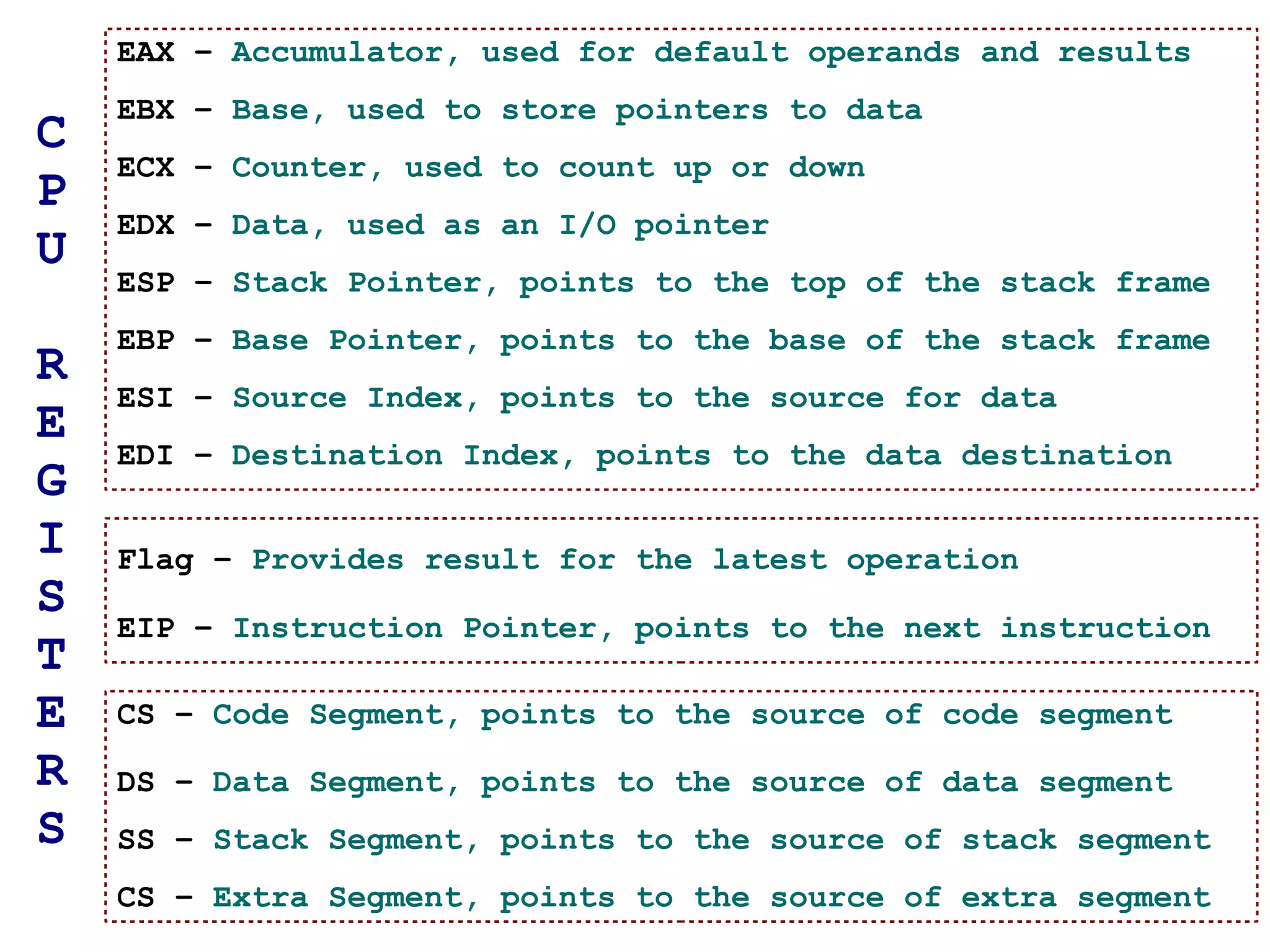
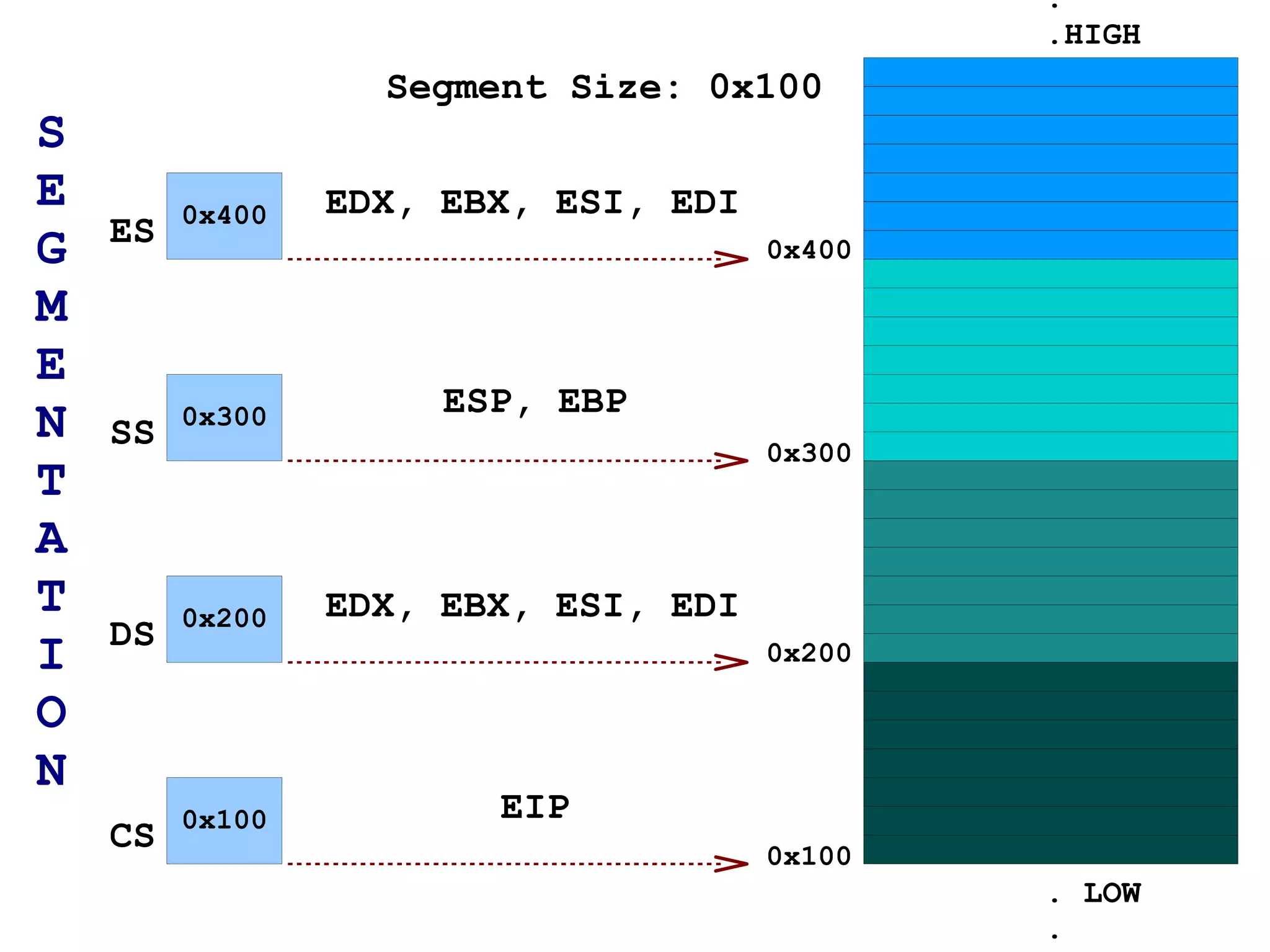
