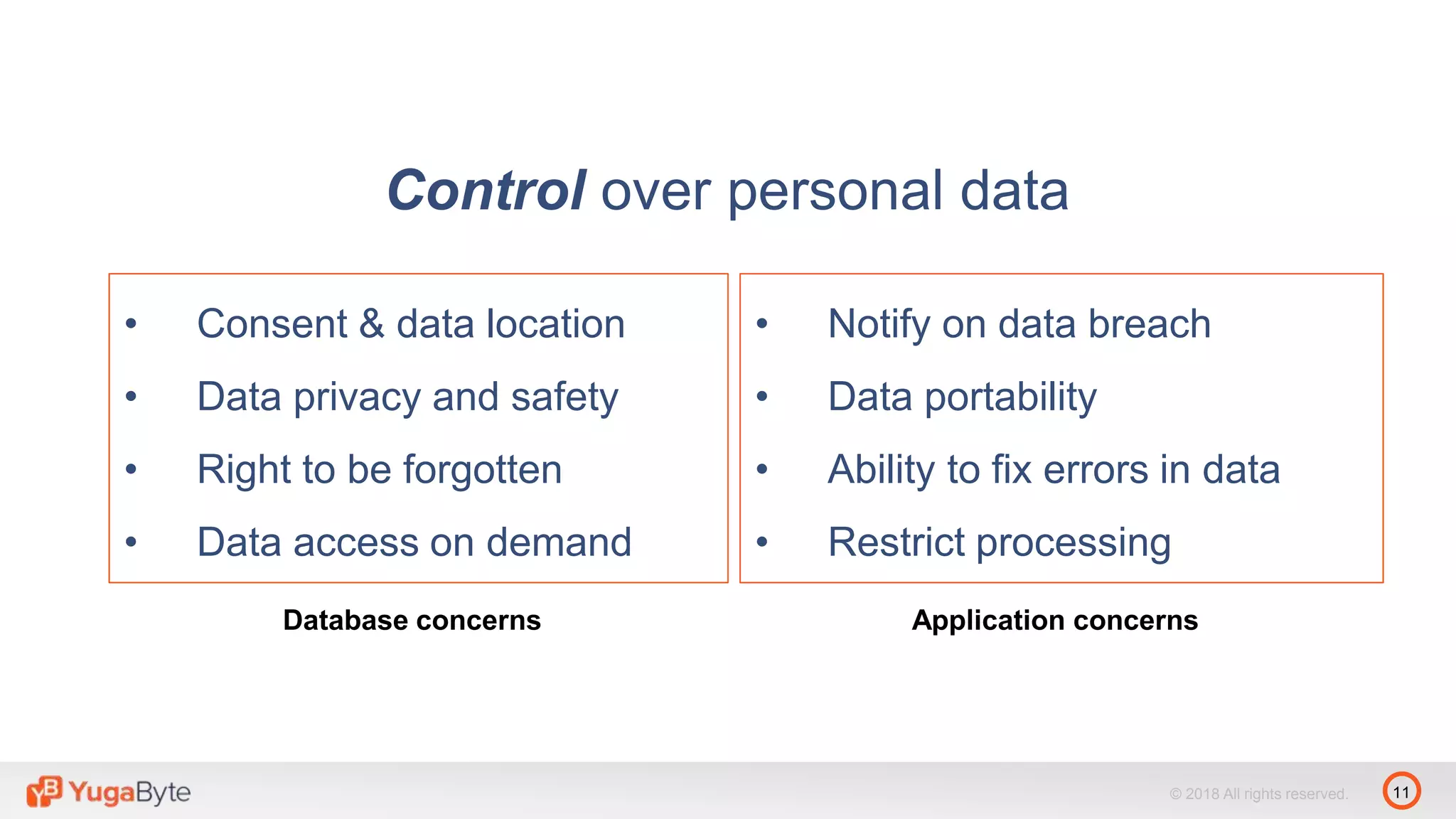
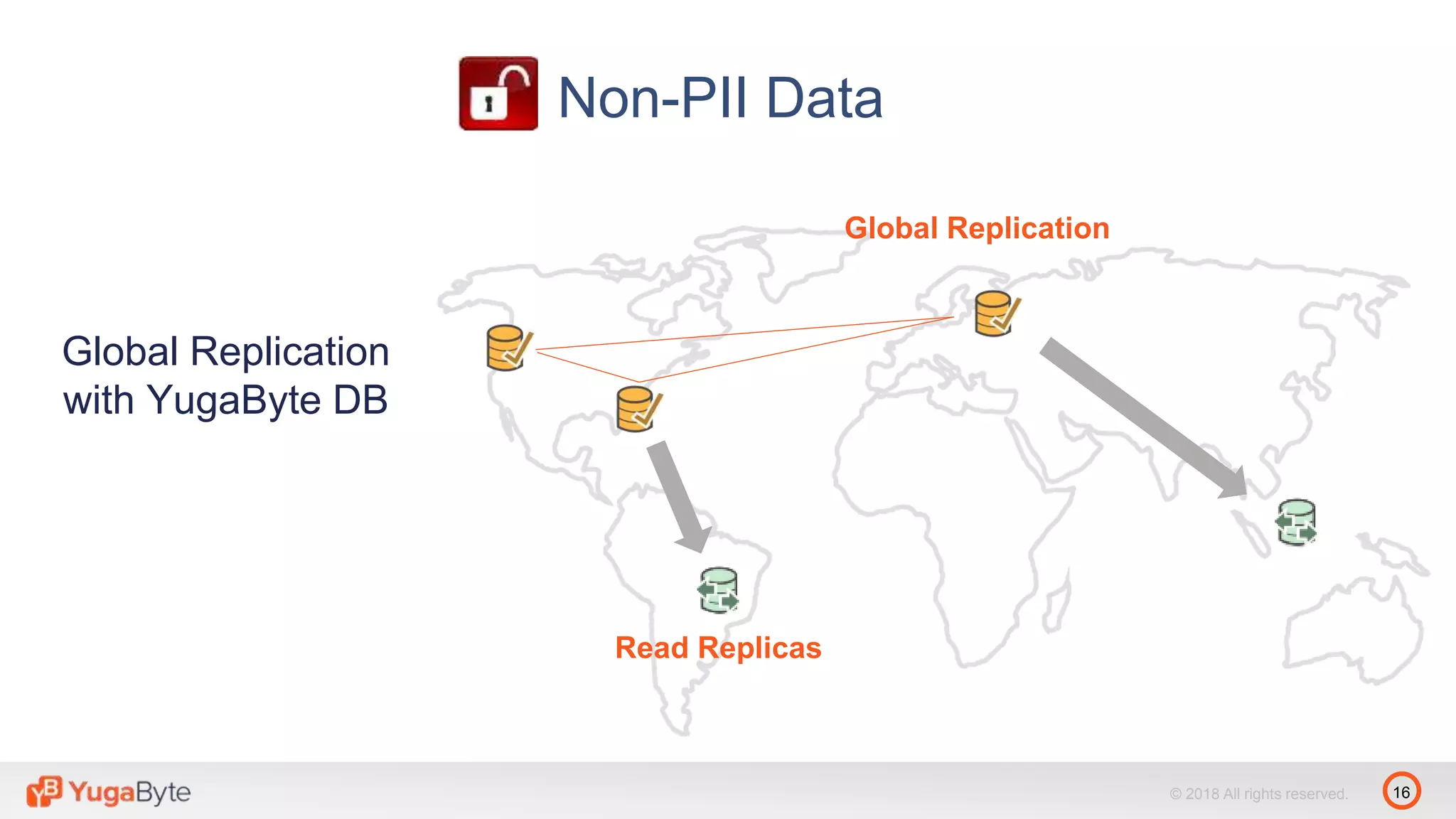
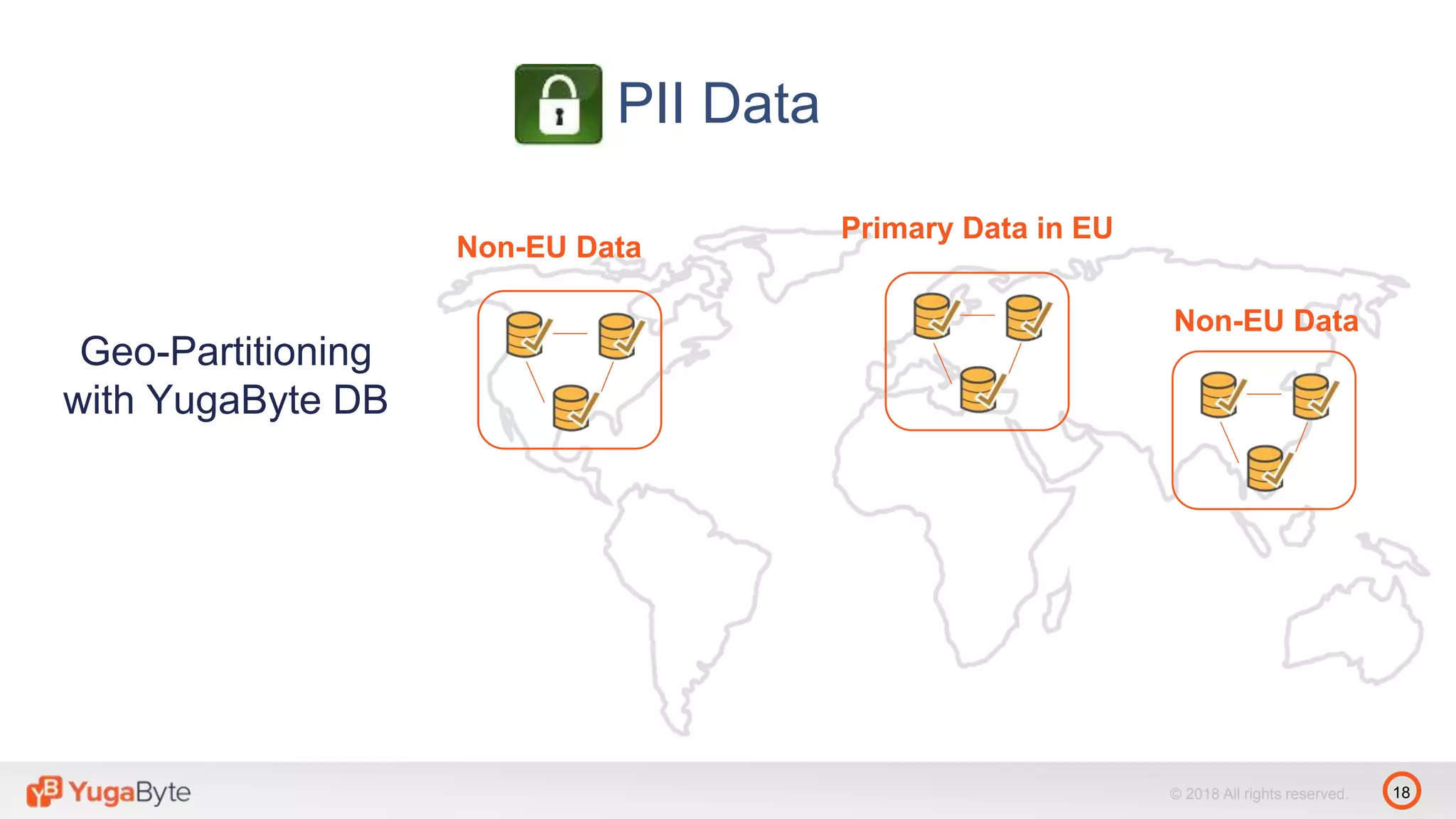
