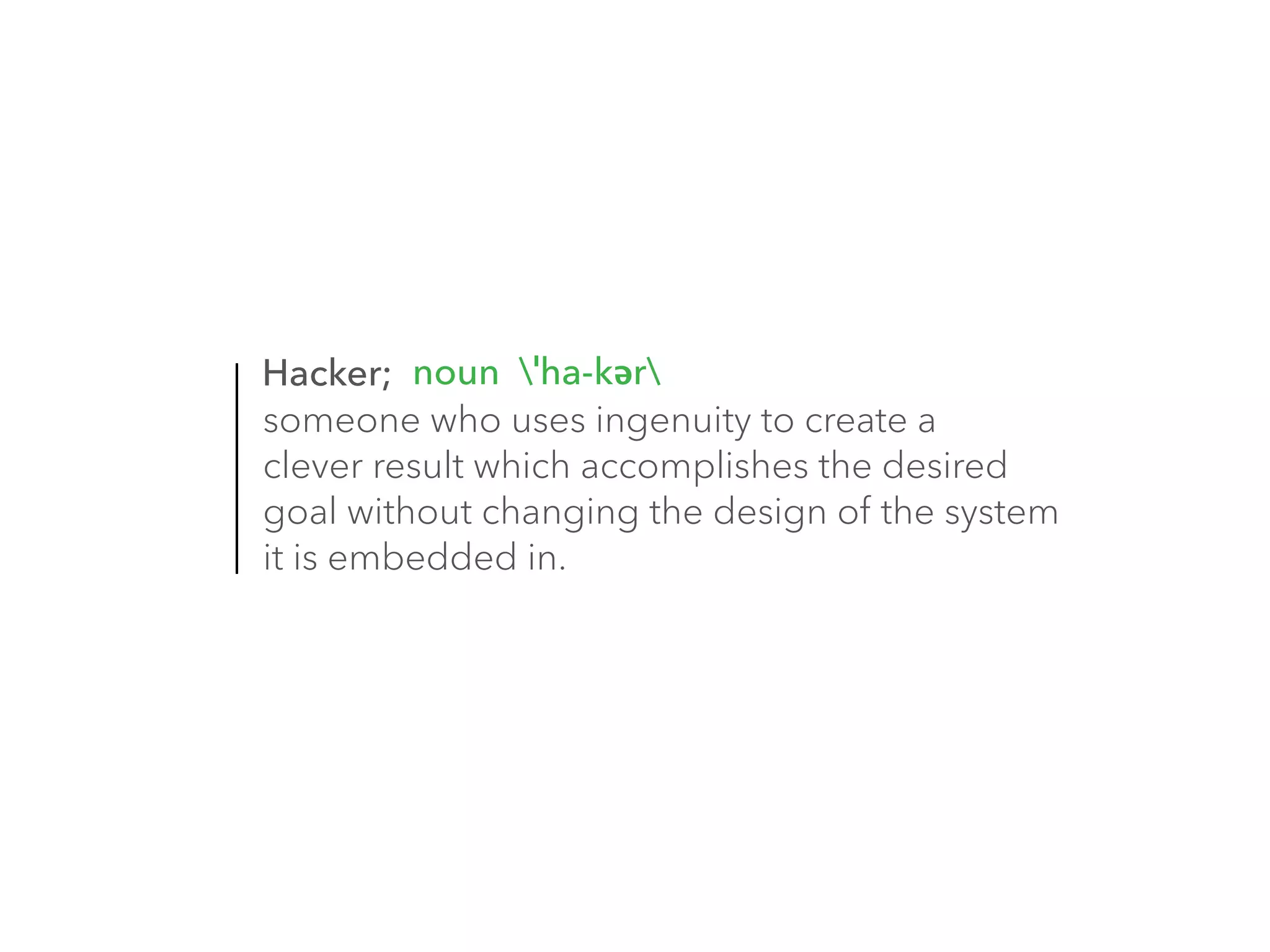
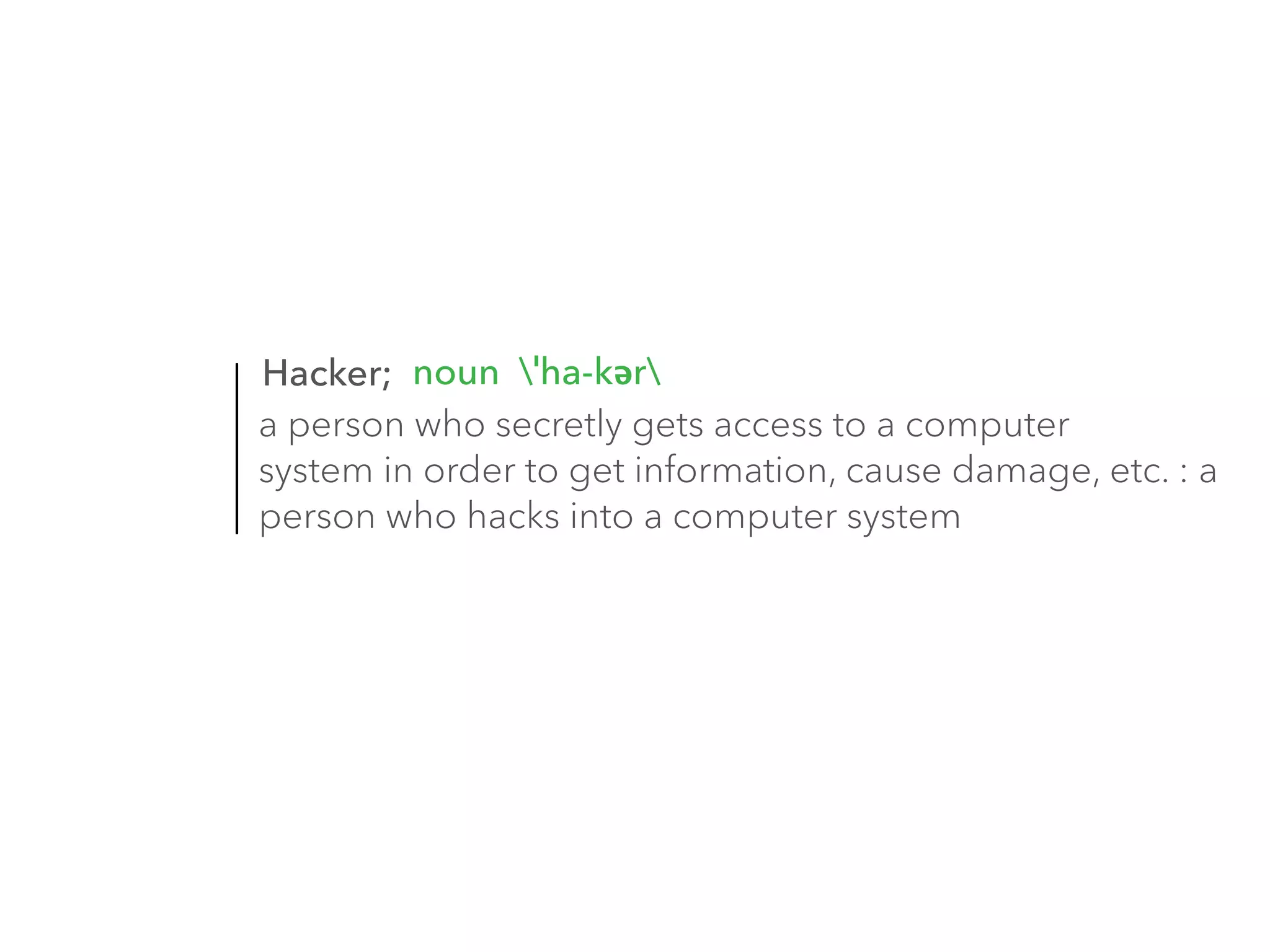
