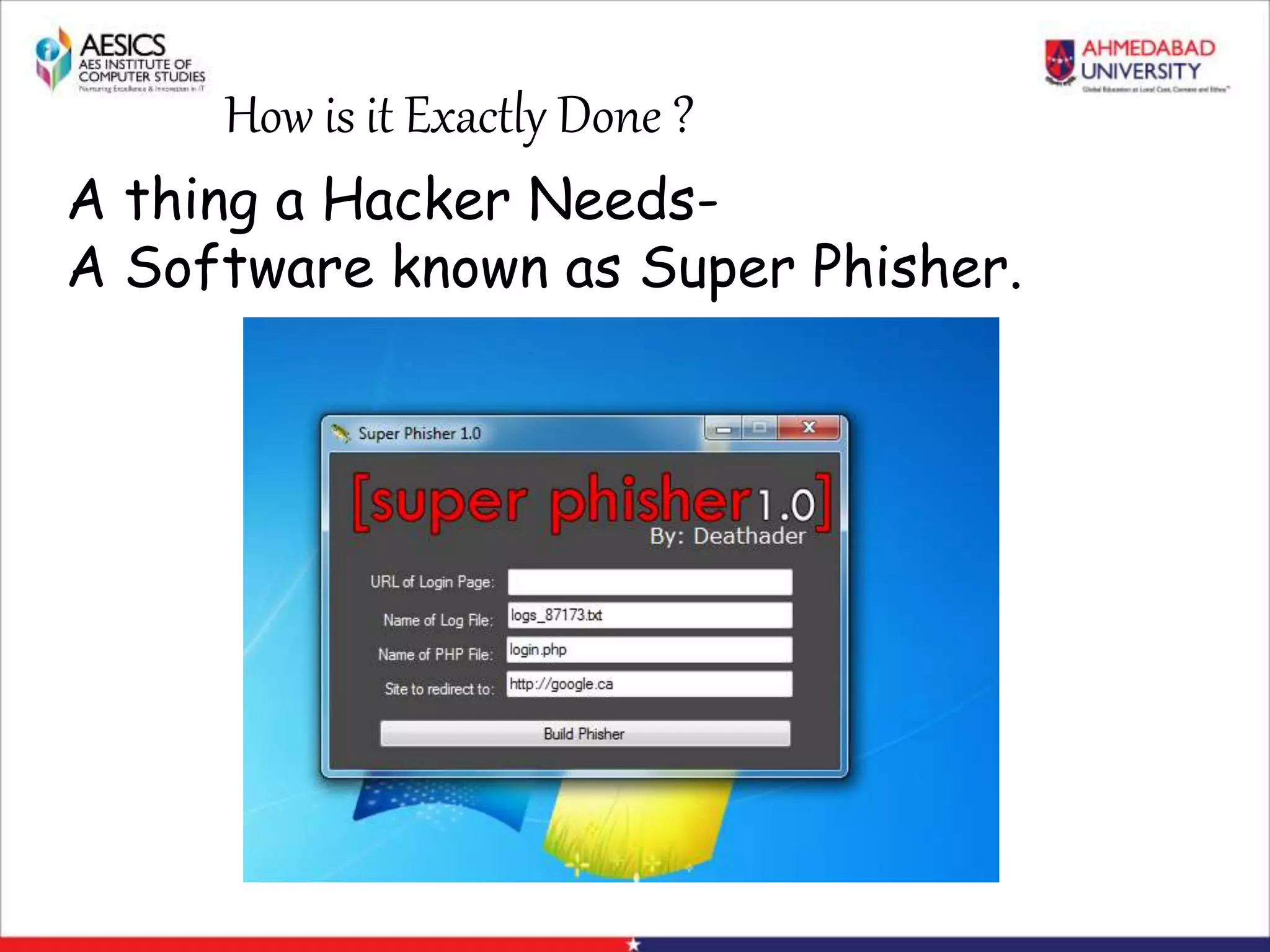
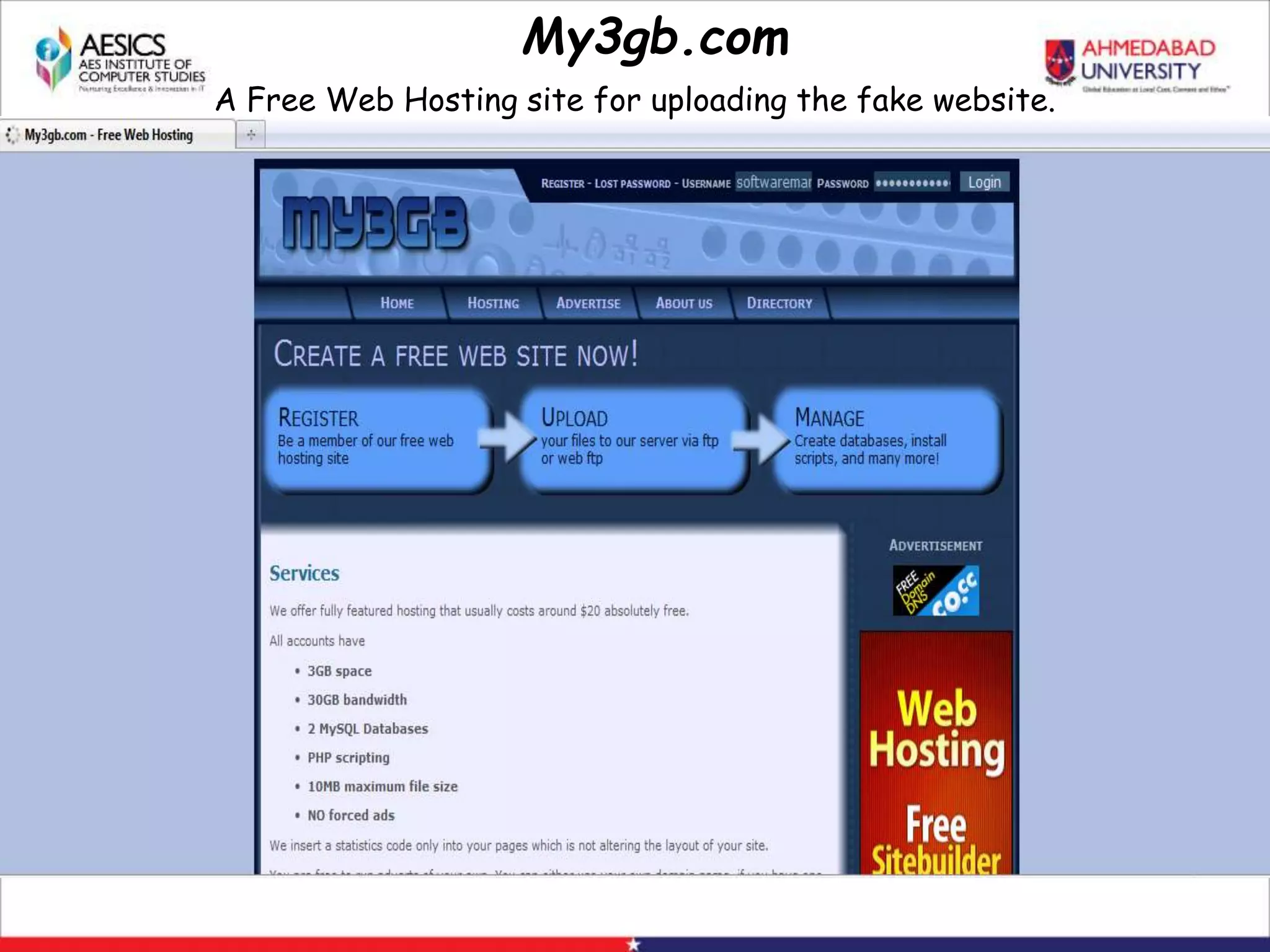
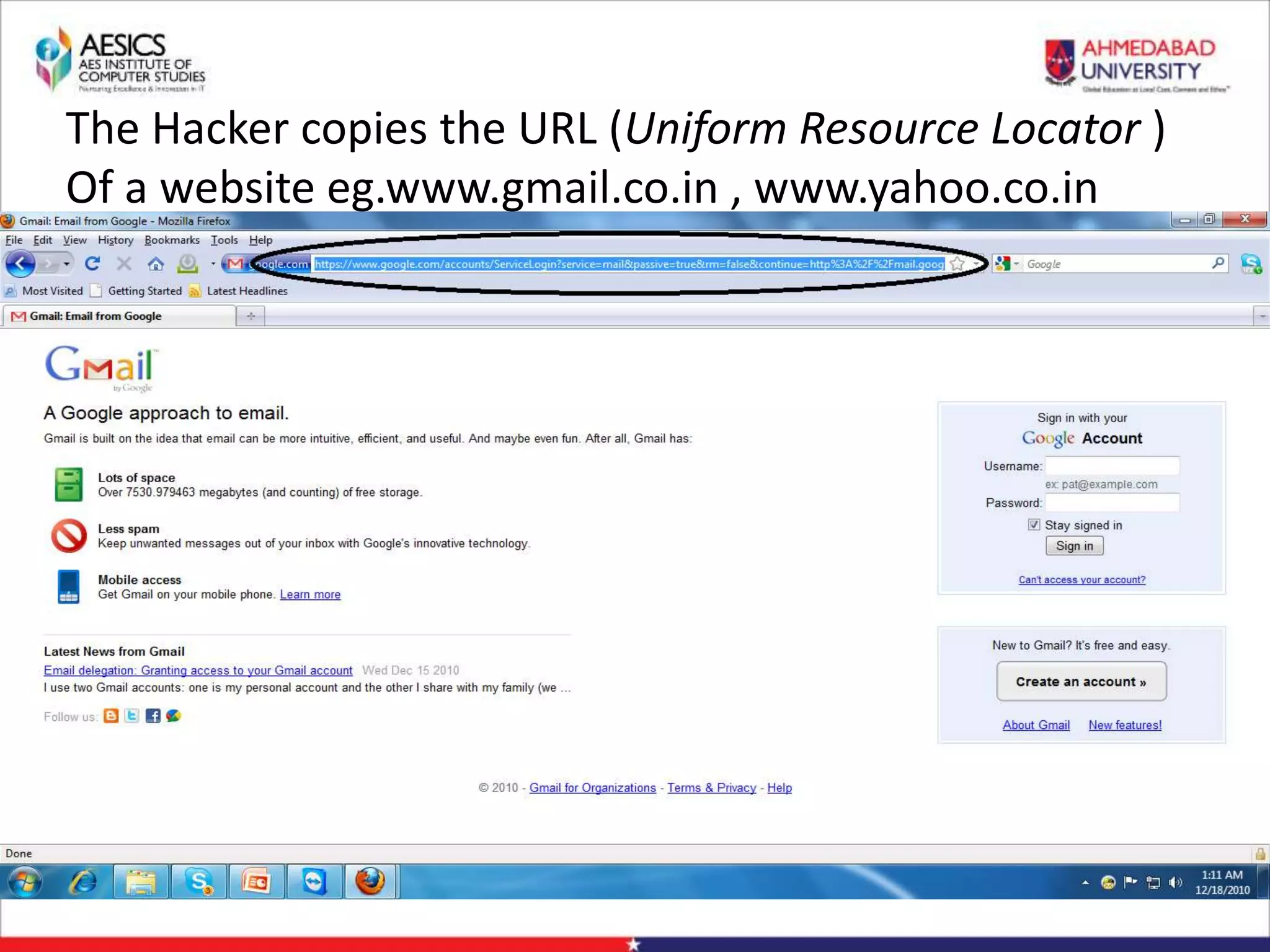
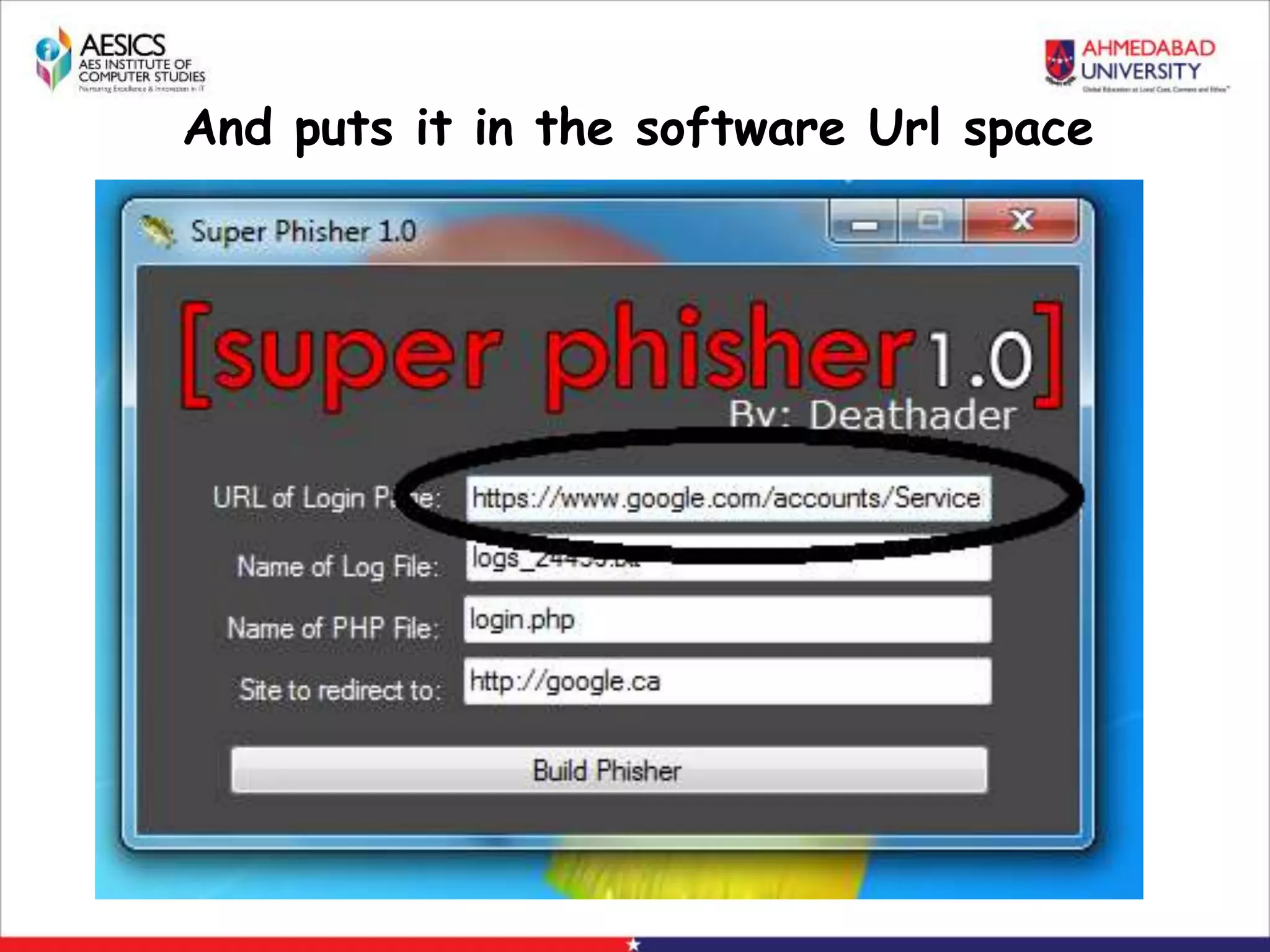
