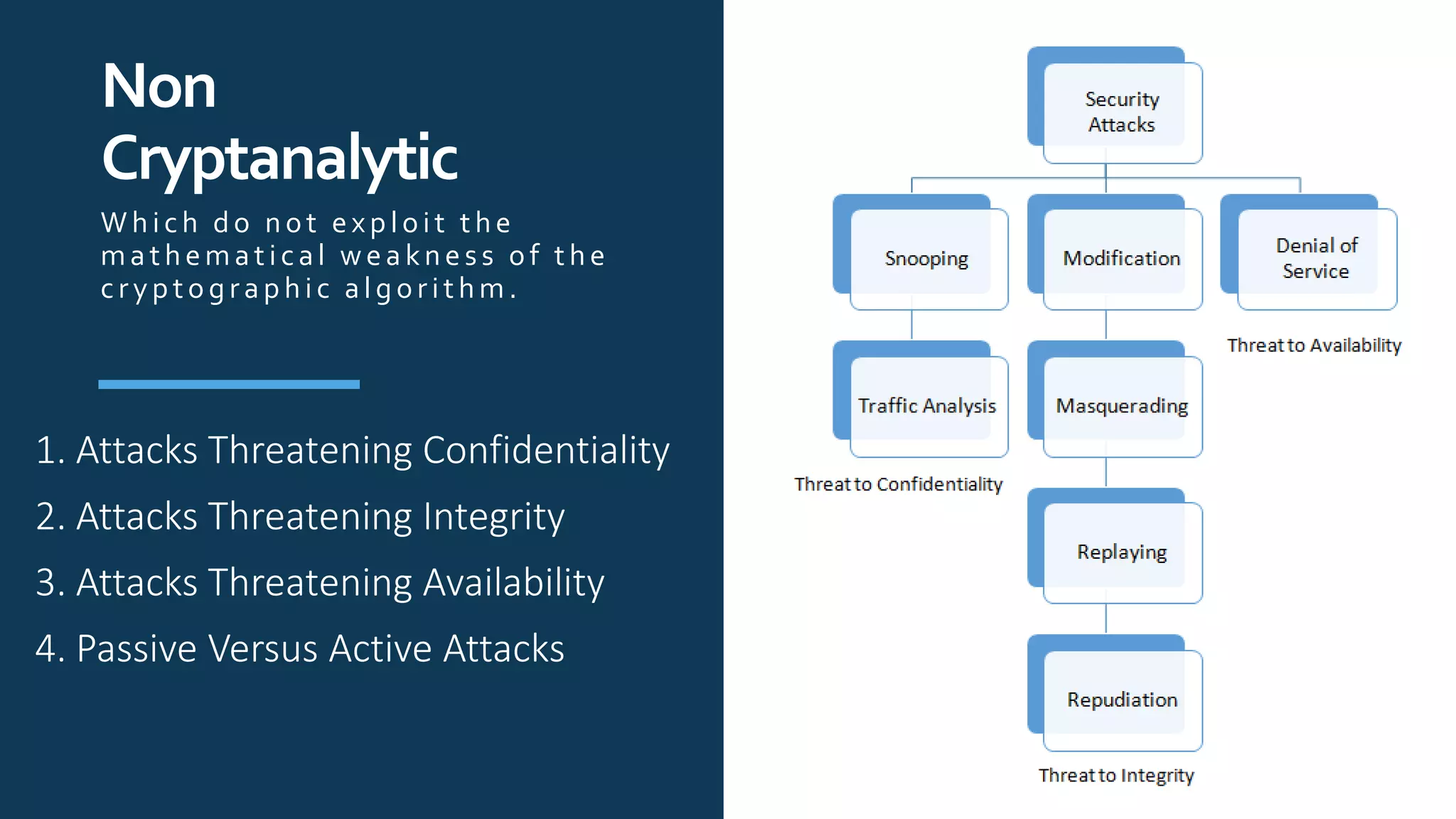
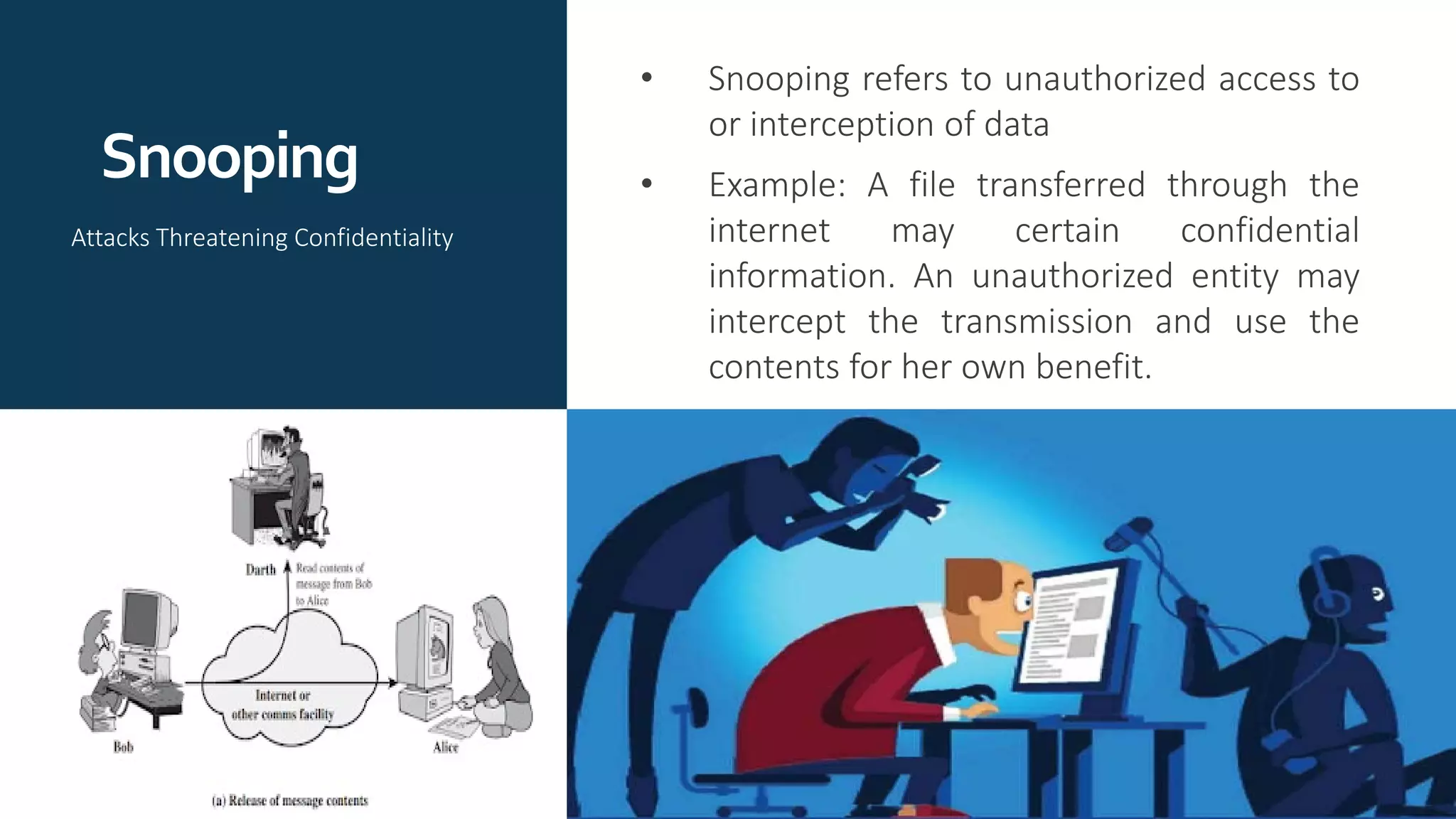
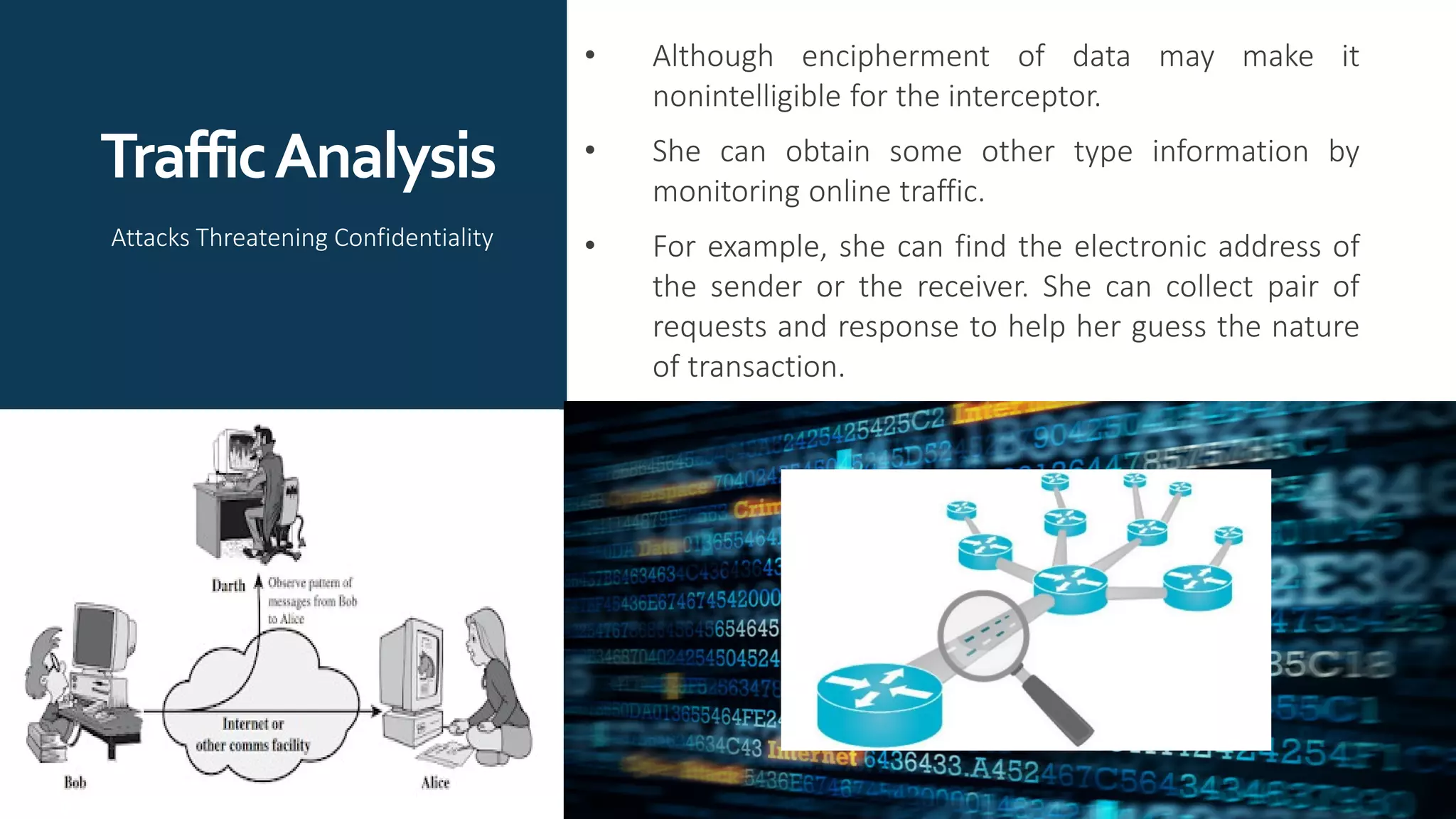
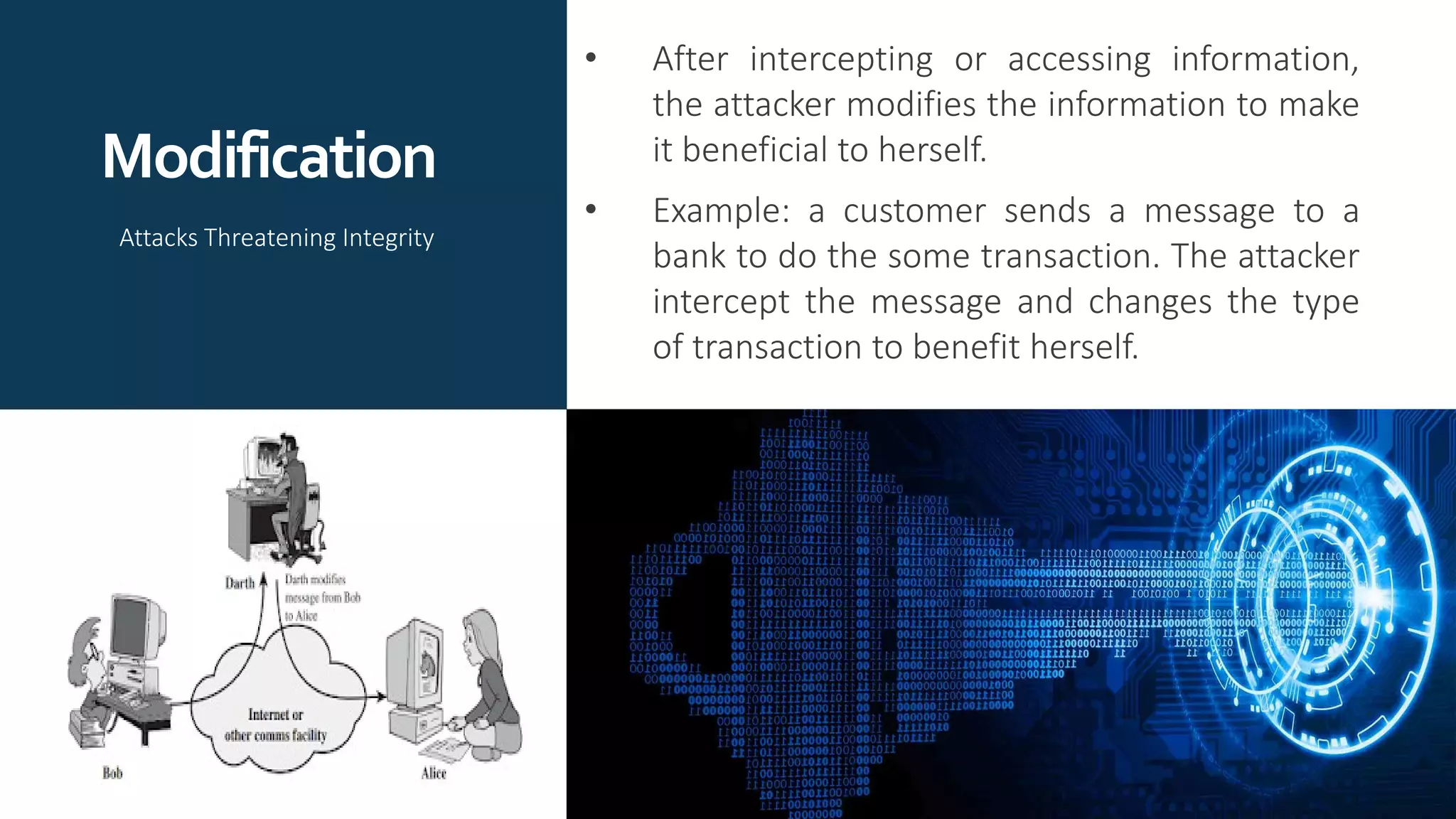
