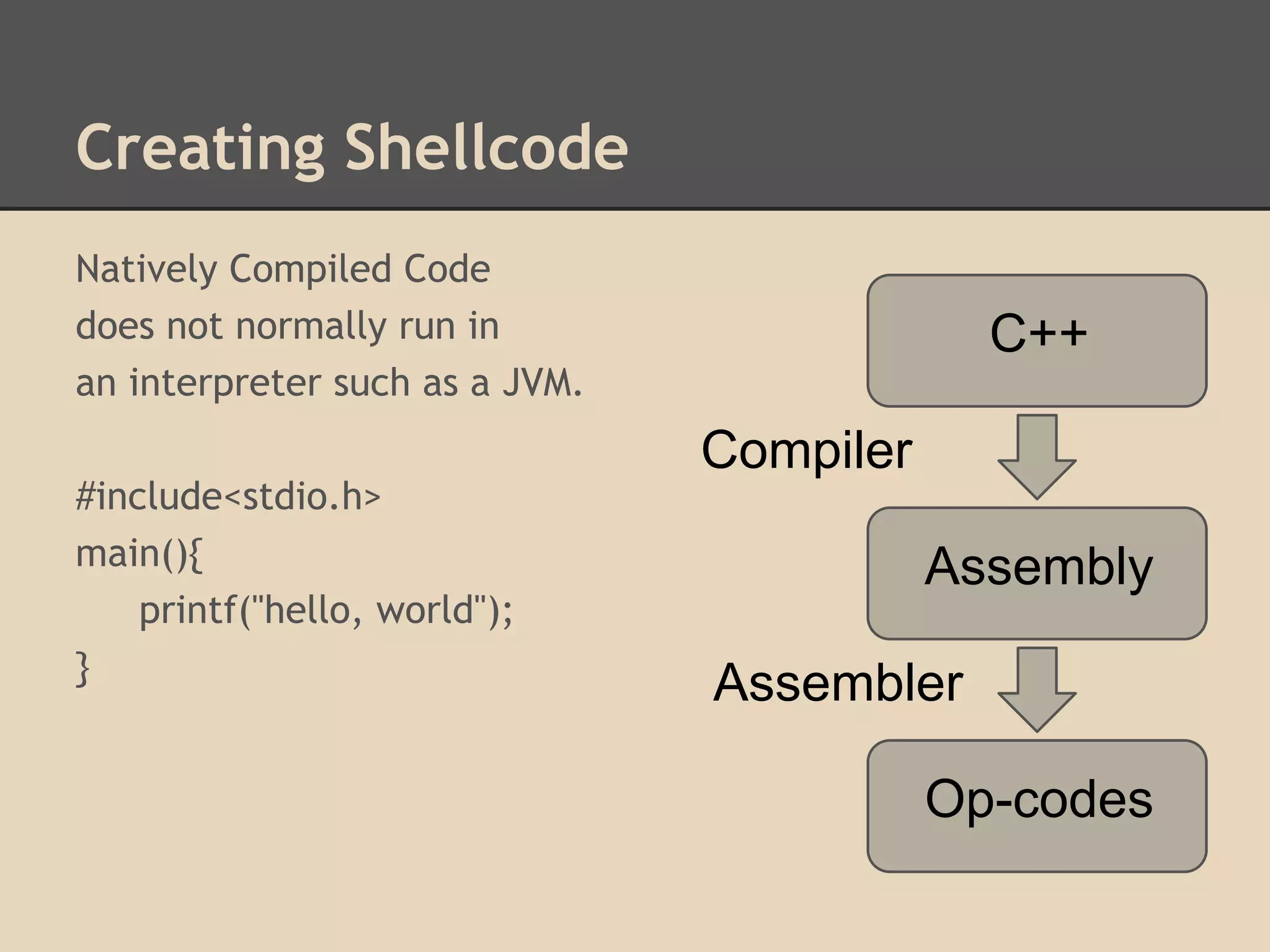
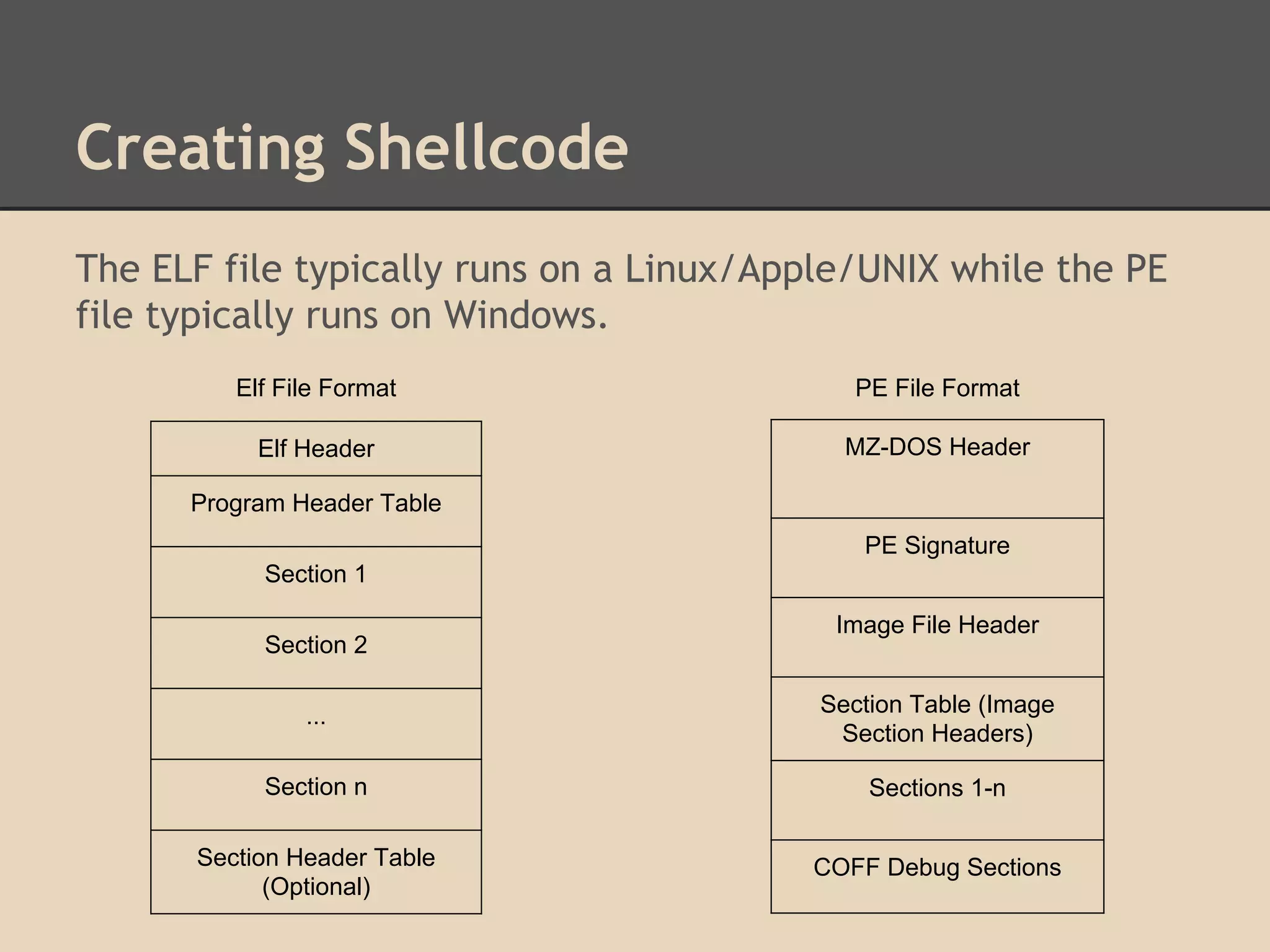
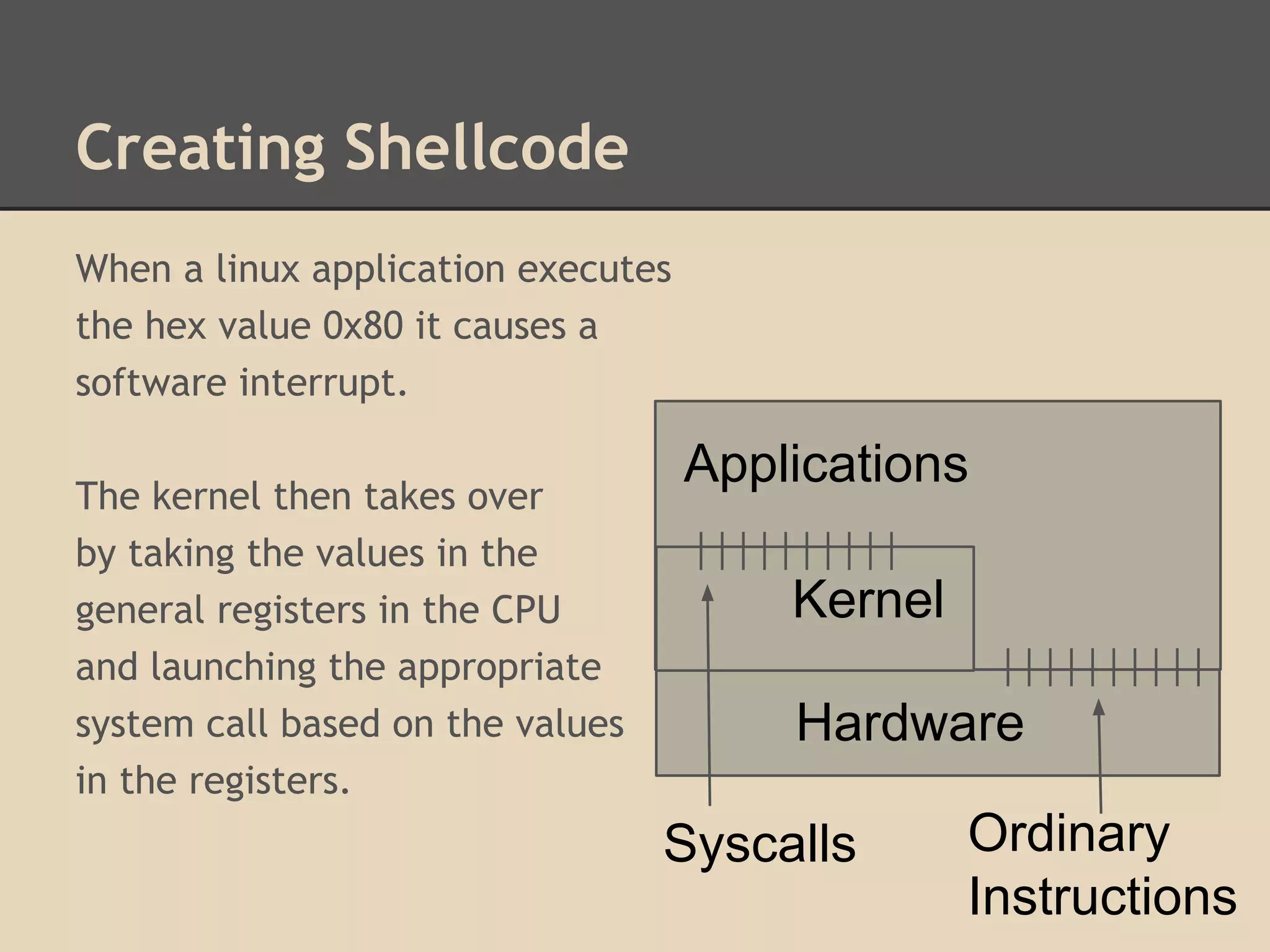
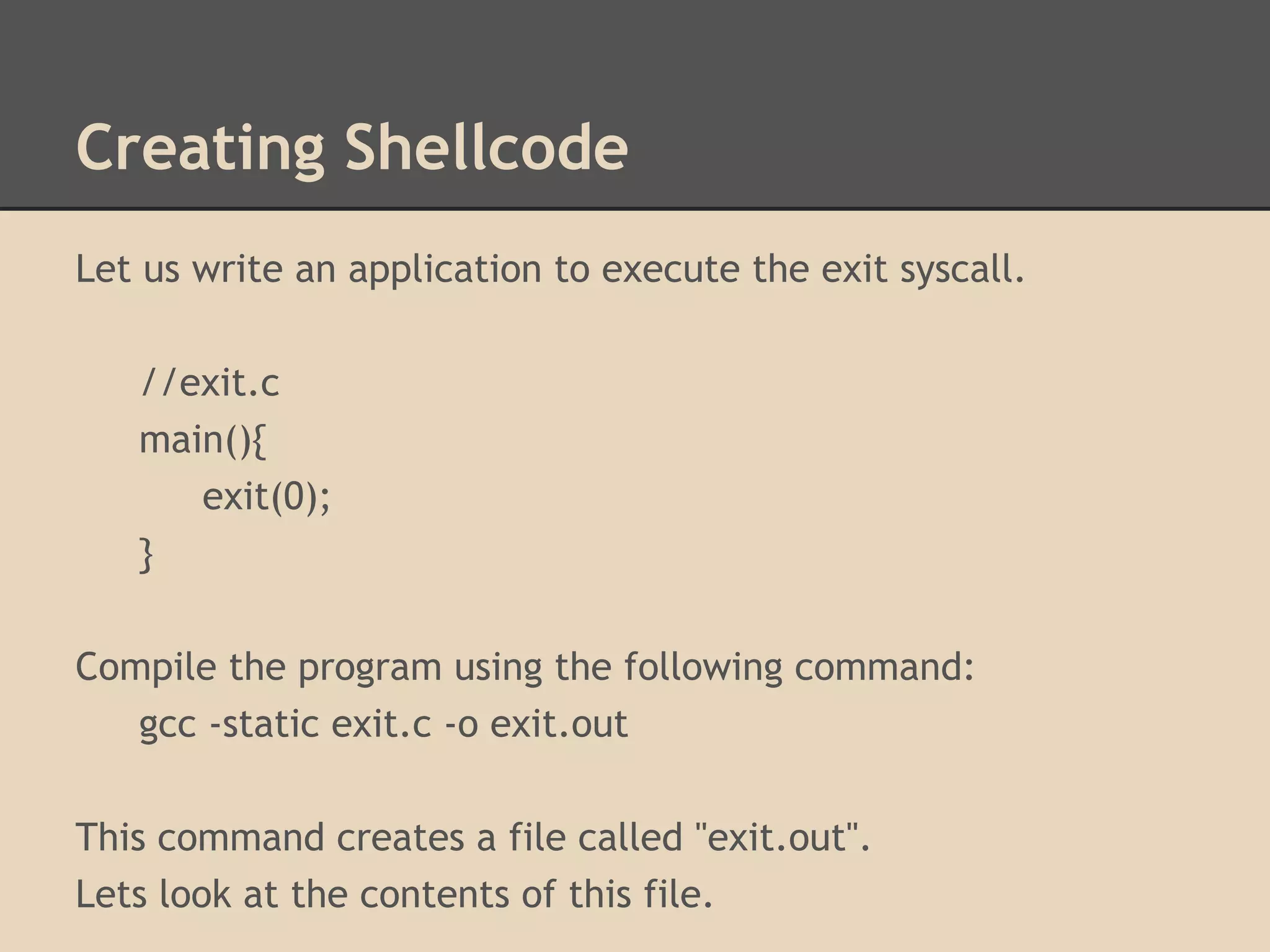
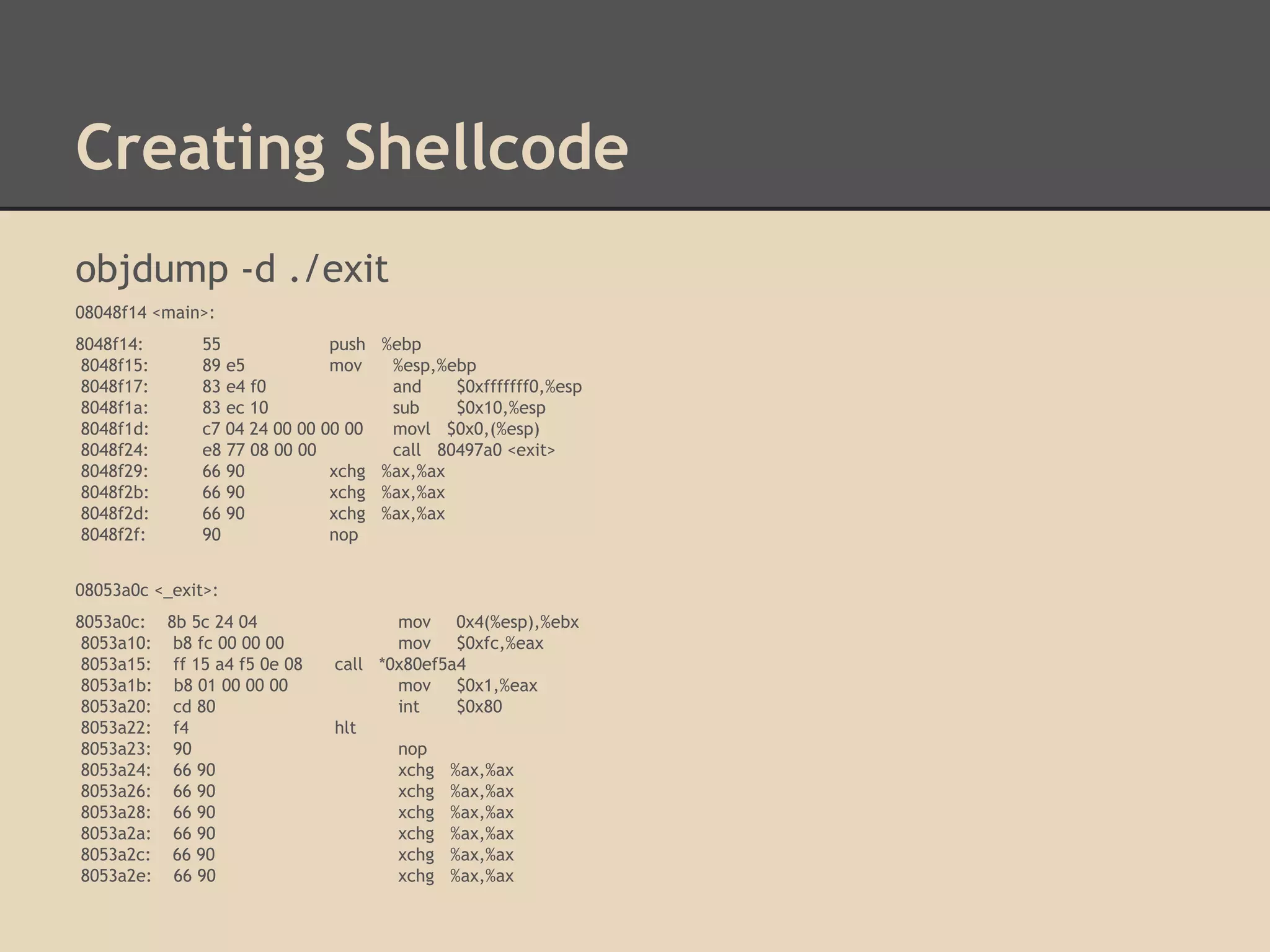
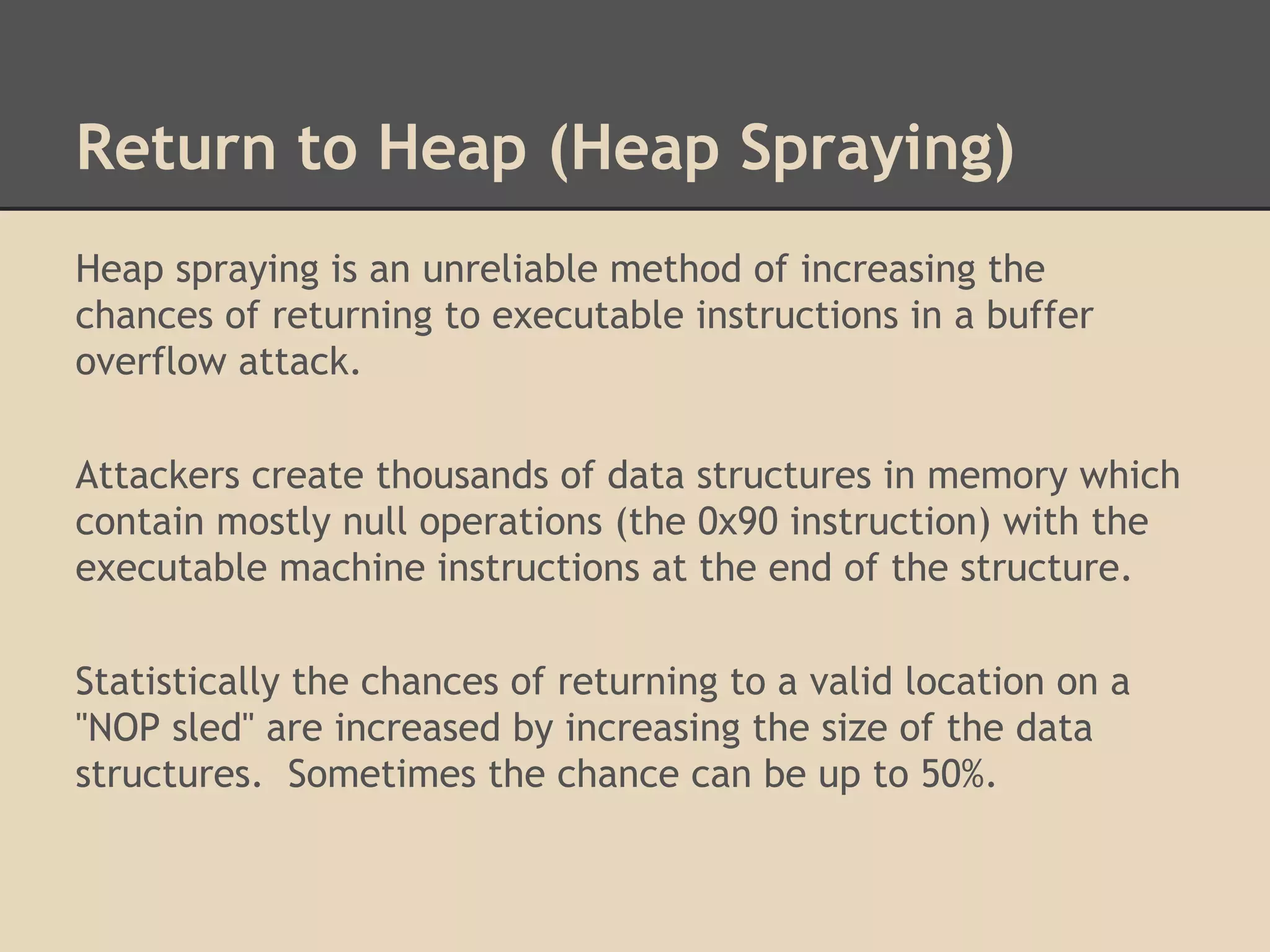
This document discusses various low-level exploits, beginning with creating shellcode by extracting opcodes from a compiled C program. It then covers stack-based buffer overflows, including return-to-stack exploits and return-to-libc. Next it discusses heap overflows using the unlink technique, integer overflows, and format string vulnerabilities. The document provides code examples and explanations of the techniques.







