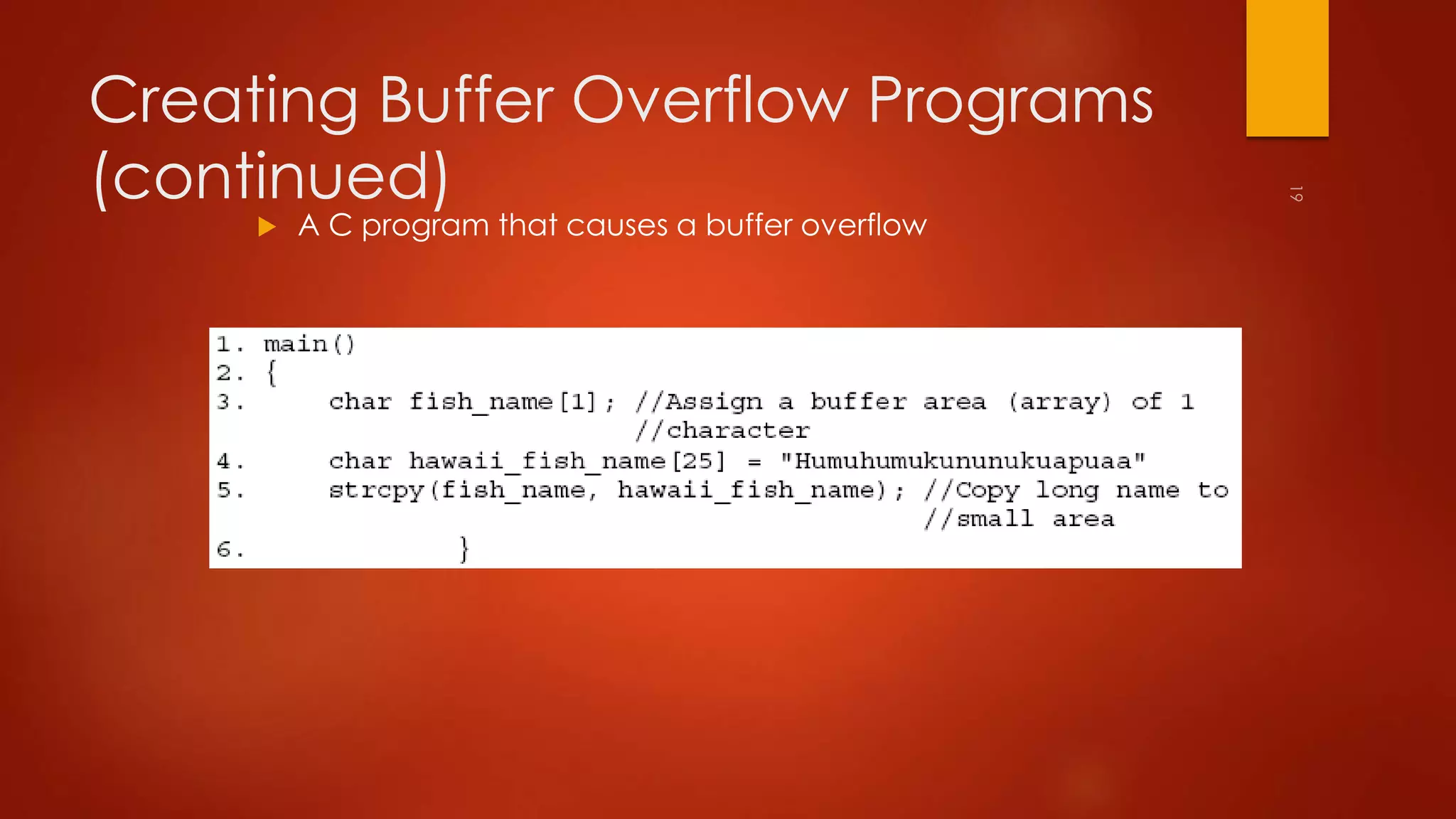
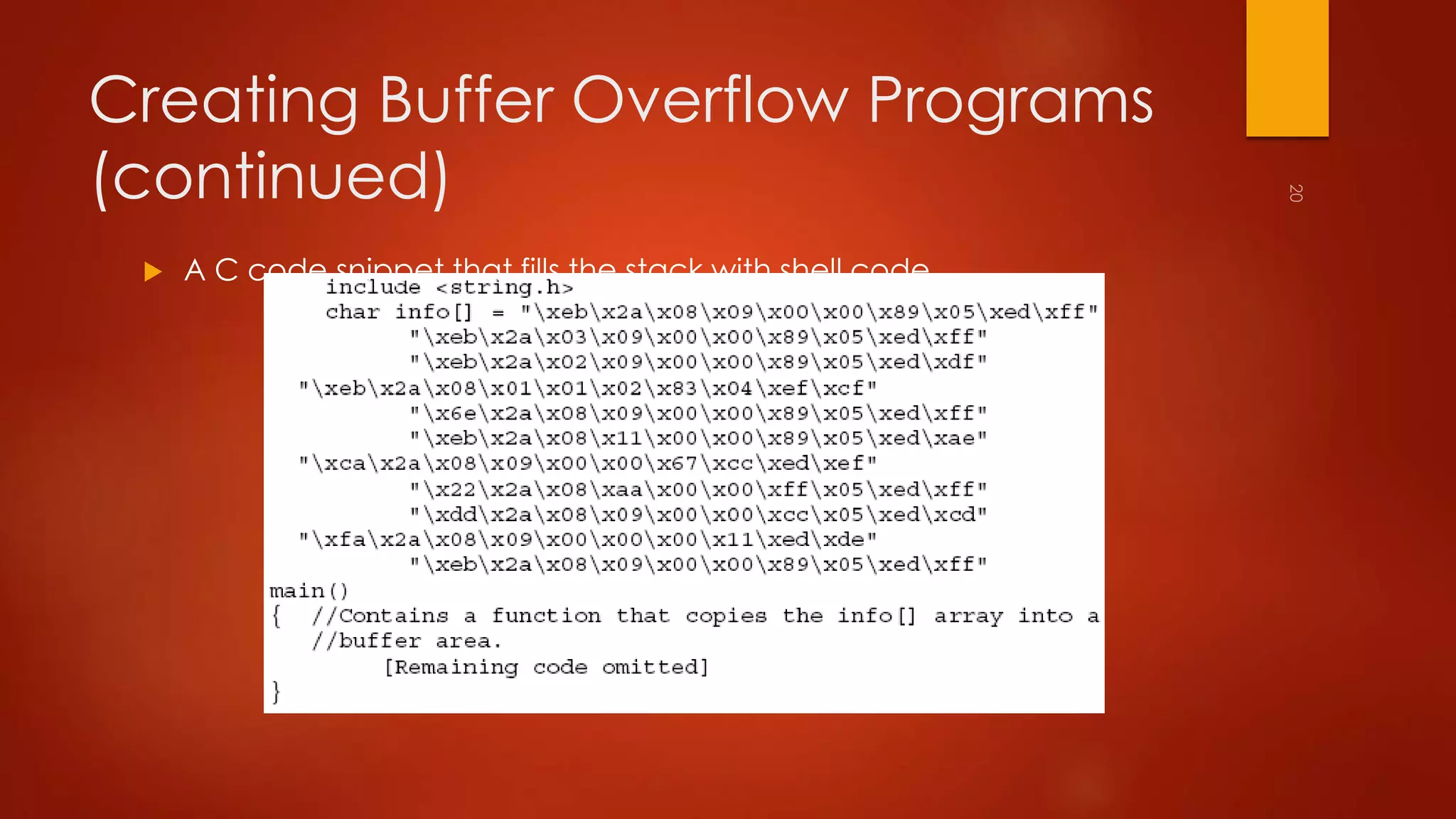
This document discusses Linux vulnerabilities and remote attacks. It describes the Linux file system and common vulnerabilities. Remote attack techniques covered include footprinting, social engineering, installing Trojan programs, buffer overflows, and using sniffers. Countermeasures include user awareness training, keeping systems updated with the latest patches, and writing secure code.