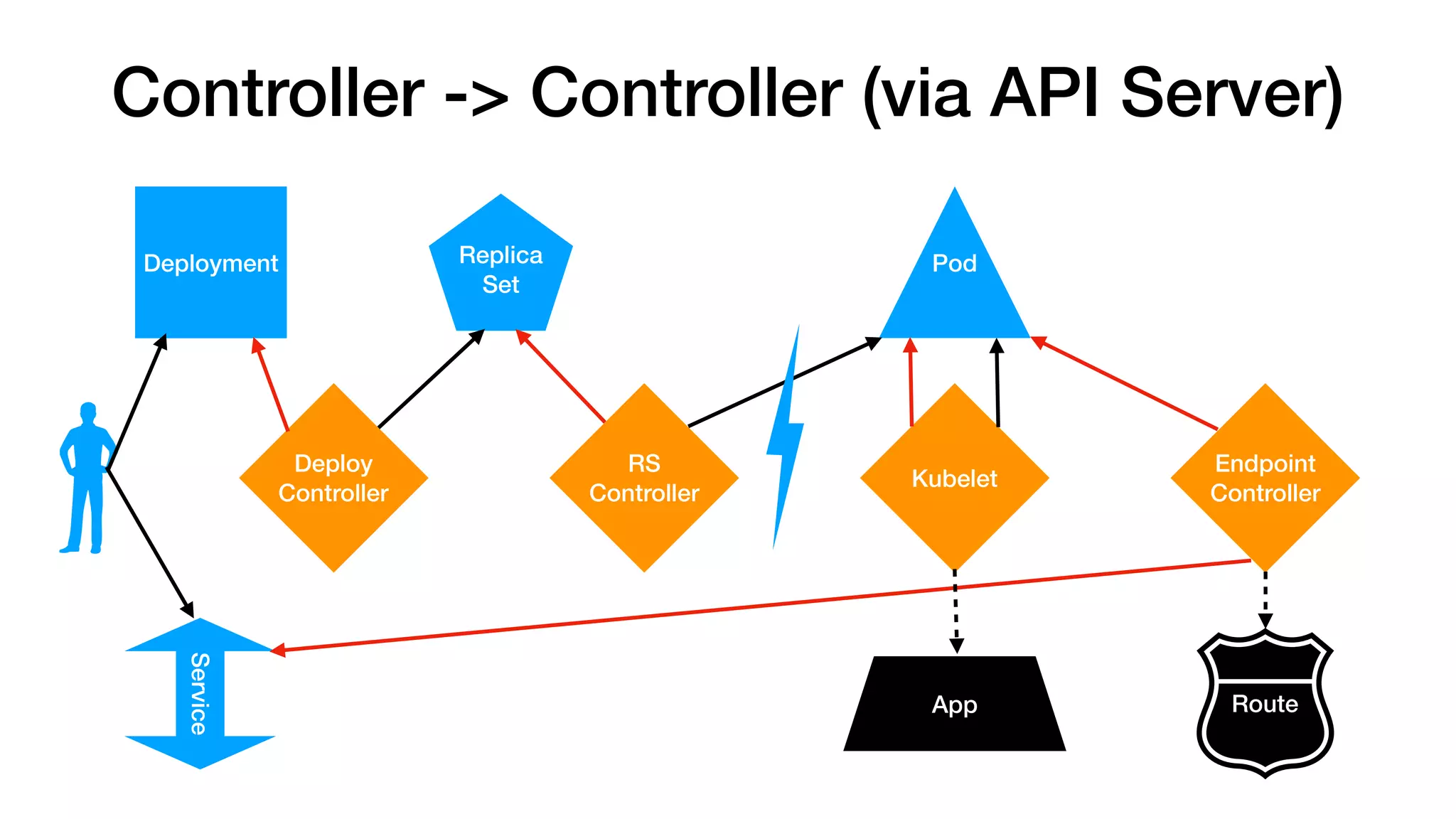
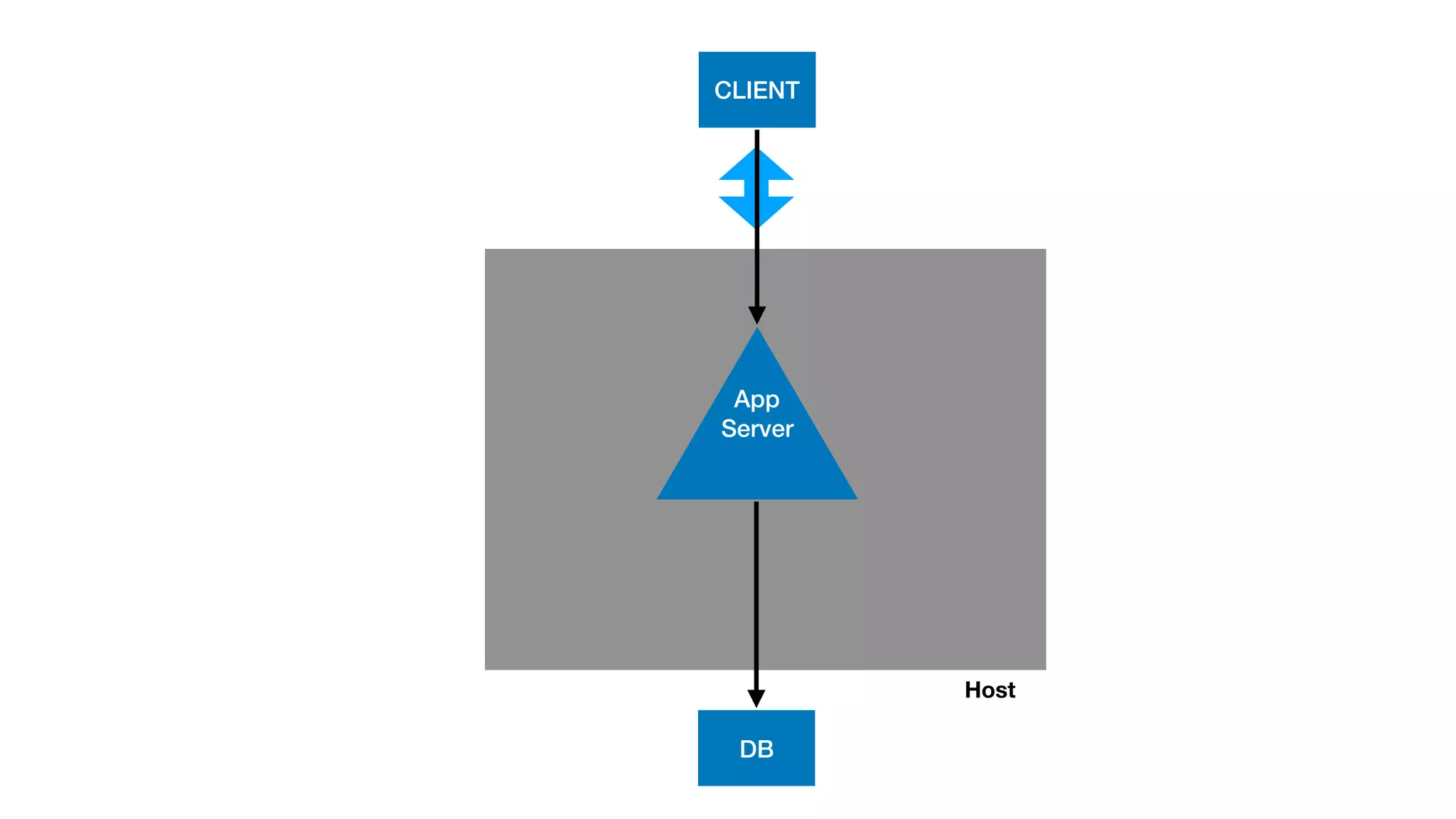
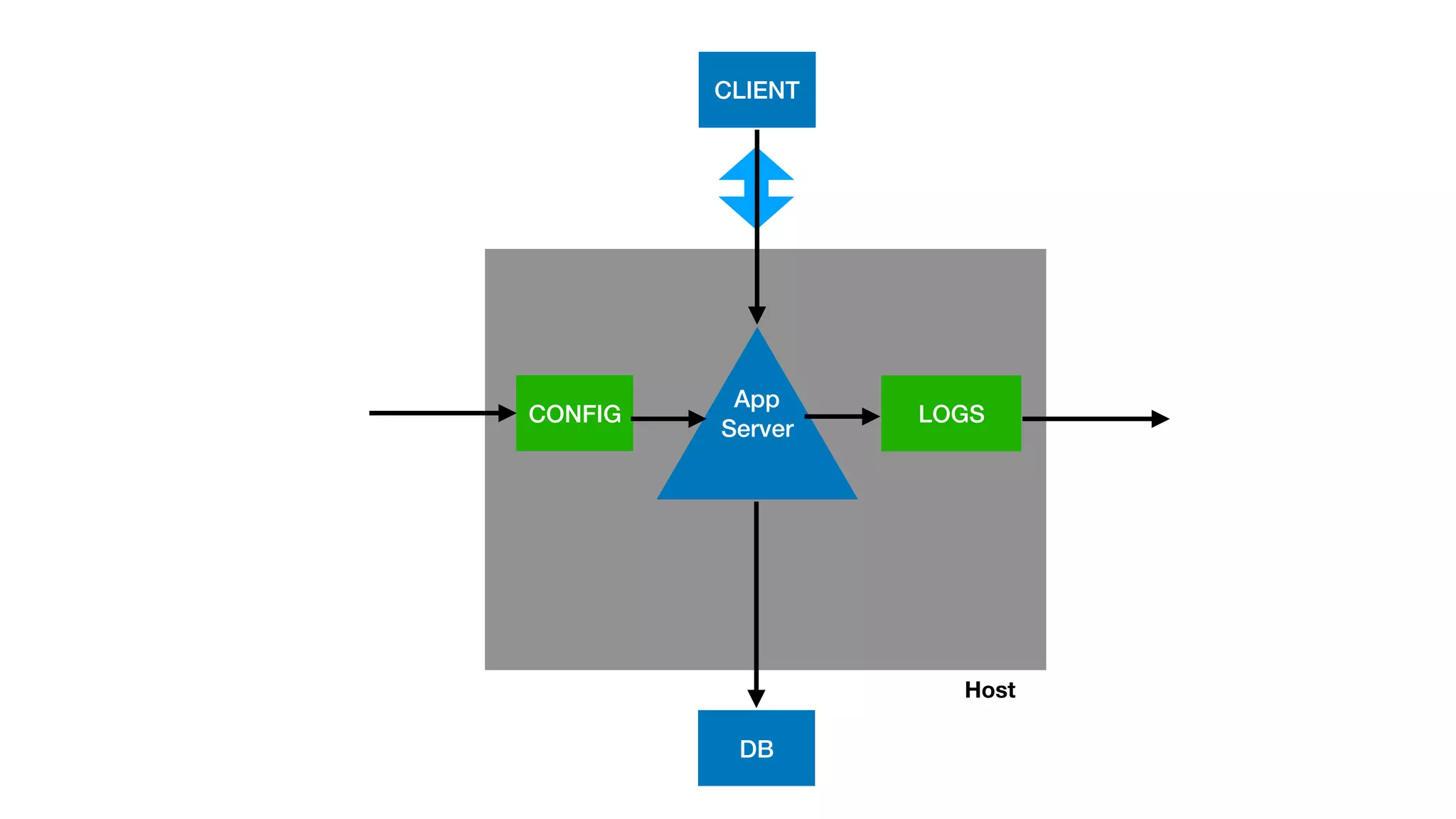
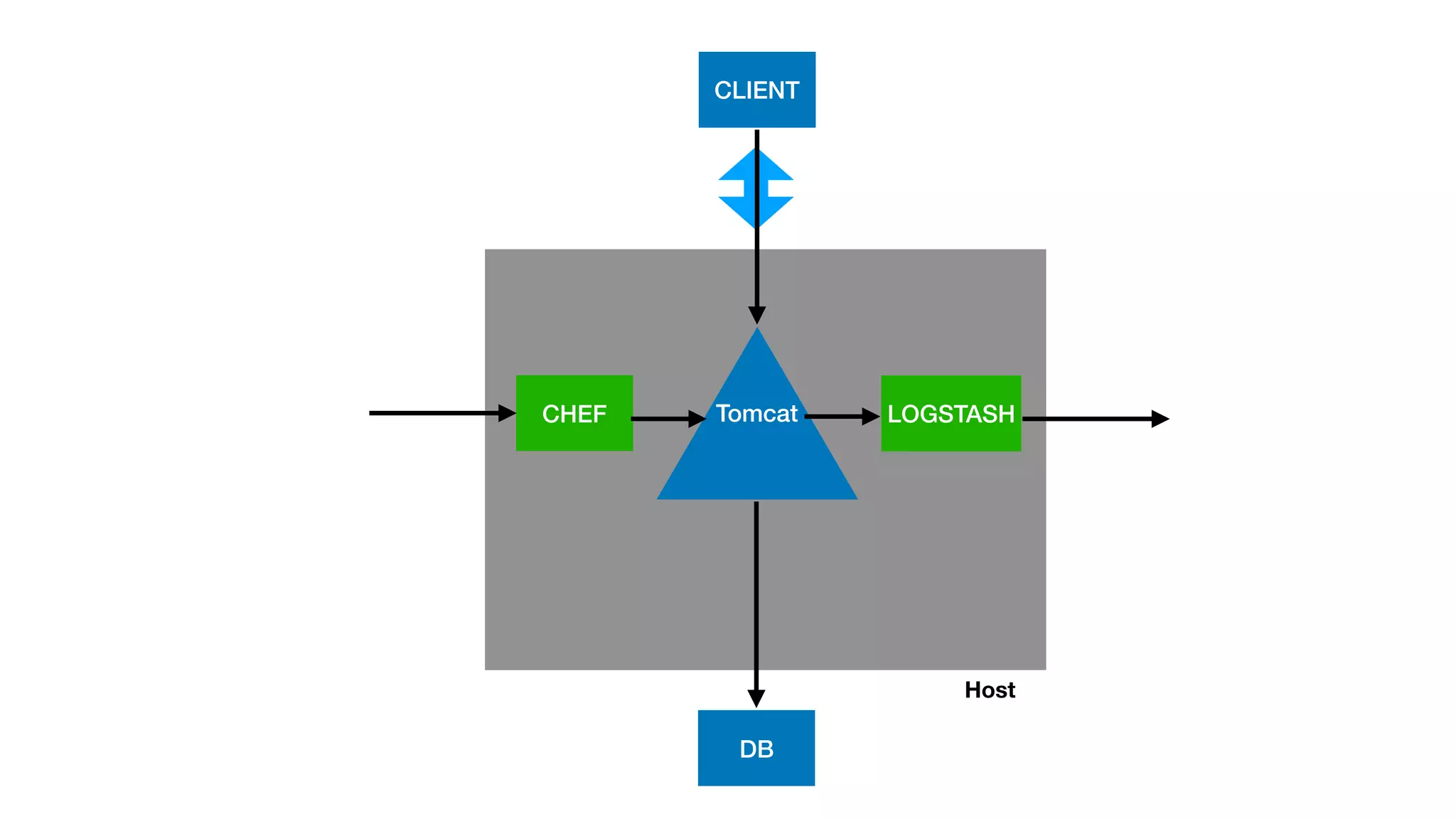
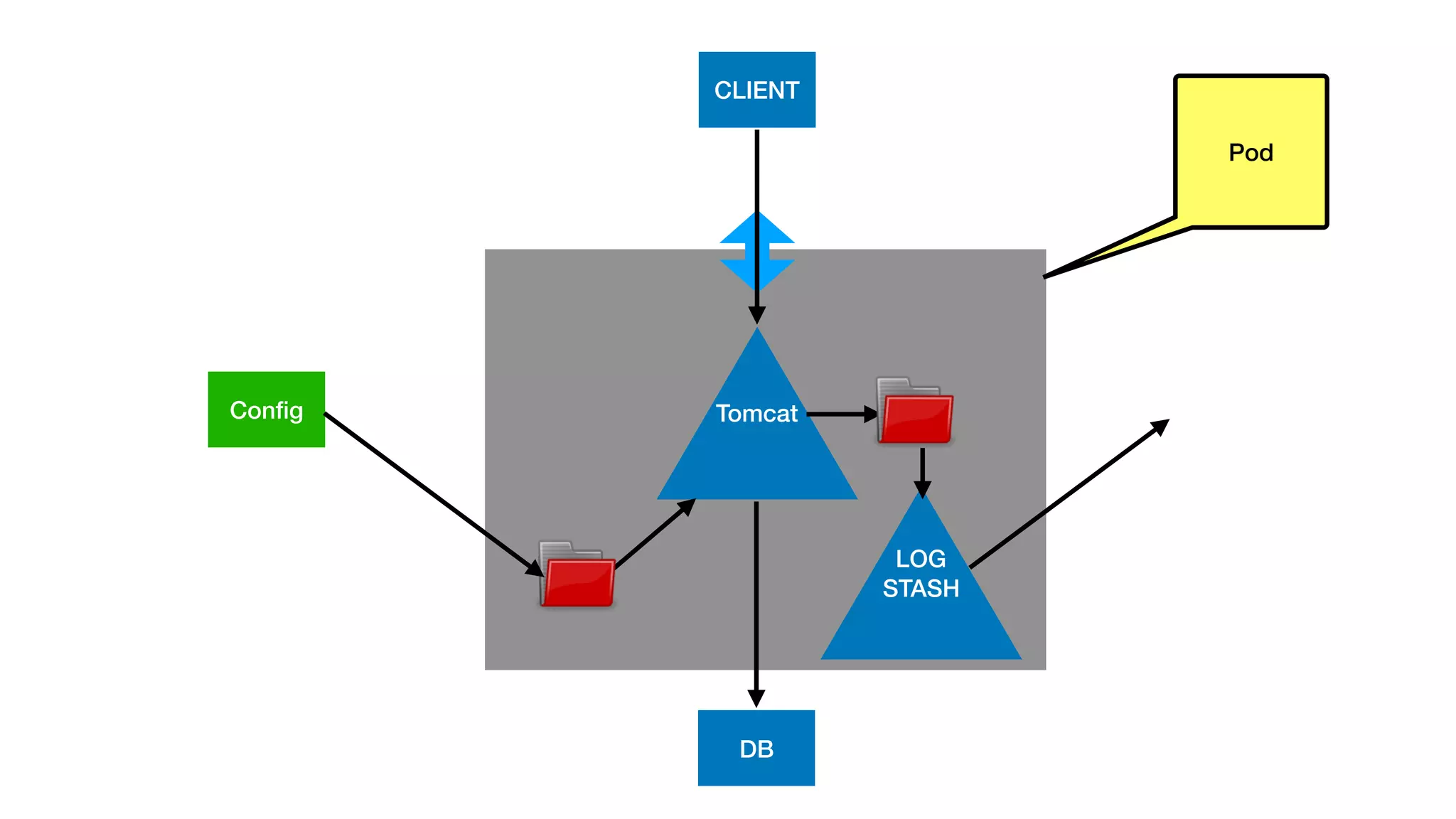
