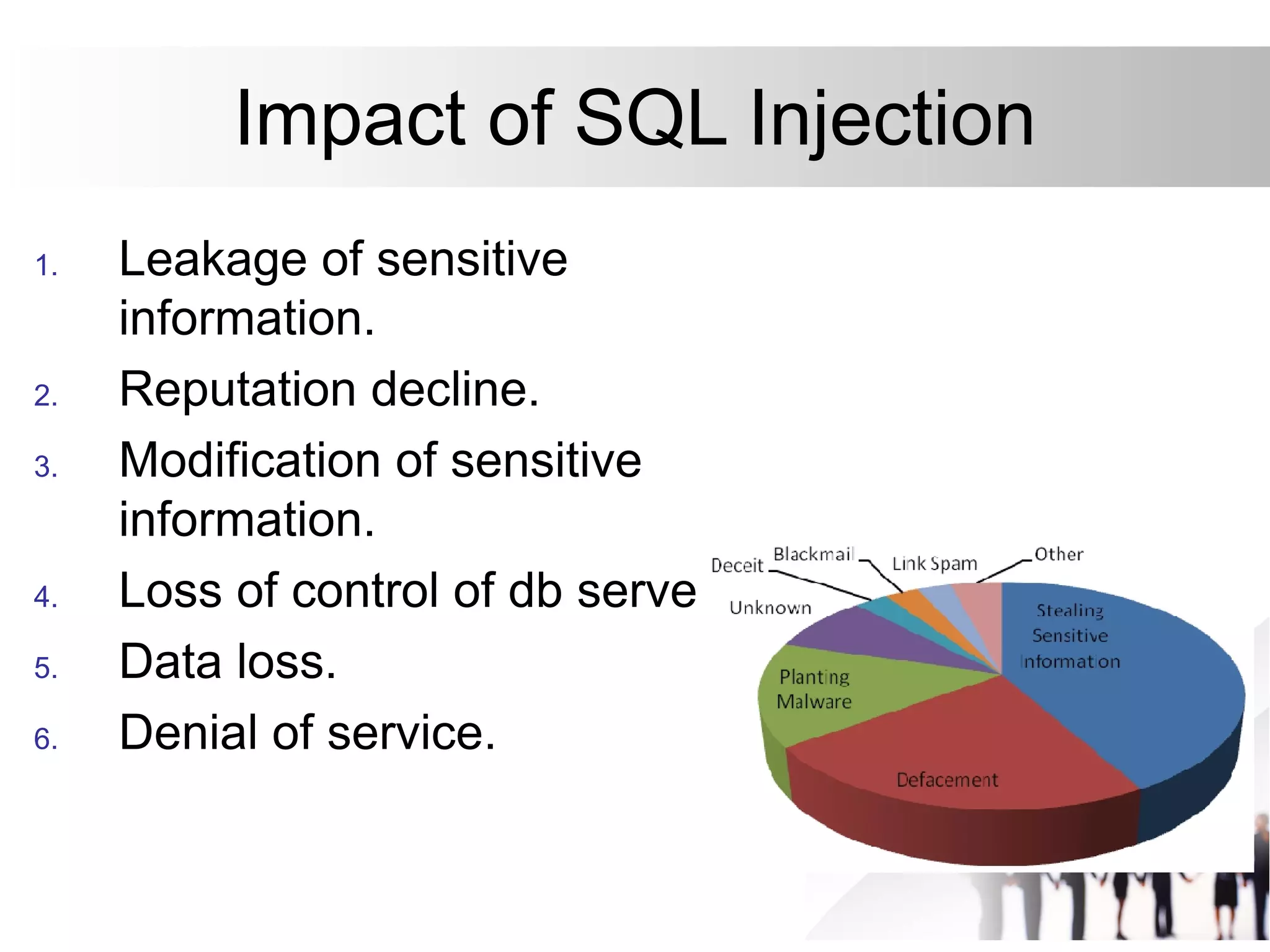
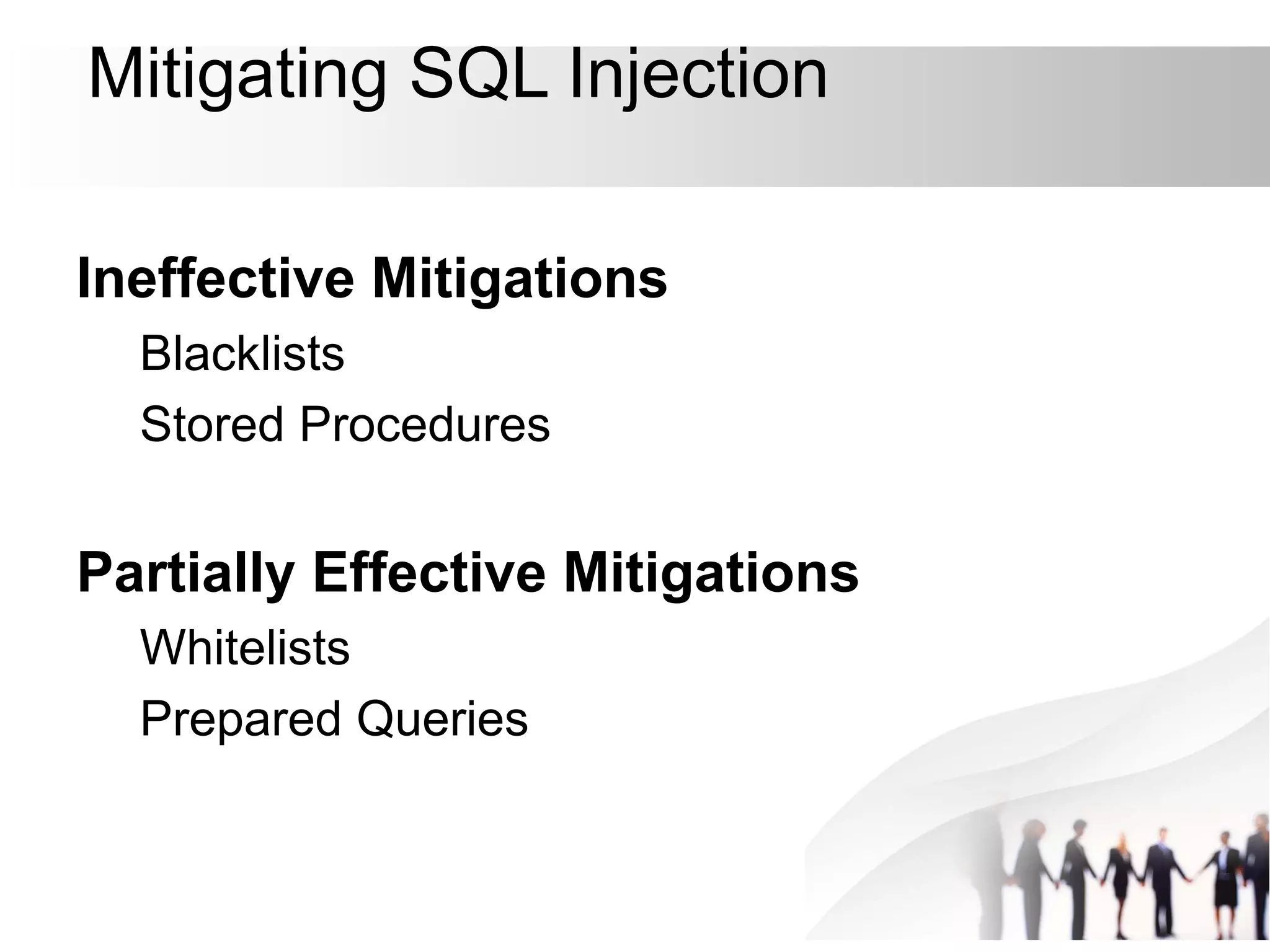
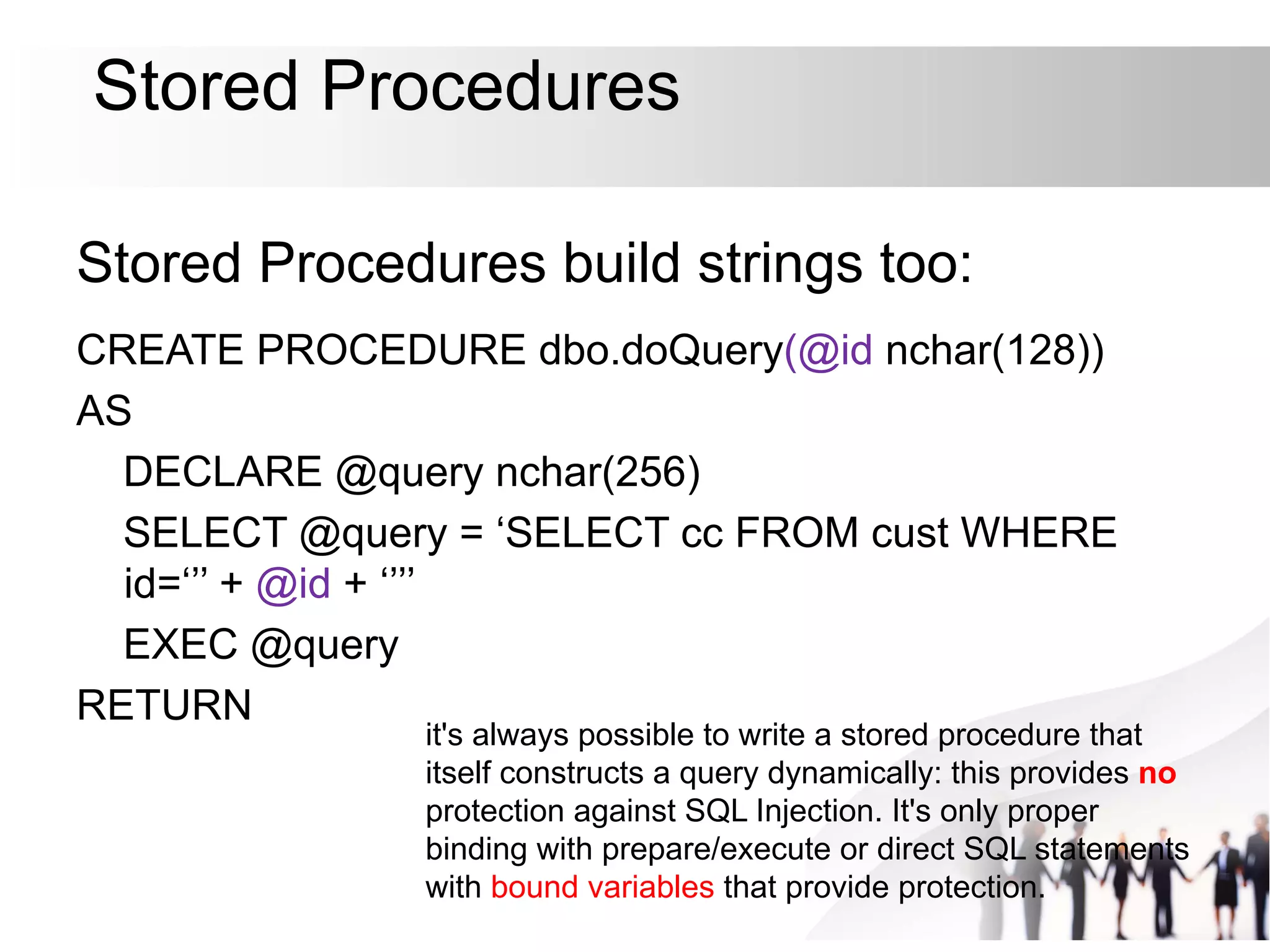
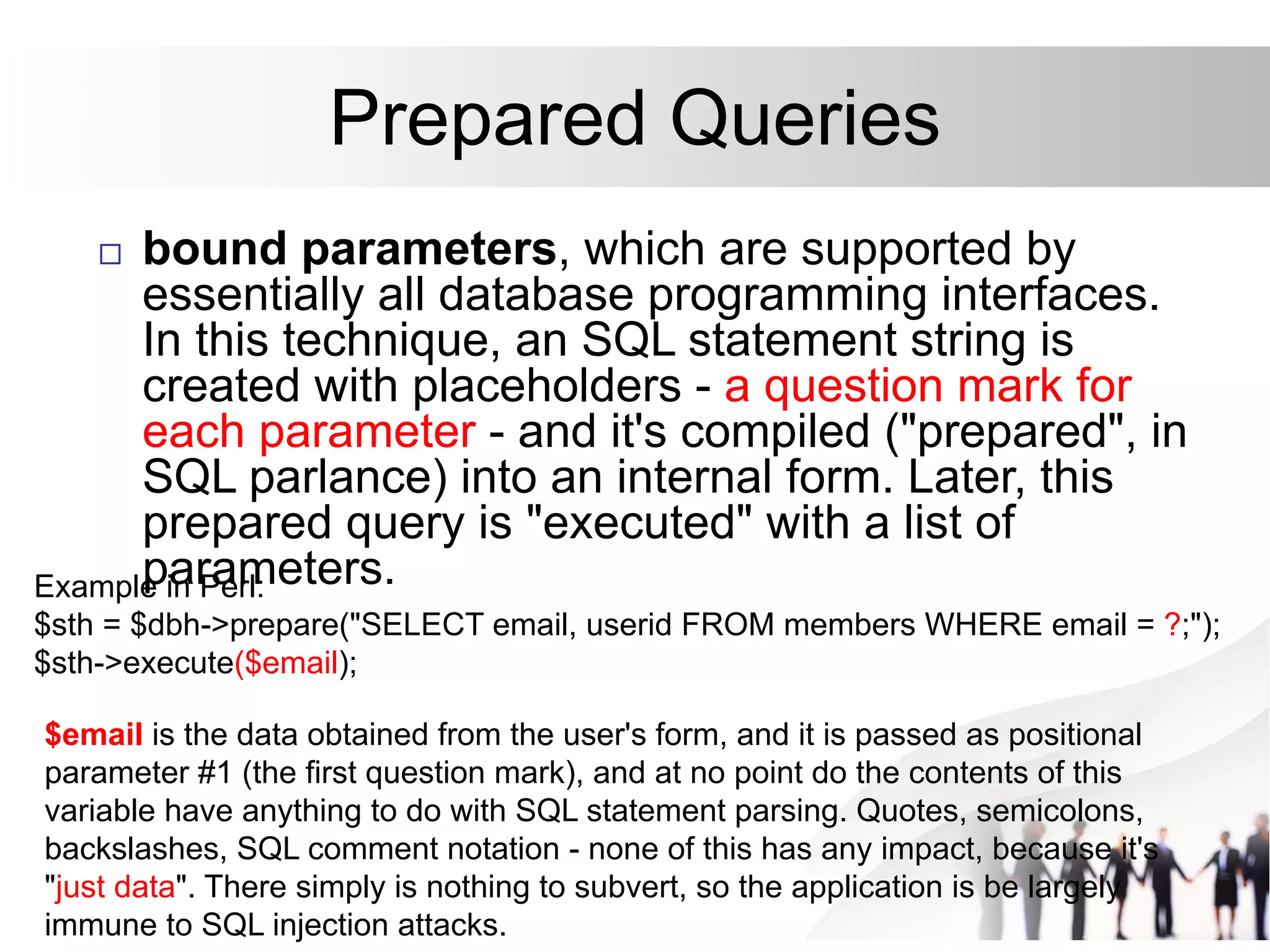