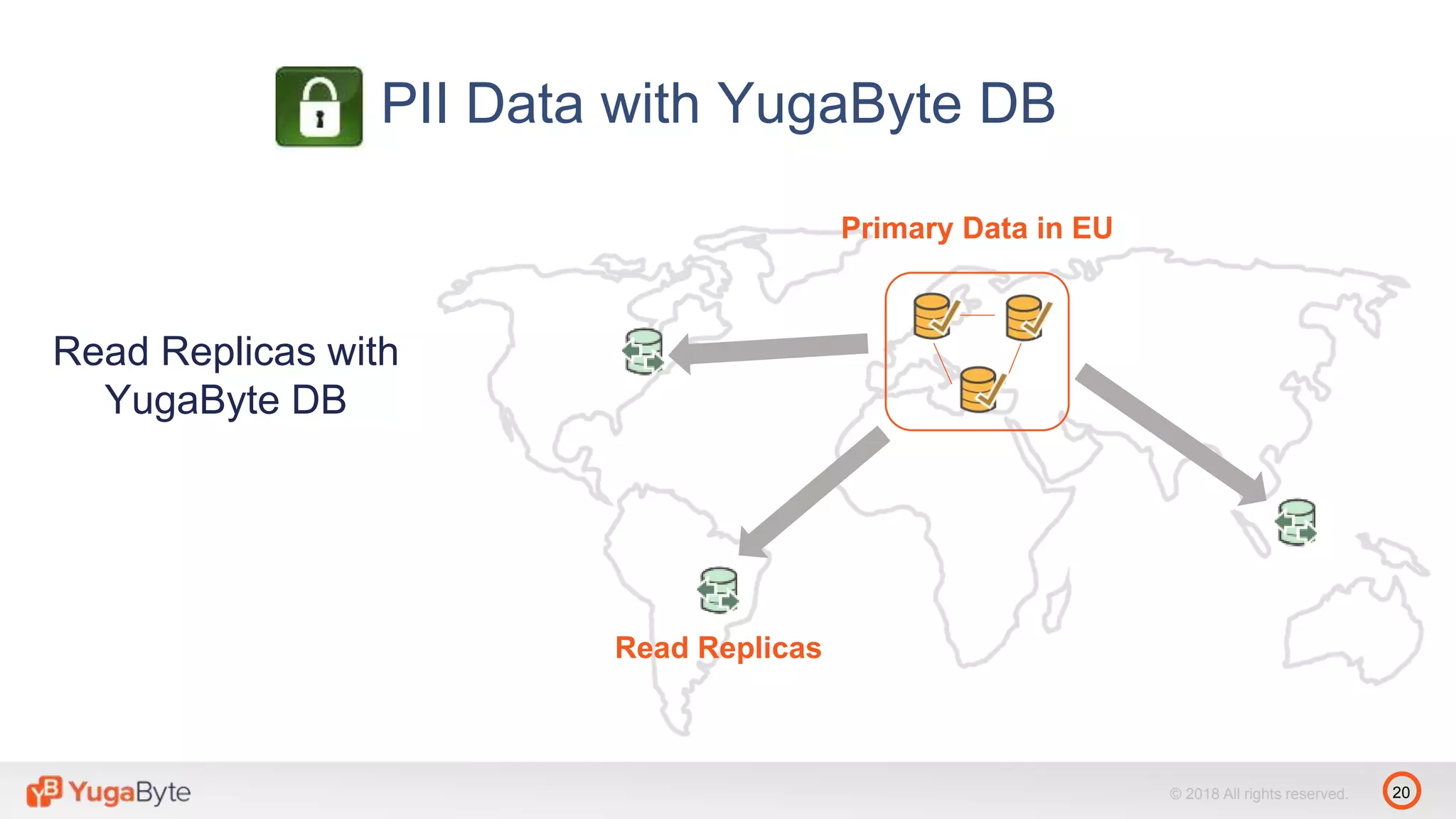
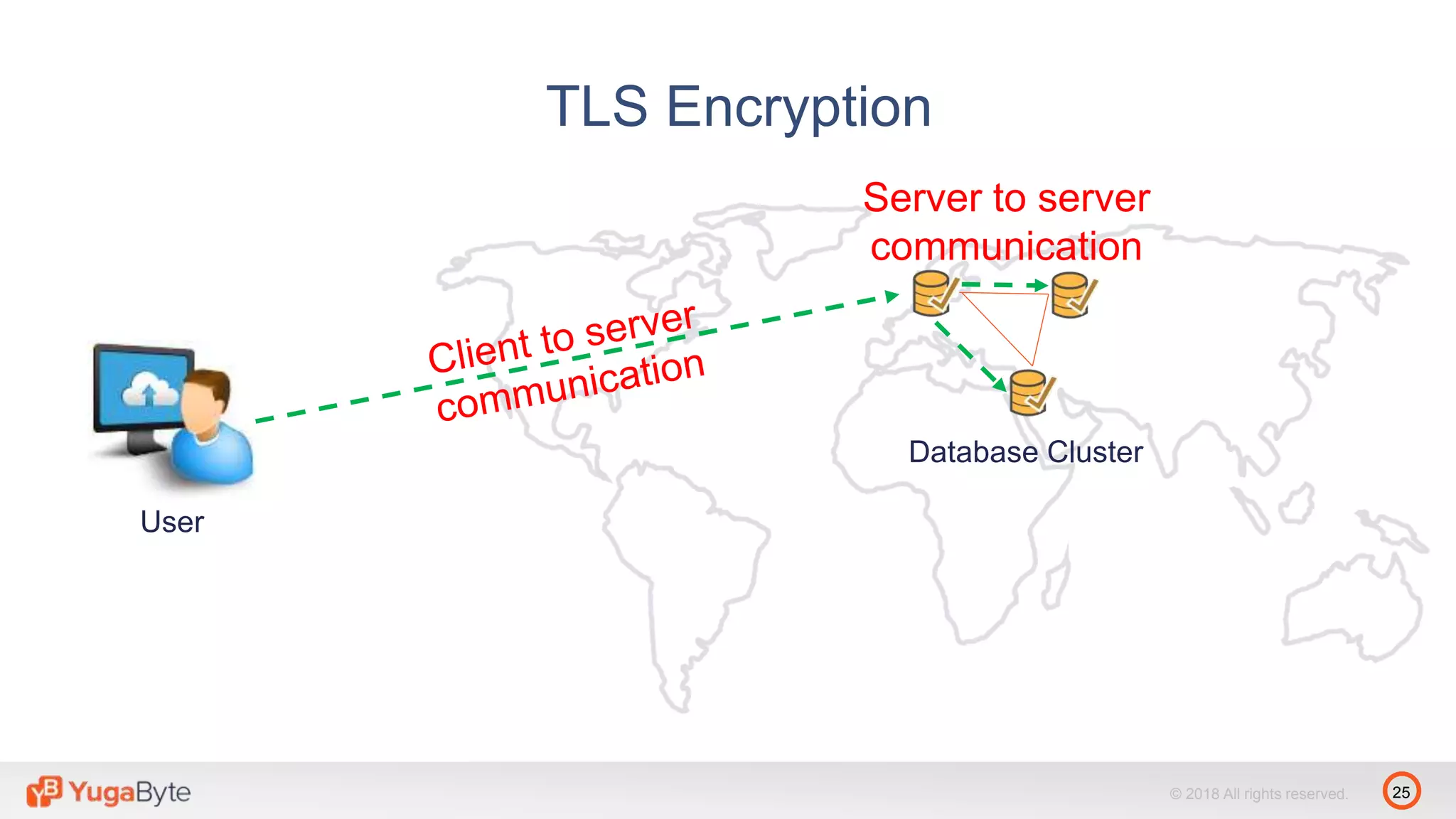
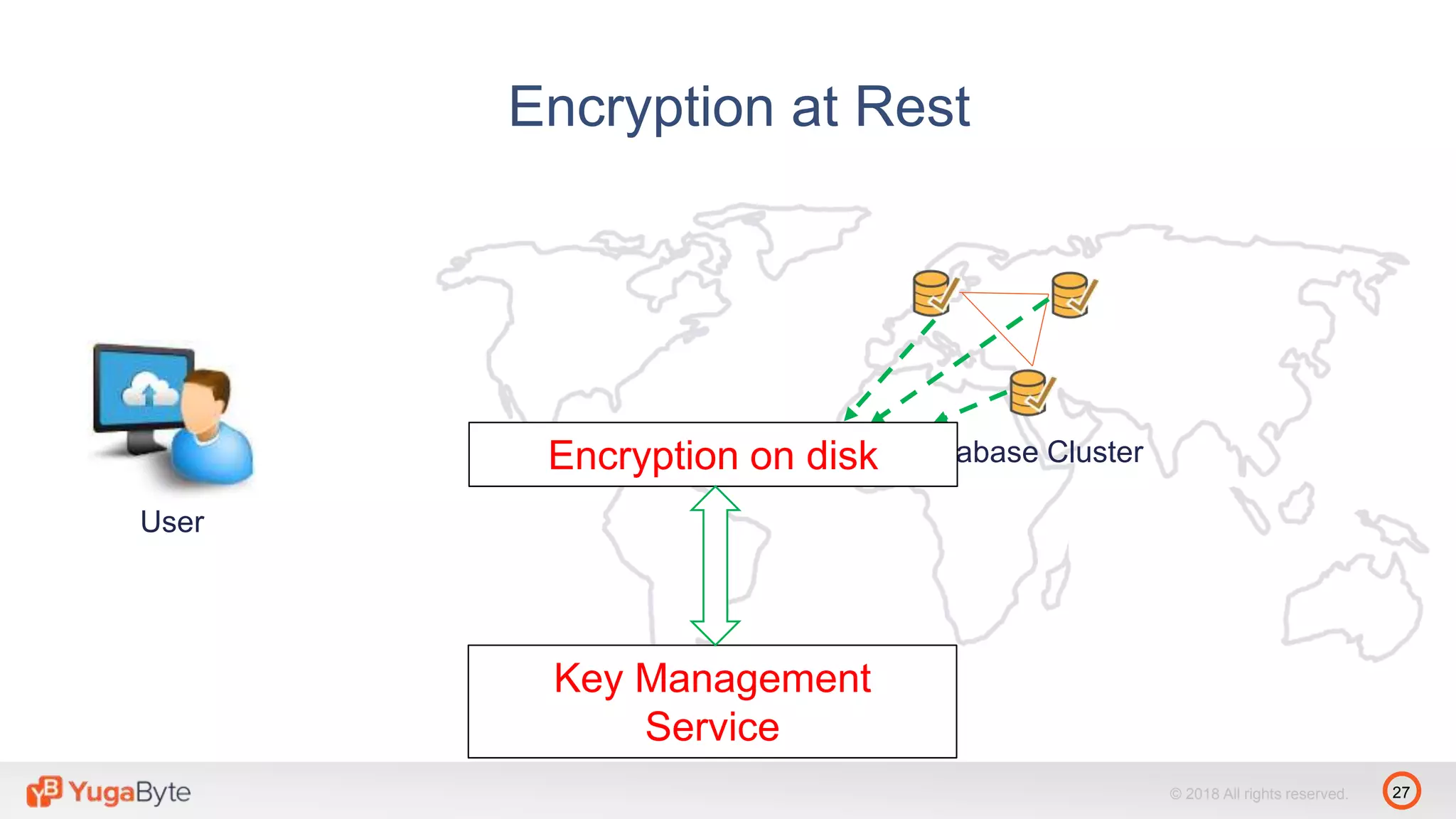
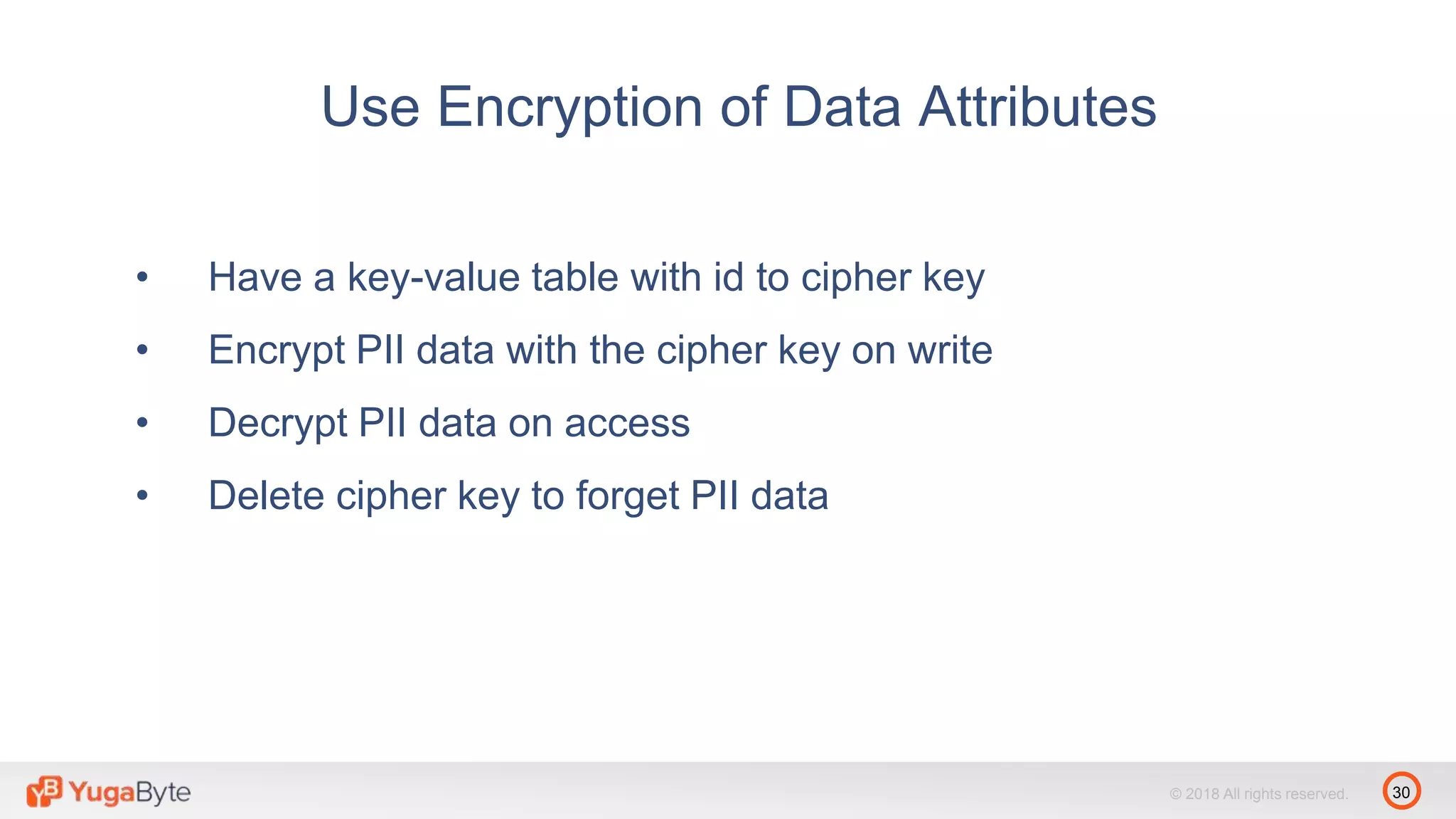
