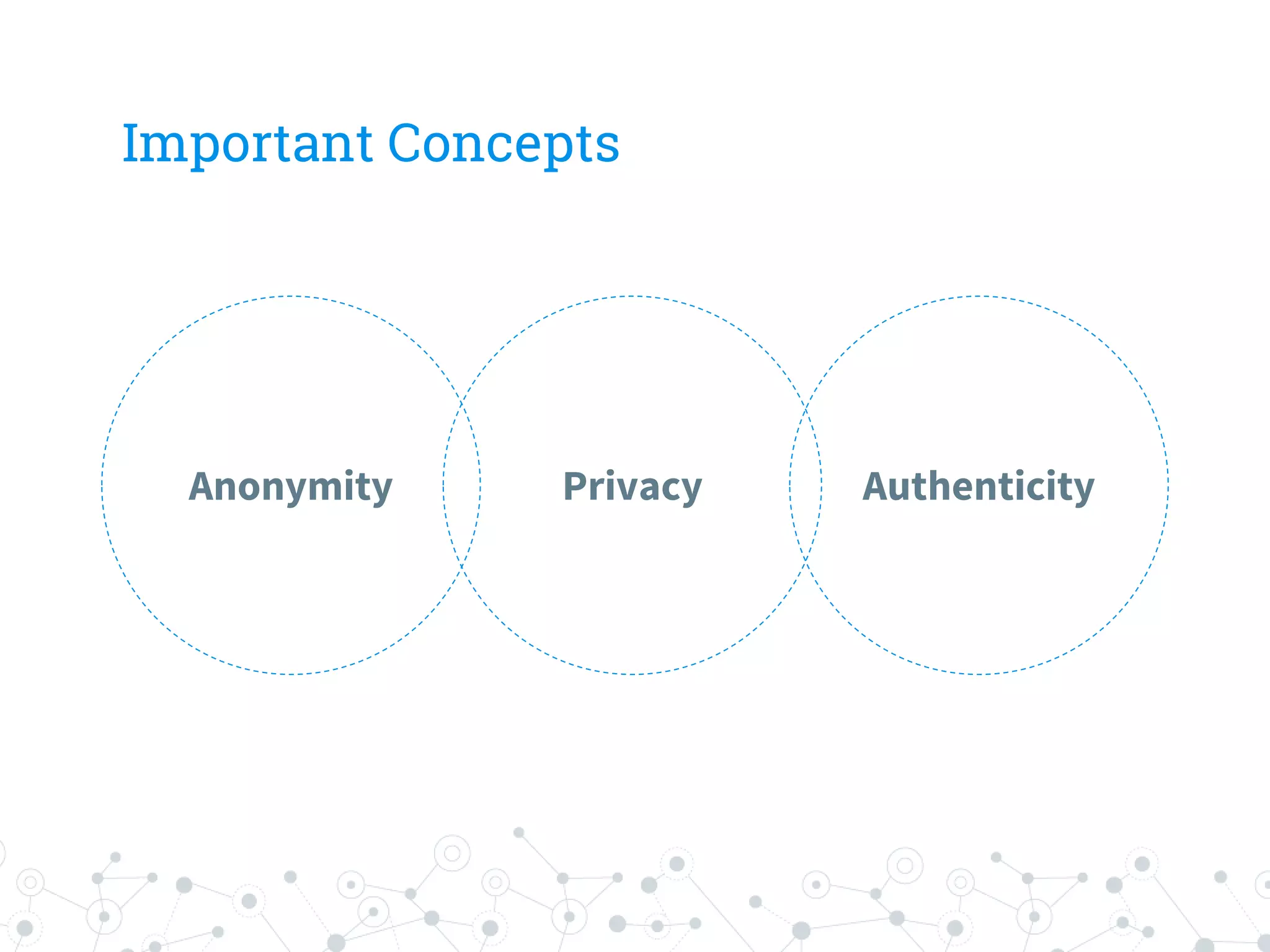
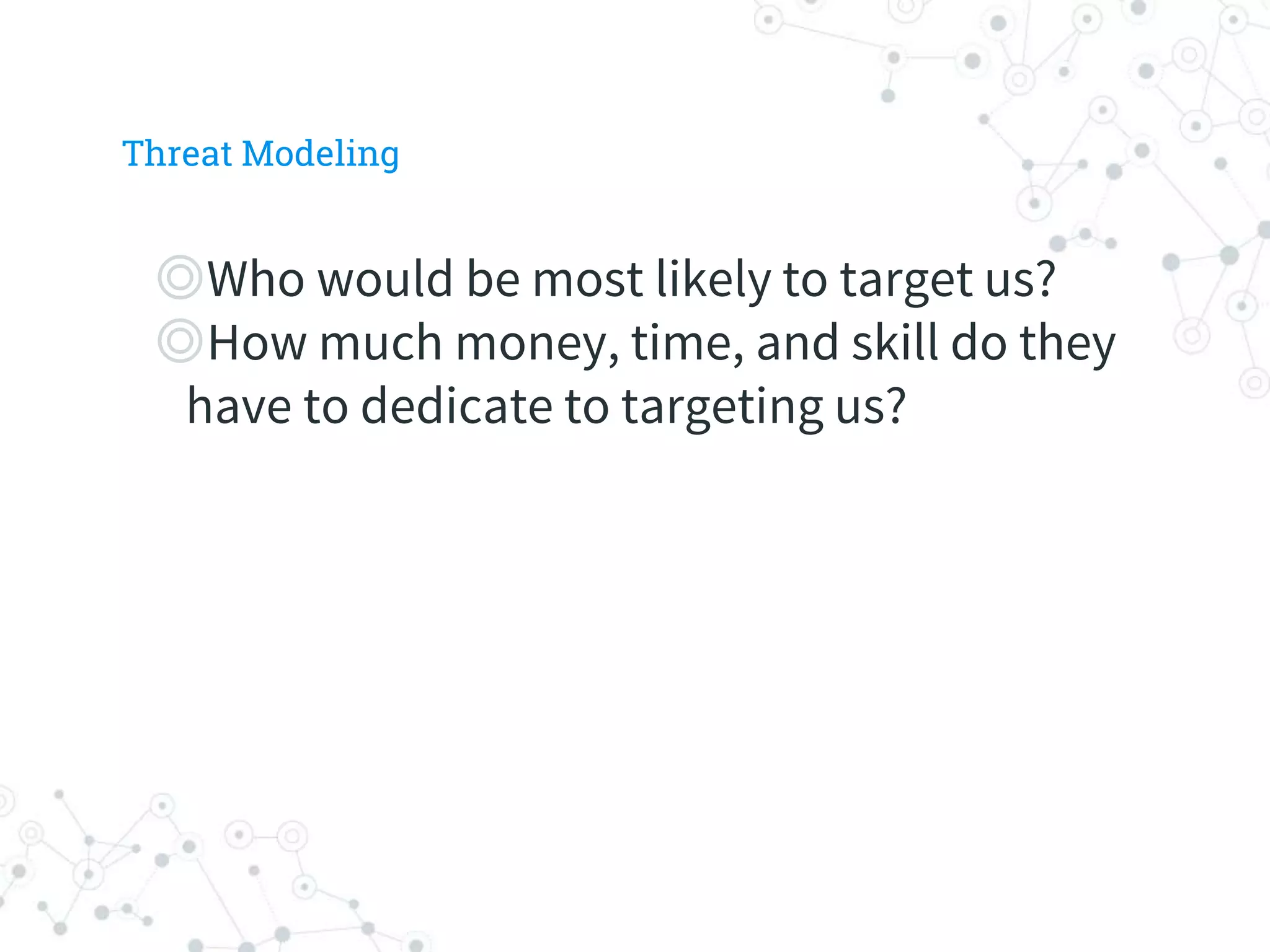
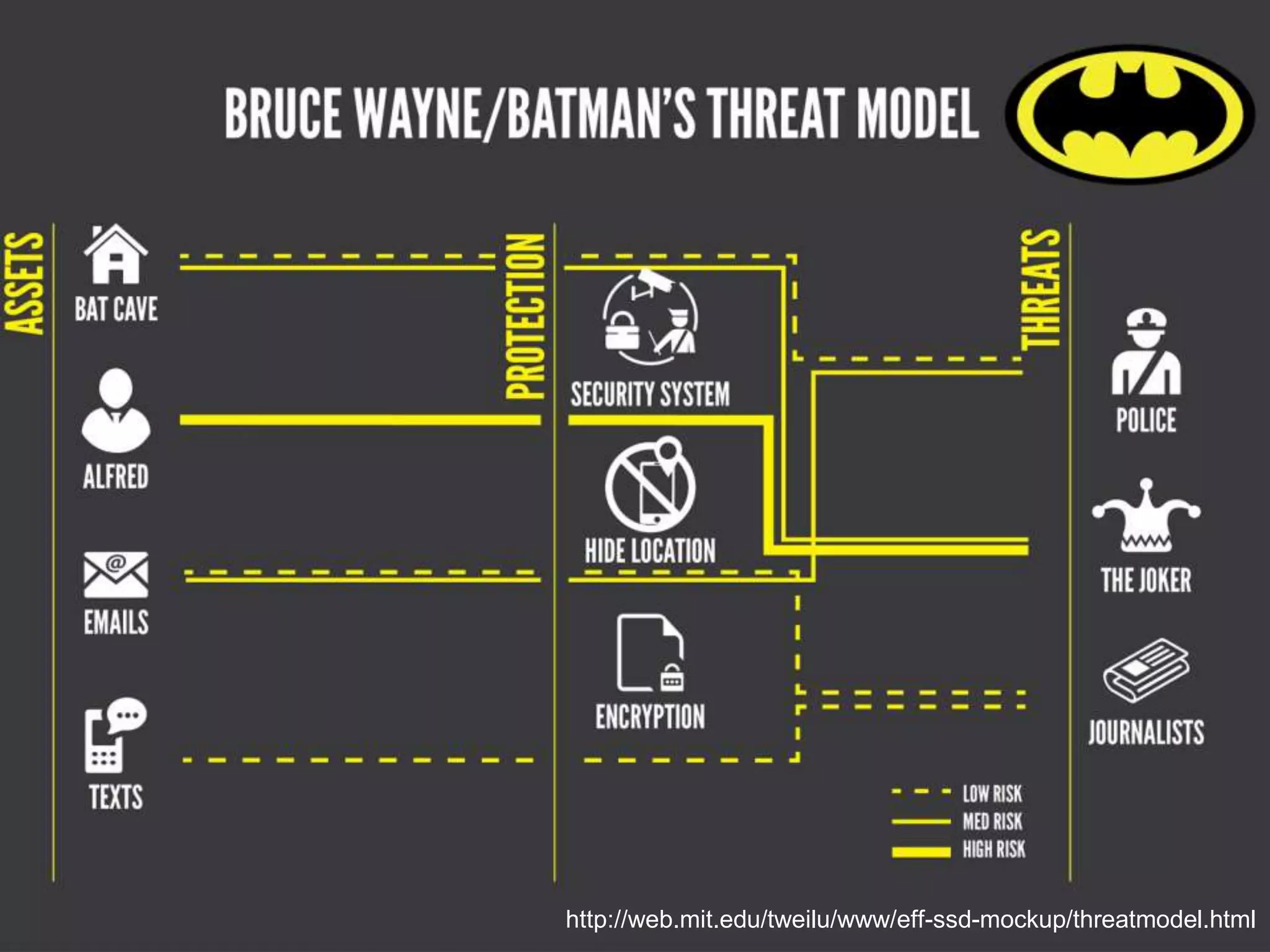