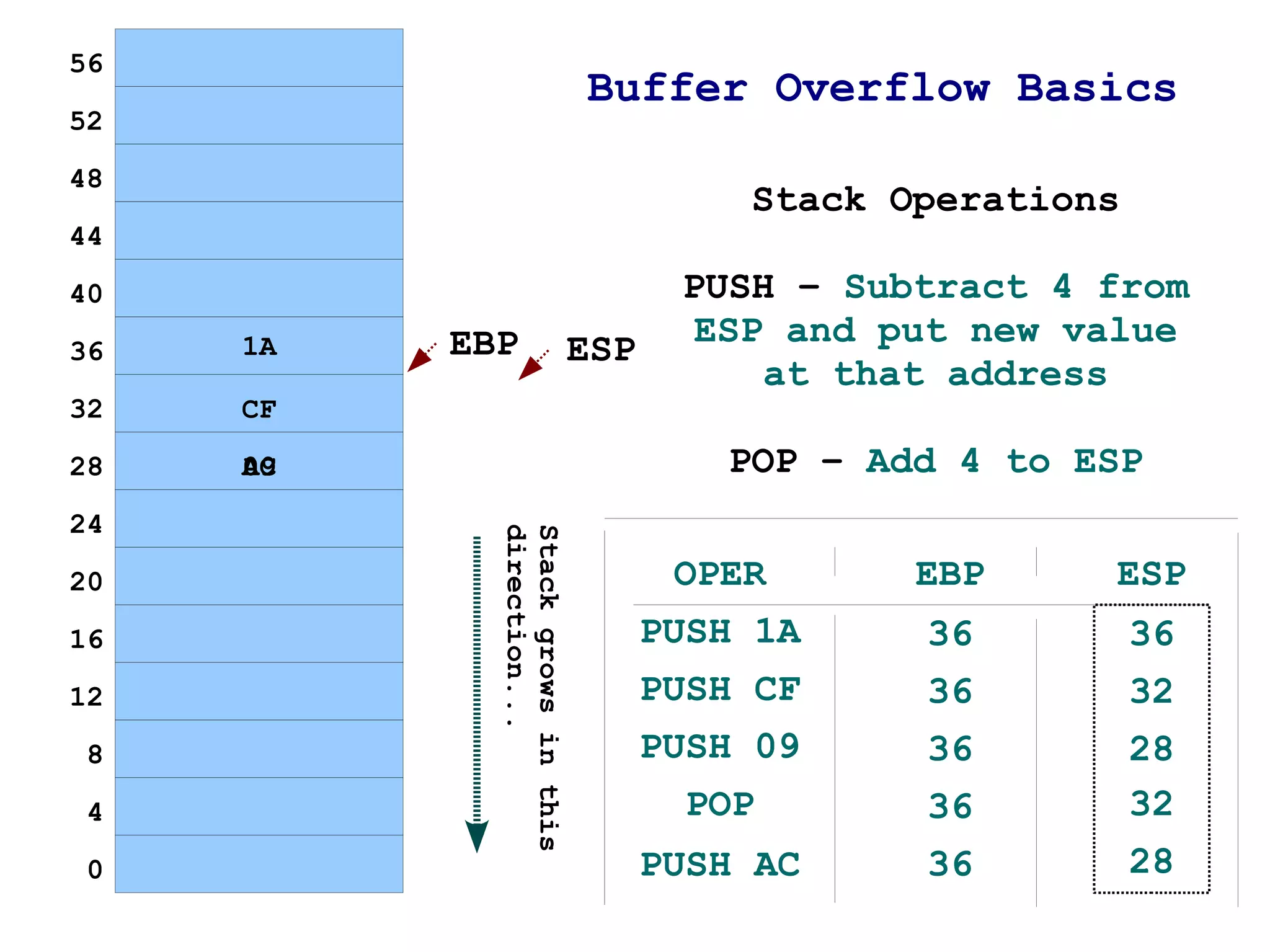
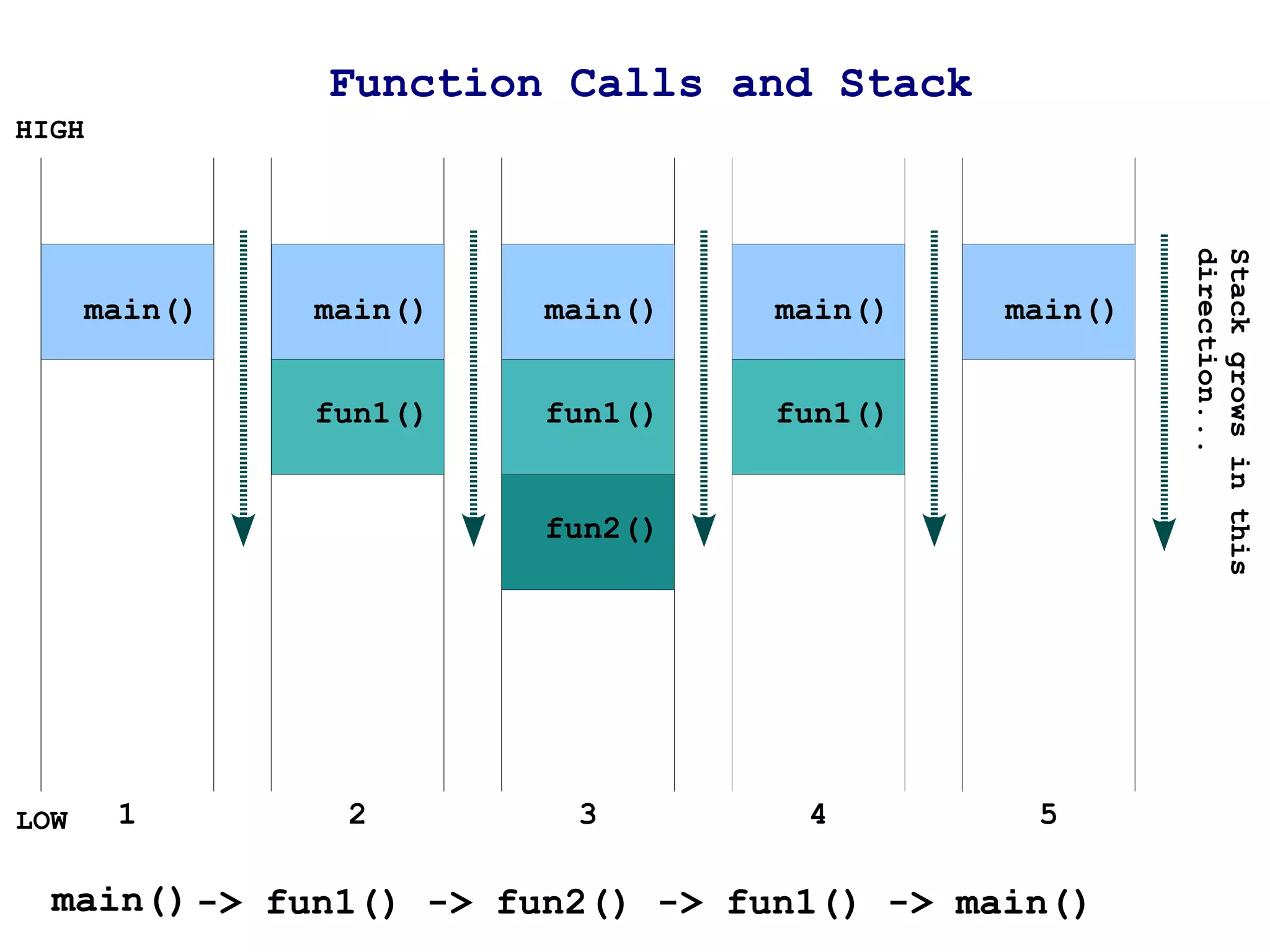
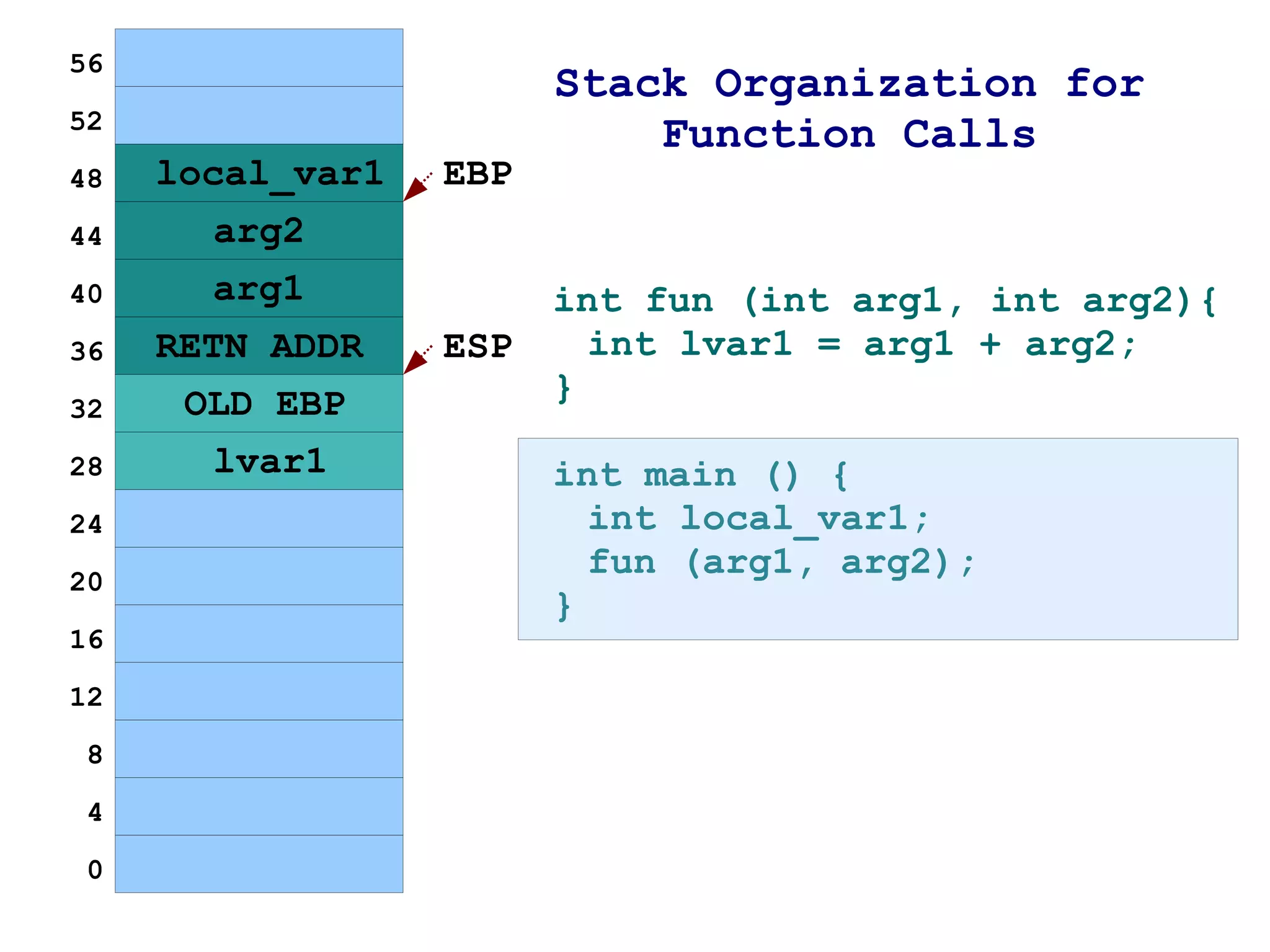
