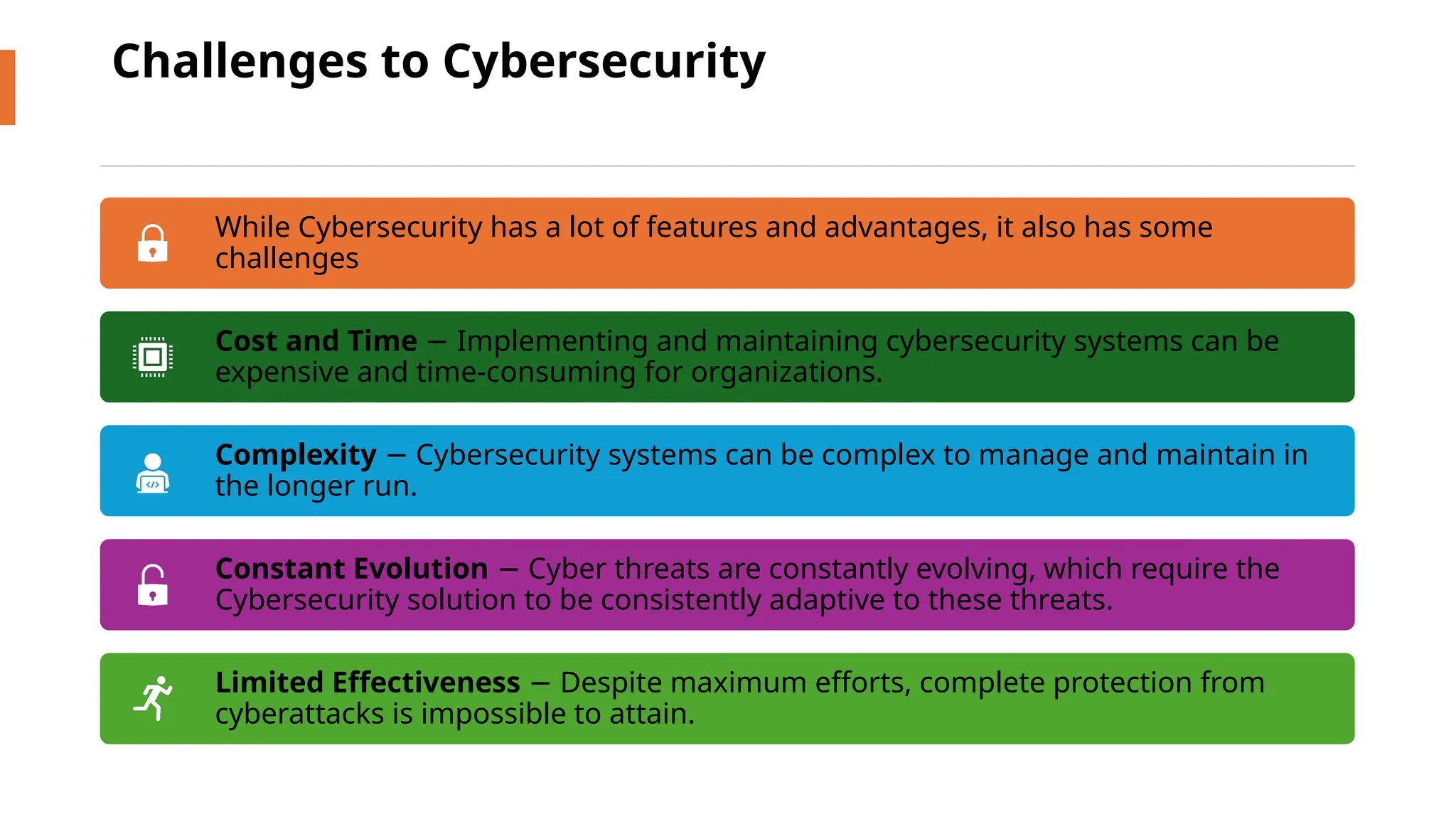
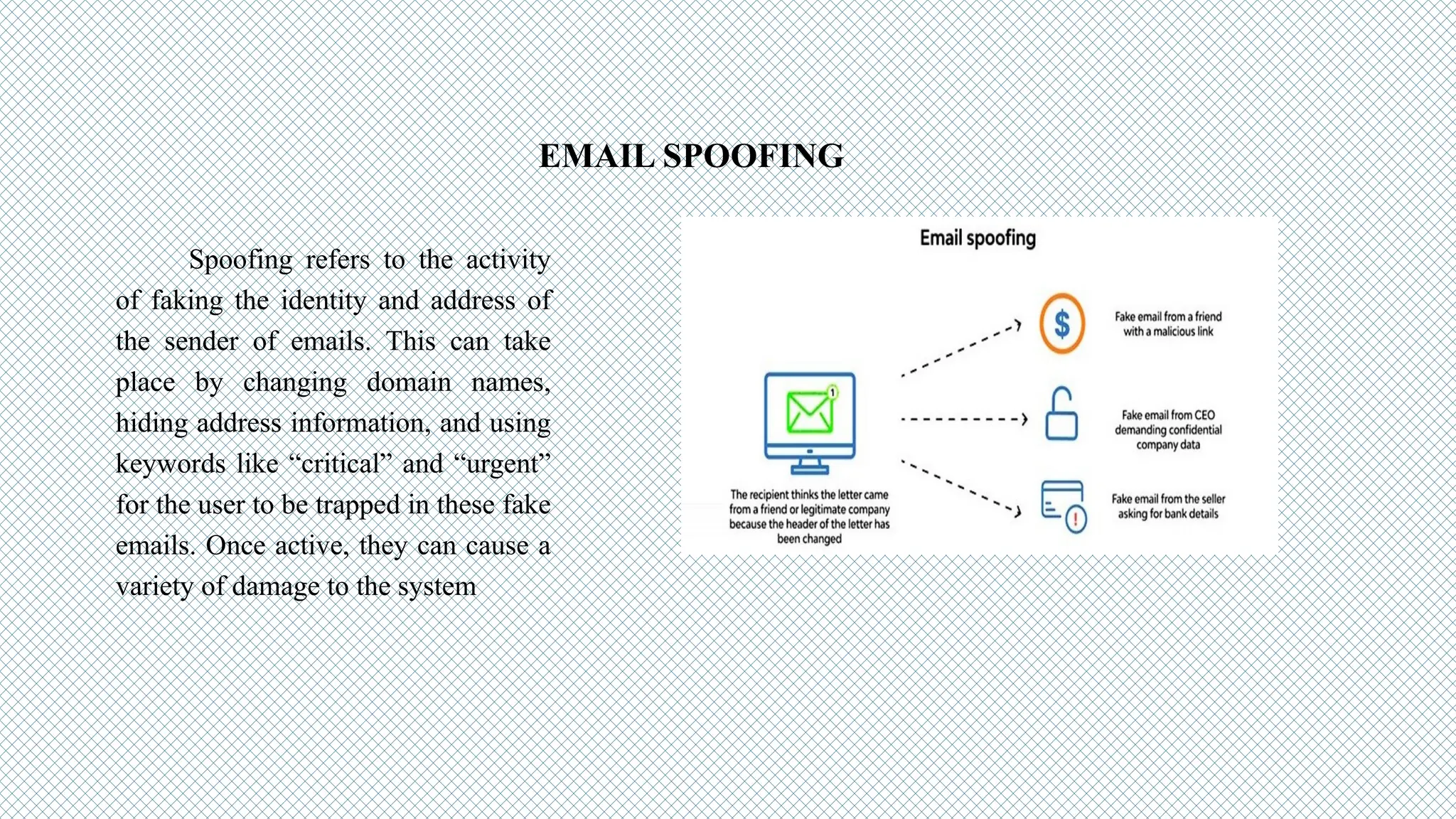
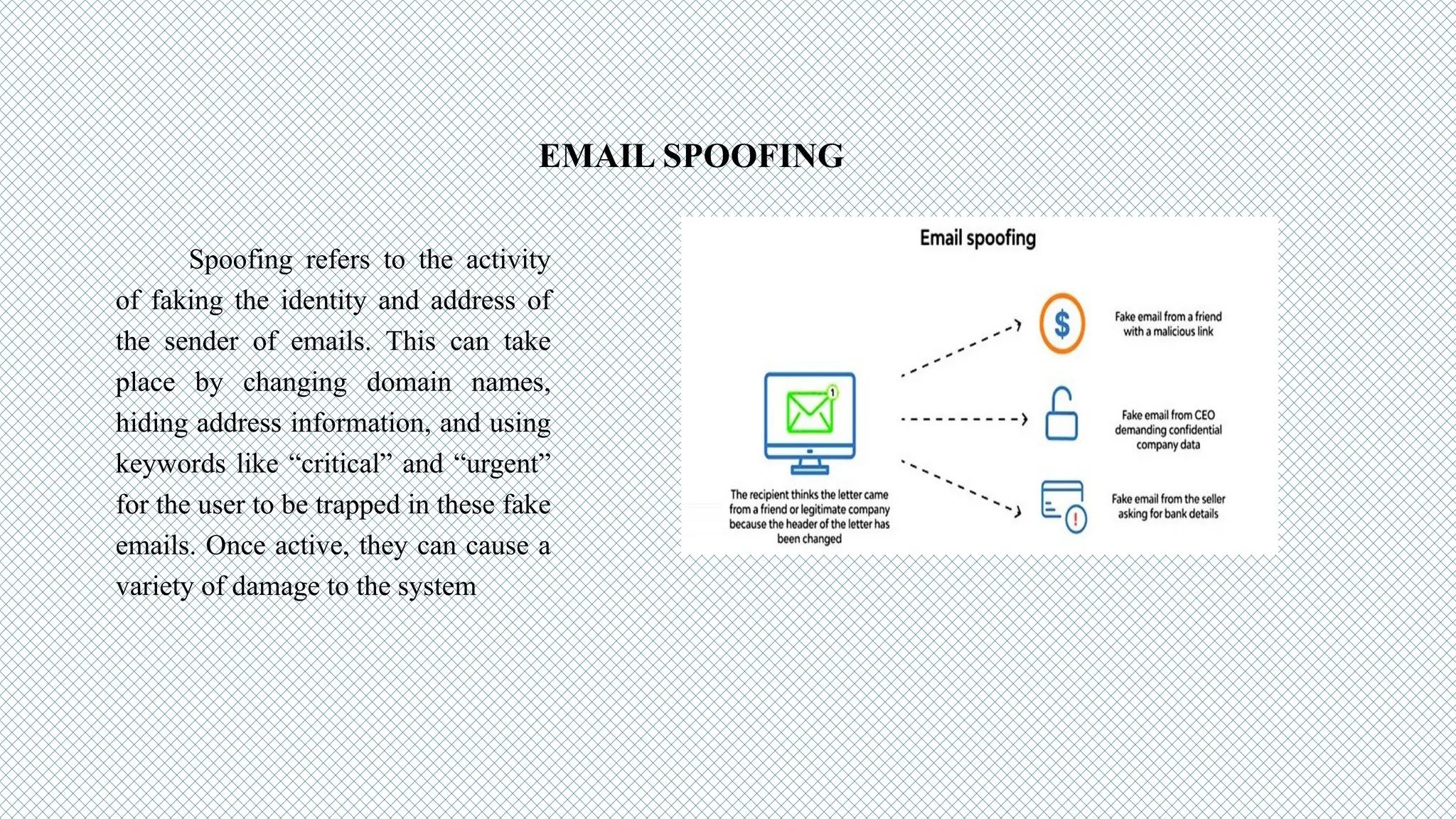