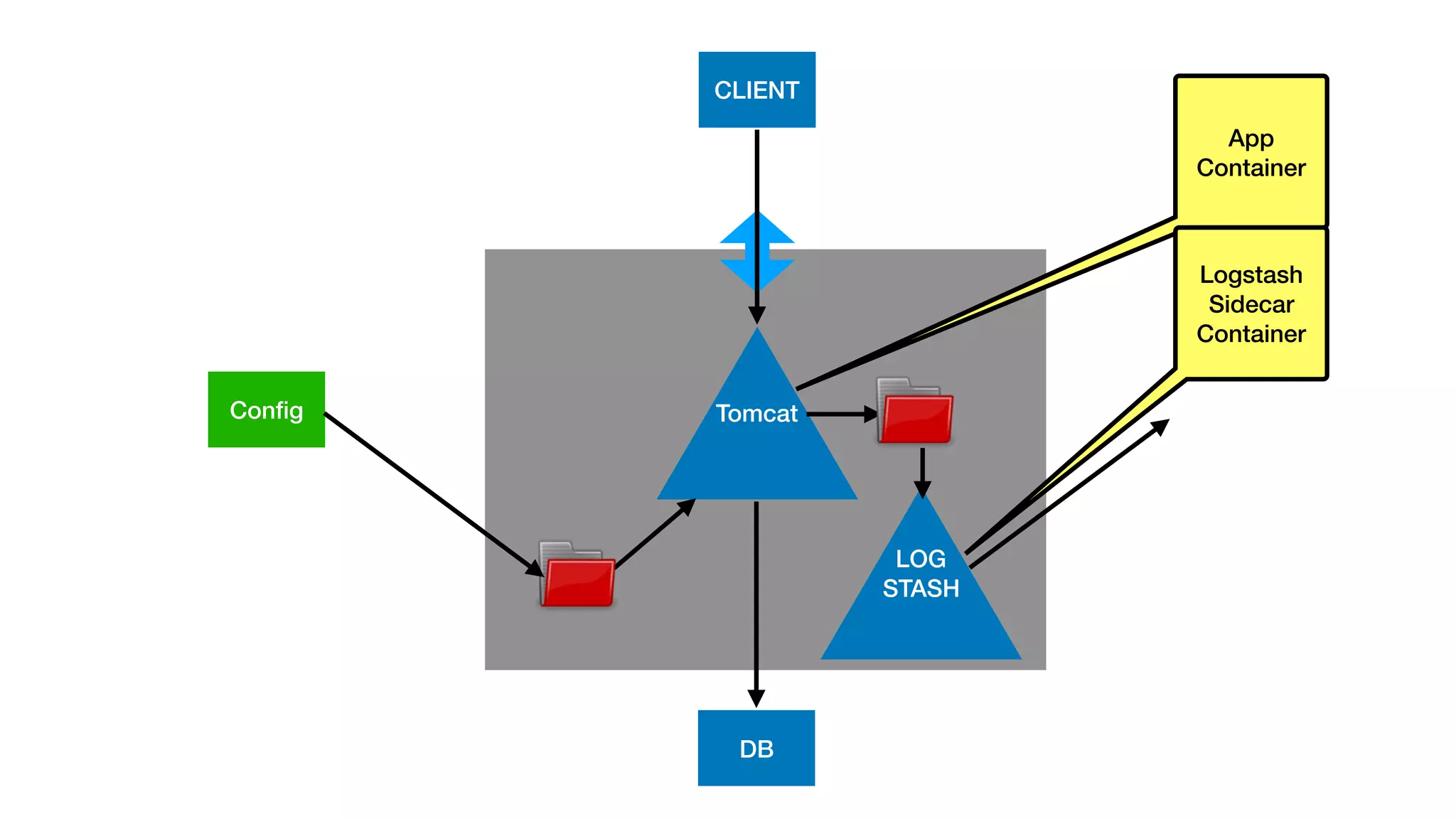
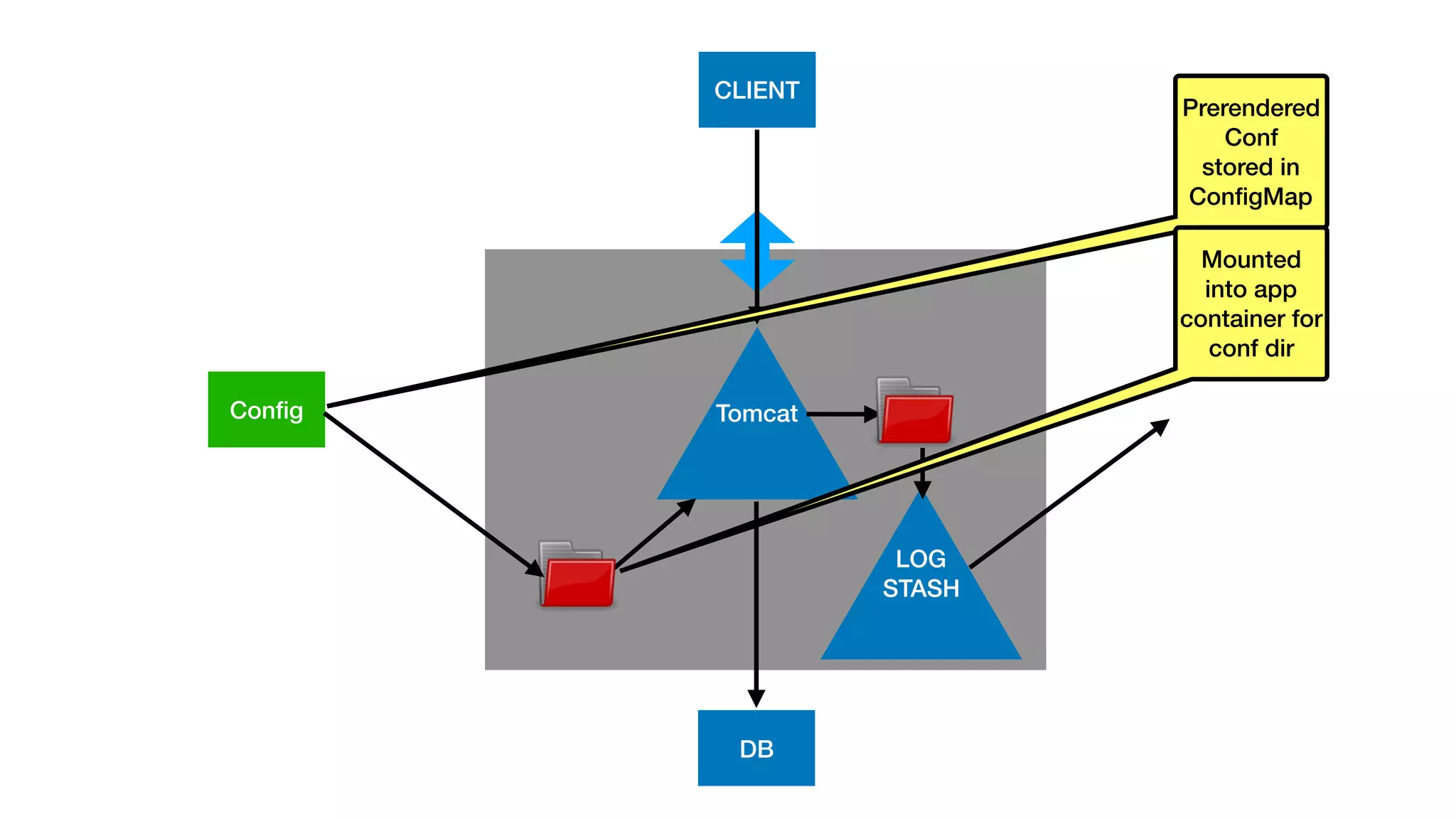
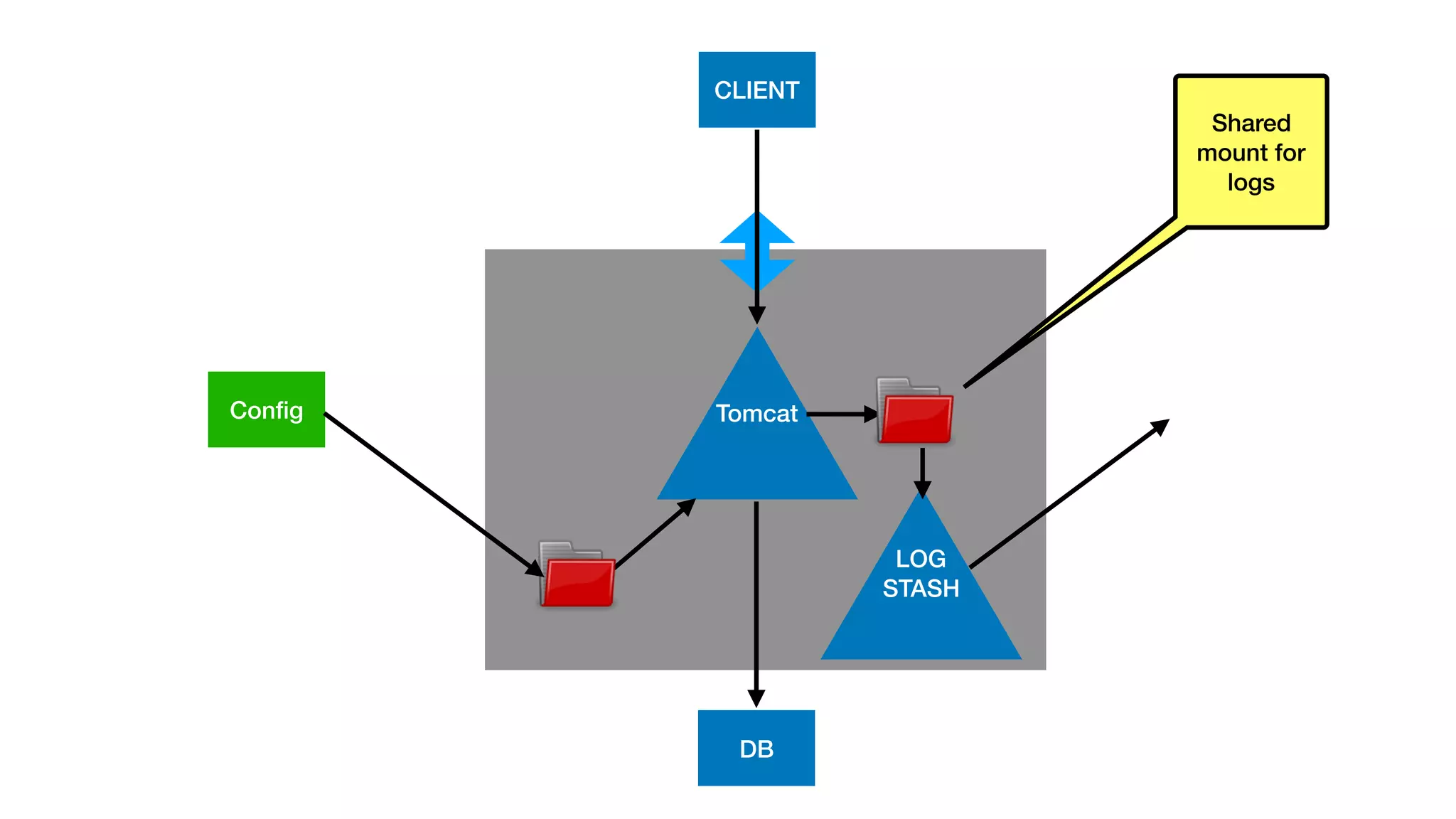
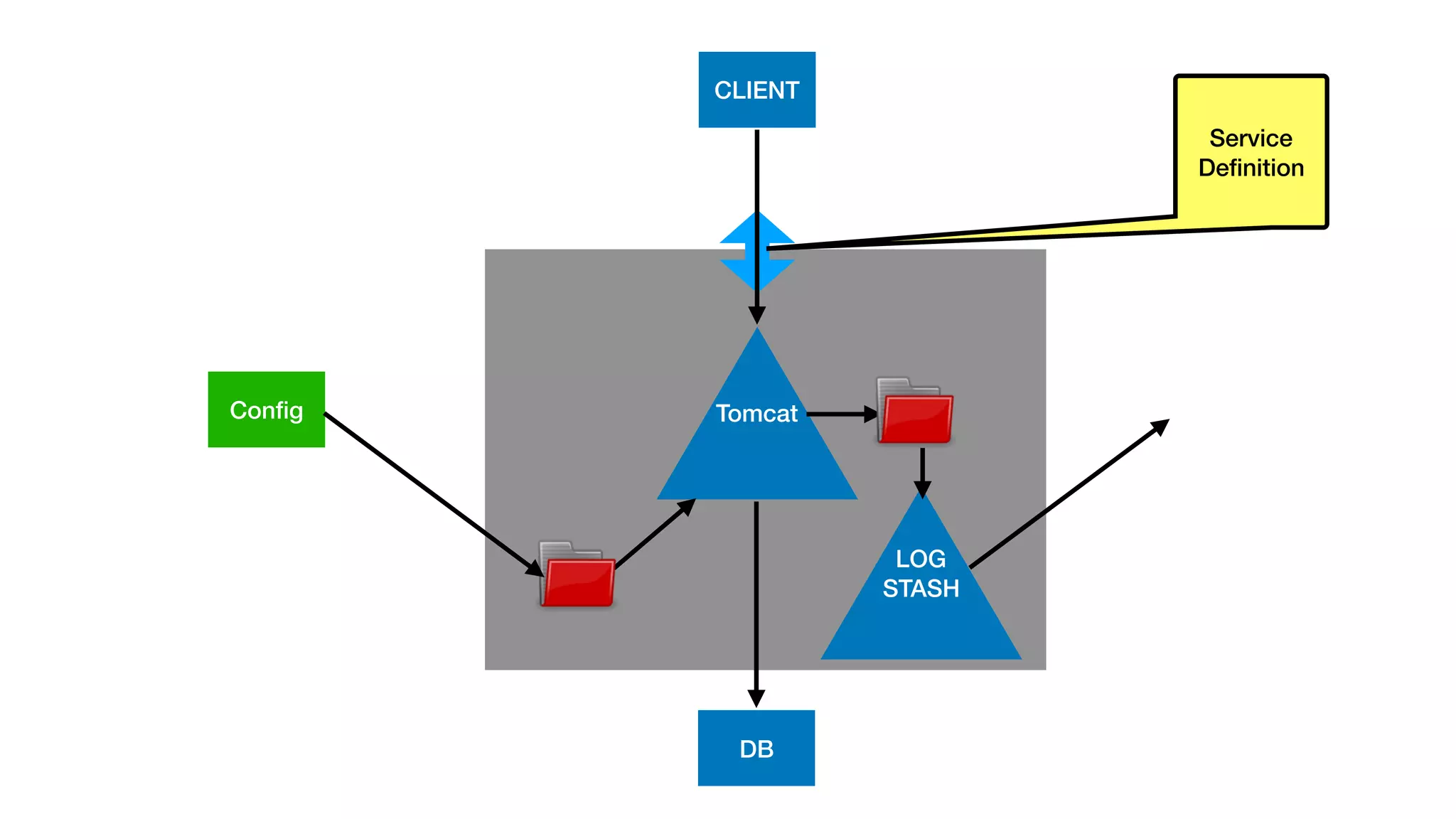
