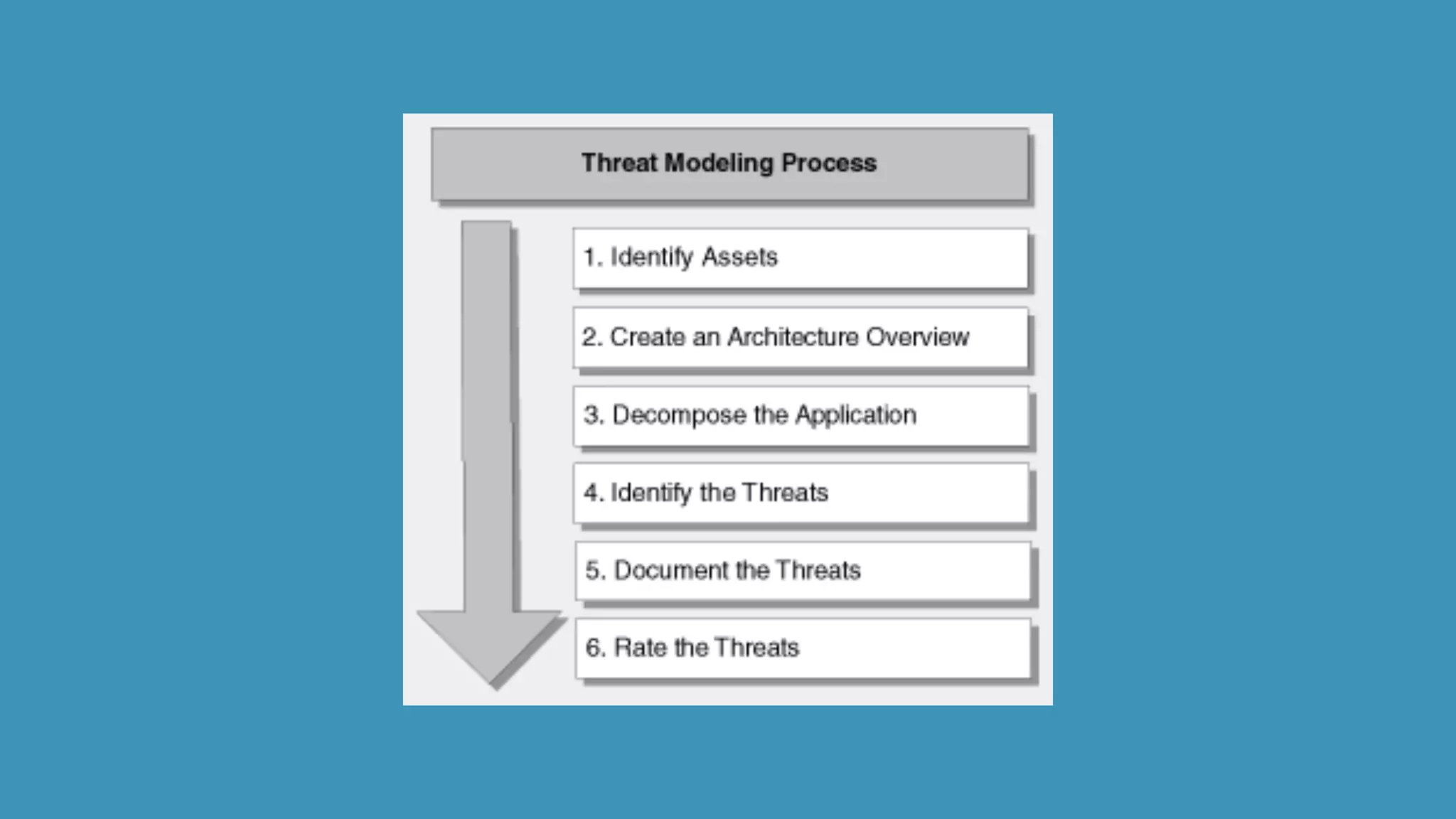
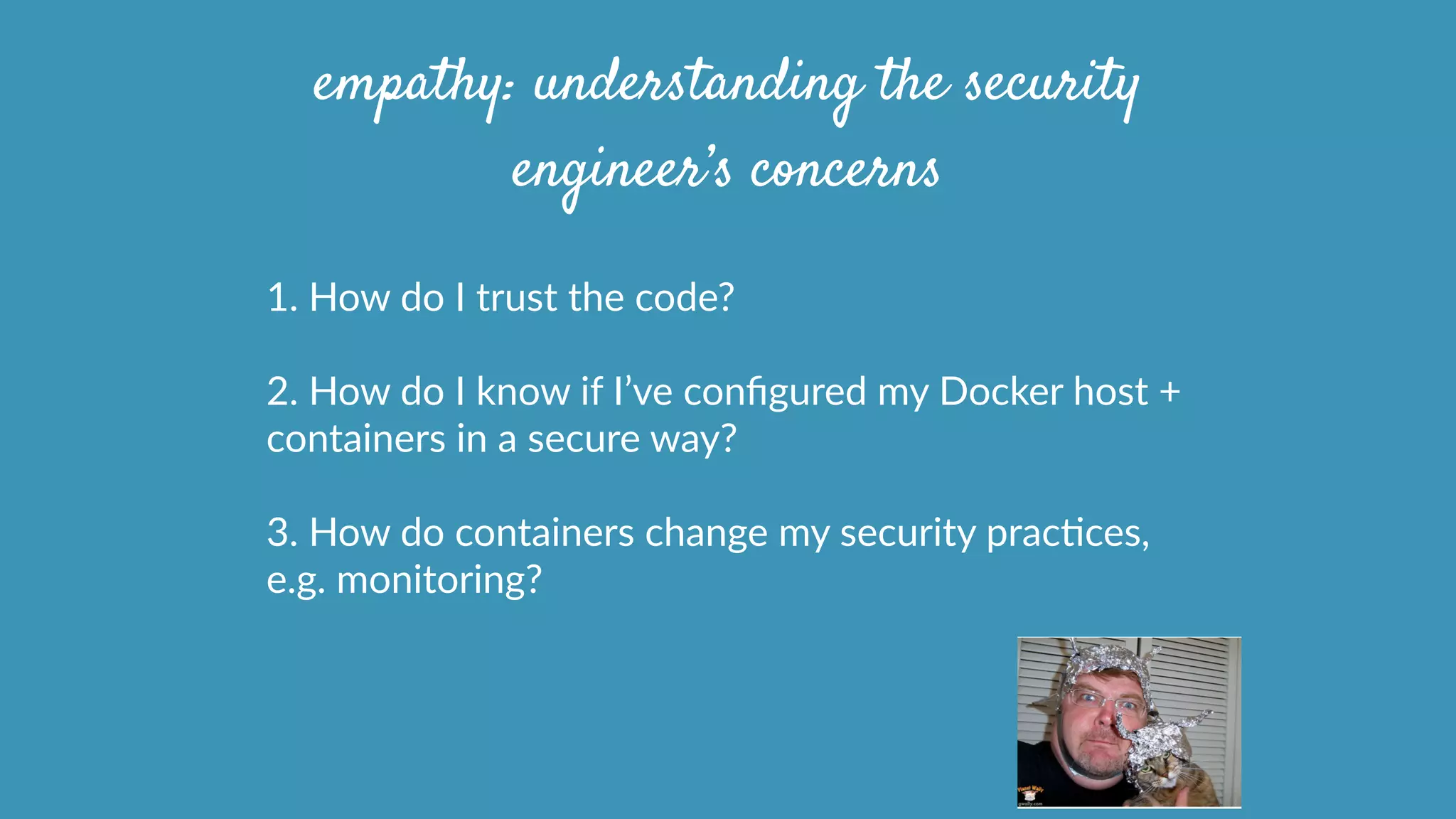
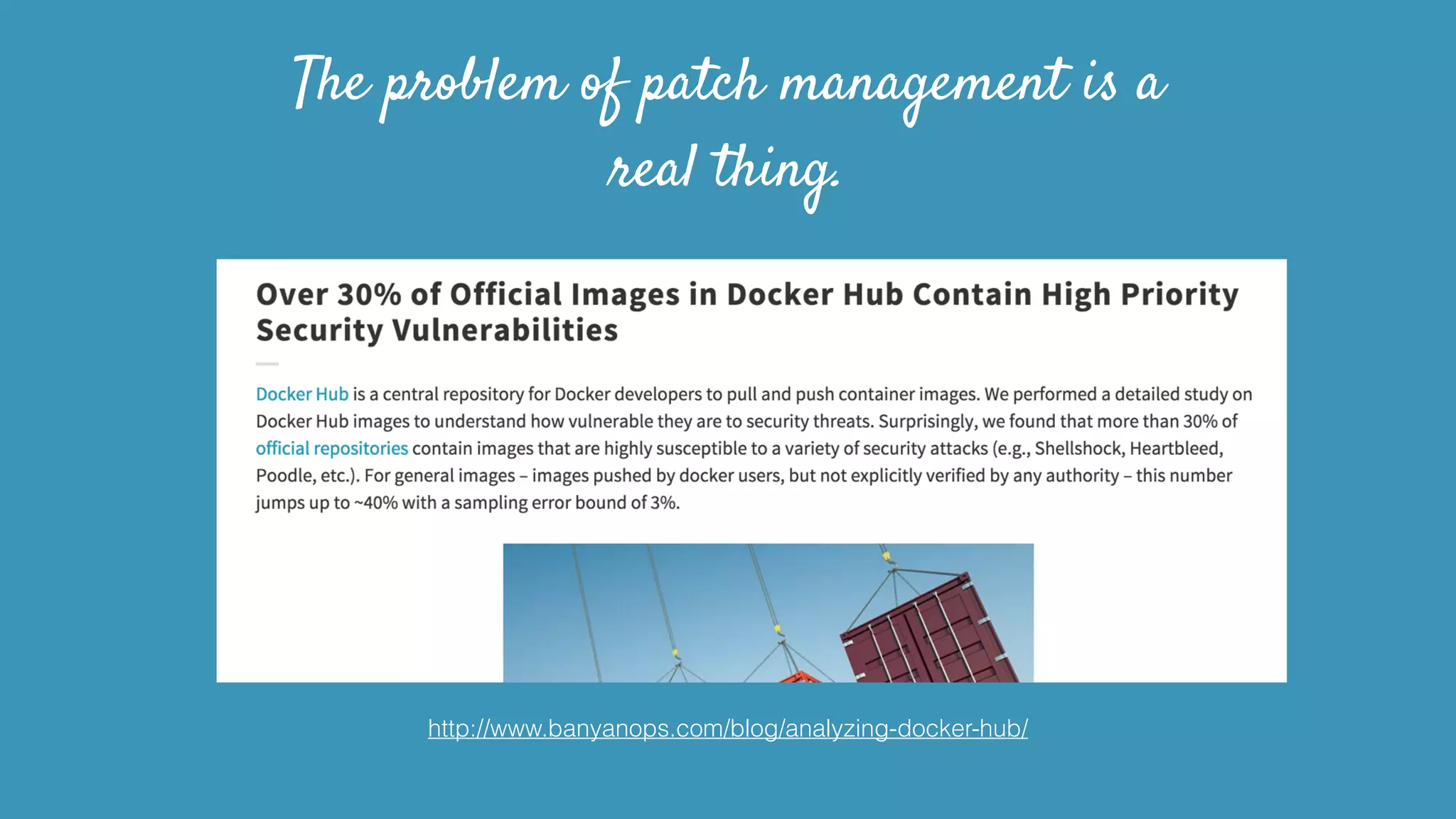
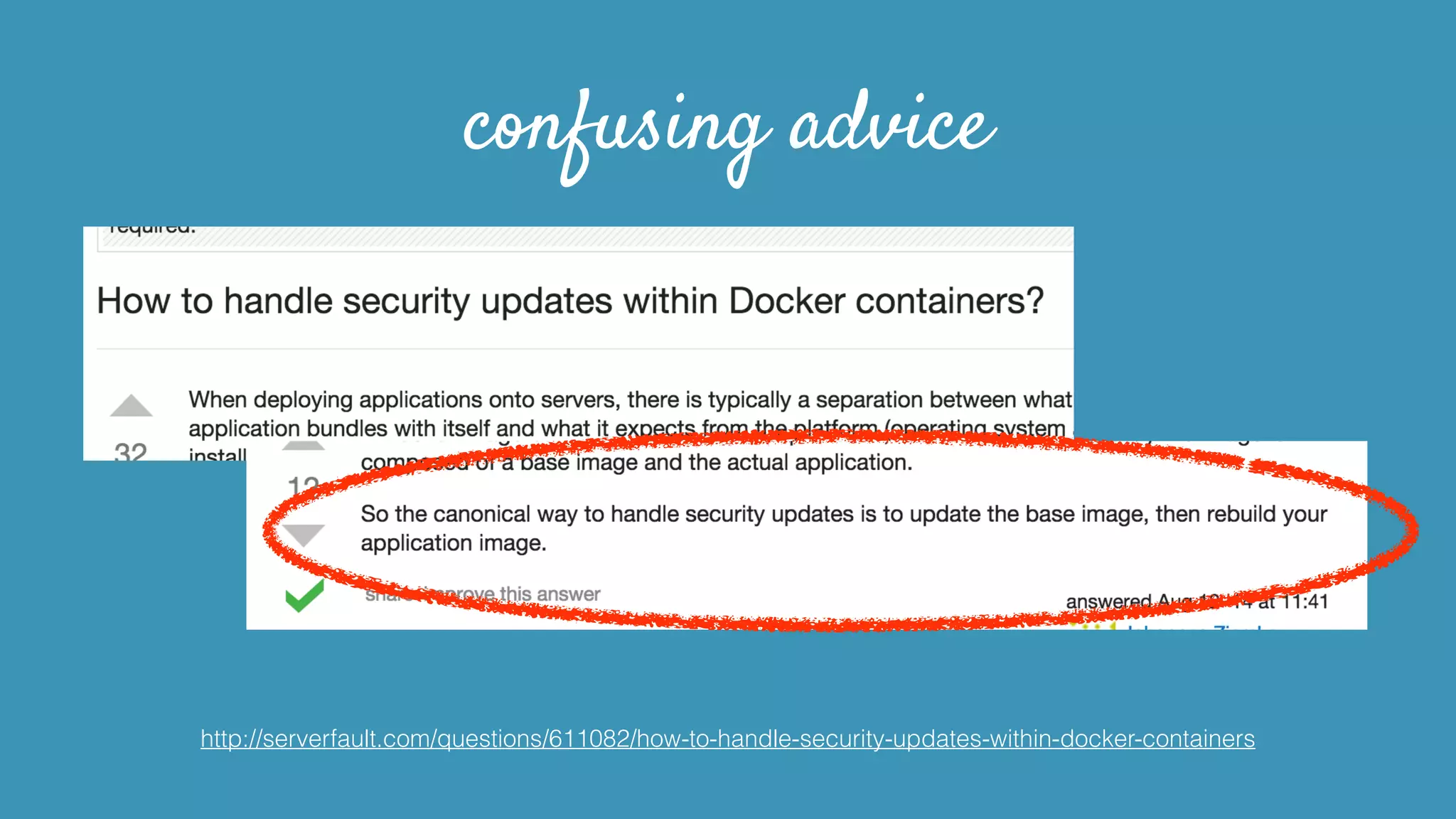
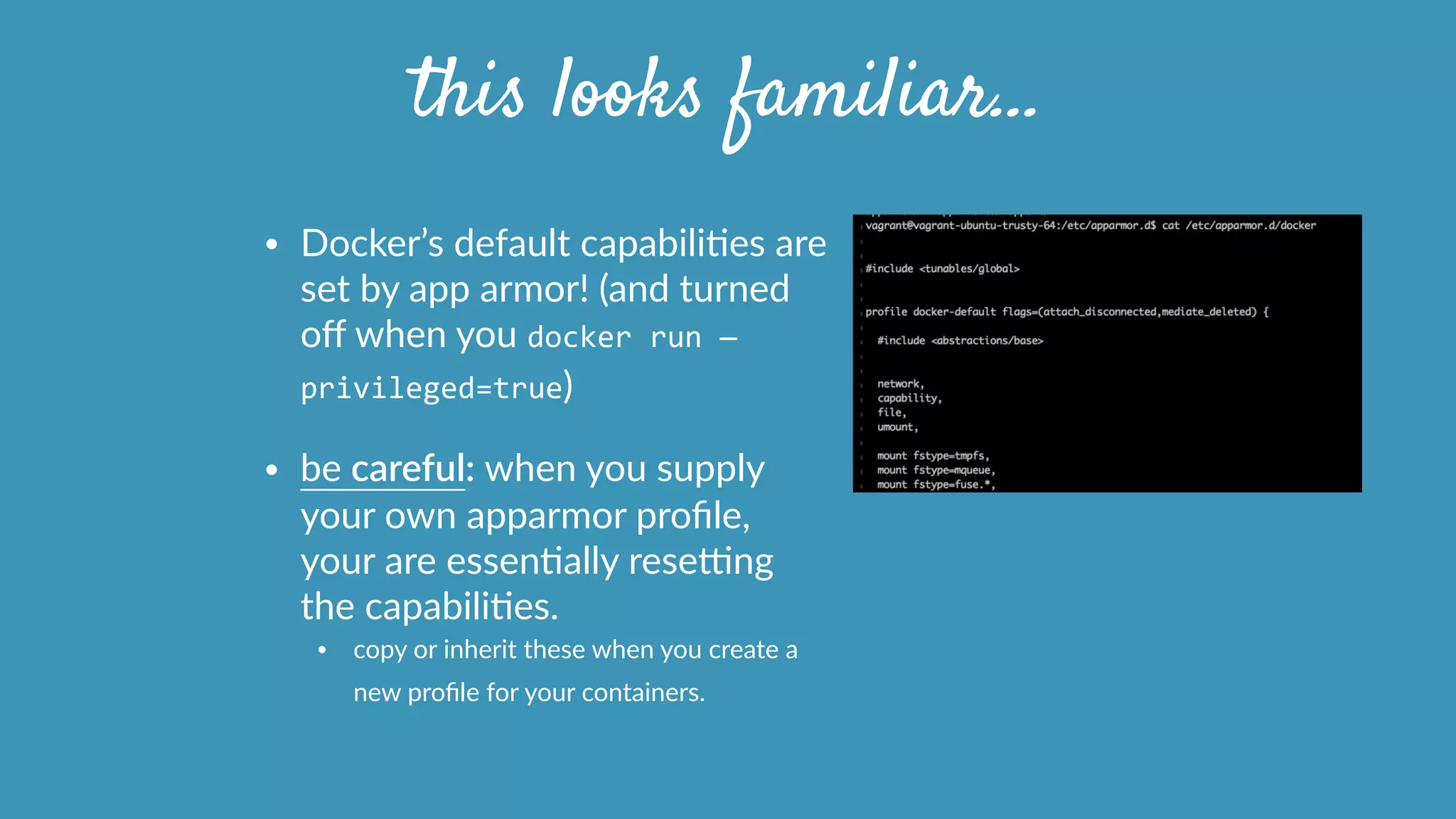
This document discusses strategies for securely operating Docker containers. It begins by acknowledging valid security concerns with Docker and advocating understanding threat models and limitations. The document then explores issues of trust in Docker images and potential solutions like auditing tools and private registries. It outlines opportunities to automate security configuration checks and generate AppArmor profiles. Finally, it presents a vision for a registry of security profiles that could reduce the burden of container hardening. Overall, the document takes an empathetic approach to security concerns while highlighting practical steps and potential technical improvements.