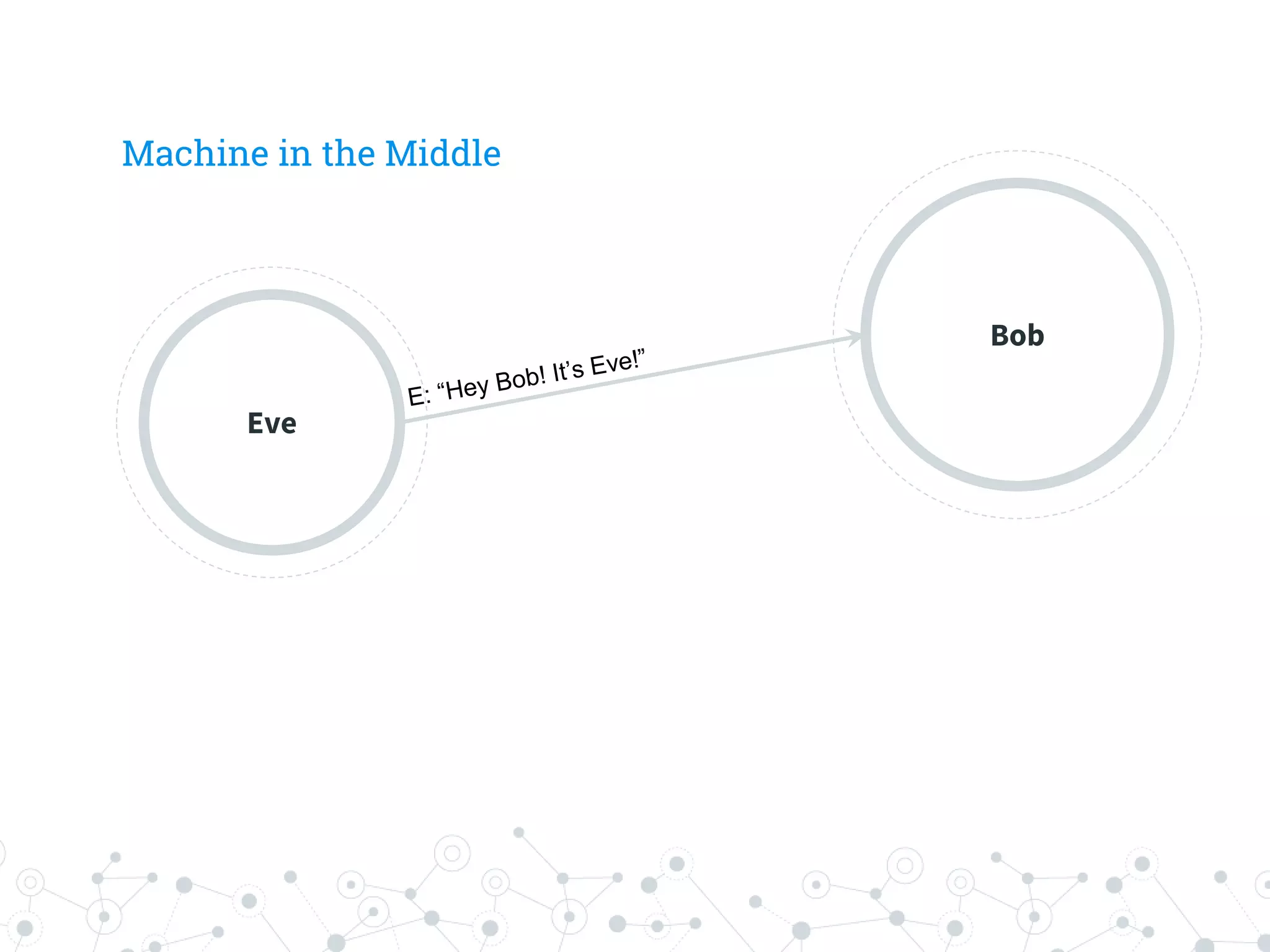
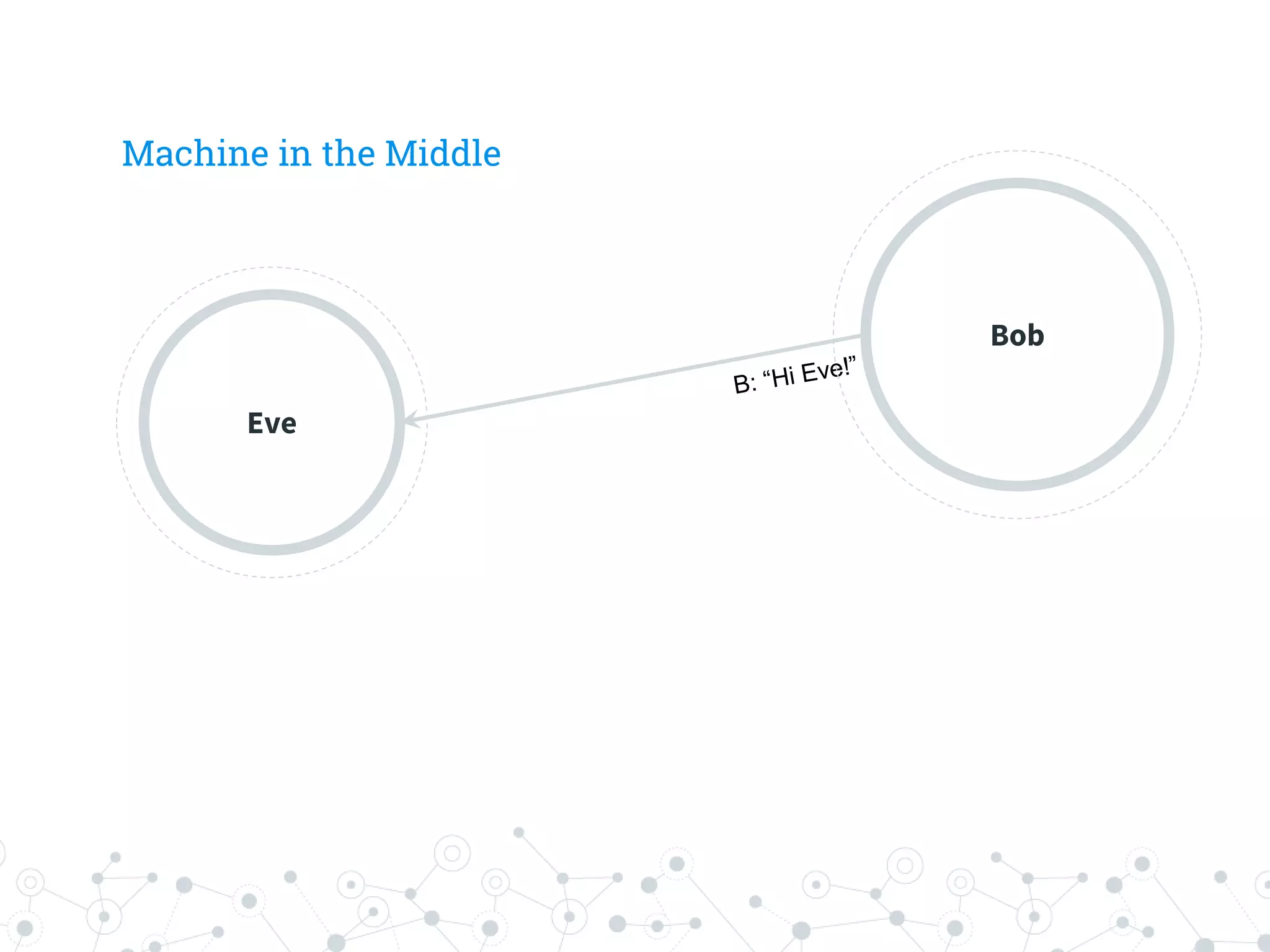
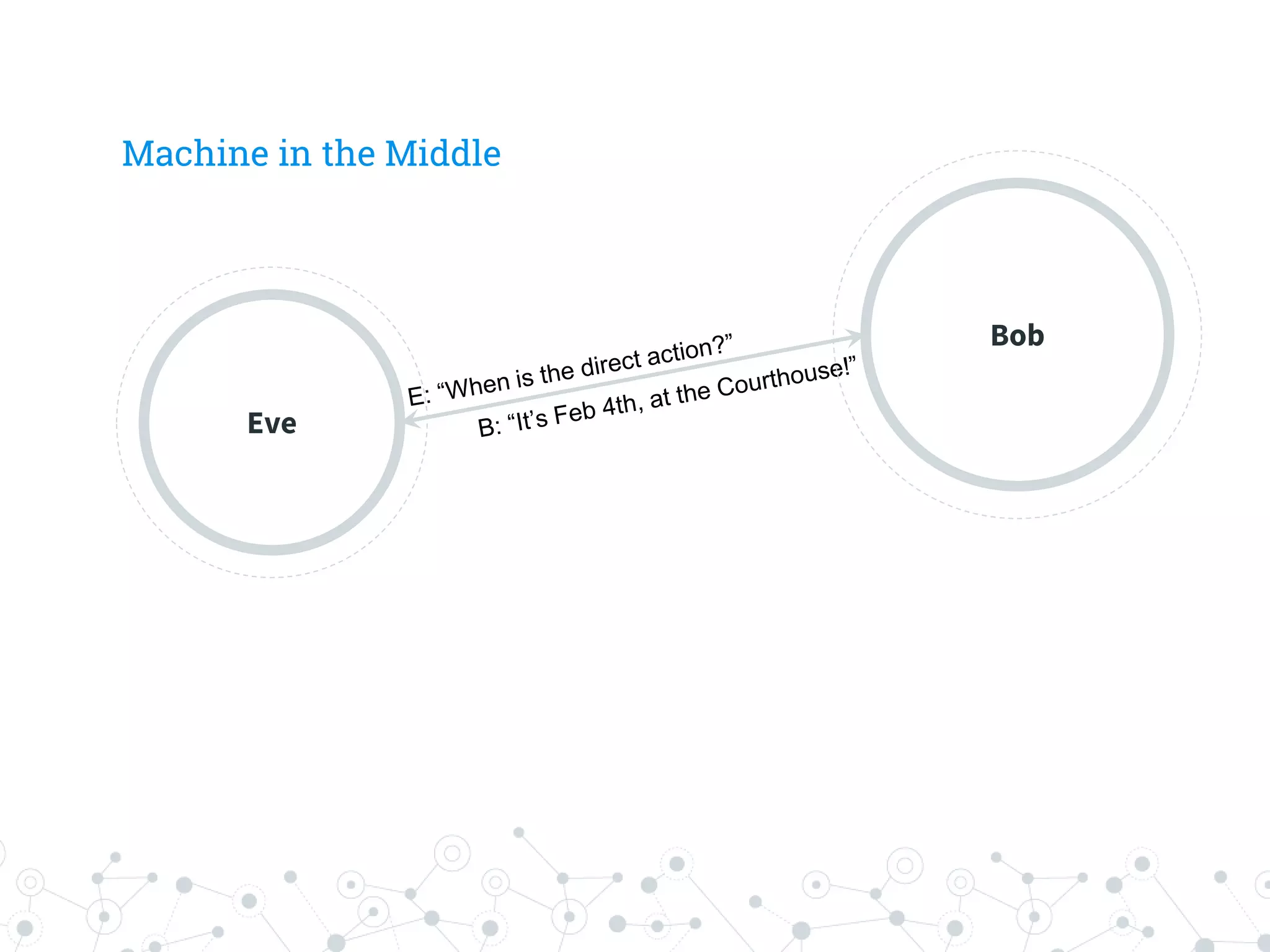
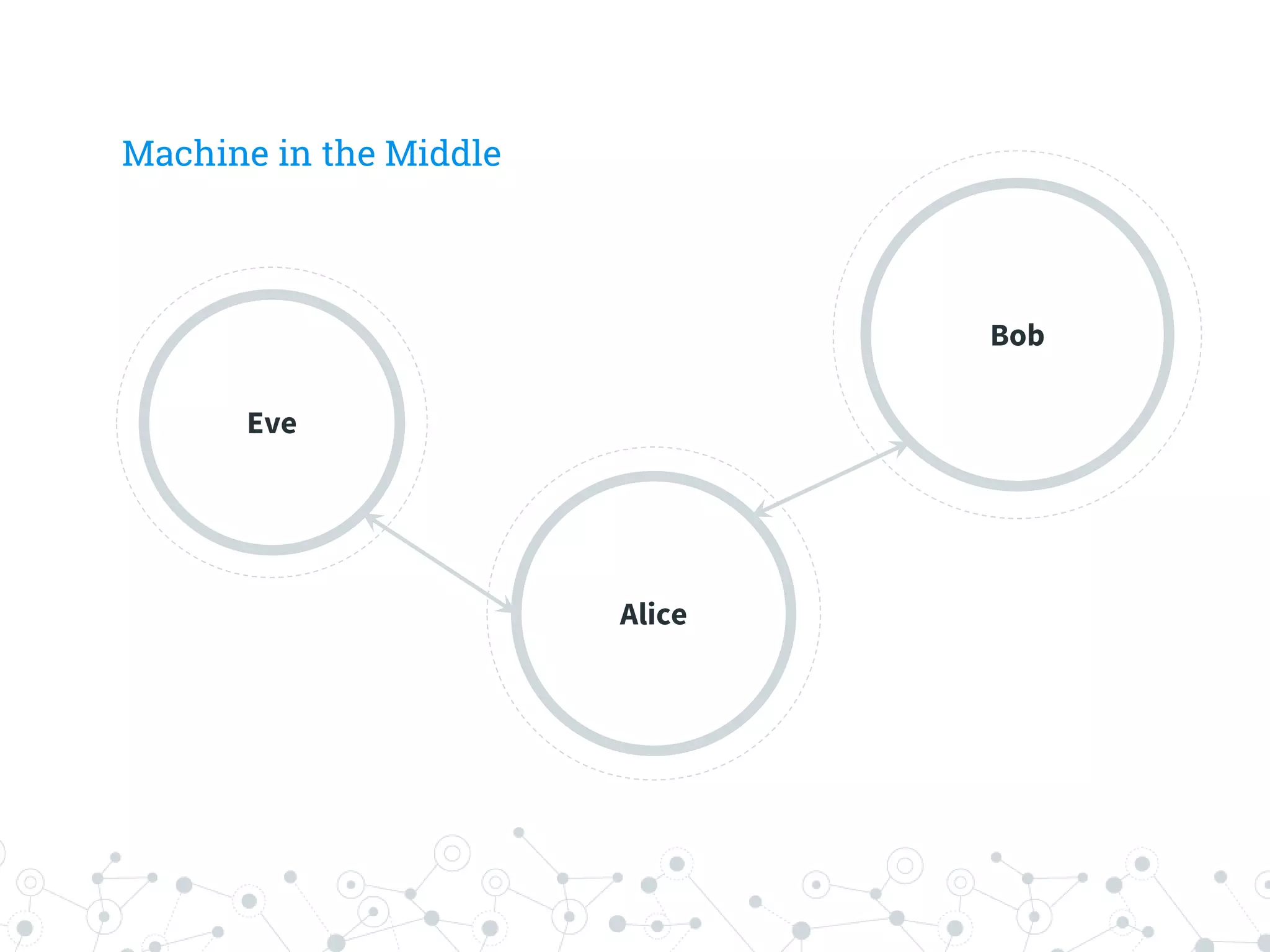
