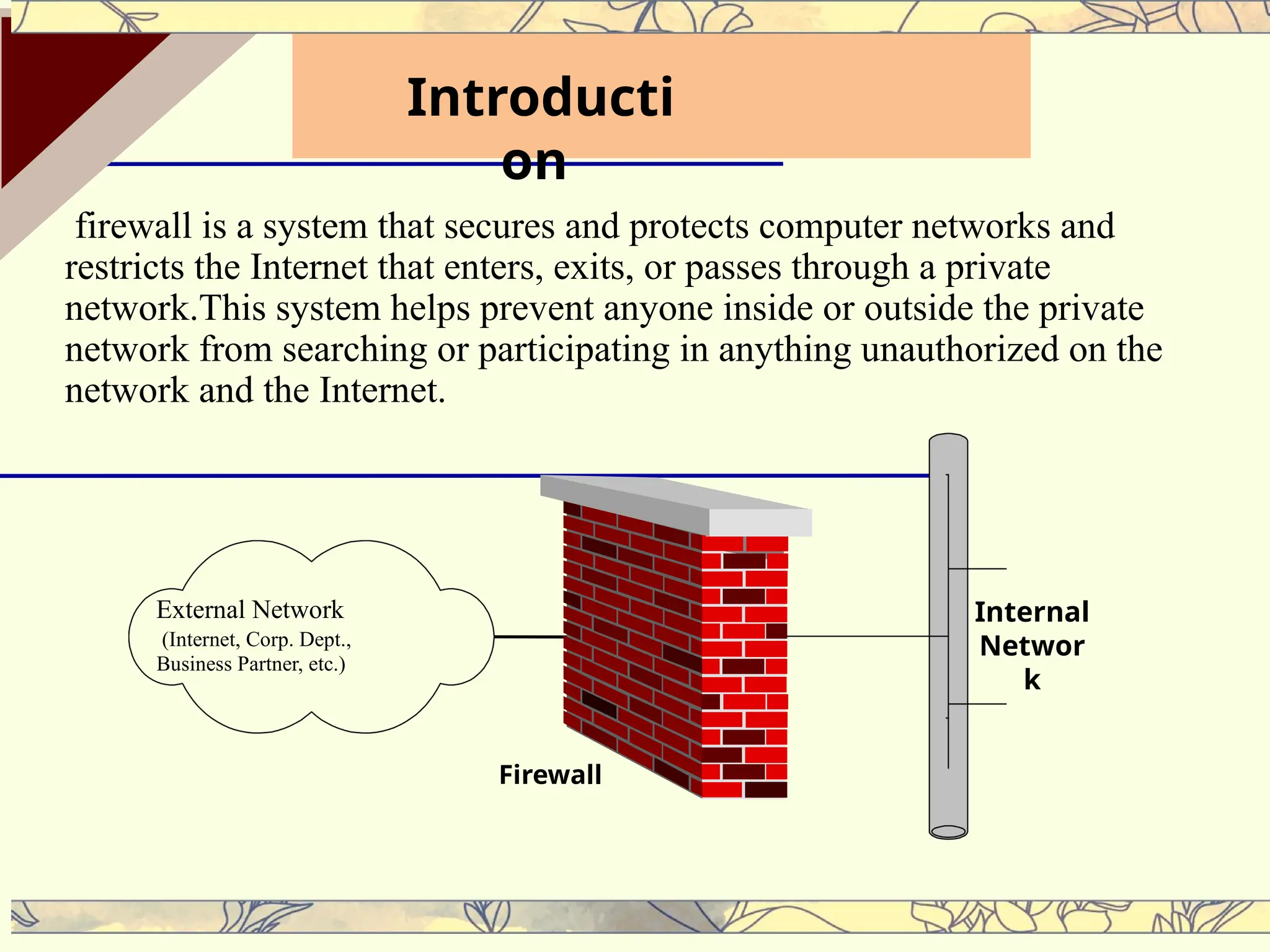
Firewalls are essential systems that secure networks by controlling the flow of internet traffic to prevent unauthorized access and cyber threats. They come in various types, including packet-filtering, stateful inspection, proxy firewalls, and next-generation firewalls, each offering unique functionalities and protection levels. In the context of escalating cyber threats, firewalls have evolved to incorporate advanced technologies, ensuring robust security for both on-premises and cloud environments.