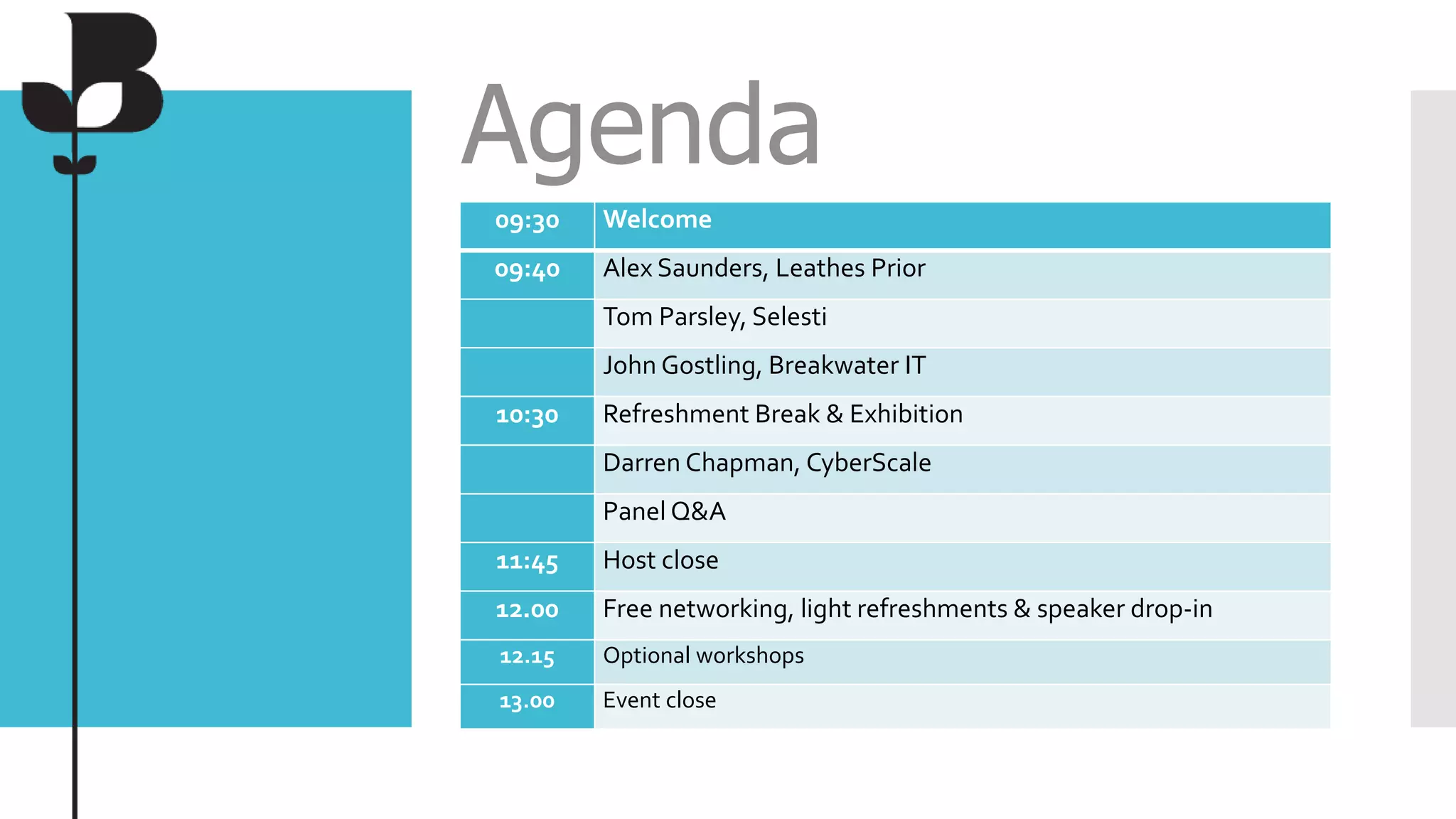
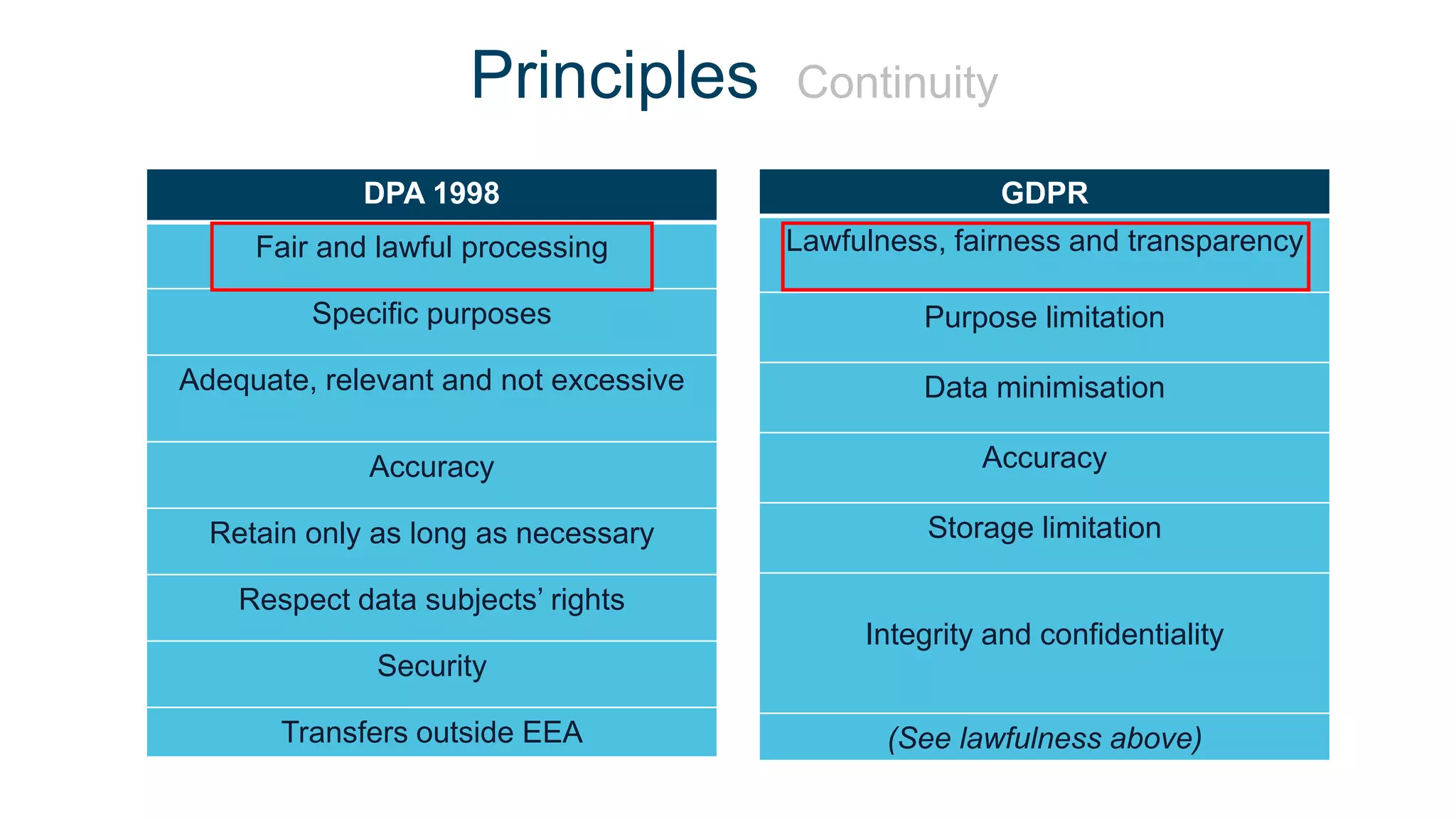
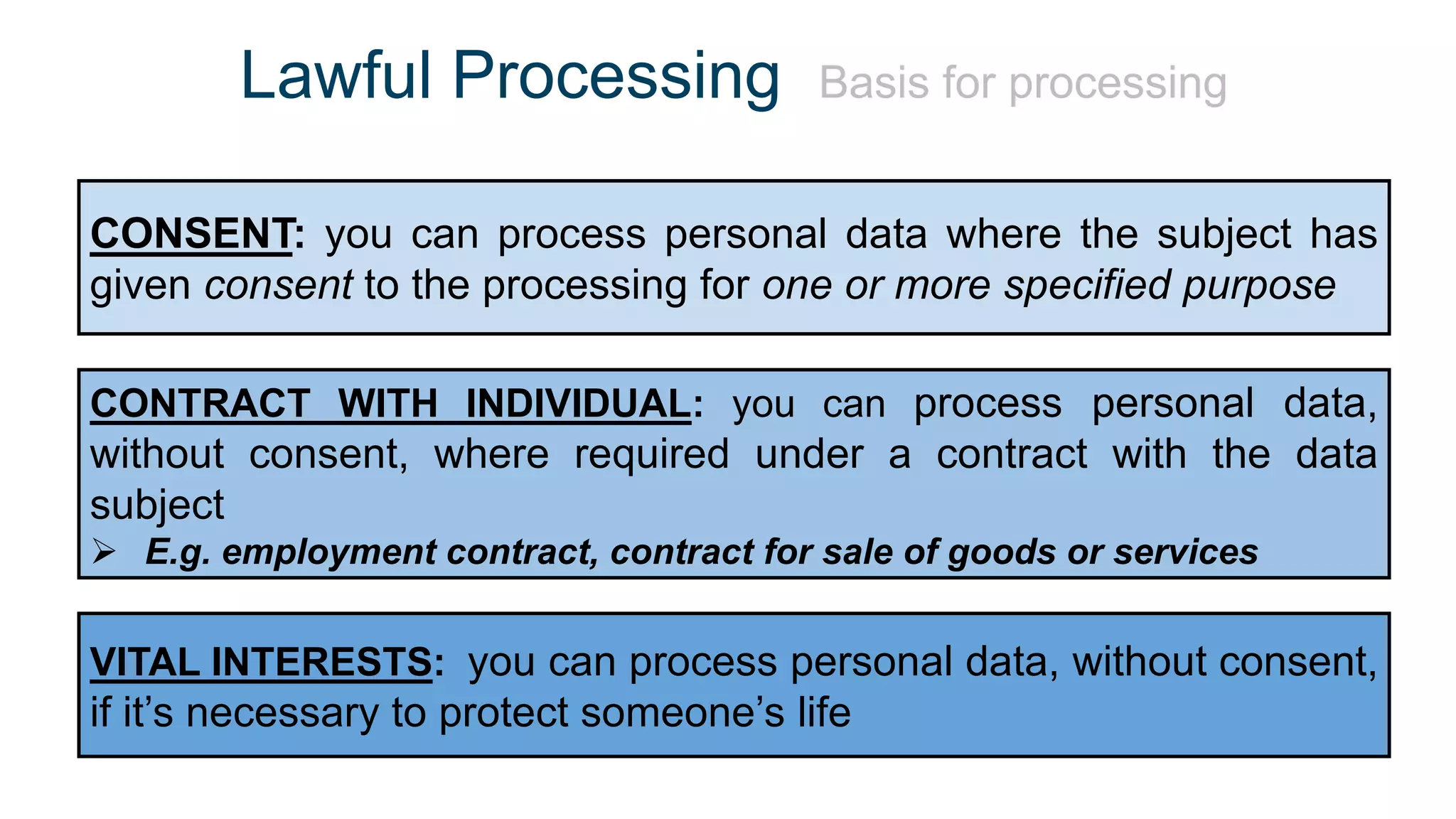
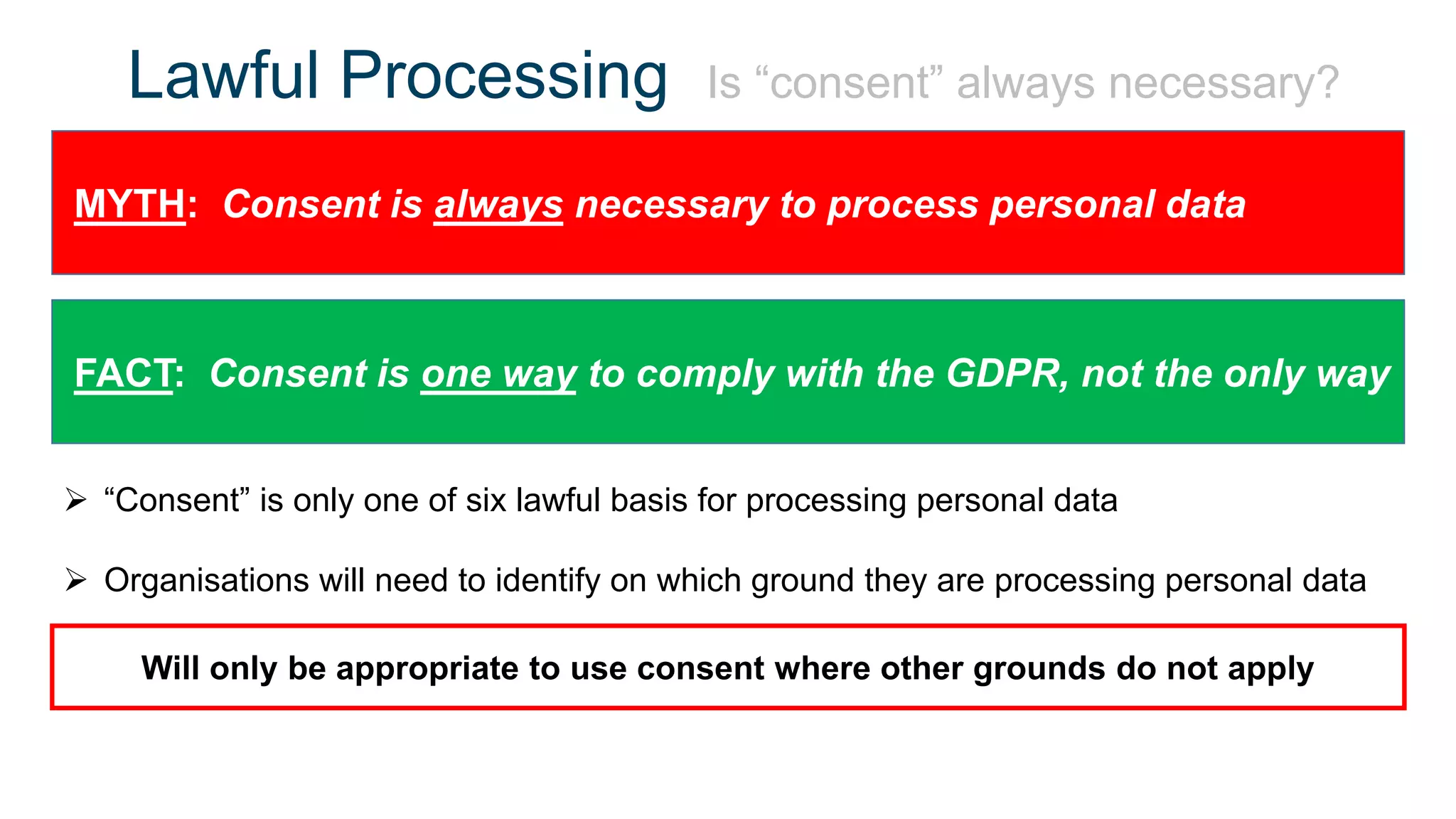
