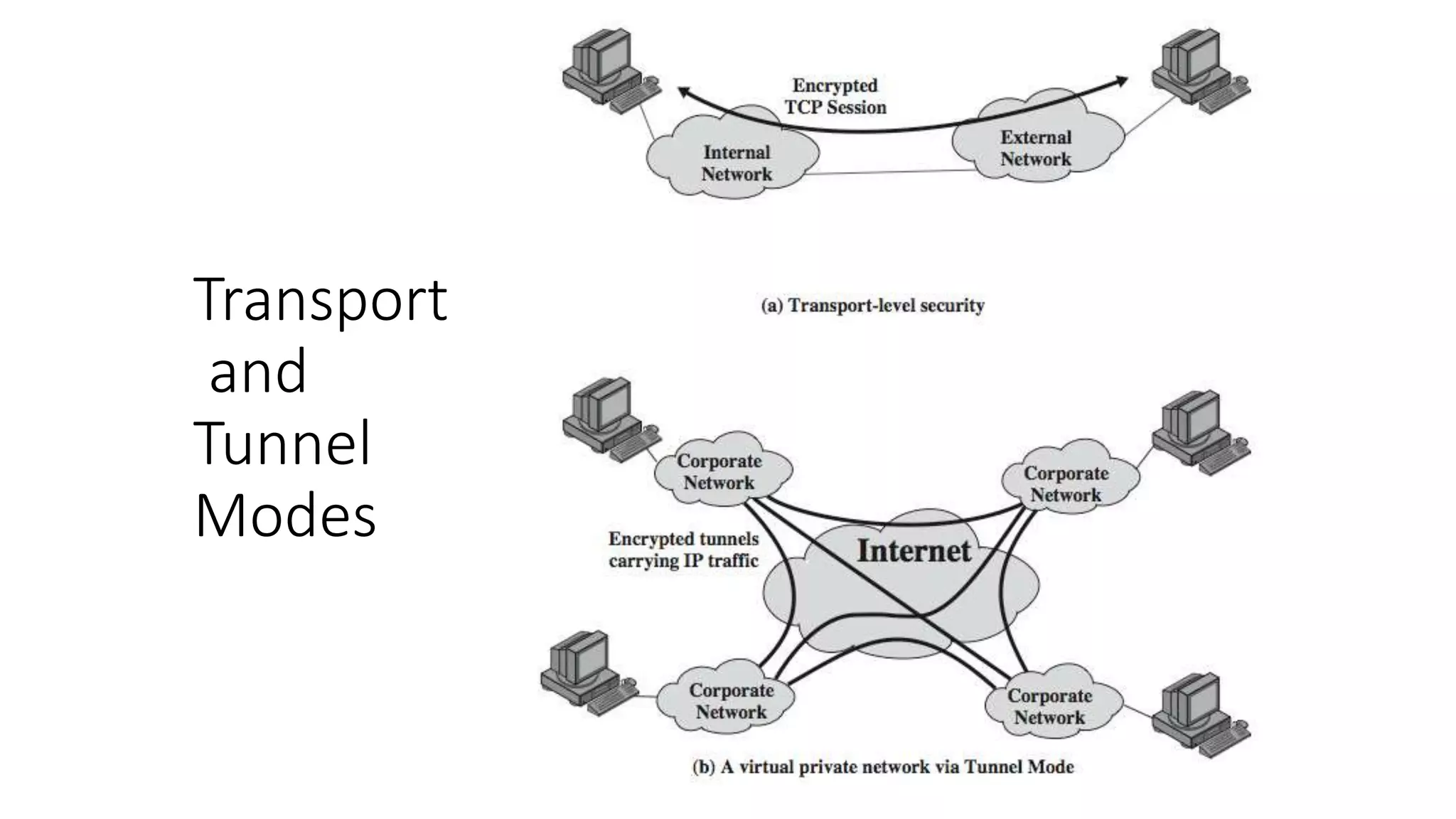
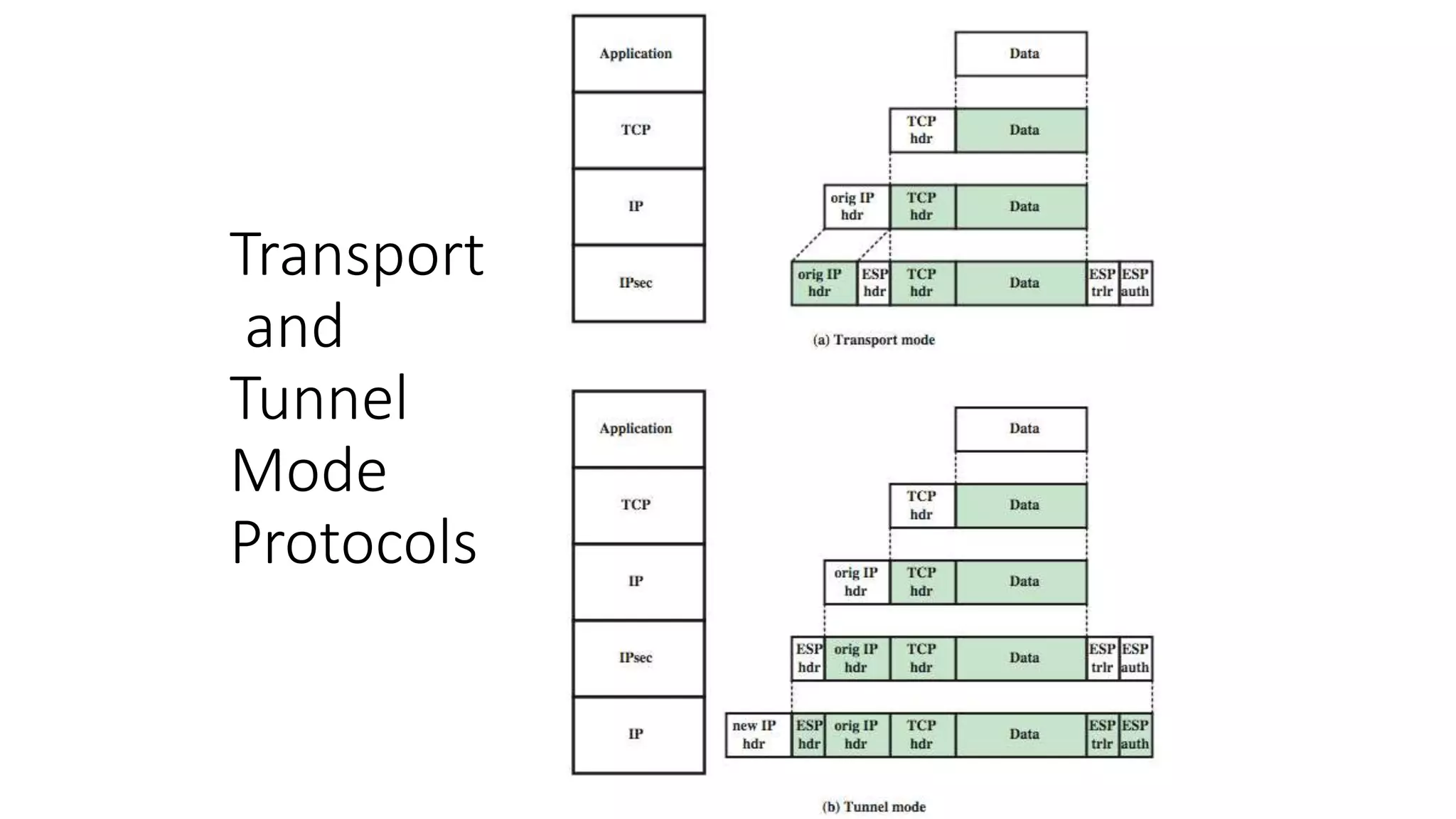
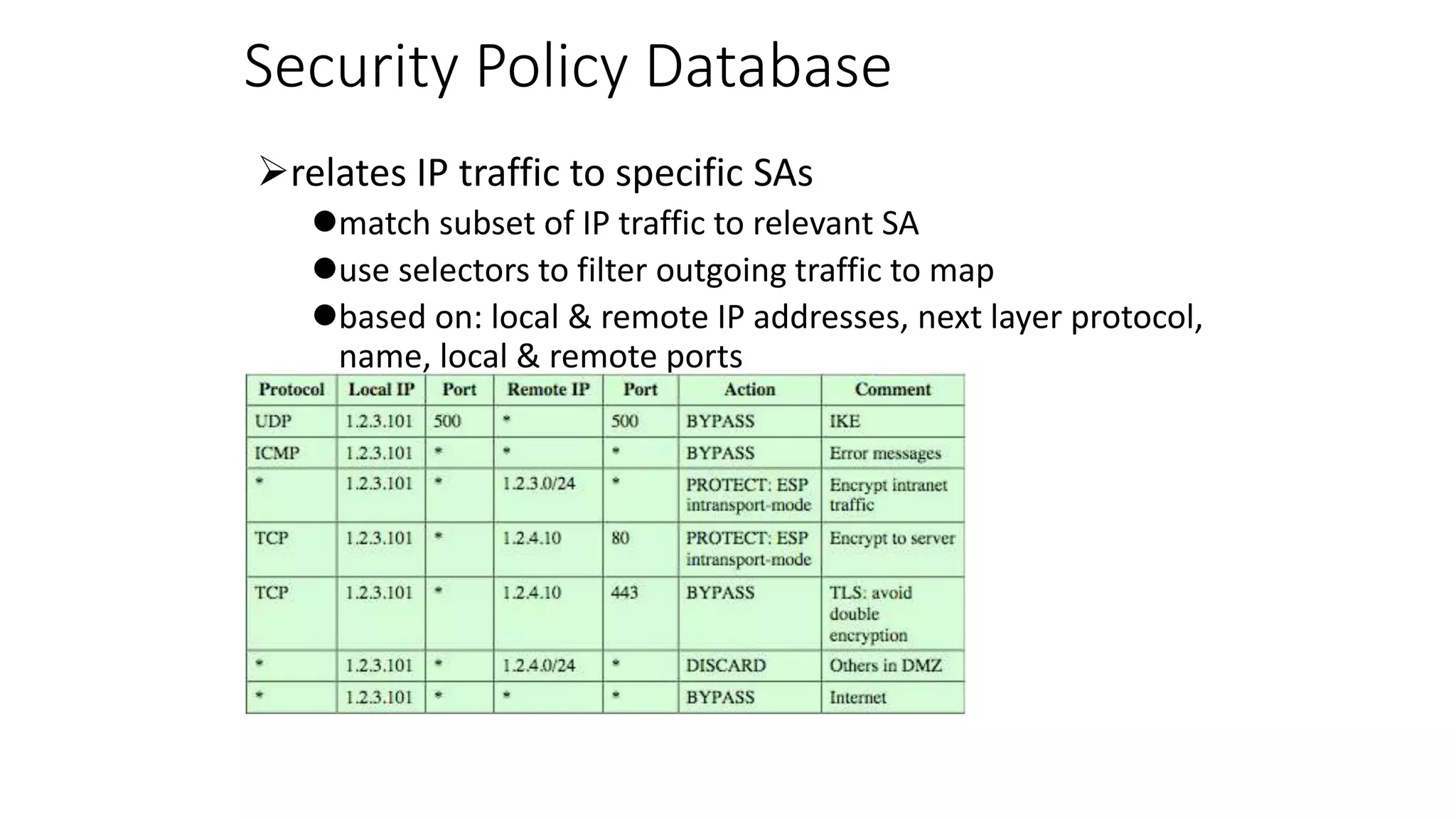
