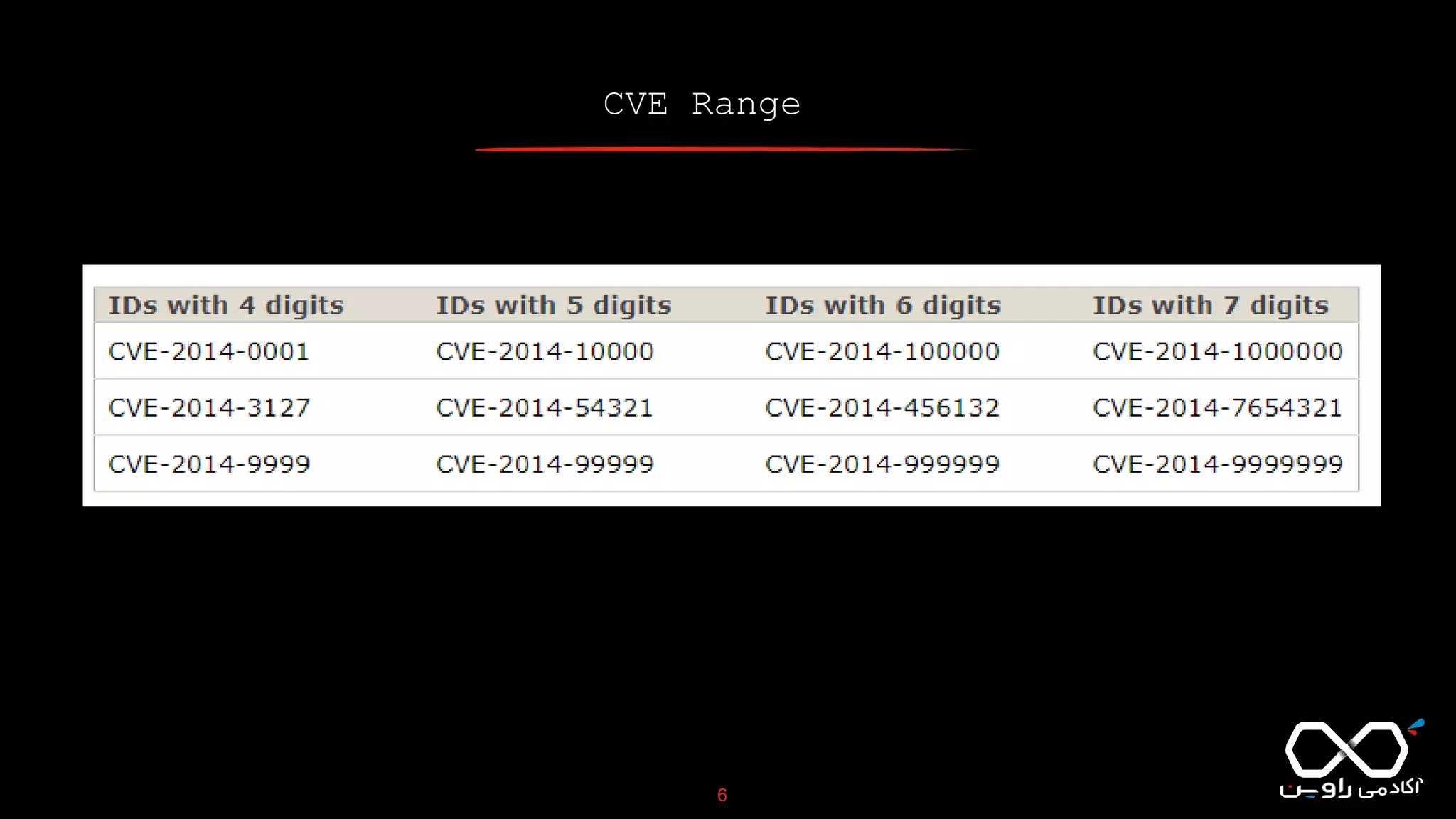