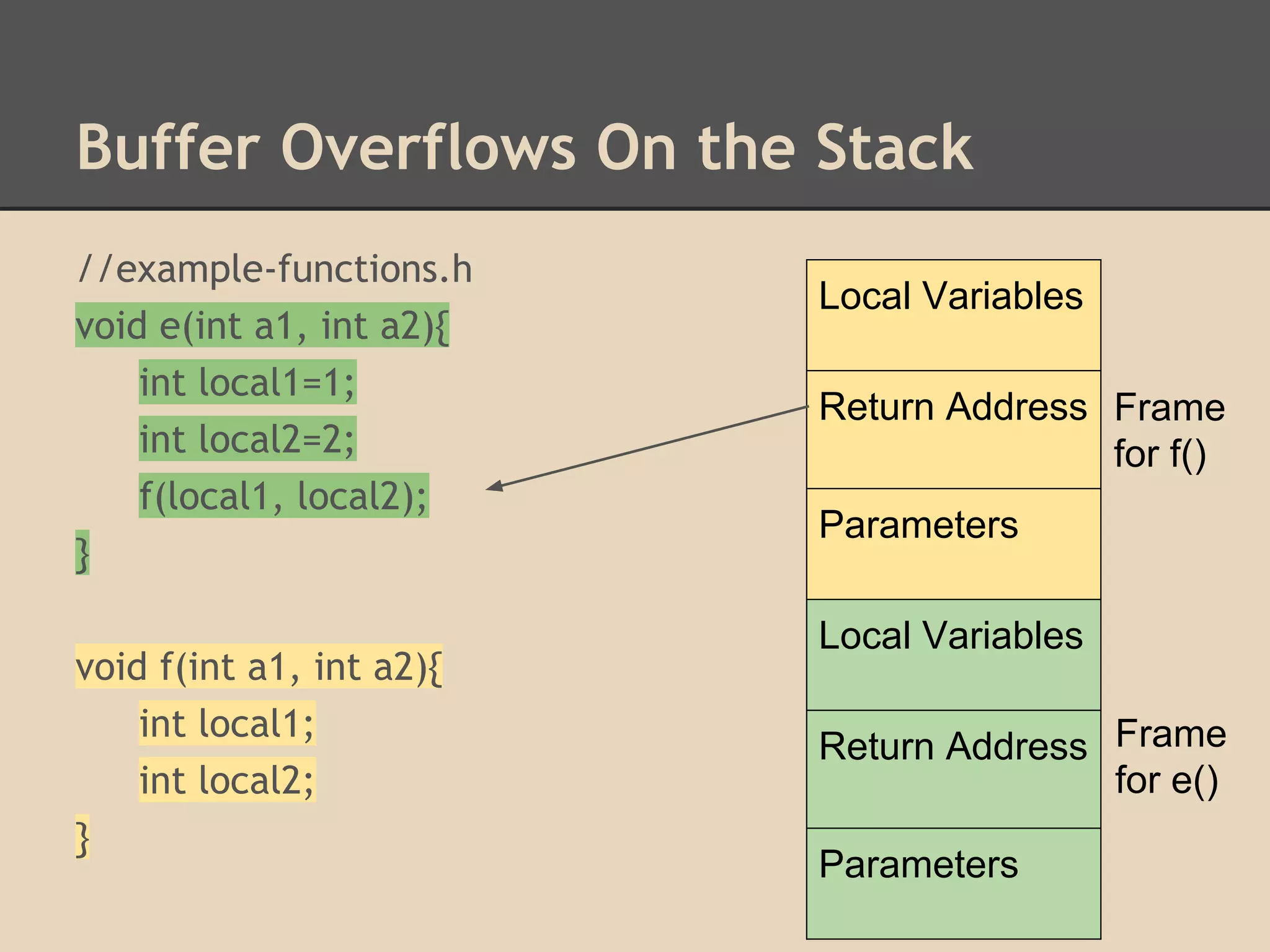
![Buffer Overflows On the Stack
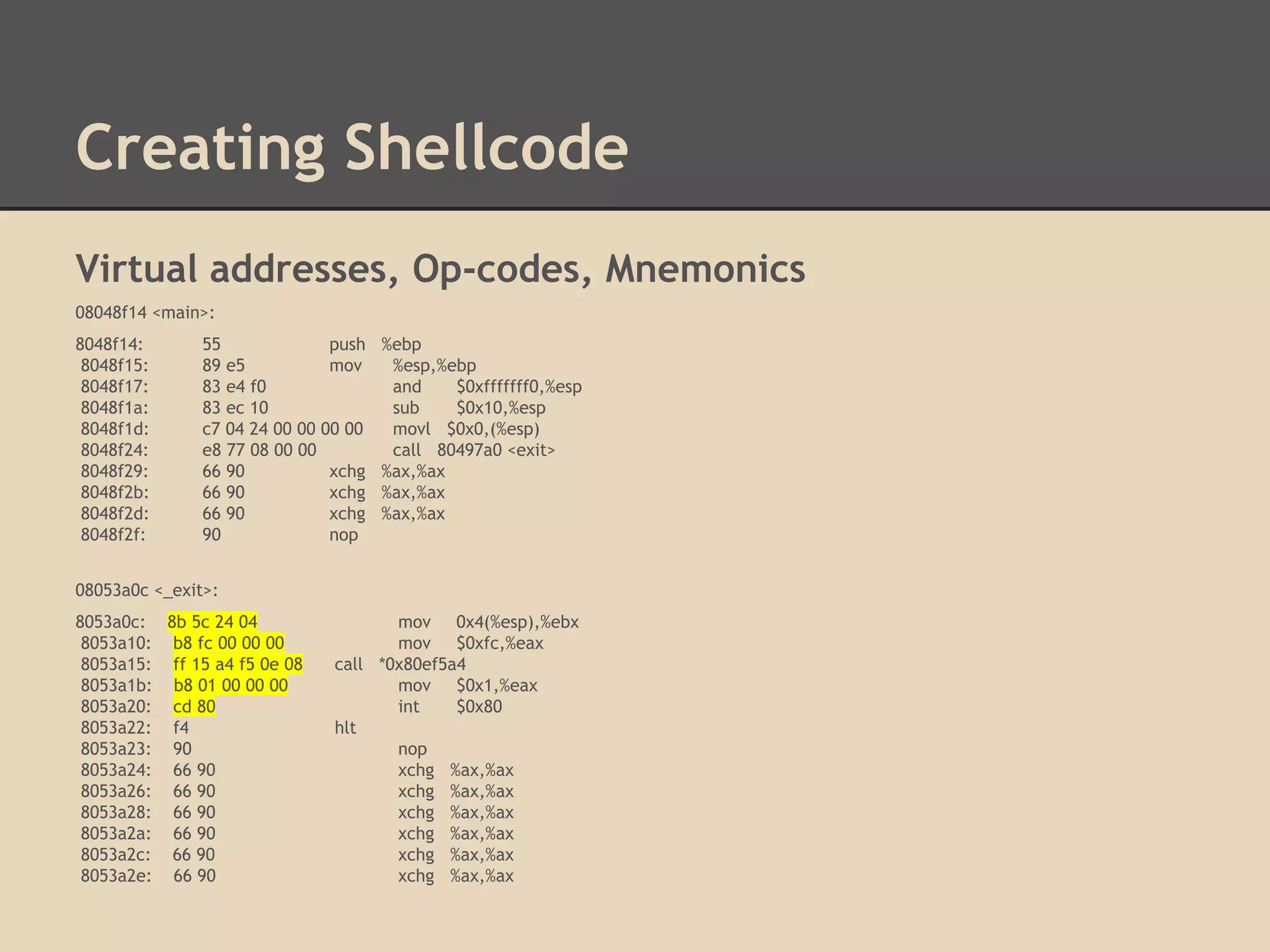
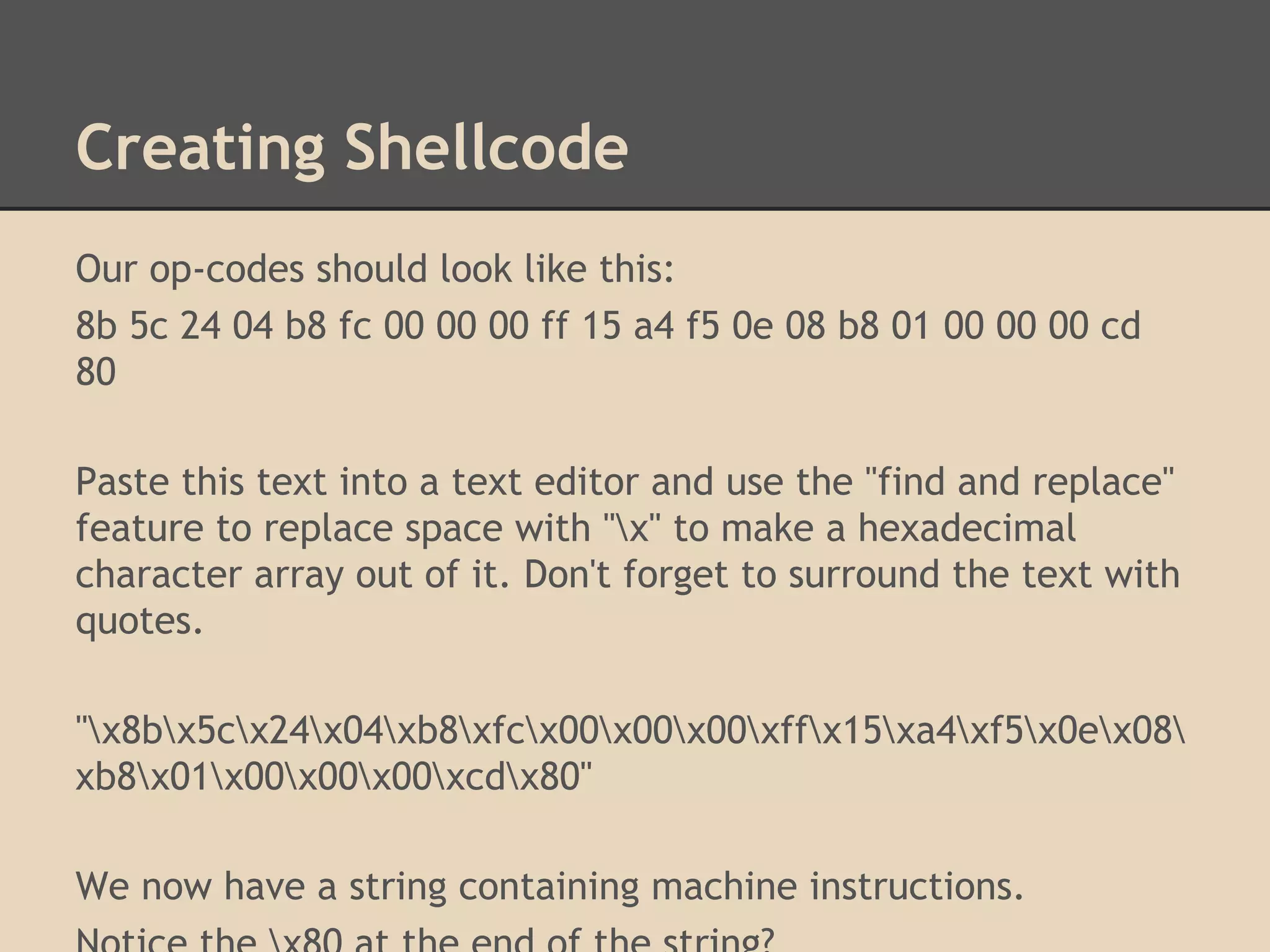
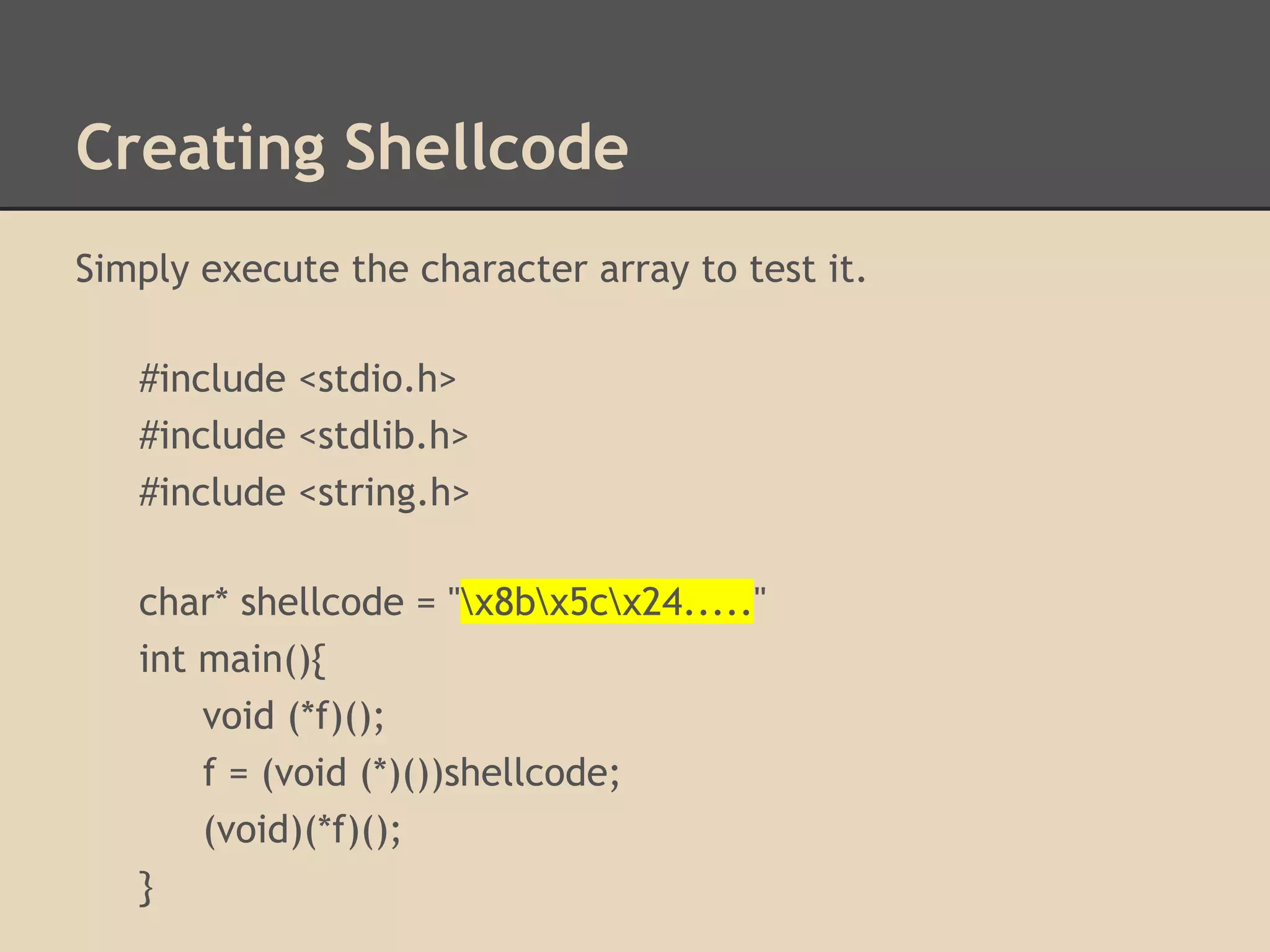
Find the address of other functions
that were statically compiled into the
program by using the command:
gdb -q -ex "info functions" --batch
./hello-world | tr -s " " |
cut -d " " -f 2 | sort | uniq
[AAAA][AAAA][AAAA][AAAA]
[AAAA][function return address]
[AAAA][AAAA]
[AAAA][AAAA]
Frame
[AAAA]
for f()
[function
return address]
Parameters
Local Variables
Return Address
Function F does not return to E;
Function F returns to X.
