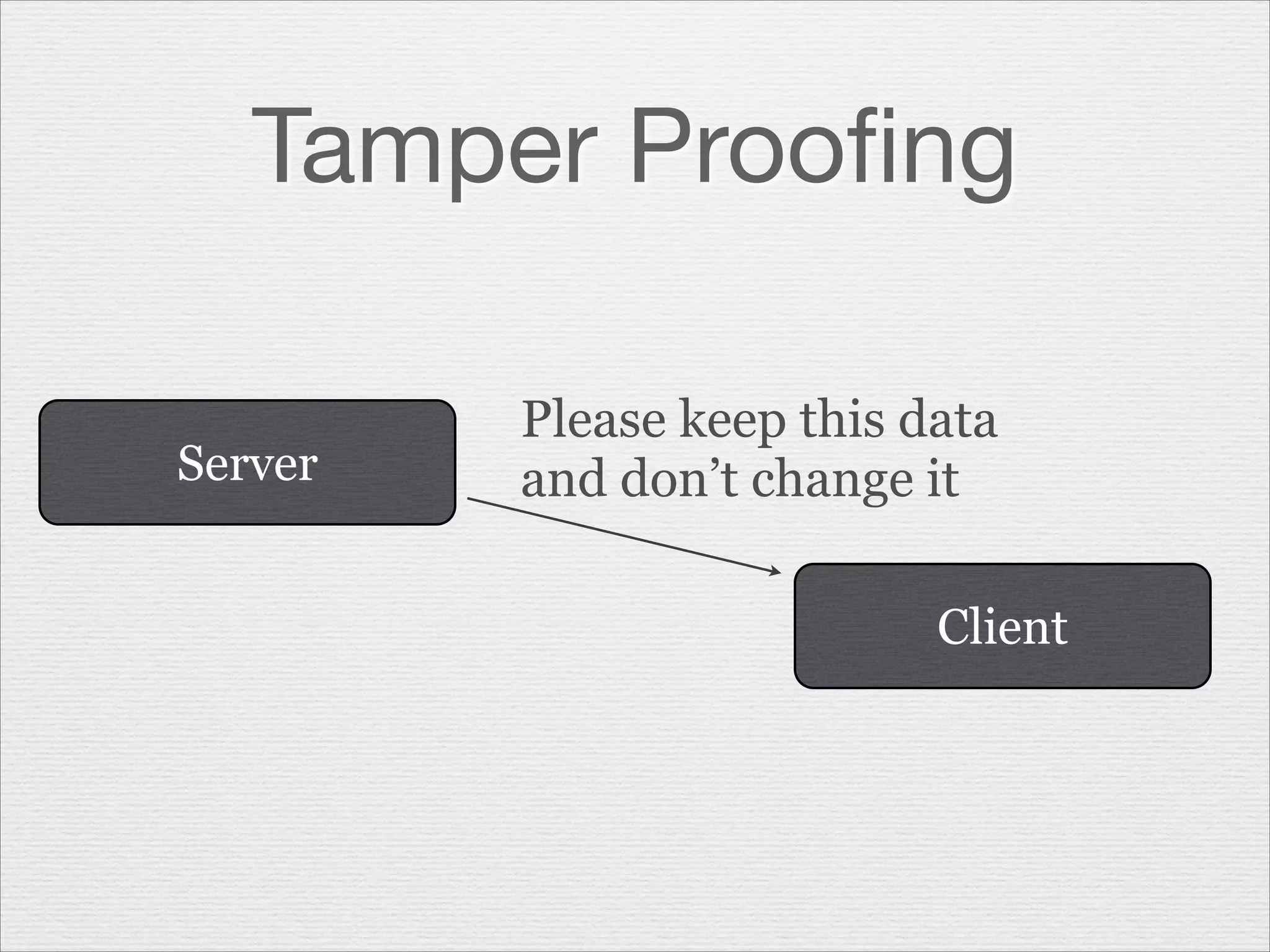
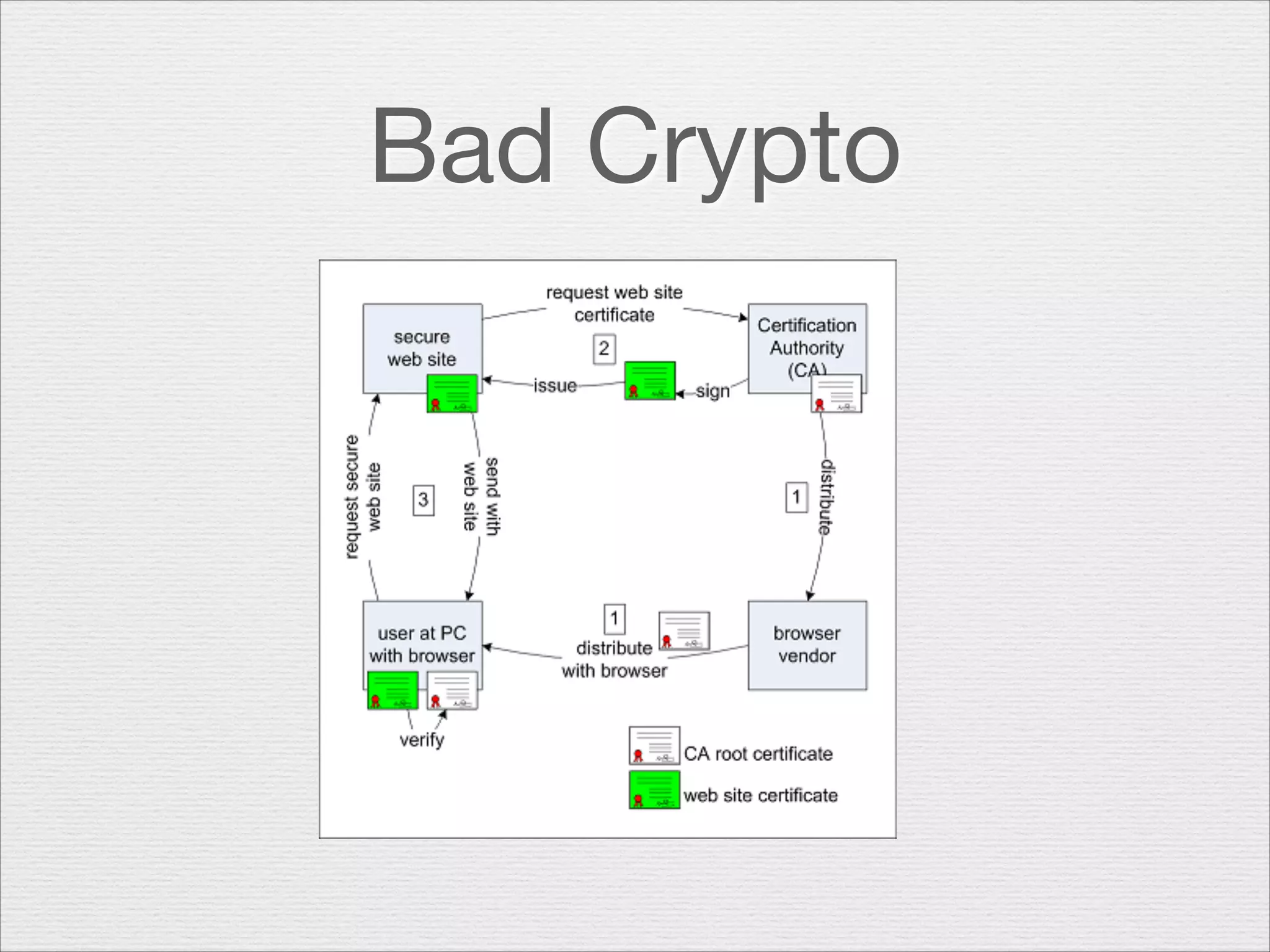
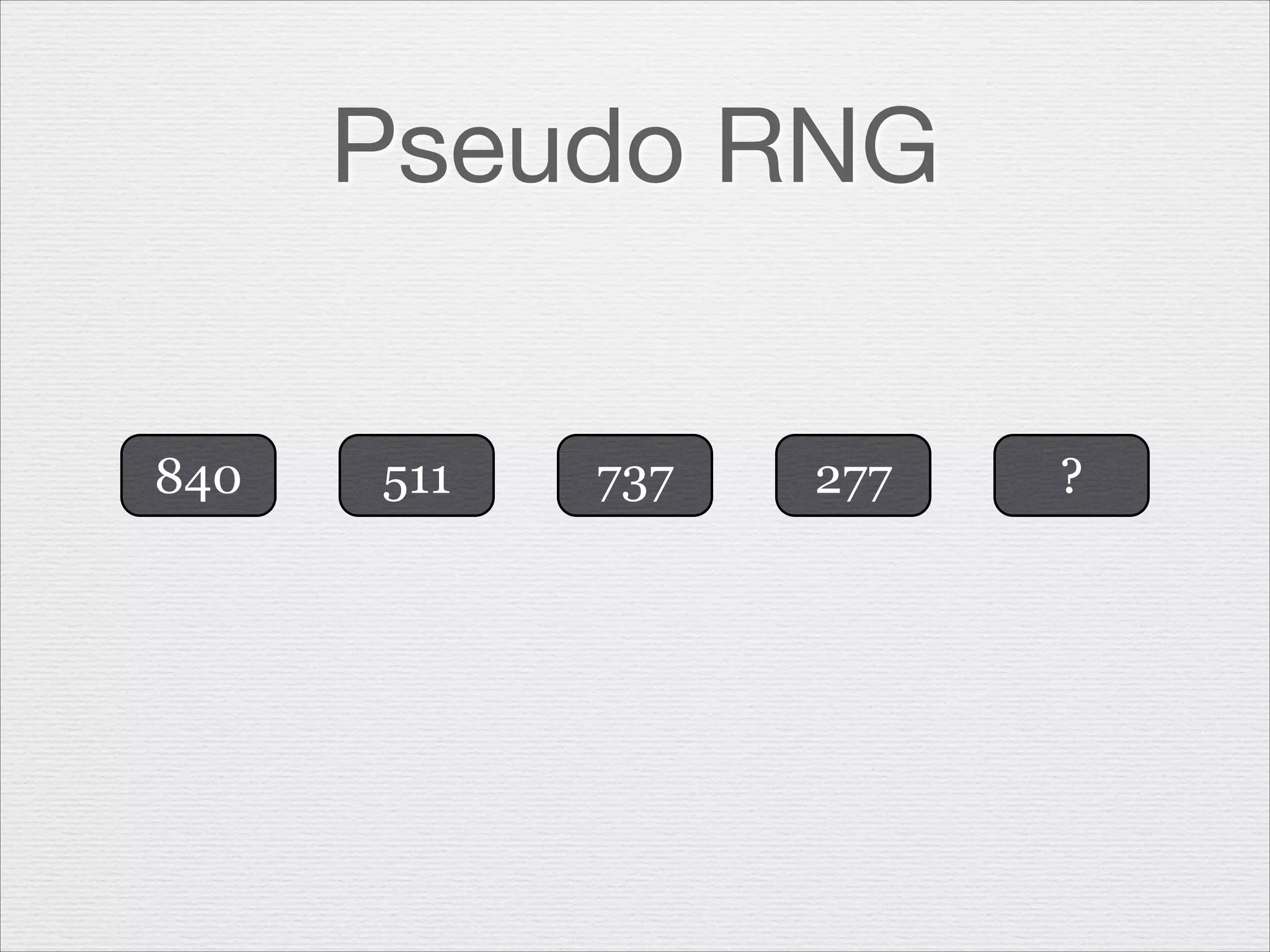
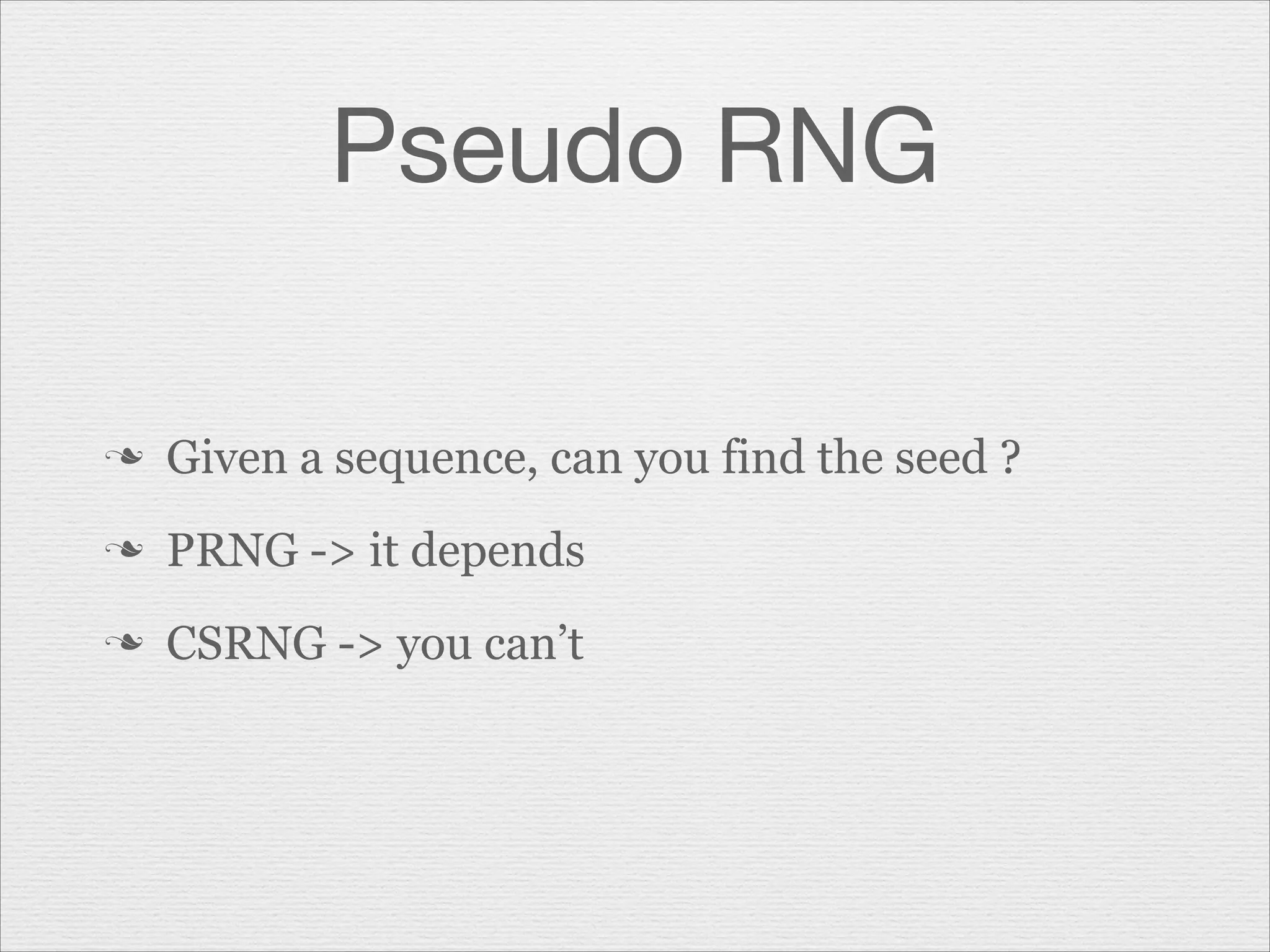