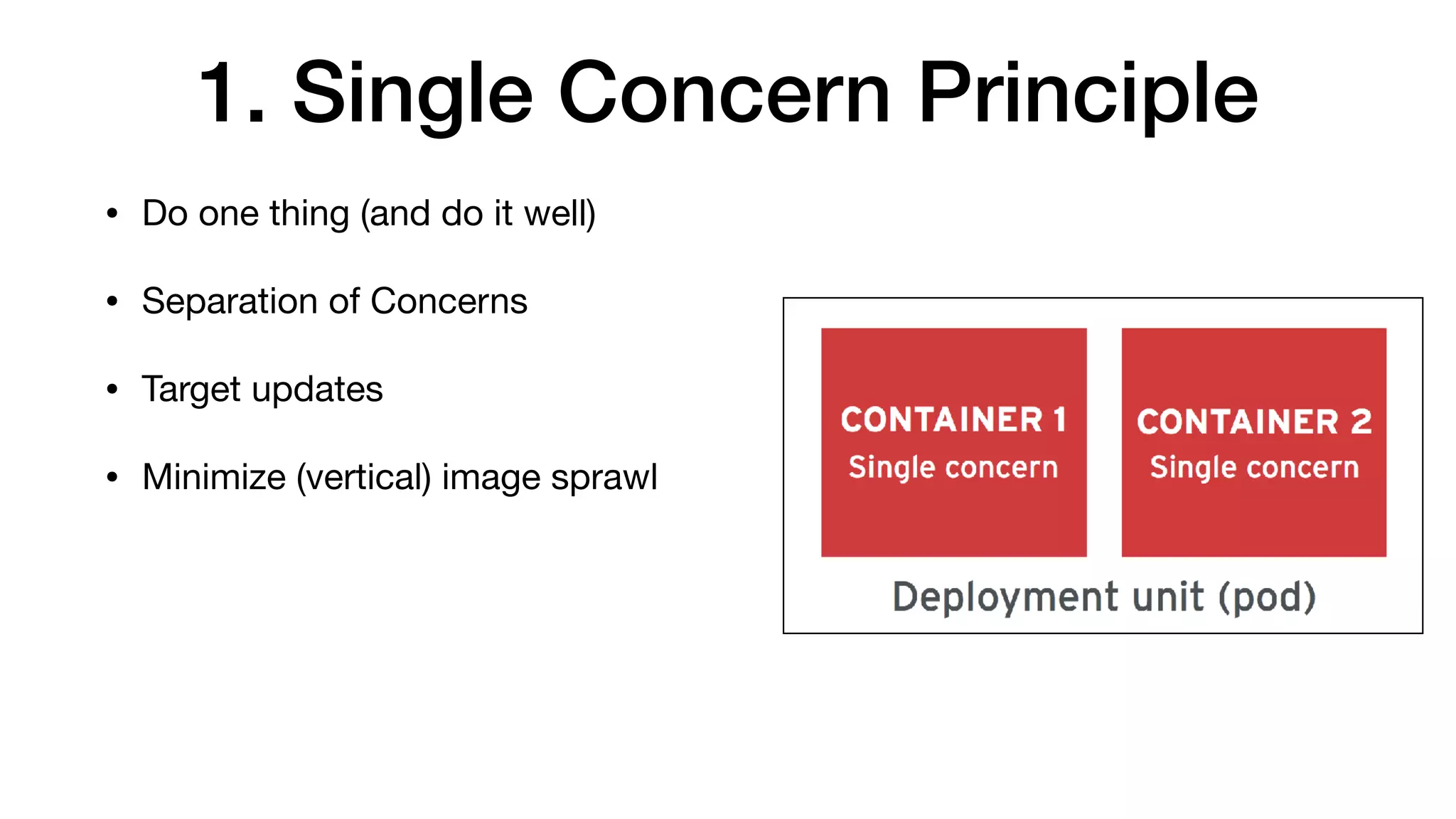
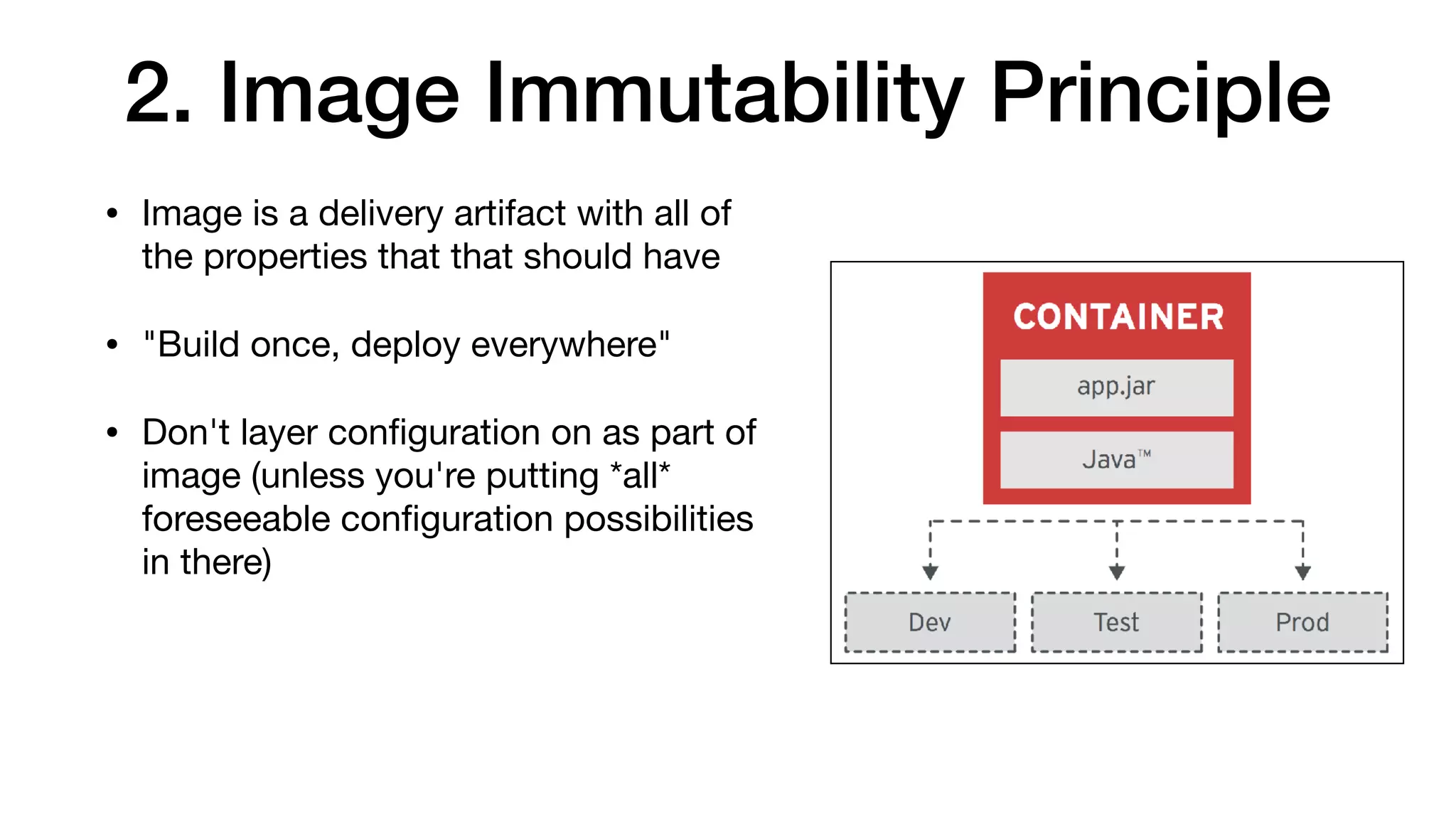
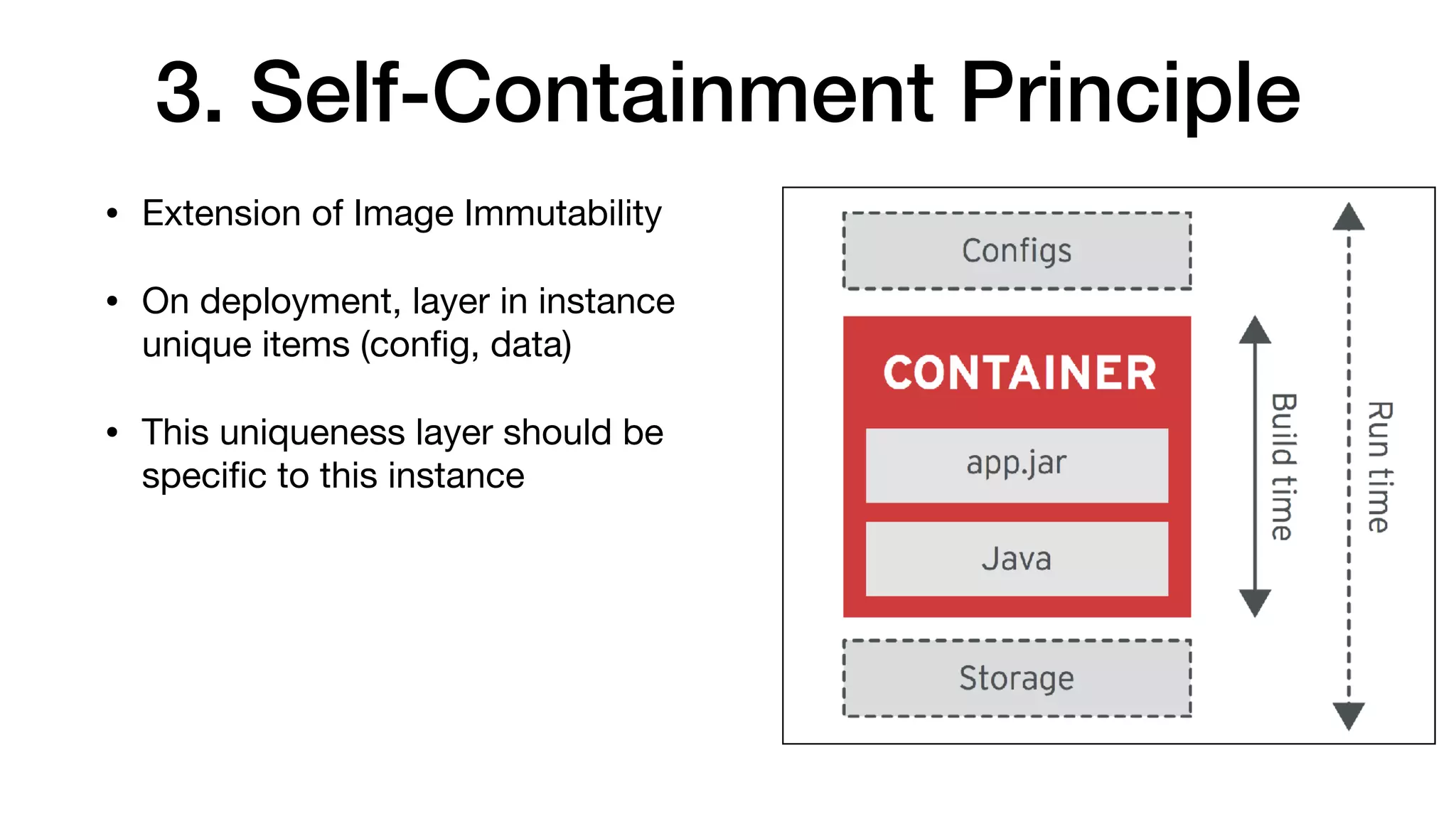
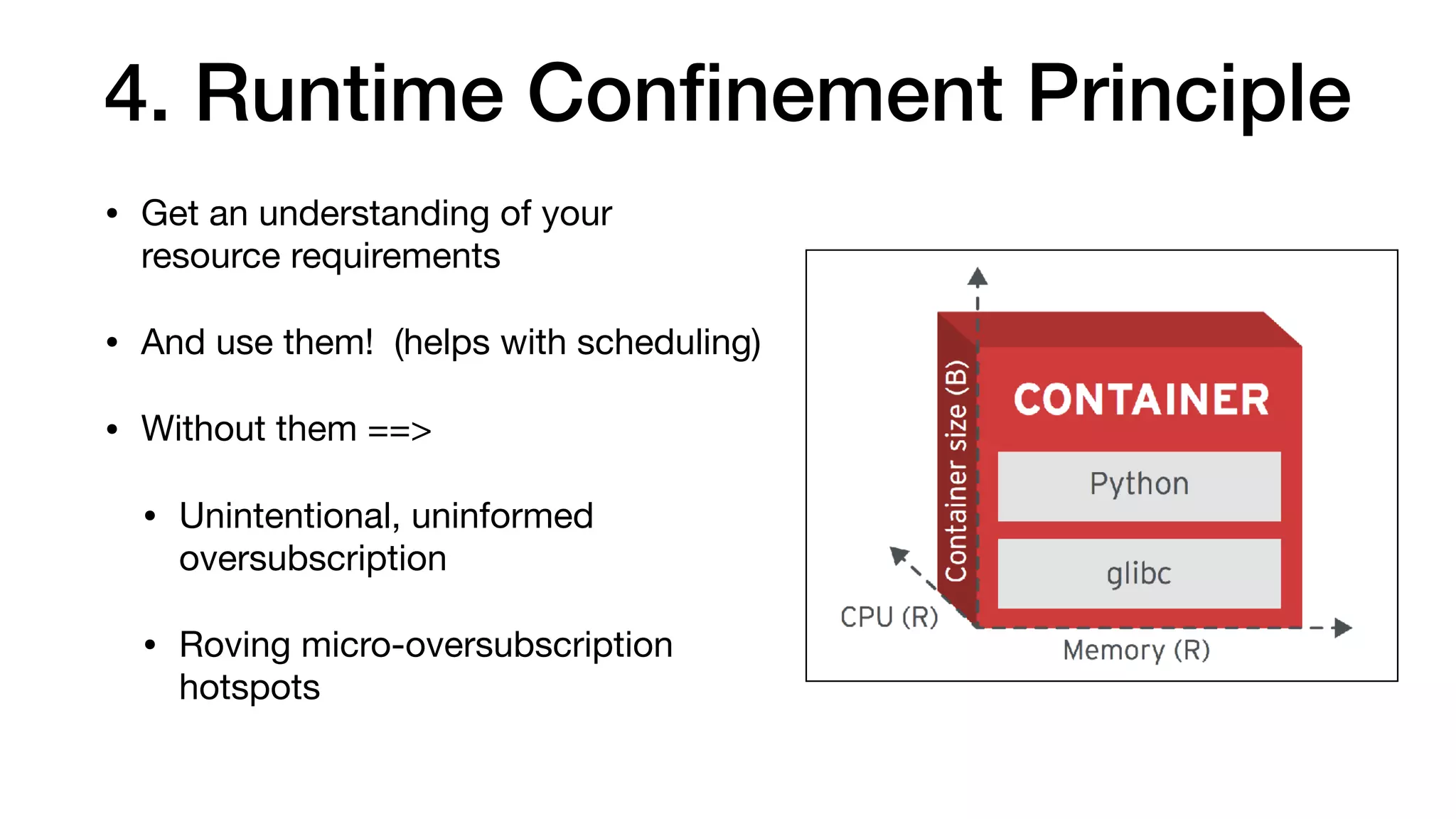
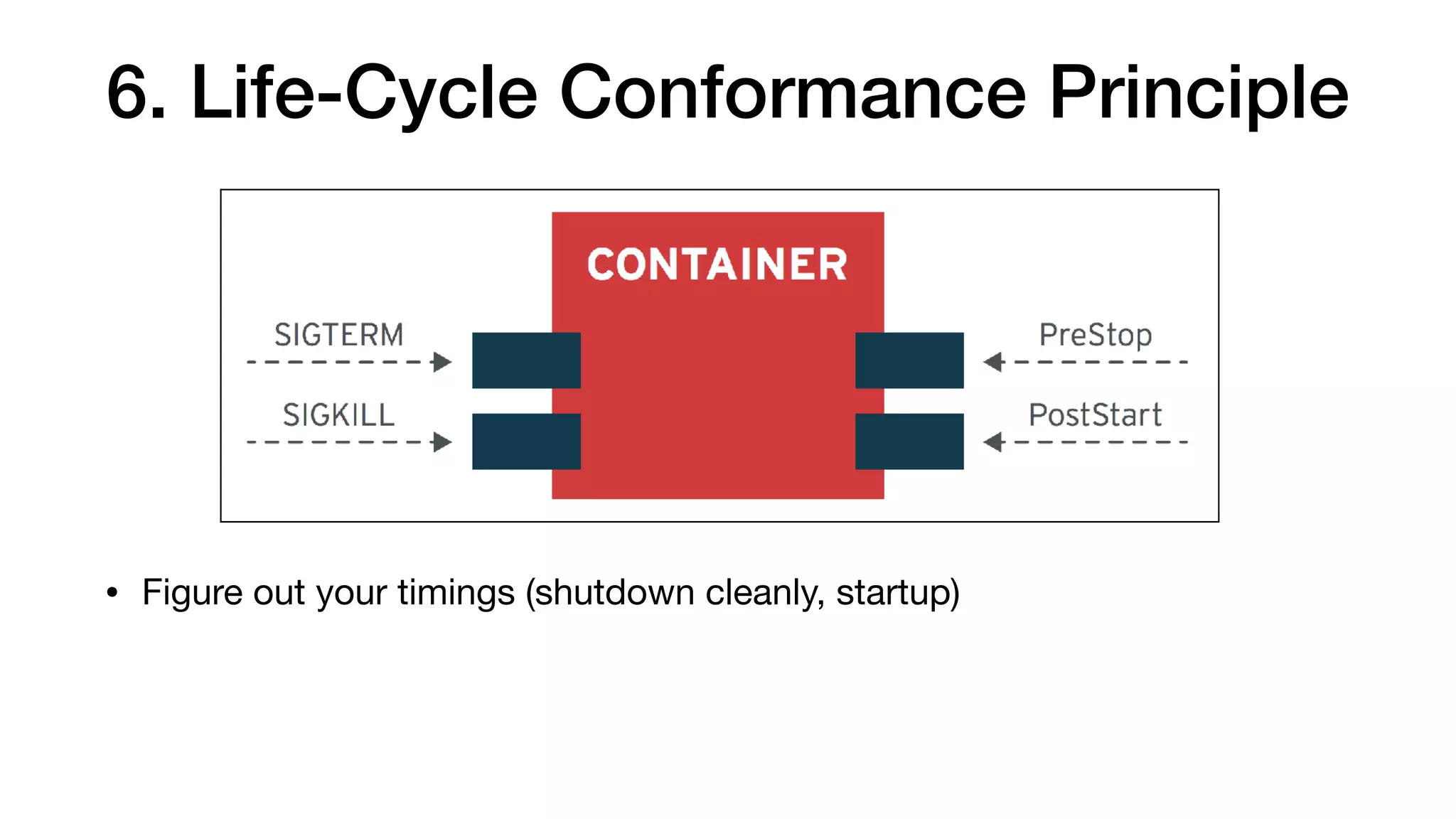