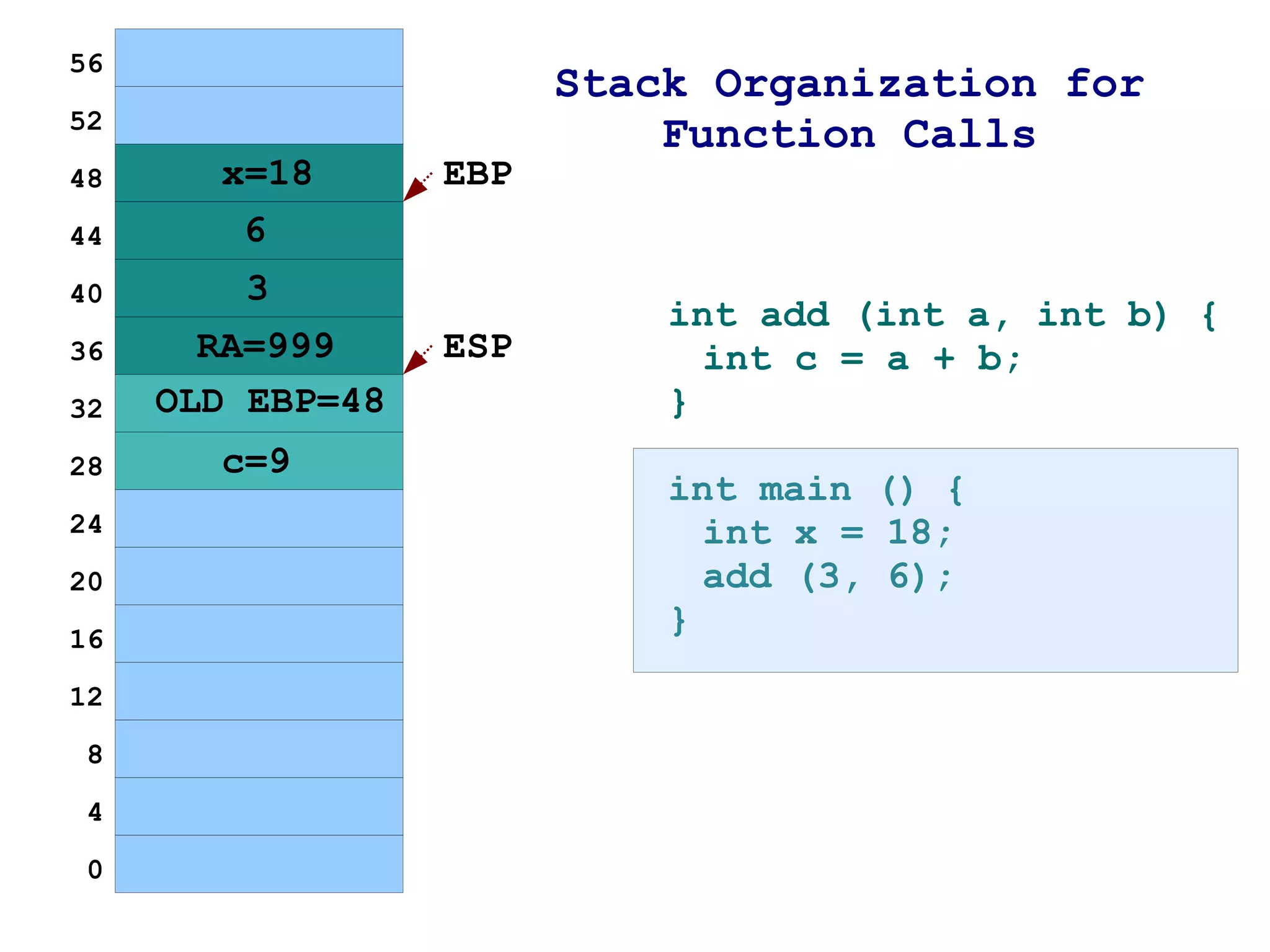
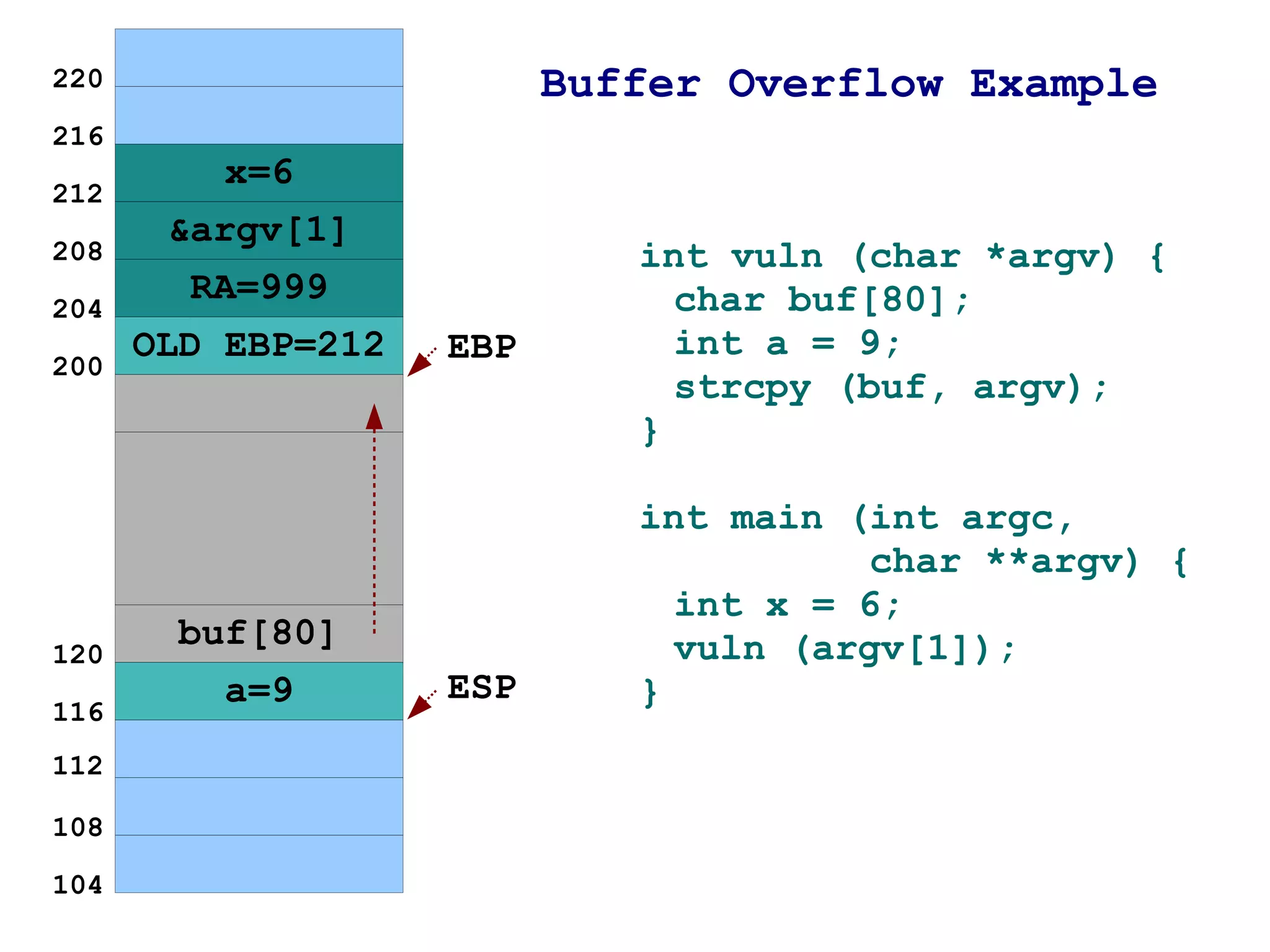
