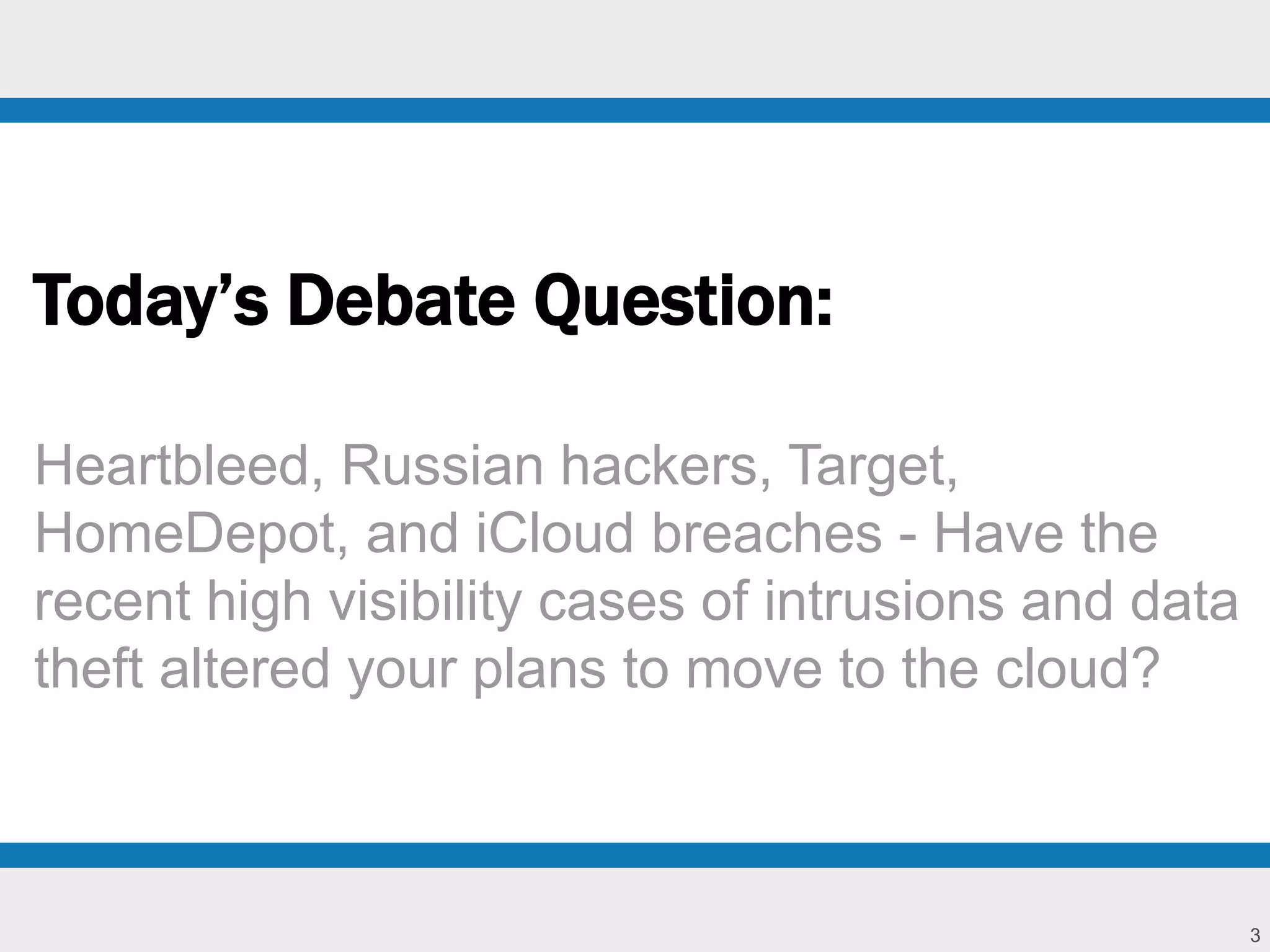
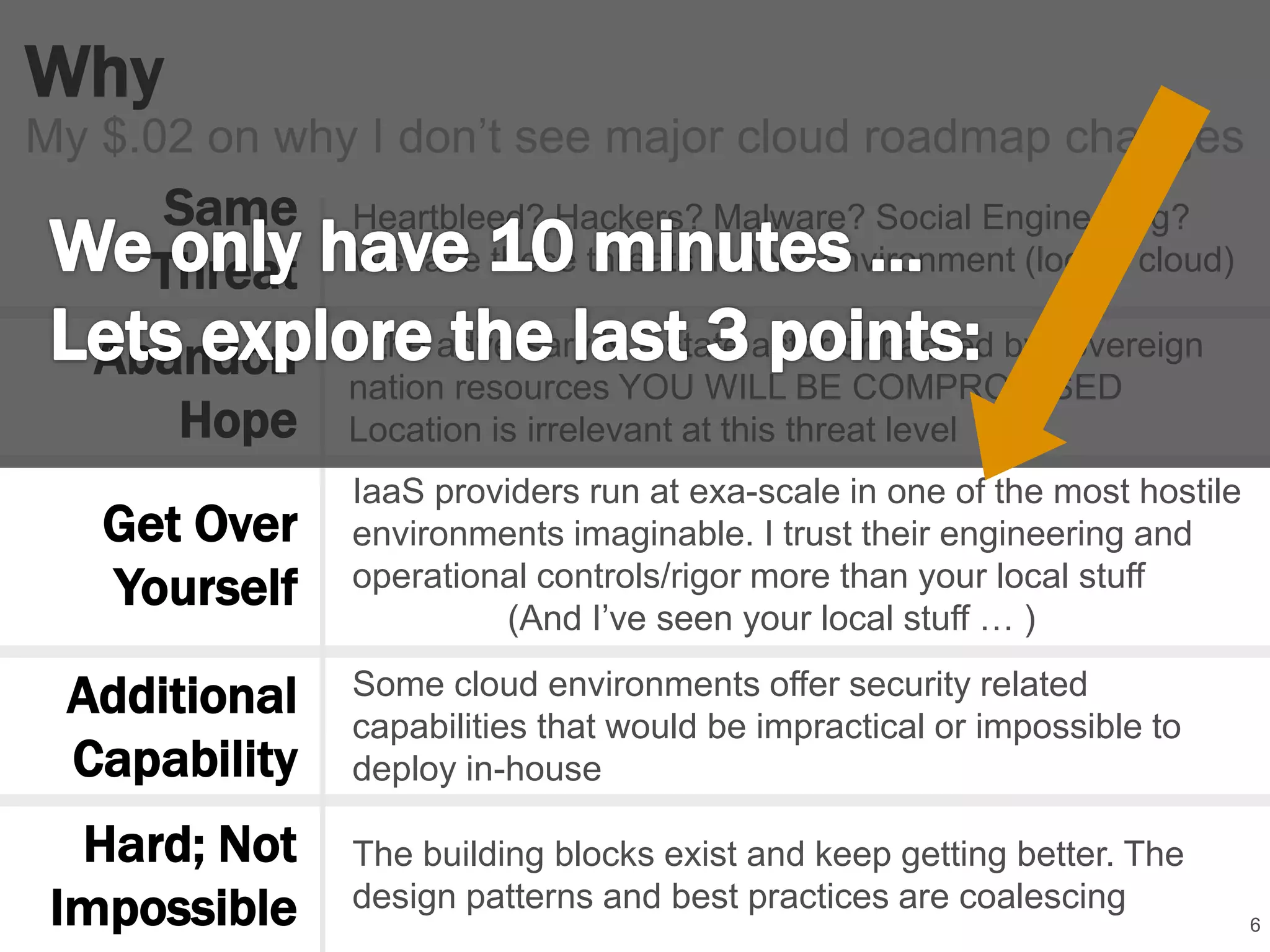
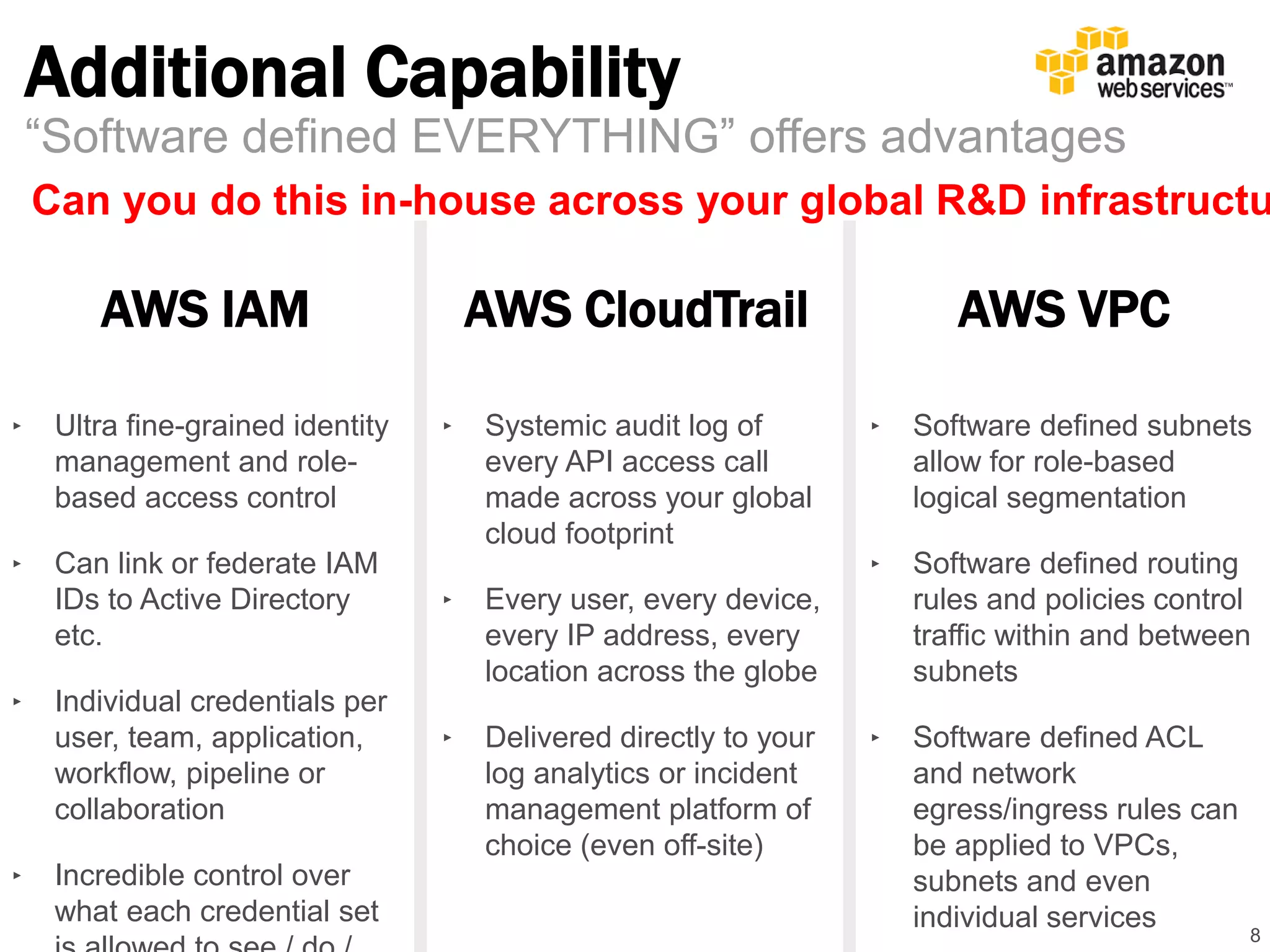
The document discusses the ongoing relevance of cloud computing despite high-profile data breaches, arguing that the risks are consistent across environments. It suggests that IaaS providers possess superior security engineering and operational controls, making them more trustworthy than local infrastructures. The text emphasizes the importance of proper monitoring and configuration in successfully utilizing cloud services while acknowledging the evolving role of IT in managing cloud architectures.