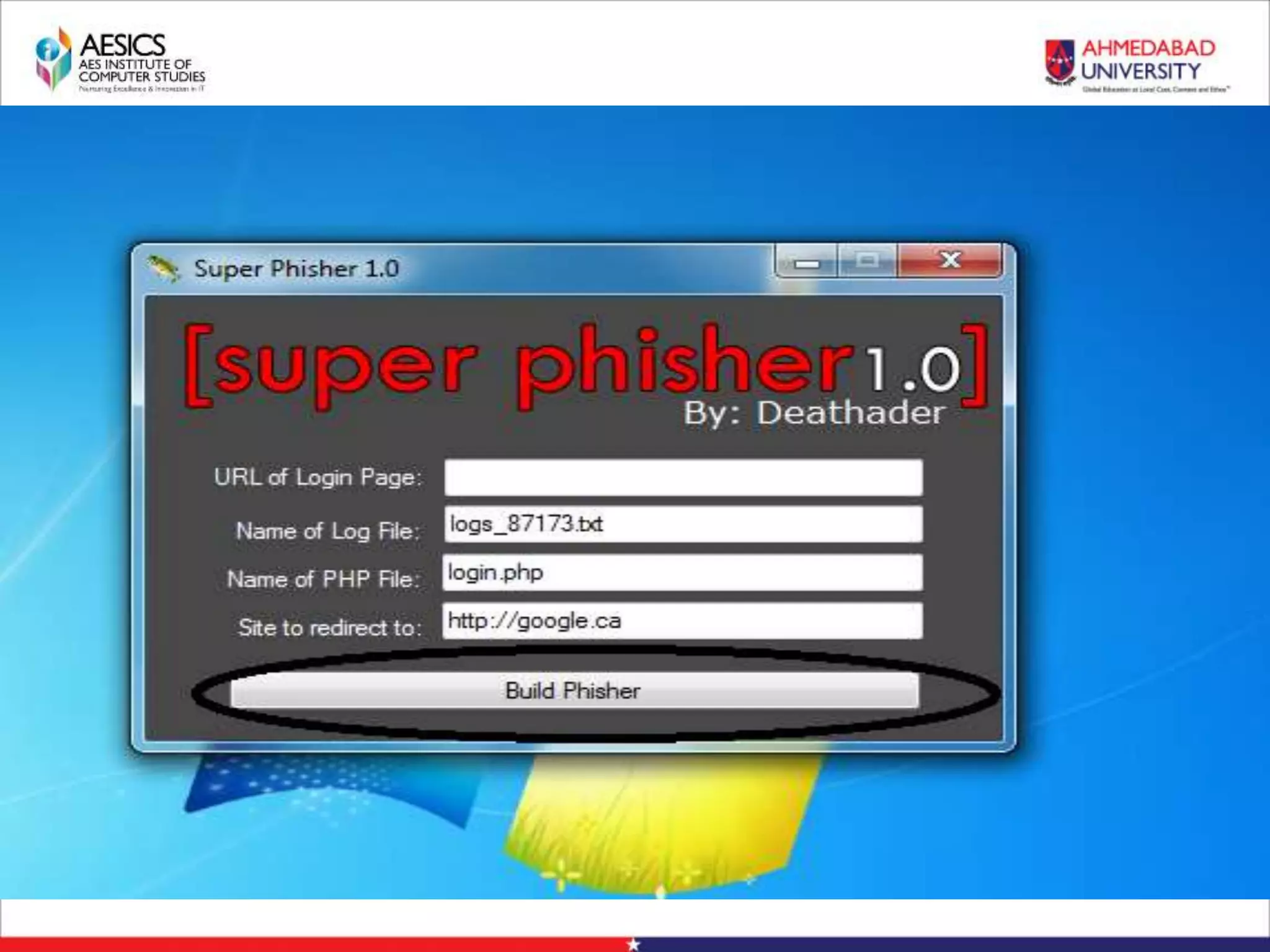
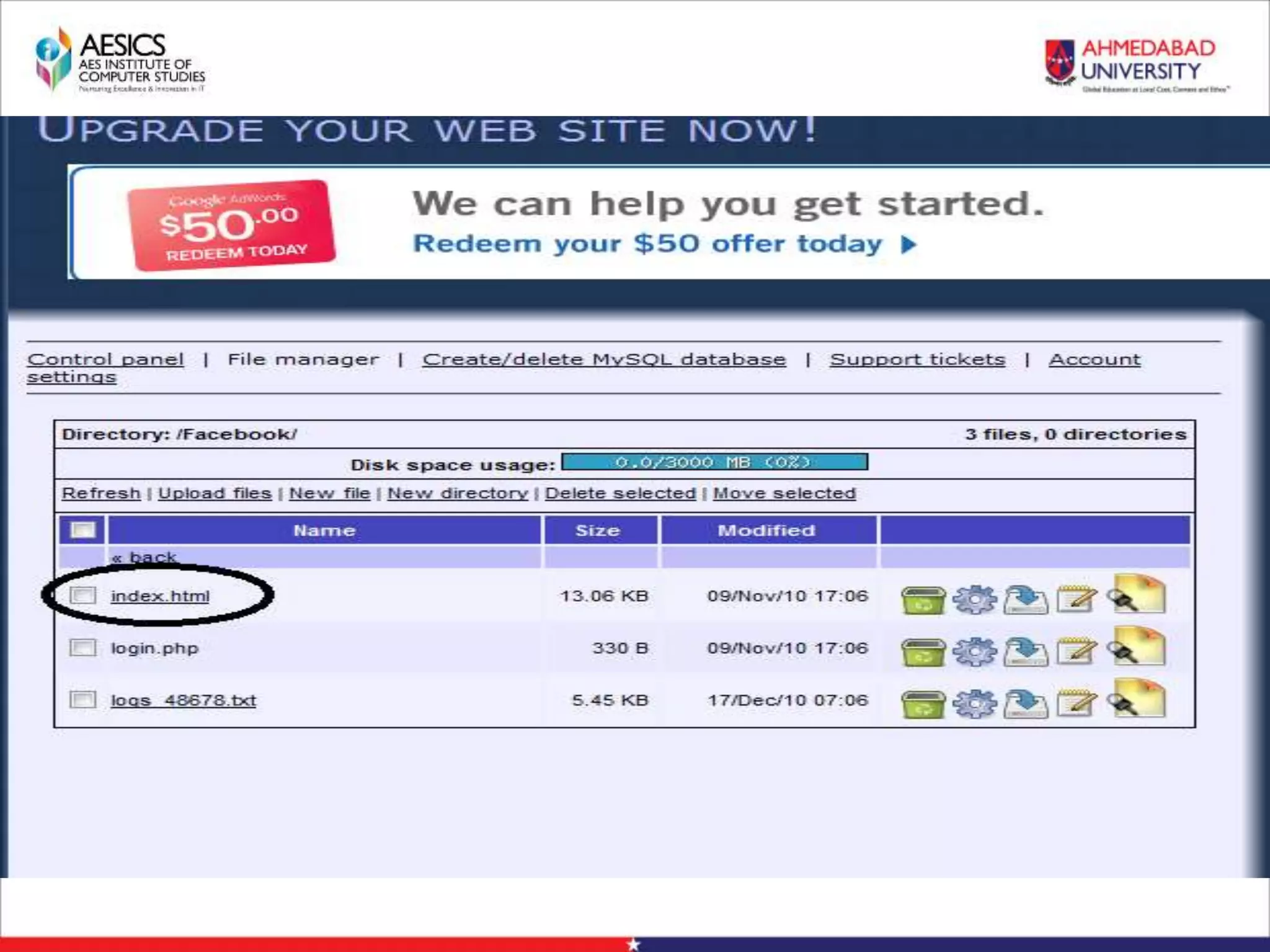
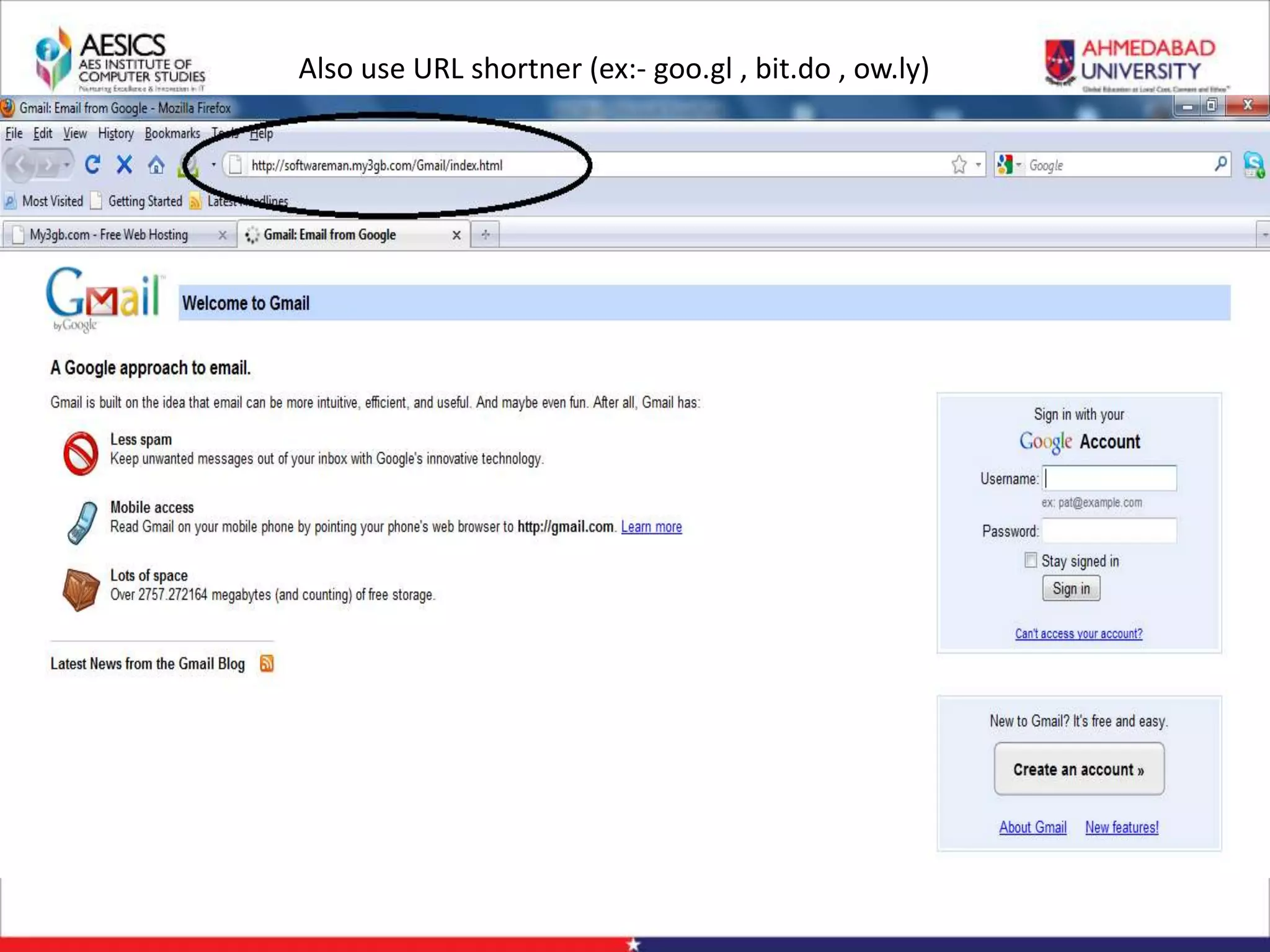
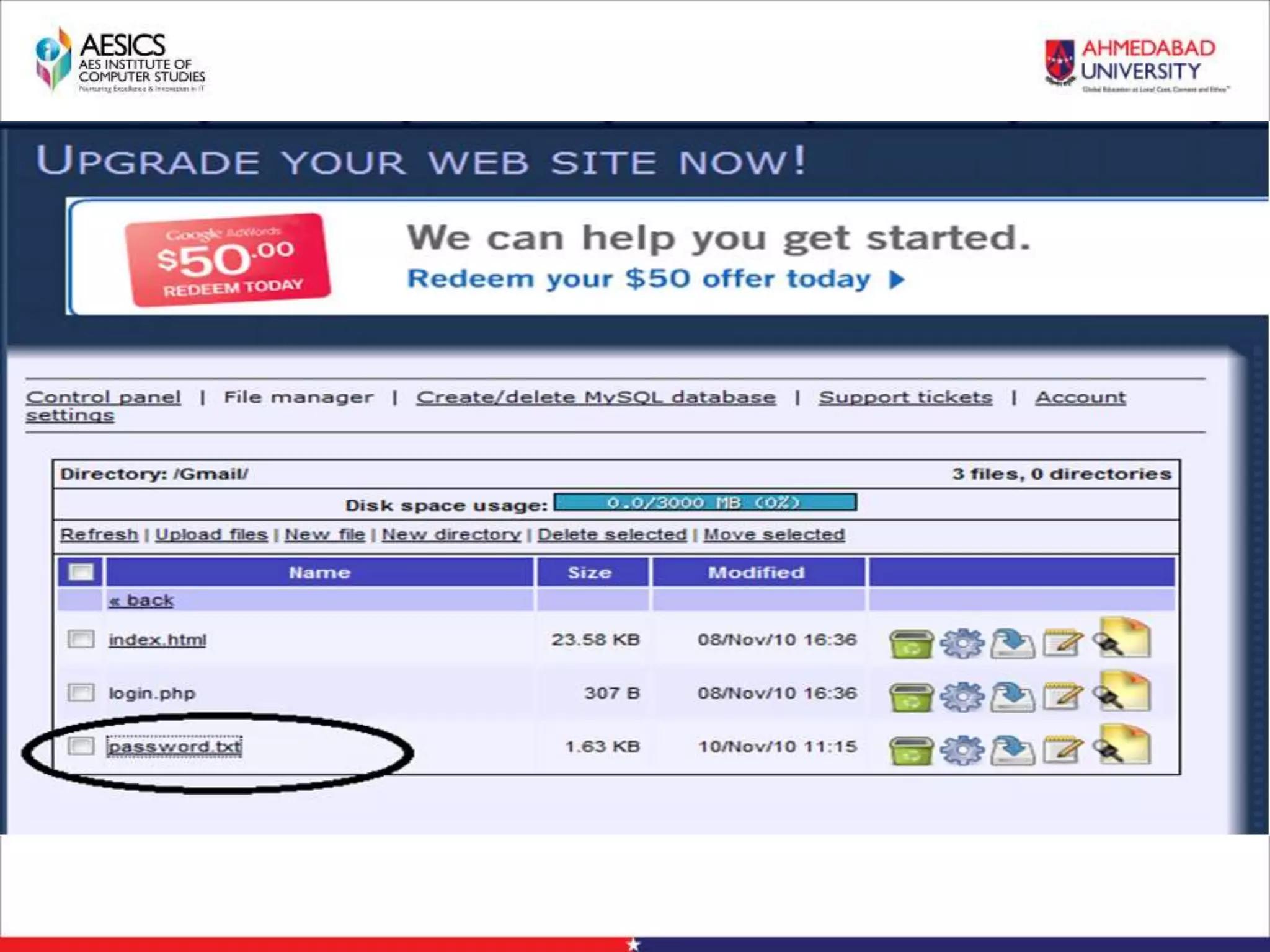