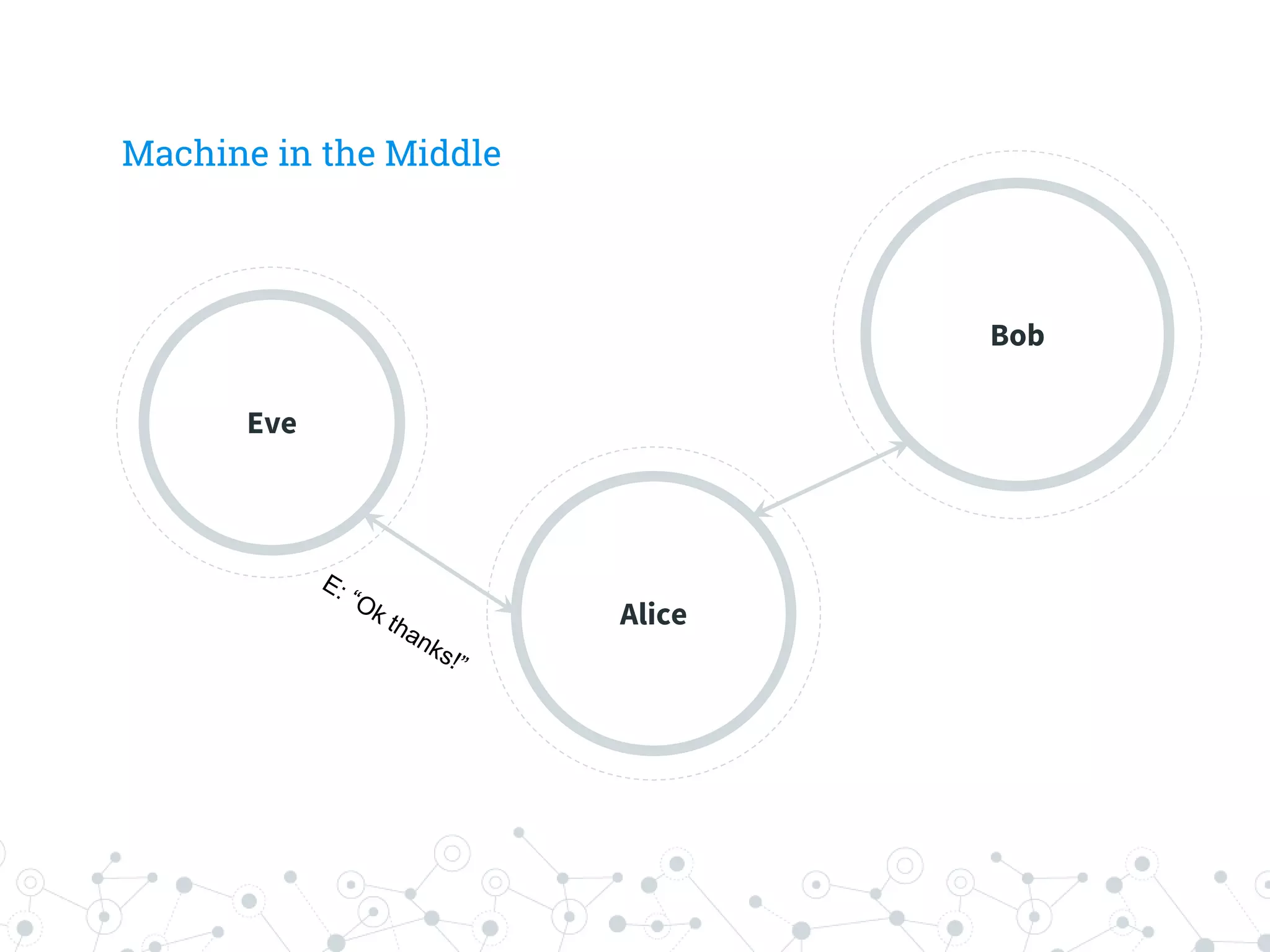
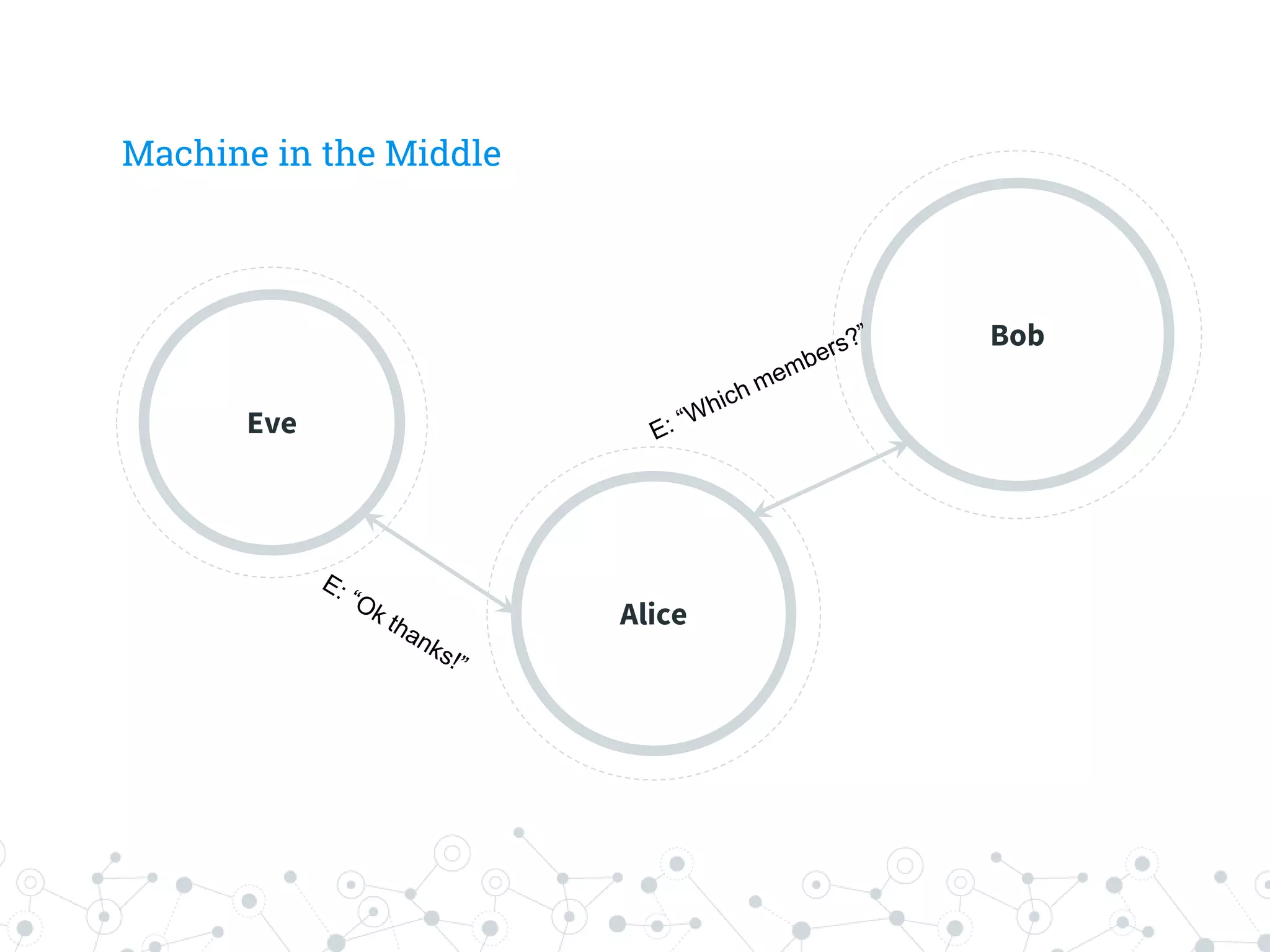
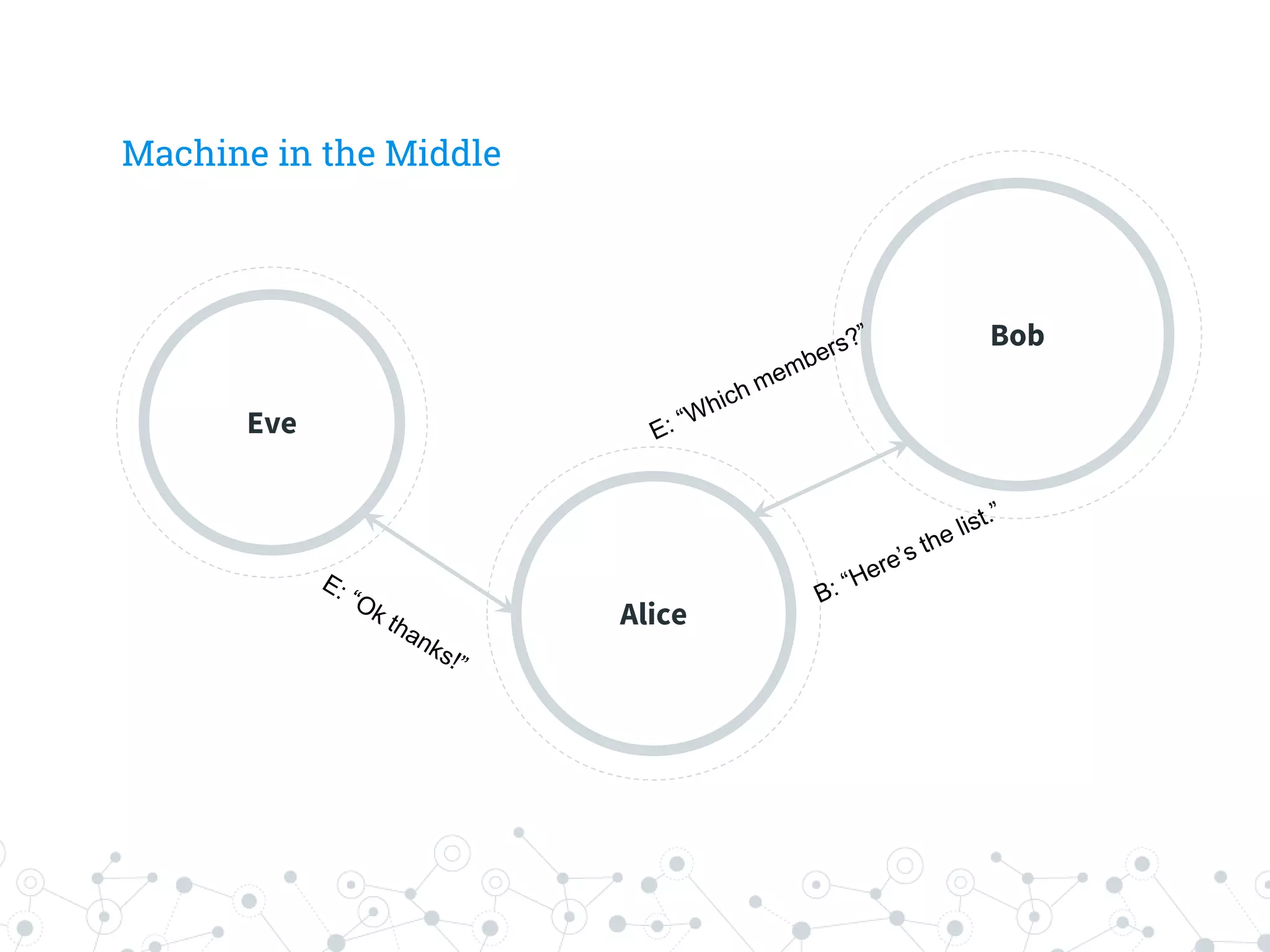