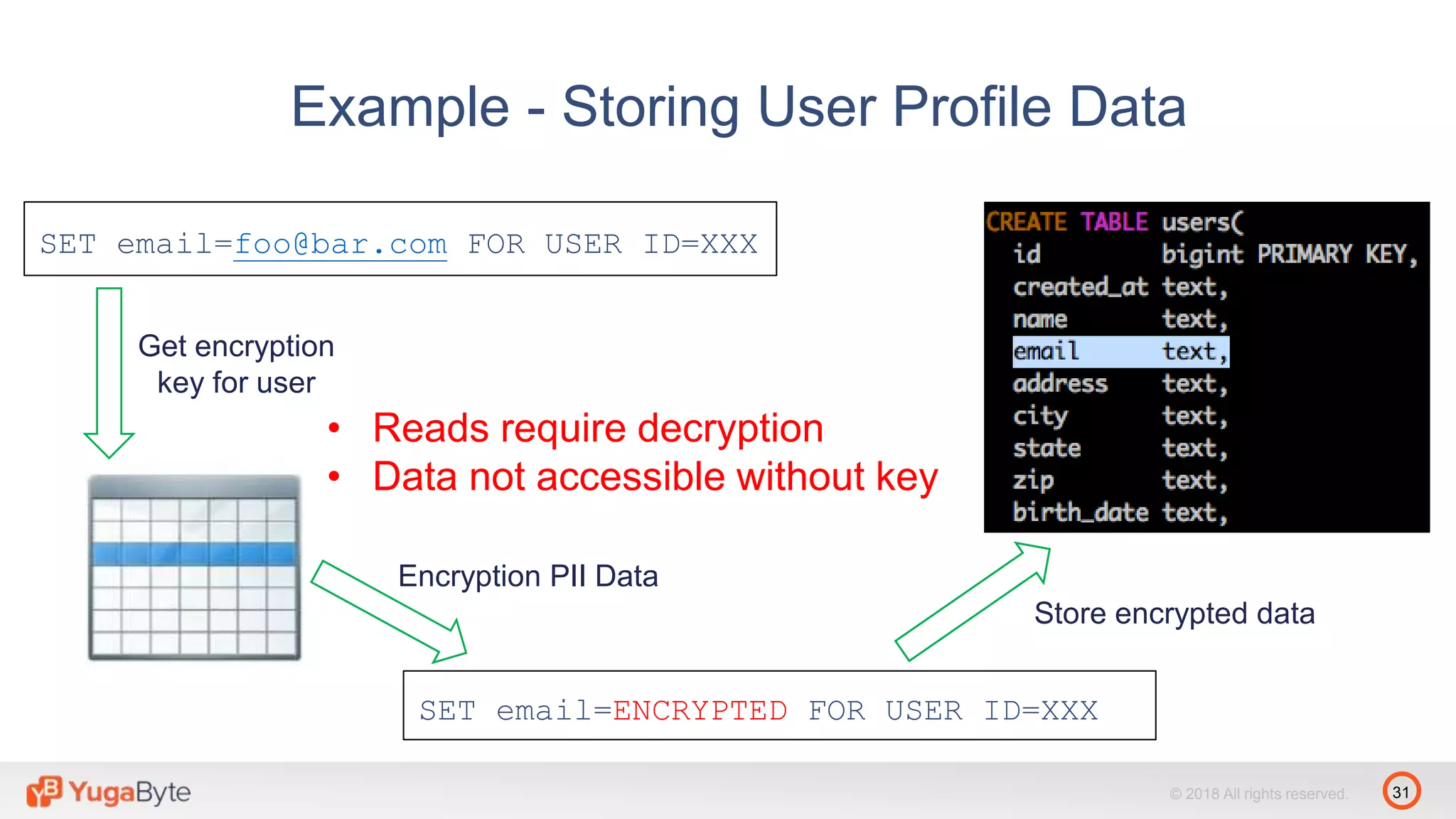
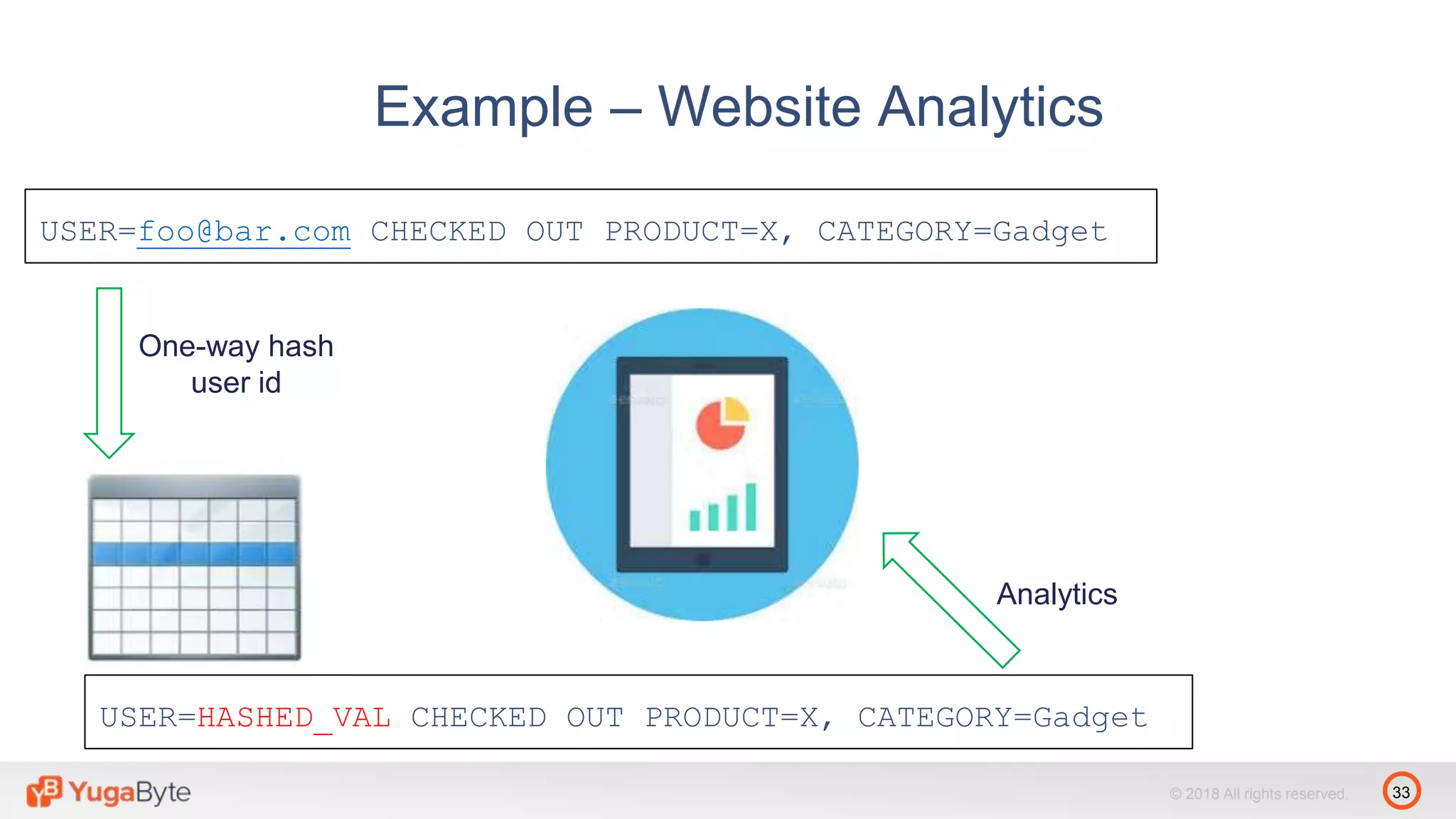
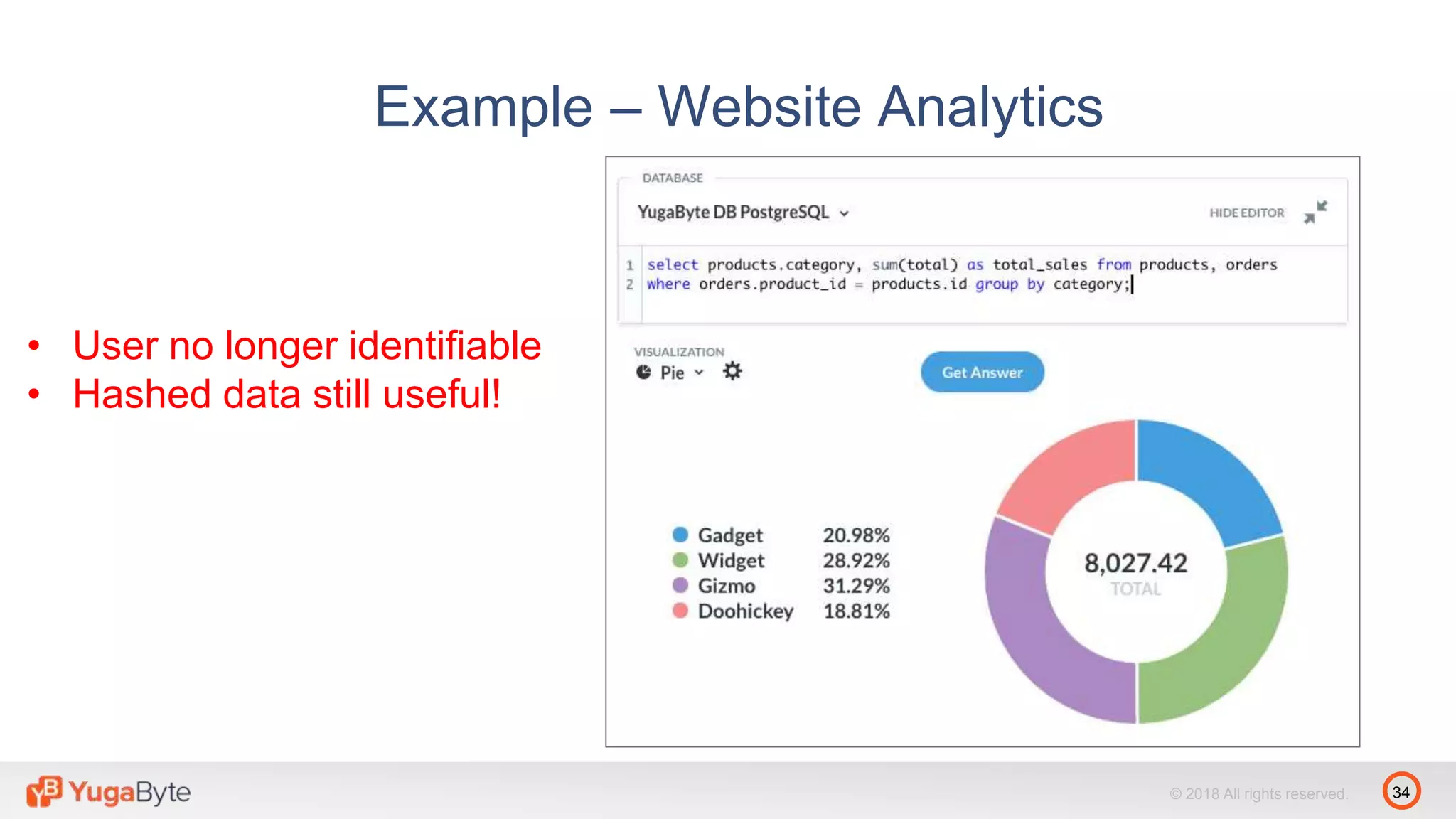