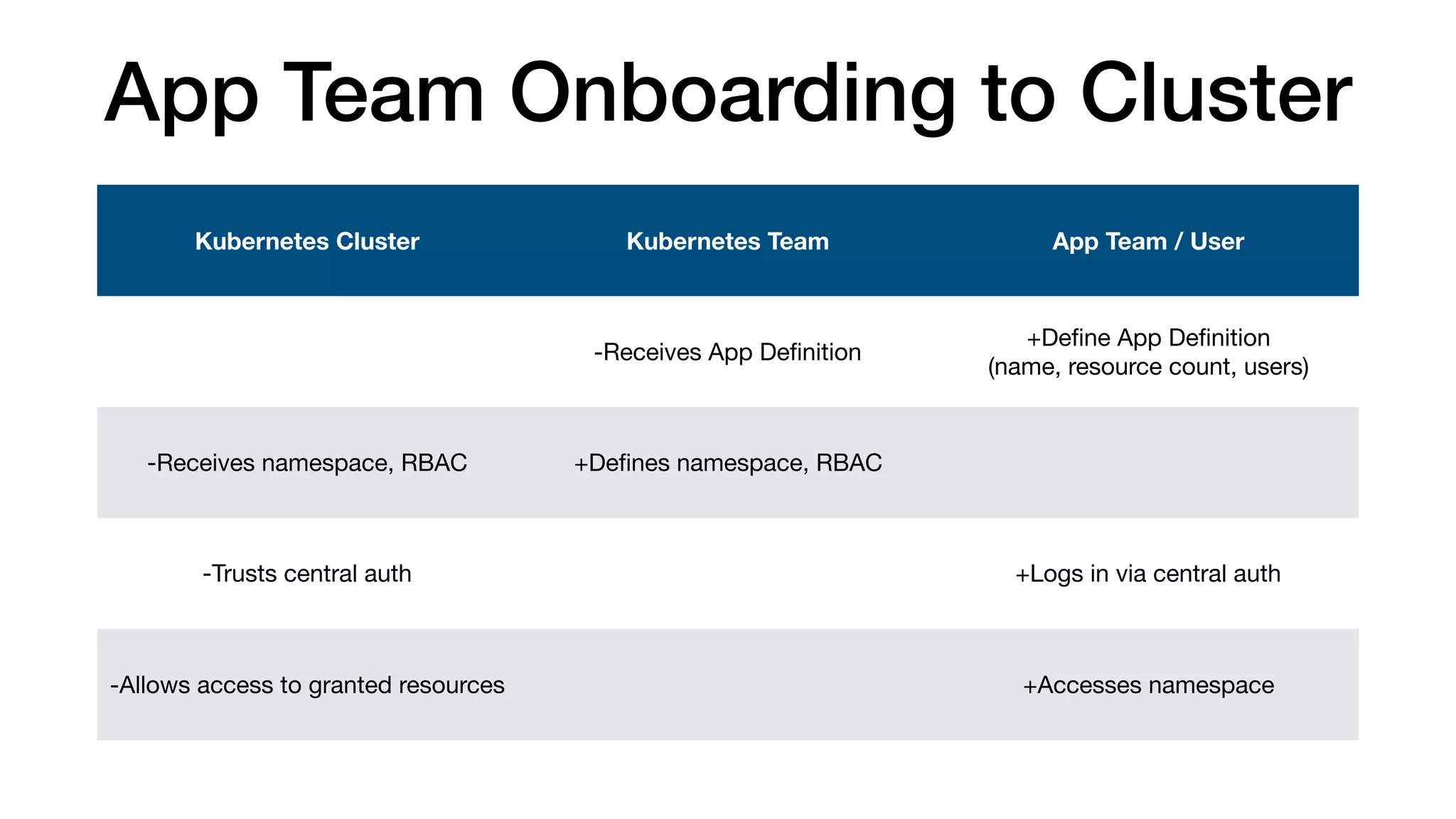
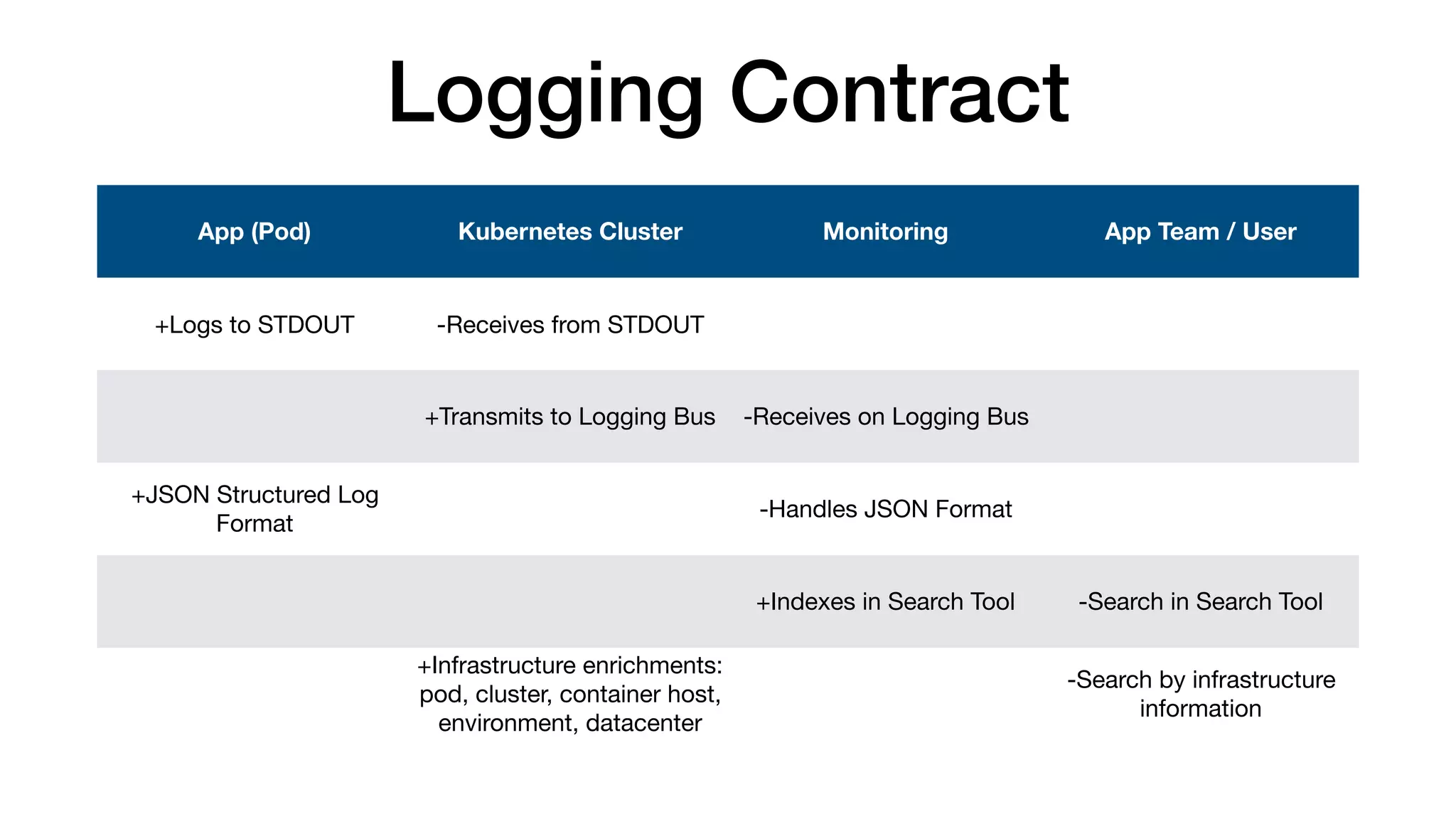
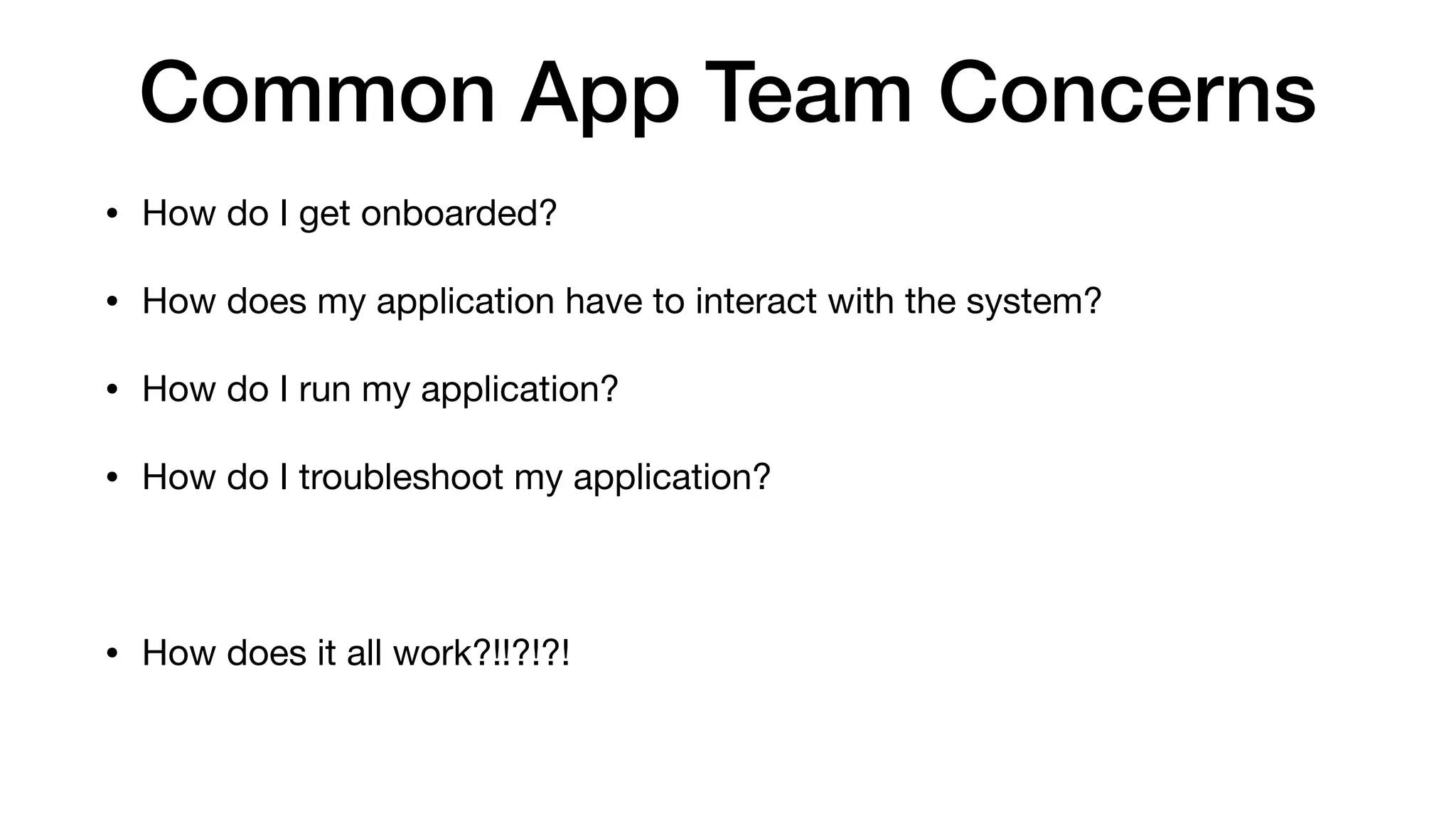
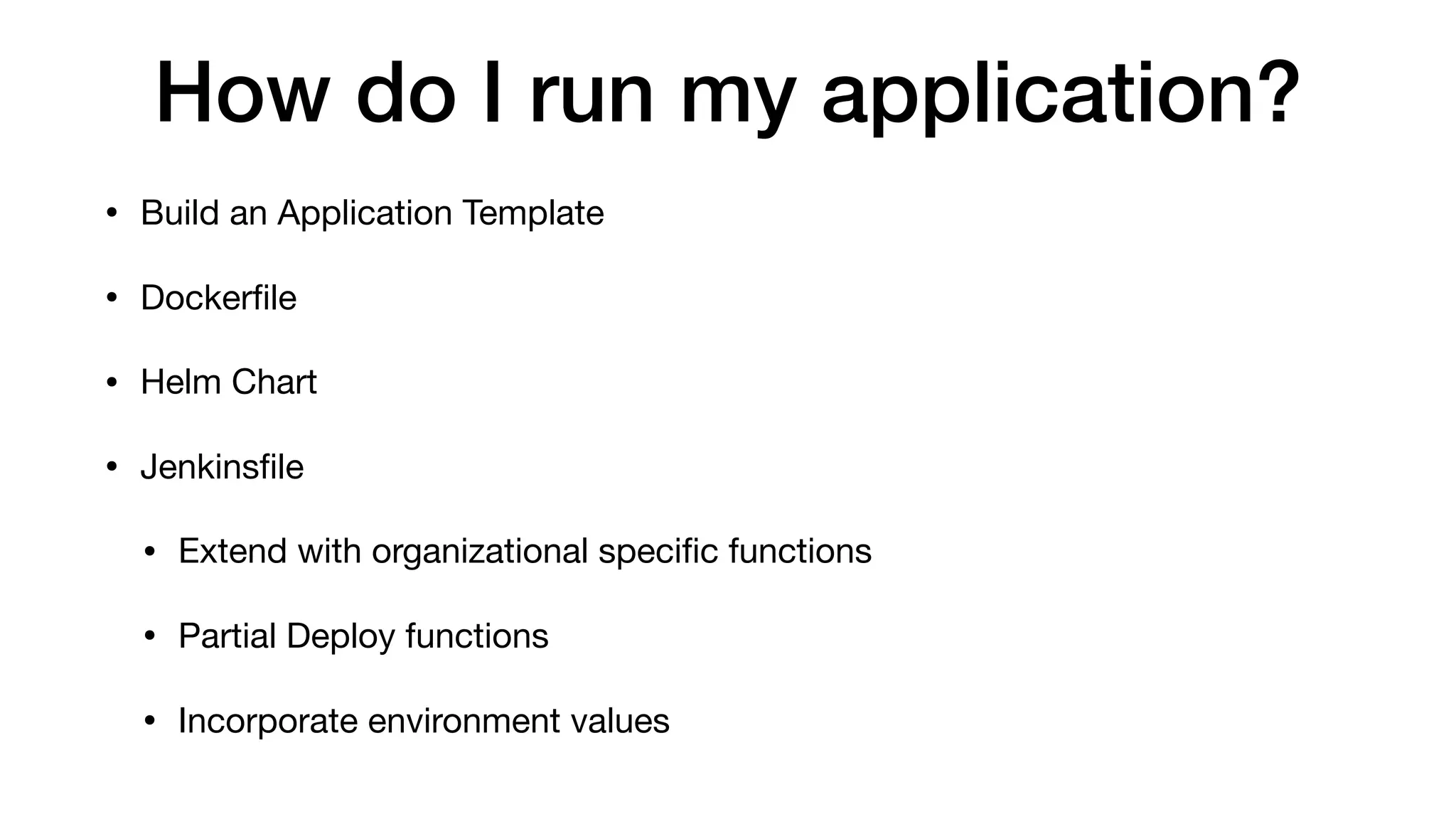
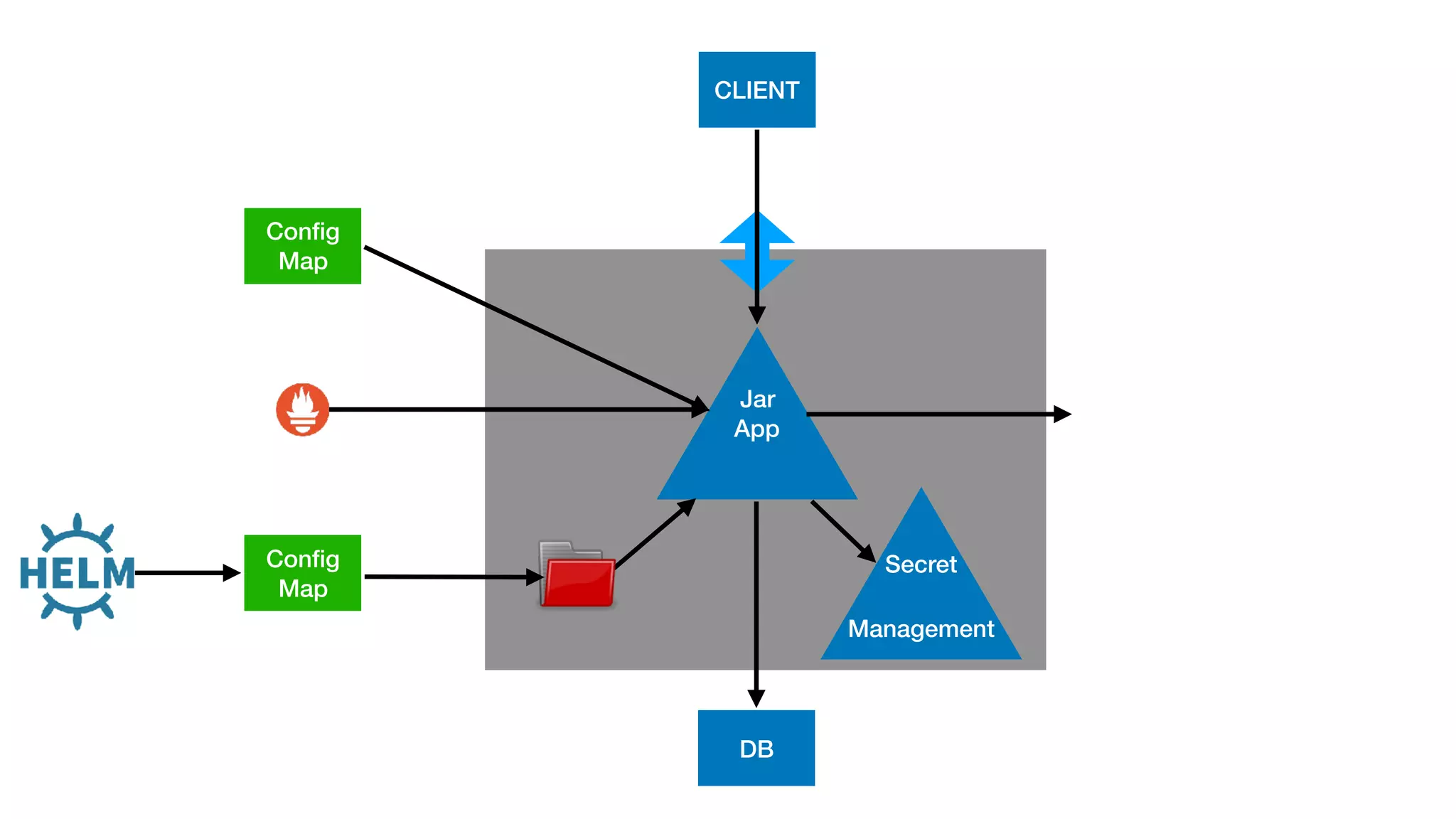
