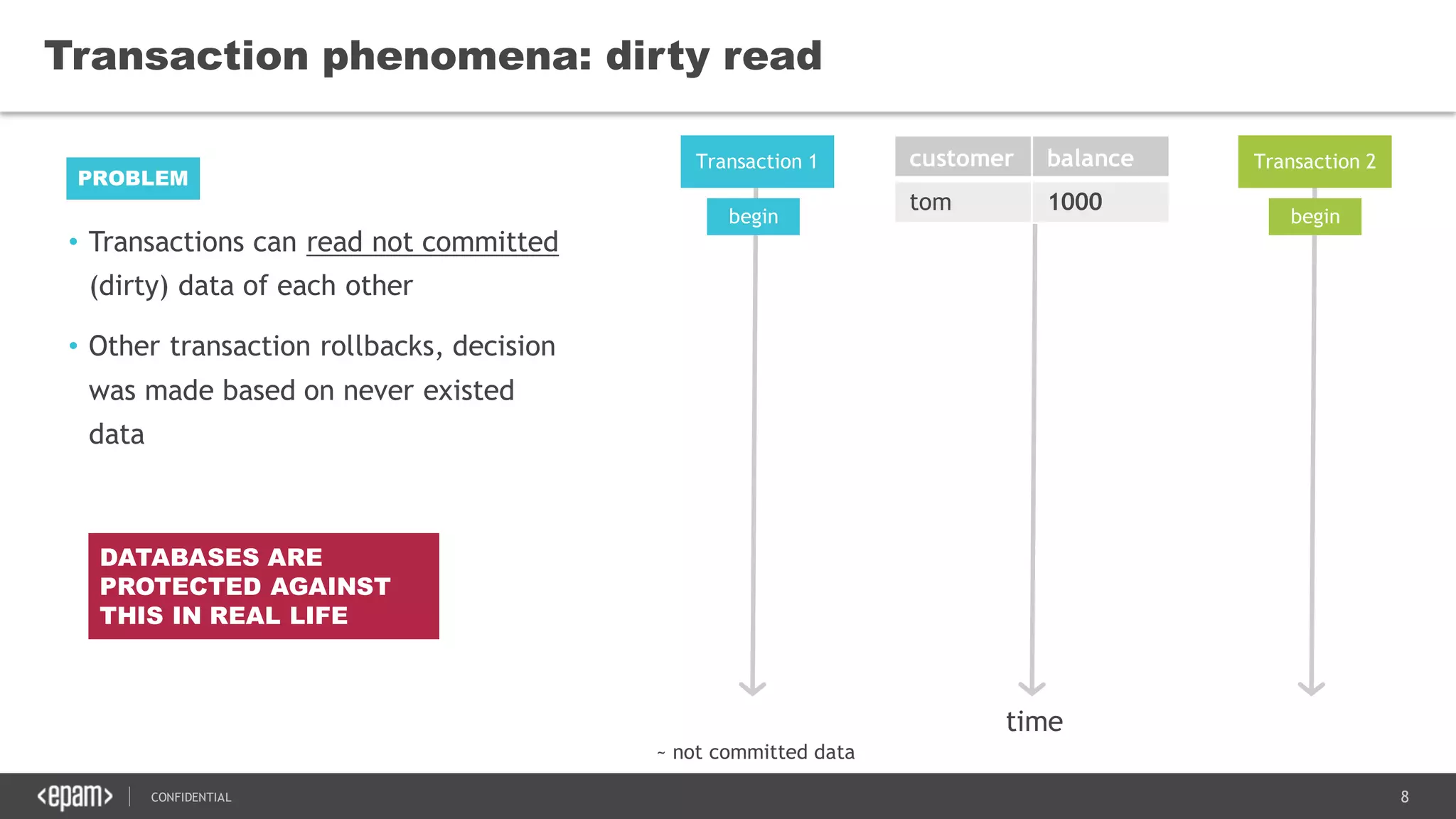
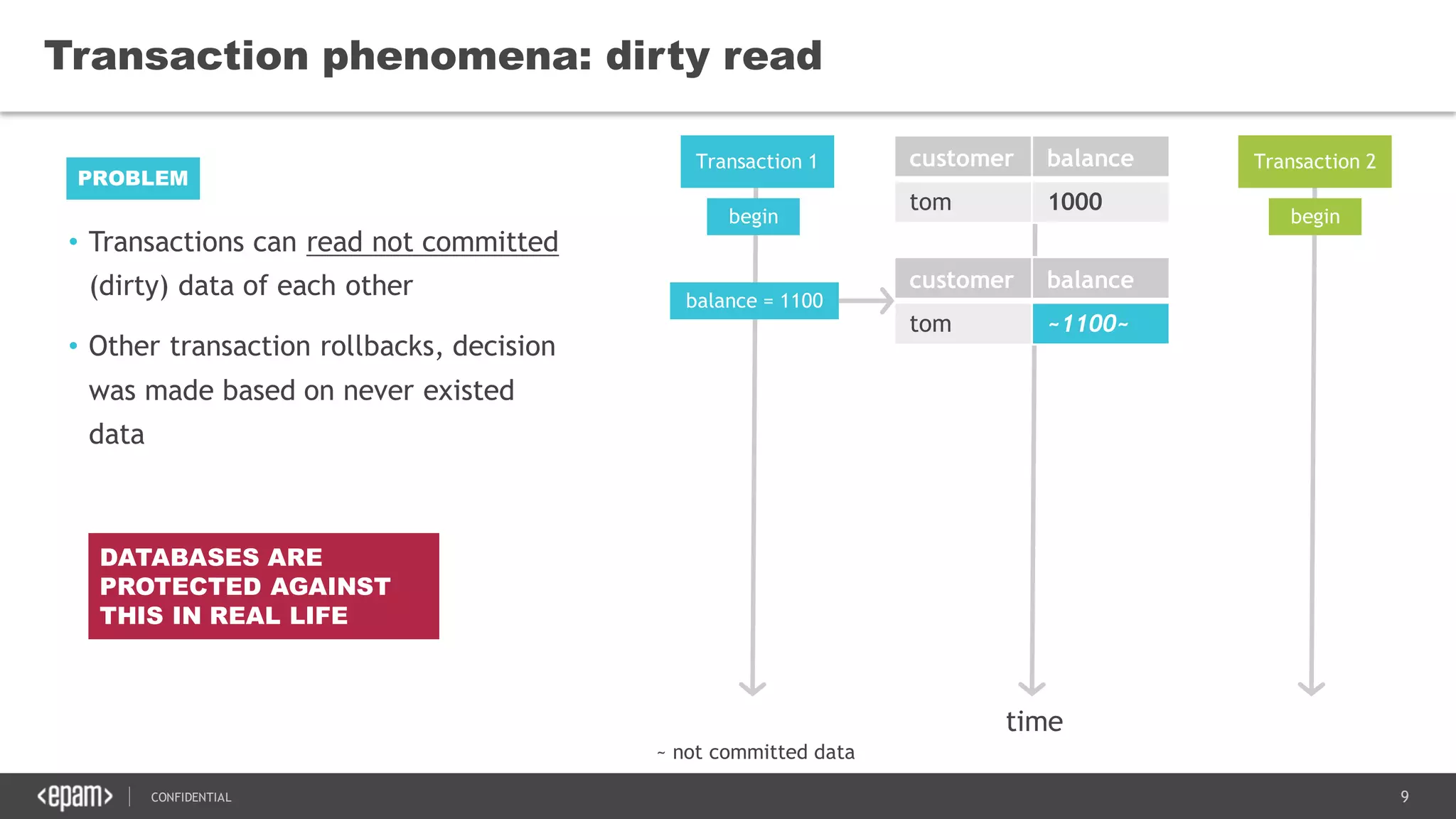
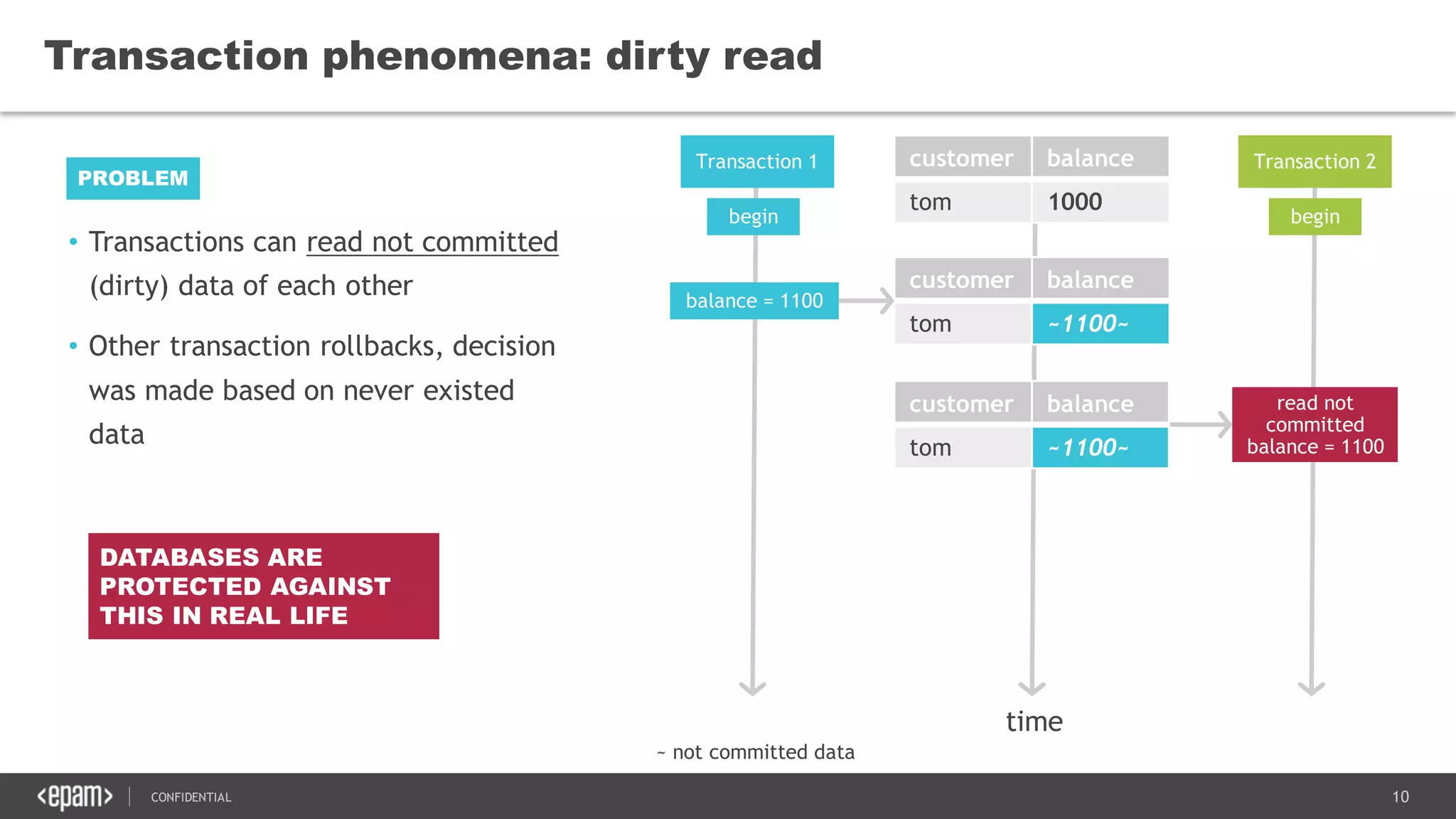
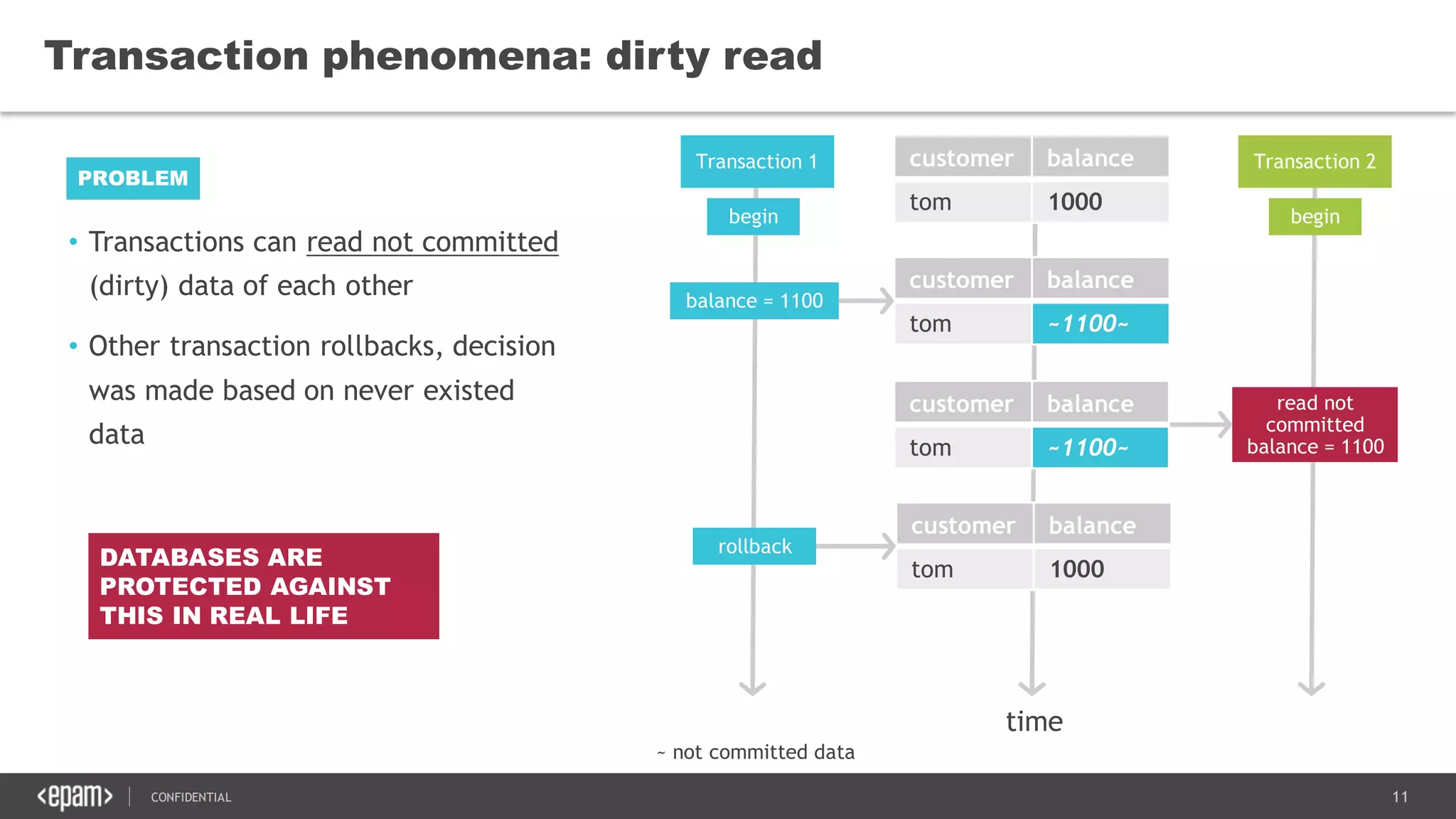