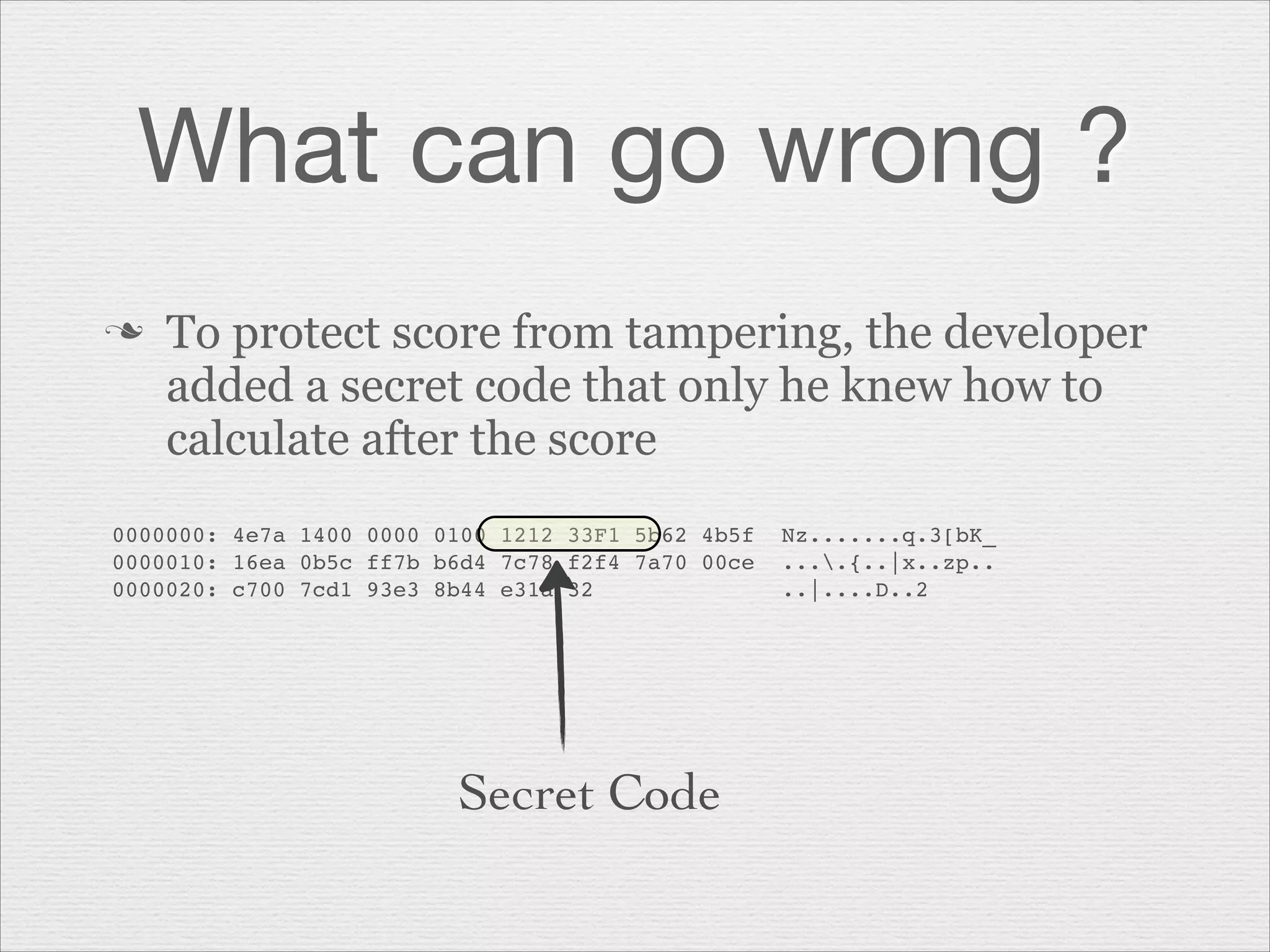
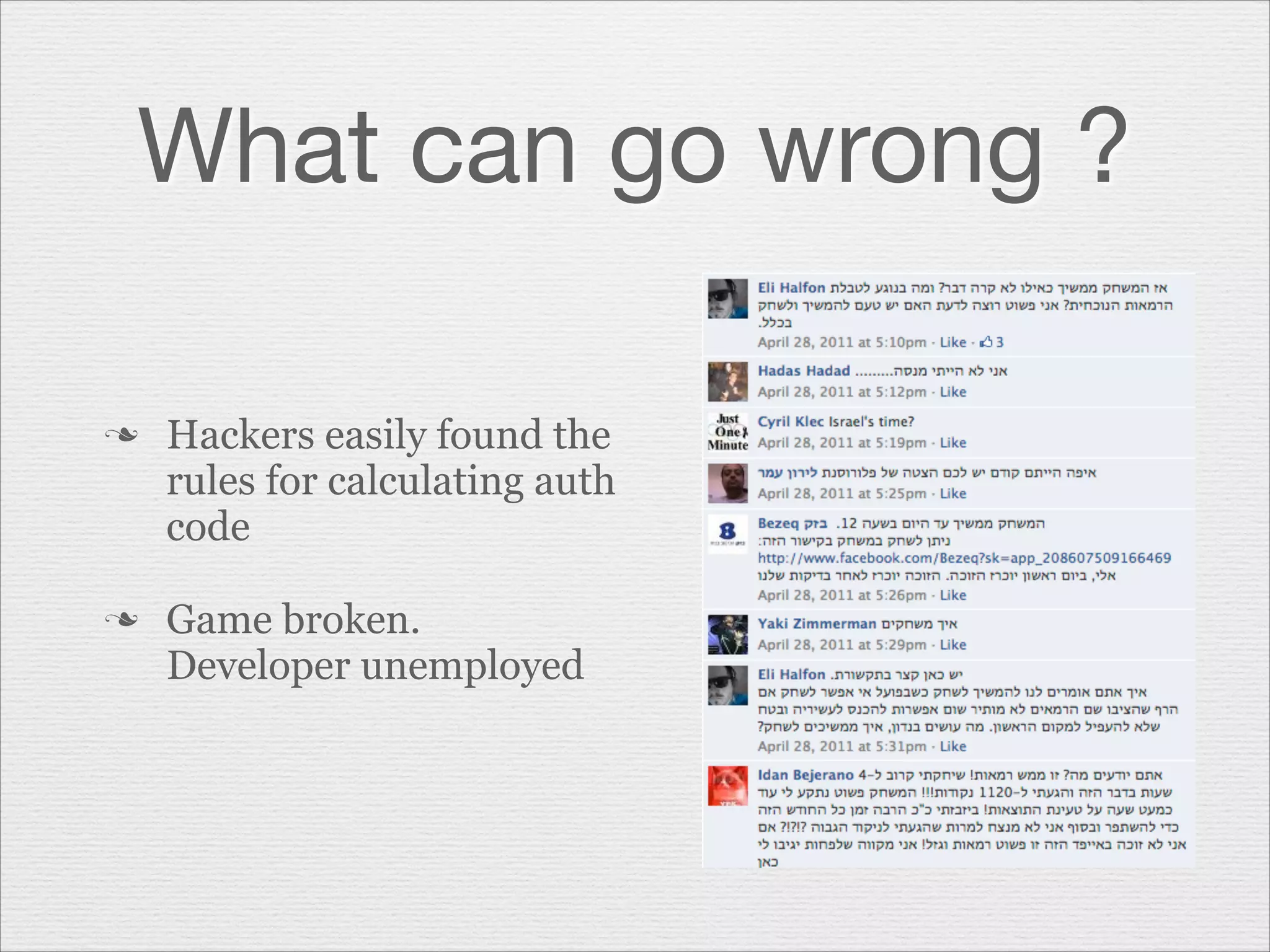
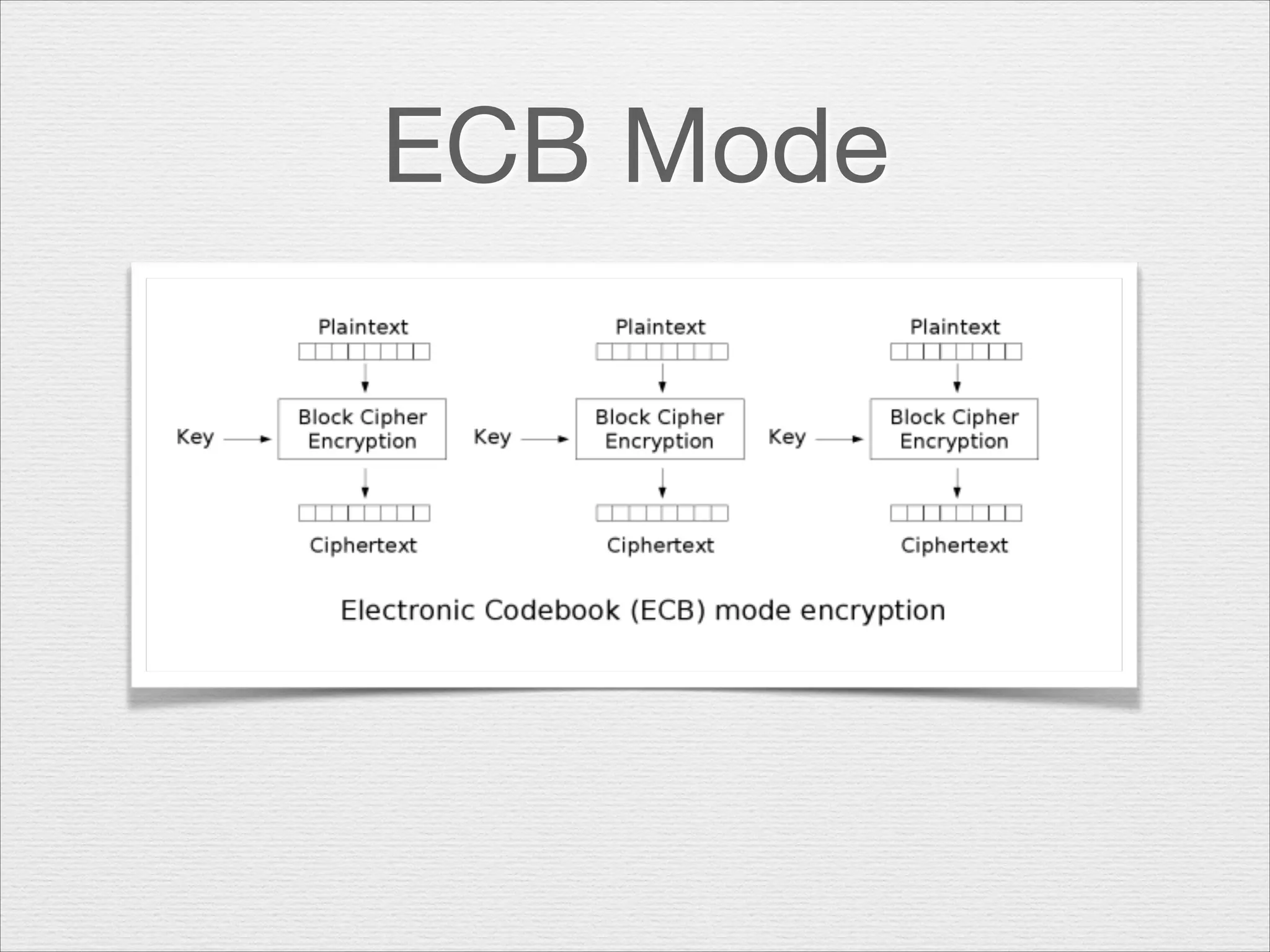
This document discusses misusing cryptography. It begins with an agenda covering why cryptography is misused and how random number generators and crypto algorithms can be misused. It then discusses examples of what can go wrong, such as a game developer unintentionally allowing hackers to easily determine the secret code protecting scores. The document emphasizes that cryptography is complex and should not be casually misused, as failures can result in compromises like hacked systems and lost jobs. It provides recommendations for proper cryptographic practices.




































![Demo: Ruby GCM
require
# currently, AES-256-GCM or AES-256-CTR-HMAC-SHA-256
mode =
key = mode.
nonce = mode.
cipher = mode.
!
aead = cipher.
# aead[1] = 'f'
plaintext = cipher.
puts](https://image.slidesharecdn.com/04cryptography-140105065513-phpapp01/75/Cryptography-48-2048.jpg)