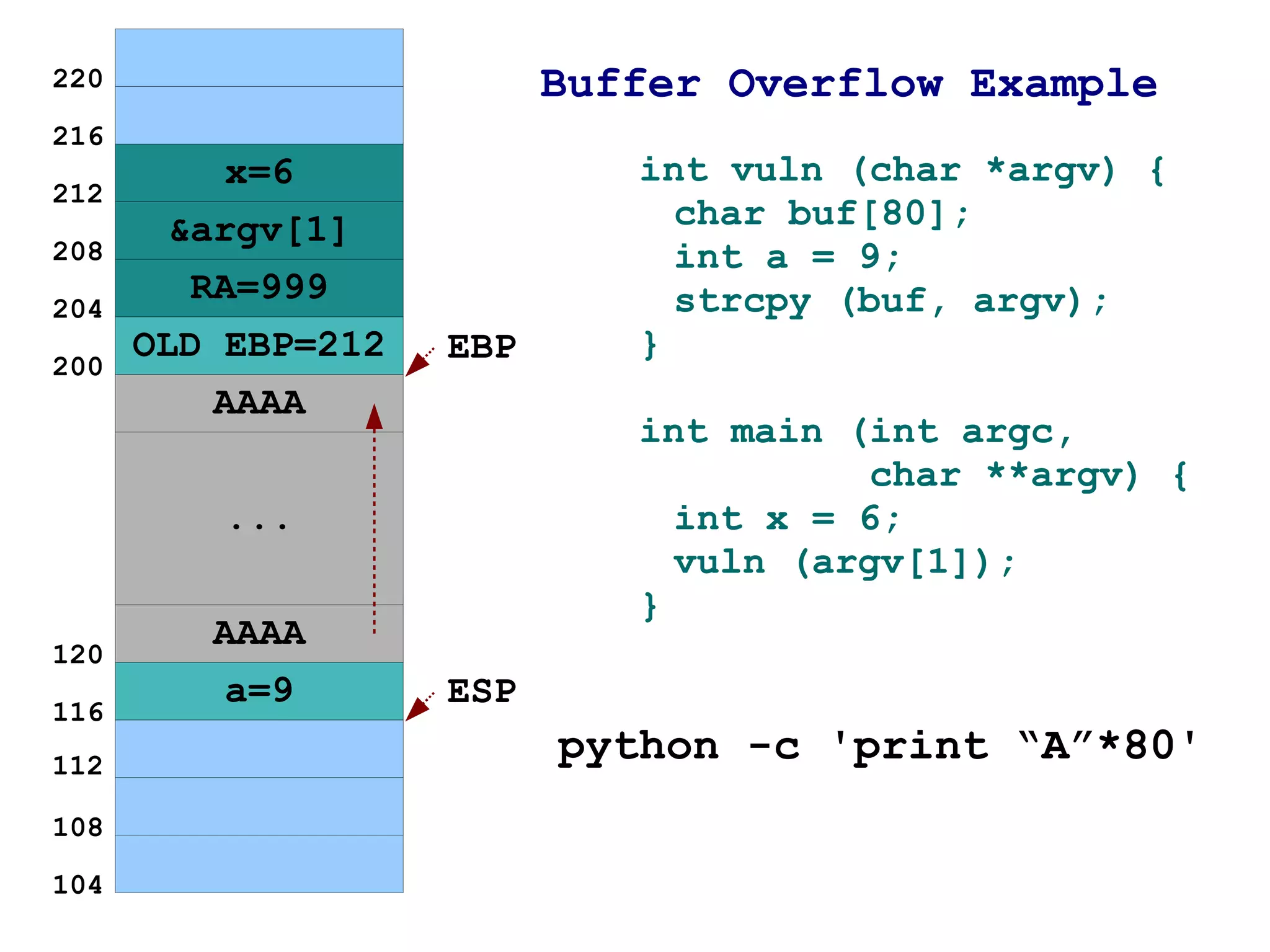
The document provides an overview of buffer overflow