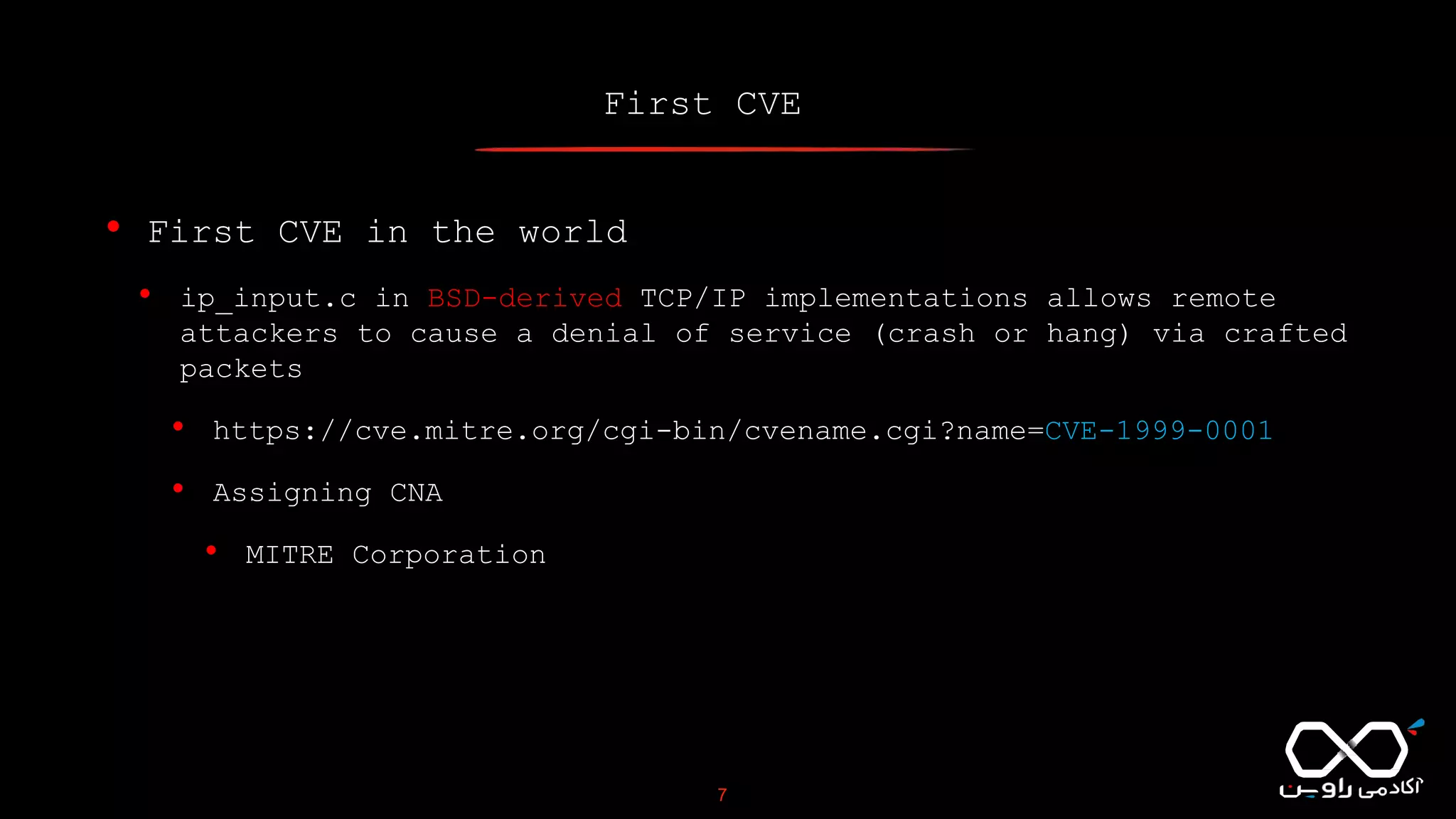