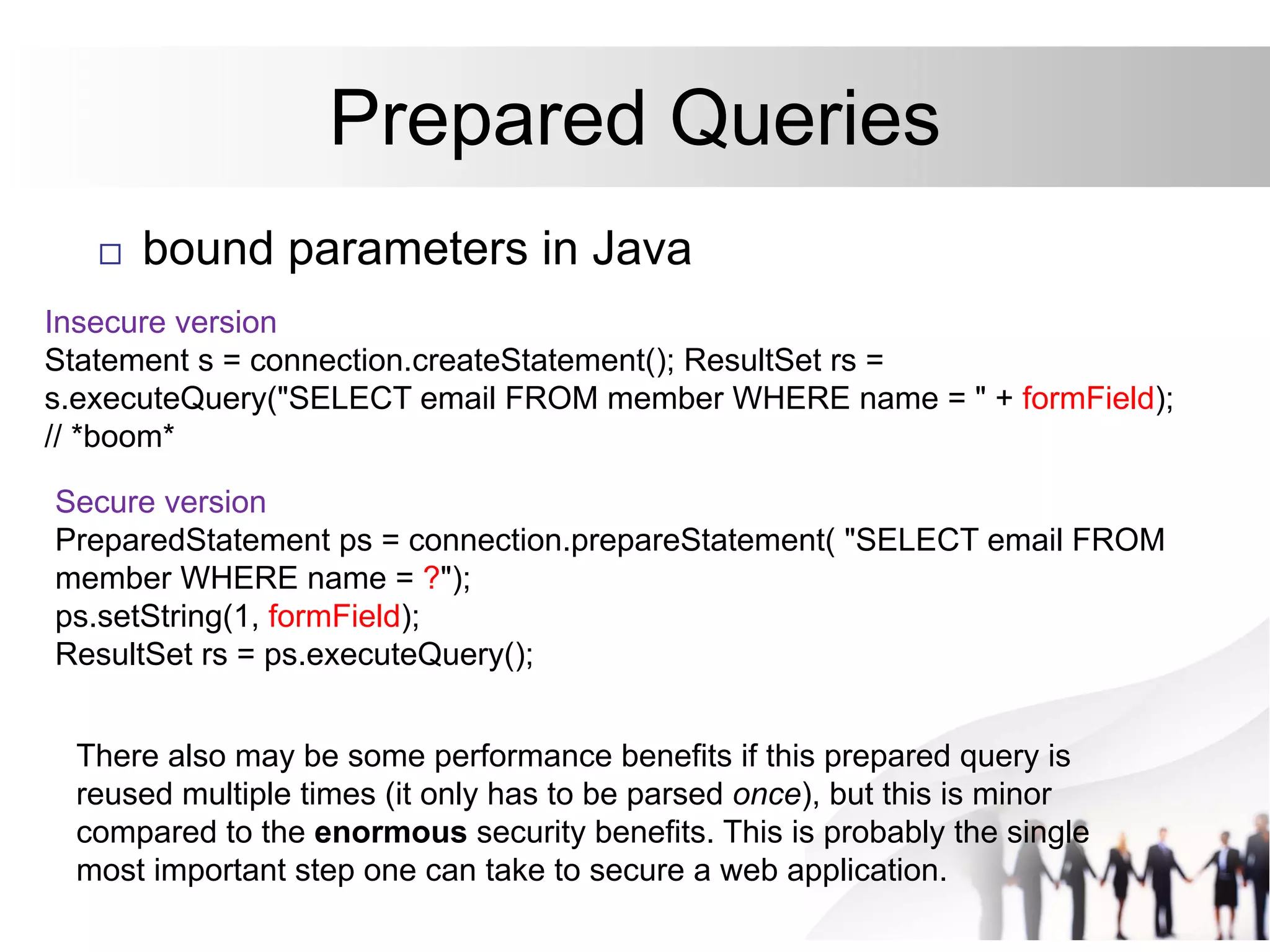
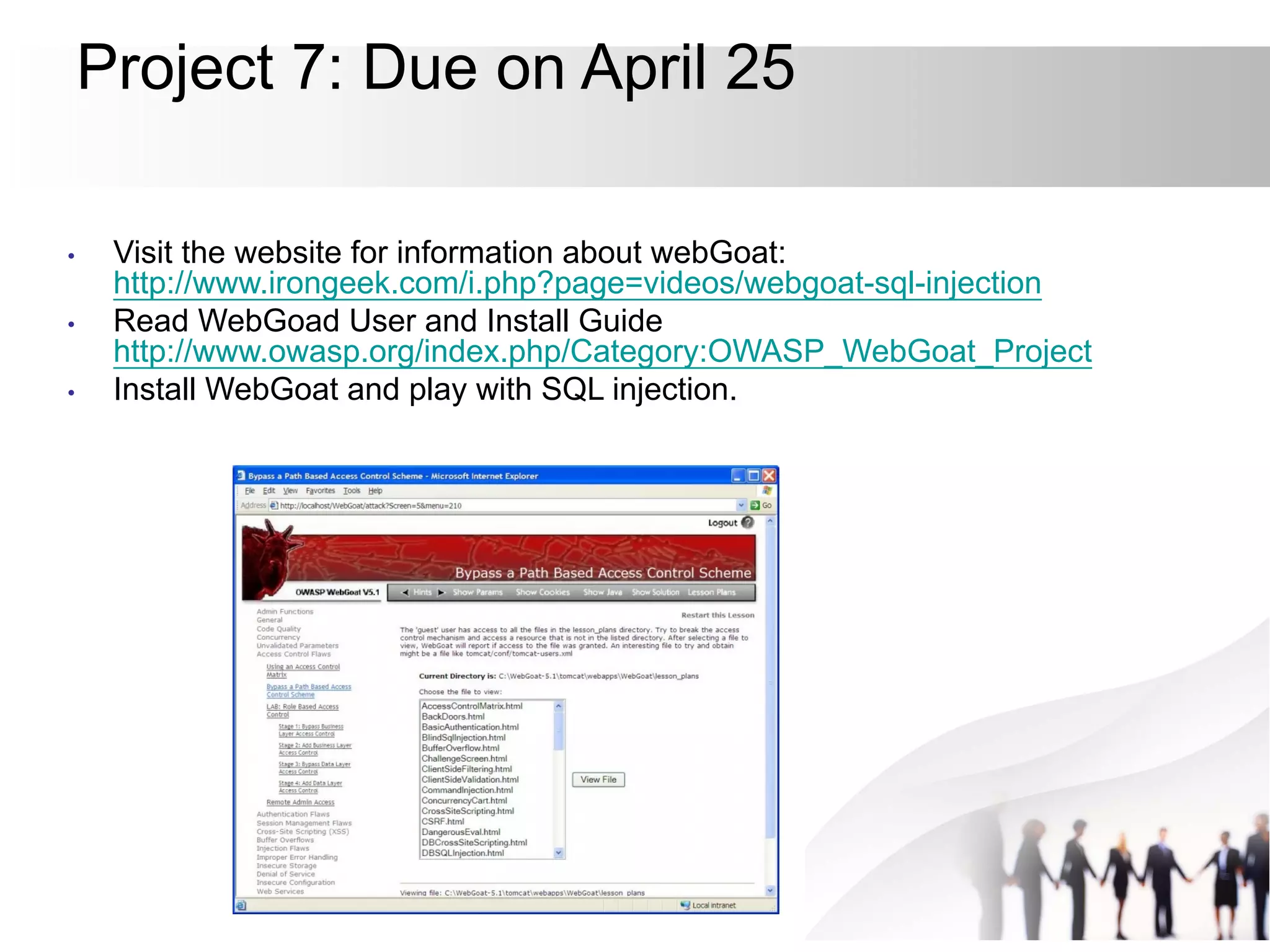
This document discusses SQL injection attacks and how to mitigate them. It begins by defining injection attacks as tricks that cause an application to unintentionally include commands in user-submitted data. It then explains how SQL injection works by having the attacker submit malicious SQL code in a web form. The document outlines several examples of SQL injection attacks, such as unauthorized access, database modification, and denial of service. It discusses techniques for finding and exploiting SQL injection vulnerabilities. Finally, it recommends effective mitigation strategies like prepared statements and input whitelisting to protect against SQL injection attacks.