Parameters
Frame
for e()](https://image.slidesharecdn.com/137730145-low-level-exploits-131023172911-phpapp01/75/Low-Level-Exploits-18-2048.jpg)
![Return to Stack
Return to Stack
A buffer overflow attack is a general definition for a class of
attacks to put more data in a buffer than it can hold thus
overwriting the return address.
Return to Stack is a specific stack buffer overflow attack where
the return address is the same as the address on the stack for
storing the variable information. Thus you are executing the
stack.
[instructions][instructions][return address]](https://image.slidesharecdn.com/137730145-low-level-exploits-131023172911-phpapp01/75/Low-Level-Exploits-20-2048.jpg)
![Return to Stack
As you can see in the diagram
the local variables of the
function have been overwritten.
The Return to Stack exploit
is also known as "Smashing The
Stack".
[instructions]
[instructions]
[stack return
address]
Frame
for f()
Parameters
Local Variables
Return Address
Parameters
Frame
for e()](https://image.slidesharecdn.com/137730145-low-level-exploits-131023172911-phpapp01/75/Low-Level-Exploits-21-2048.jpg)

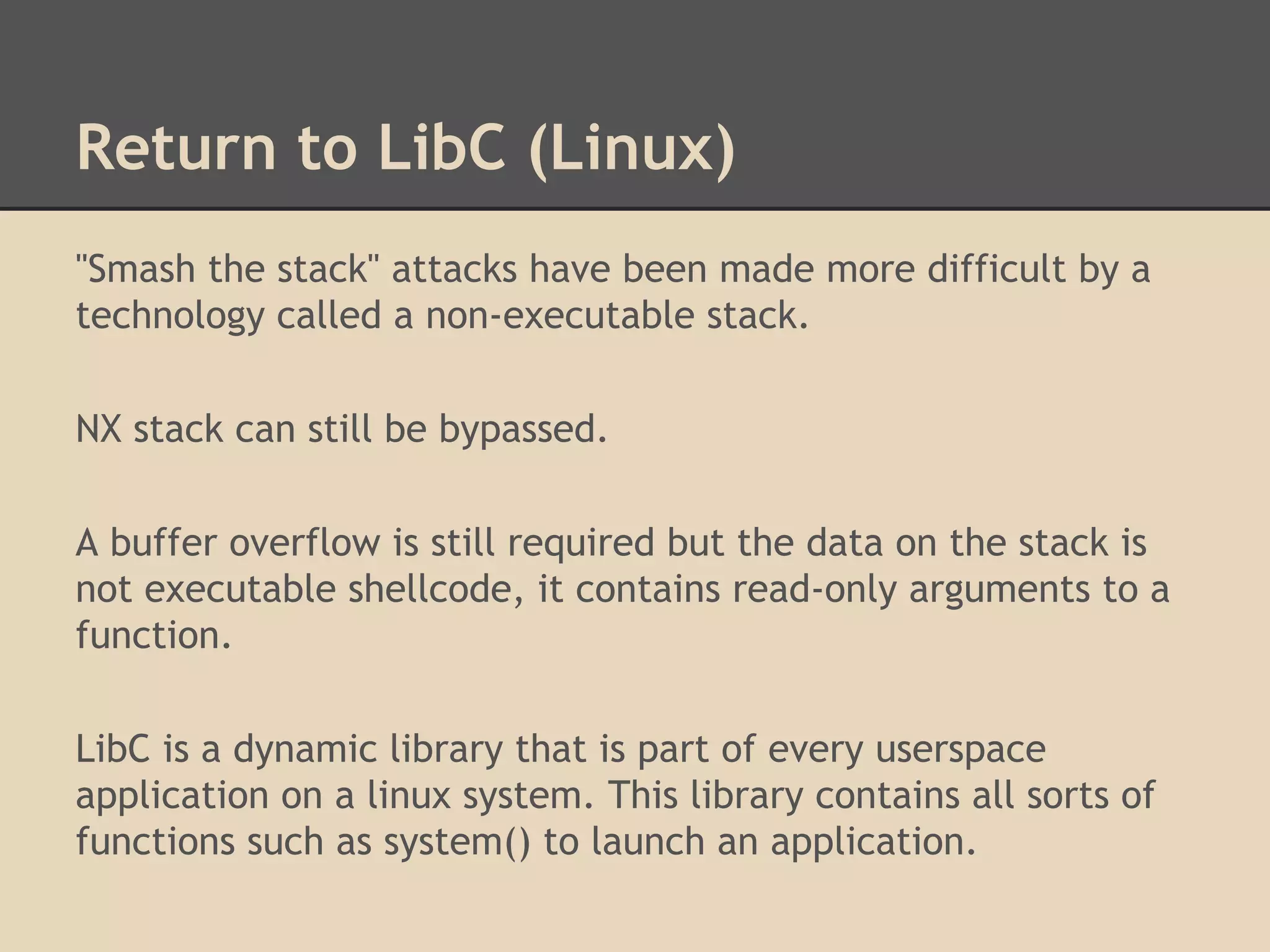
![Return to LibC (Linux)
Now we can
spawn a shell
system("/bin/bash wget ...");
system()
in LibC [arguments]
[arguments]
[stack return
address]
Frame
for f()
Parameters
Local Variables
Return Address
Parameters
Frame
for e()](https://image.slidesharecdn.com/137730145-low-level-exploits-131023172911-phpapp01/75/Low-Level-Exploits-24-2048.jpg)

![Return to SEH (Windows)
Stack cookies are numbers that are placed before the return
address when a function begins, and checked before the
function returns. This prevents buffer overflow attacks.
[buffer][cookie][saved EBP][saved EIP]](https://image.slidesharecdn.com/137730145-low-level-exploits-131023172911-phpapp01/75/Low-Level-Exploits-26-2048.jpg)
![Return to SEH (Windows)
If the overwritten cookie does not match with the original
cookie, the code checks to see if there is a developer defined
exception handler. If not, the OS exception handler will kick in.