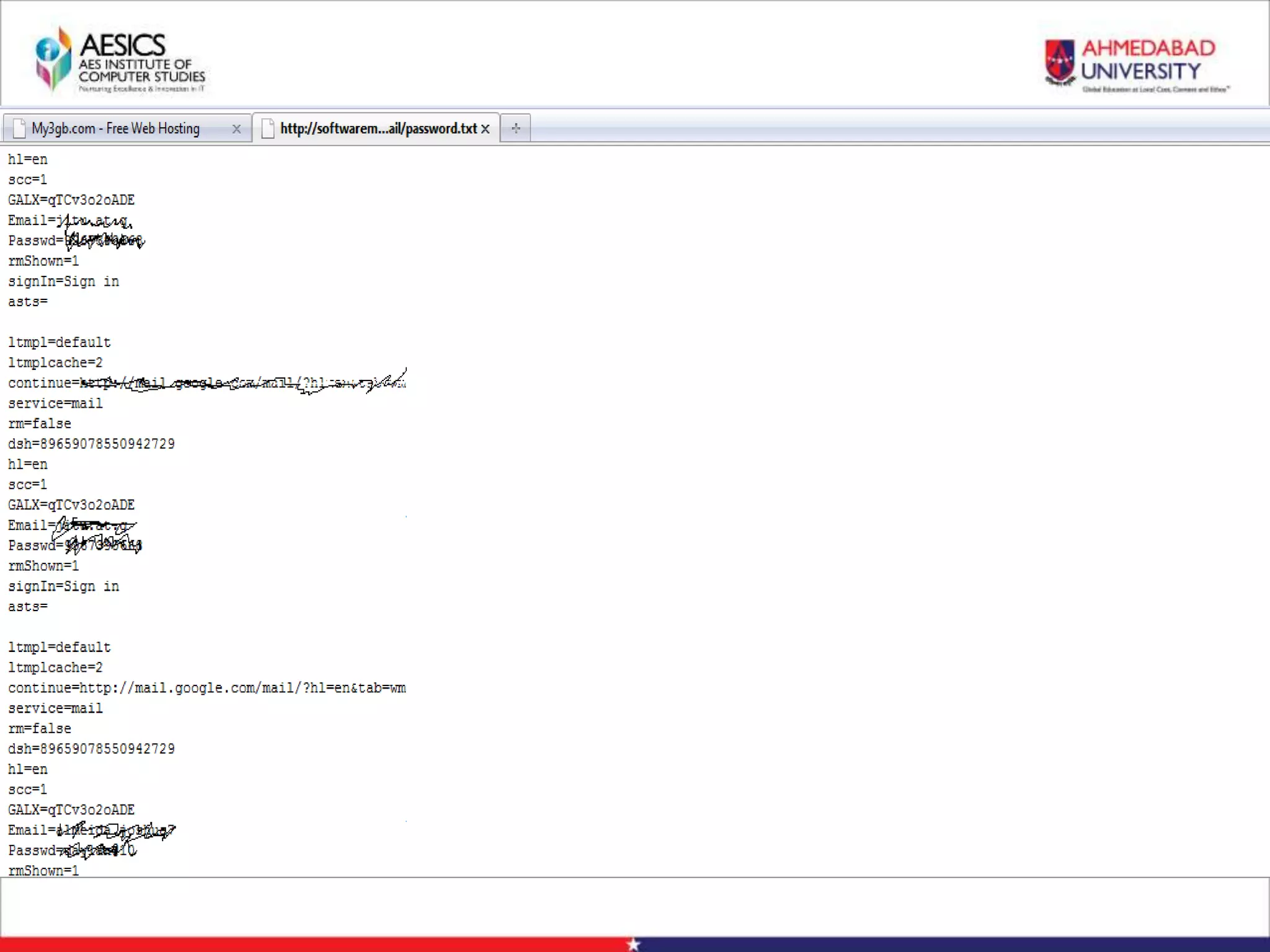
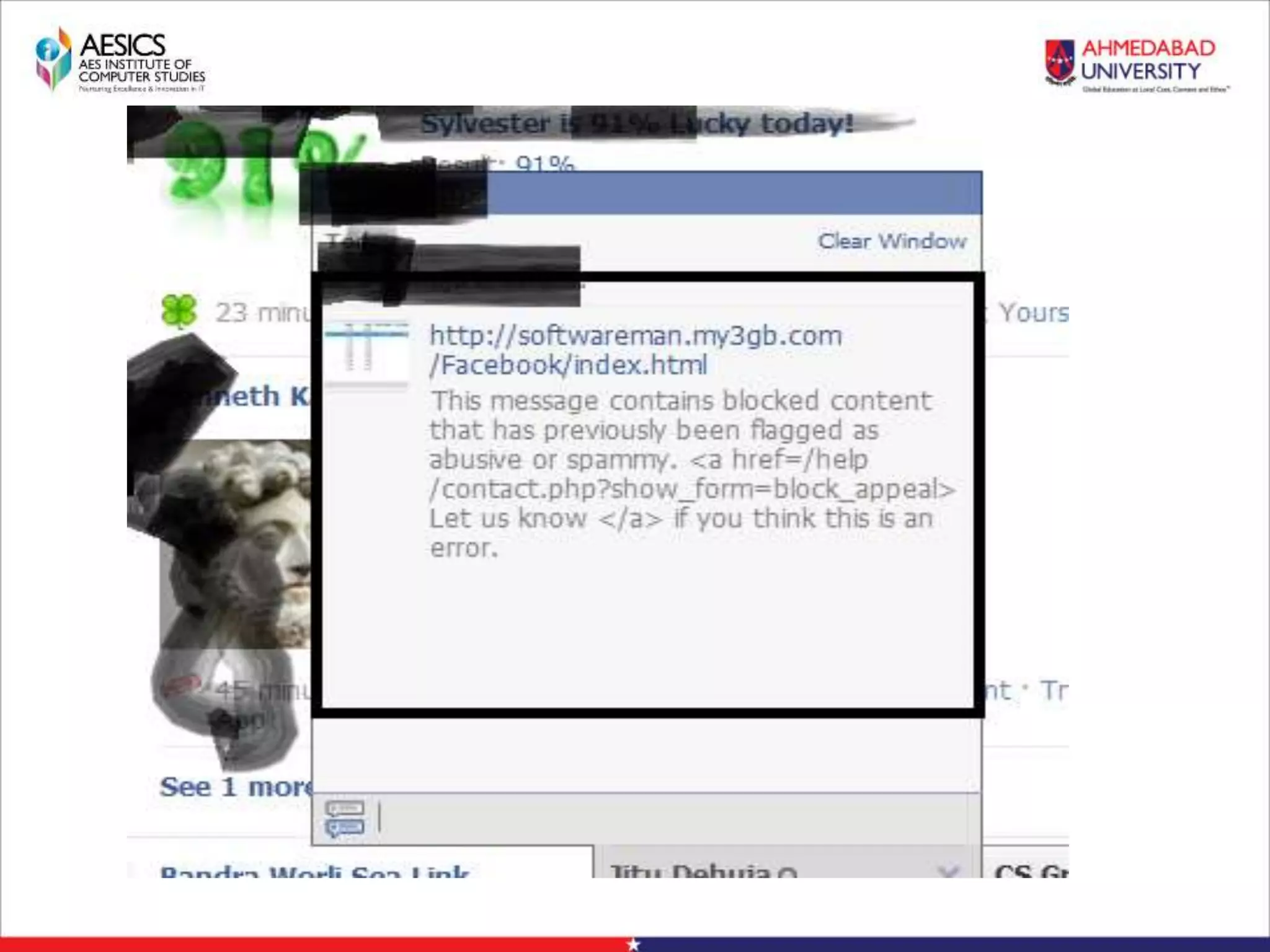
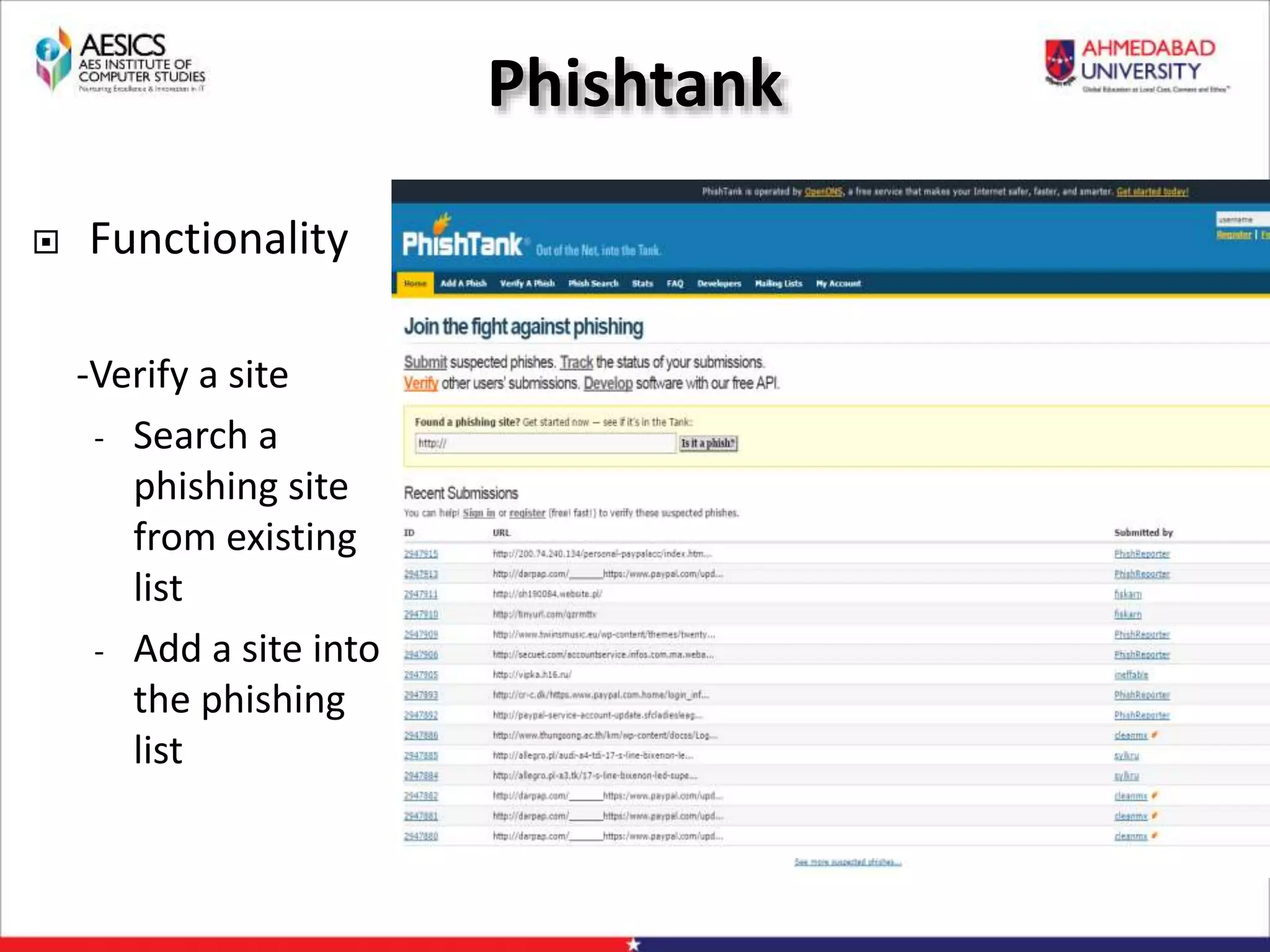