vulnerabilities including:
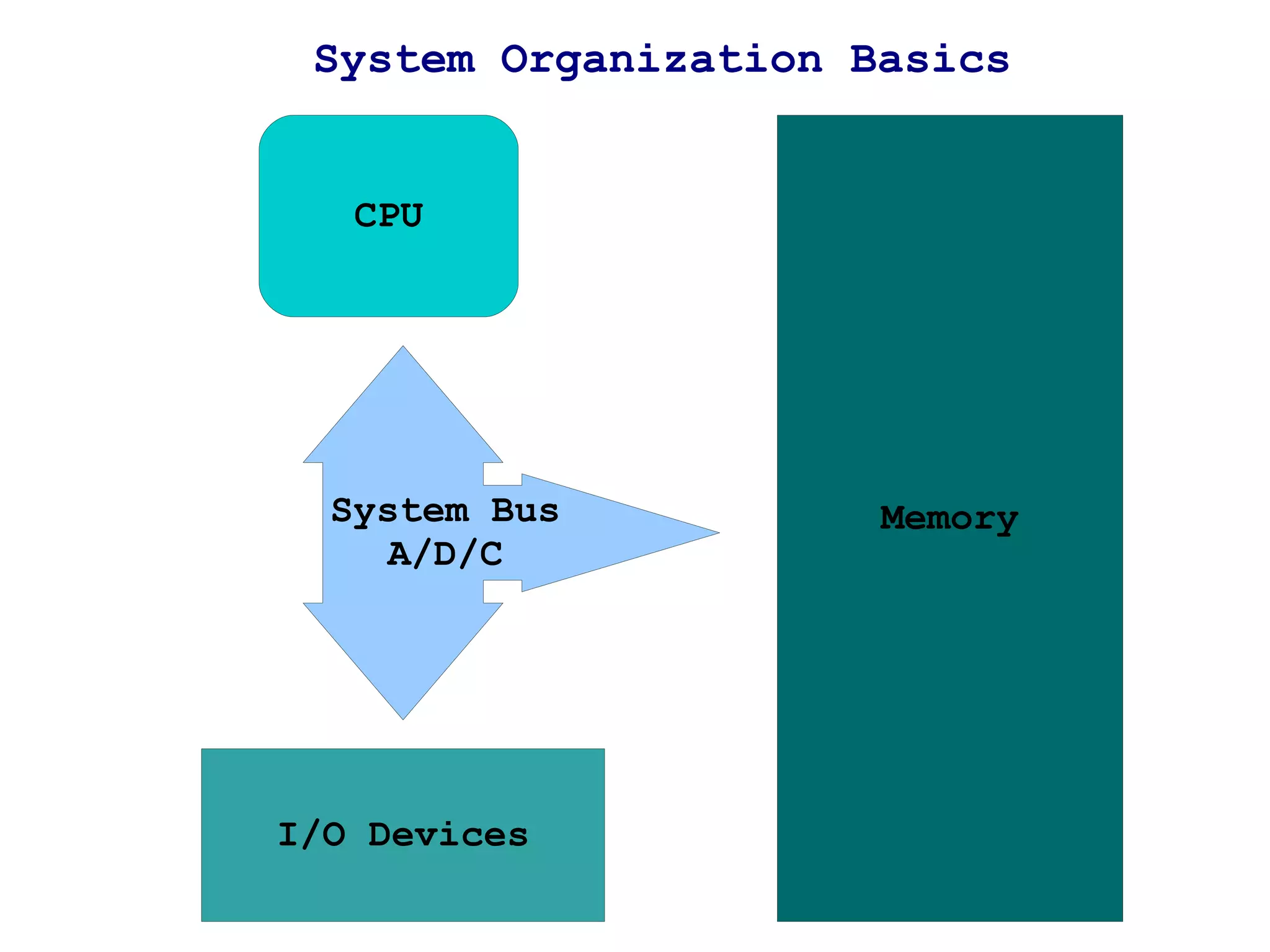
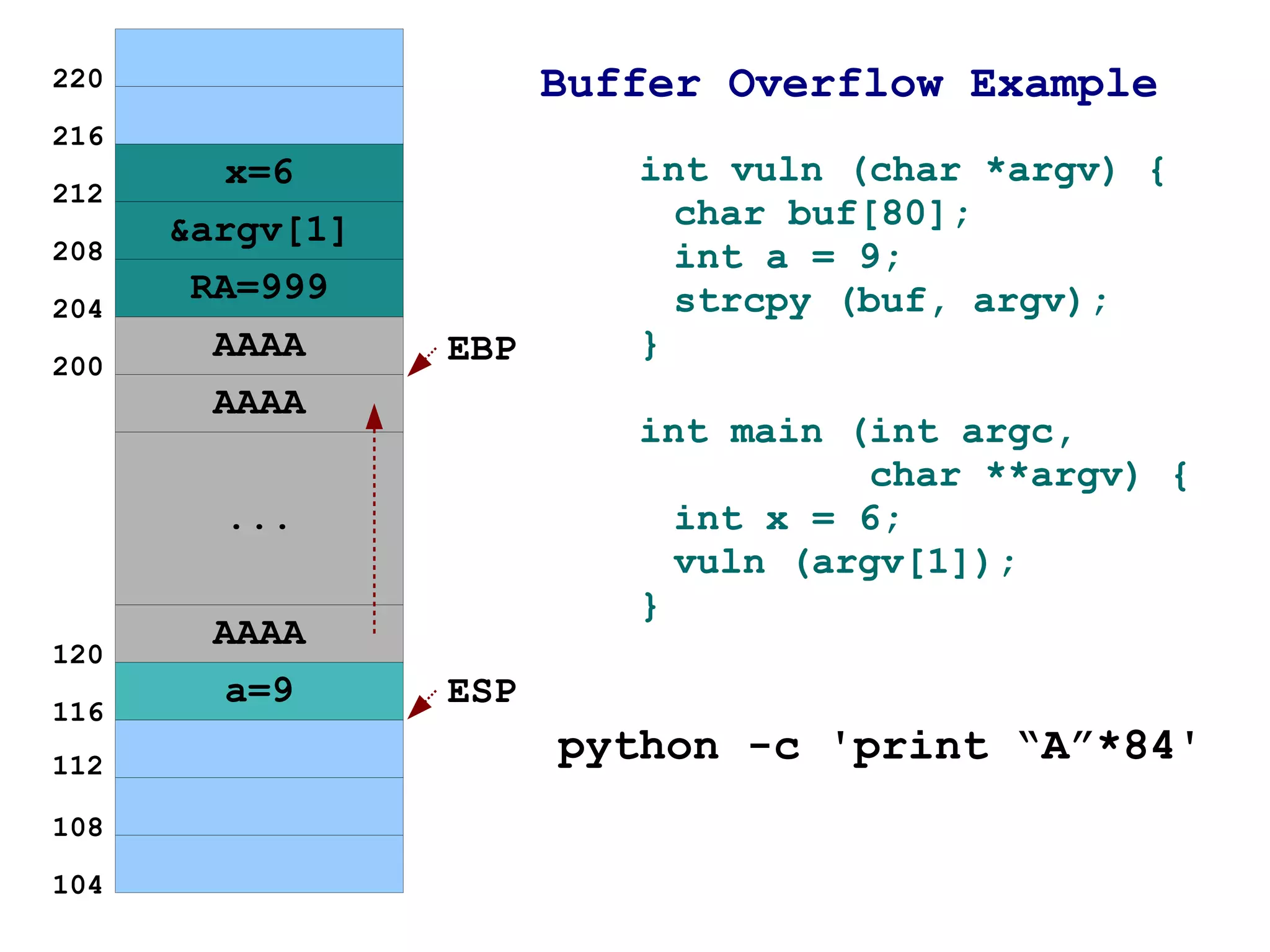