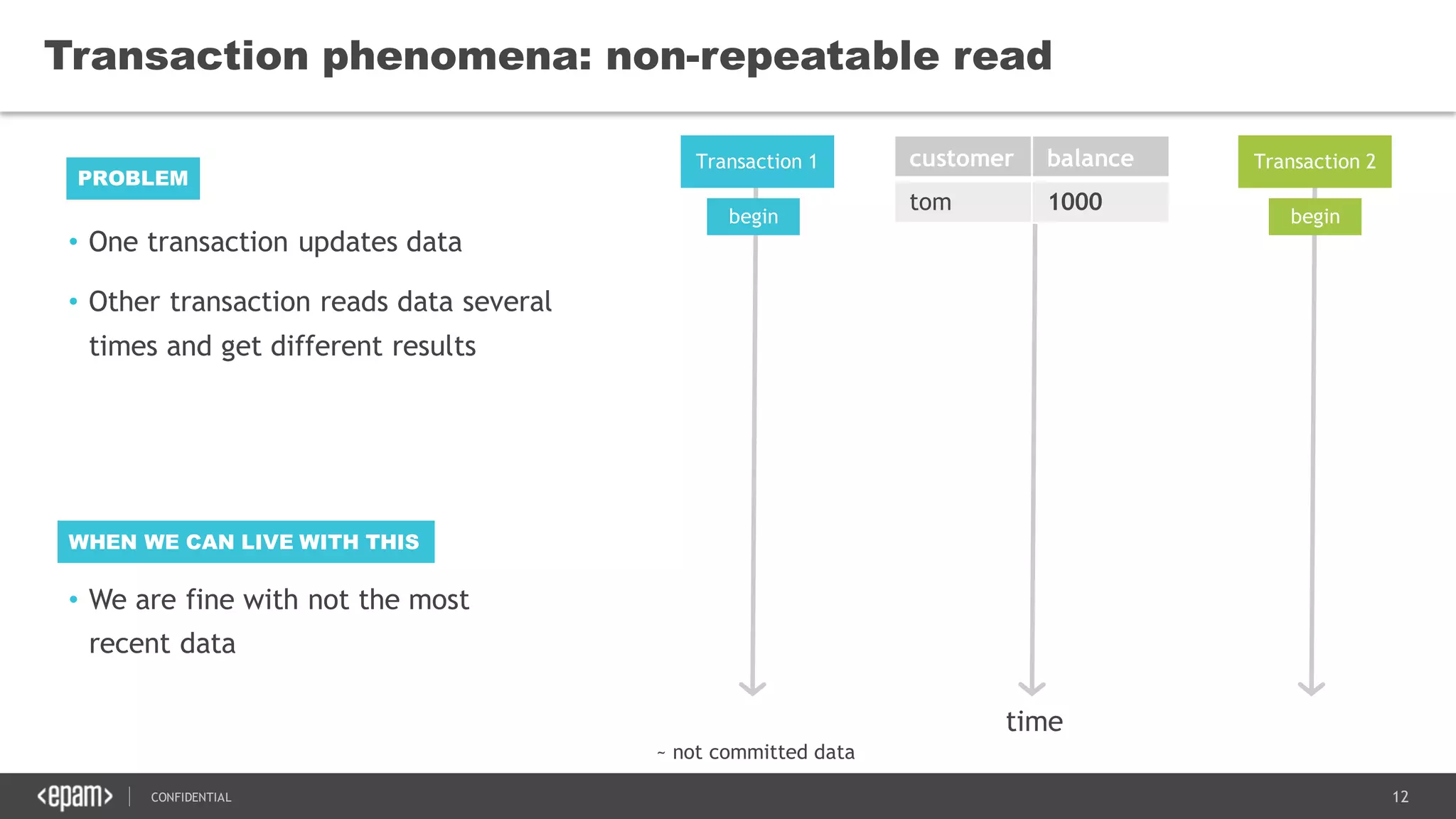
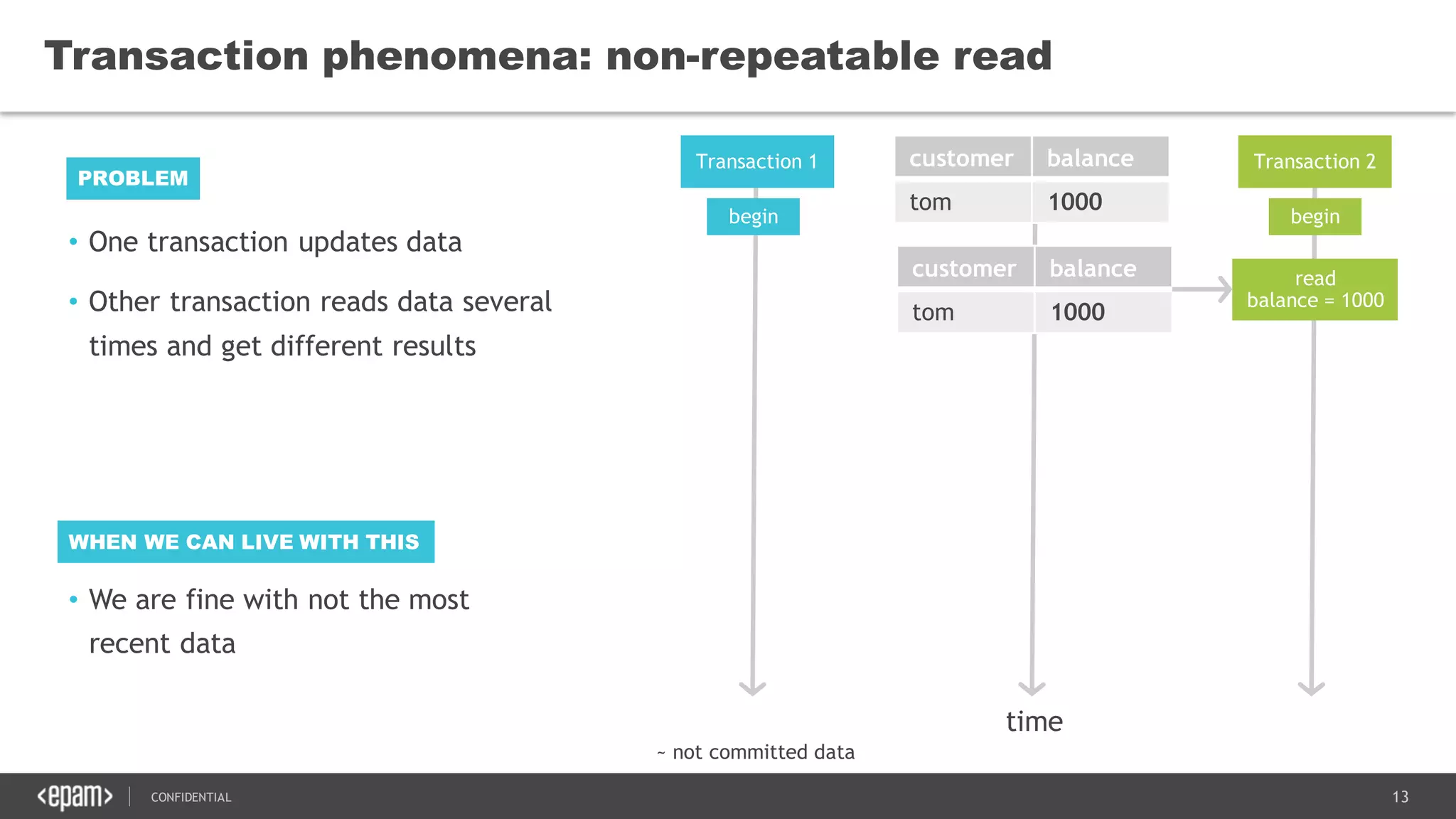
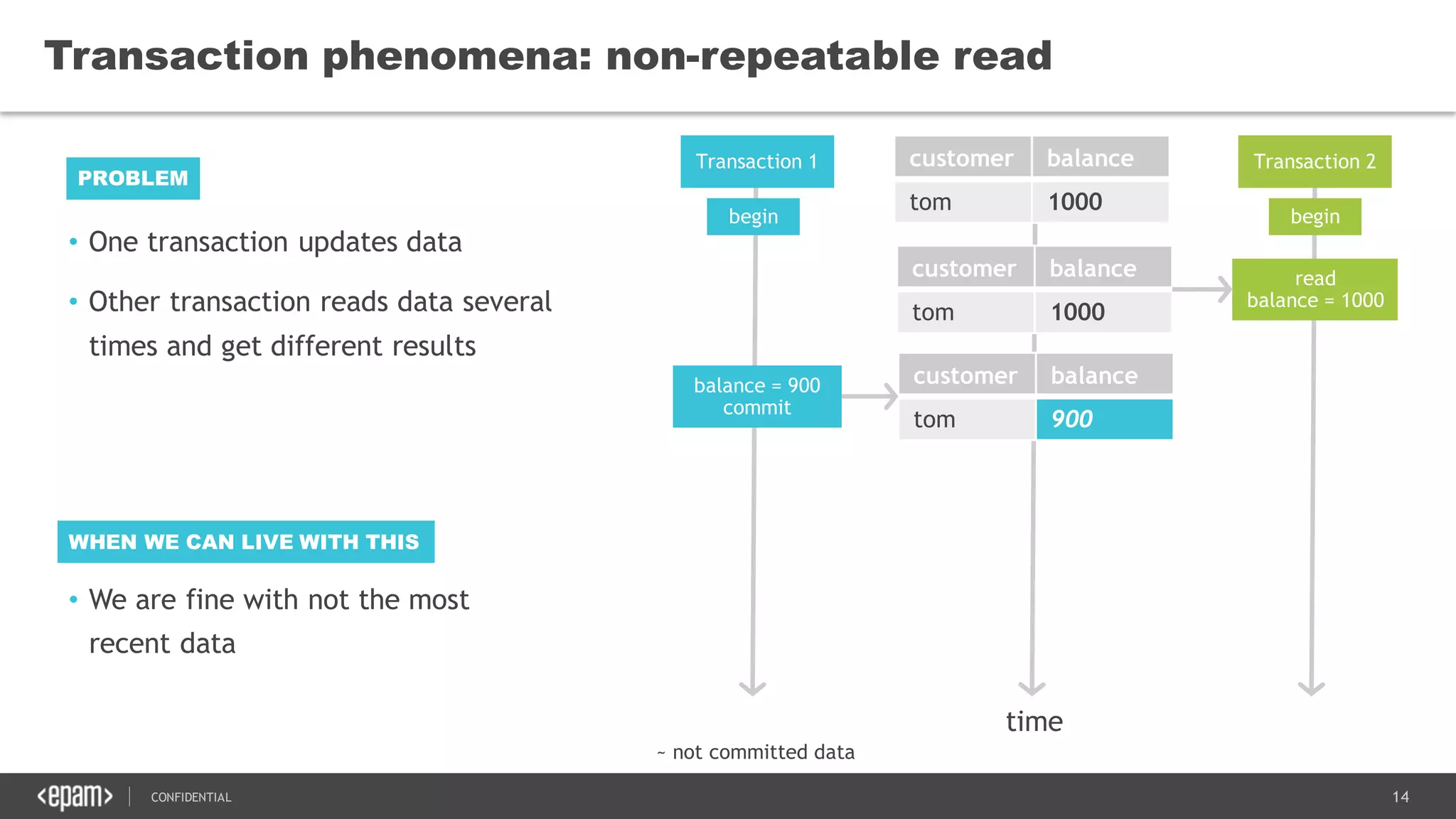
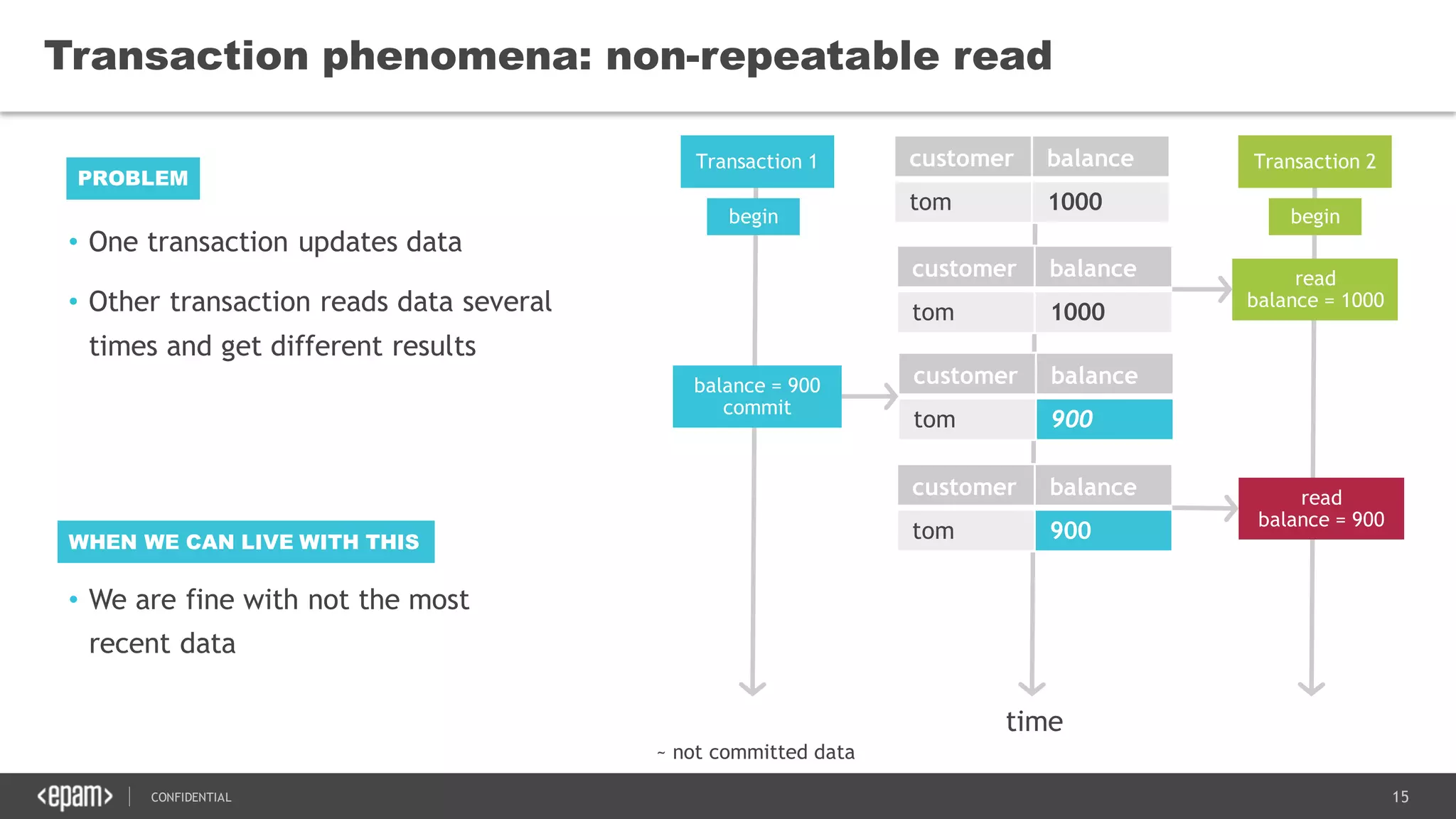
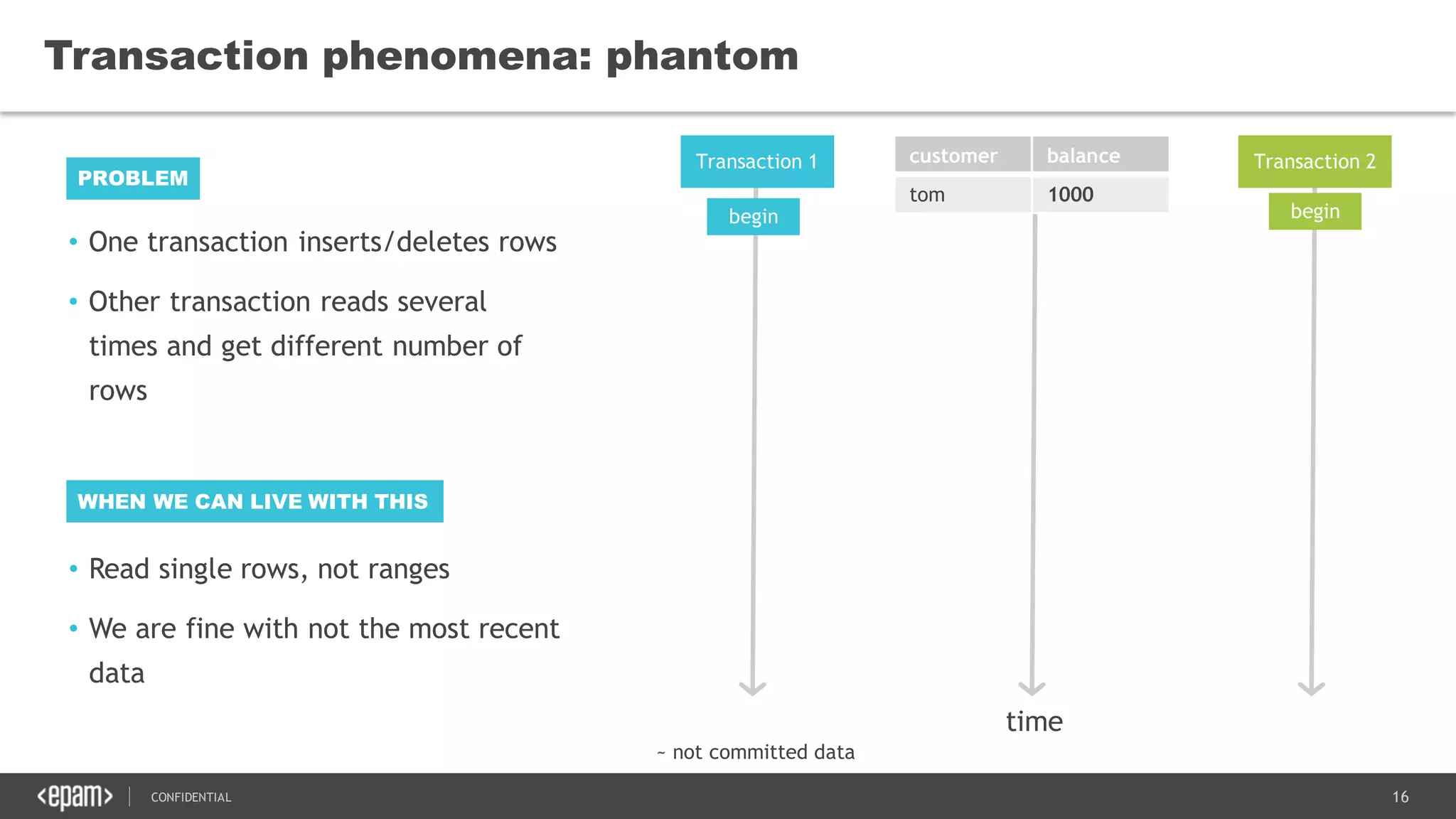