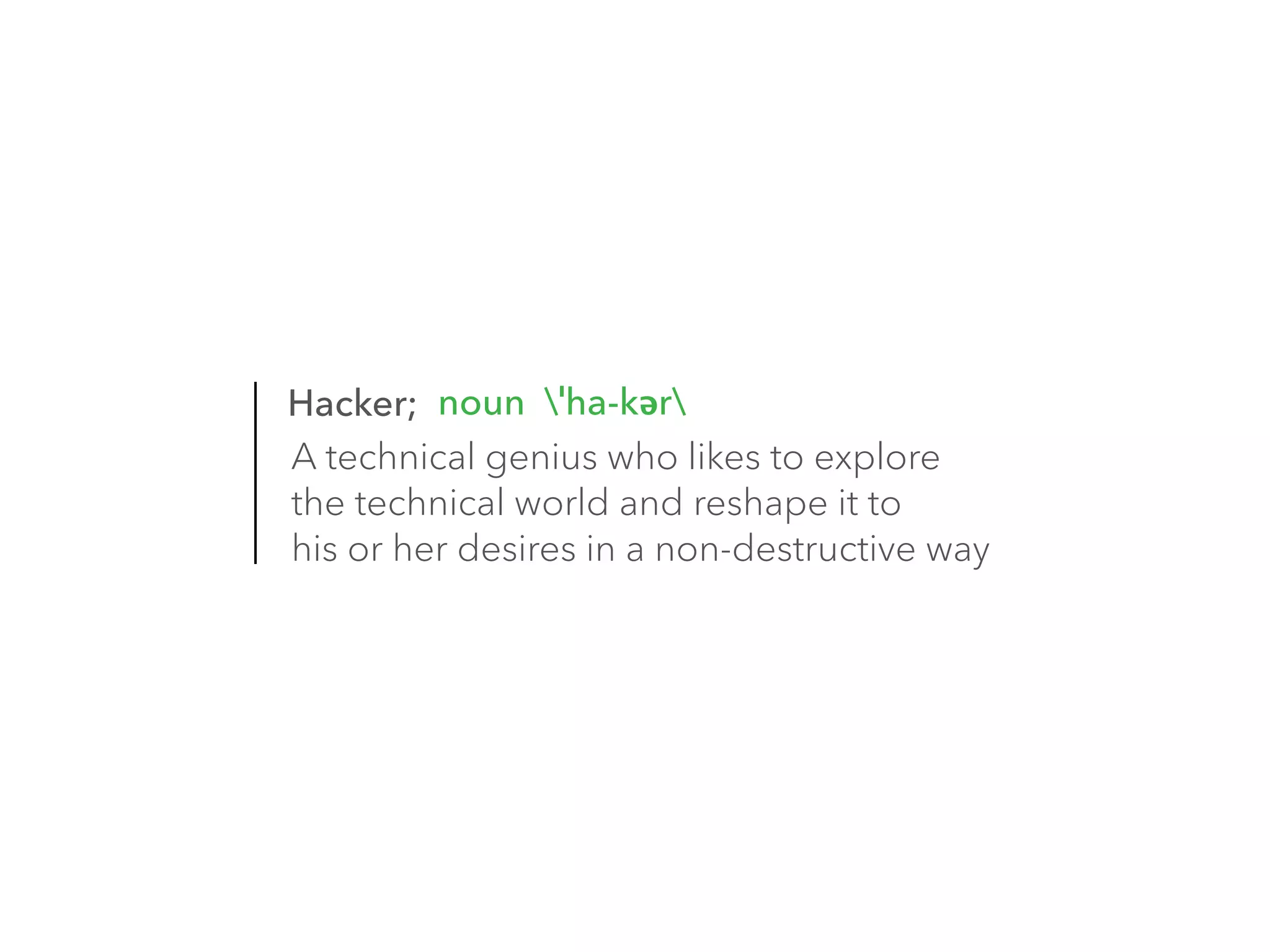
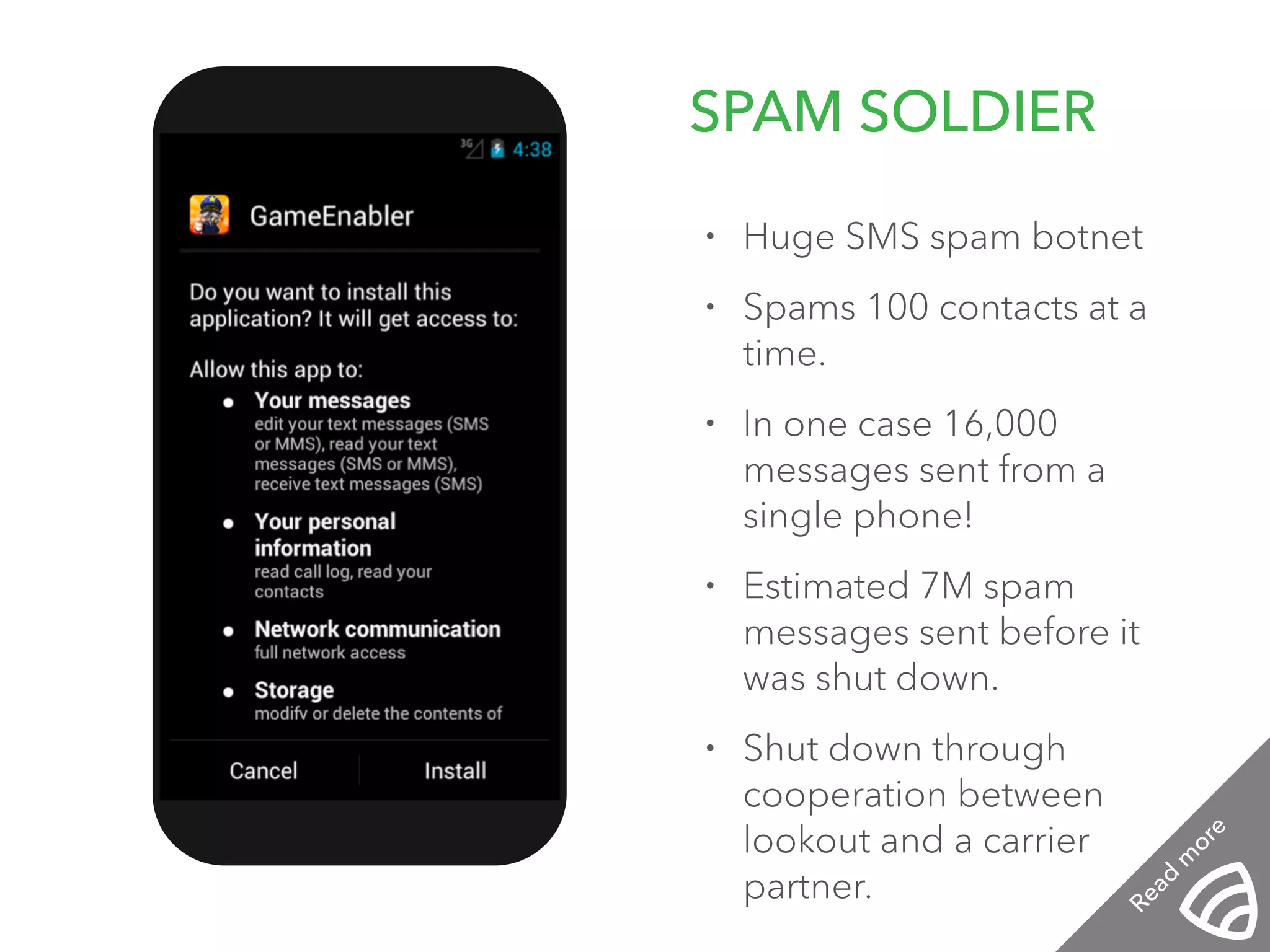
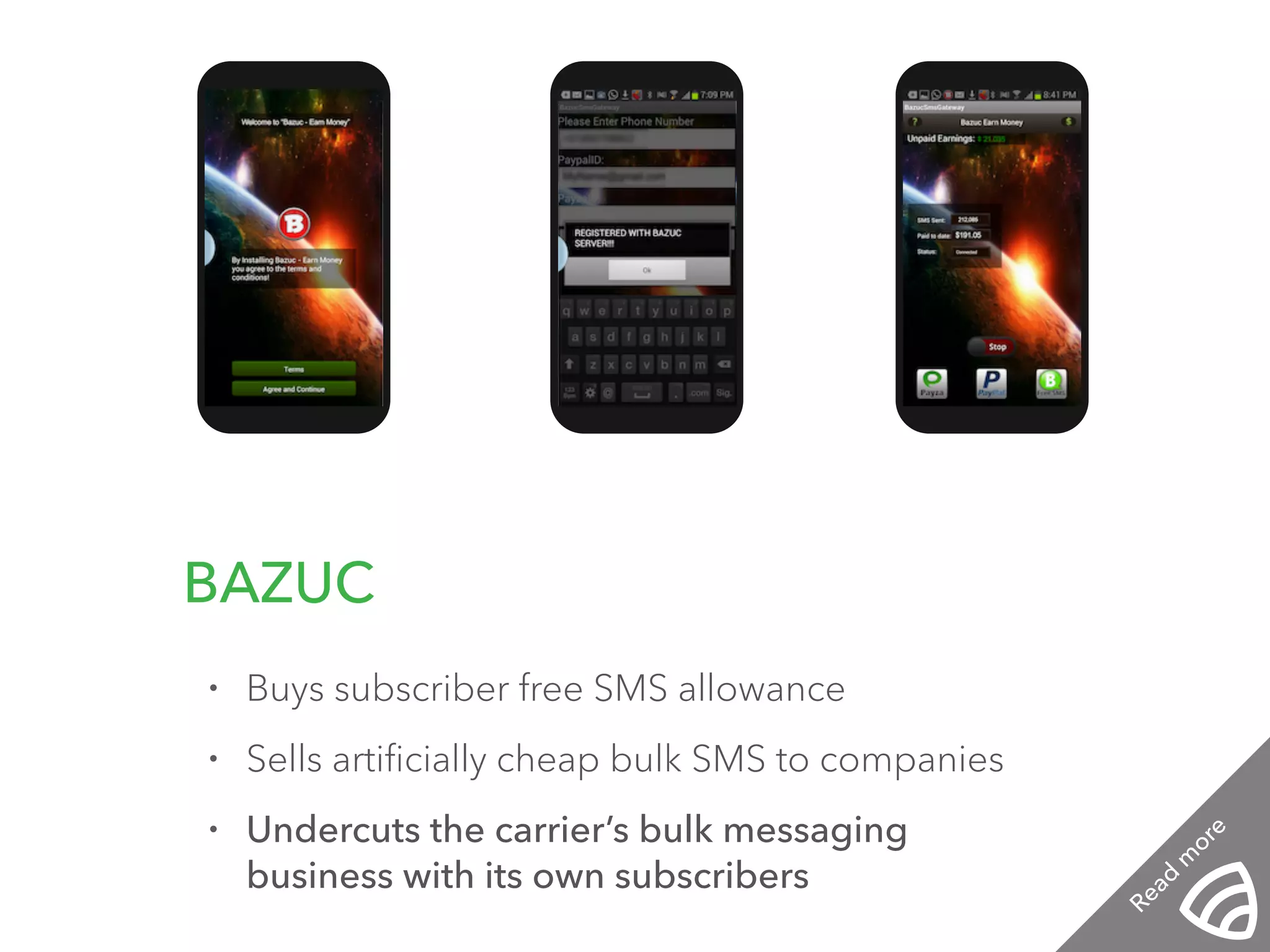