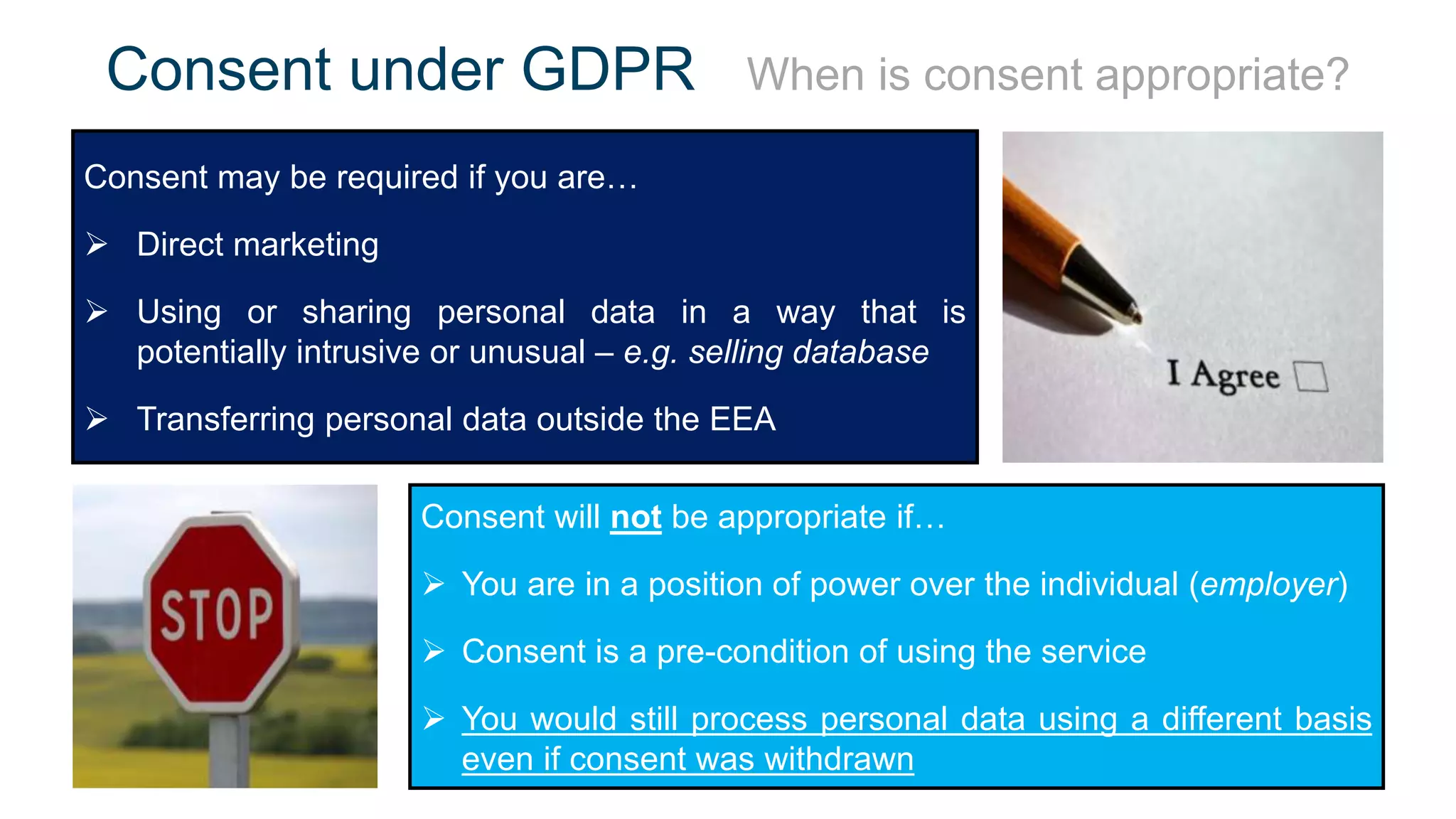
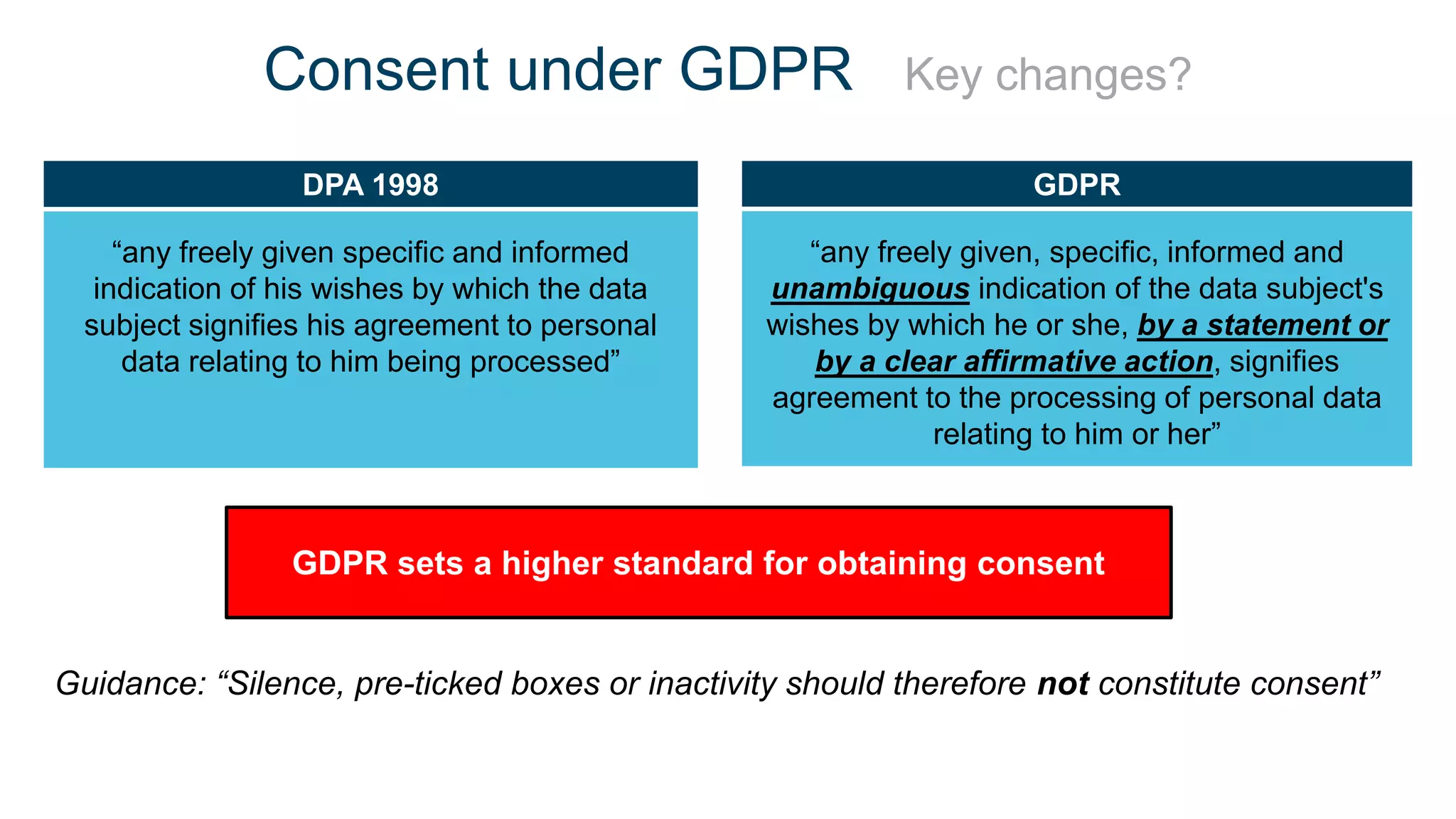
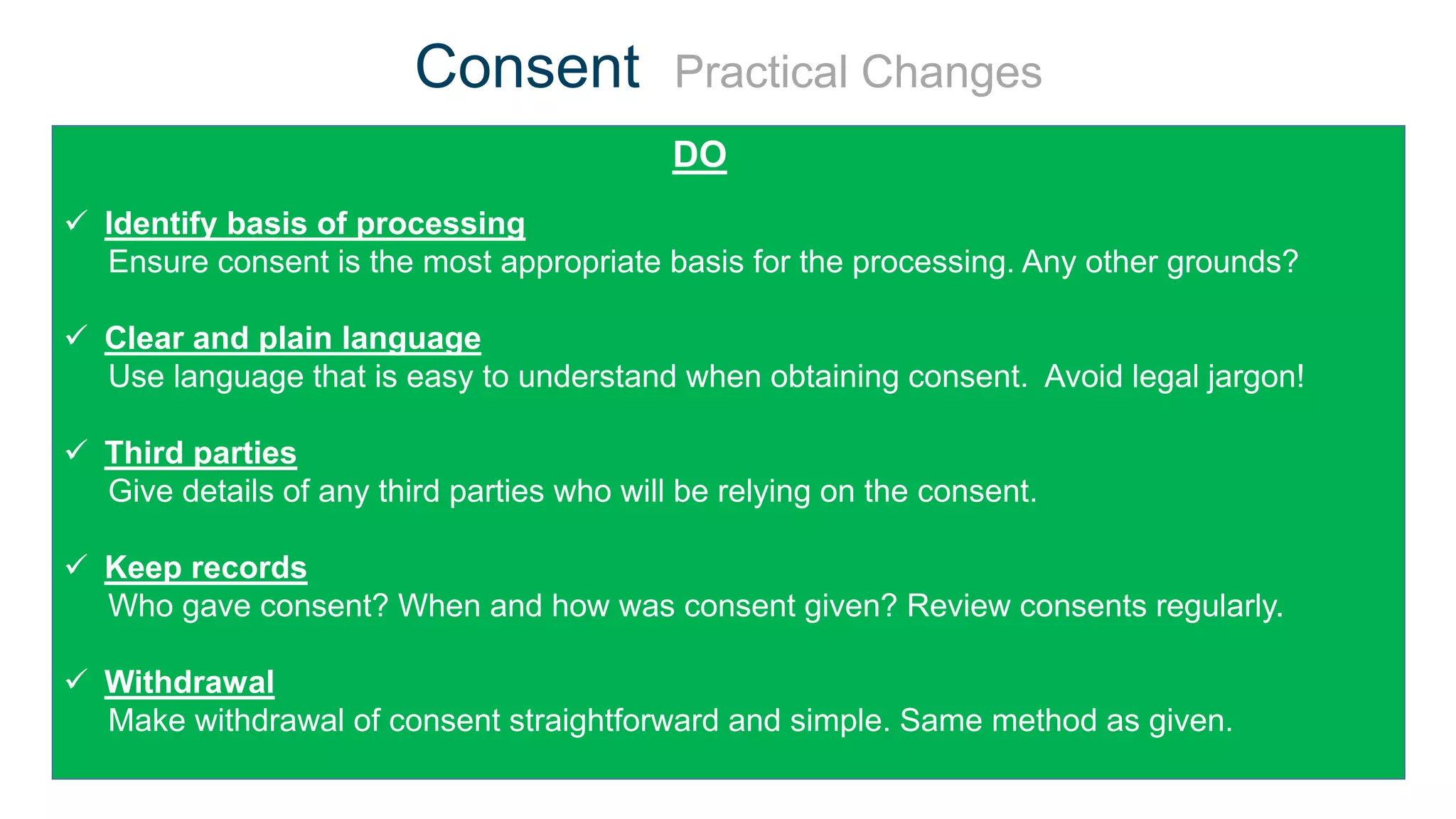