[buffer][cookie][SEH record][saved ebp][saved eip]
(1.) - Overwrite an Exception Handler registration structure
(2.) - Trigger an exception before the cookie is checked
(3.) - Return to overwritten Exception Handler](https://image.slidesharecdn.com/137730145-low-level-exploits-131023172911-phpapp01/75/Low-Level-Exploits-27-2048.jpg)
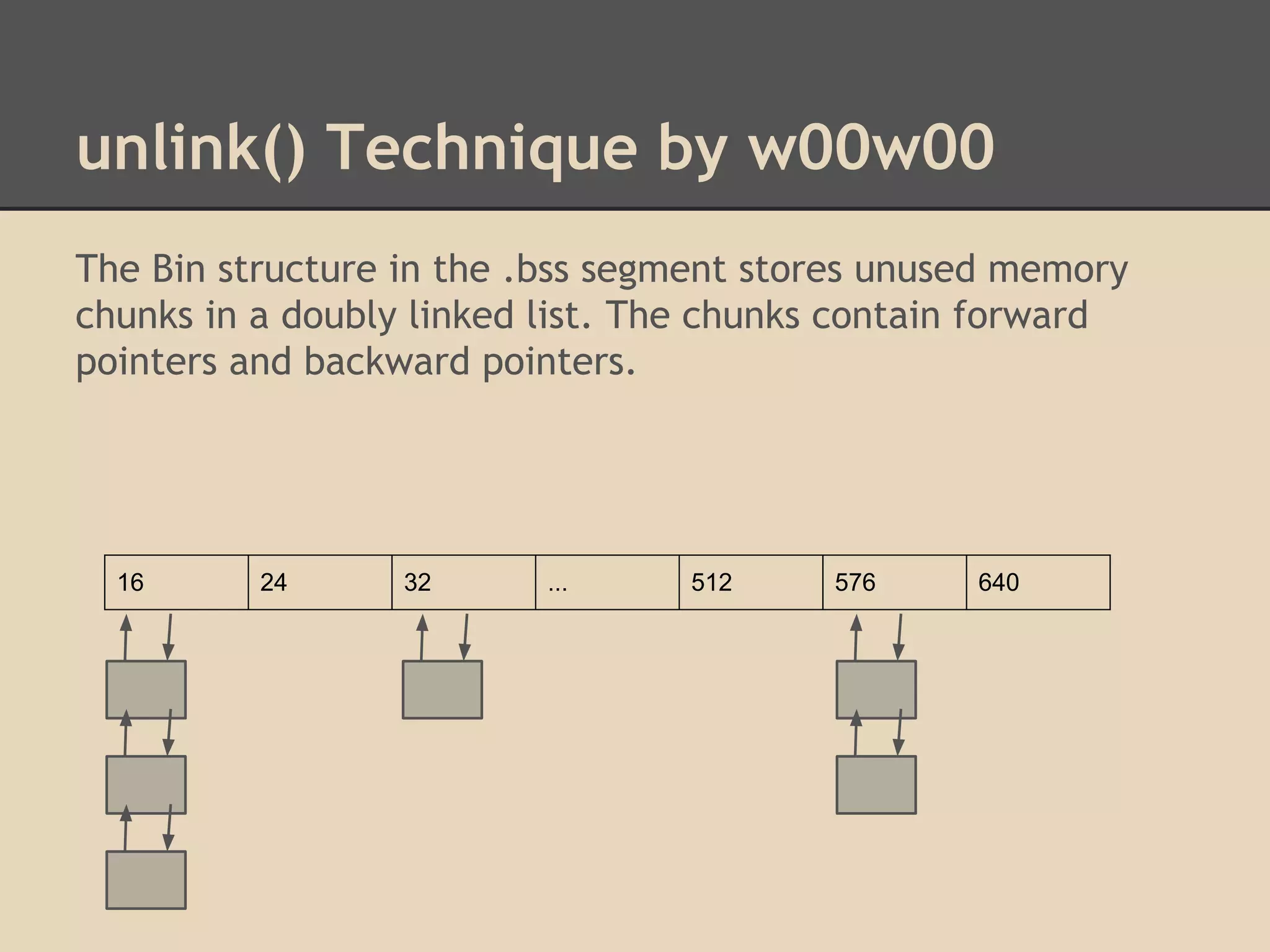

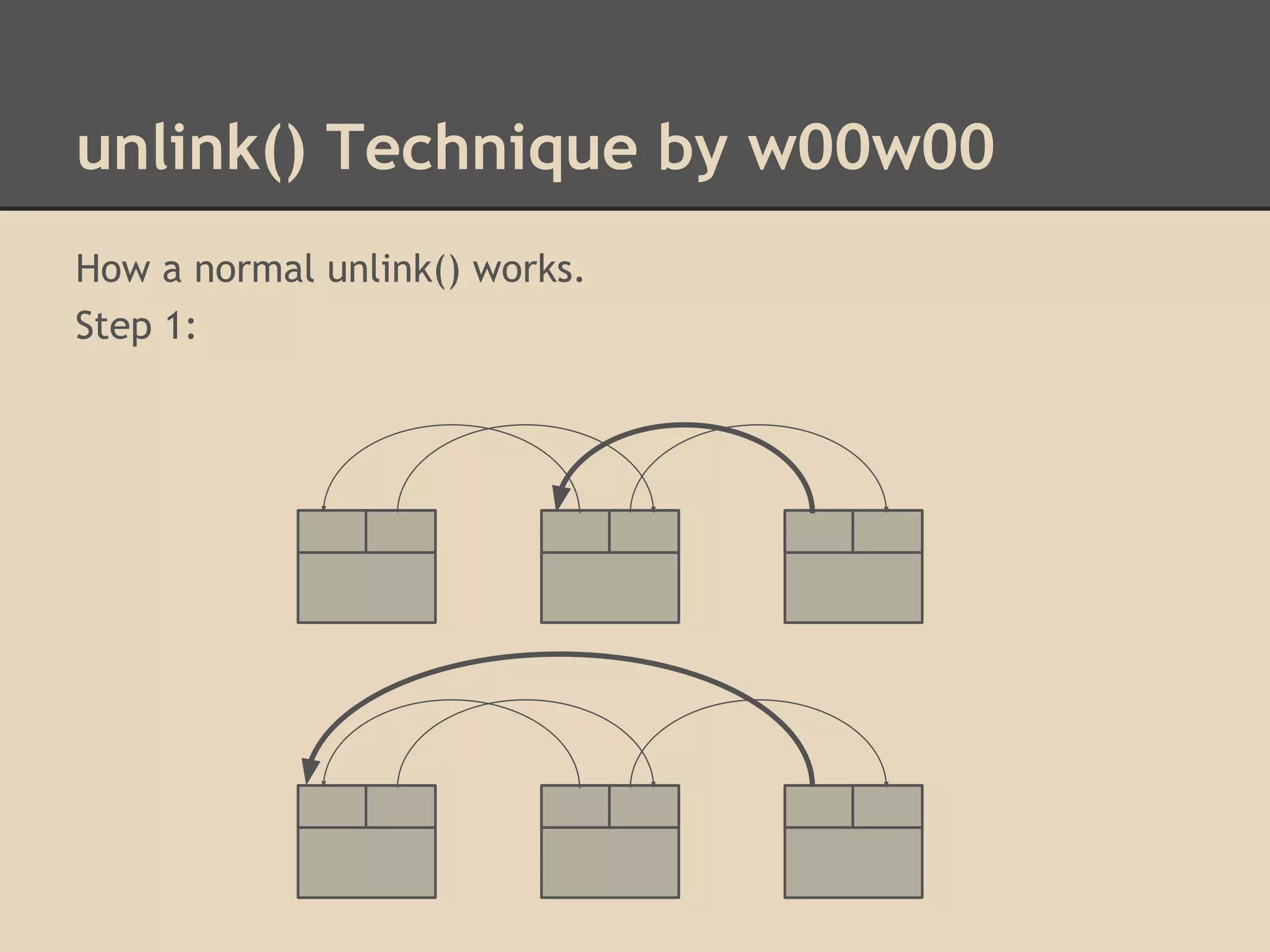
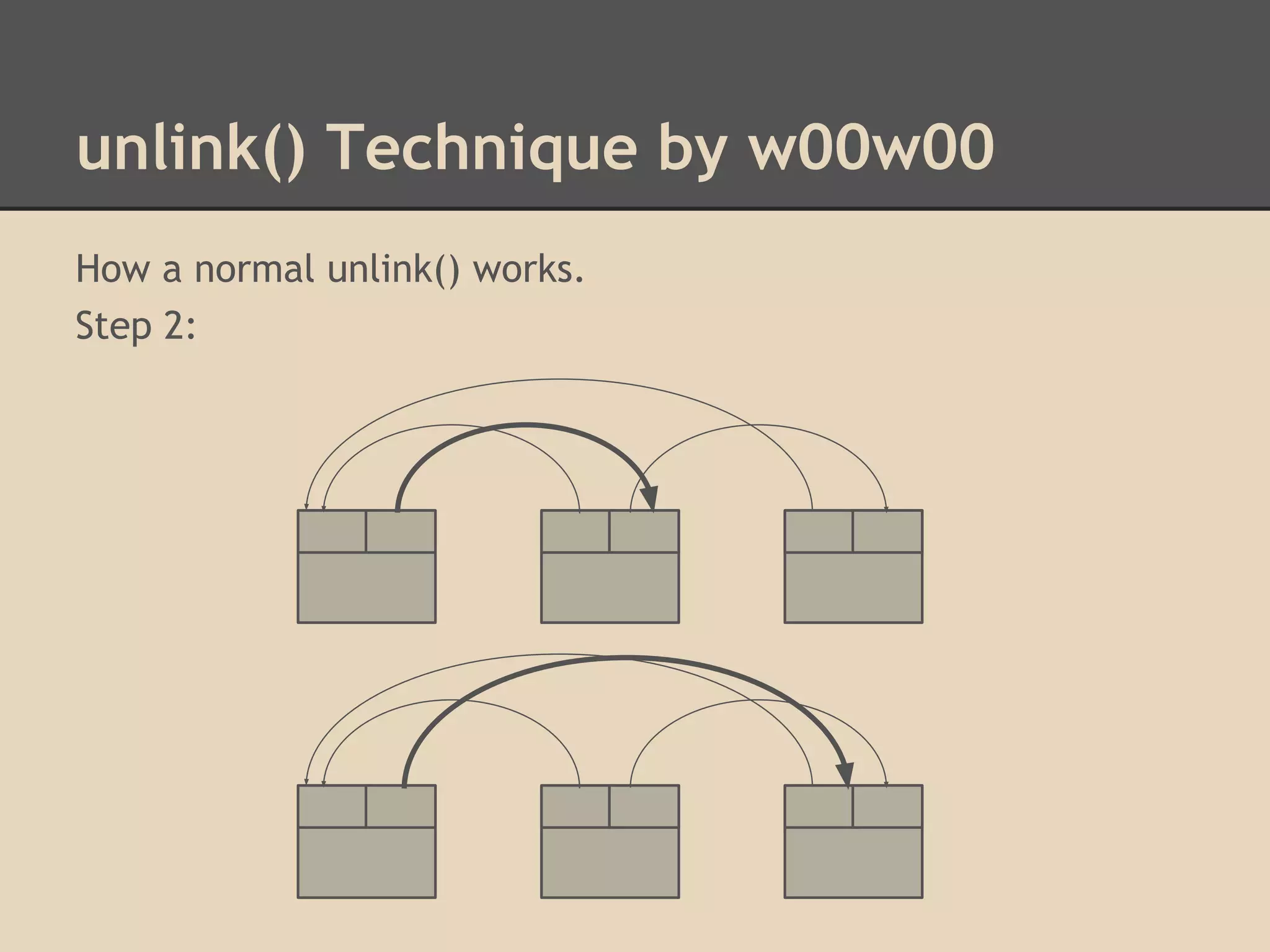