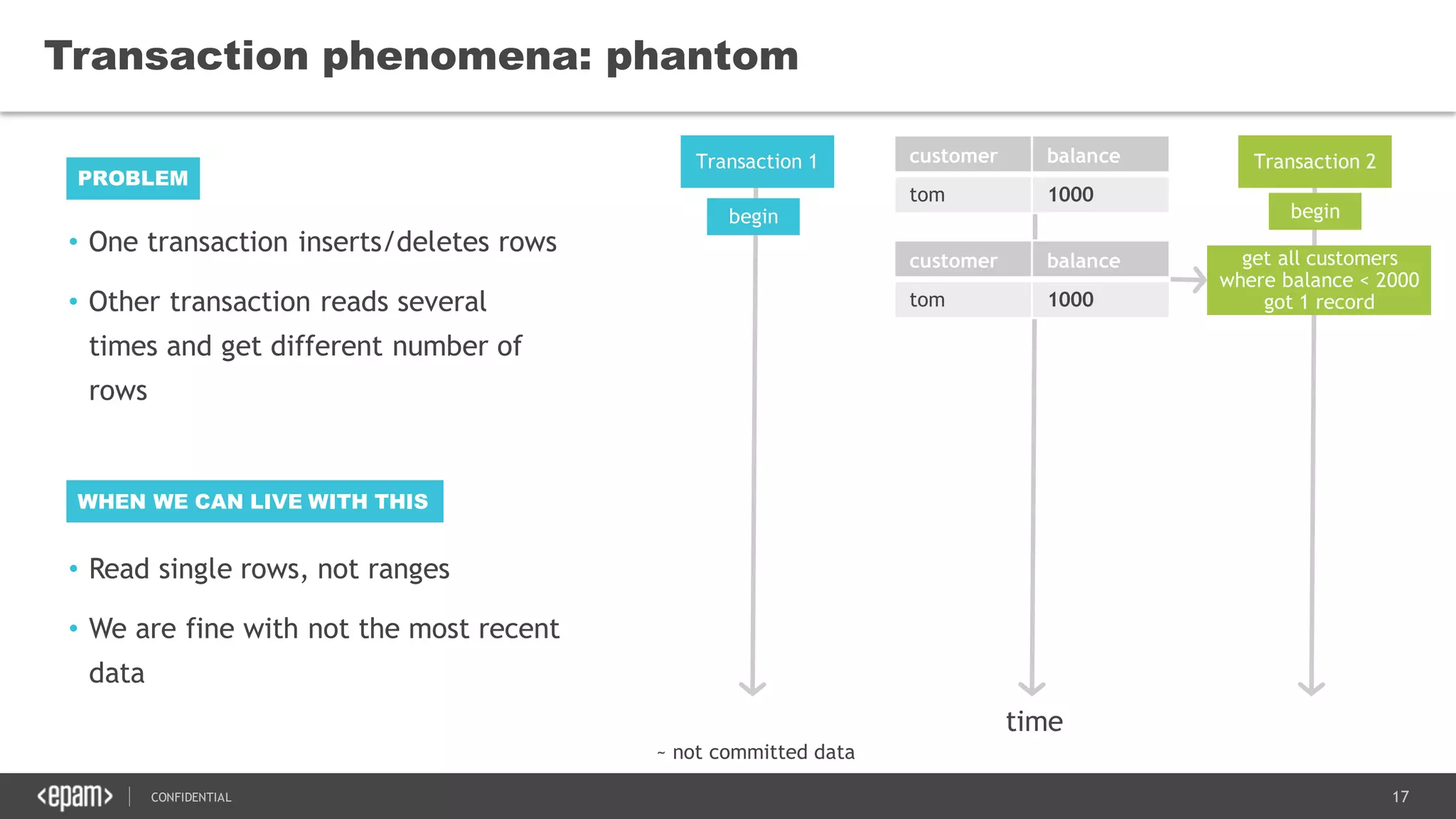
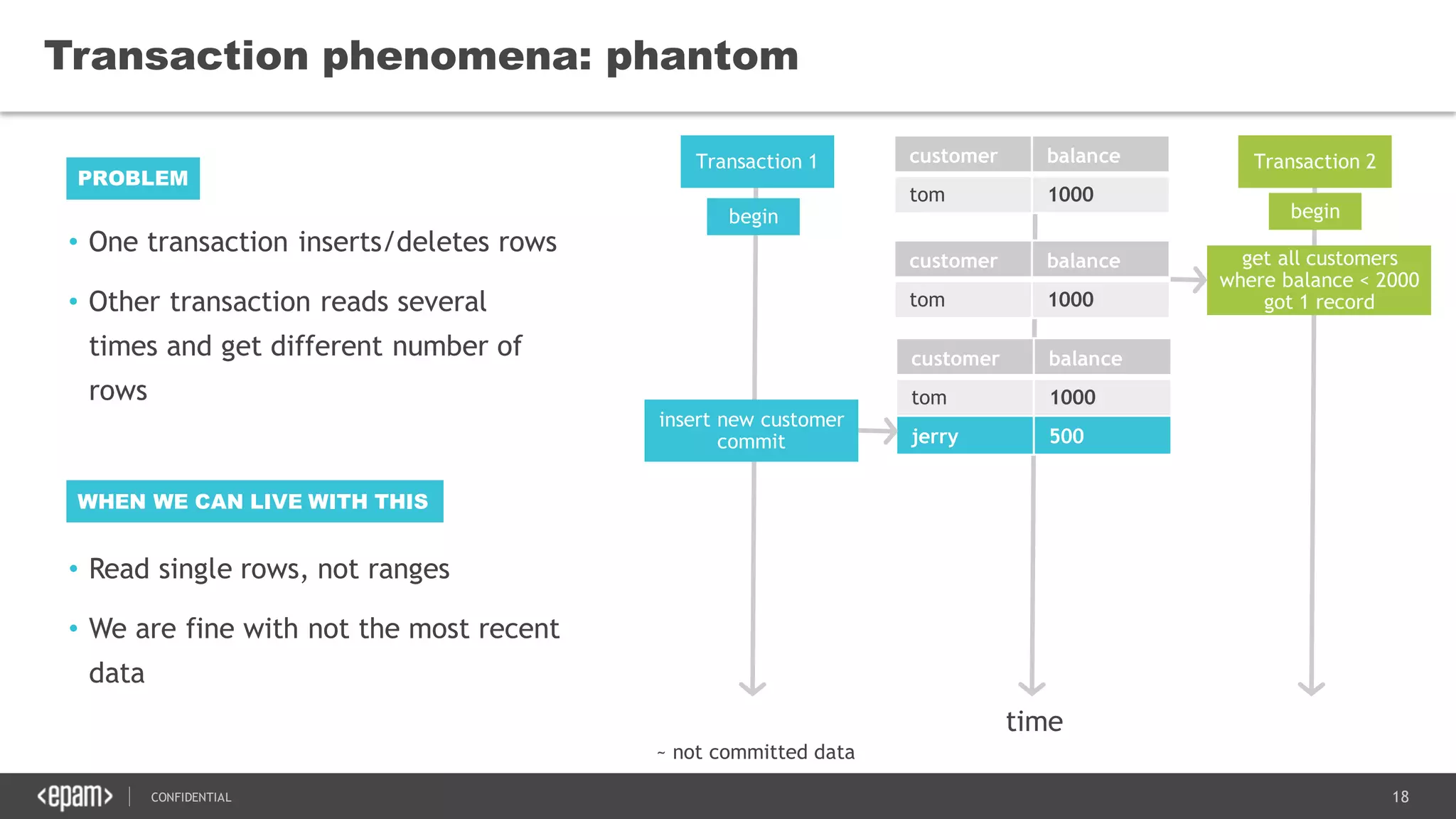
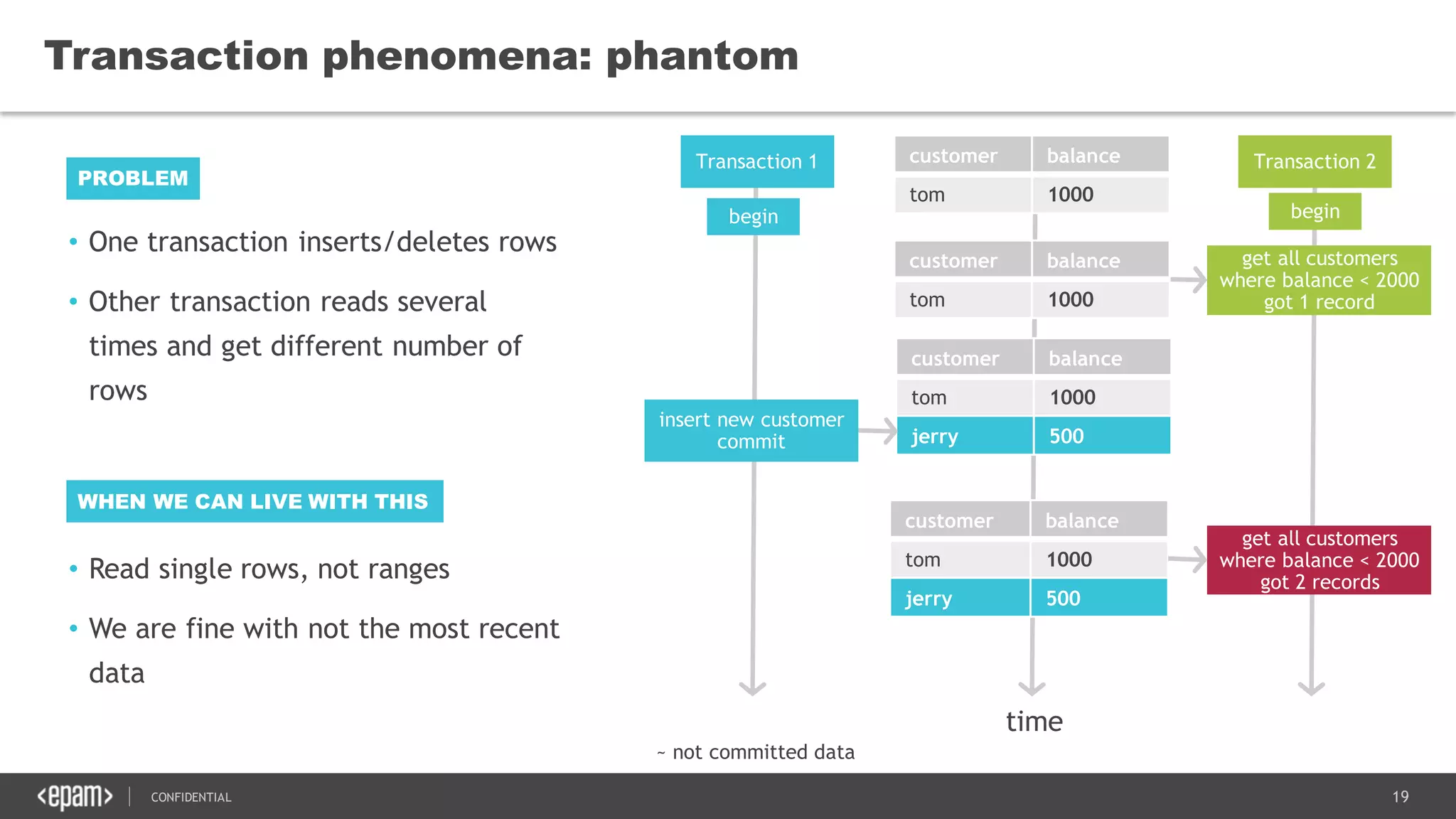
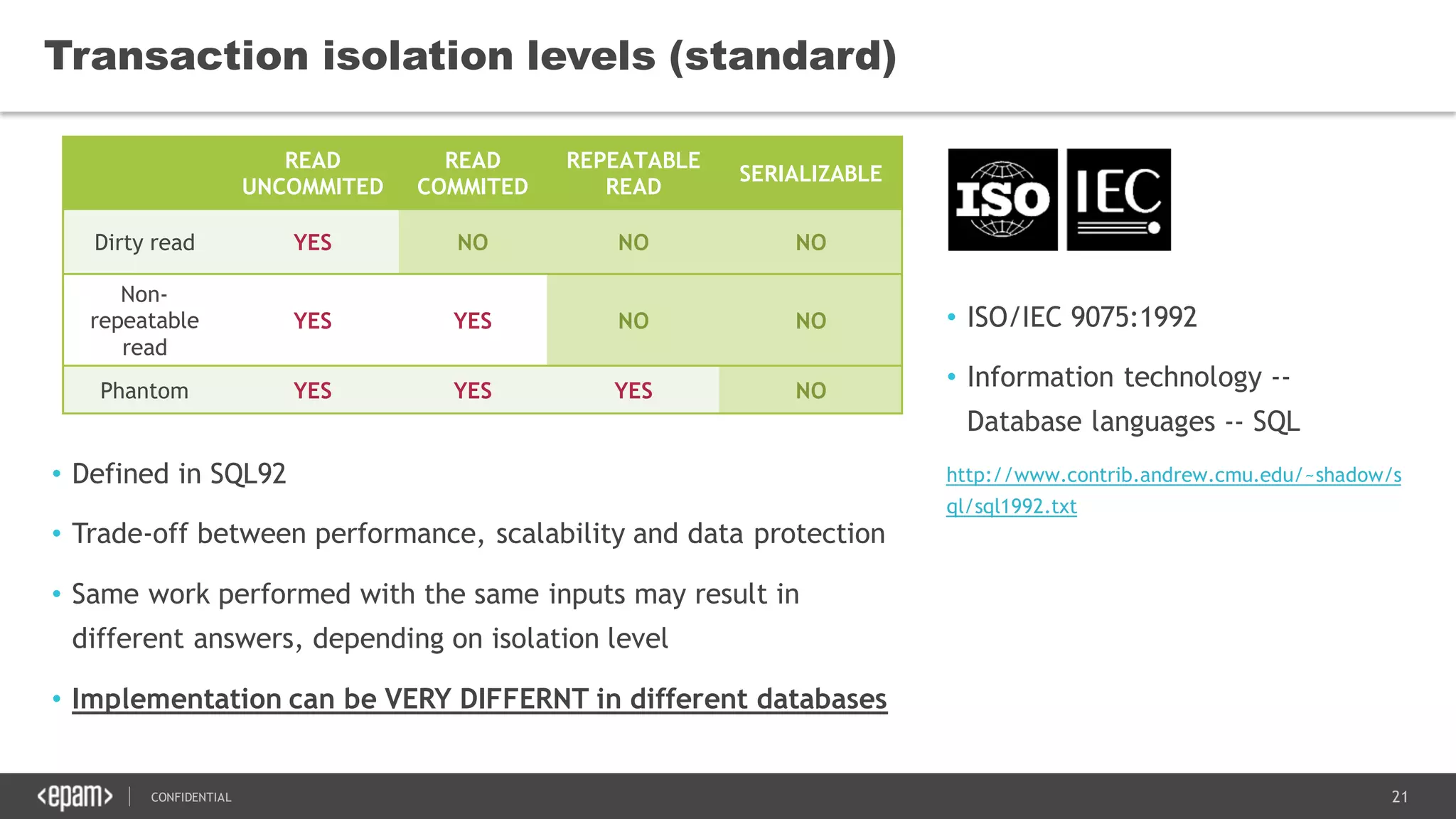