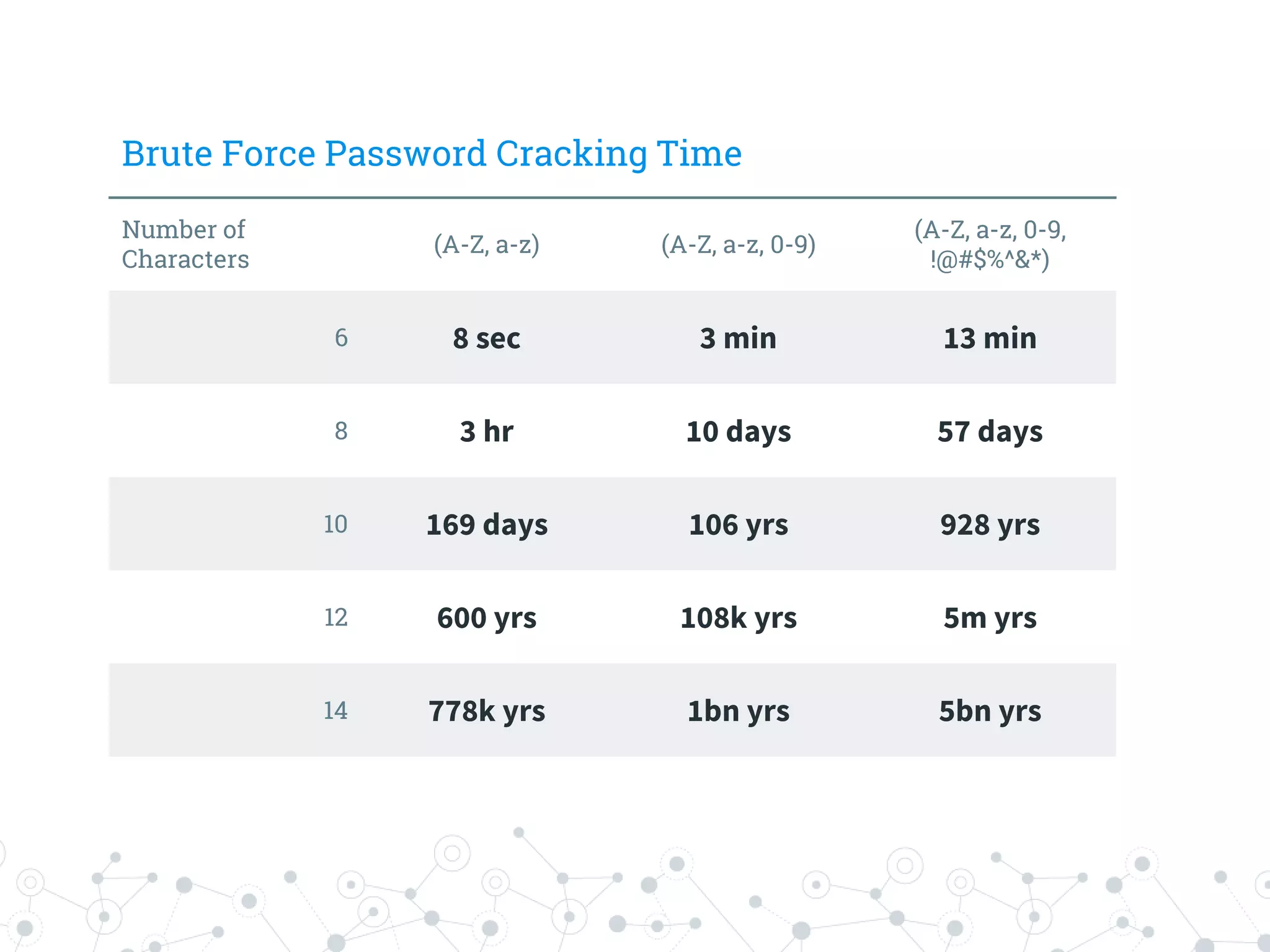
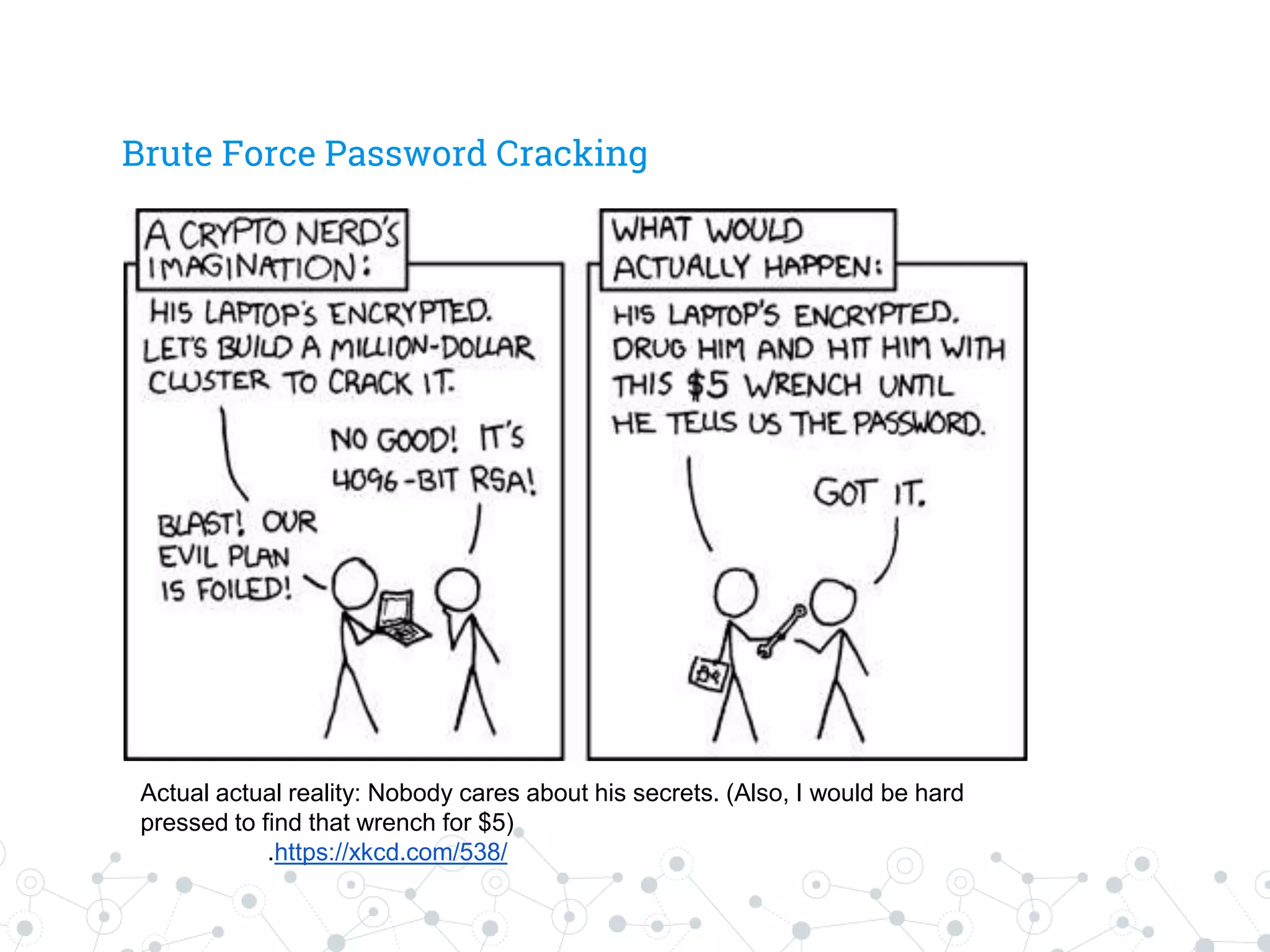
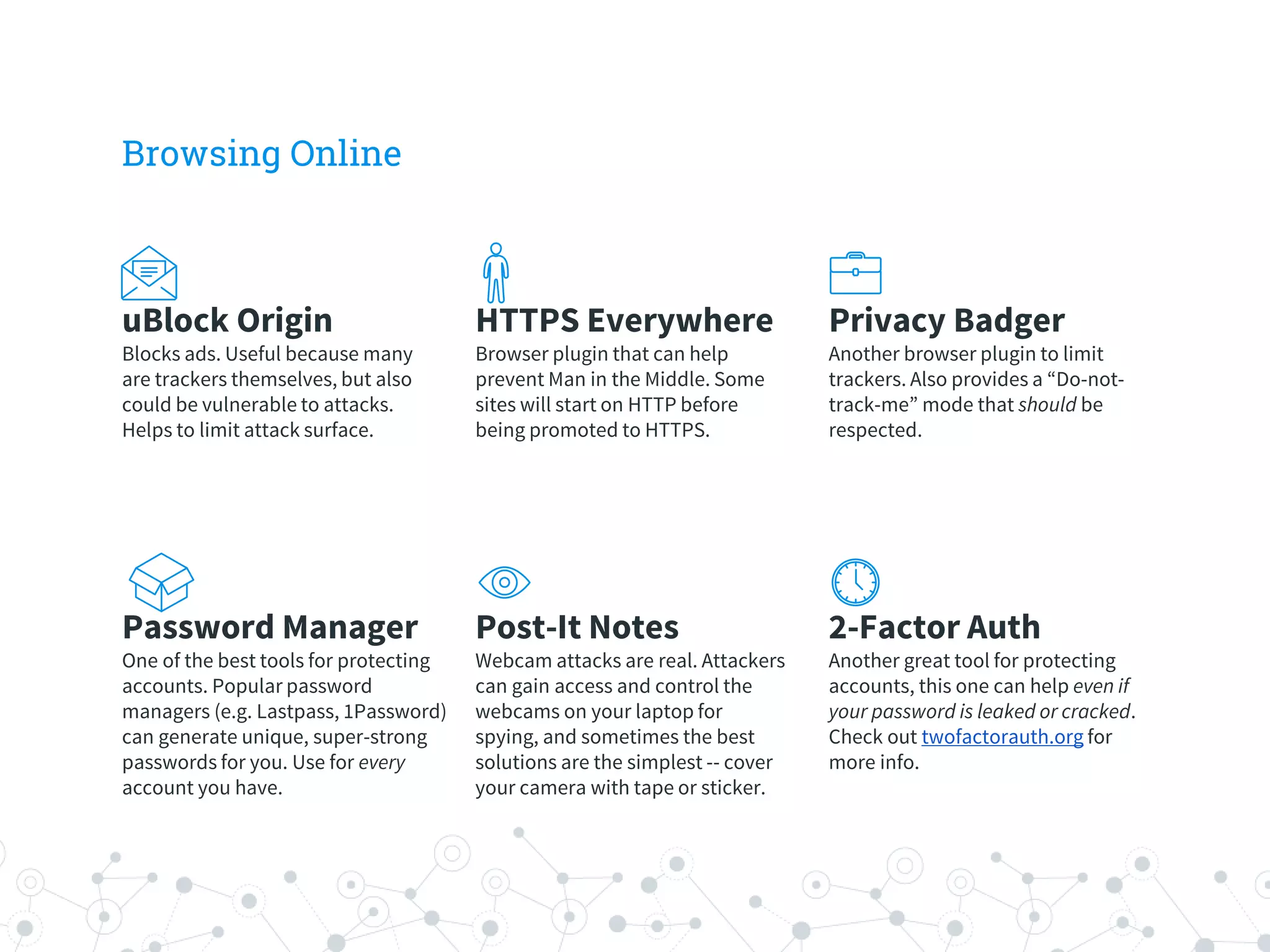
