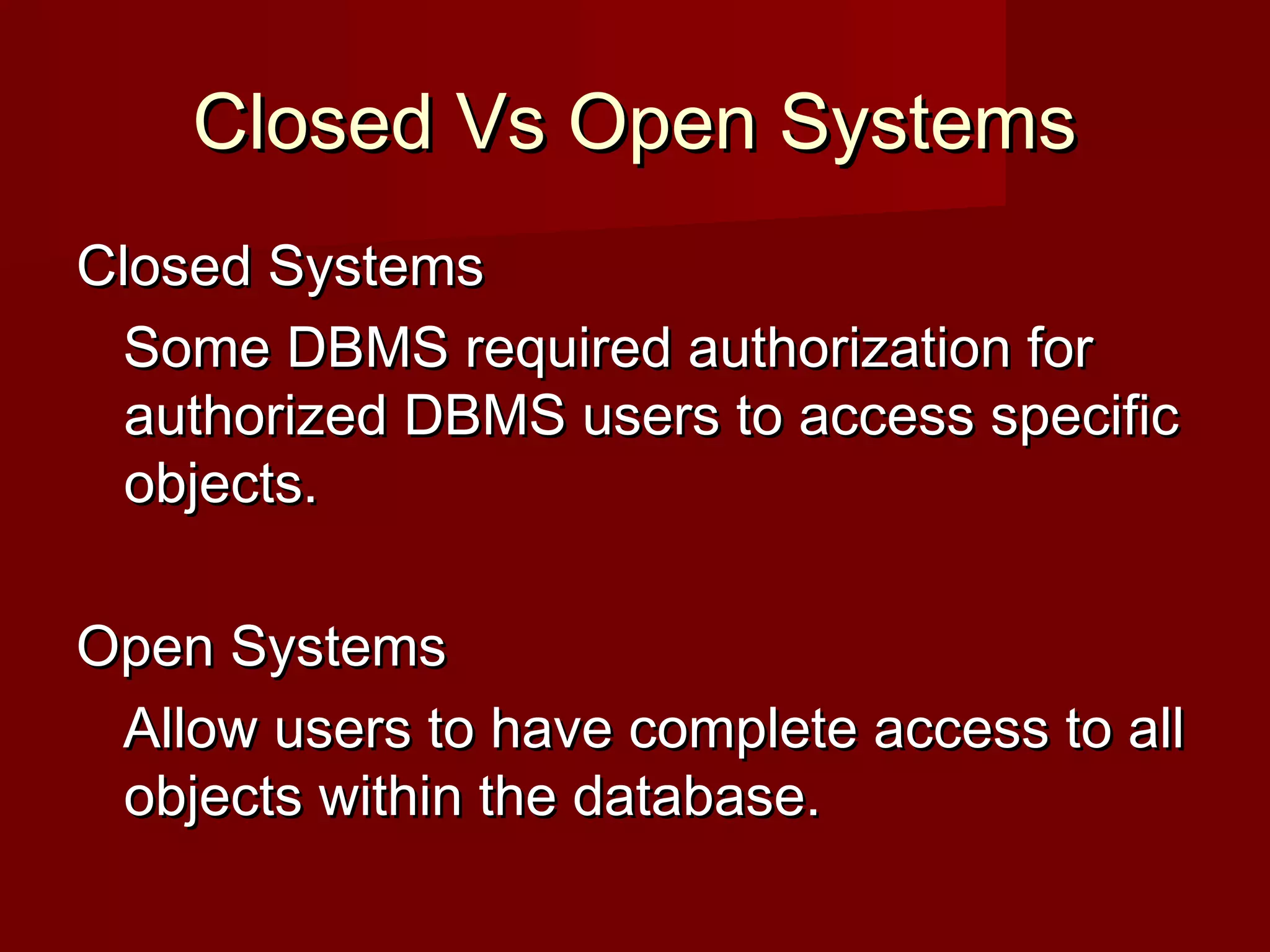
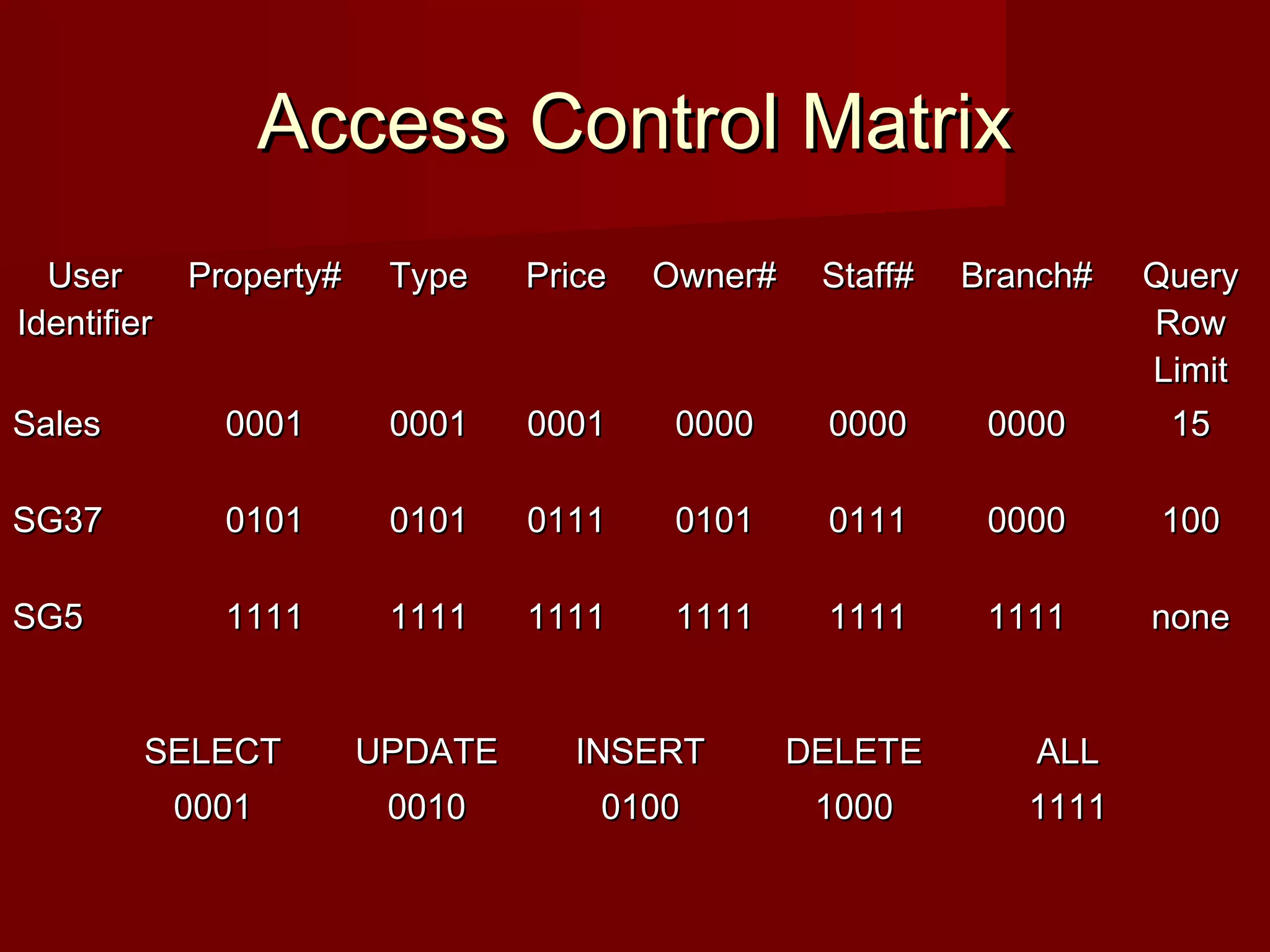
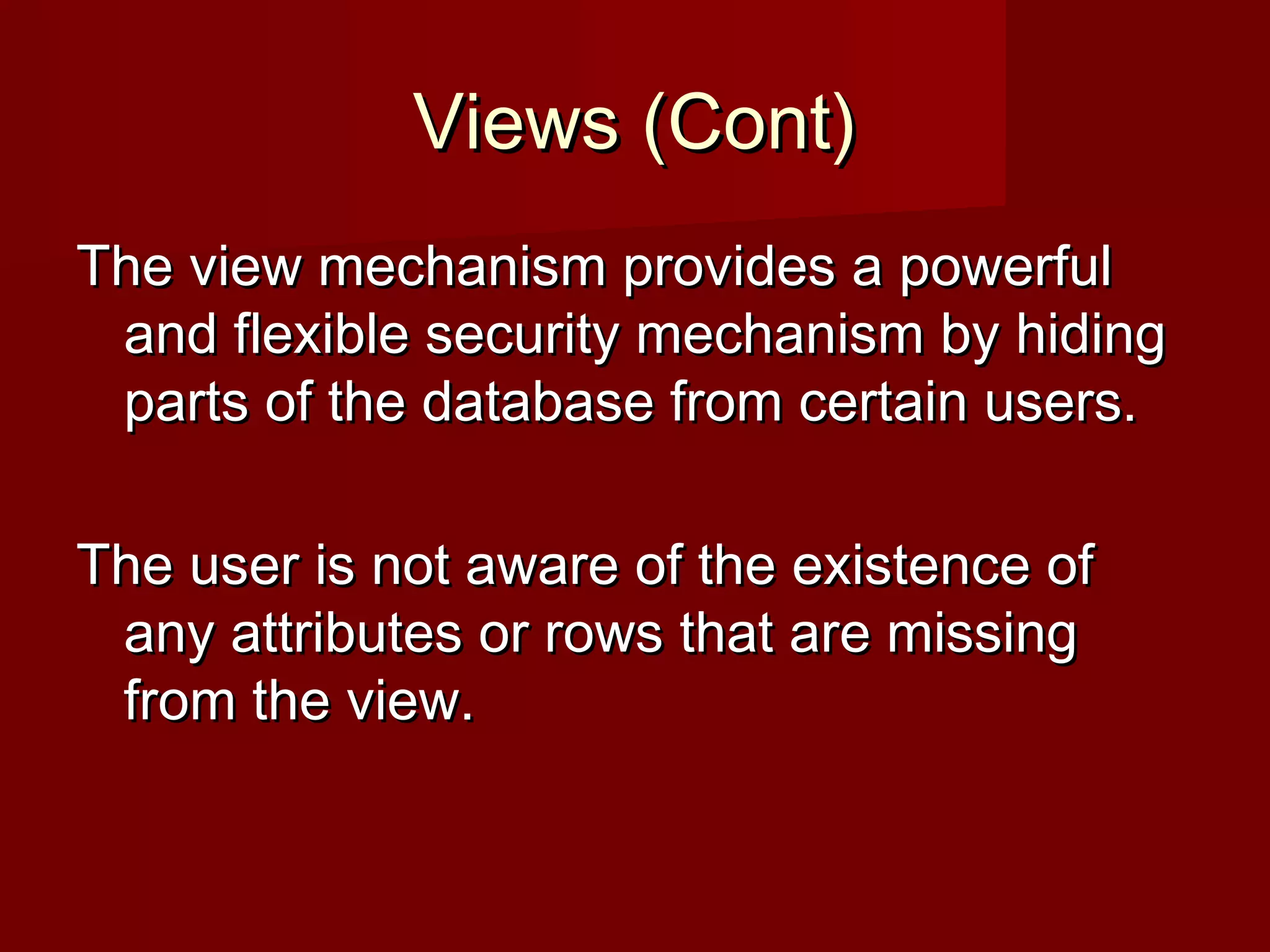
The document discusses database security and the mechanisms used to protect databases from intentional and accidental threats. It describes various threats like theft, fraud, and loss of confidentiality, privacy, integrity, or availability. Some countermeasures discussed include authorization, views, backups, encryption, and RAID technology to improve reliability and performance while protecting data.