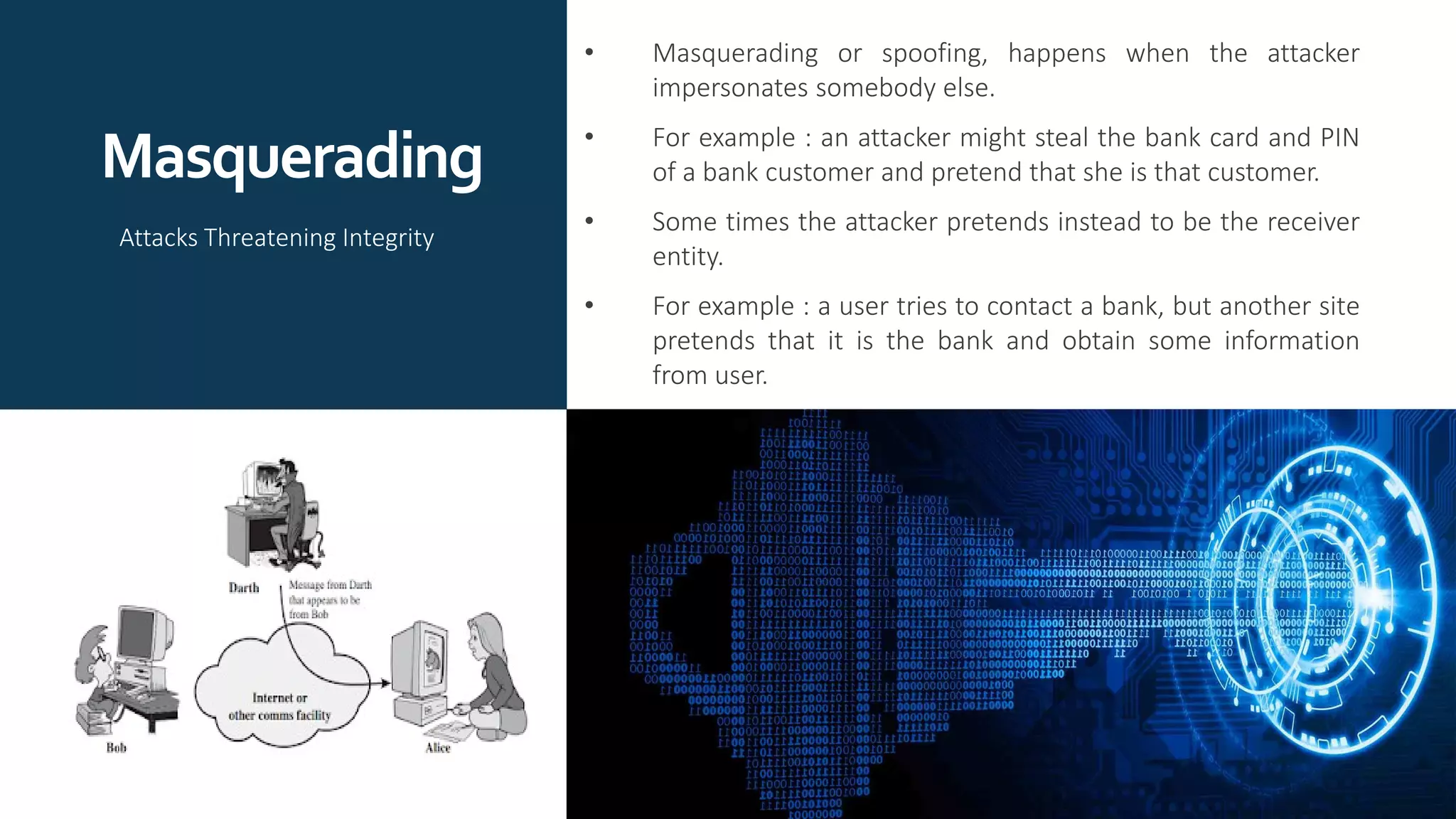
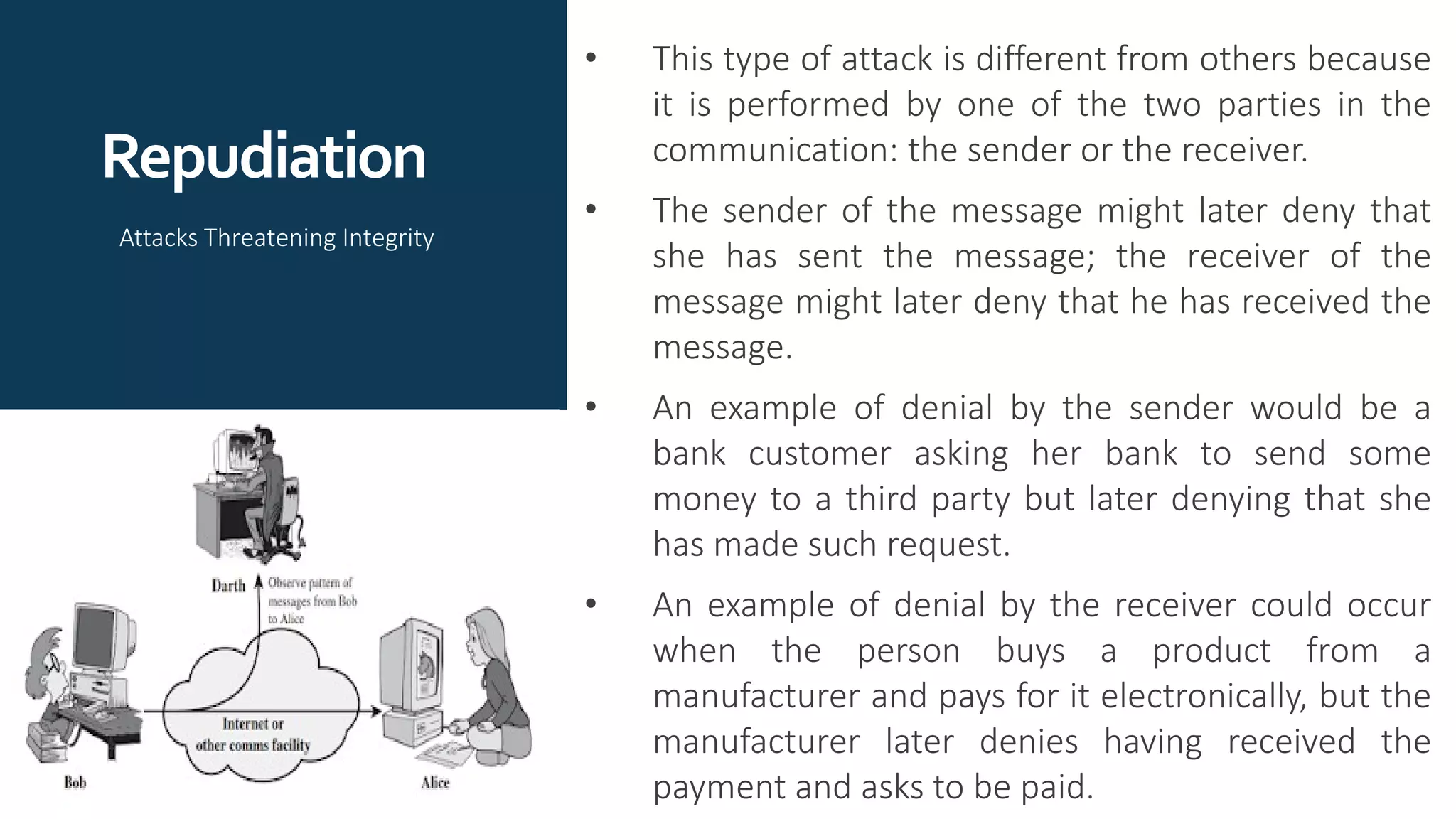
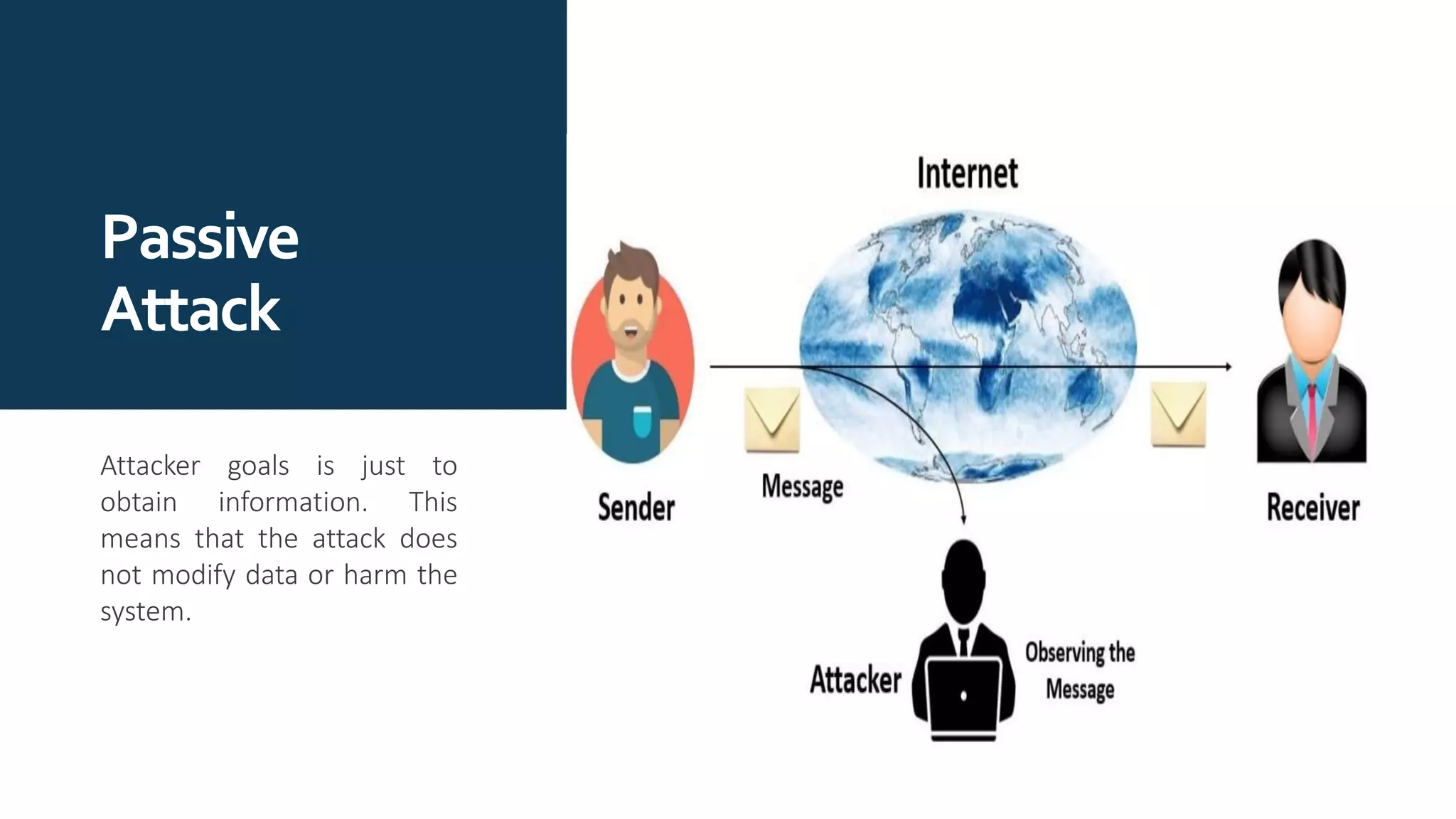
