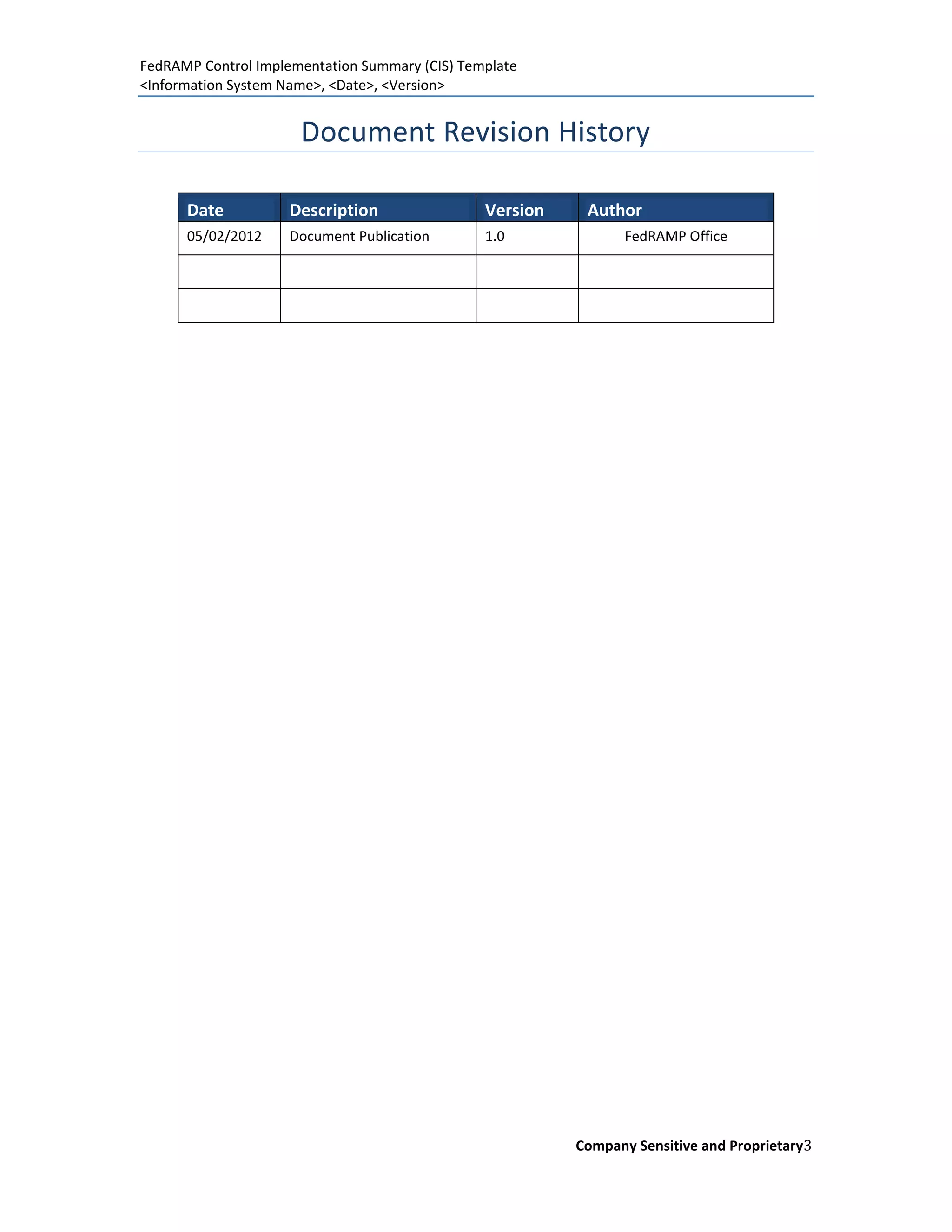
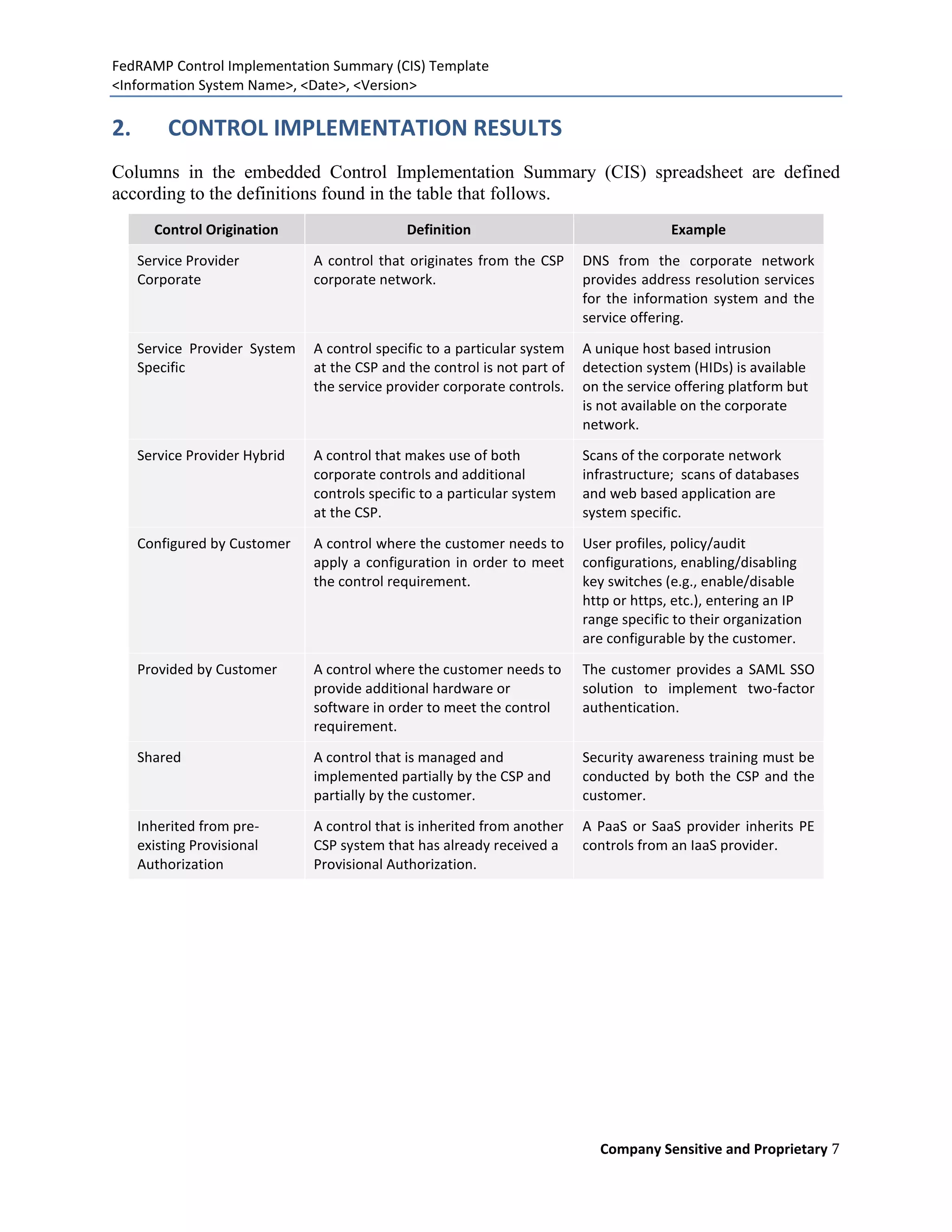
The document is a Control Implementation Summary (CIS) template designed for cloud service providers applying for authorization to operate through the FedRAMP program. It includes sections on document purpose, scope, control implementation results, and guidelines for filling out the template. The CIS captures the responsibilities and statuses of security controls of the information system in compliance with federal requirements.