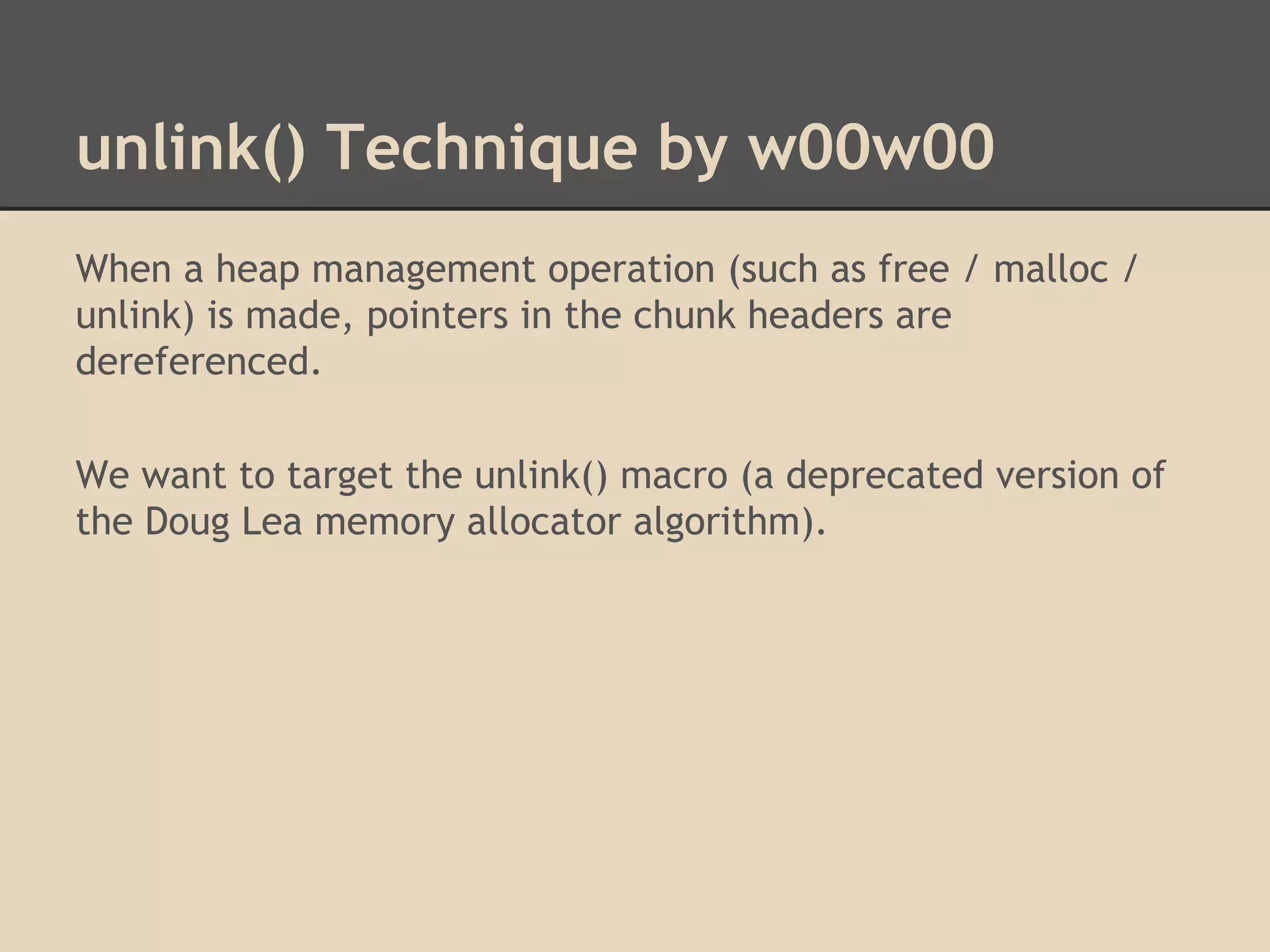
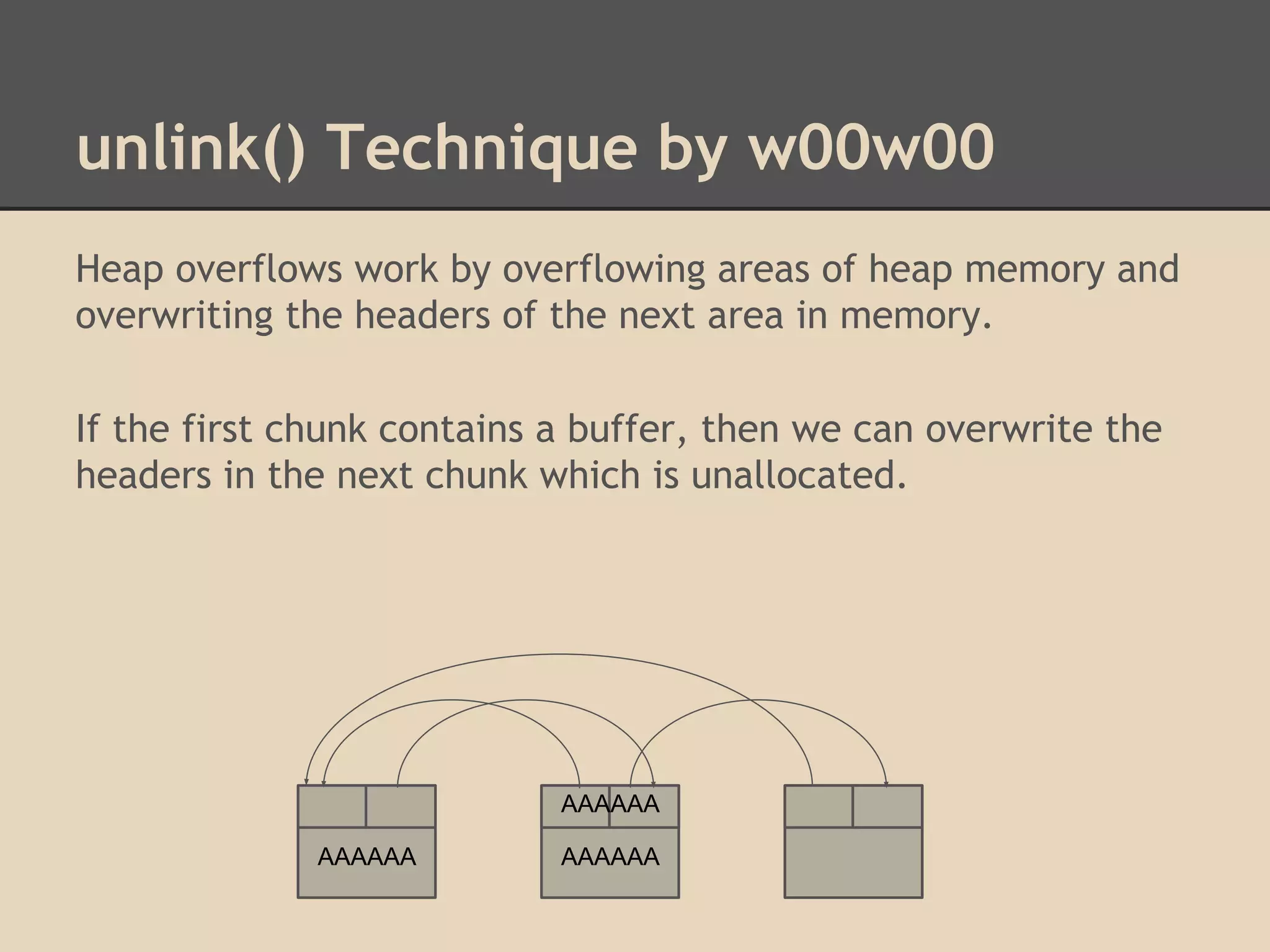
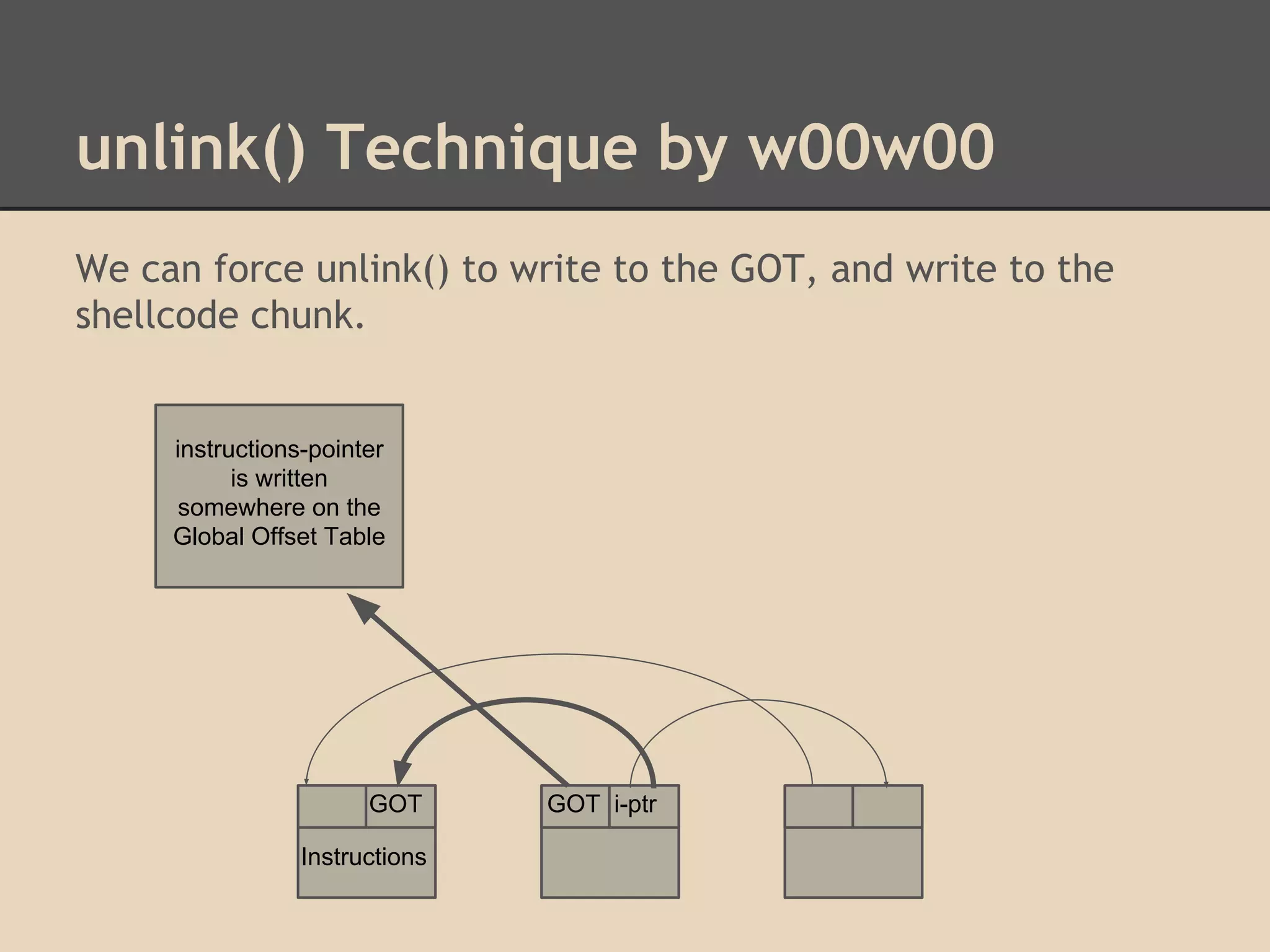
![unlink() Technique by w00w00
By altering these pointers we can write to arbitrary addresses
in memory. Dereferencing is confusing!
Unlink has 2 write operations. By overwriting the header of a
chunk, we can choose what we write to memory!
[fwd-ptr] = bk-ptr
and
[bk-ptr] = fwd-ptr