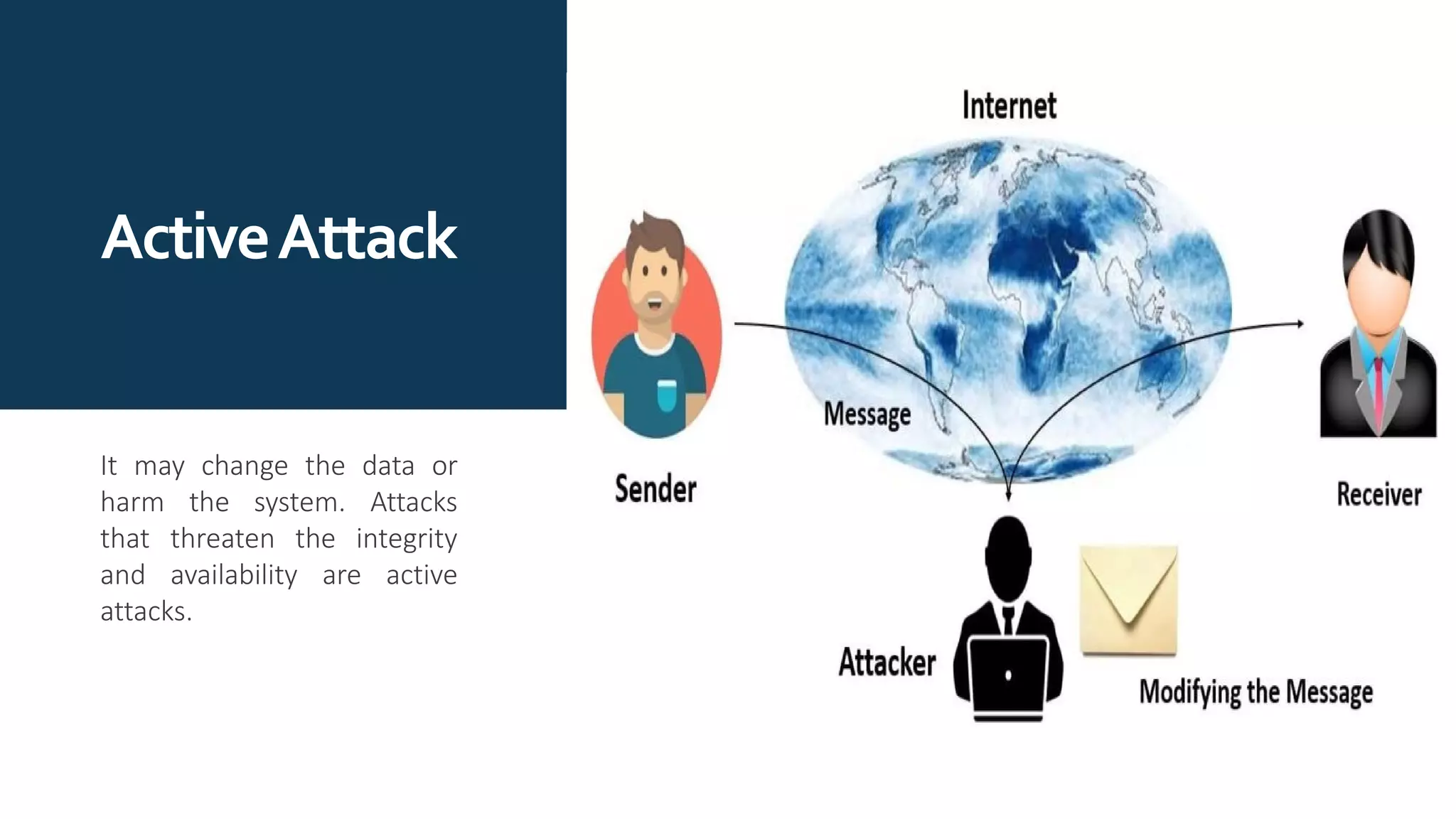
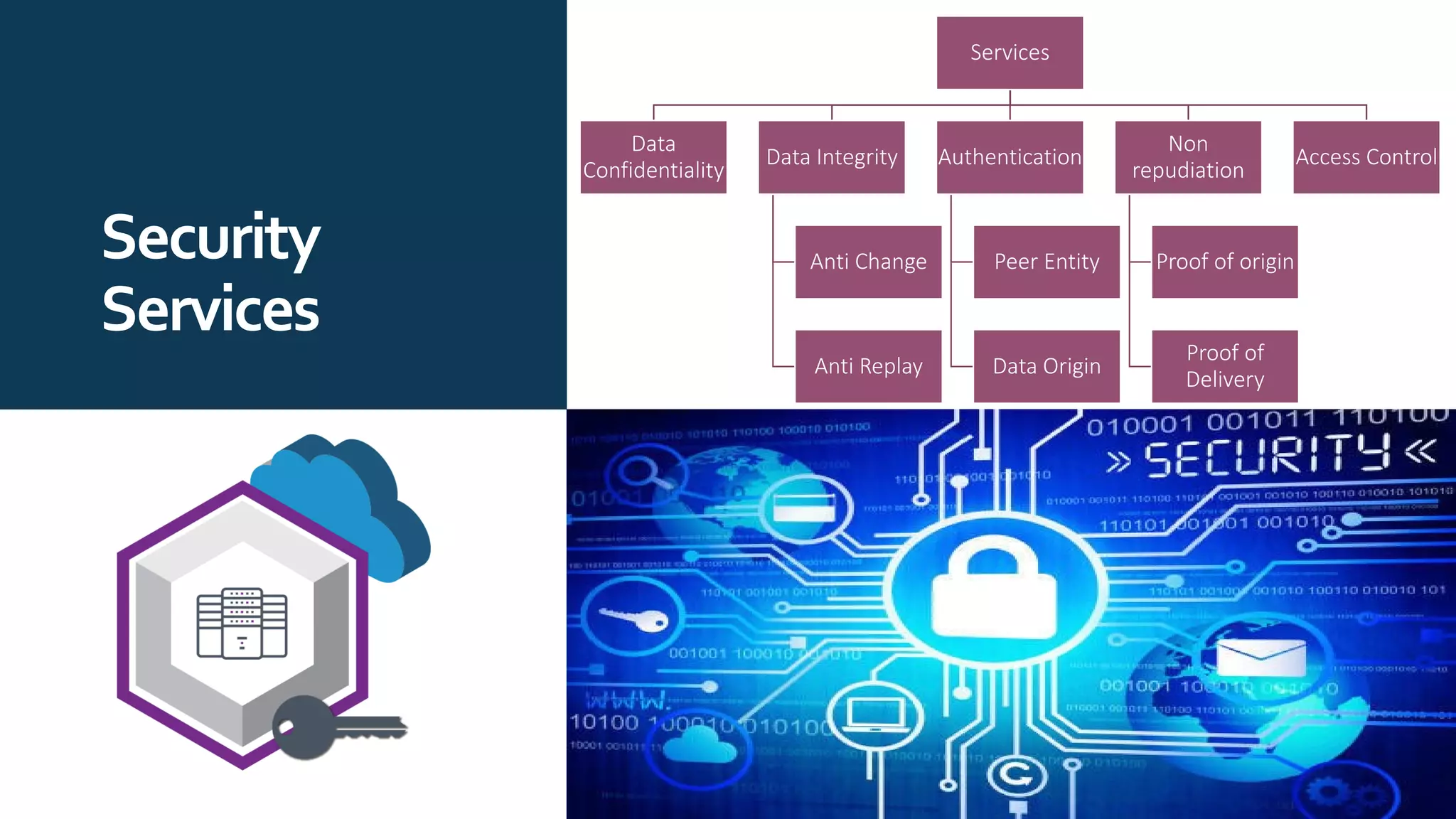
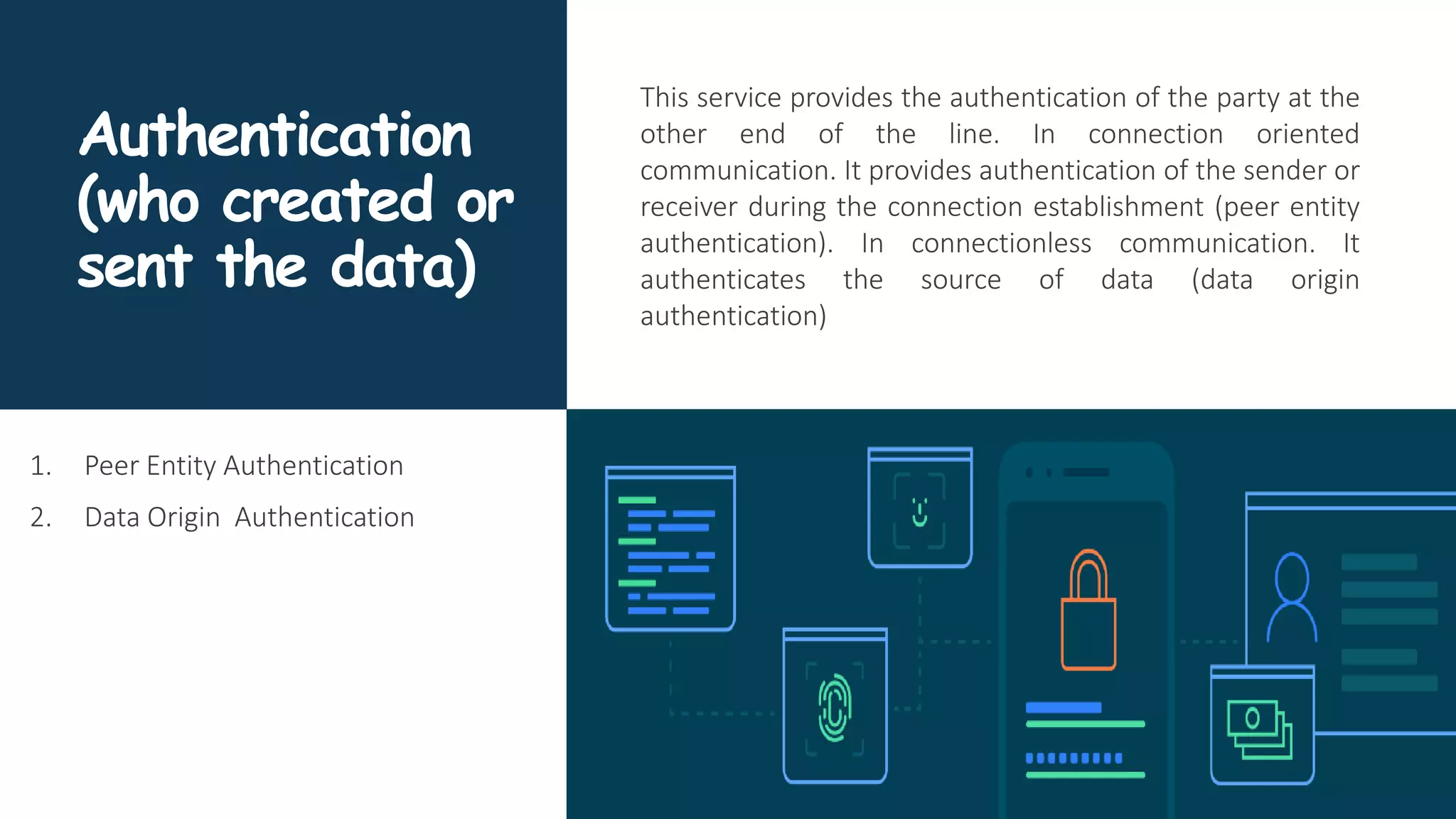
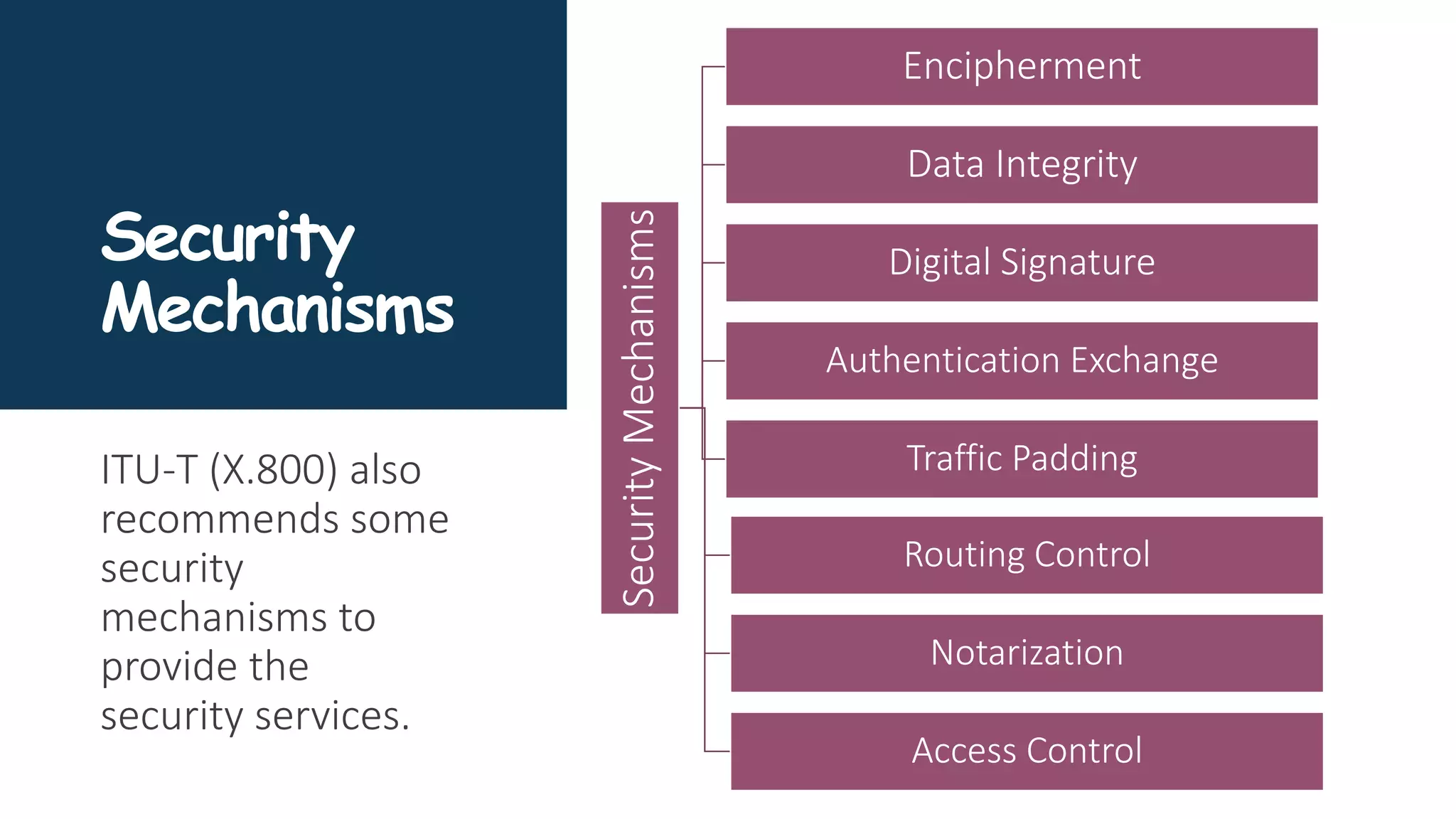
