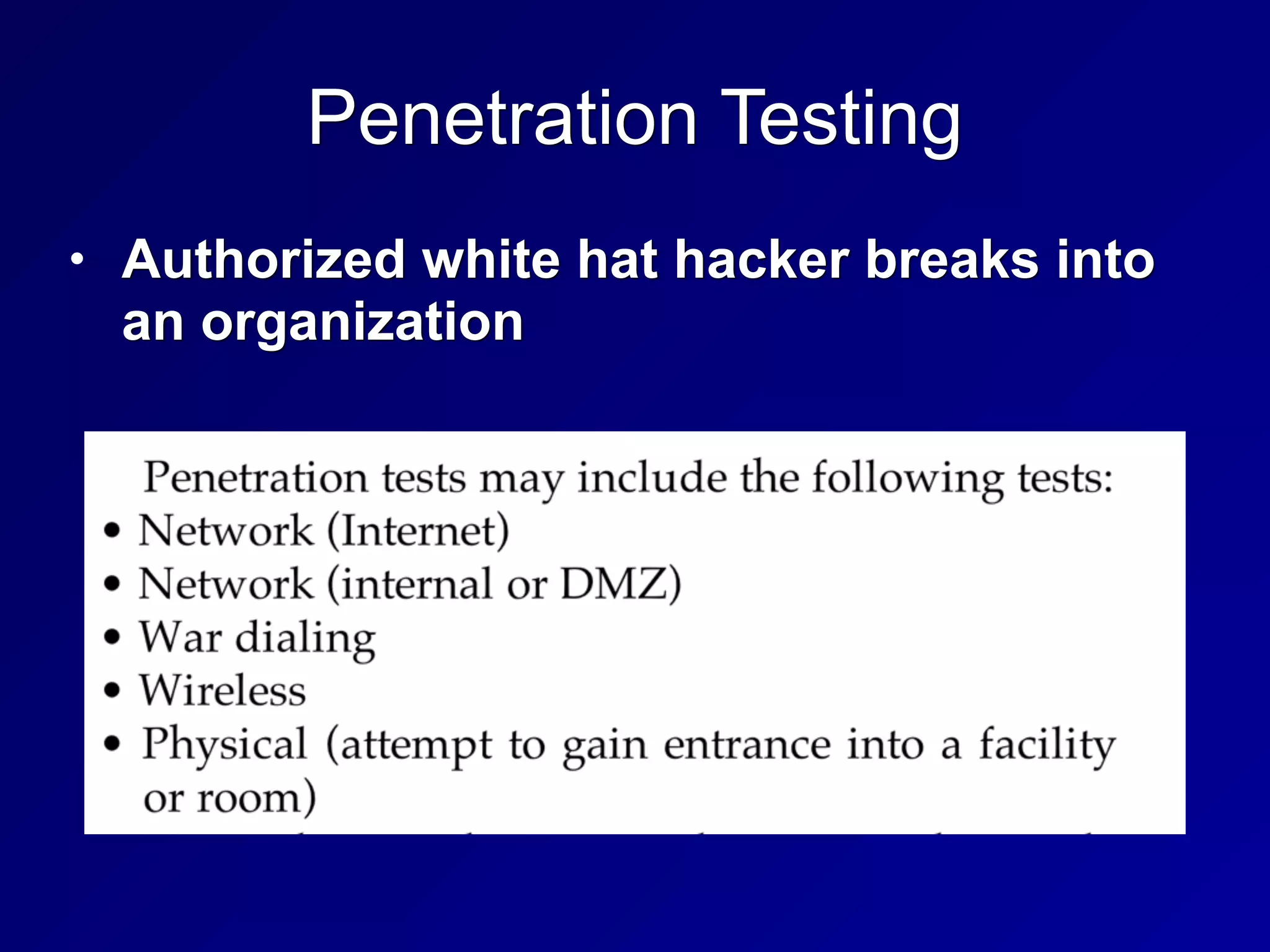
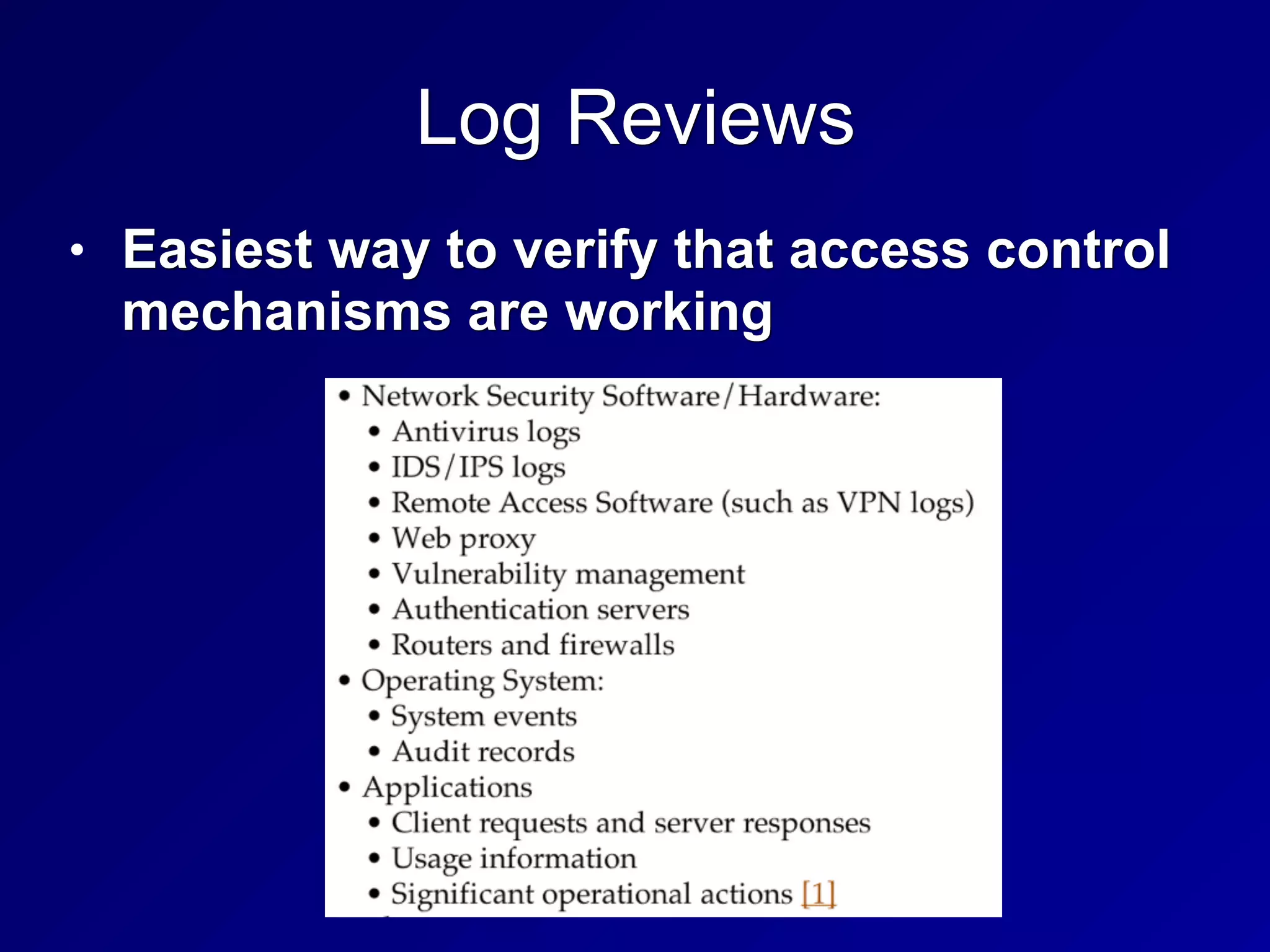
The document covers various concepts in information security, focusing on security assessments and testing methodologies, including penetration testing techniques, vulnerability scanning, and security audits. It details methods for software testing such as static and dynamic analysis, regression testing, and fuzzing, as well as the importance of compliance with standards like PCI-DSS. The emphasis is on ensuring data confidentiality and integrity while addressing potential security threats through structured testing and audits.