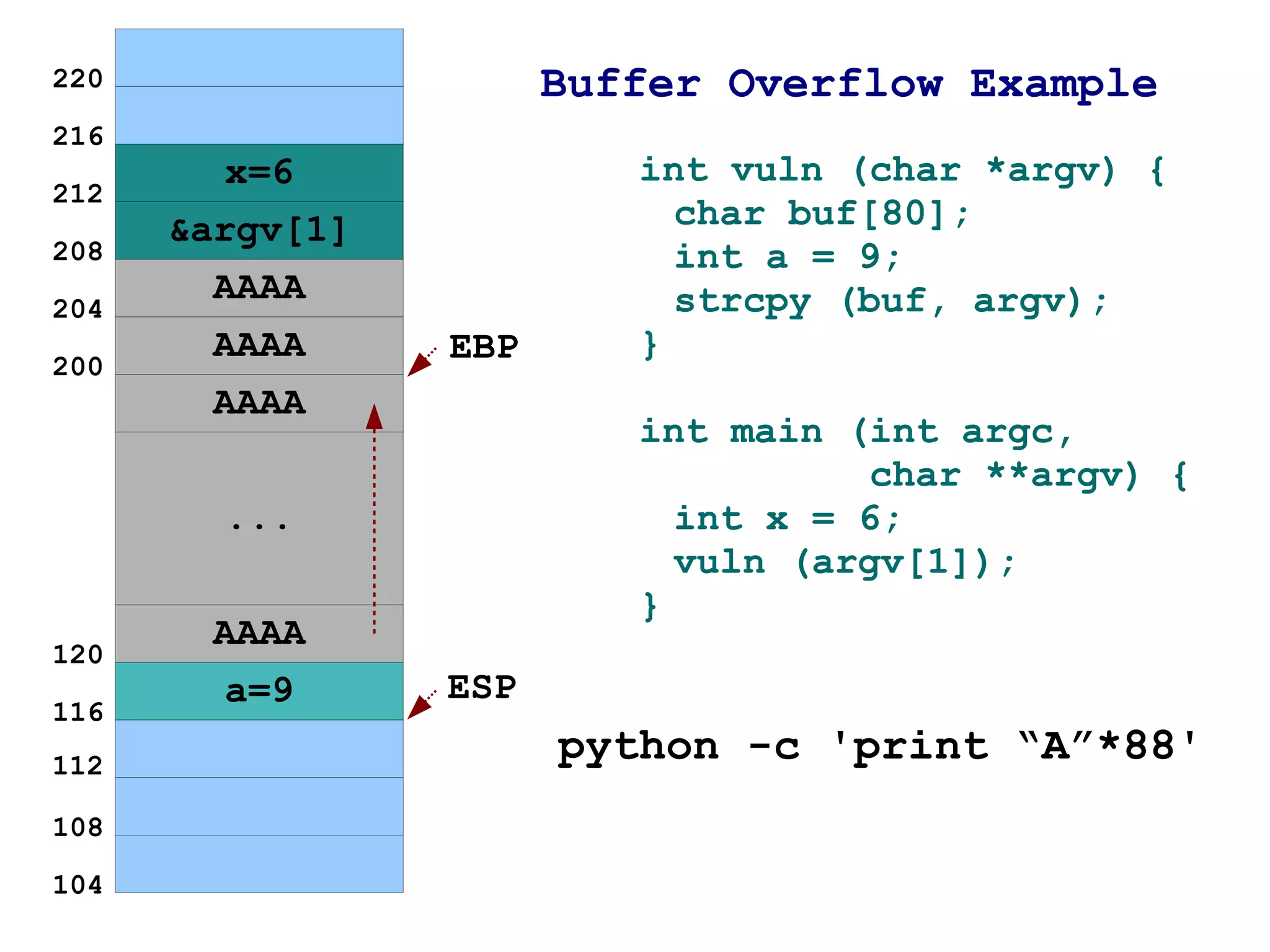
1) It explains how buffer overflows work by writing more data to a buffer than it was allocated to hold, overwriting adjacent memory.