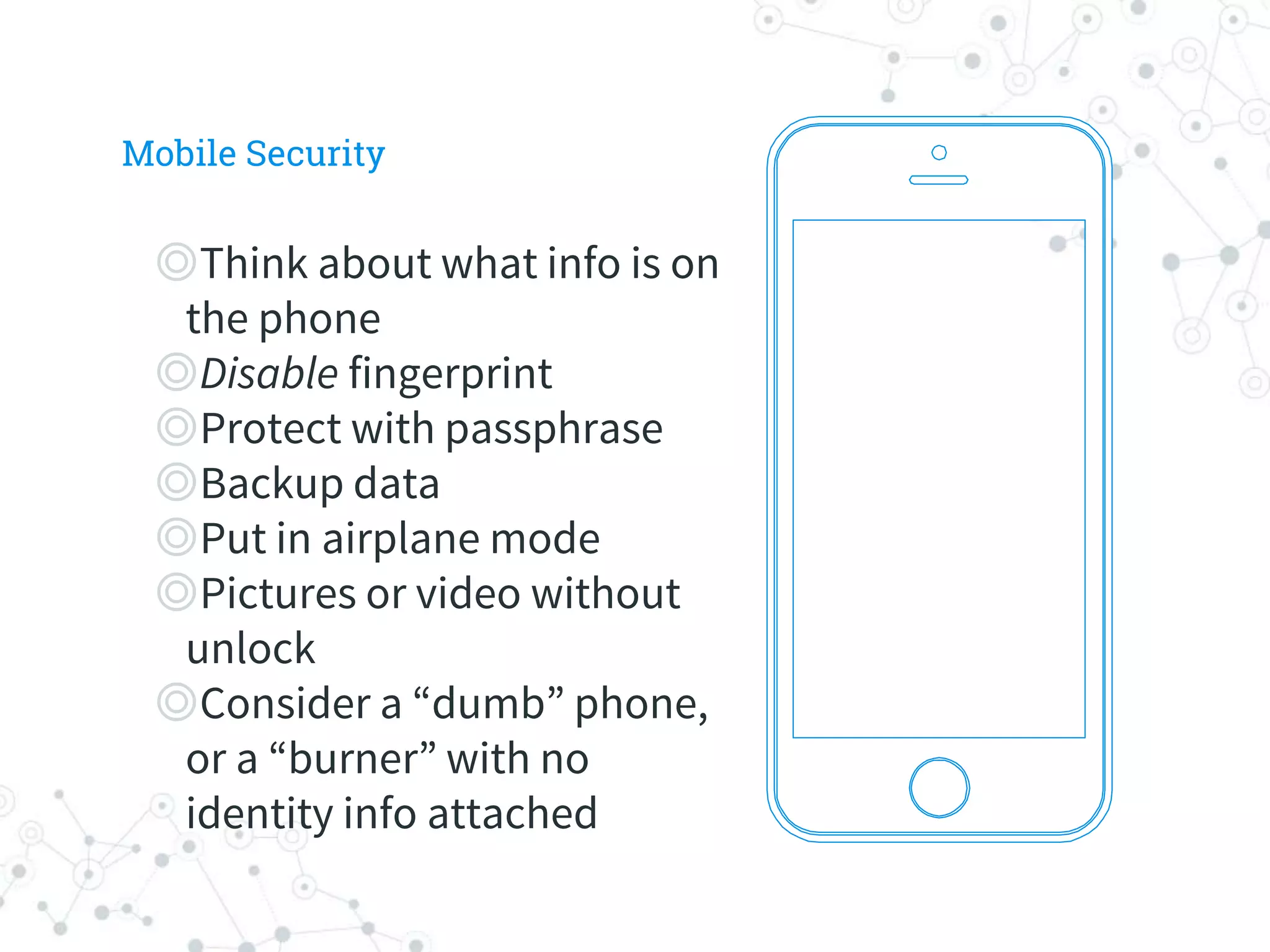
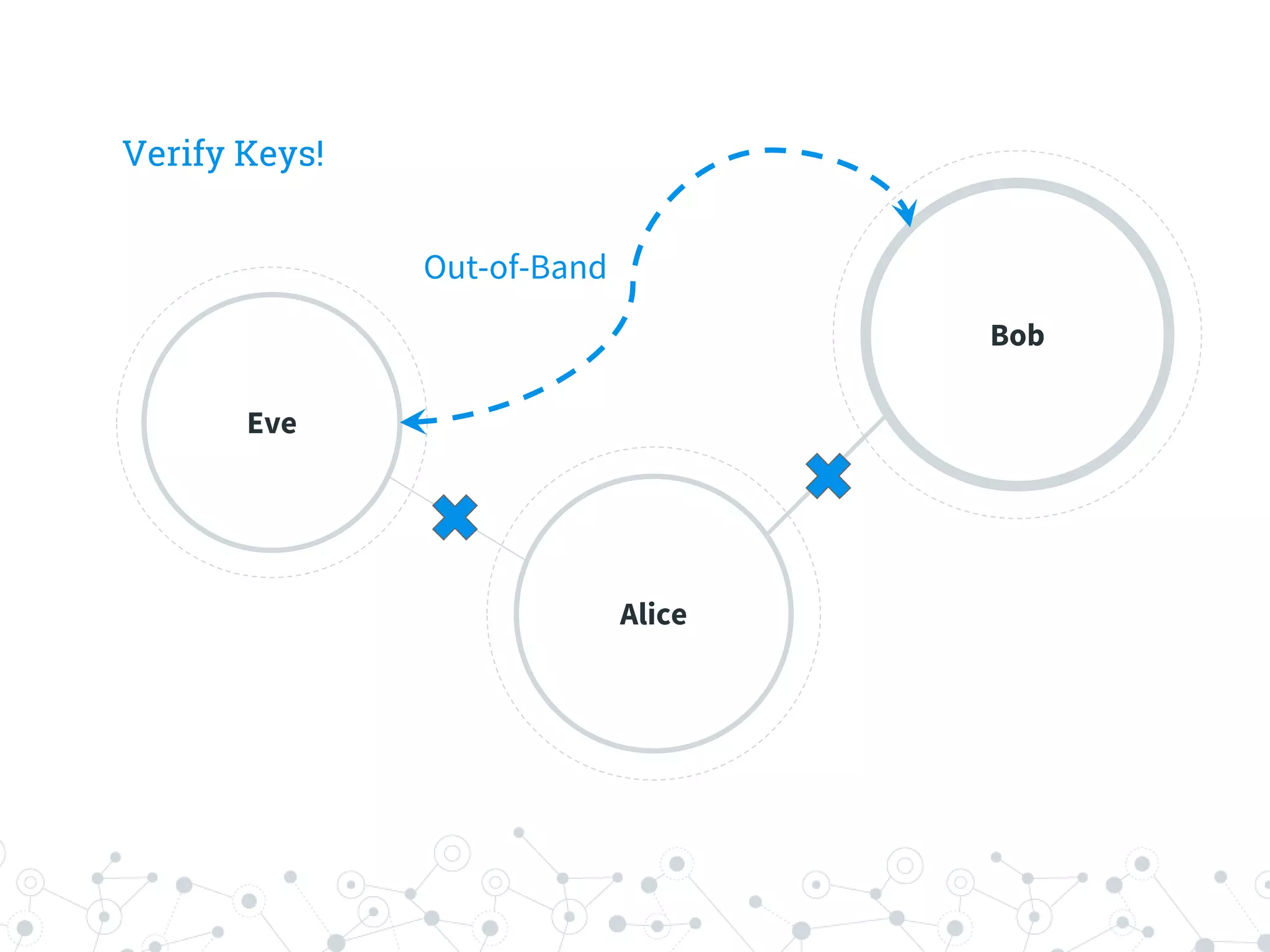
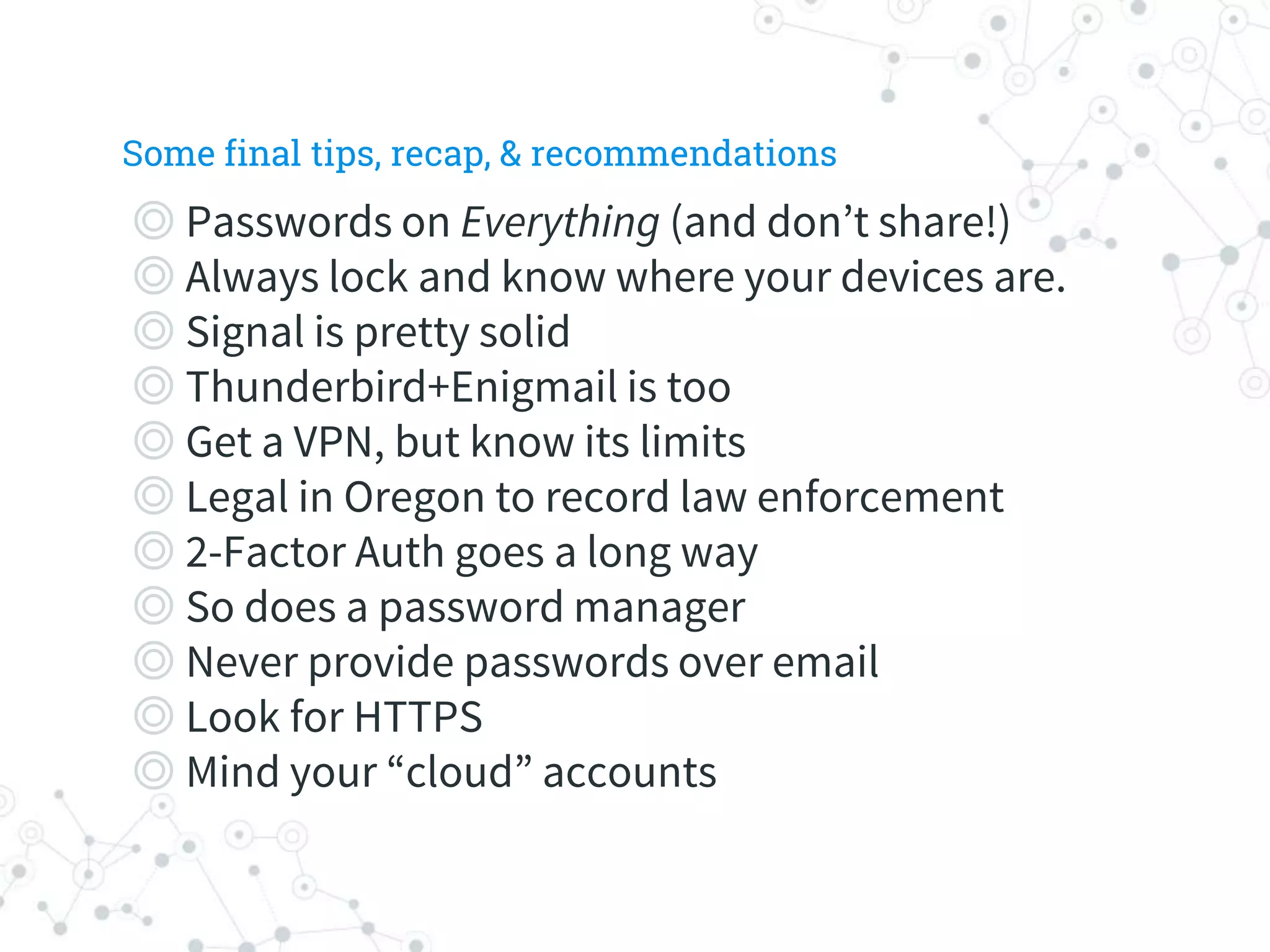
The document is a workshop guide focused on data privacy for activists, outlining the importance of privacy, key concepts, and practical tools for safeguarding personal information. It includes topics such as encryption, common attack vectors, threat modeling, and recommended technologies like password managers and VPNs. The workshop emphasizes the need for secure habits and awareness of digital security risks when organizing activist activities.