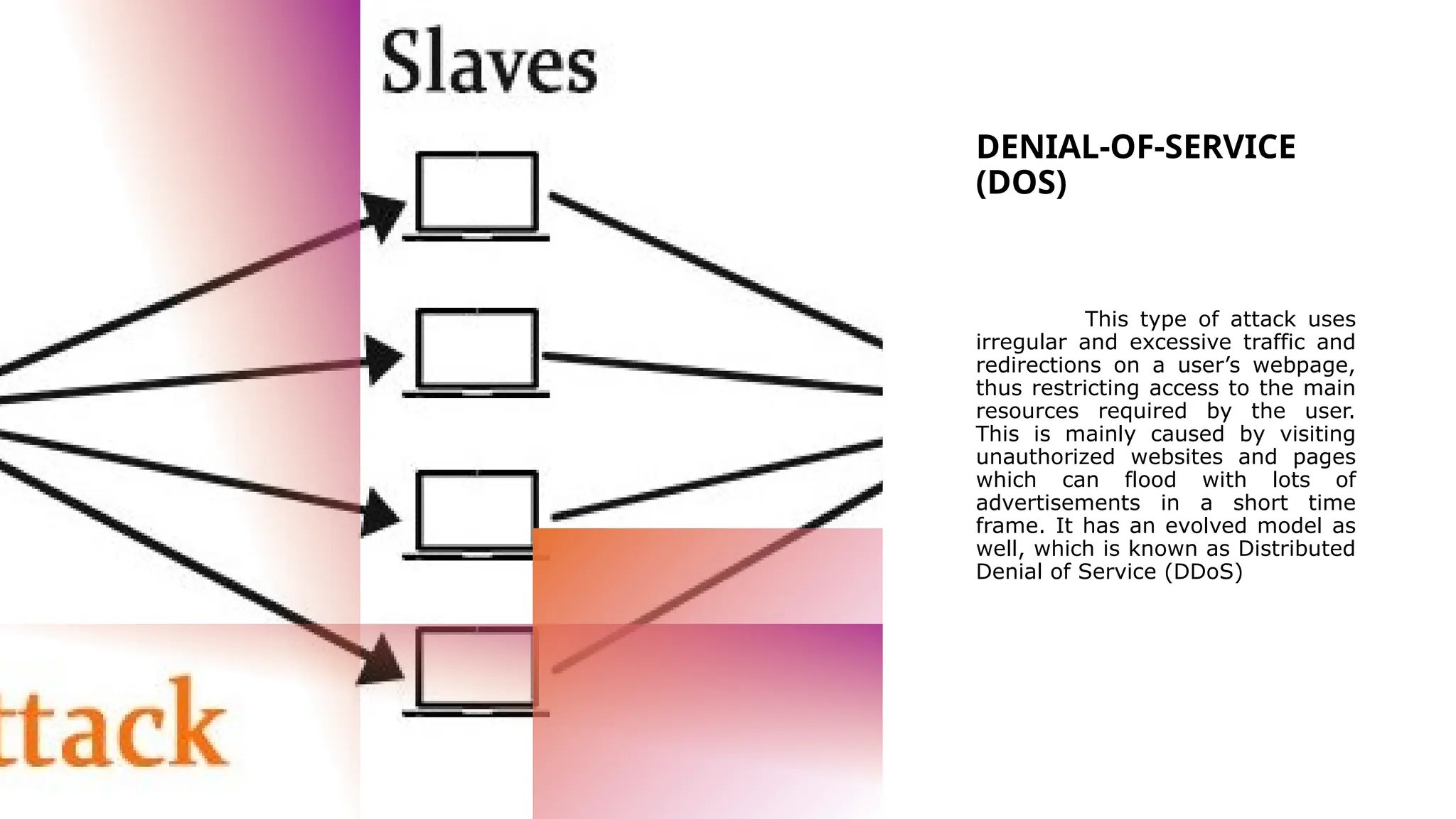
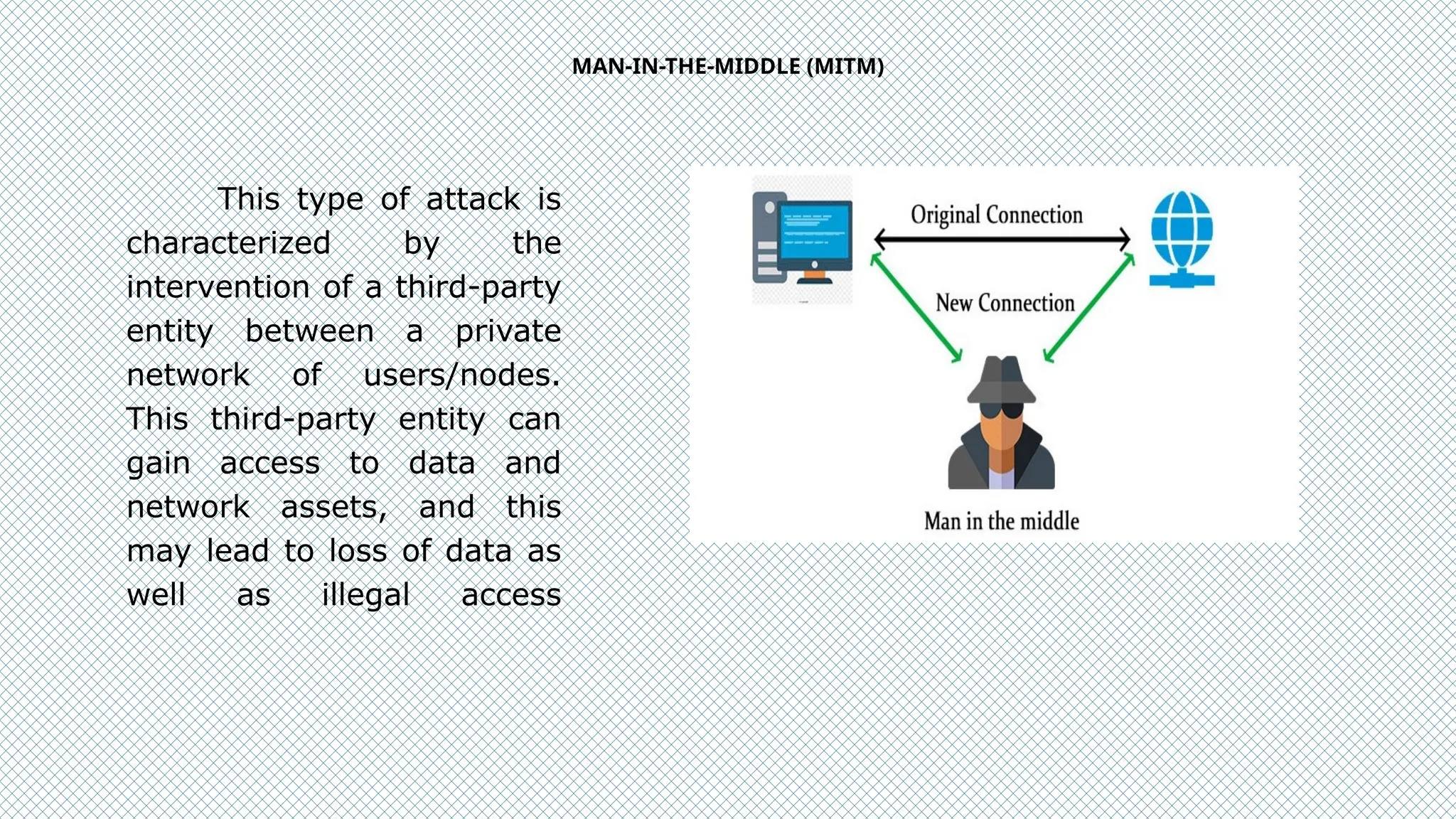
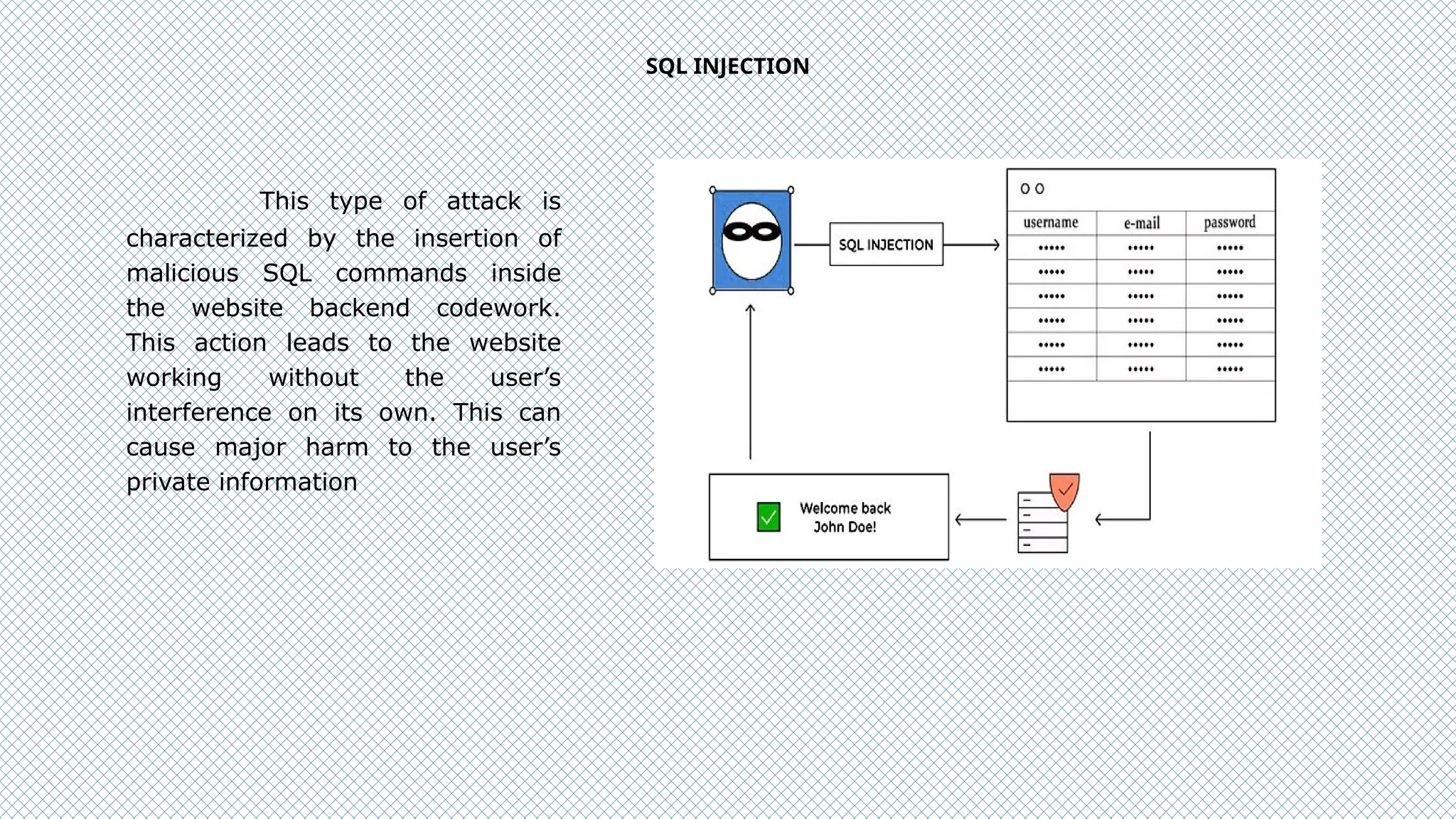