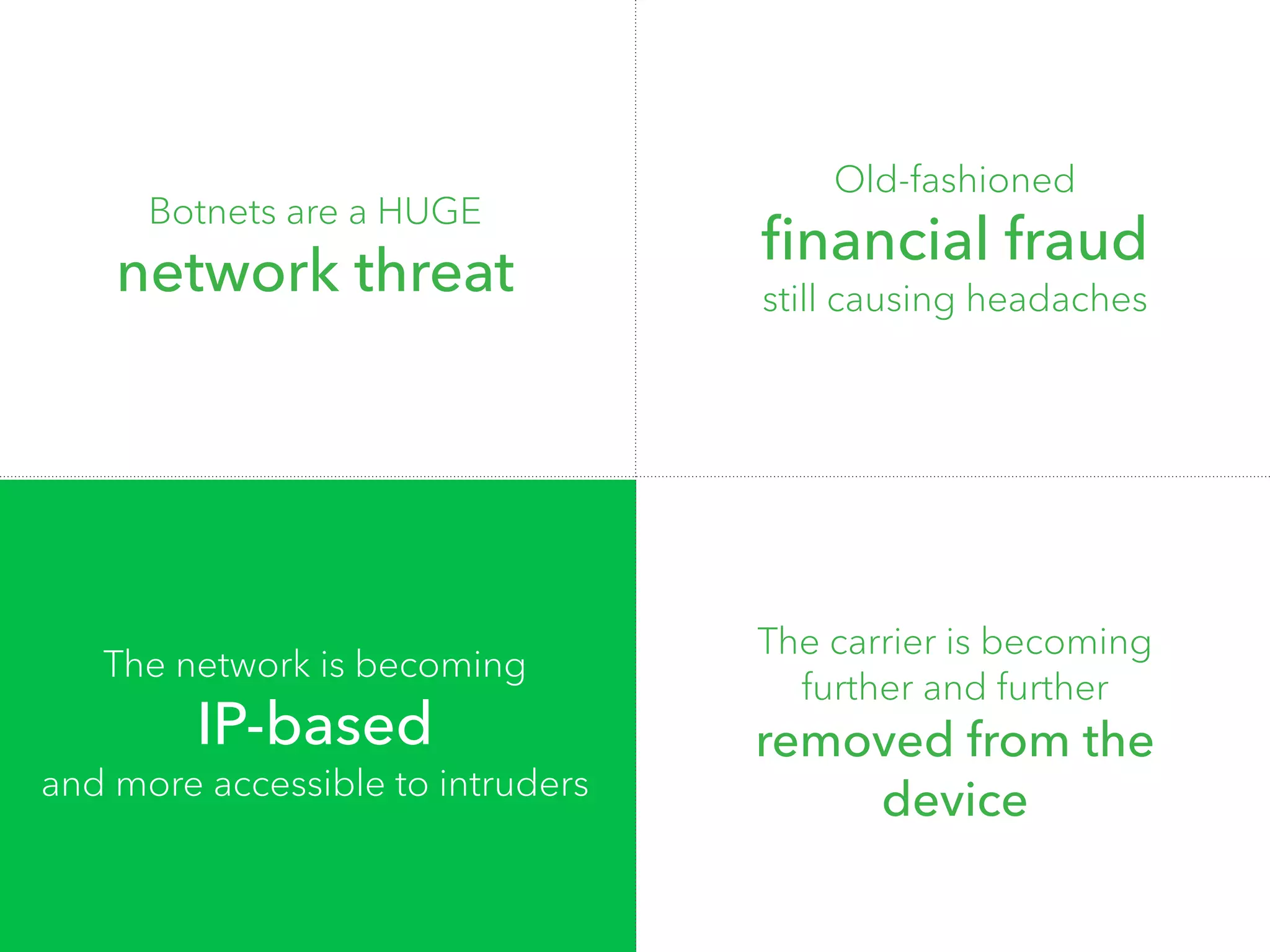
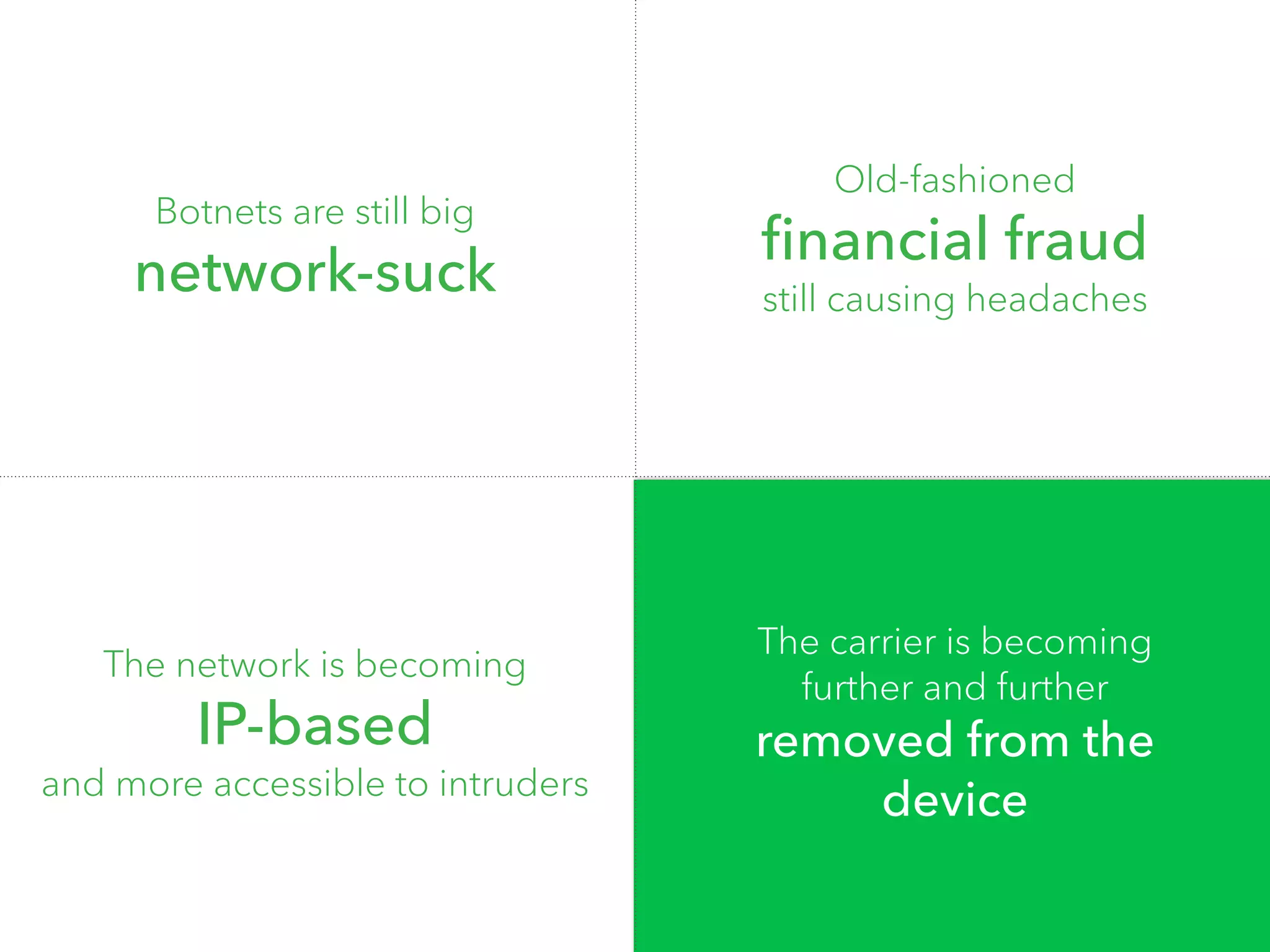