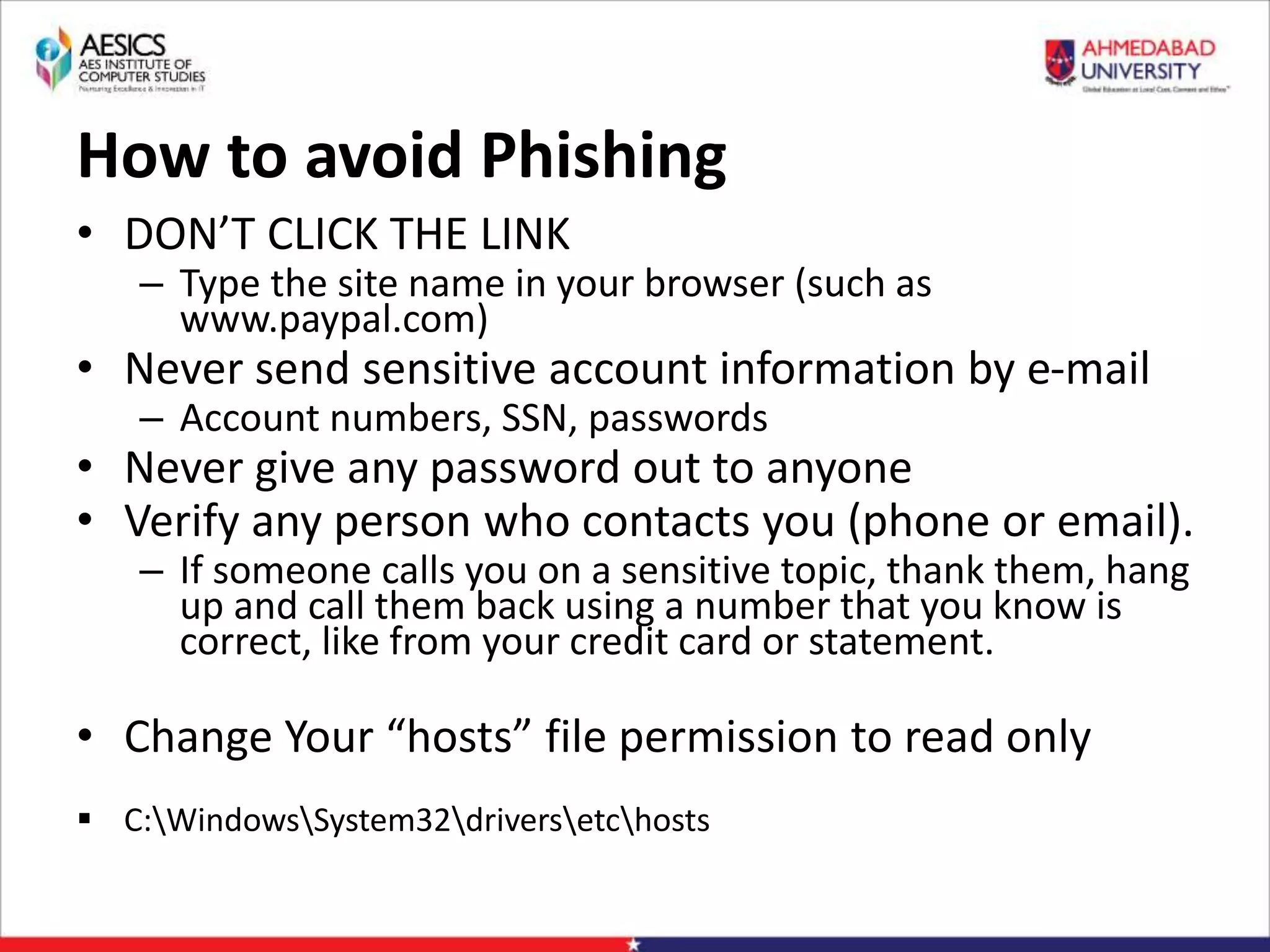
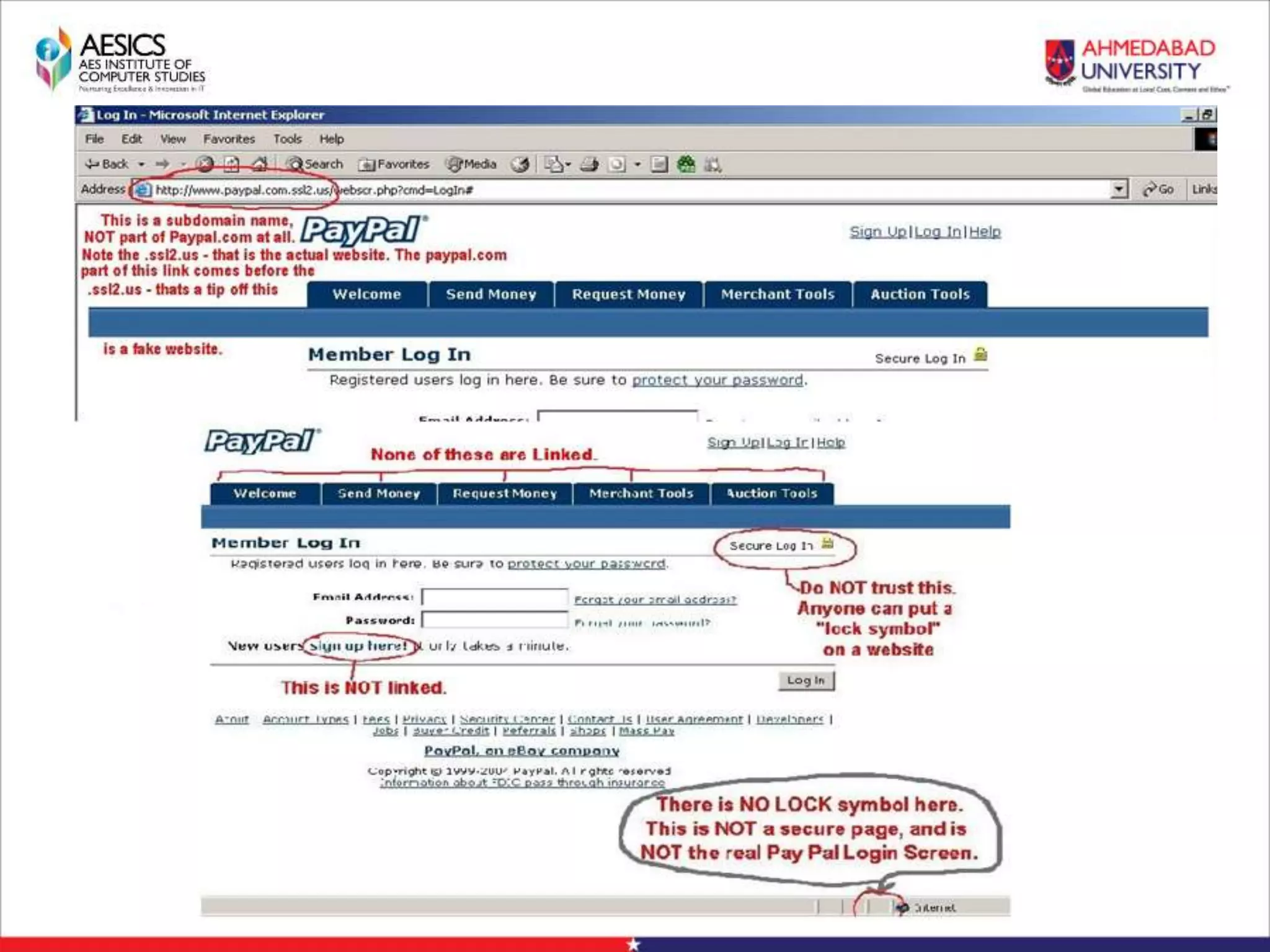
Internet Phishing involves criminals masquerading as trustworthy entities to acquire sensitive user information. Hackers use software to create fake websites mimicking legitimate sites, then use URL shorteners to send phishing links. Users who click the links and enter information enable the hacker to access their accounts. Keyloggers secretly record keyboard input to steal usernames, passwords and other private details. People can avoid phishing by being wary of unsolicited links and calls, using strong passwords, and keeping software up to date.




