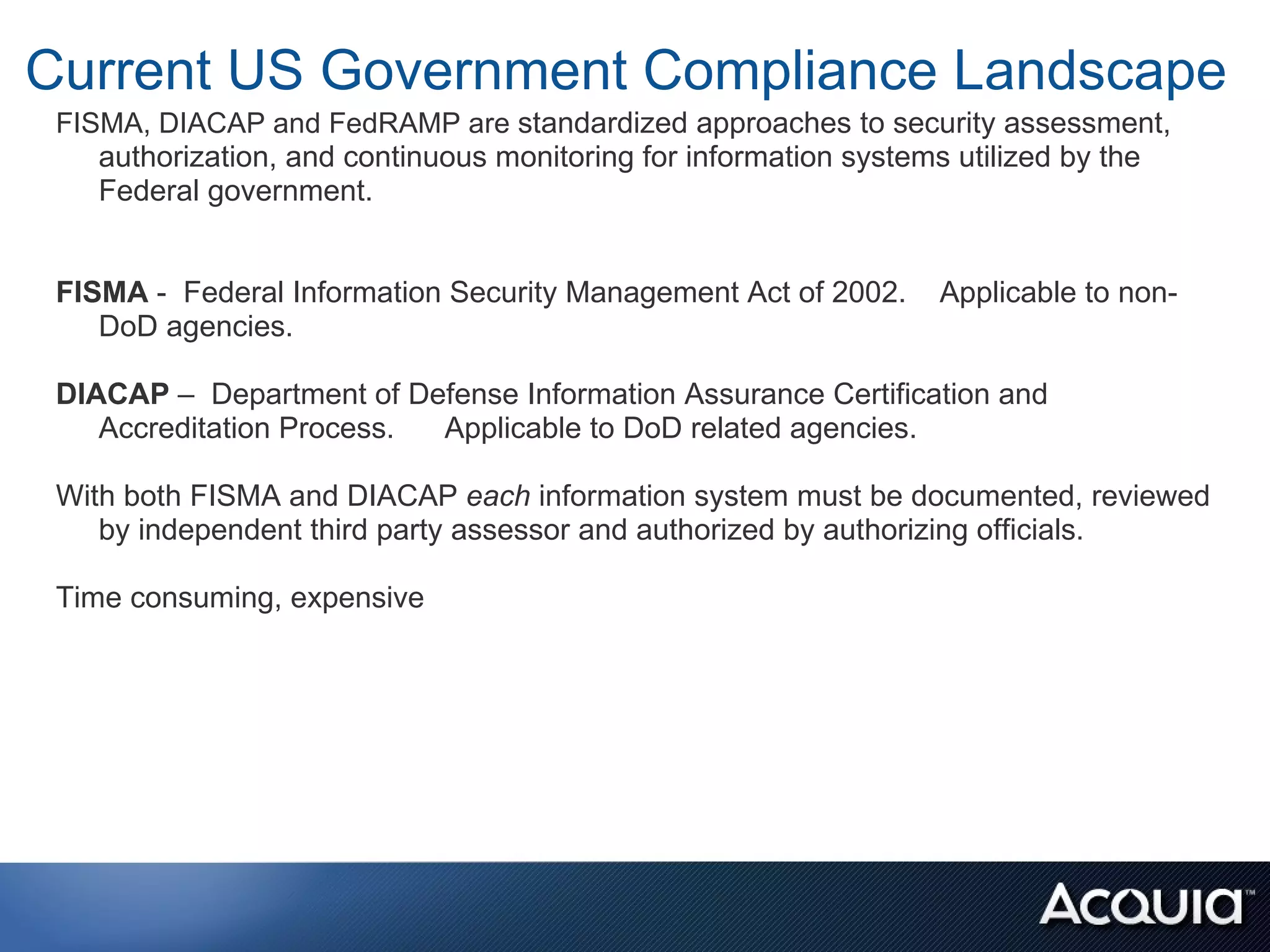
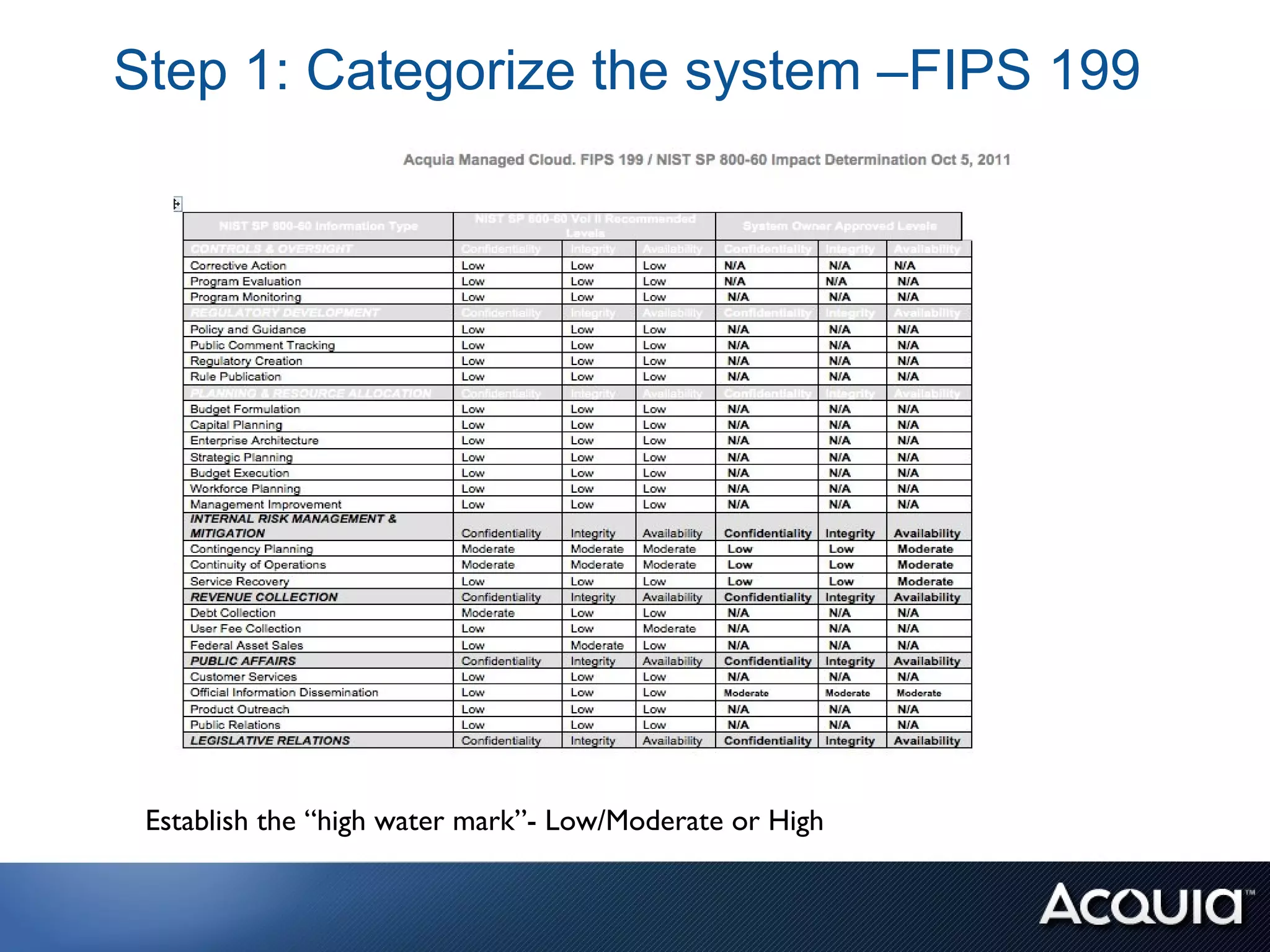
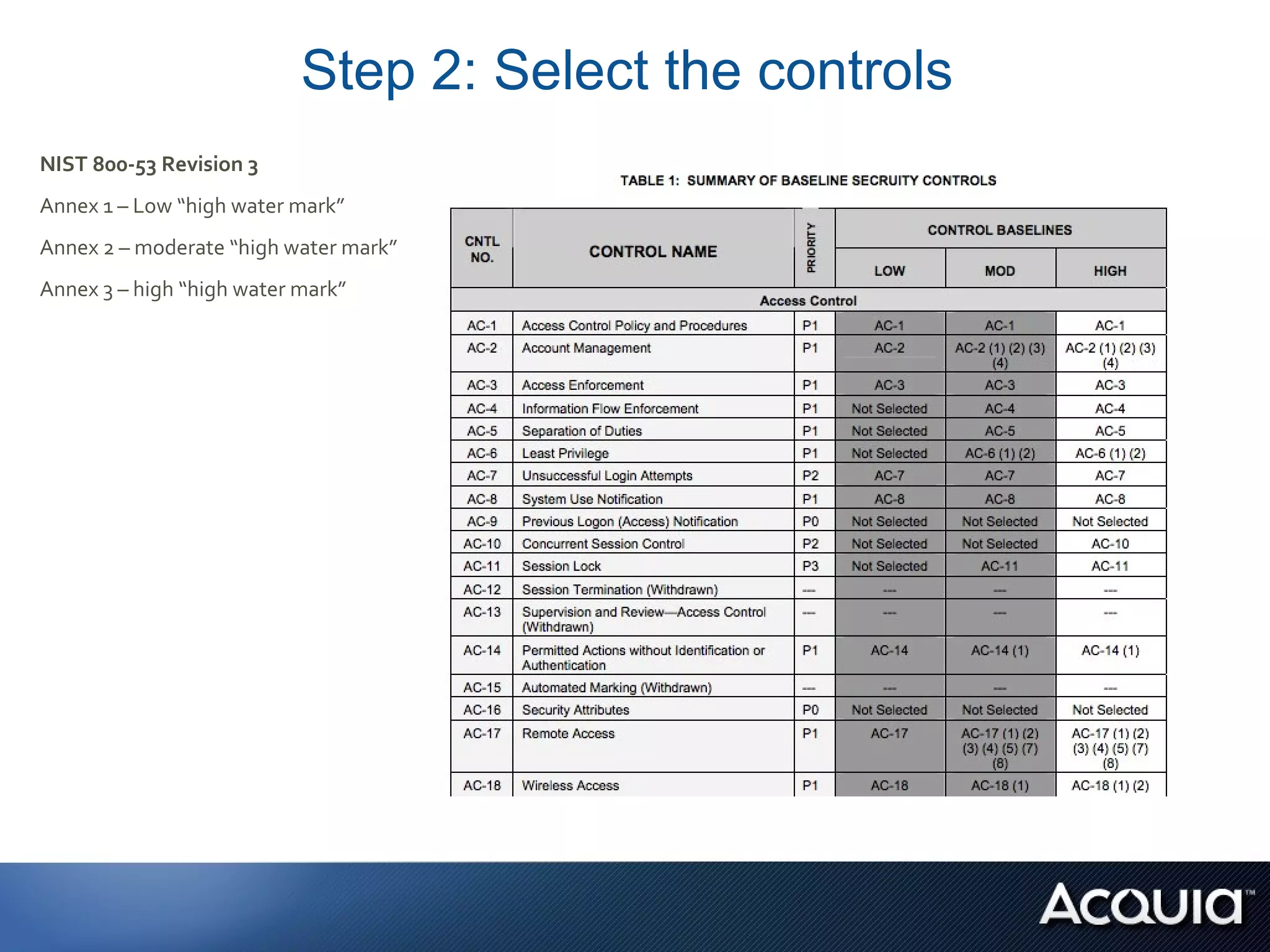
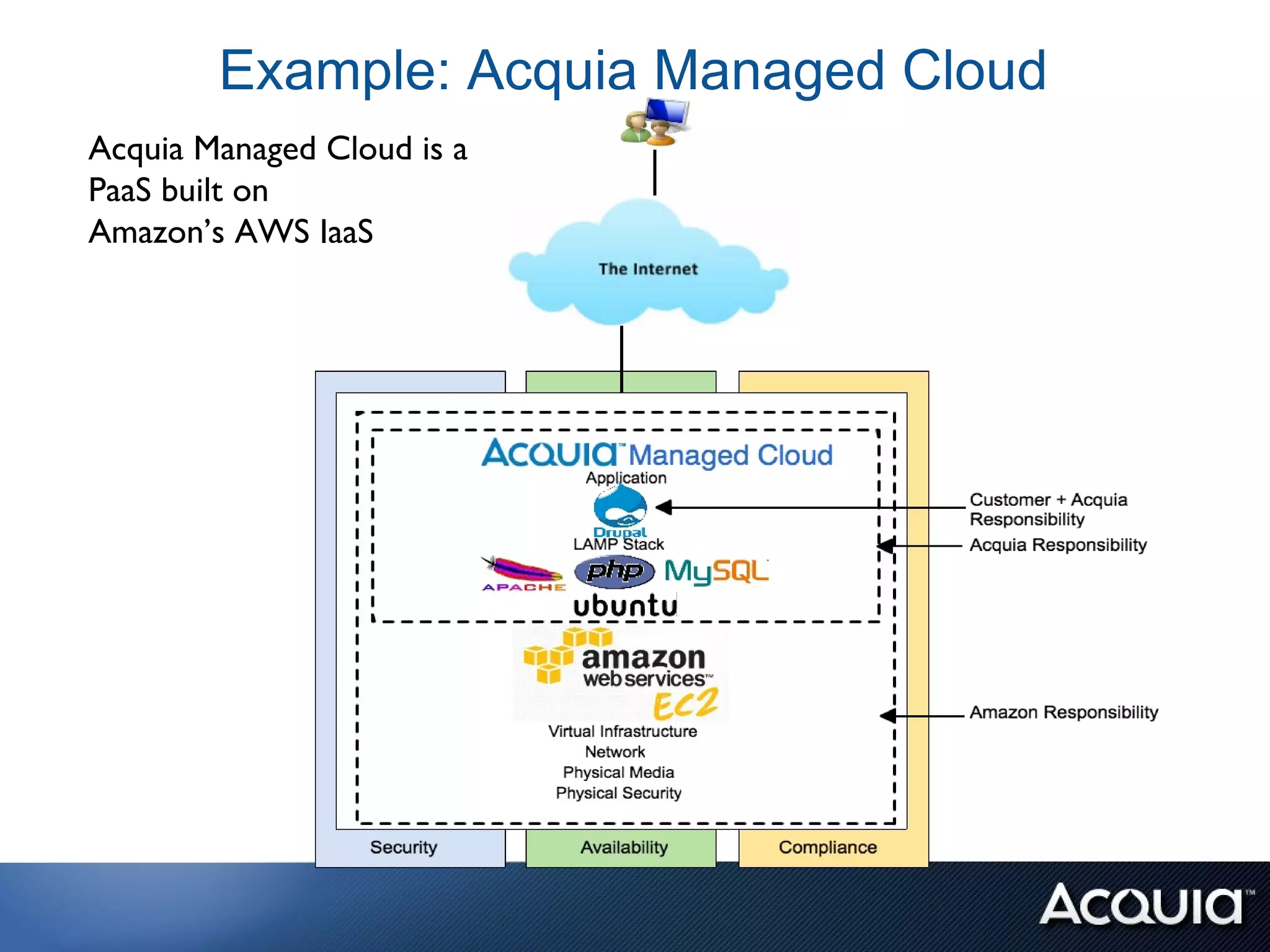
