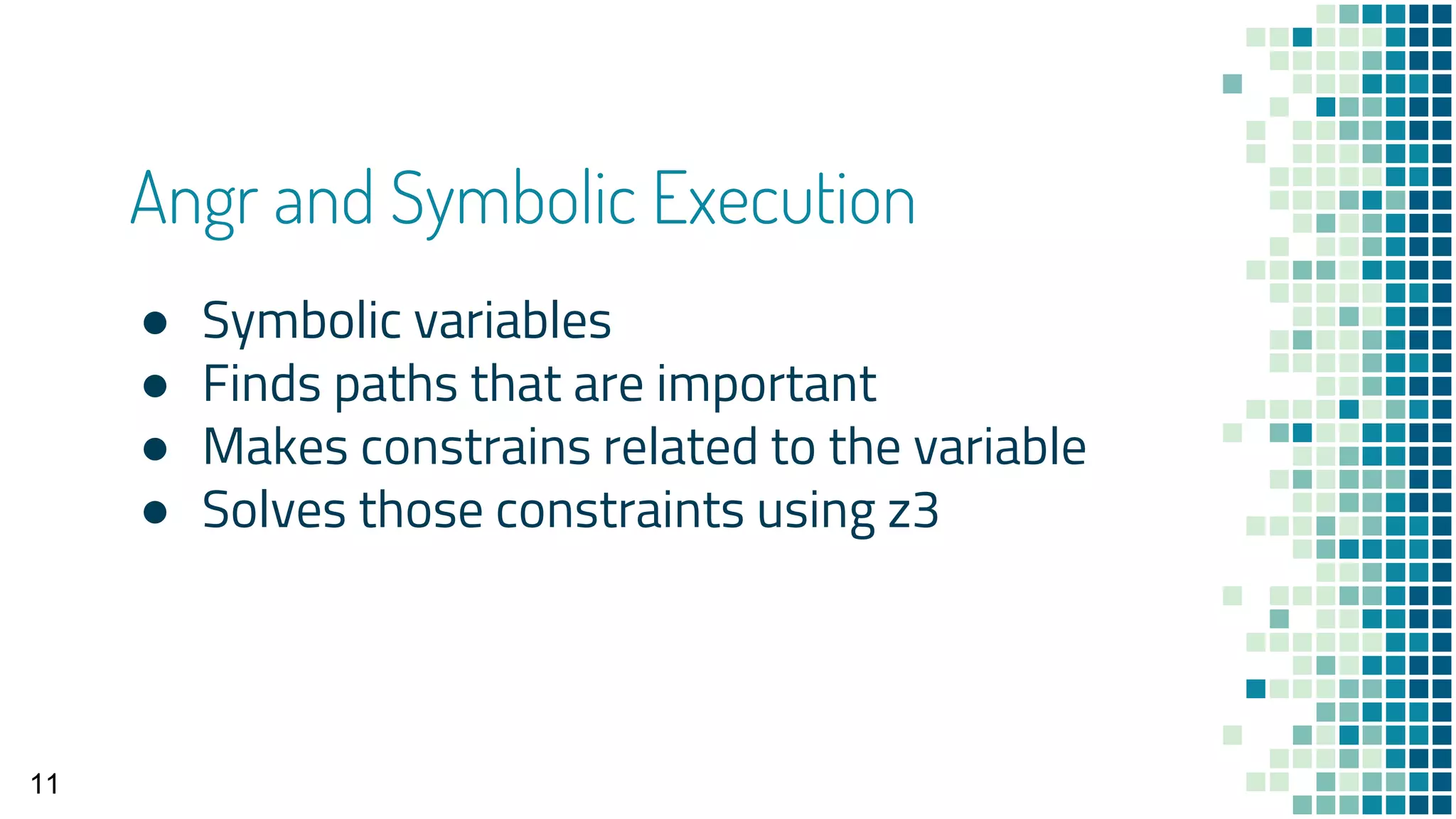
The document presents a talk by Siddharth M on dynamic binary analysis using the angr framework, which automates analyzing executables to identify vulnerabilities efficiently. It covers the basics of binary analysis, the uses of angr including symbolic execution and hooking, and demonstrates its application with examples. Additionally, it highlights the benefits of using angr for reverse engineering tasks, emphasizing its open-source nature and various analytical capabilities.