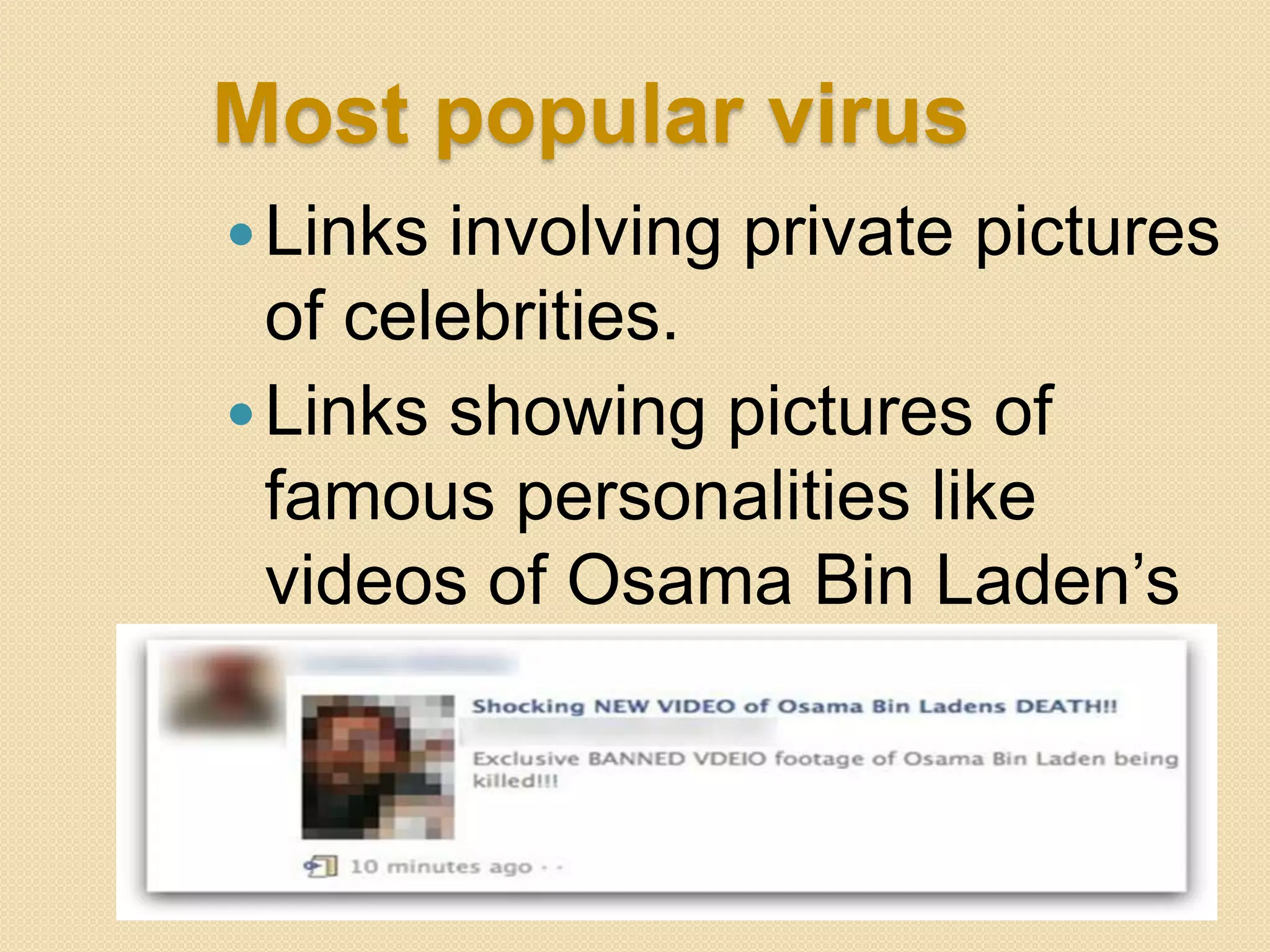
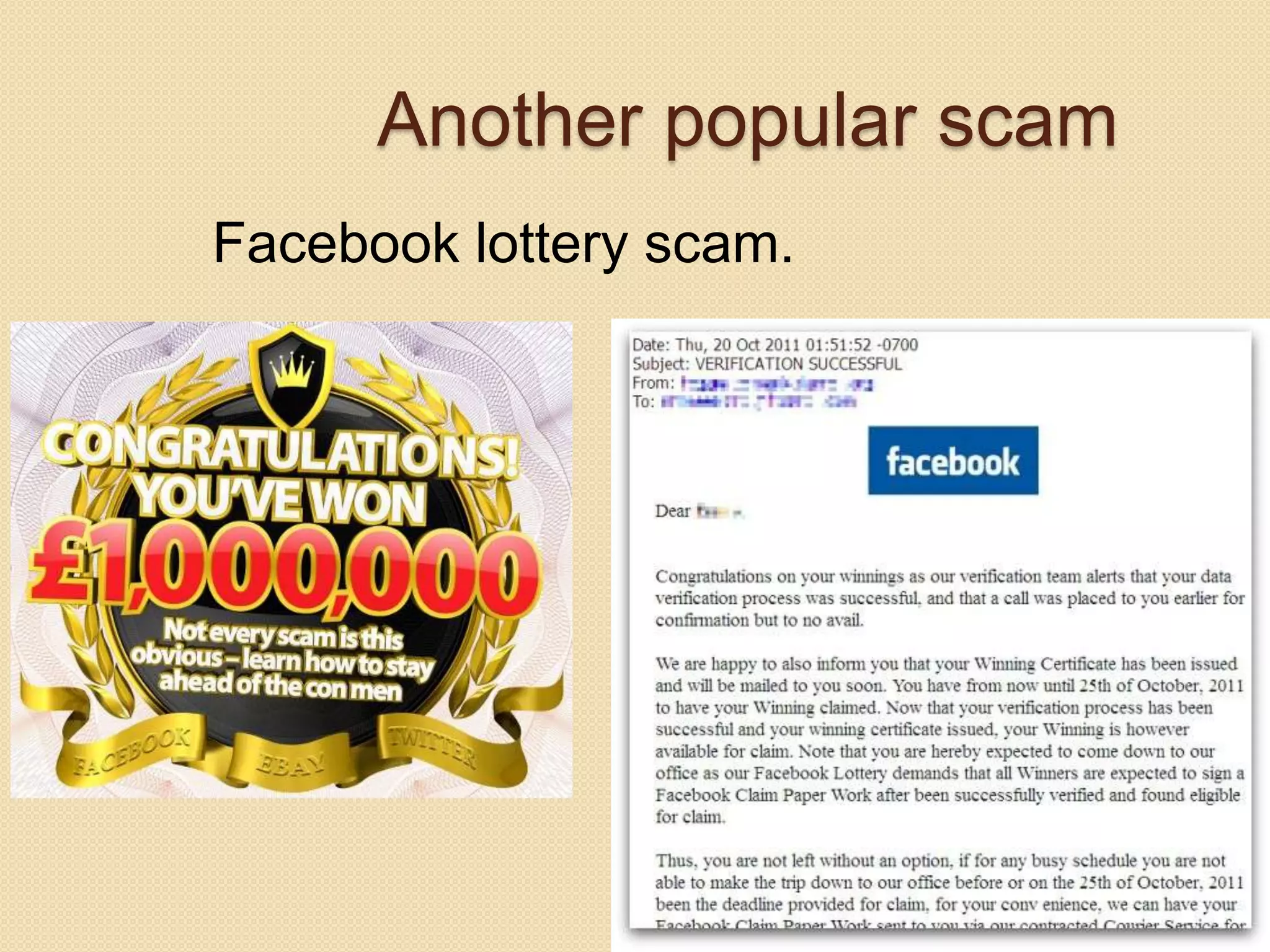
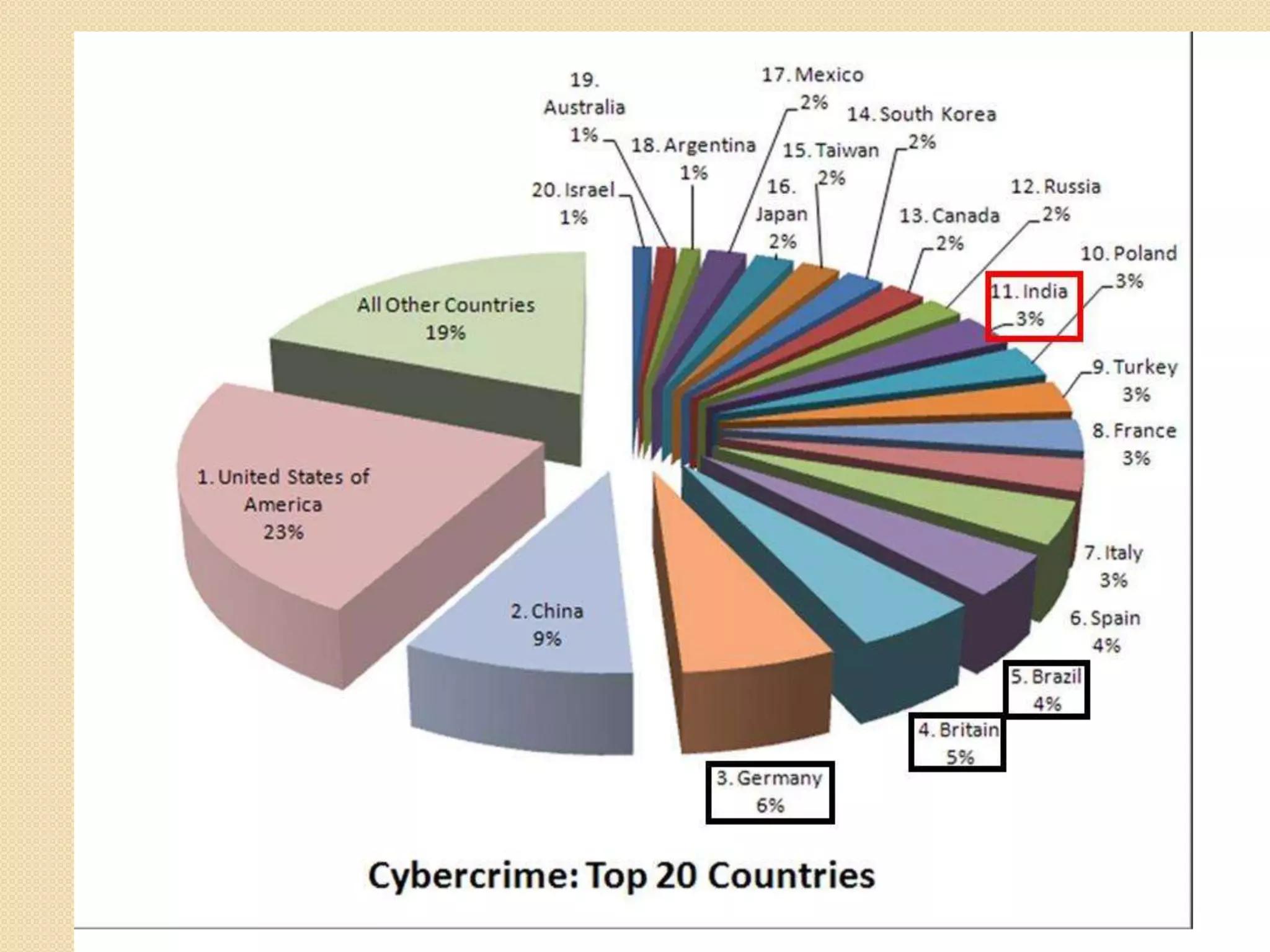
This document discusses hacking and cracking. It defines hacking as unauthorized attempts to bypass security systems or networks, and distinguishes between ethical ("white hat") hackers and criminal ("black hat") hackers. It describes common hacking techniques like phishing and pretexting. The document also provides examples of famous hackers and notes that most hacking targets social media sites. It recommends security measures like antivirus software and firewalls to prevent hacking.