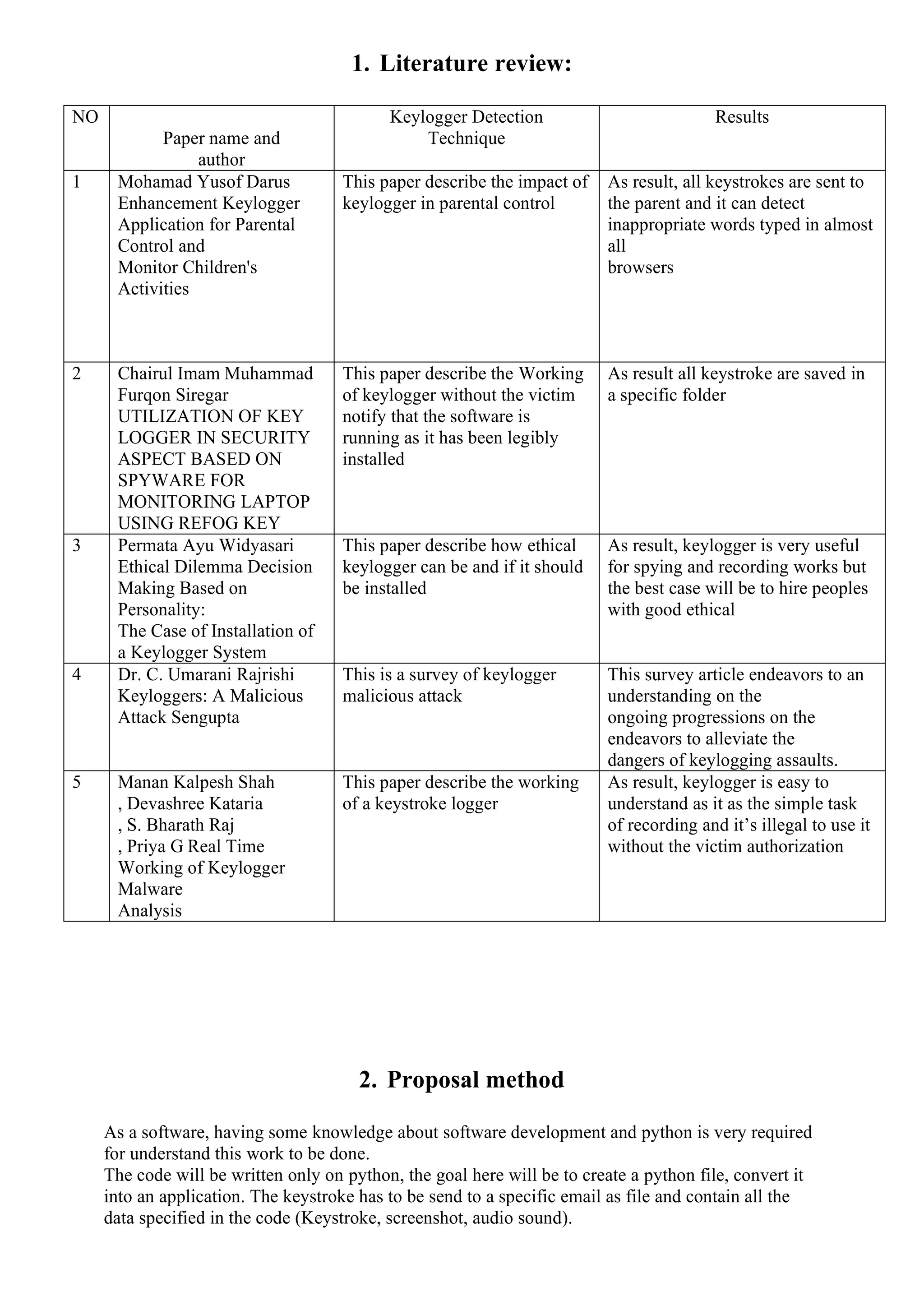
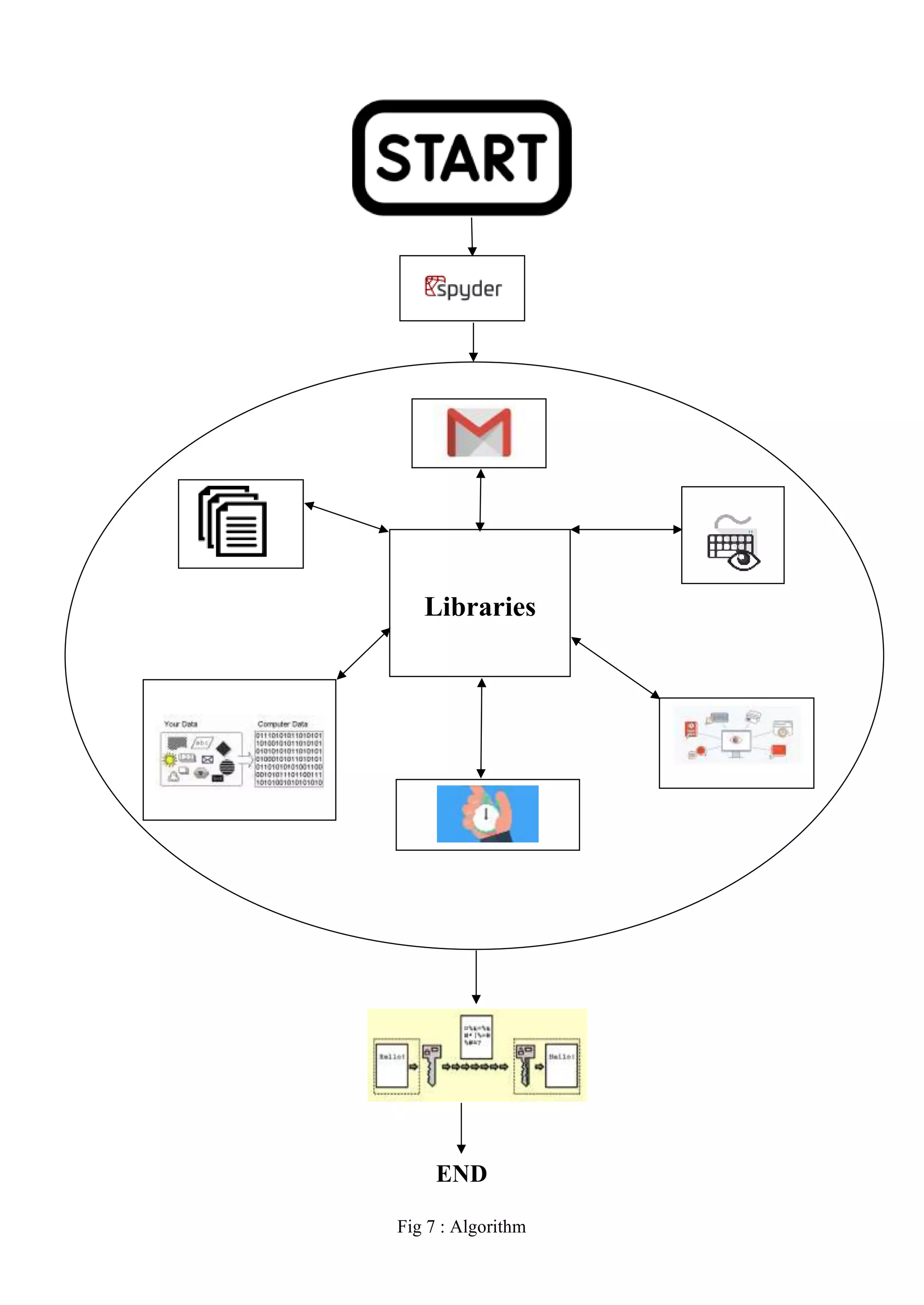
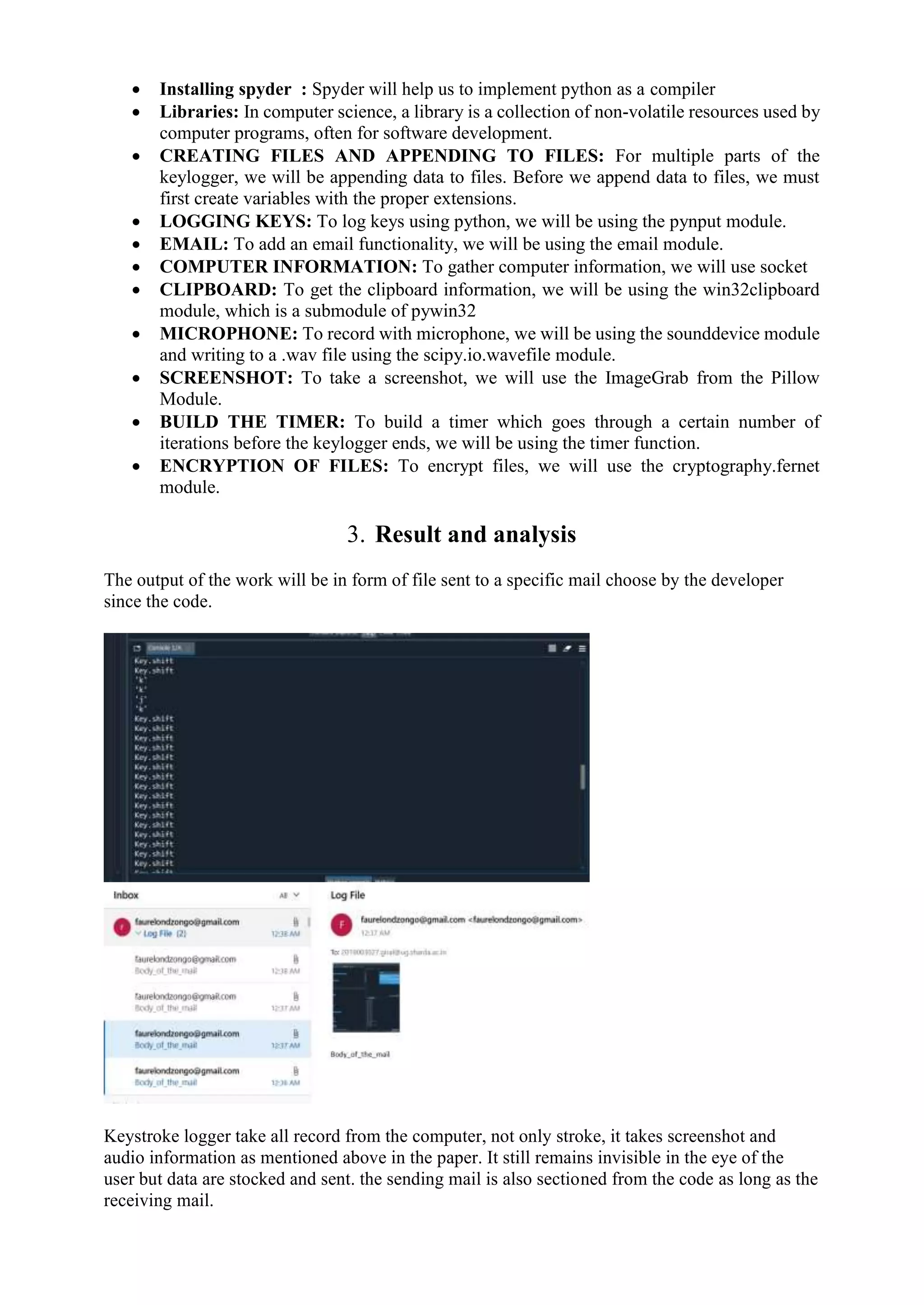
The document discusses the development of a software keylogger used in cybersecurity to monitor keystrokes on a victim's computer. It outlines the various types of hackers, the workings of keyloggers, and highlights their use in ethical hacking versus malicious attacks. The project aims to create a non-malicious keylogger that can help users track their own keystrokes for security purposes.