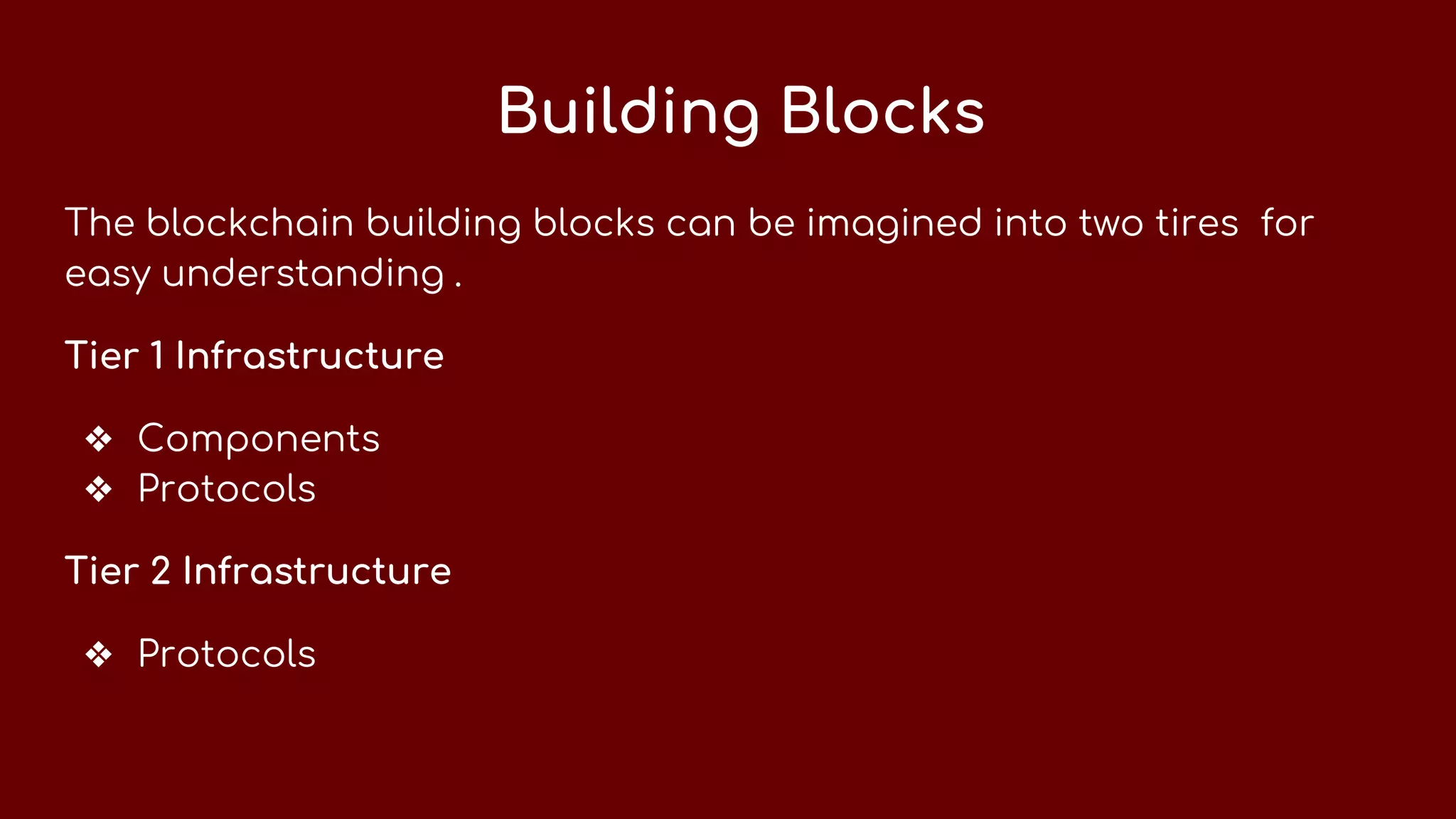
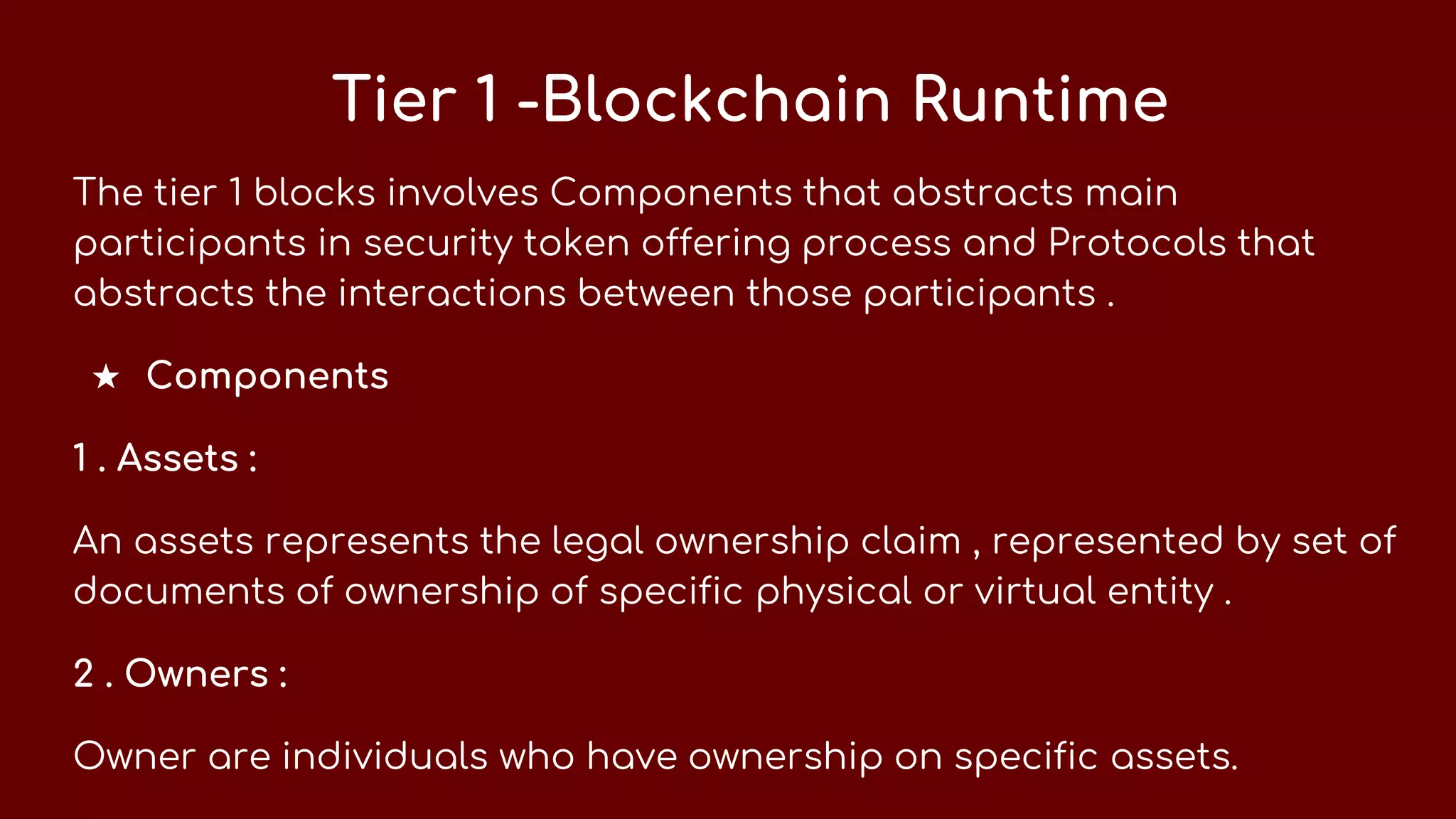
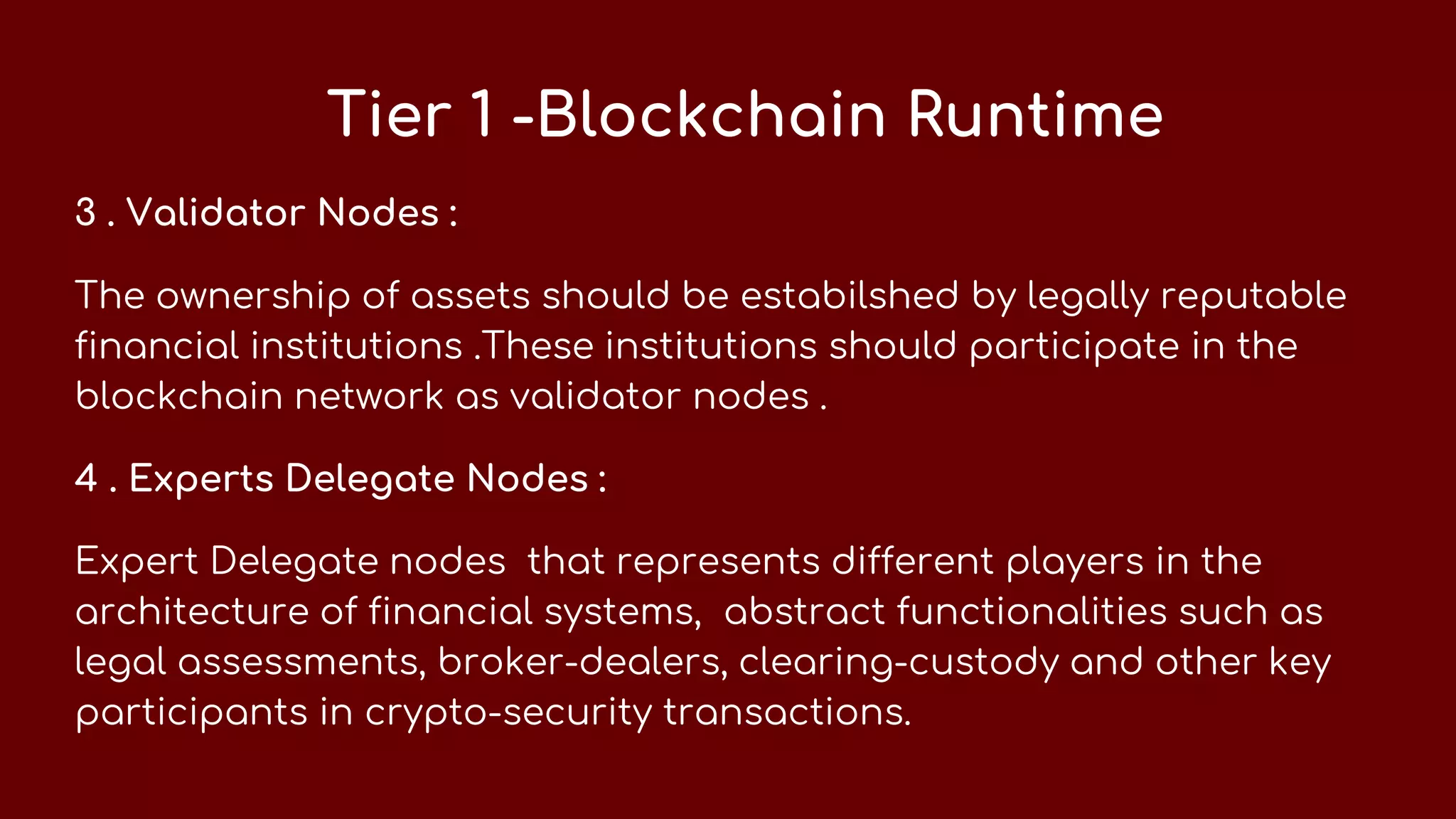
This document discusses how security tokens can be created using blockchain. It explains that security tokens allow investors to claim profits or shares after an ICO launch, unlike utility tokens. A security token blockchain requires a different infrastructure than a utility token blockchain. The security token blockchain architecture involves two tiers - the first includes components like assets, owners, validator nodes, and experts that interact through protocols for tokenization, identity, ownership consensus, and privacy. The second tier includes protocols for crypto-security primitives, compliance, and disclosures.