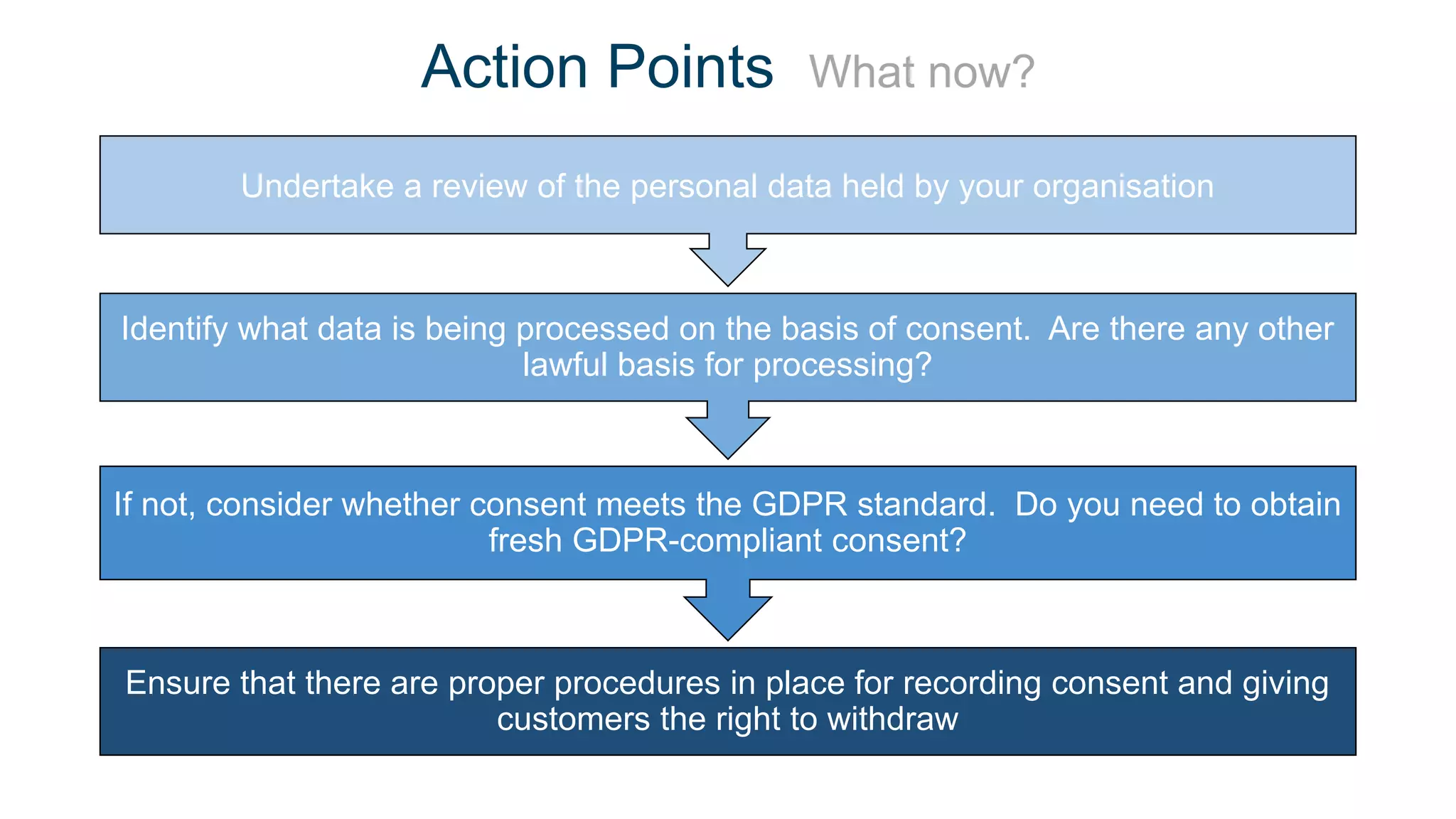
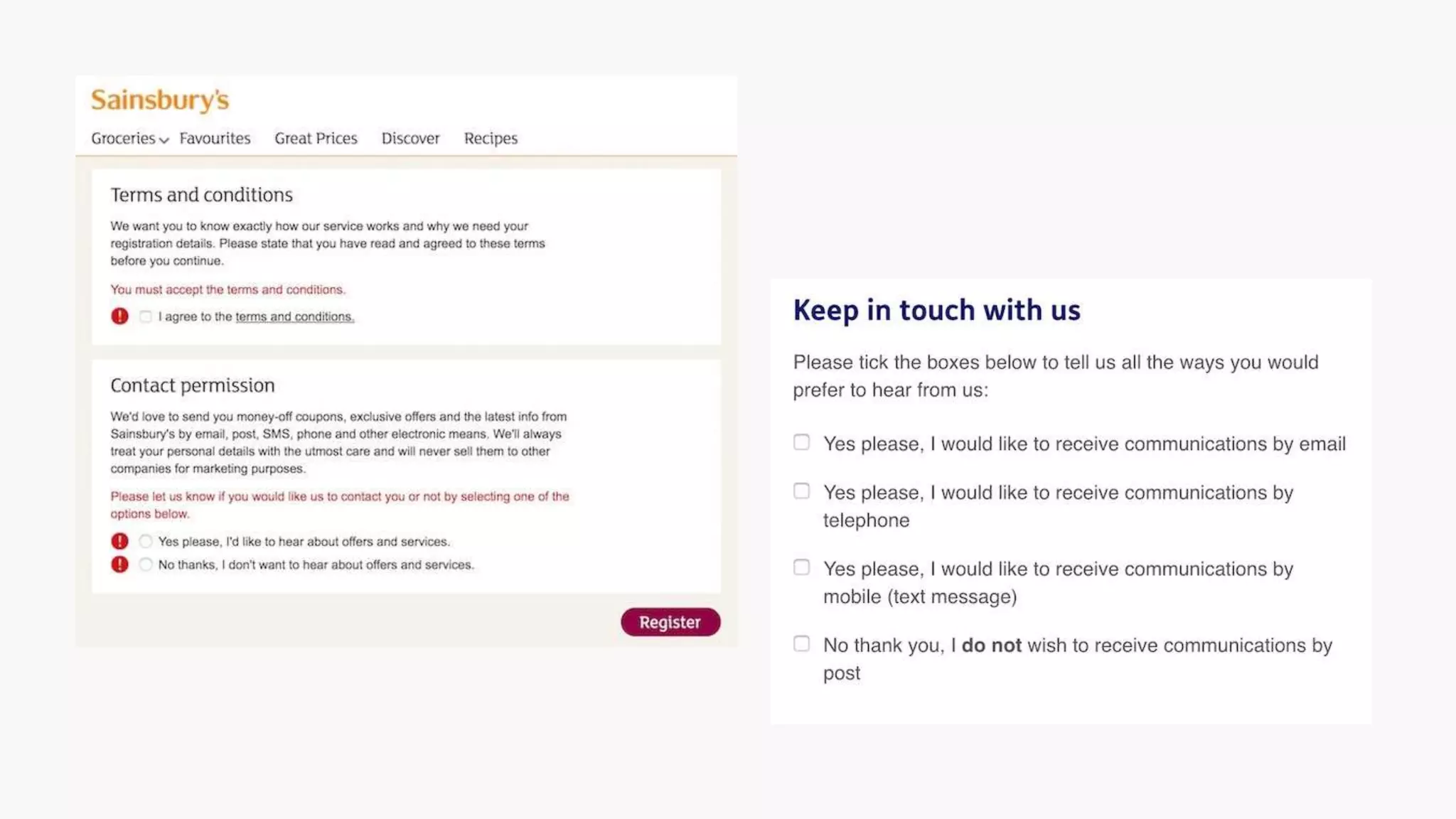
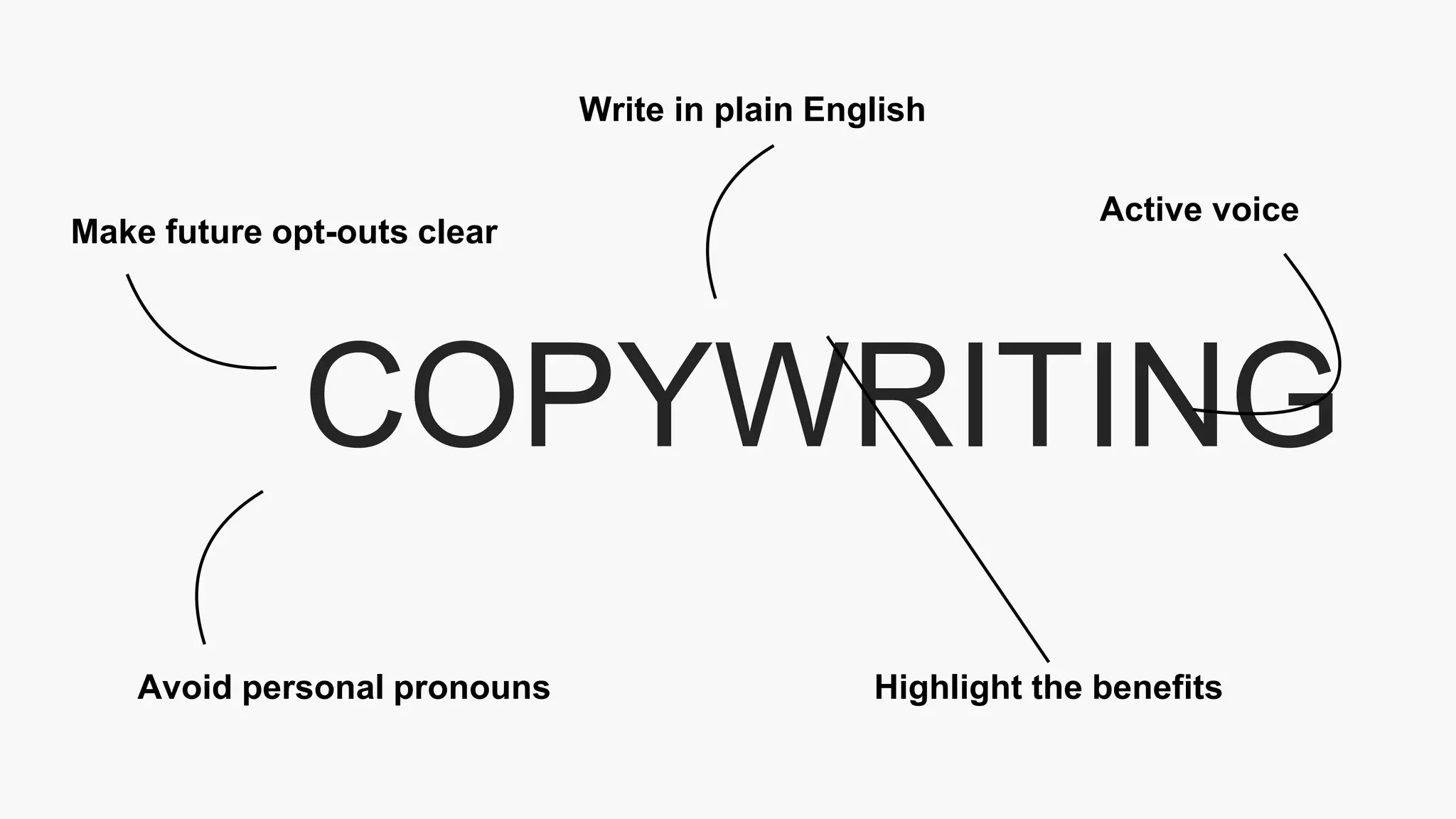
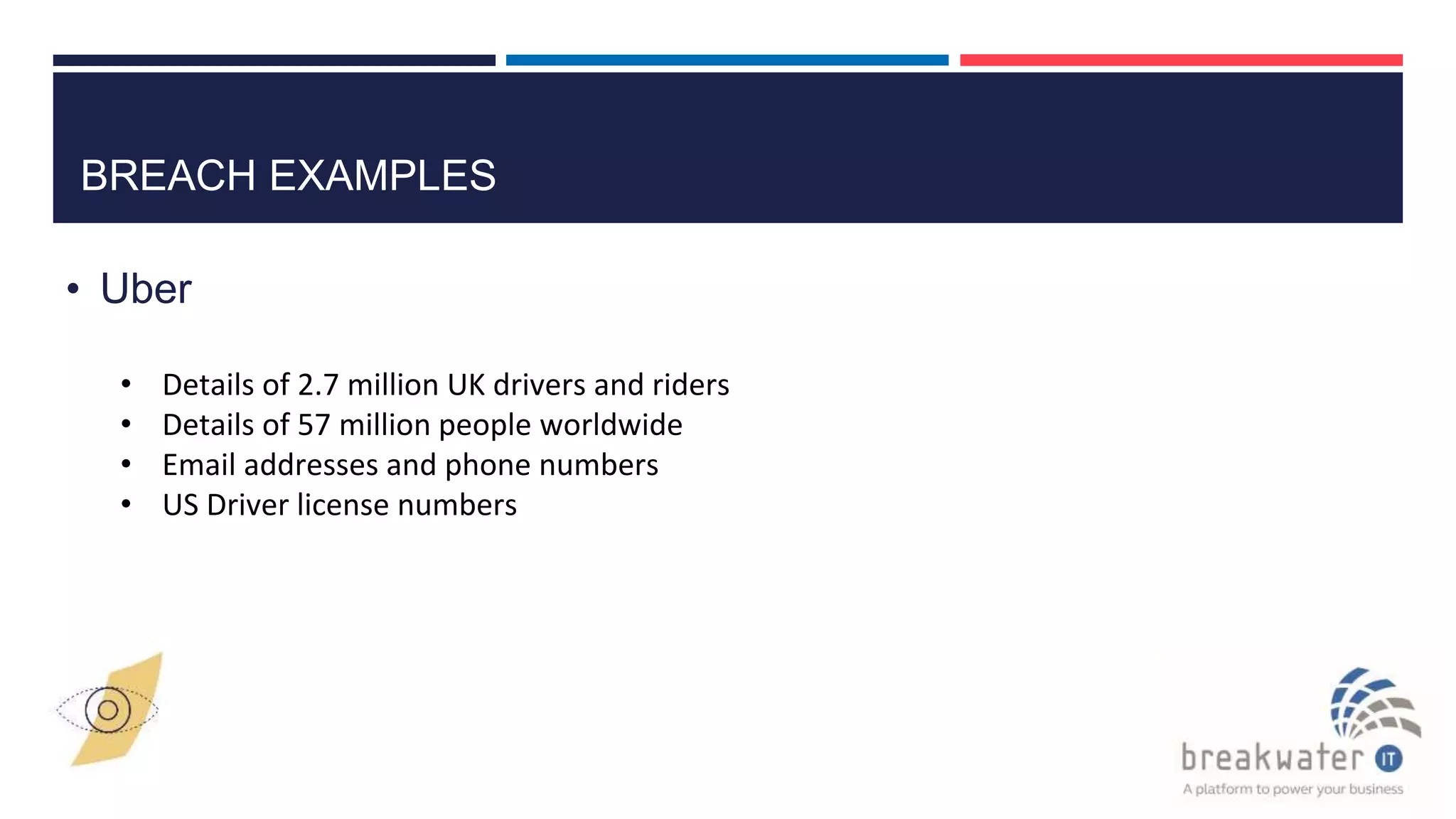
