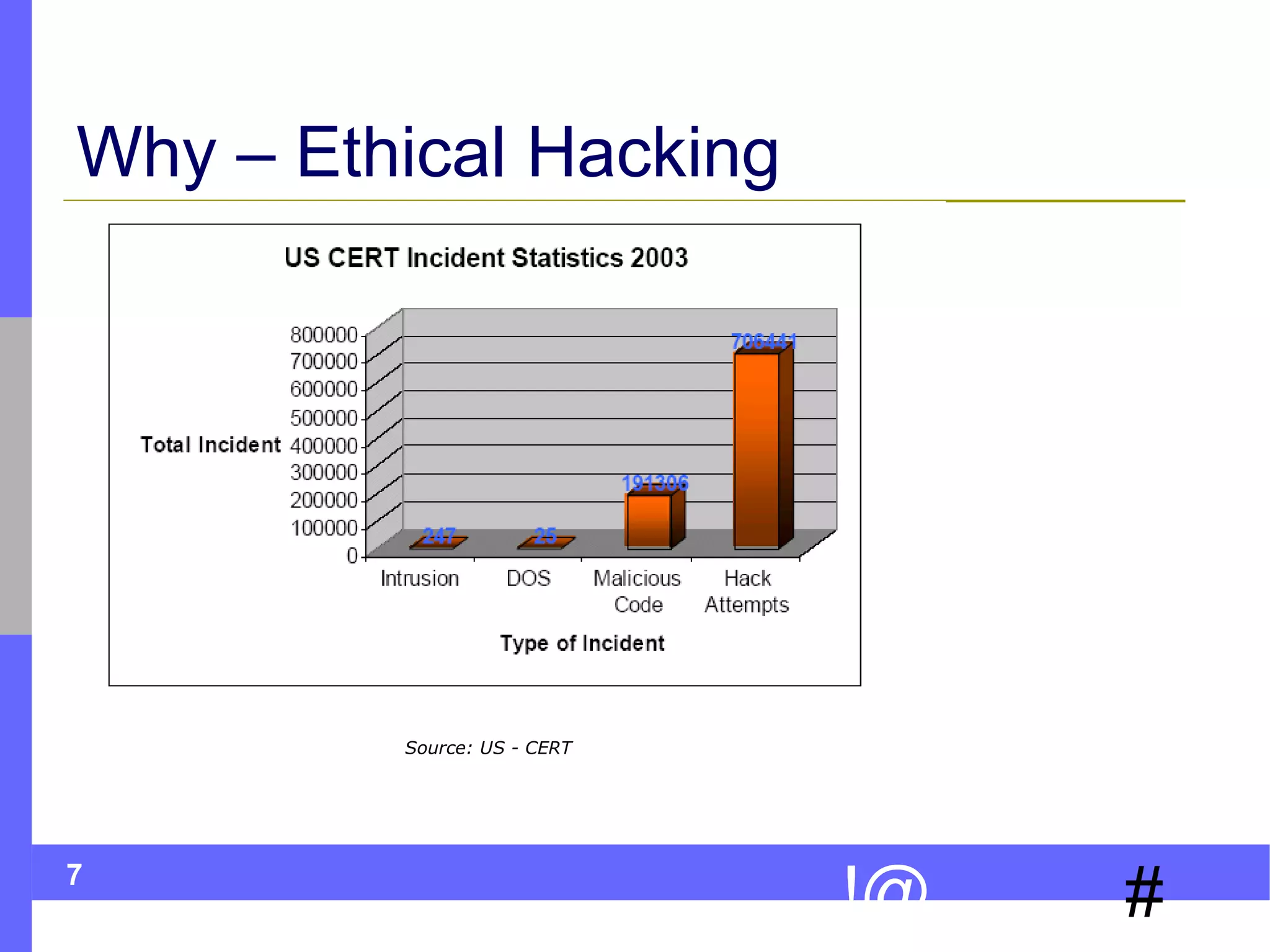
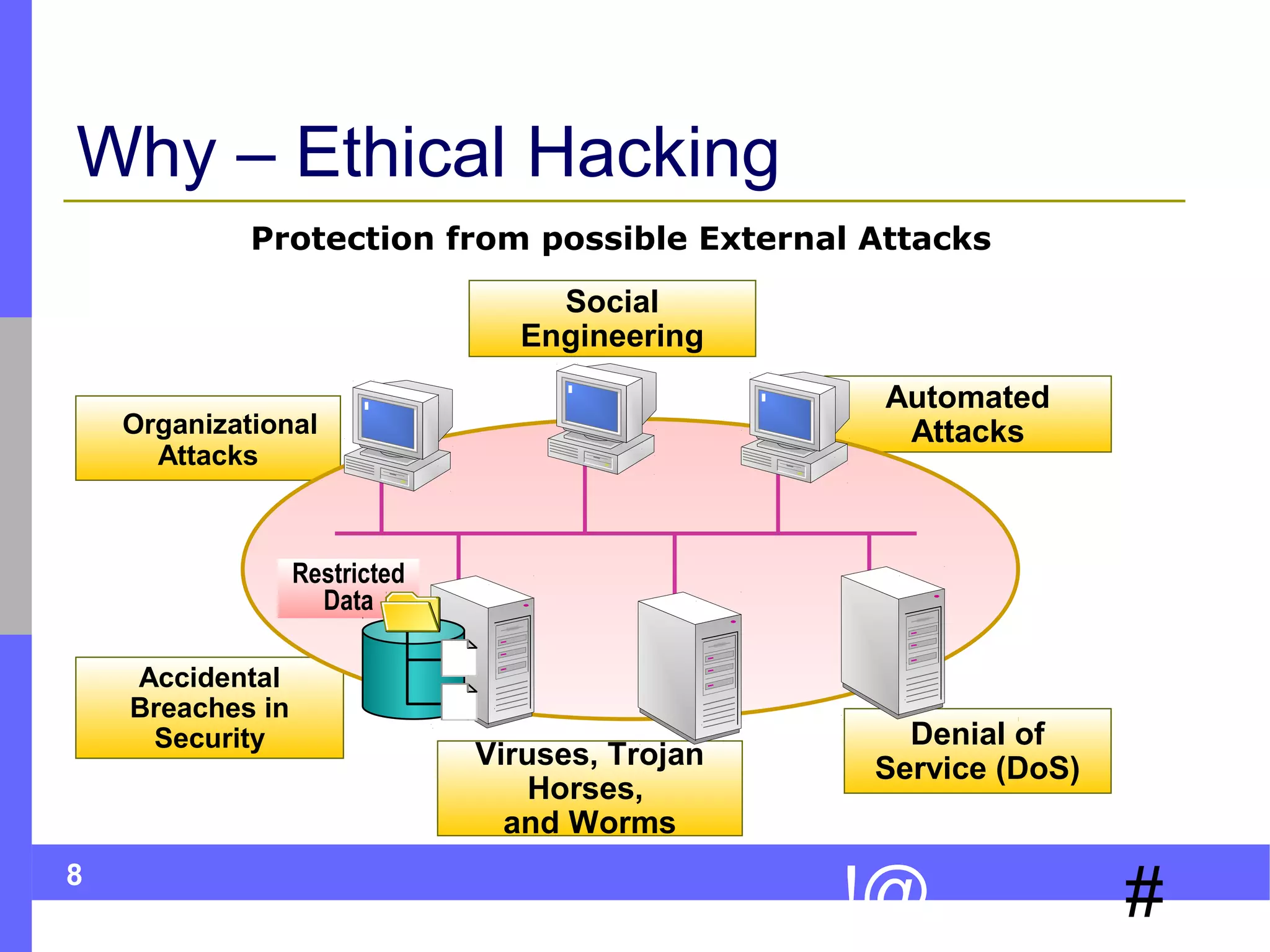
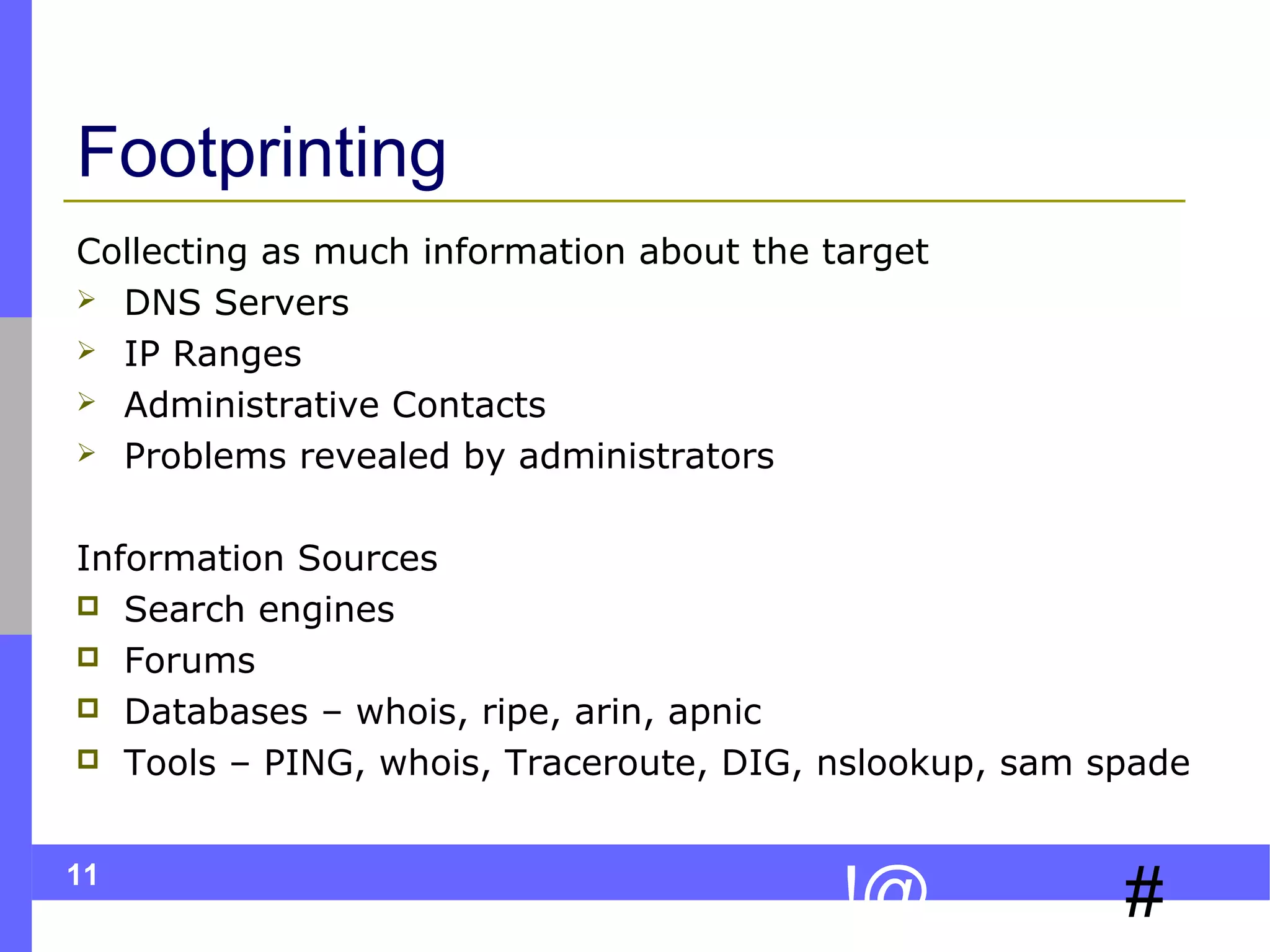
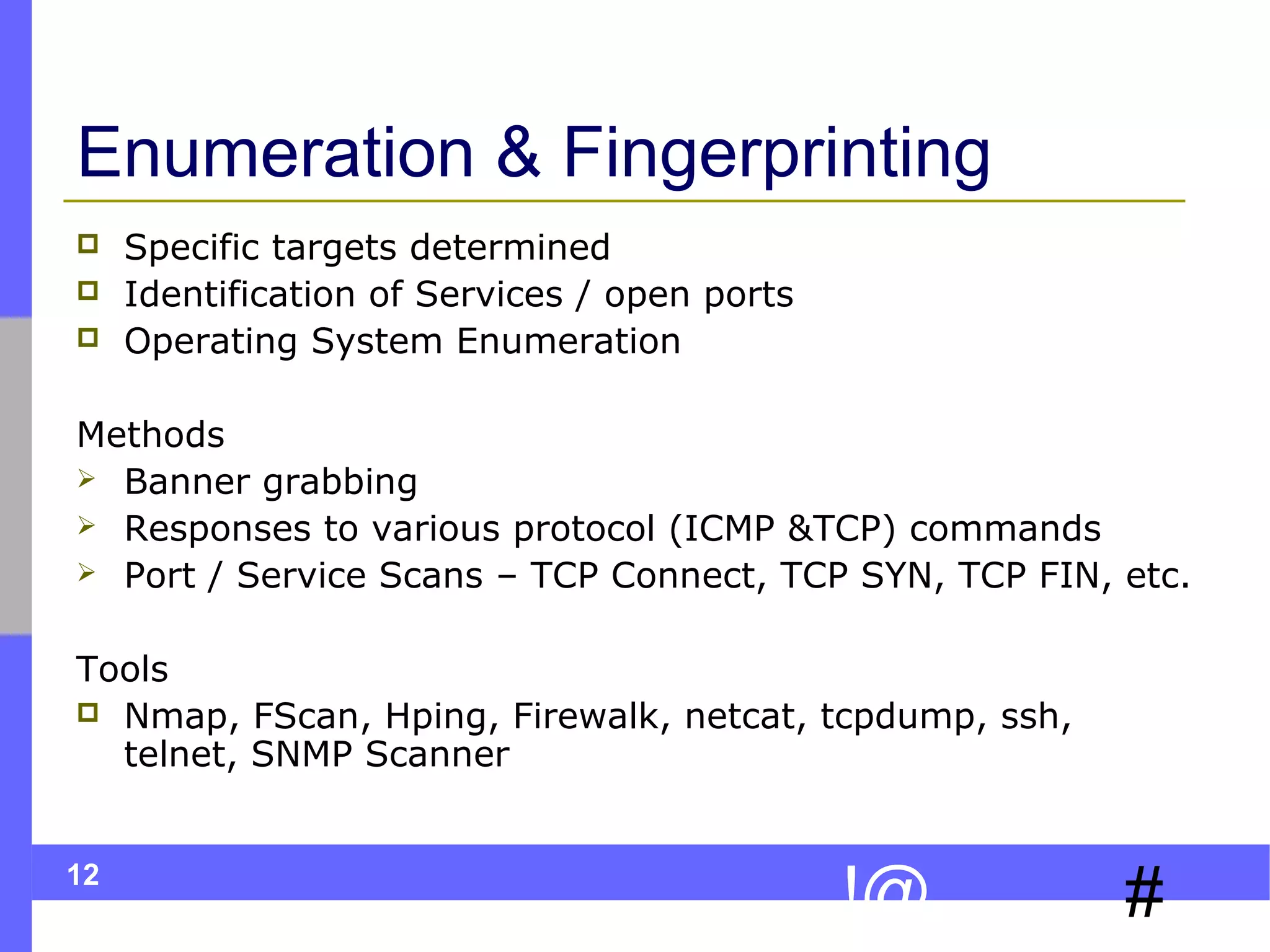
The document discusses ethical hacking, which involves legally testing a system's security vulnerabilities to help strengthen security. It describes the process of ethical hacking, including preparation, footprinting, enumeration and fingerprinting, identifying vulnerabilities, and attacking to exploit vulnerabilities. The goal is to help organizations identify and remedy security flaws by emulating real attacks but in a controlled, non-destructive manner.