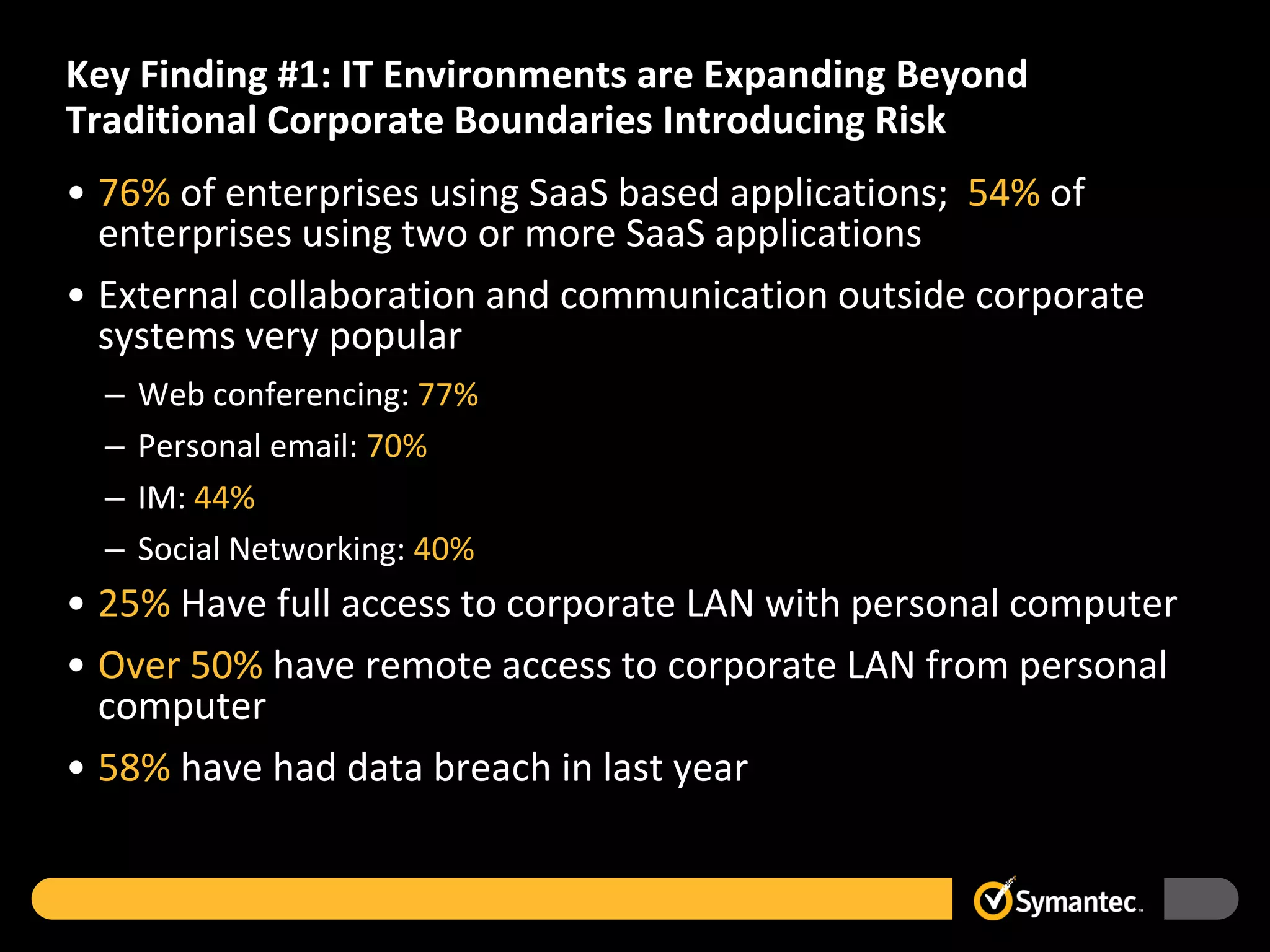
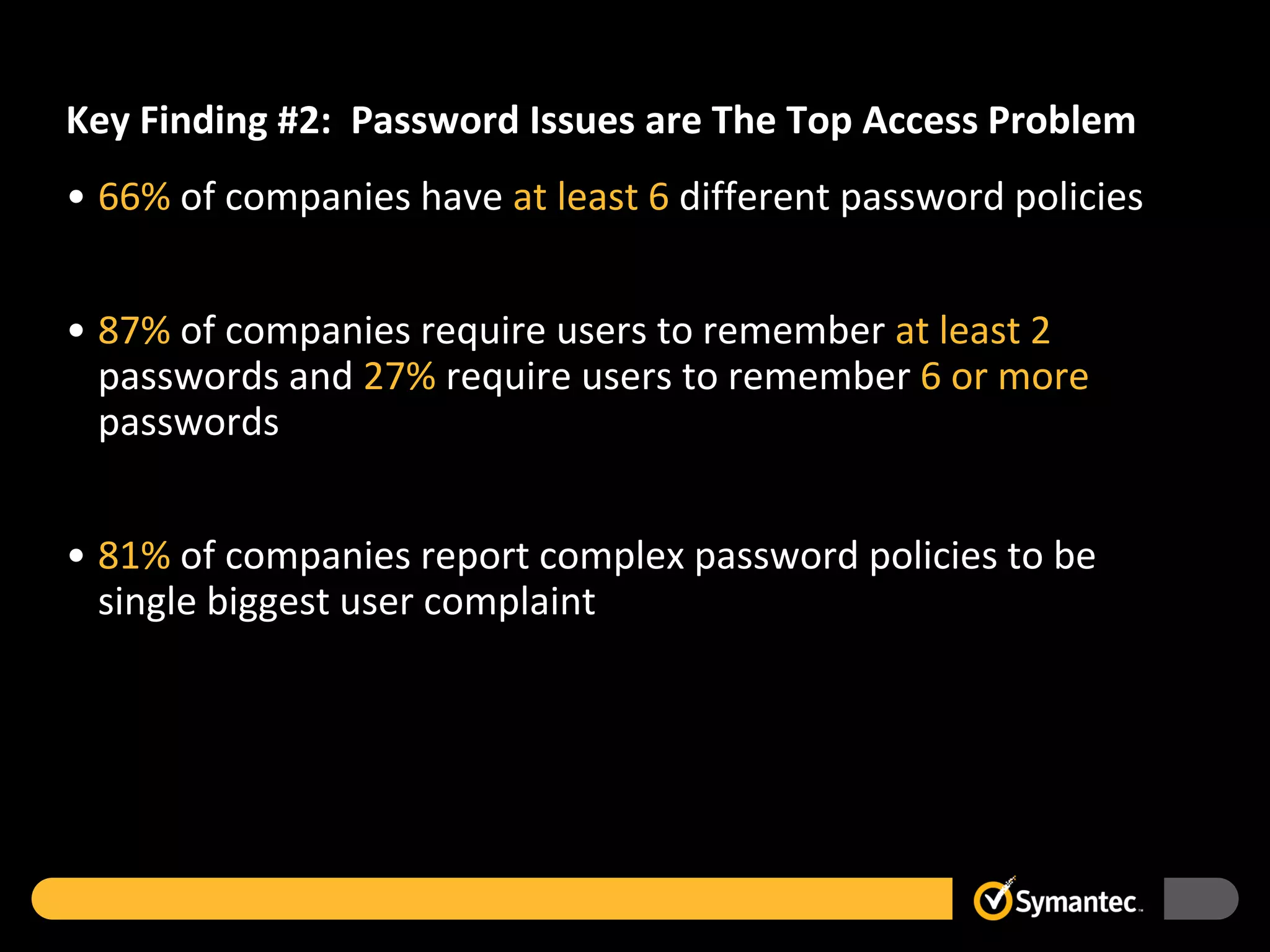
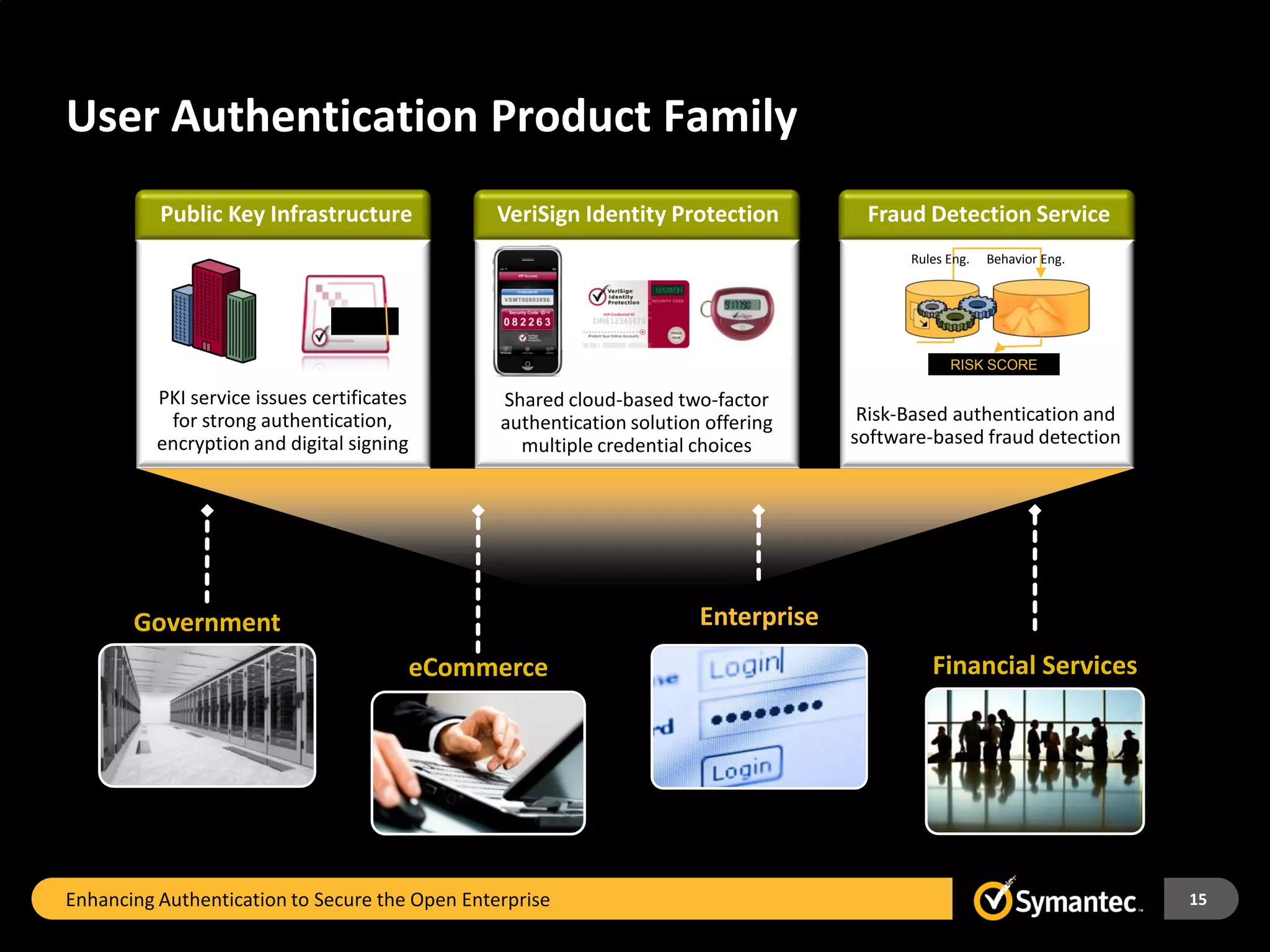
The Forrester Consulting study highlights the increasing risks in corporate IT environments due to the rise of cloud applications and remote work, with 58% of enterprises reporting data breaches in the past year. It identifies key challenges, including complex password issues and outdated perceptions about the cost of strong authentication, which hinder its widespread adoption. Recommendations include expanding strong authentication practices and reassessing technology implementations to better secure corporate networks.