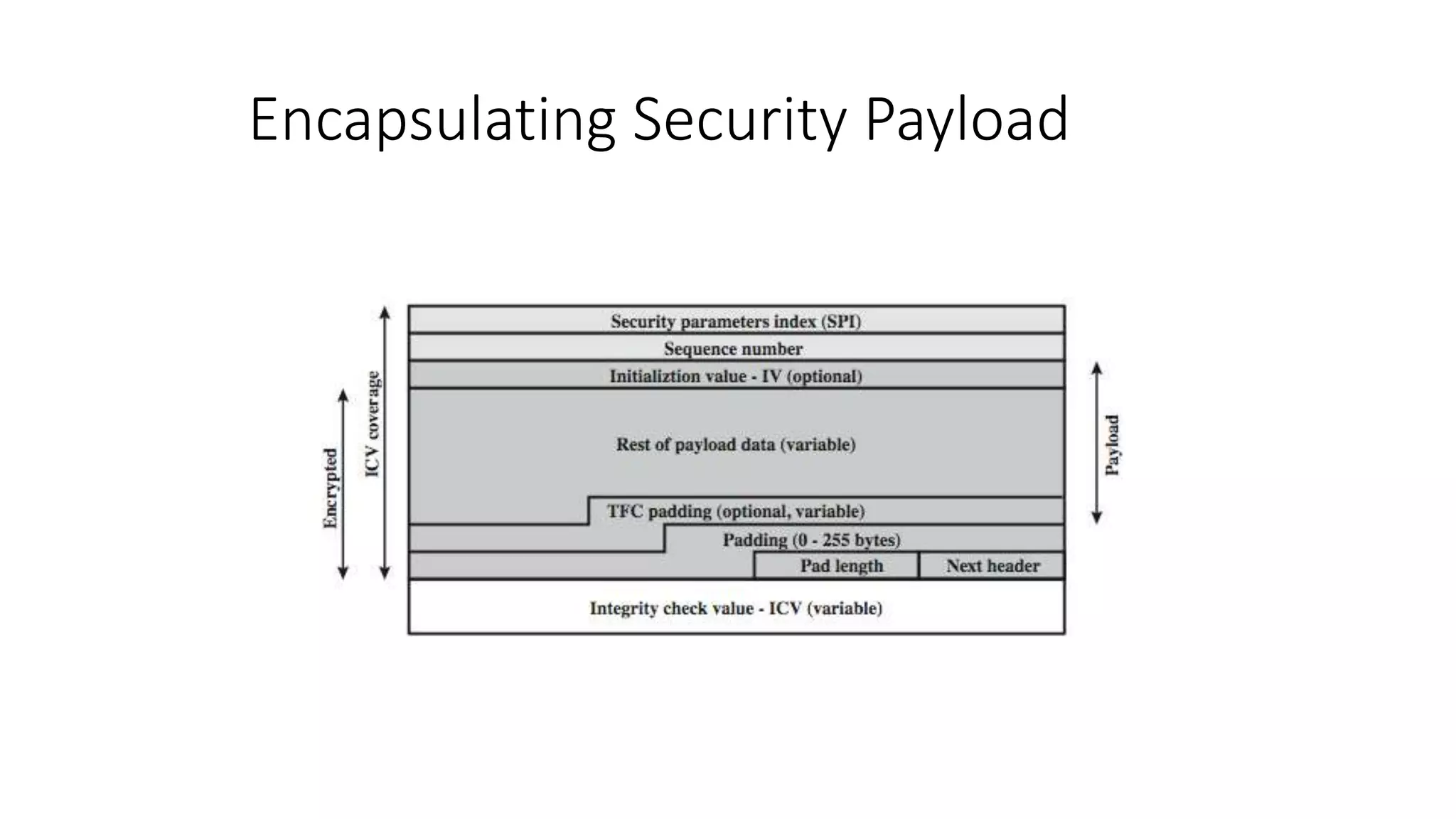
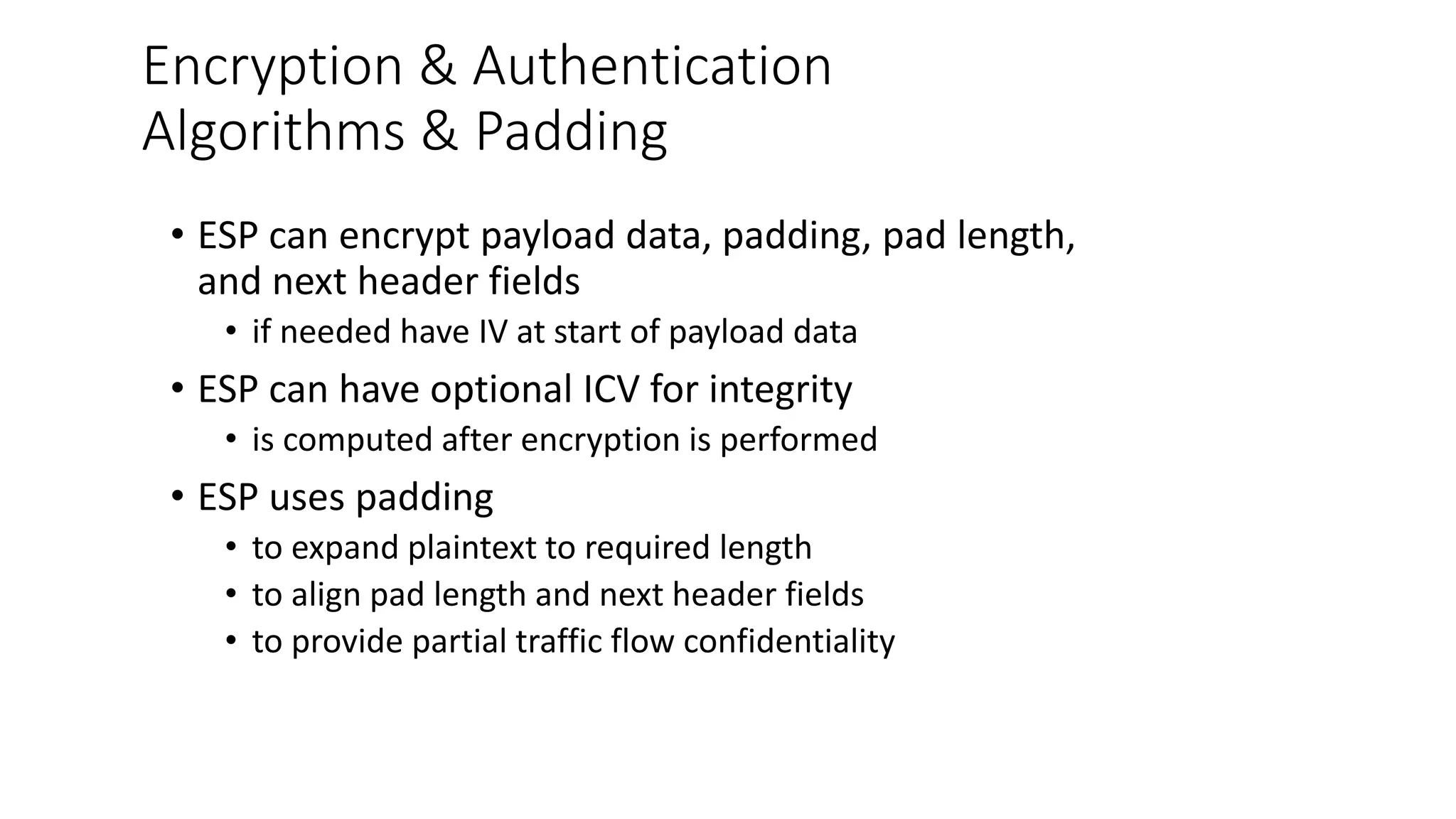
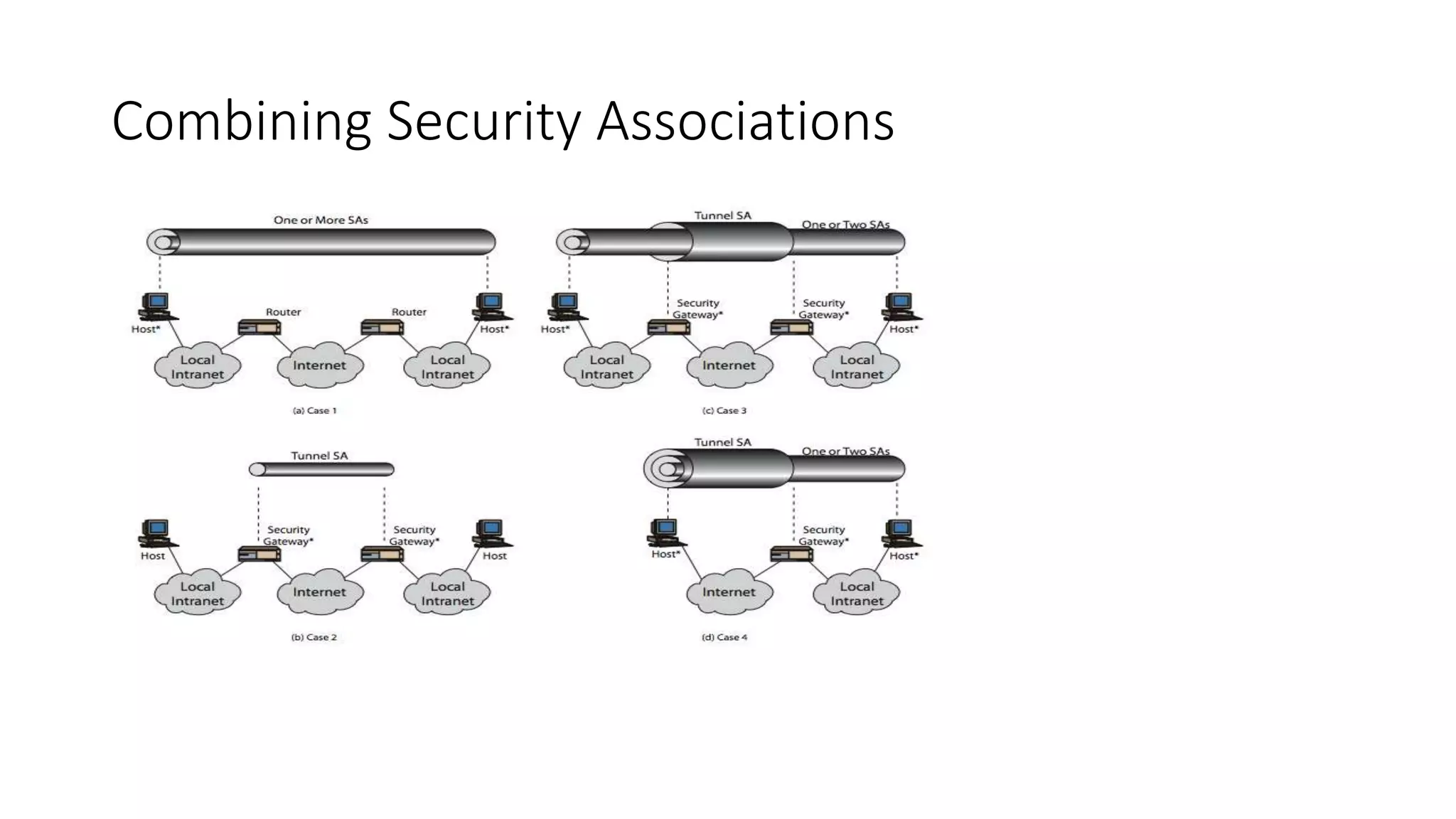