2) An example is given of a function that is vulnerable to buffer overflow by copying user input into a fixed-size buffer without checks.
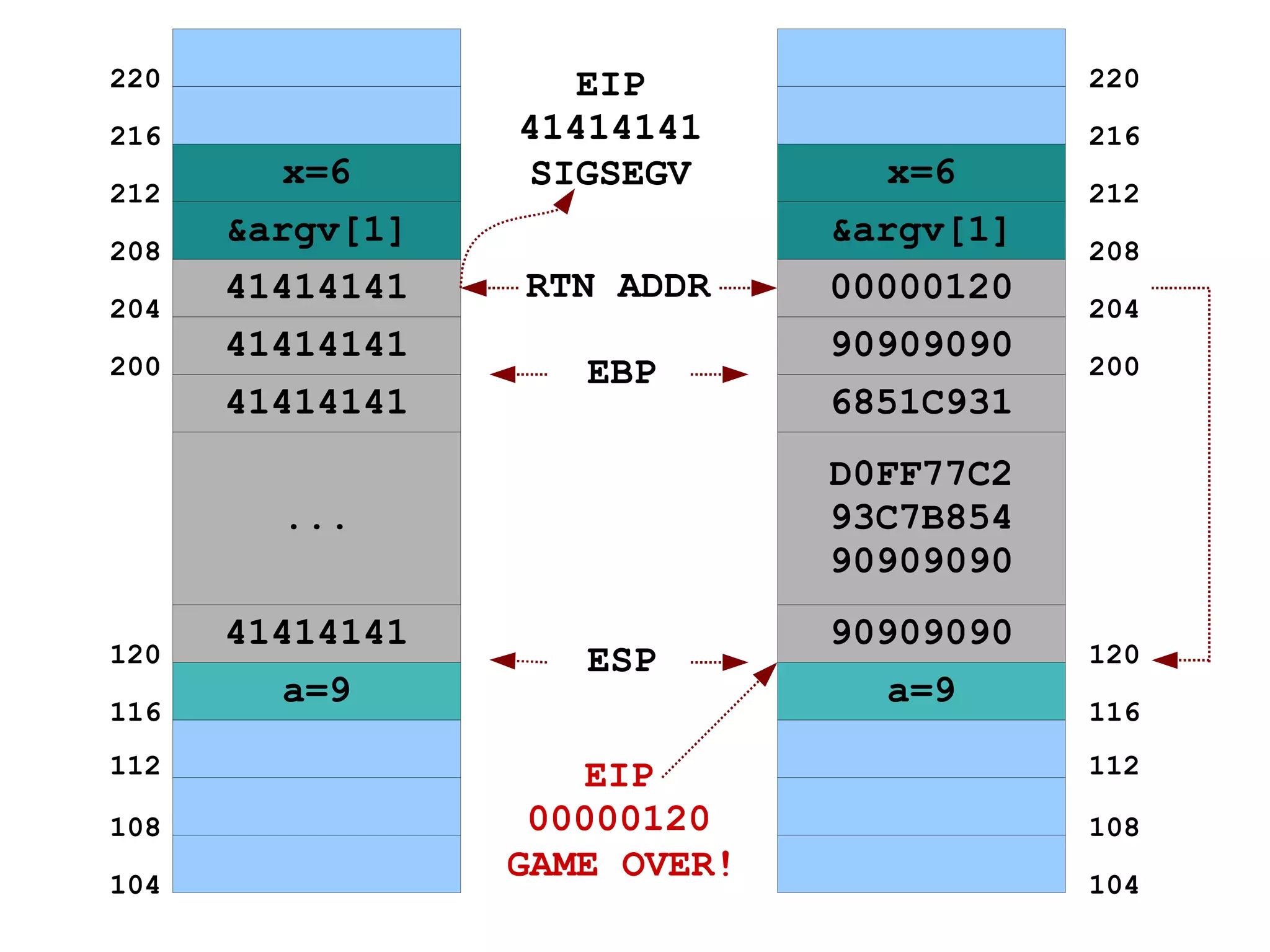
3) It shows how by passing too much input data, the buffer can be overflown and the return address on the stack overwritten to point to the injected data instead of the intended return location.