![best practices,
hardening, &
secure
configurations
]](https://image.slidesharecdn.com/dockersecuritytalk-150529130637-lva1-app6891/75/Operating-Docker-23-2048.jpg)





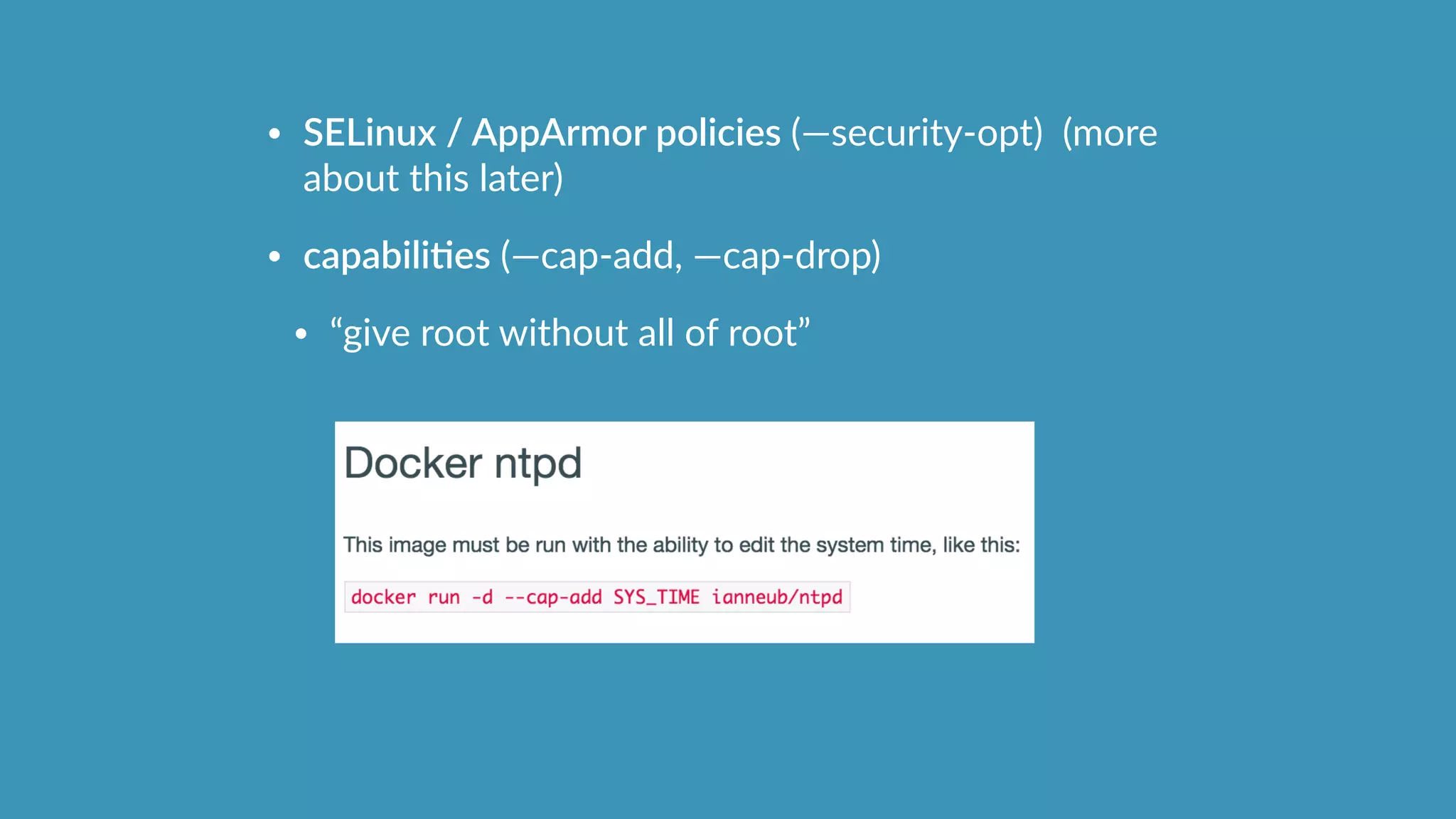

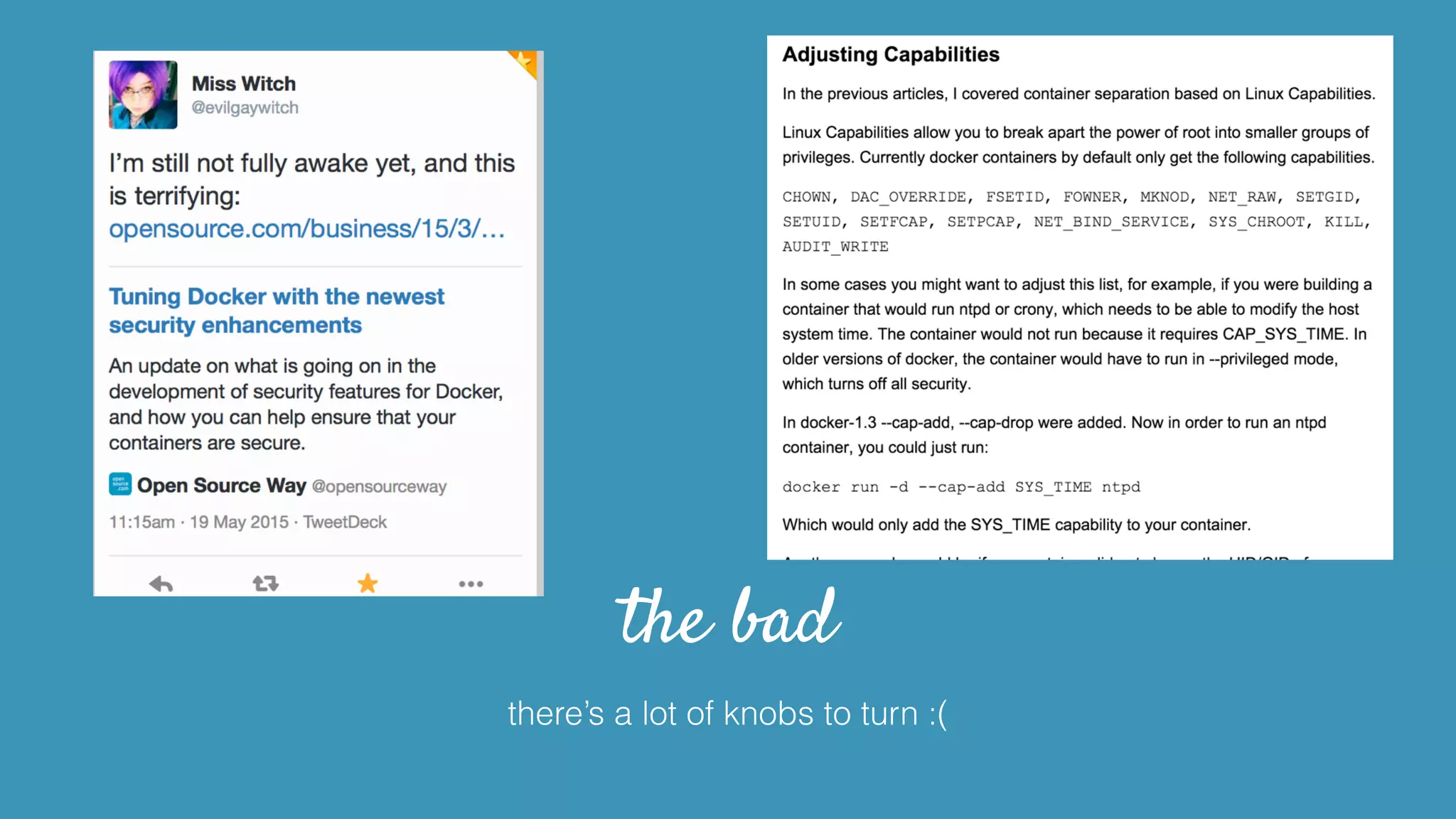



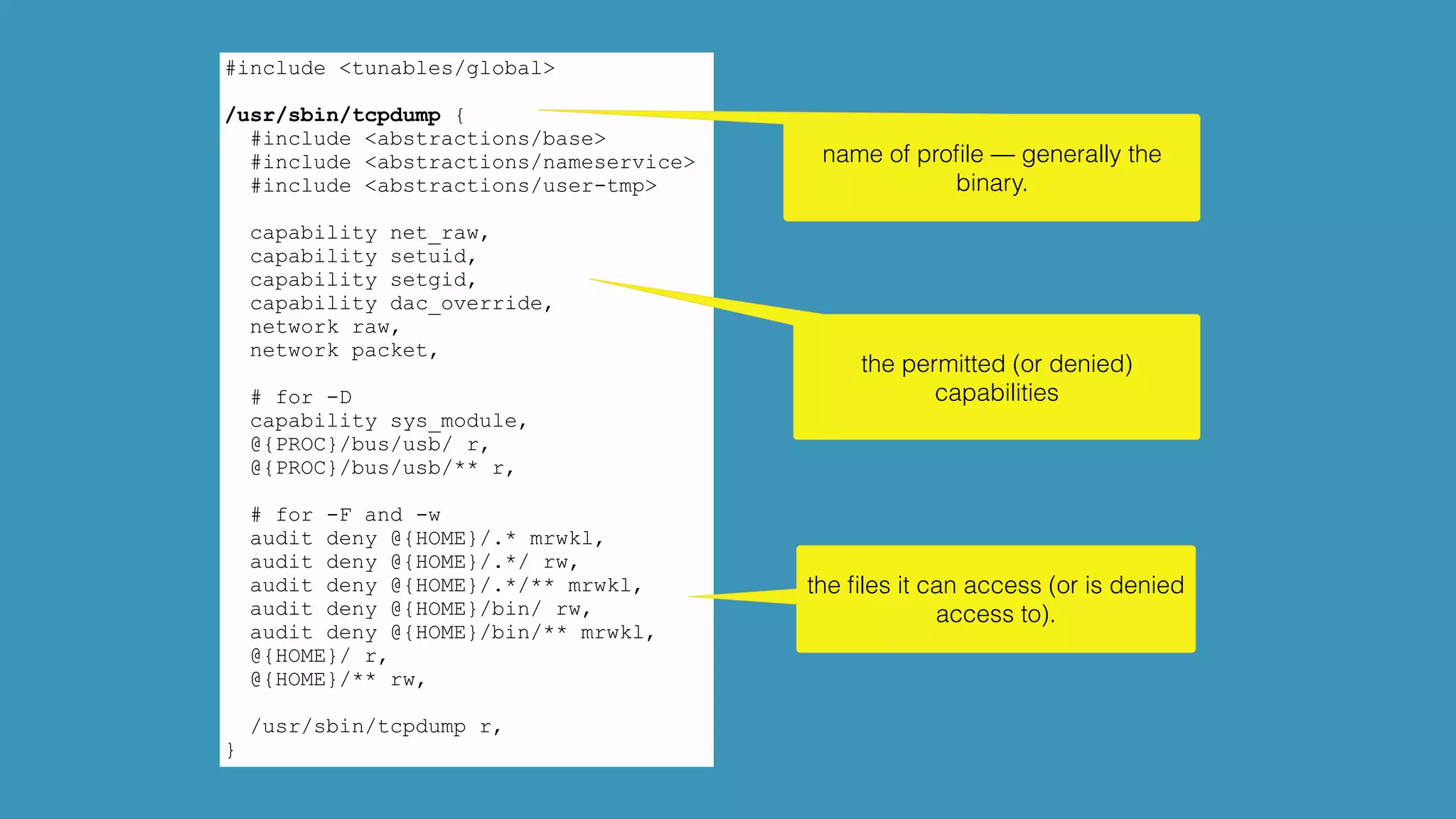

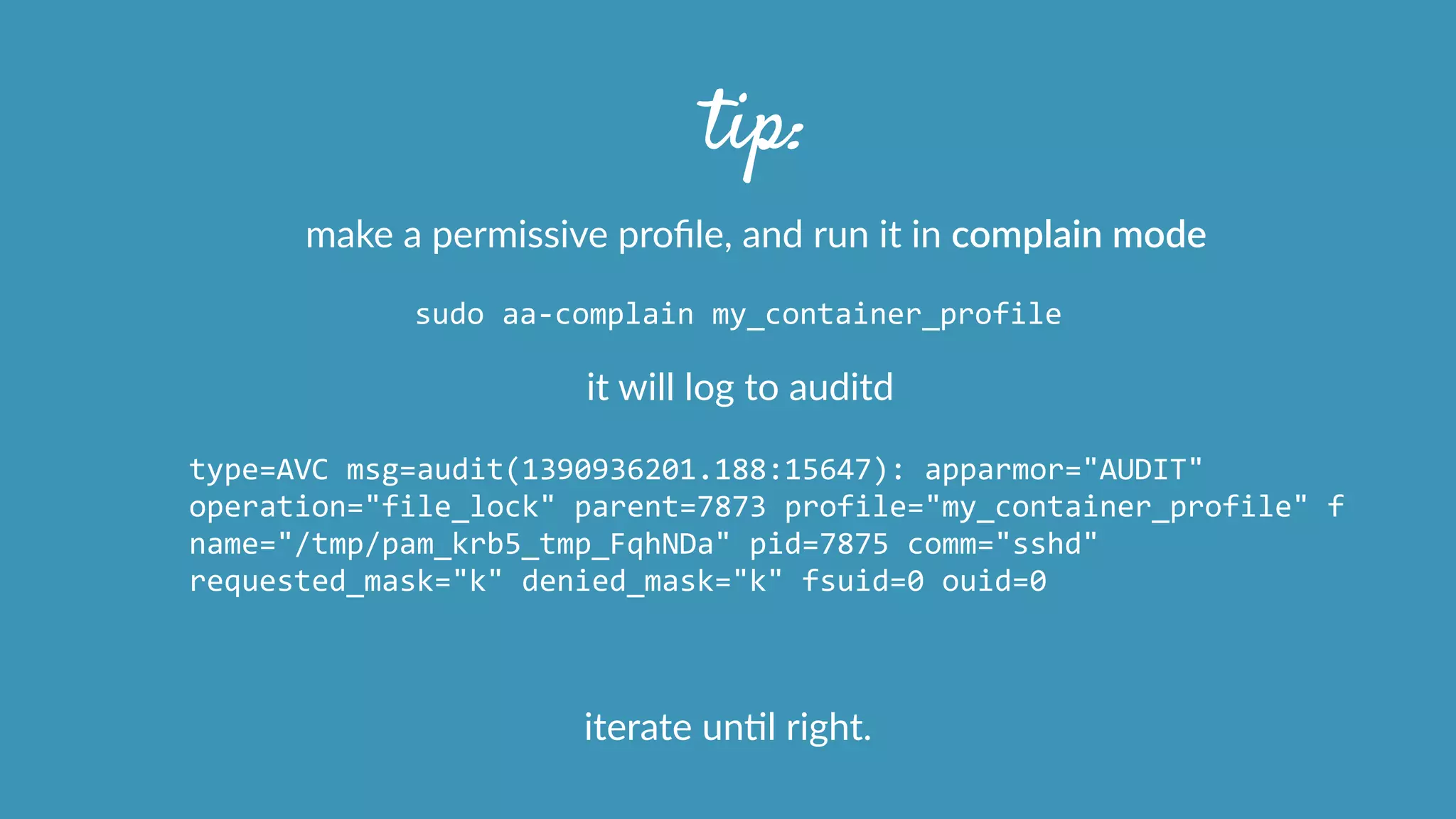

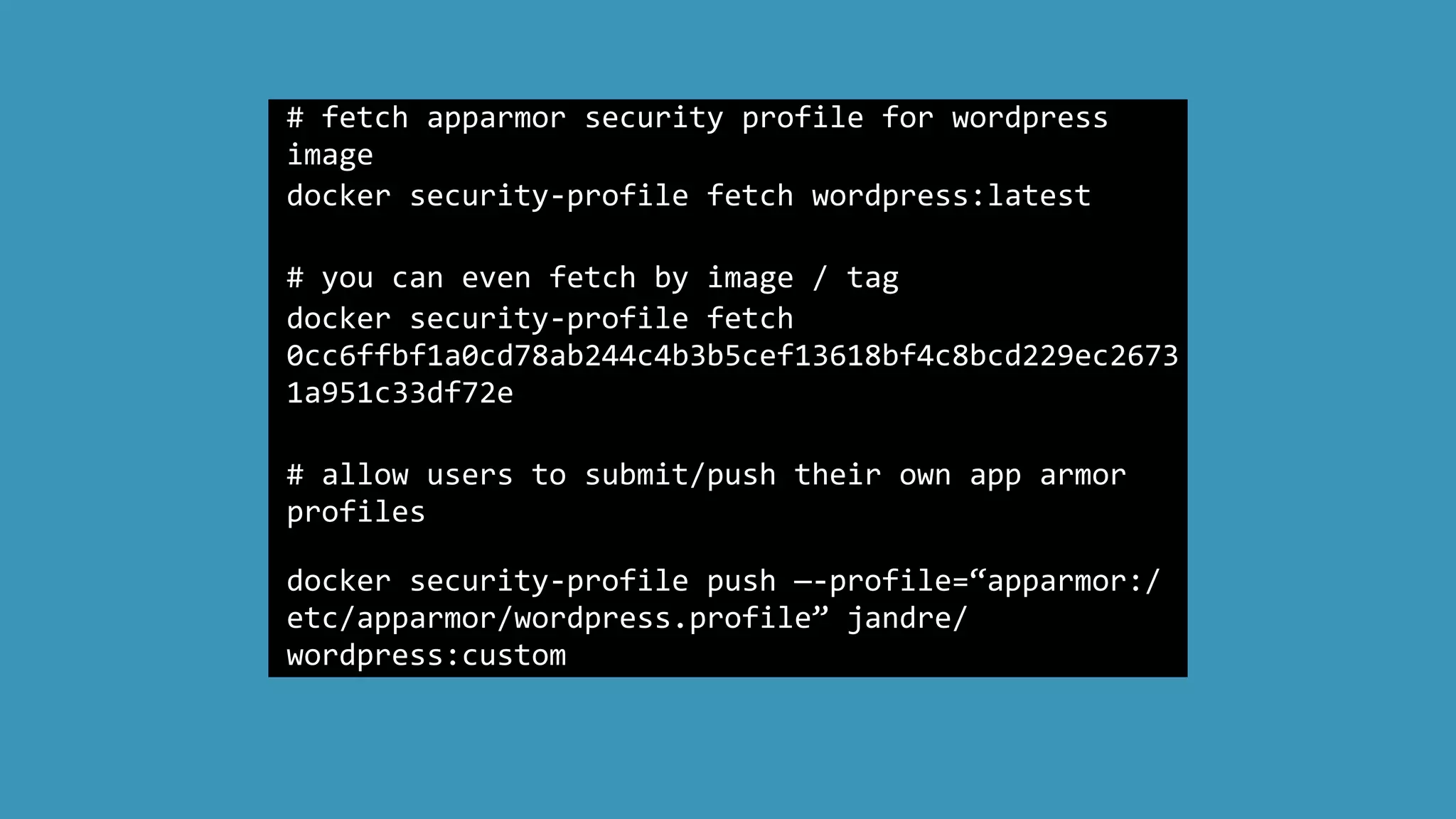
![tip:
use aa-‐logprof to generate the apparmor profiles
automagically?
aa-‐logprof
[
-‐d
/path/to/profiles
]
[
-‐f
/path/to/logfile
]
!! don’t use these without manual review and ediHng !!
http://manpages.ubuntu.com/manpages/natty/man8/aa-‐logprof.8.html](https://image.slidesharecdn.com/dockersecuritytalk-150529130637-lva1-app6891/75/Operating-Docker-45-2048.jpg)