![Key loggers
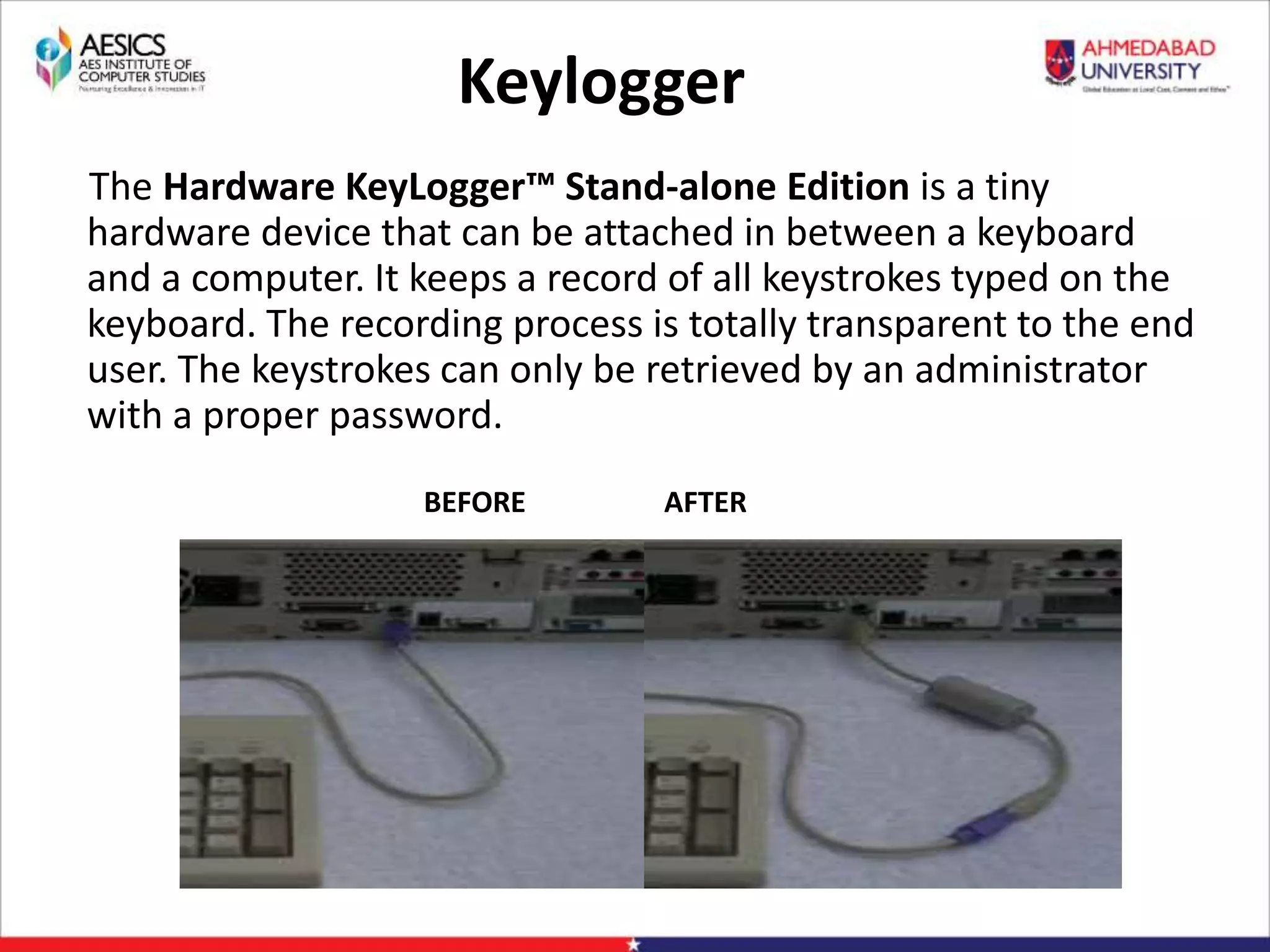
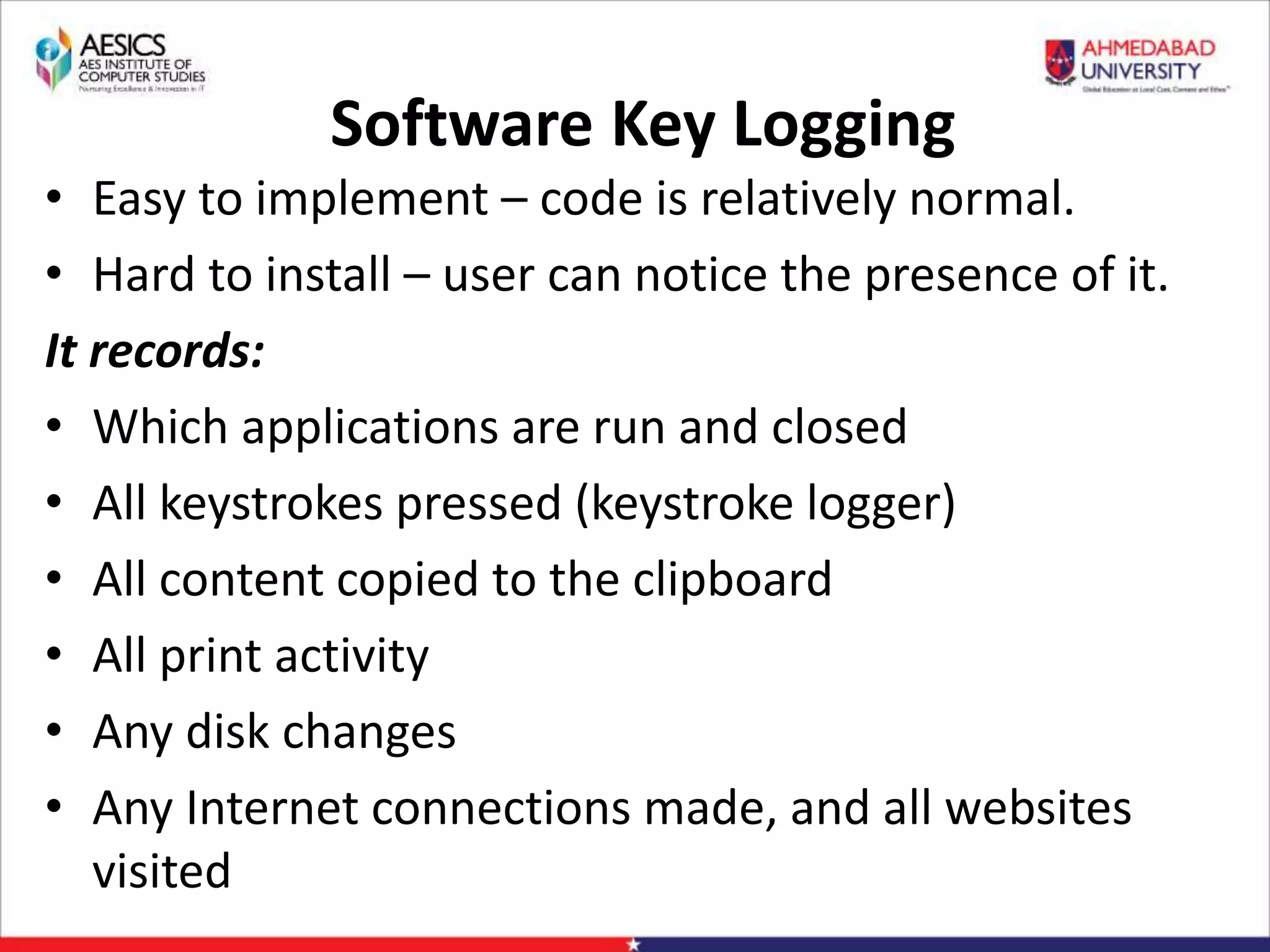
Definition: “A keylogger is something that records
keystrokes made on a computer. It captures every key
pressed on the keyboard and stores it down in a file or
memory bank that can be viewed by the person
performing the monitoring in real-time, or at a later date.”
[1]
There are two types of keylogger: hardware keylogger and
software keylogger
[1] http://www.keyghost.com/keylogger](https://image.slidesharecdn.com/symcalroolno035phishing-160228120736/75/secure-from-Phishing-Hacking-and-Keylogger-22-2048.jpg)