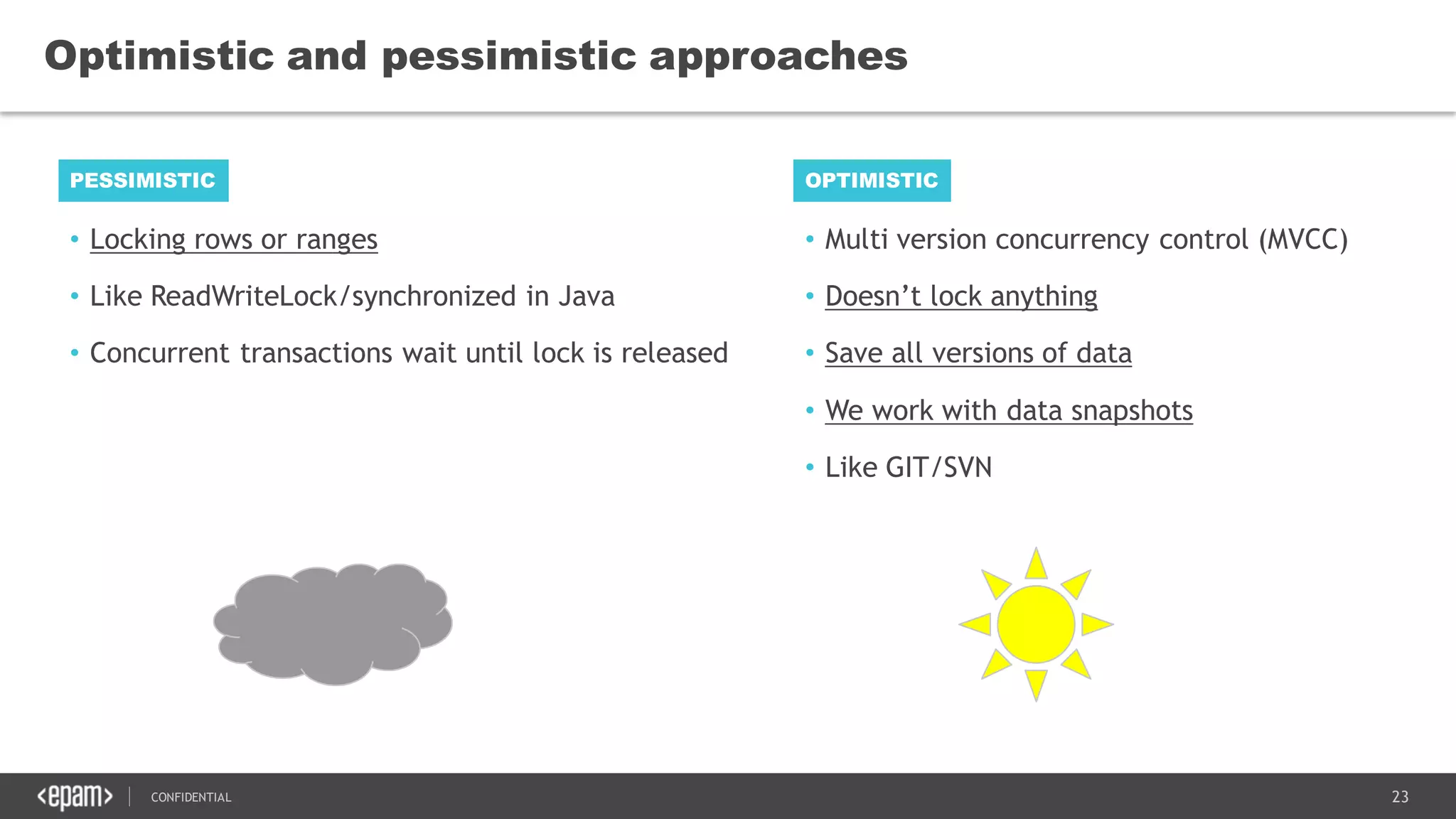
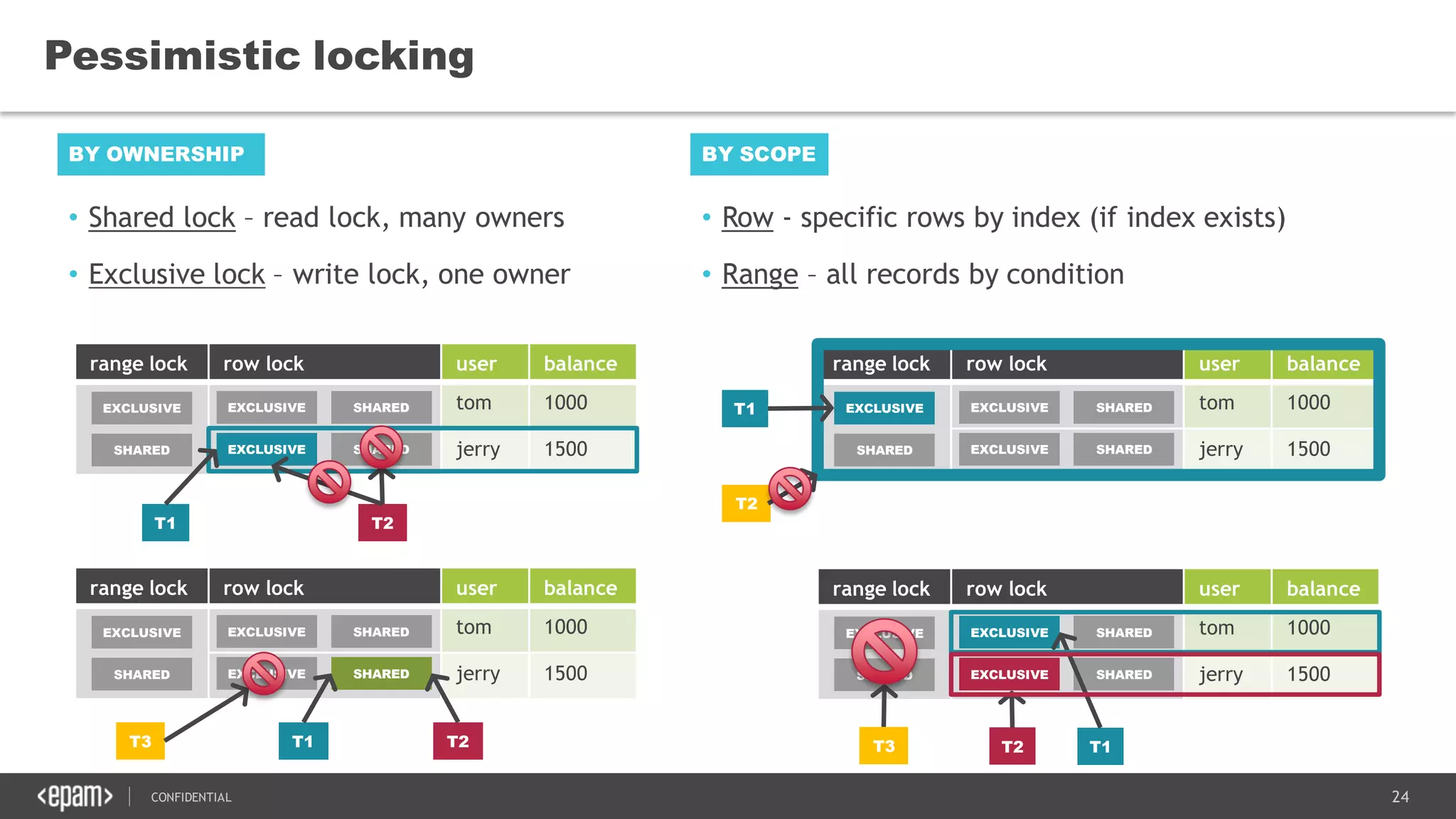
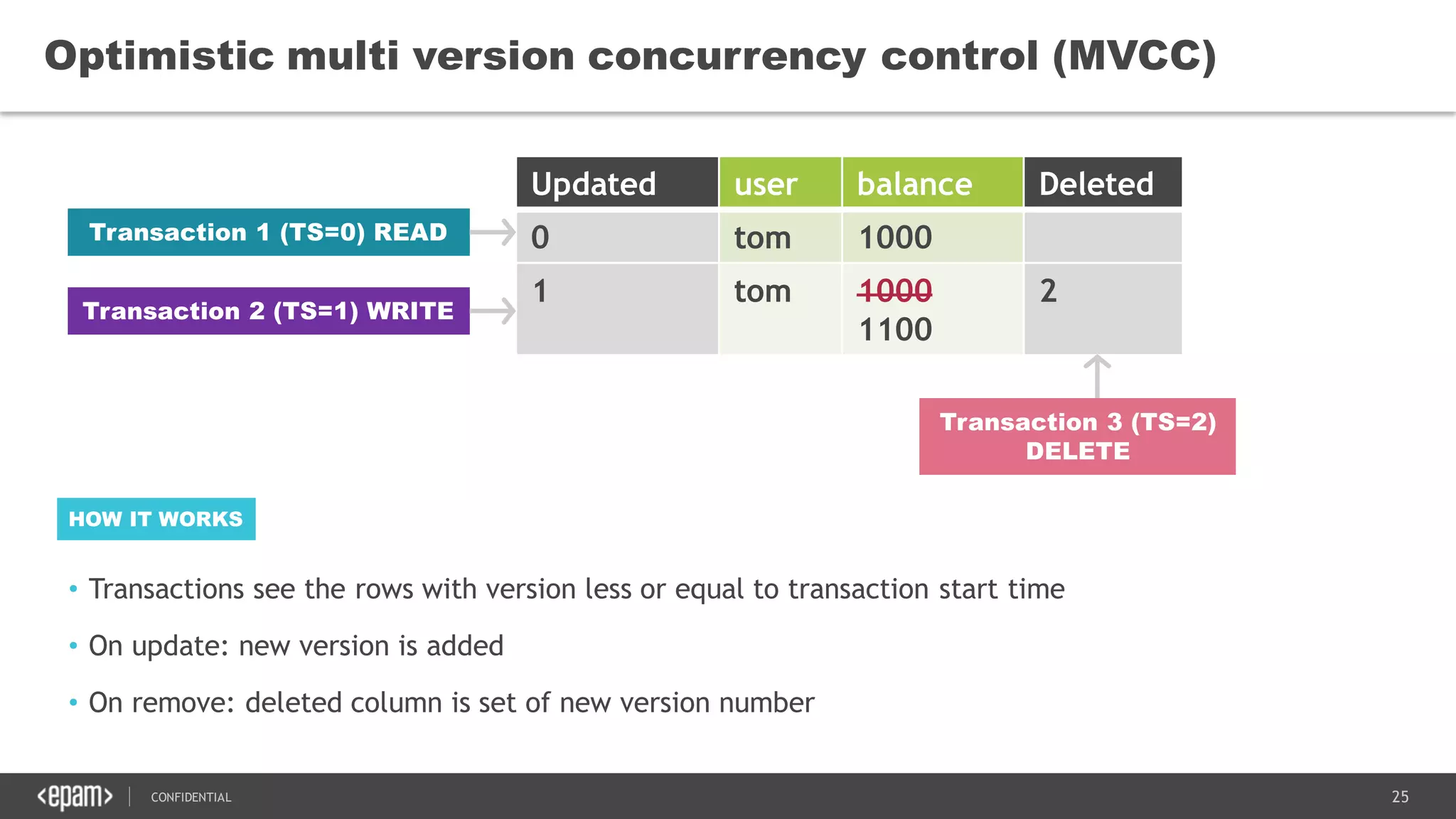
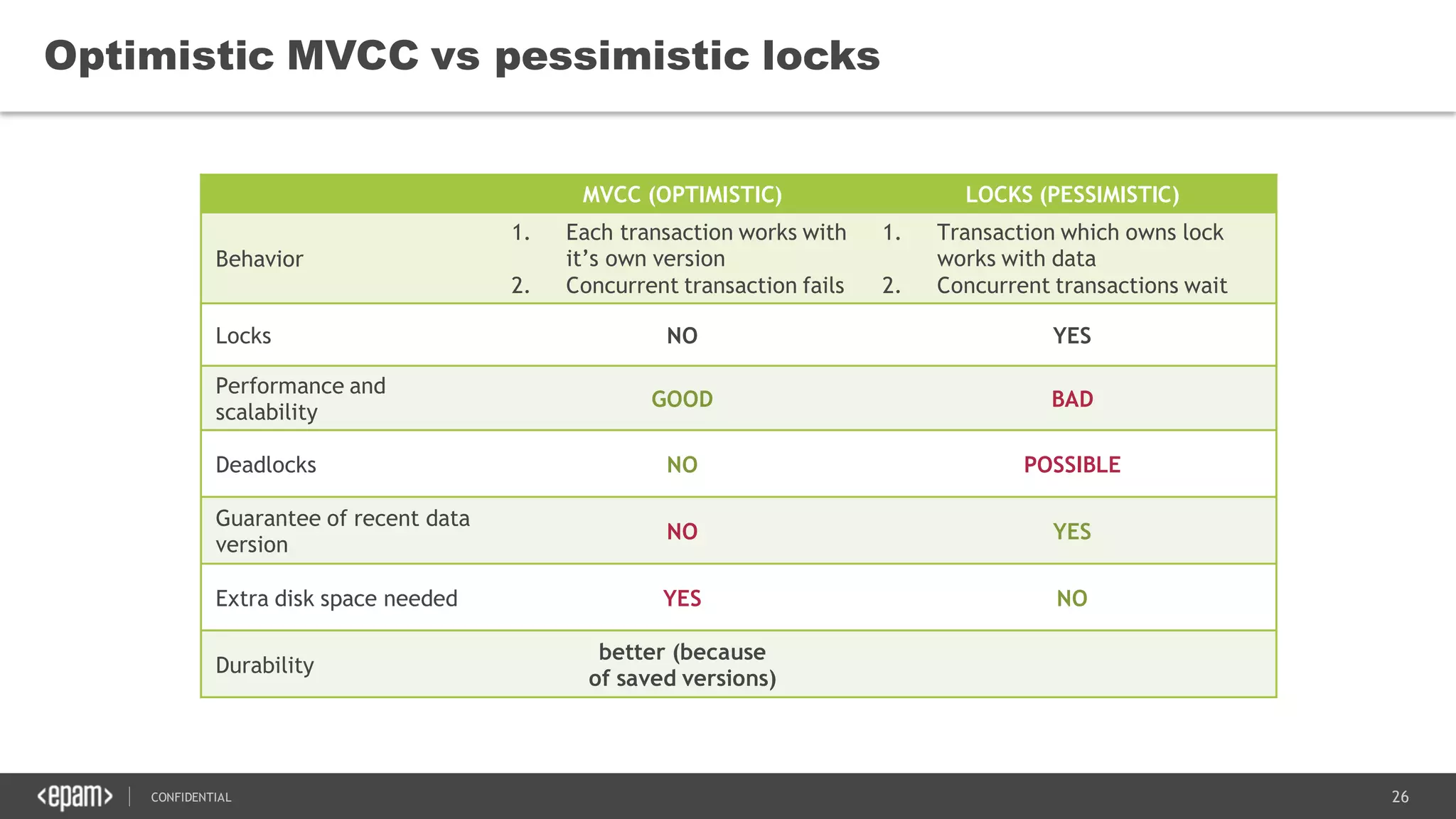