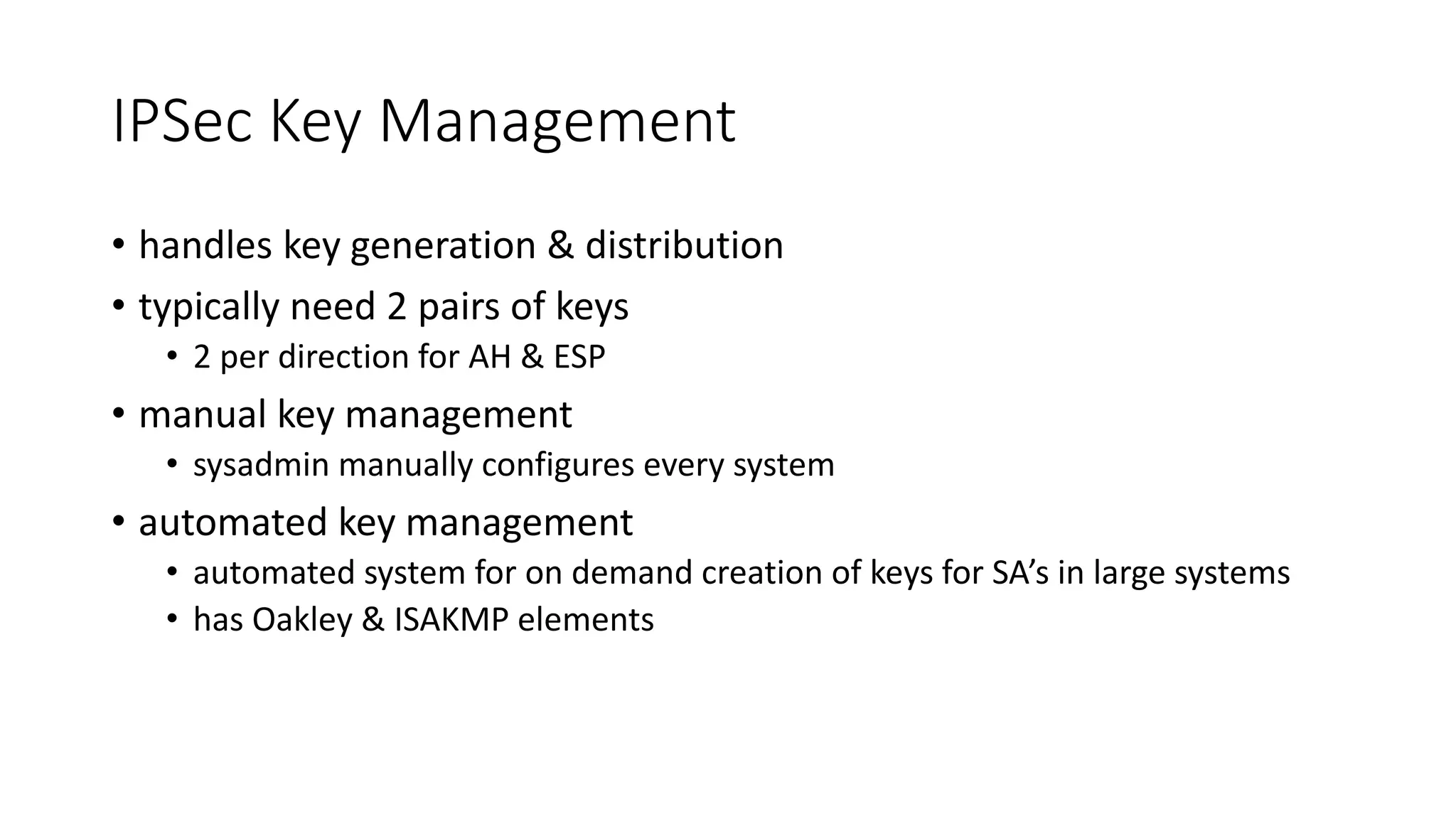
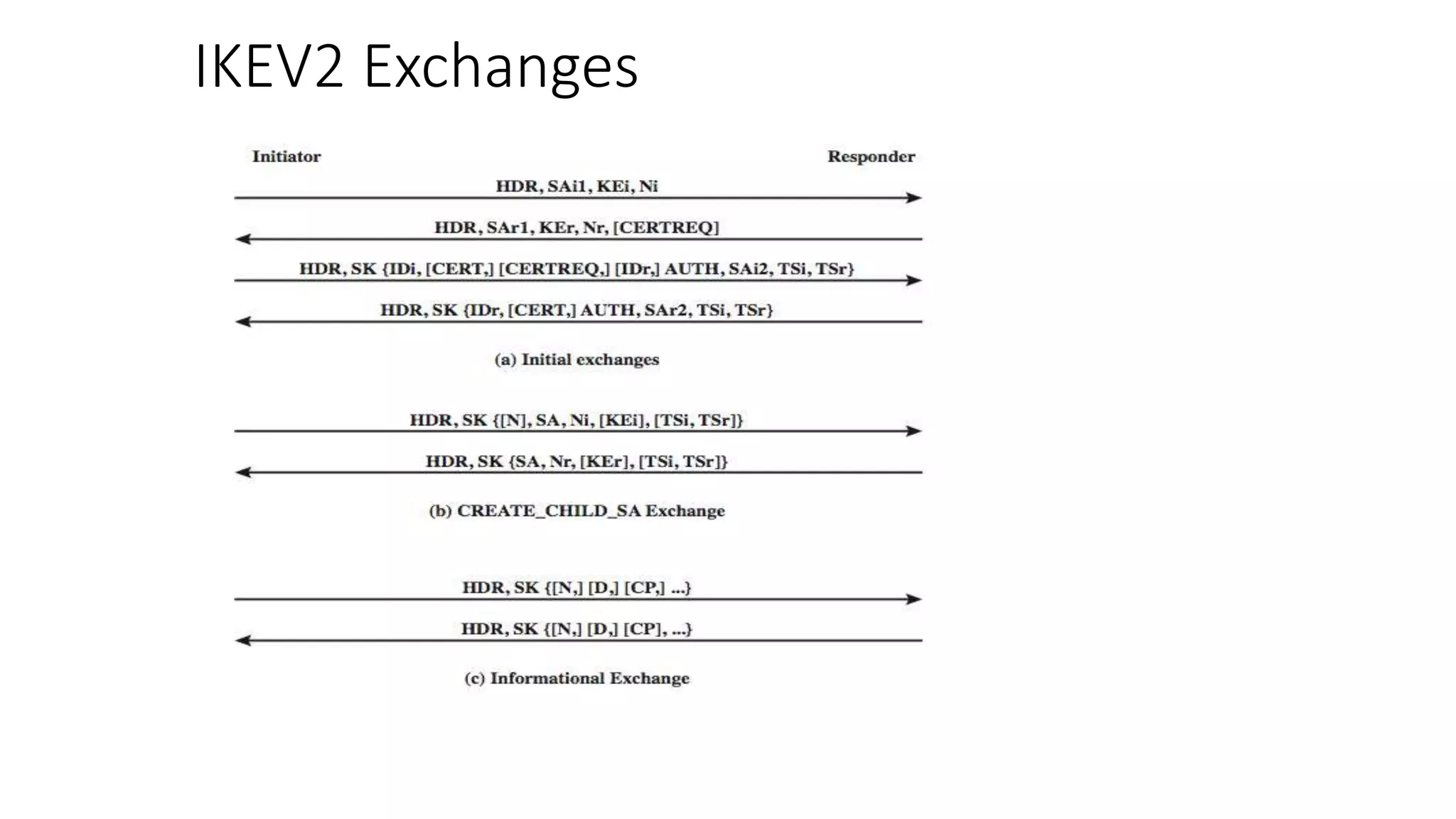