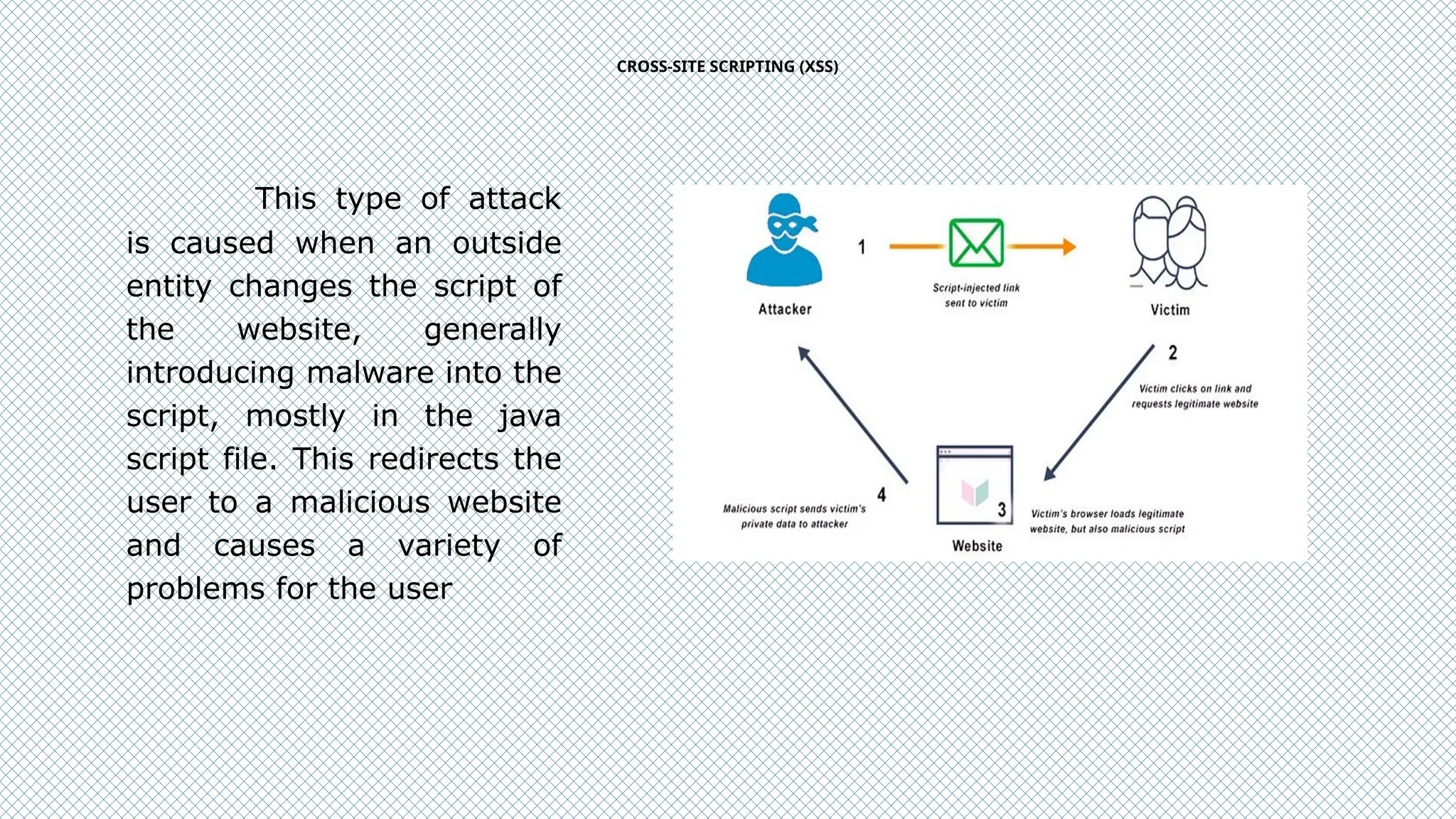
The document discusses cybersecurity as a critical defense against online threats such as phishing, data breaches, and ransomware attacks affecting both individuals and organizations. It outlines the role of cybersecurity engineers, ethical hacking practices, and various types of cyberattacks, including viruses, Trojan horses, and denial-of-service attacks. Additionally, it highlights the challenges faced in maintaining effective cybersecurity solutions due to evolving threats and the complexity of security systems.