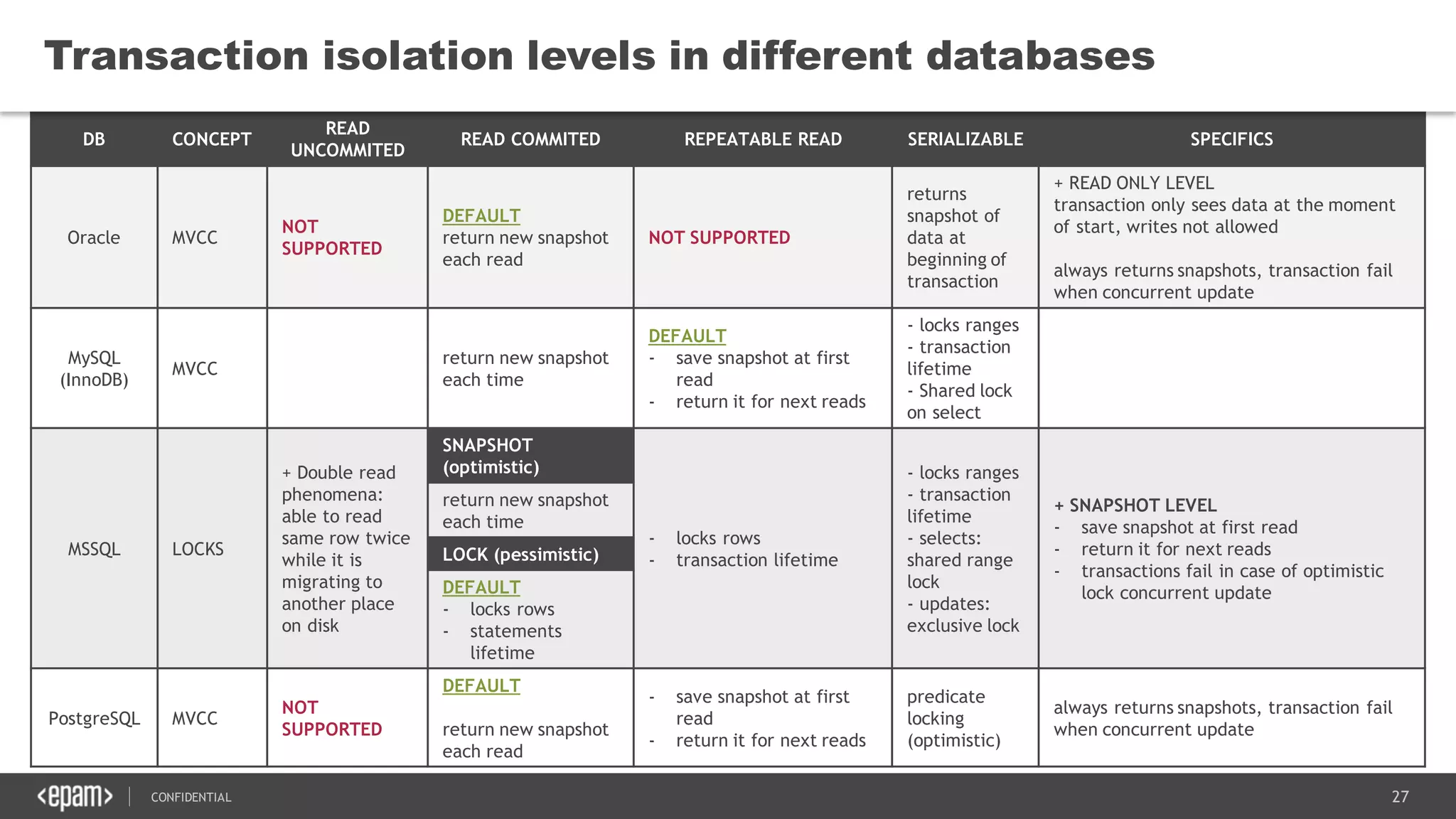
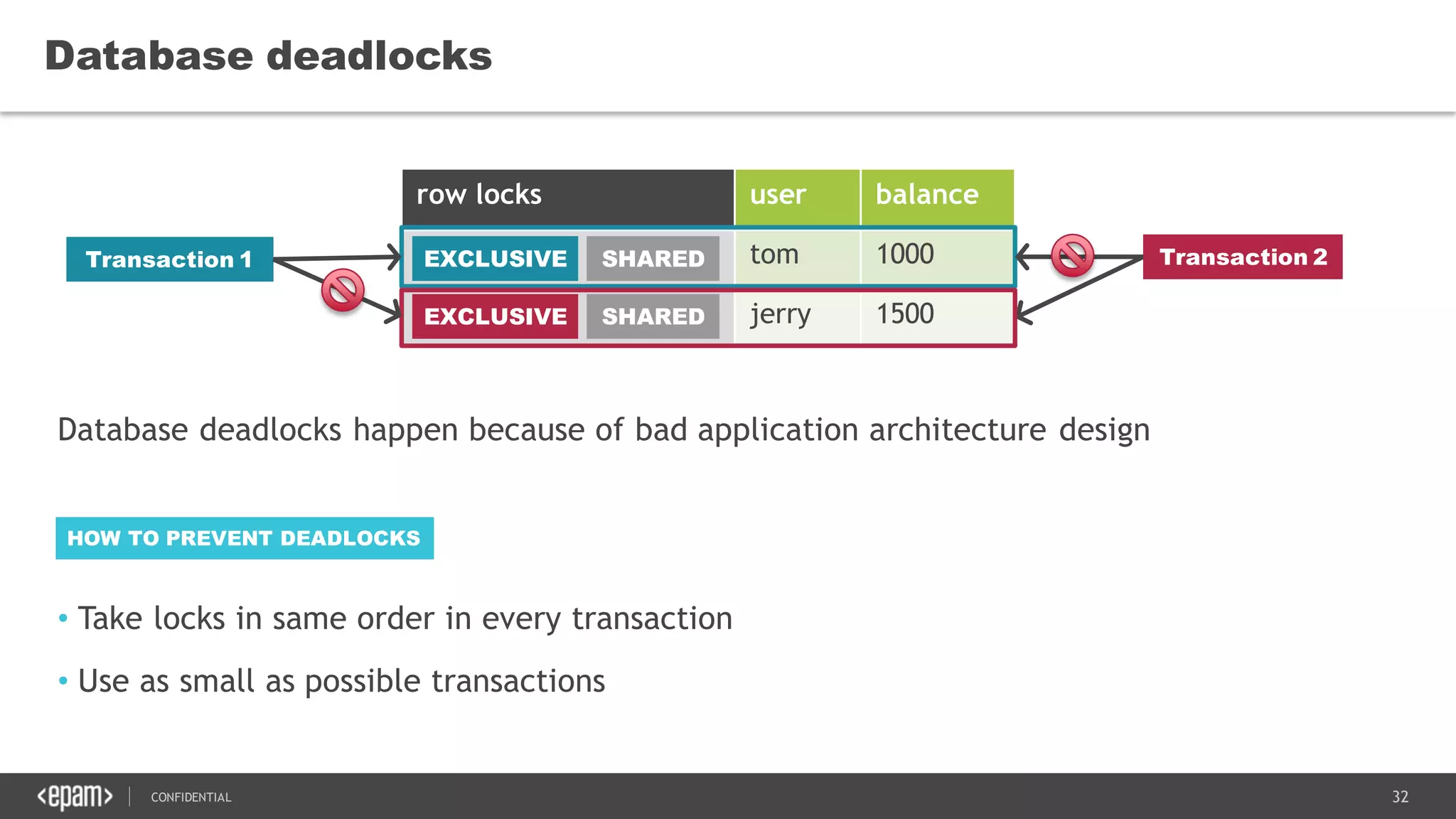
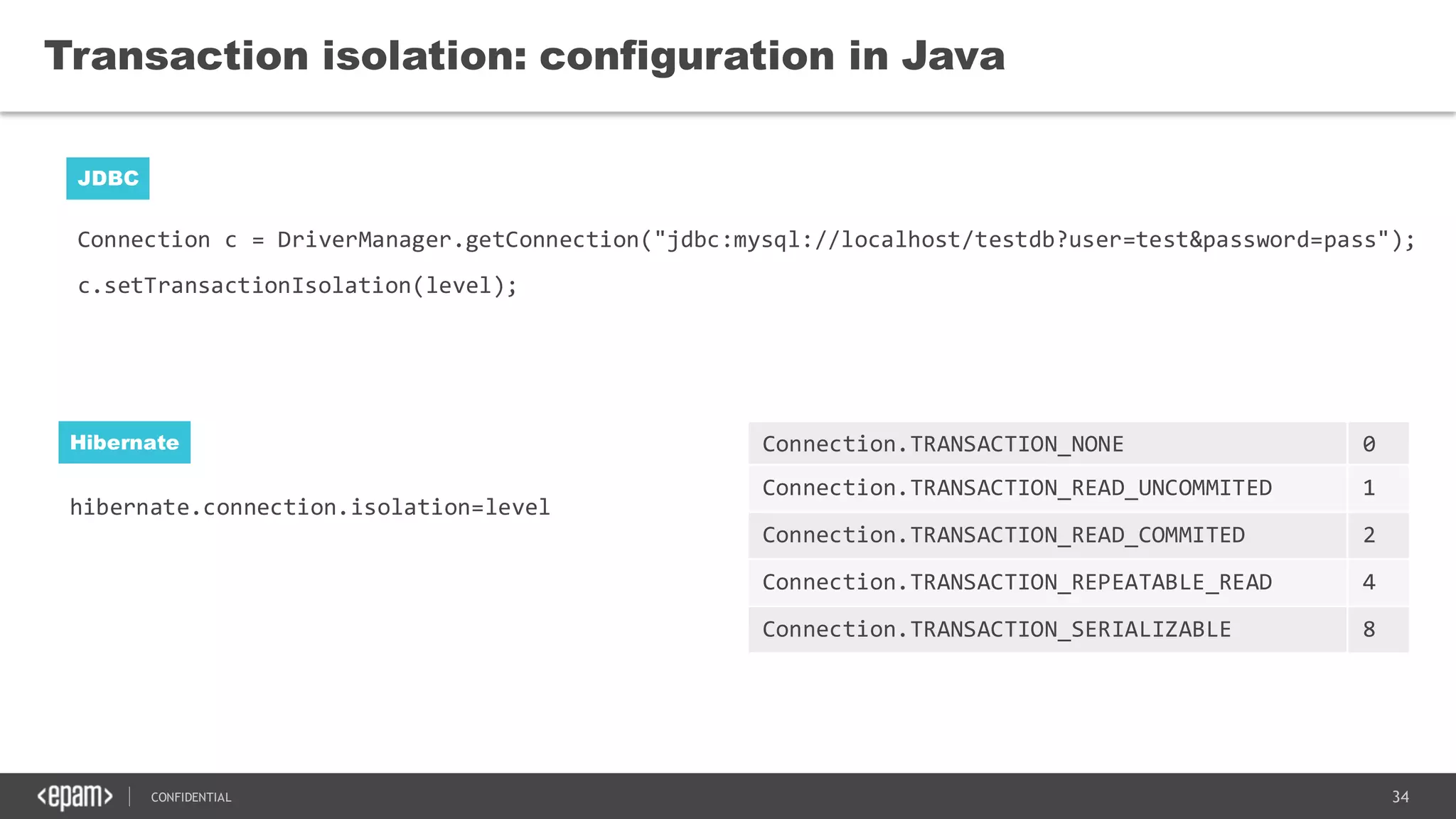
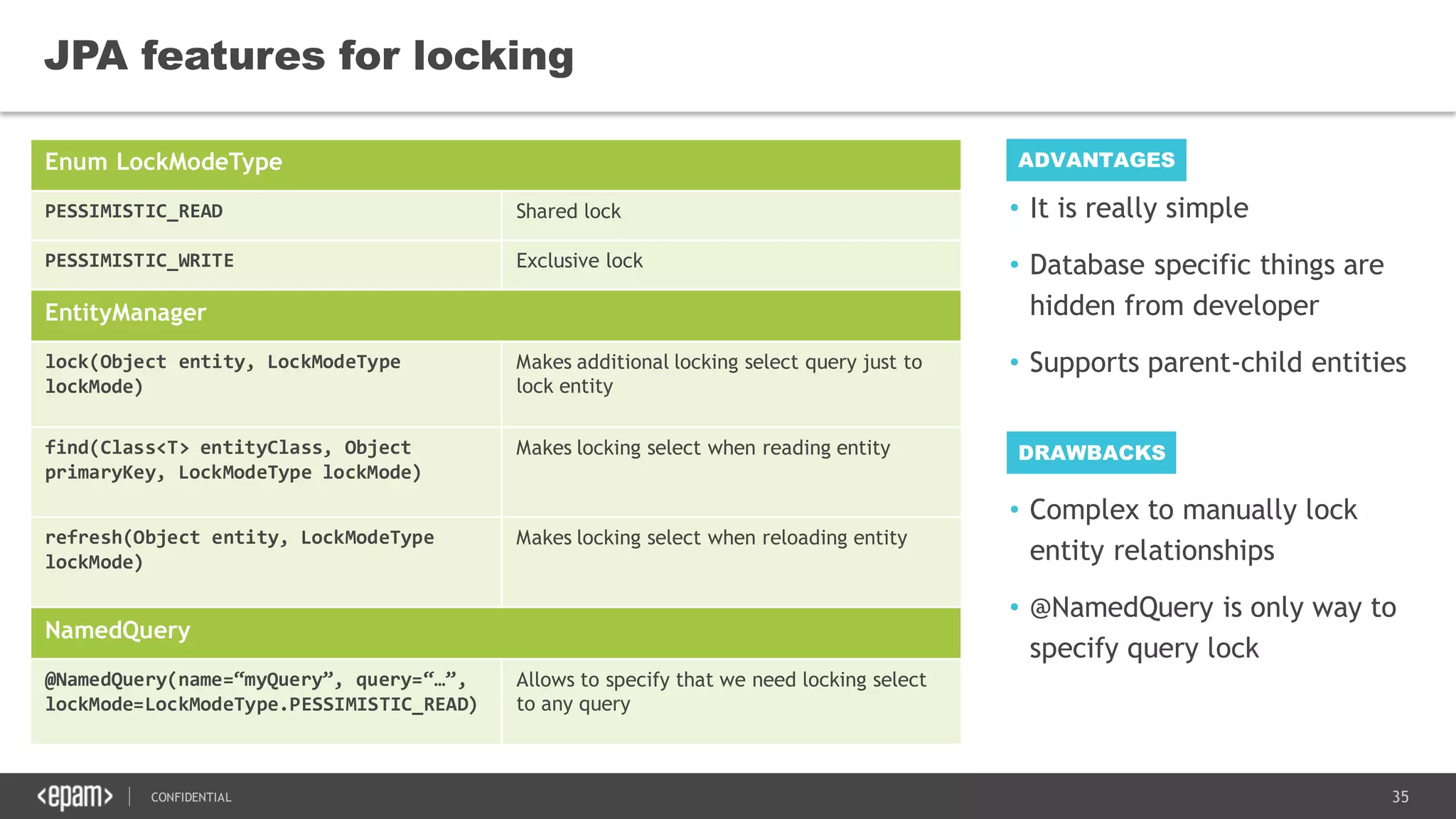