Try overwriting pointers in the Global Offset Table.](https://image.slidesharecdn.com/137730145-low-level-exploits-131023172911-phpapp01/75/Low-Level-Exploits-37-2048.jpg)


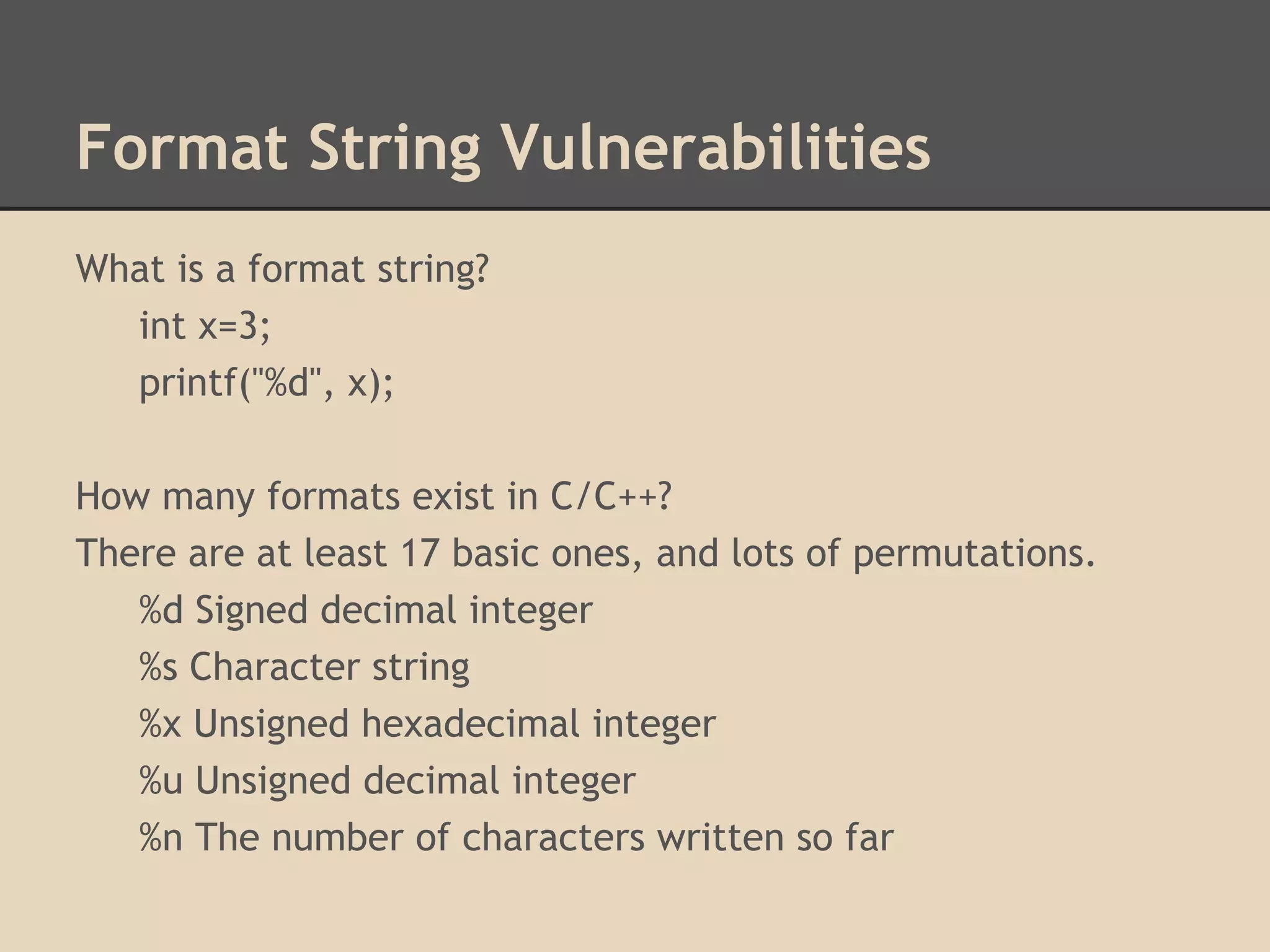
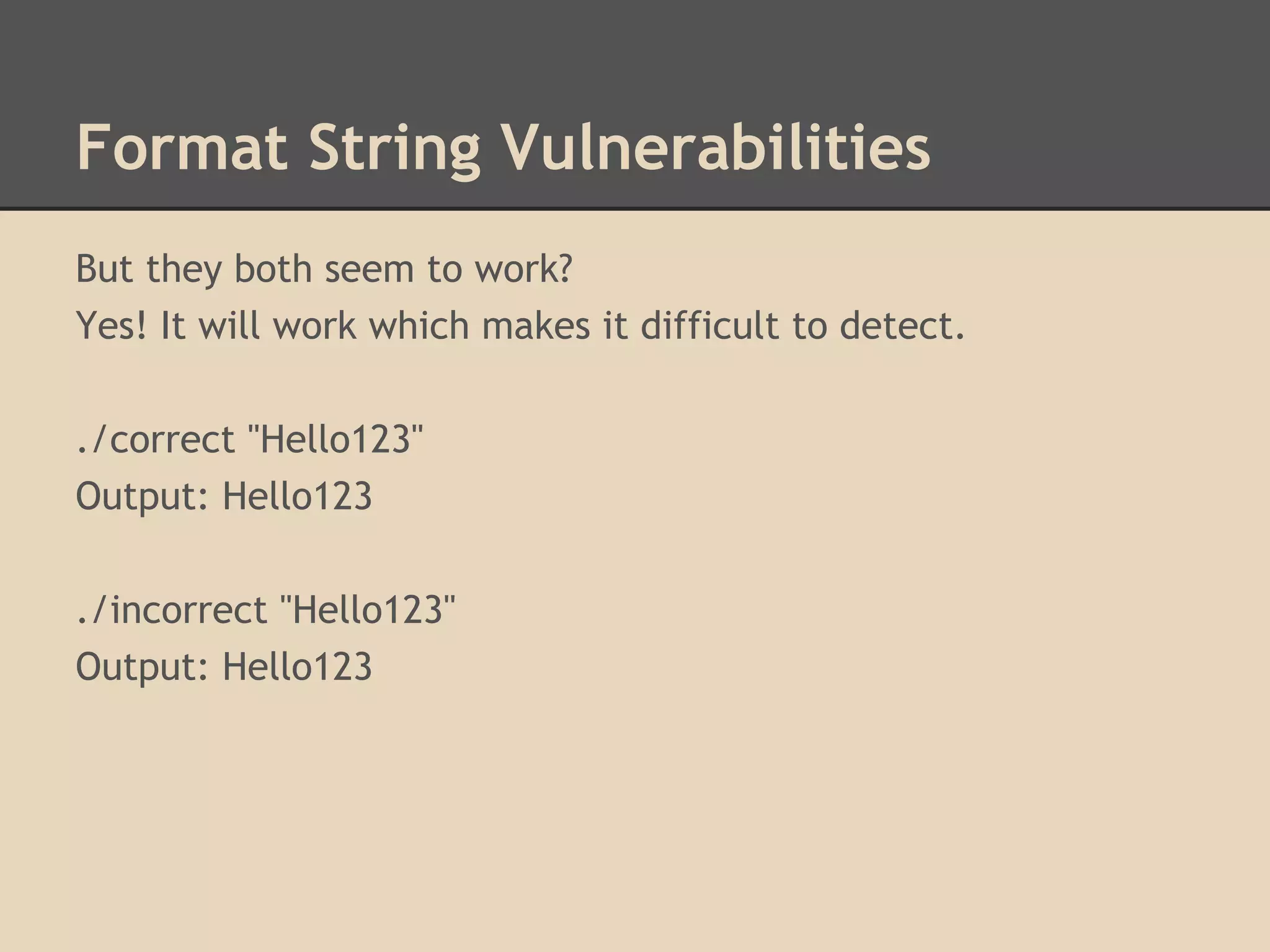
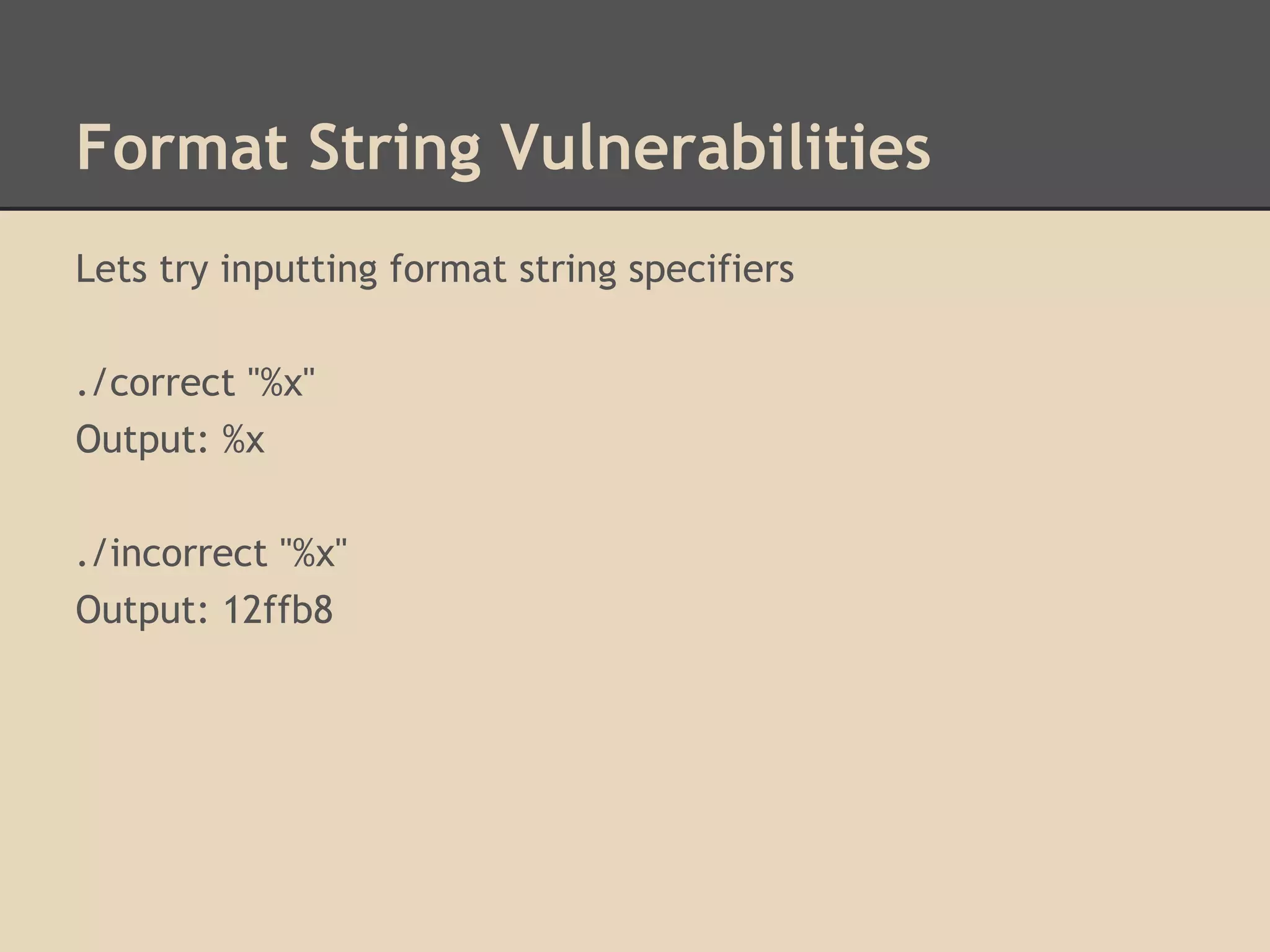
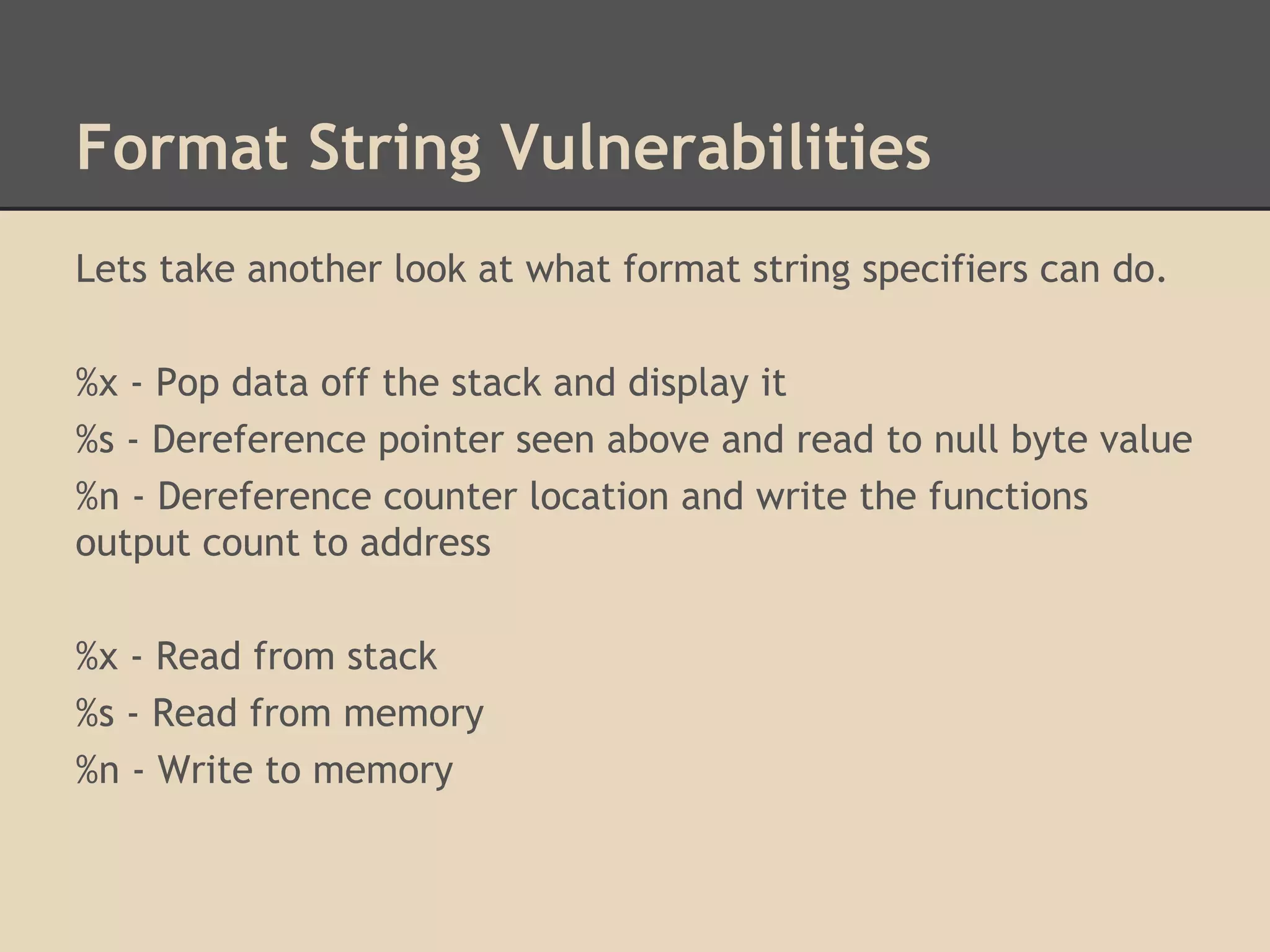
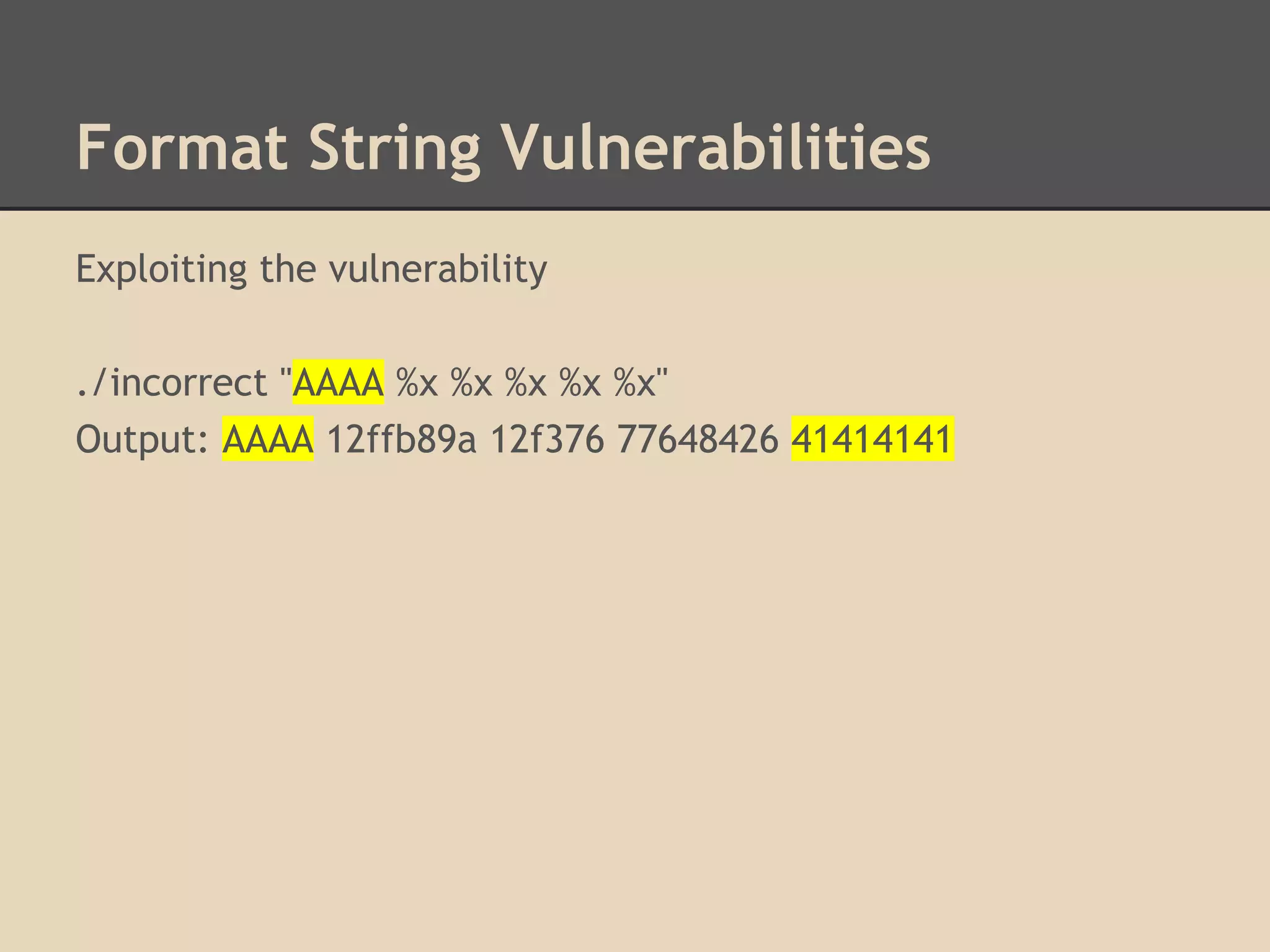
![Format String Vulnerabilities
How do format string vulnerabilities occur?