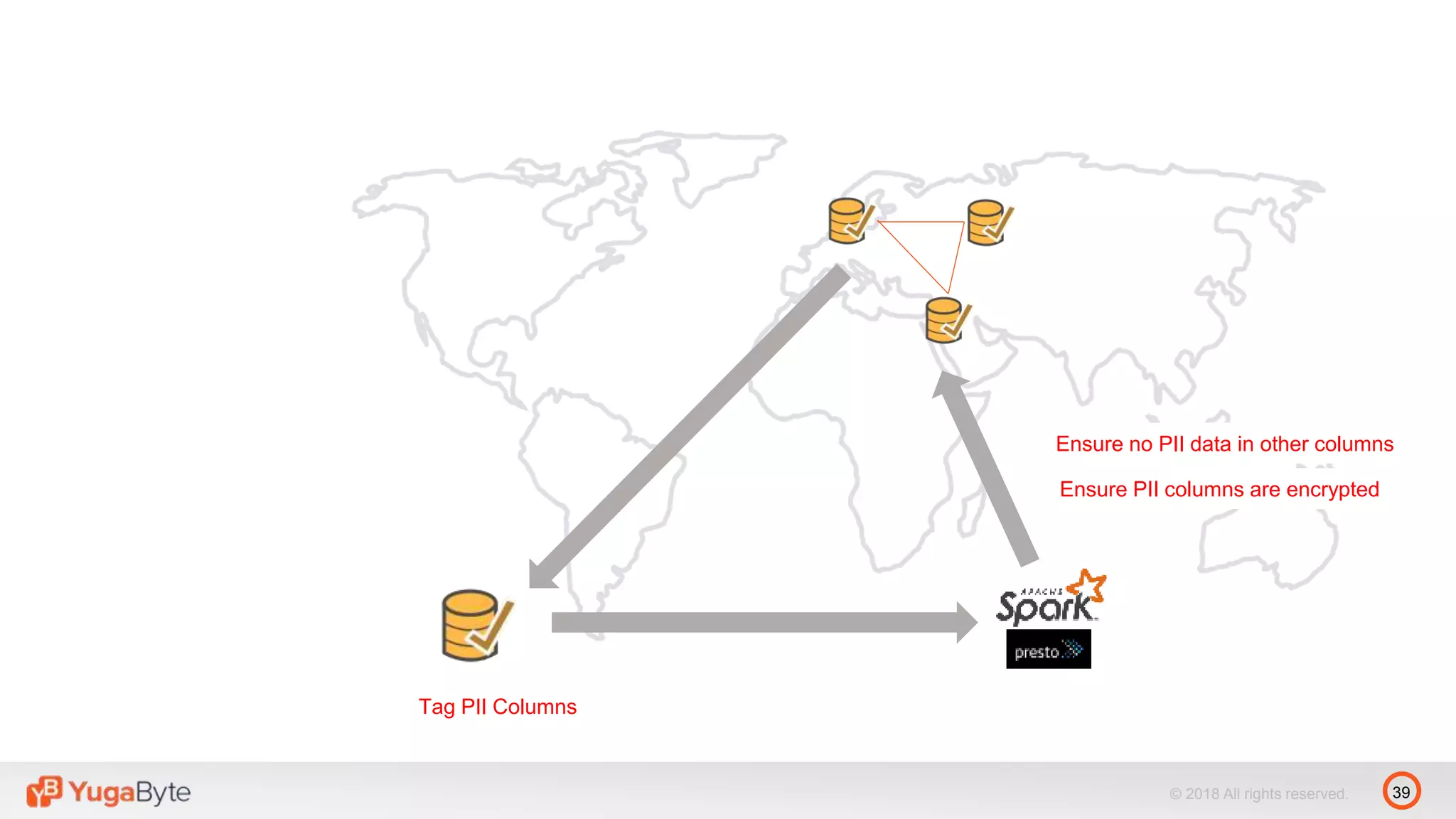
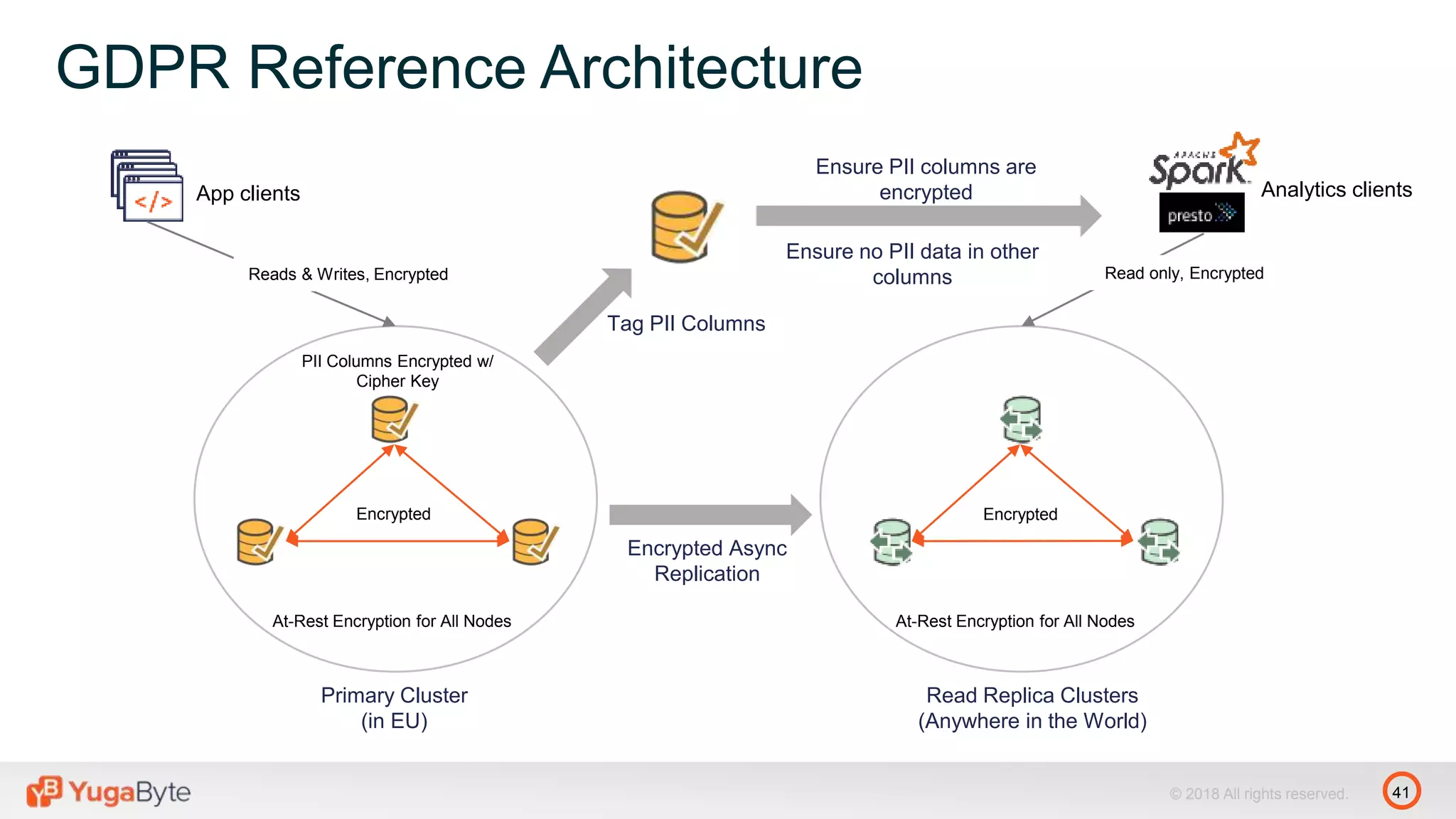
The document discusses YugabyteDB, a transactional database designed for high-performance cloud services that comply with the General Data Protection Regulation (GDPR). It highlights key GDPR requirements such as user consent, data privacy, the right to be forgotten, and data access on demand, and explains how YugabyteDB accommodates these through features like data encryption, geo-partitioning, and compliance checks. The document emphasizes the importance of secure data handling practices and provides architectural insights for maintaining GDPR compliance while managing personal data.