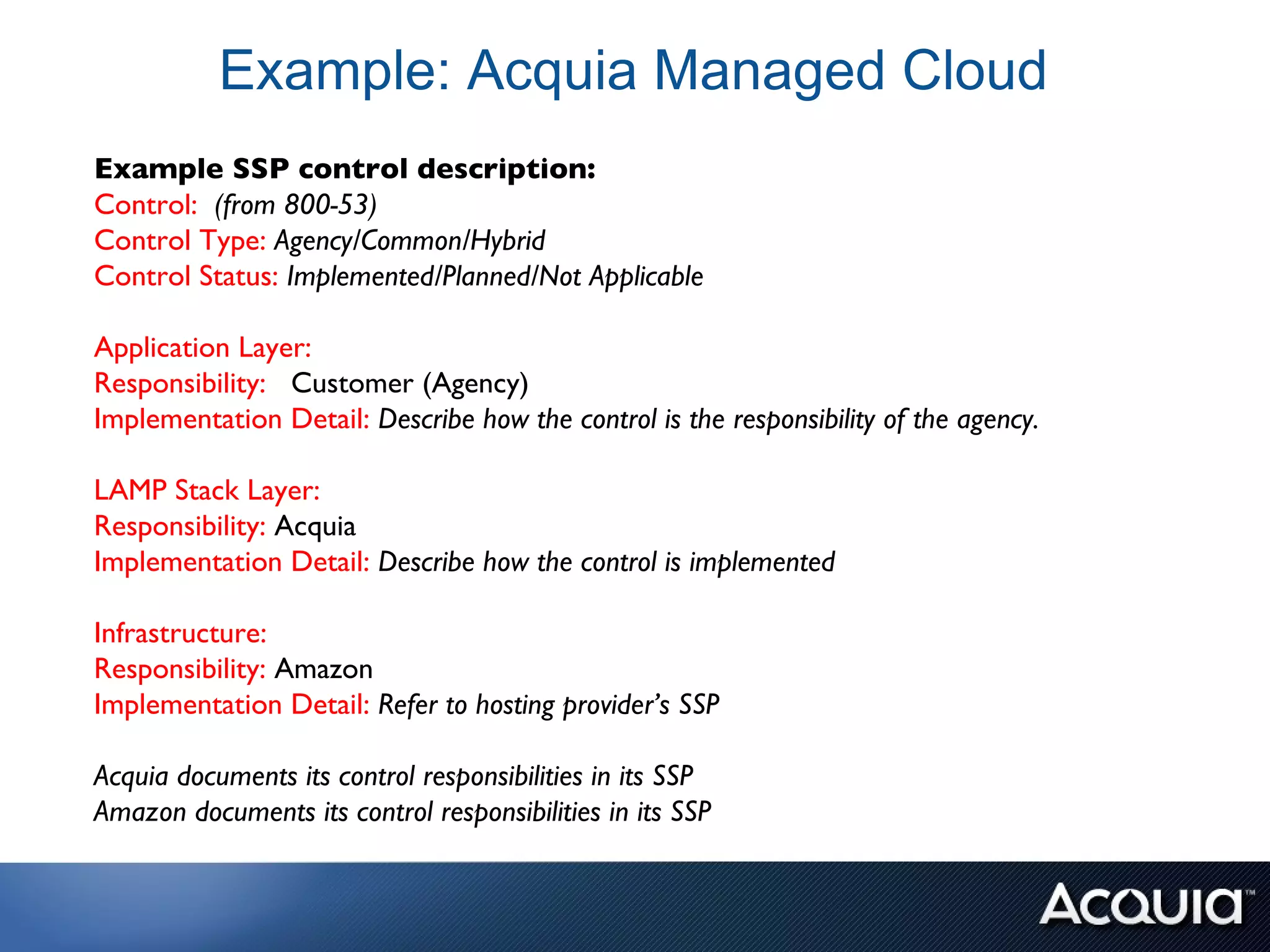
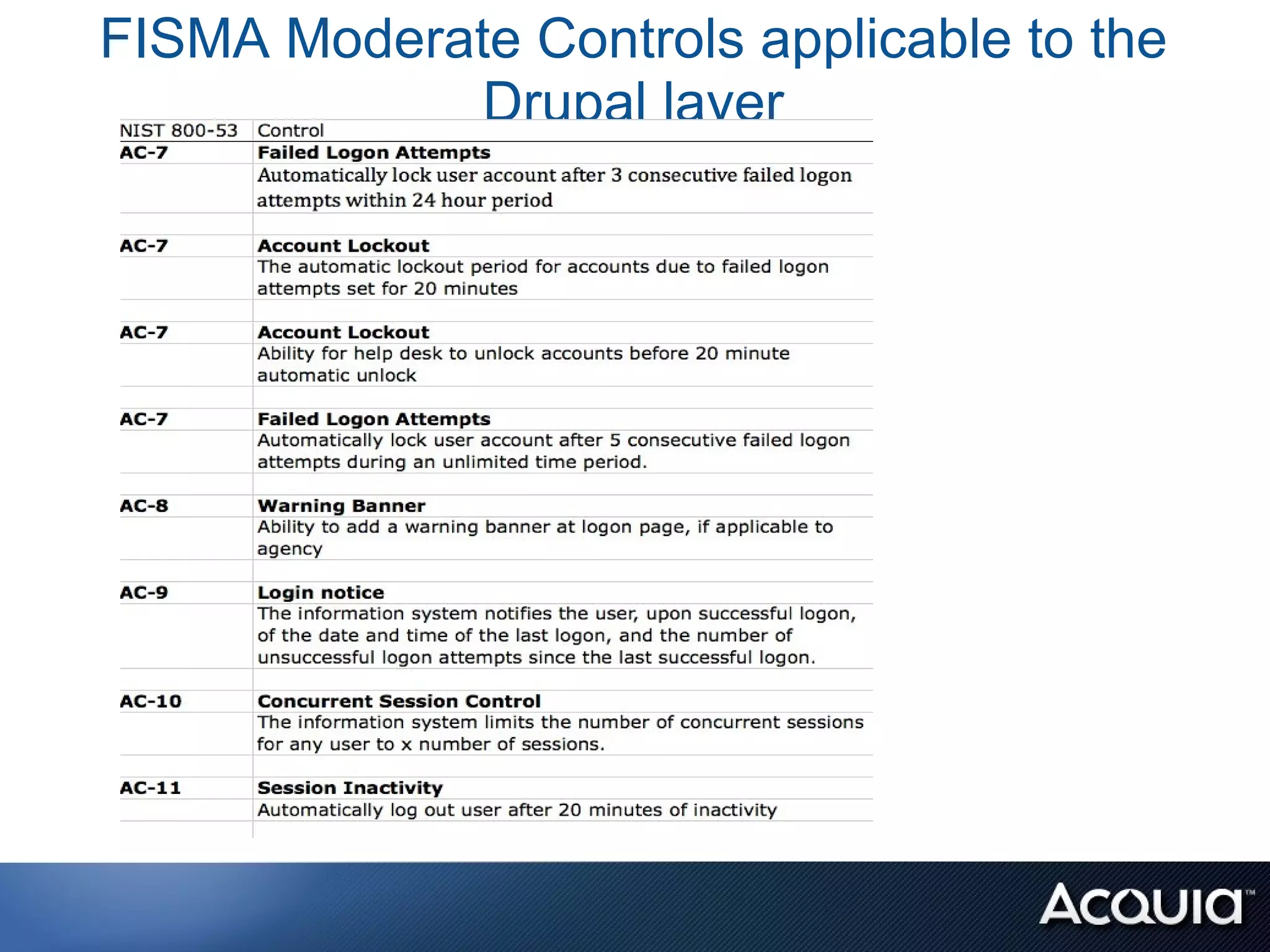
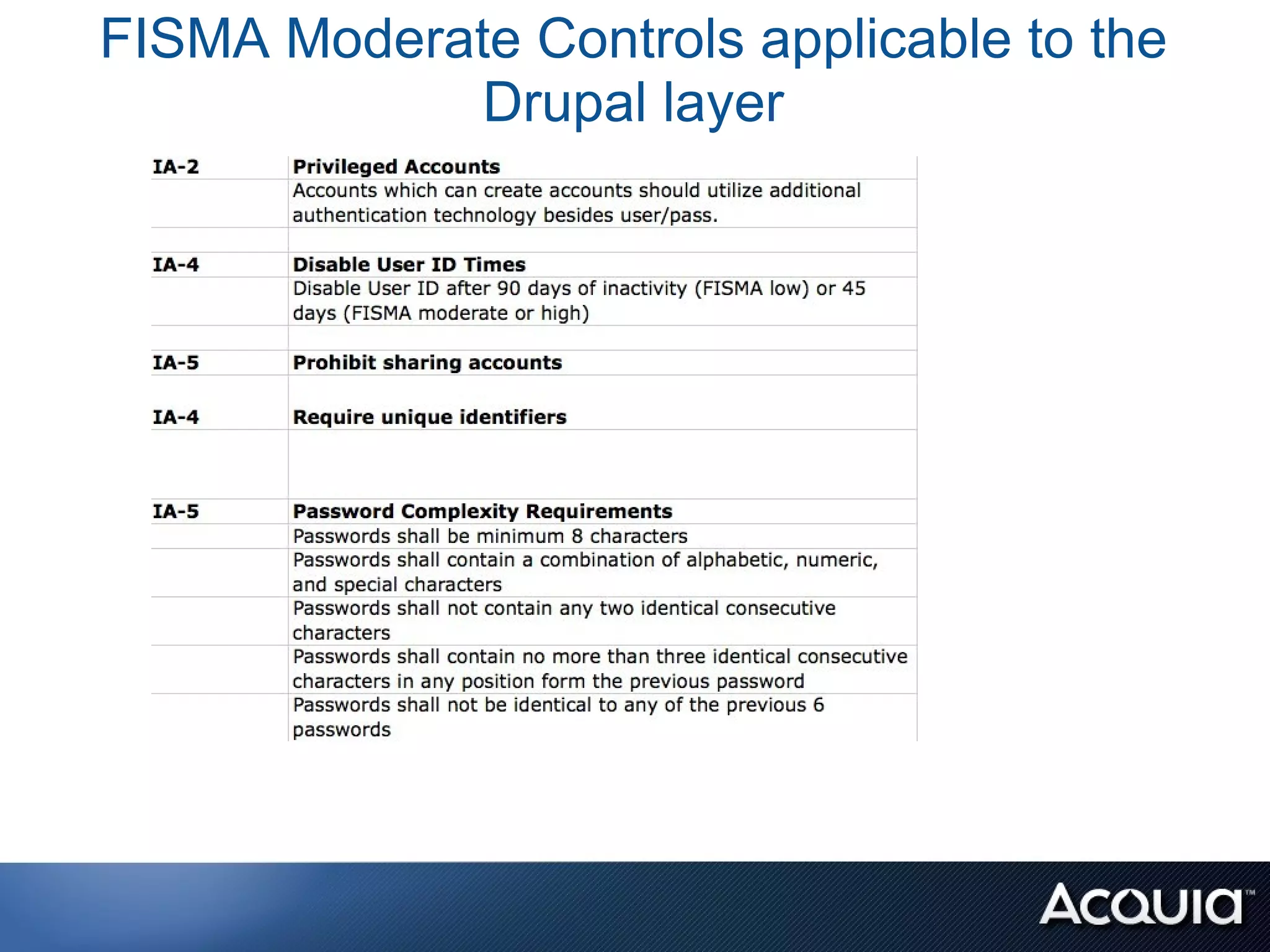
The document discusses federal compliance standards for information systems used by the US government, including FISMA, DIACAP, and the upcoming FedRAMP. It outlines the six step process for achieving compliance: 1) categorizing the system, 2) selecting controls, 3) implementing and documenting controls, 4) assessing controls, 5) authorizing the system, and 6) ongoing monitoring. It provides an example of how a cloud service provider like Acquia can achieve compliance for their platform by documenting the controls each party is responsible for across the application, OS stack, and infrastructure layers. Finally, it lists some specific FISMA moderate controls applicable to the Drupal content management system.