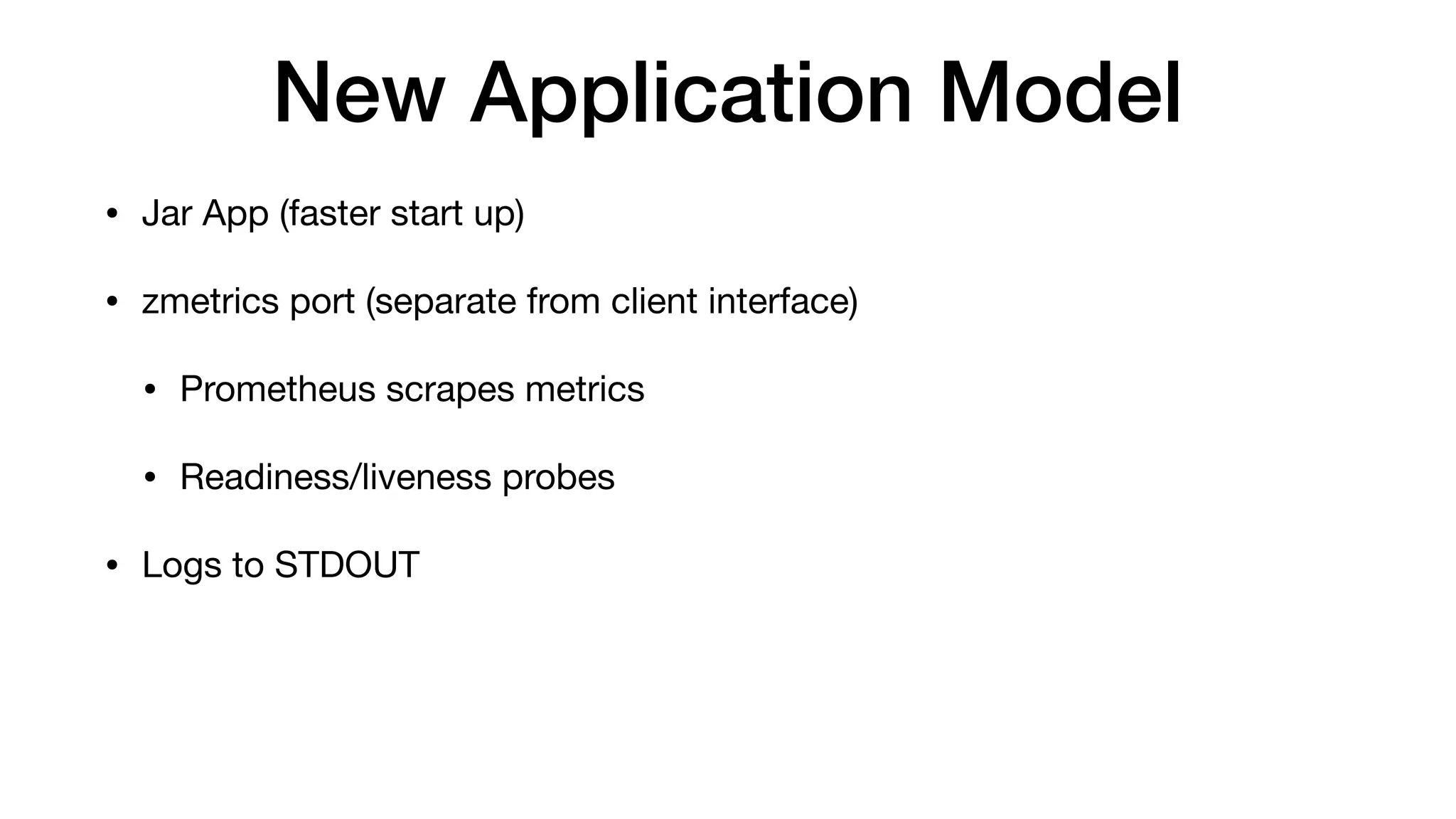
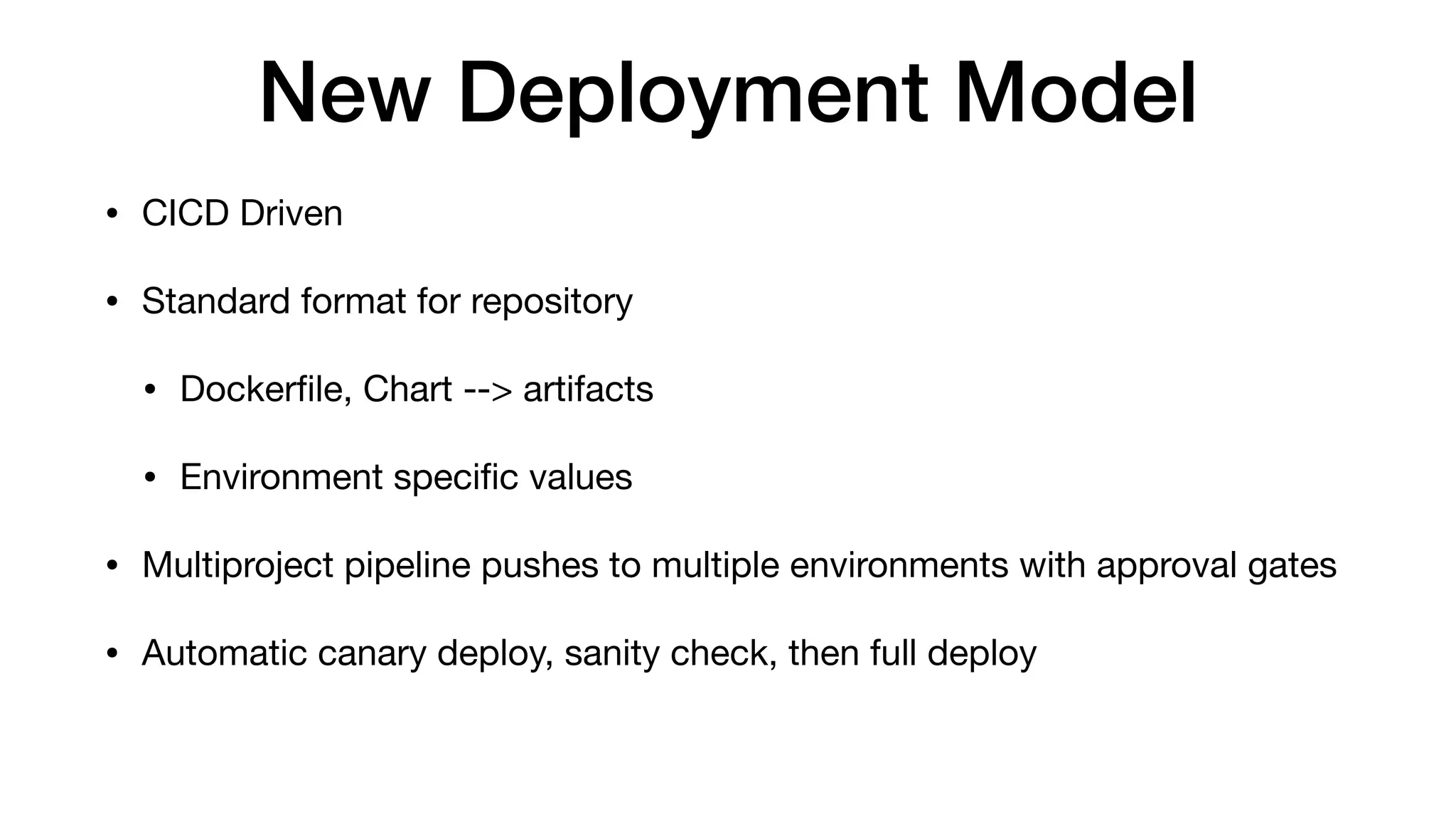
This document provides an overview of Kubernetes concepts and best practices for evolving applications to run on Kubernetes. It discusses initial "lift and shift" approaches as well as principles for container and application design that are well-suited for Kubernetes. These include having containers do one thing, making images immutable, ensuring self-containment and runtime confinement, and designing for process disposability and observability. The document also covers how people and processes need to change, such as adopting new deployment strategies, defining interaction contracts, and being comfortable with change and new approaches to debugging.