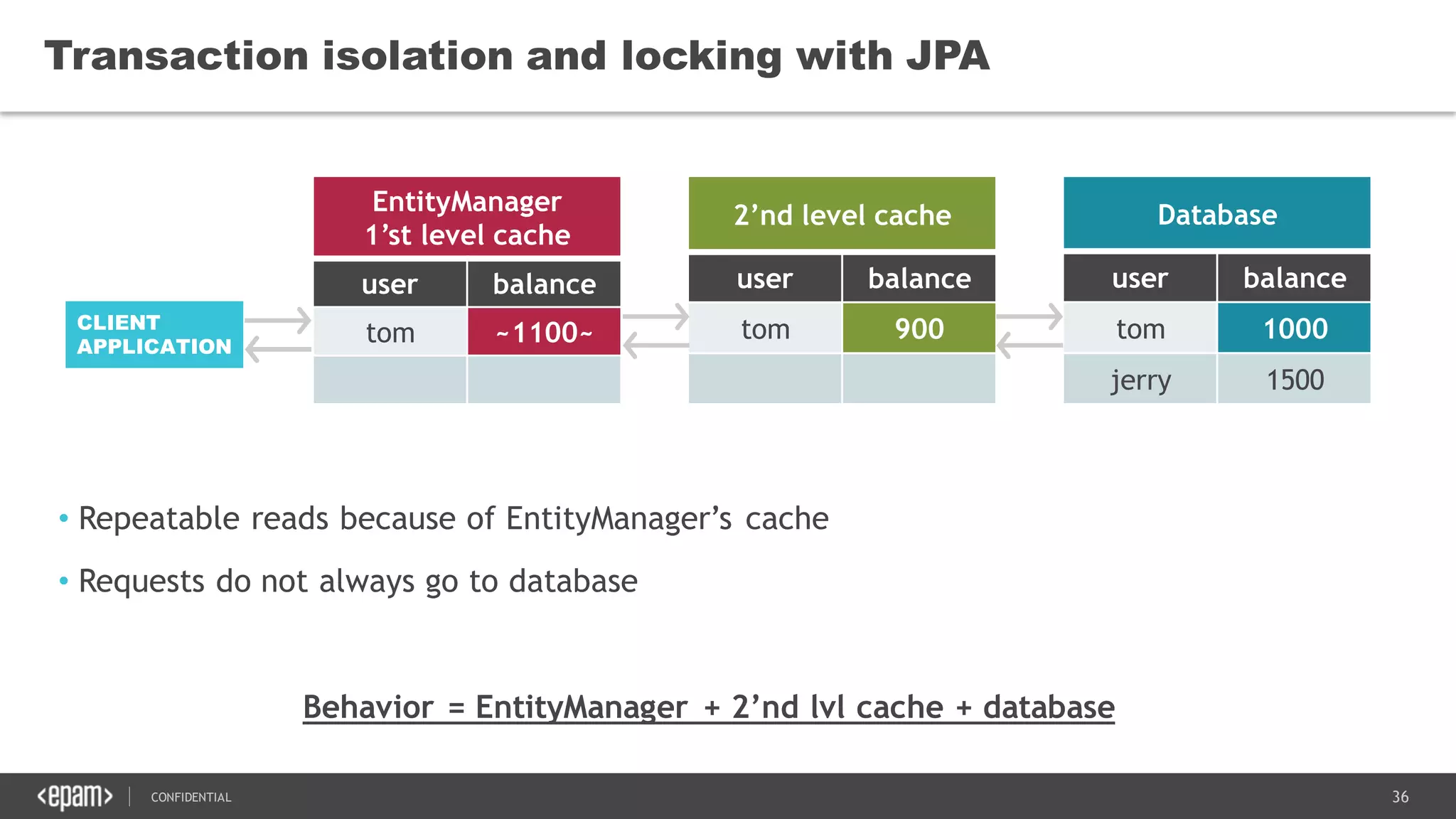
The document discusses transaction isolation and locking mechanisms in Java, focusing on various database transaction phenomena such as dirty reads, non-repeatable reads, and phantom inserts. It explains the differences between optimistic and pessimistic locking strategies, detailing how different databases implement these concepts and their respective isolation levels. Additionally, it covers best practices for managing database transactions to avoid issues like deadlocks and performance degradation.