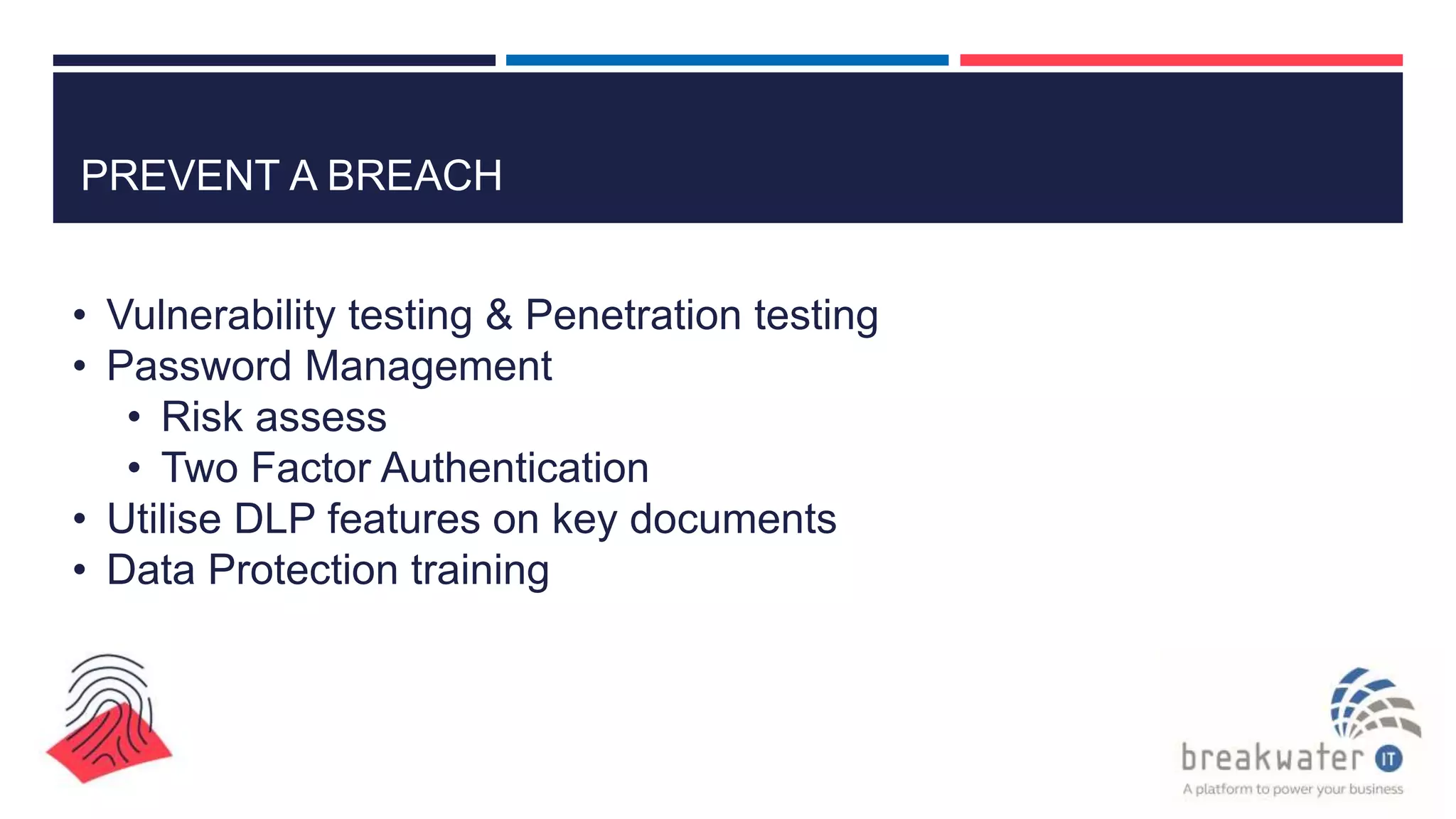
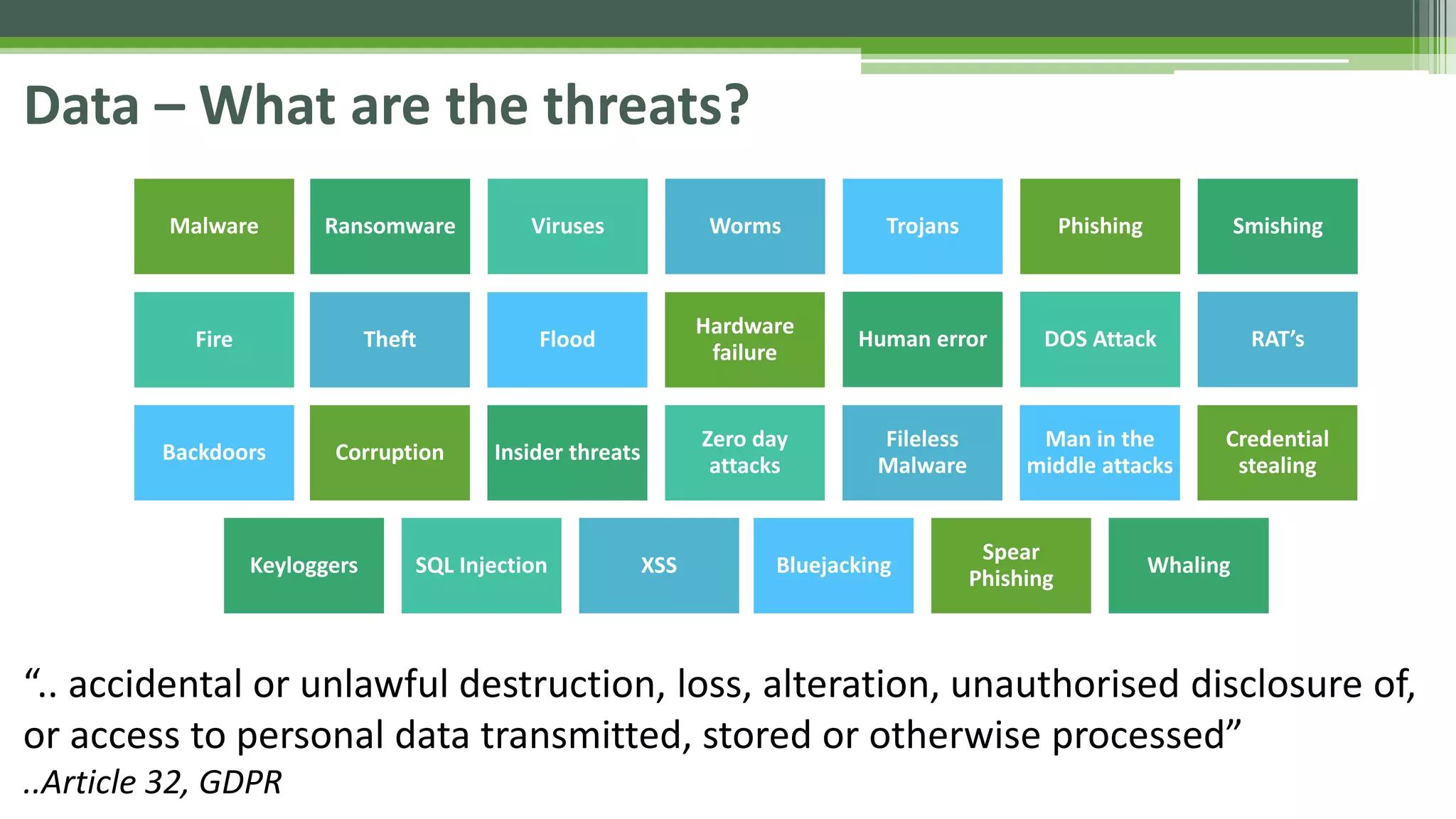
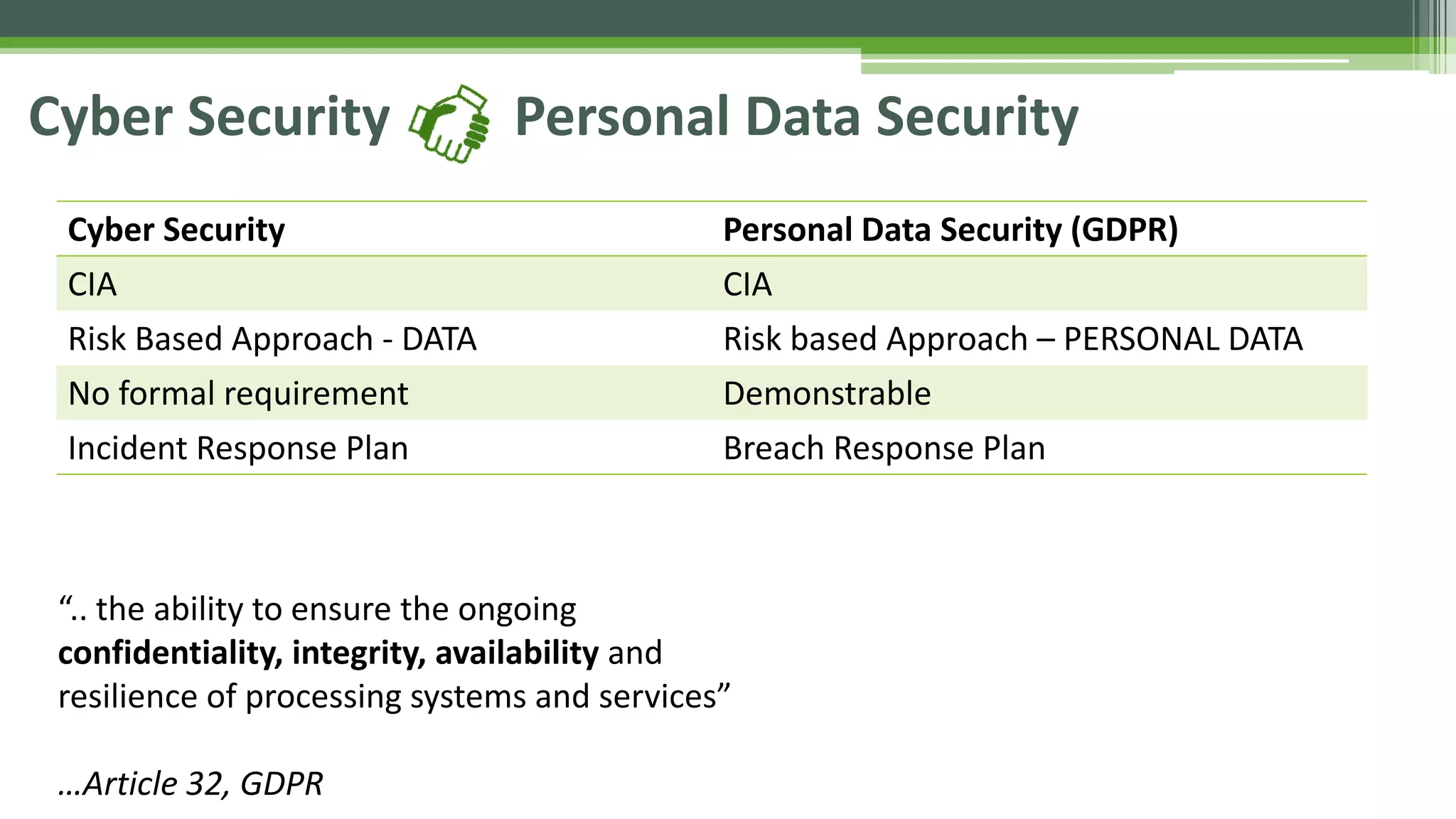