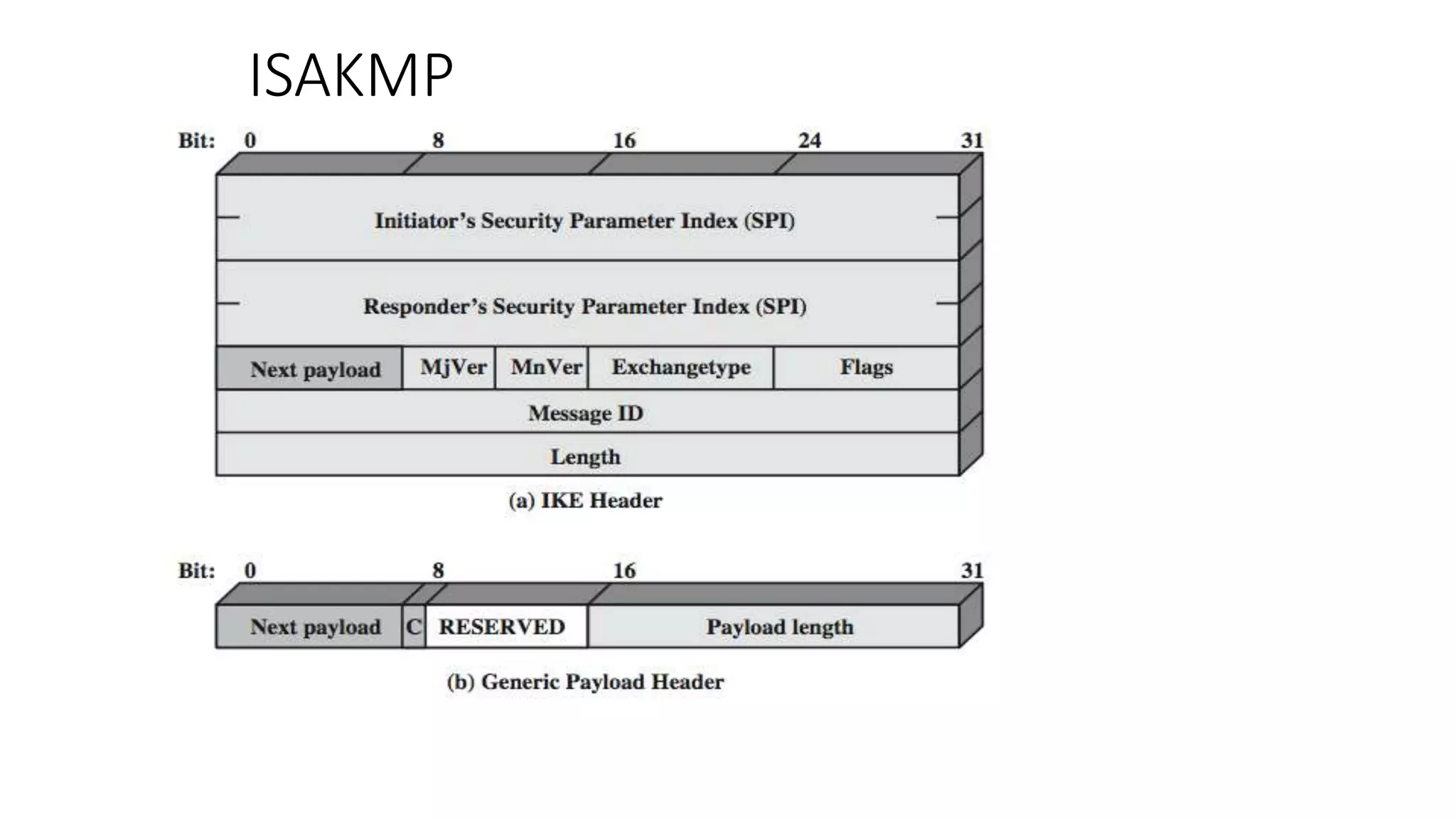
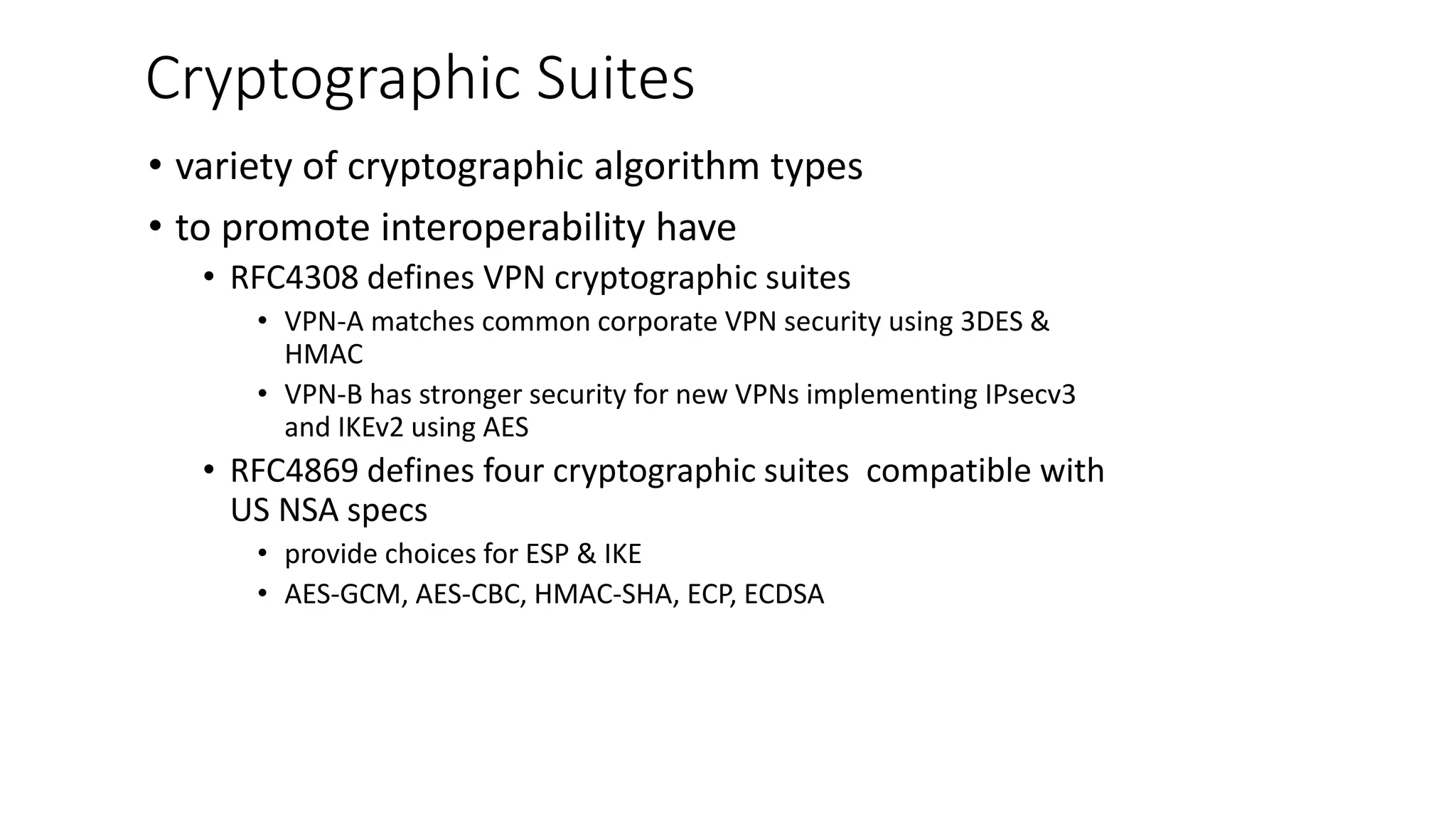
The document discusses the 3C-CSIRT model for cybersecurity, focusing on IP security (IPsec) to enhance network security for Afghanistan's Bakhtar University. It outlines IPsec's features, including authentication, integrity, confidentiality, and capabilities for securing communications across various networks. Additionally, it details the framework for key management and cryptographic algorithms, highlighting the importance of secure data transmission and prevention of unauthorized access.