They are usually lazy programmers who make mistakes.
This is correct:
printf("%s", argv[1]);
This is incorrect:
printf(argv[1]);
#include <stdio.h>
void main(int argc, char *argv[]){
printf("%s", argv[1]);
}](https://image.slidesharecdn.com/137730145-low-level-exploits-131023172911-phpapp01/75/Low-Level-Exploits-46-2048.jpg)



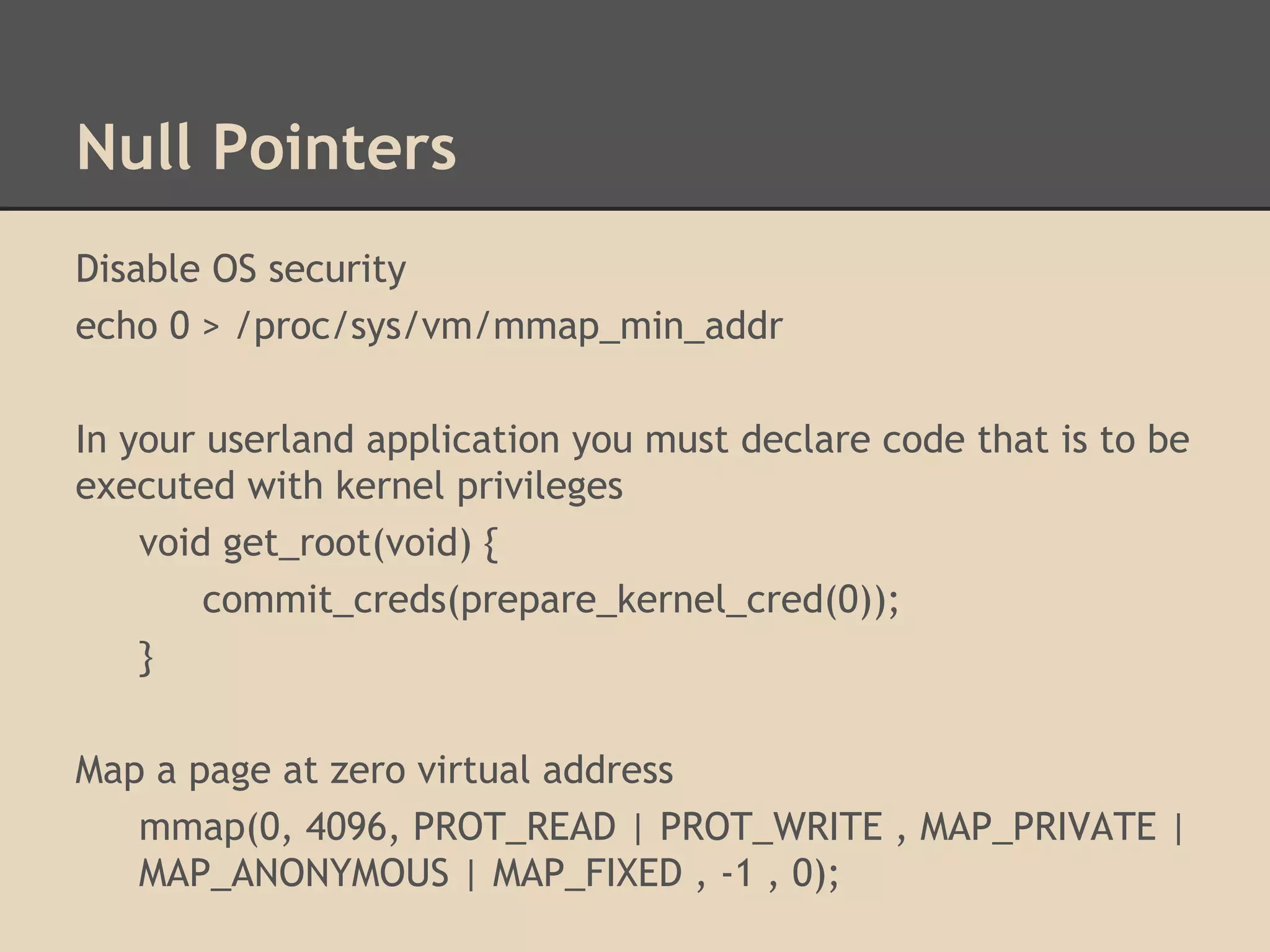

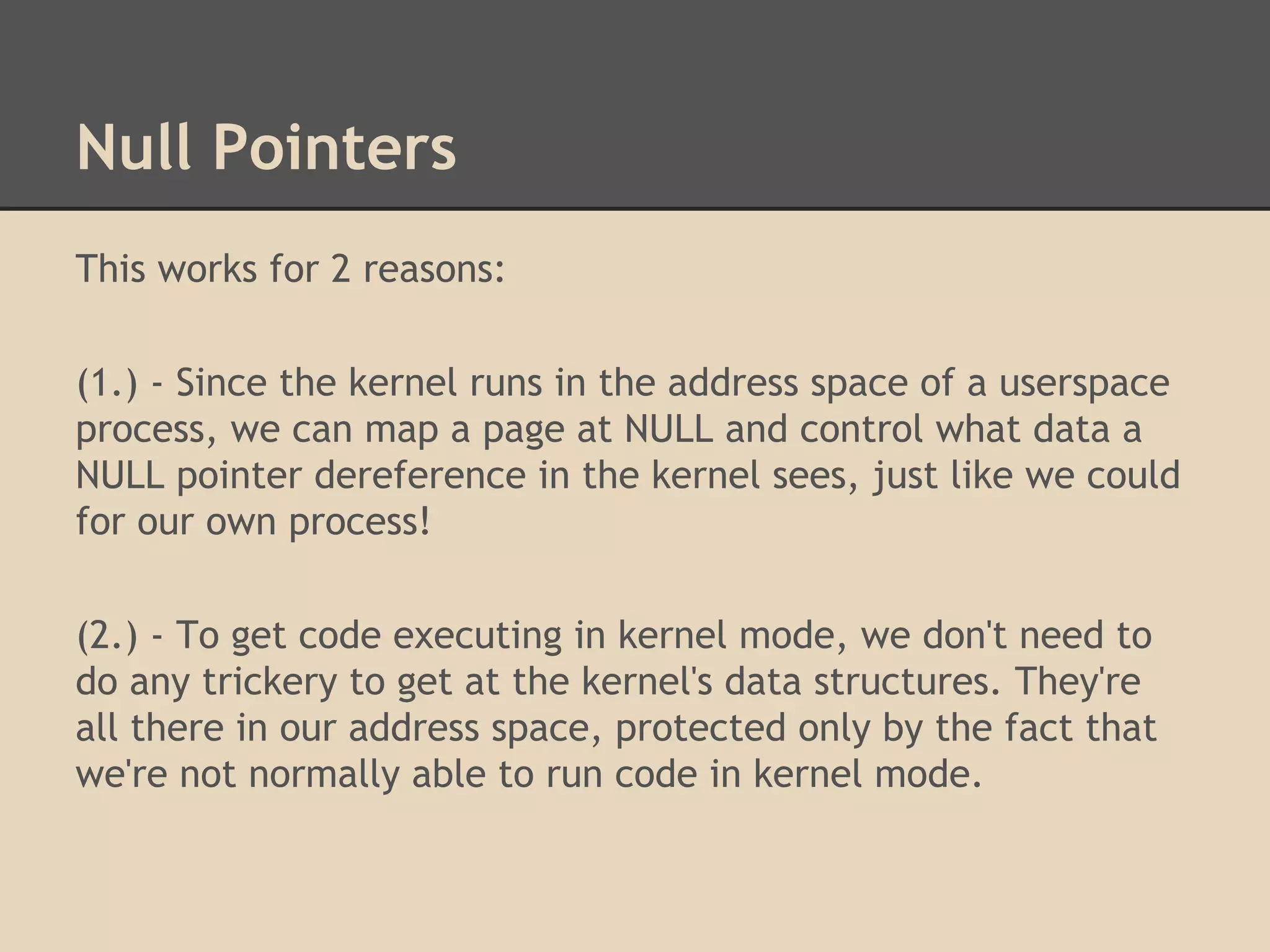

![ROP Chains
A single gadget would just
continue to follow a path of
execution that is being stored
in the stack.
This means we only control
the instruction pointer for 2
instructions.
We have to select a gadget
that can alter multiple frames.
ROP
Gadget
[AAAA][AAAA]
[AAAA][AAAA]
Frame
[AAAA][stack
return address] for f()
Parameters
Local Variables
Return Address
Parameters
Frame
for e()](https://image.slidesharecdn.com/137730145-low-level-exploits-131023172911-phpapp01/75/Low-Level-Exploits-62-2048.jpg)