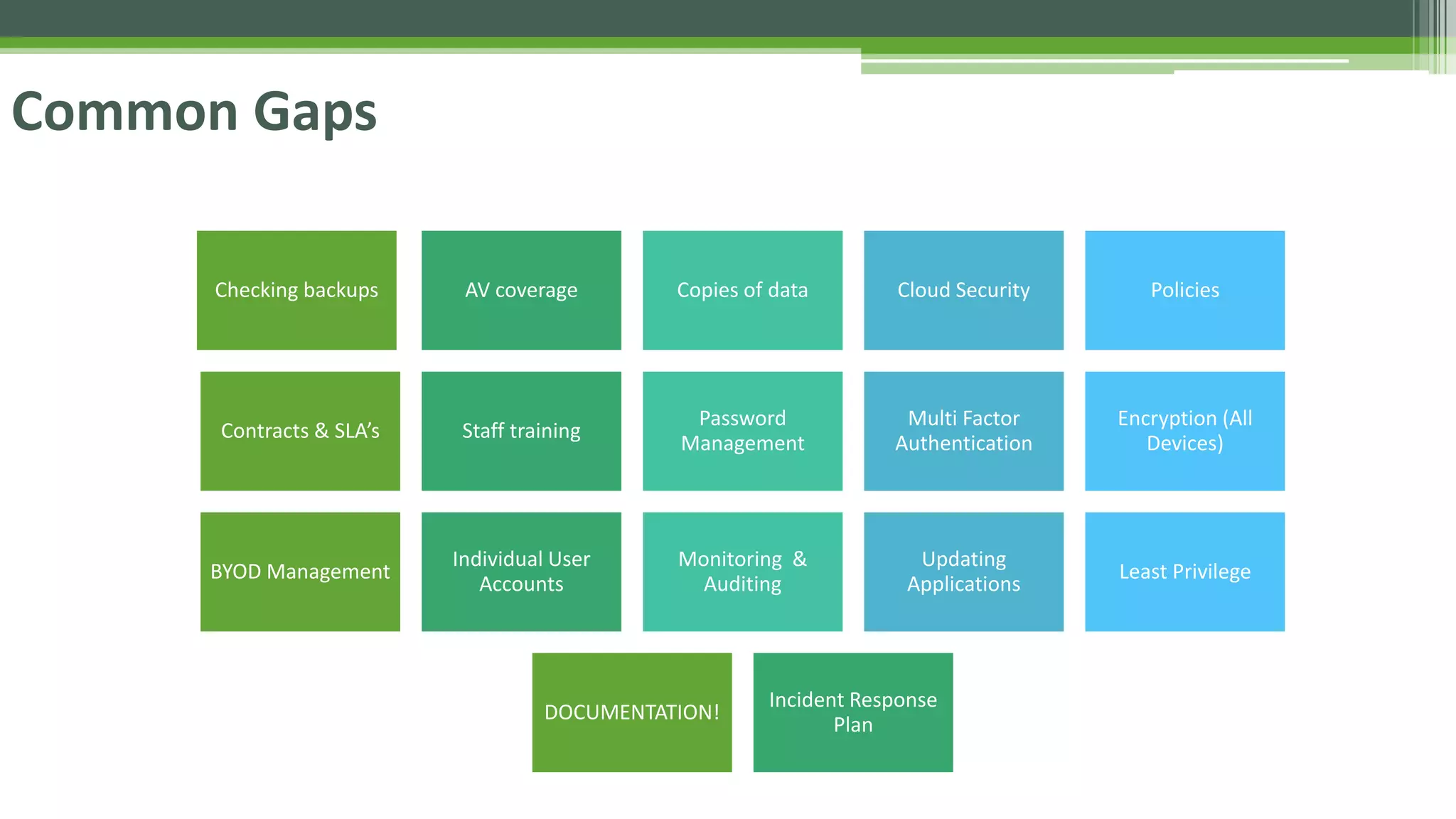
The document outlines the details of the GDPR conference held on March 13, 2018, including the agenda, speakers, and topics discussed, such as the importance of GDPR, consent management, personal data breaches, and cyber security. It emphasizes the necessity for organizations to comply with GDPR regulations and implement appropriate measures for data protection. Key takeaways include the clarification that consent is not always required for processing personal data and the need for organizations to have proper procedures in place to record and manage consent.