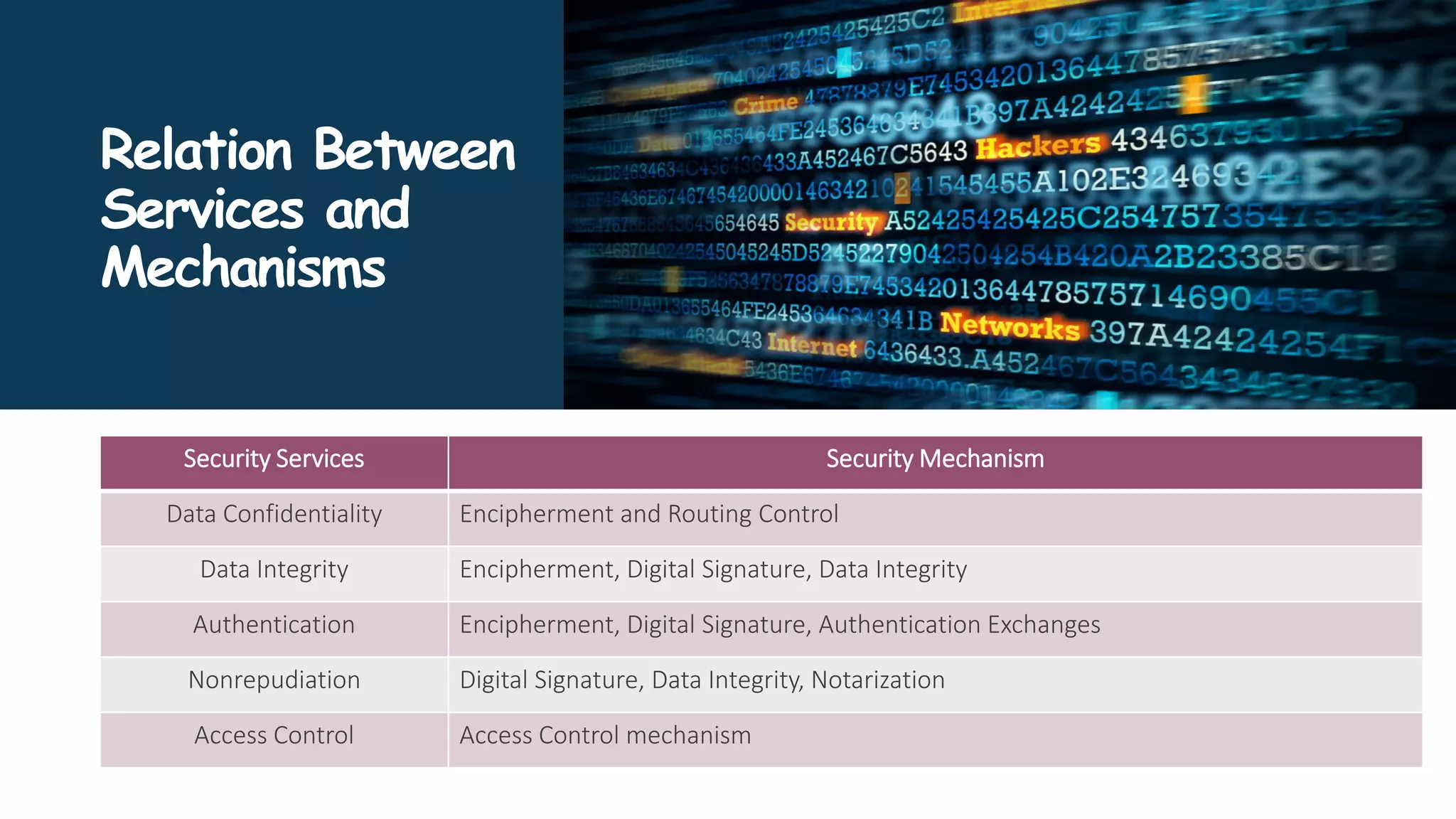
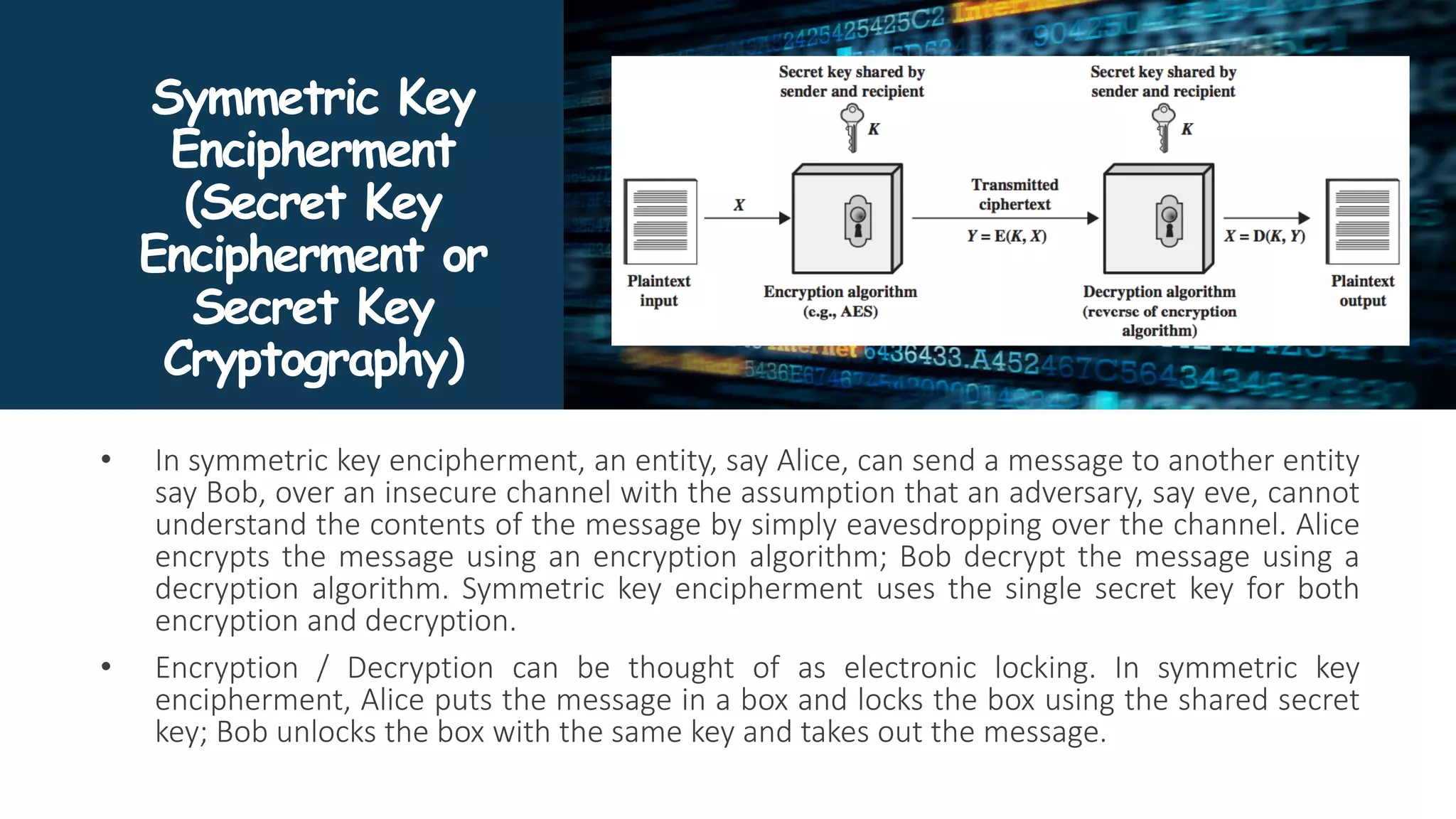
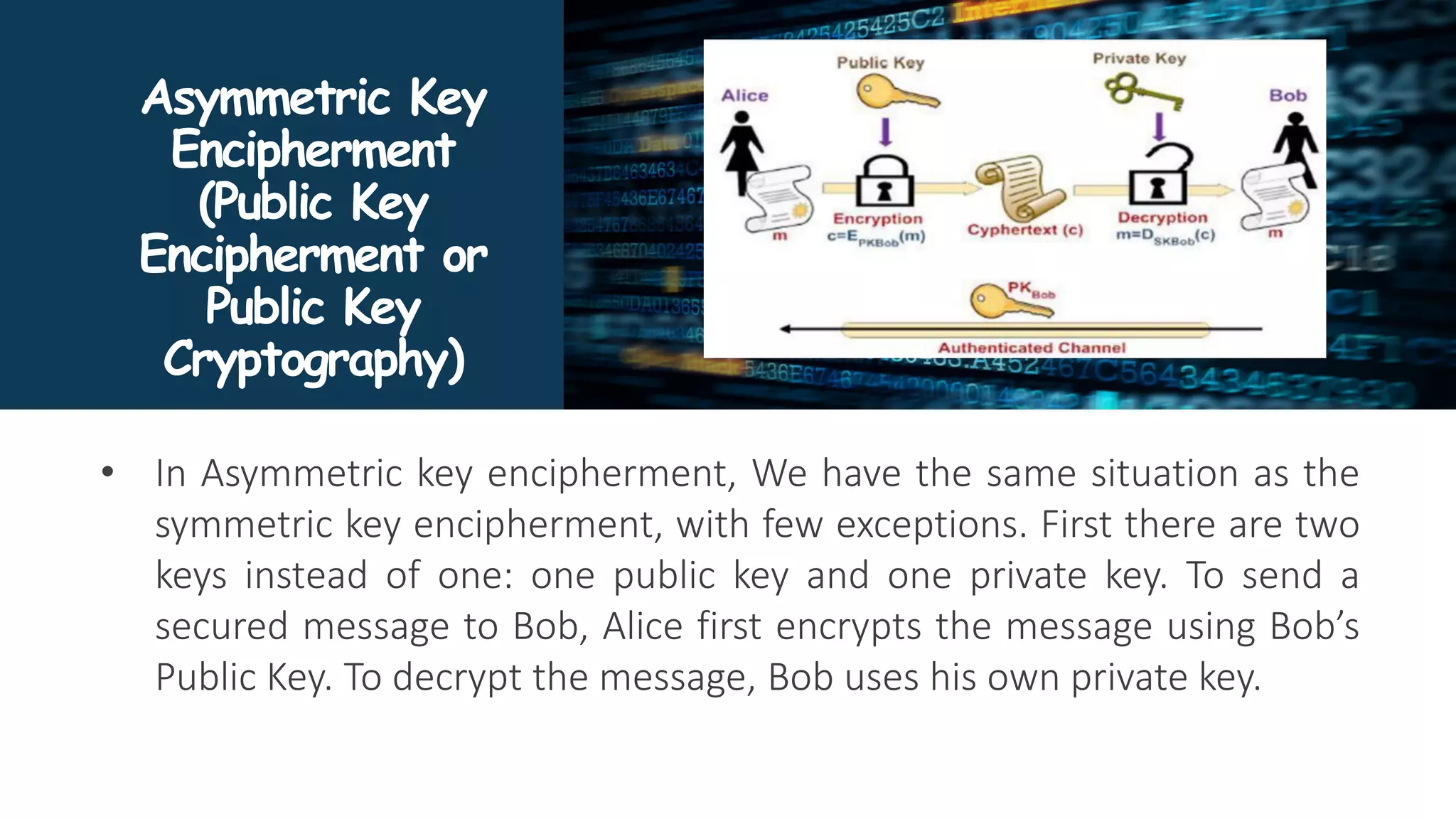
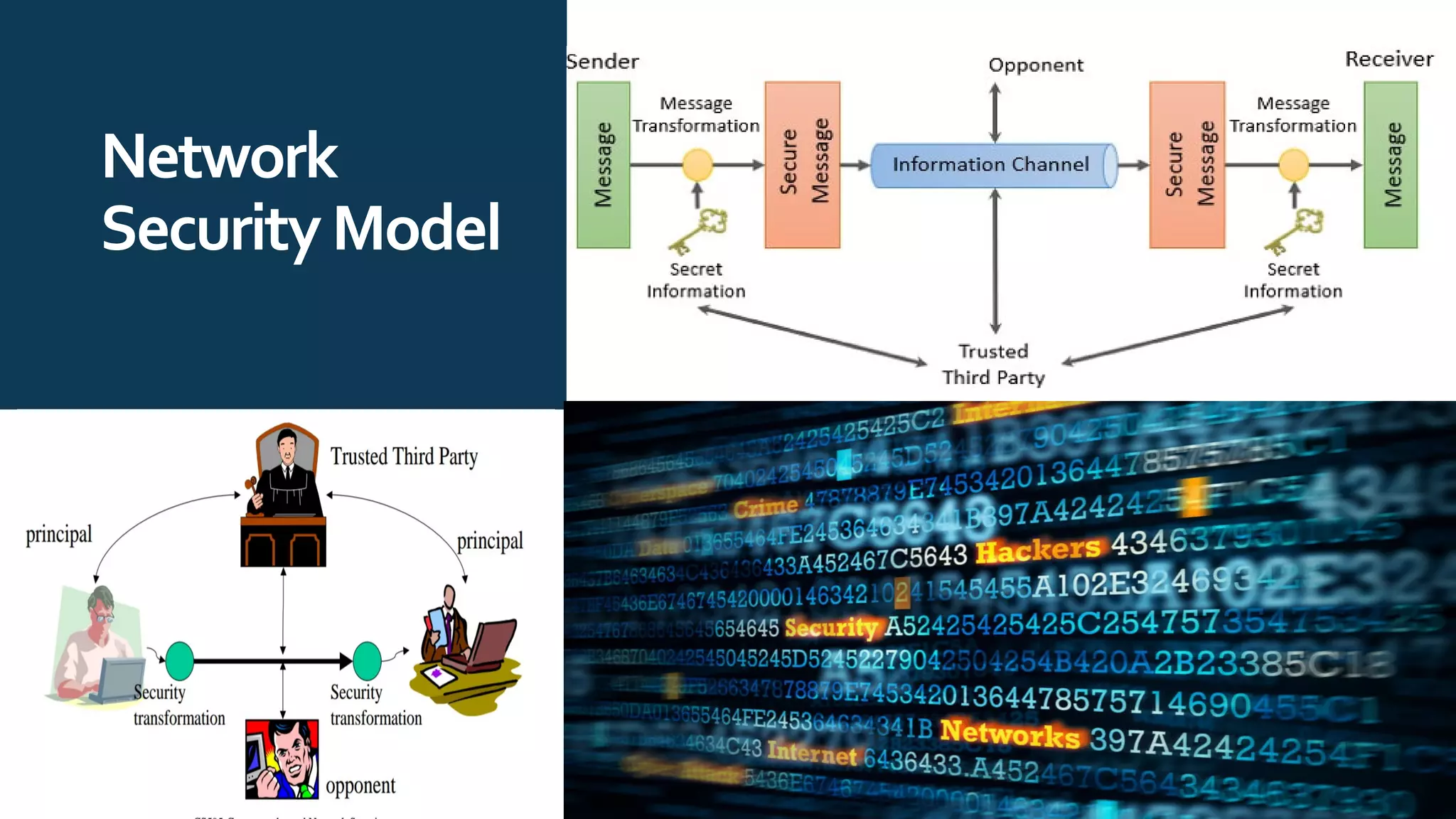
The document provides an overview of communication network security. It defines three security goals of confidentiality, integrity, and availability. It also defines security attacks like cryptanalytic attacks and non-cryptanalytic attacks that threaten the security goals. The document discusses security services like confidentiality, integrity, authentication, non-repudiation, and access control. It relates these services to security mechanisms like encipherment, digital signatures, and access control. Finally, it introduces cryptography and steganography techniques used to implement security mechanisms.