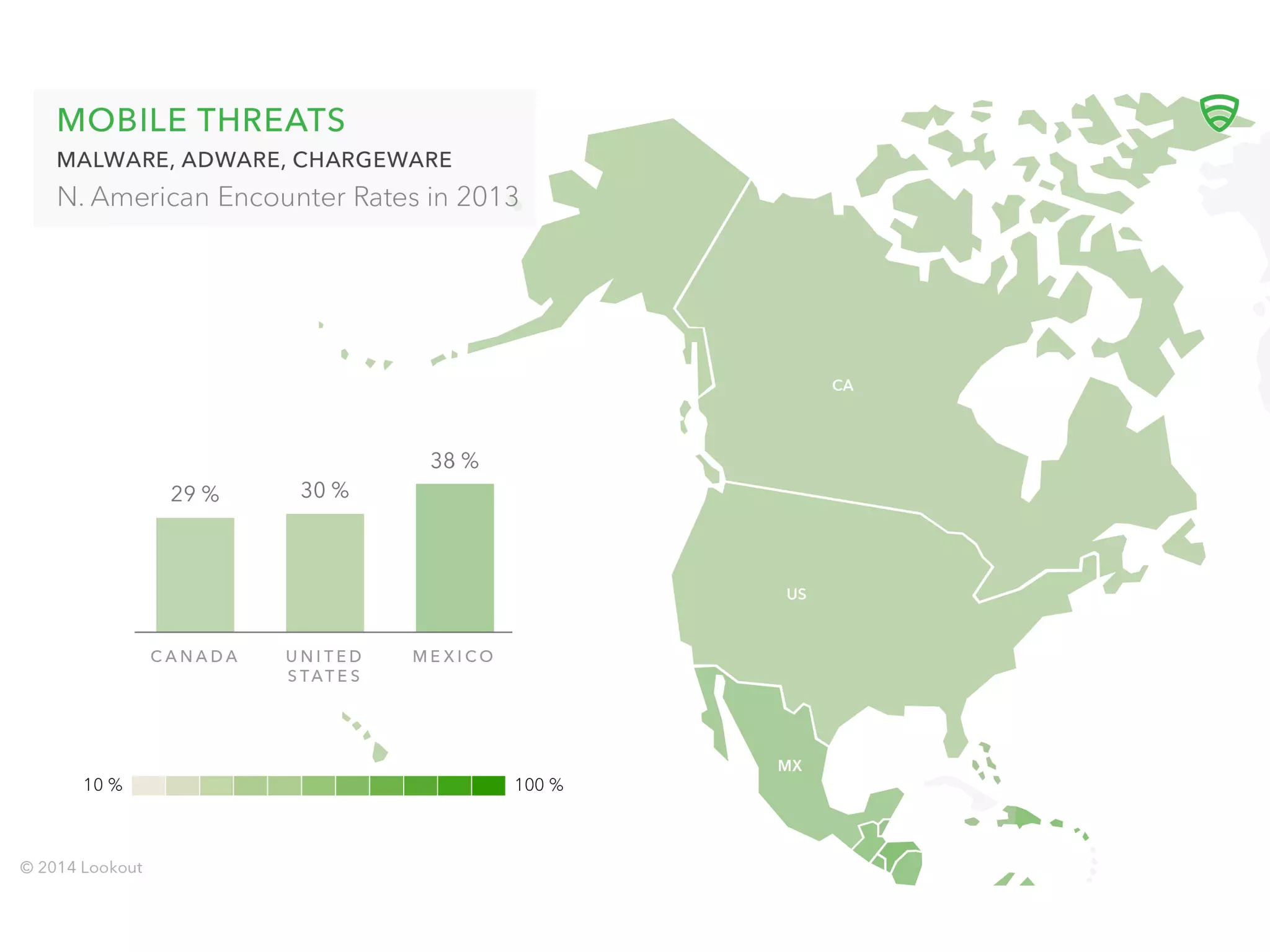
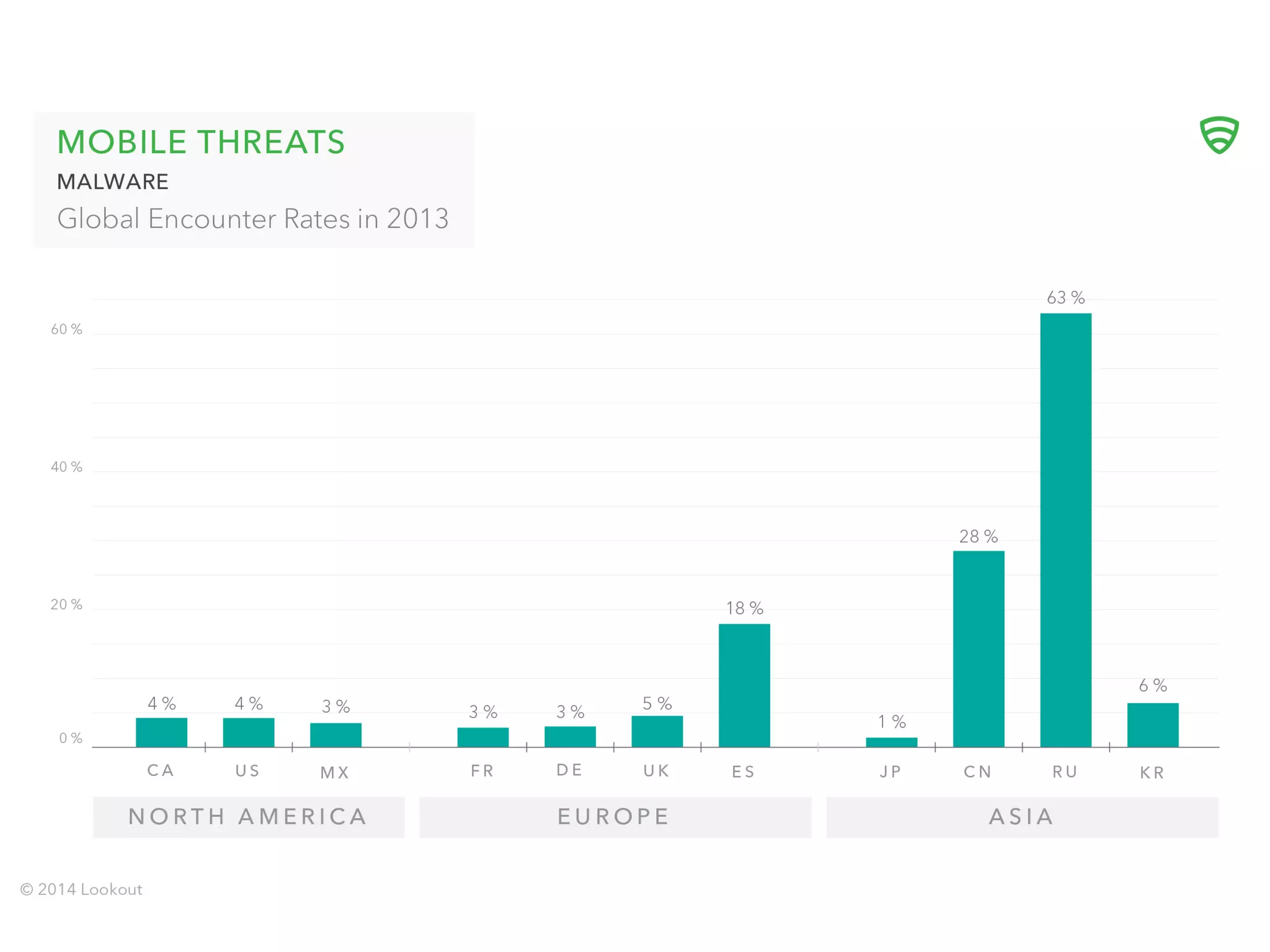
The document discusses the importance of hiring hackers in enterprises, emphasizing the unique problem-solving skills and mindset they bring. It addresses threats such as botnets and old-fashioned financial fraud that challenge carriers, who are increasingly distanced from devices as networks become more accessible to intruders. The author highlights various hacking initiatives and collaborations aimed at enhancing mobile security.