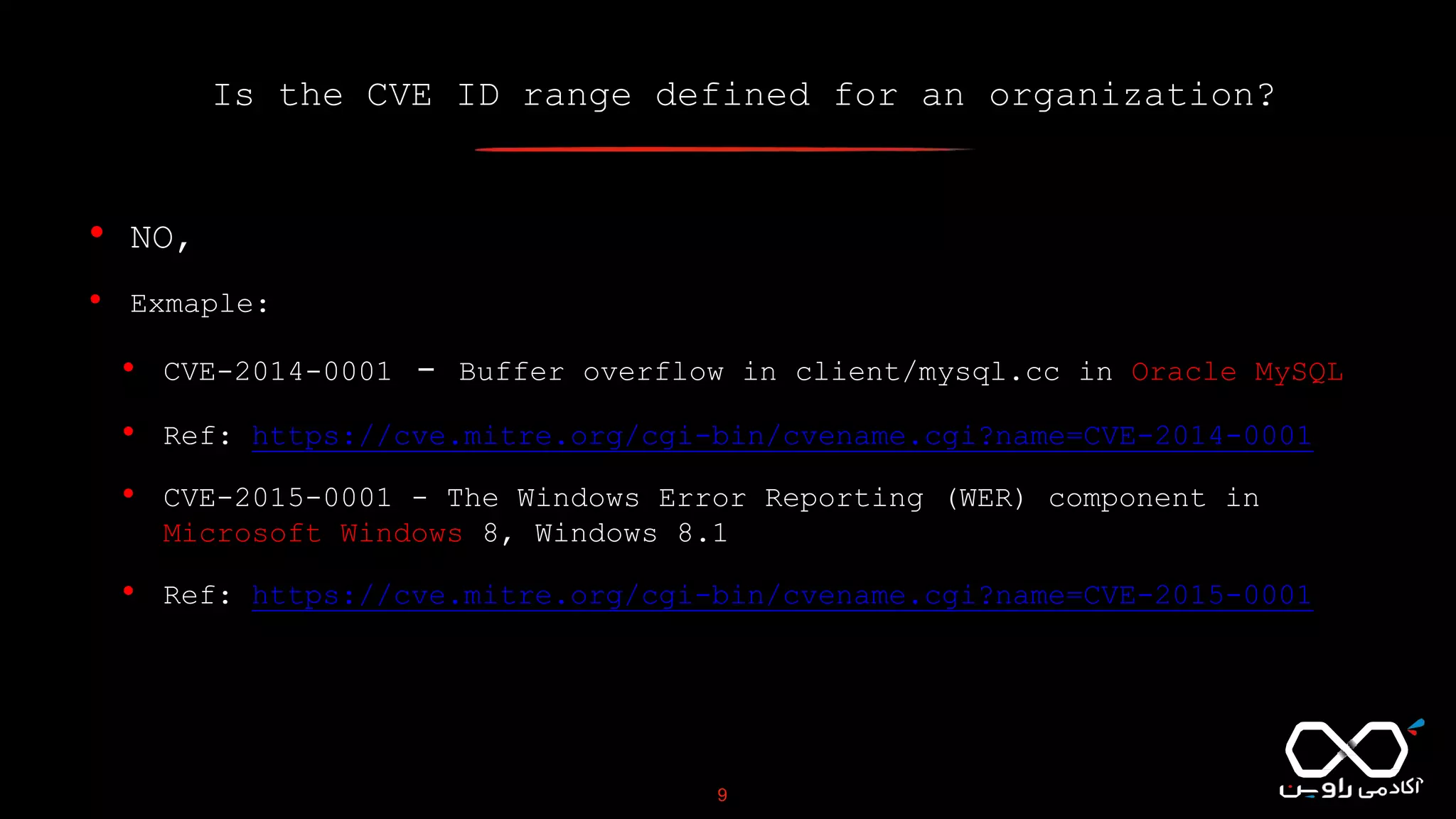
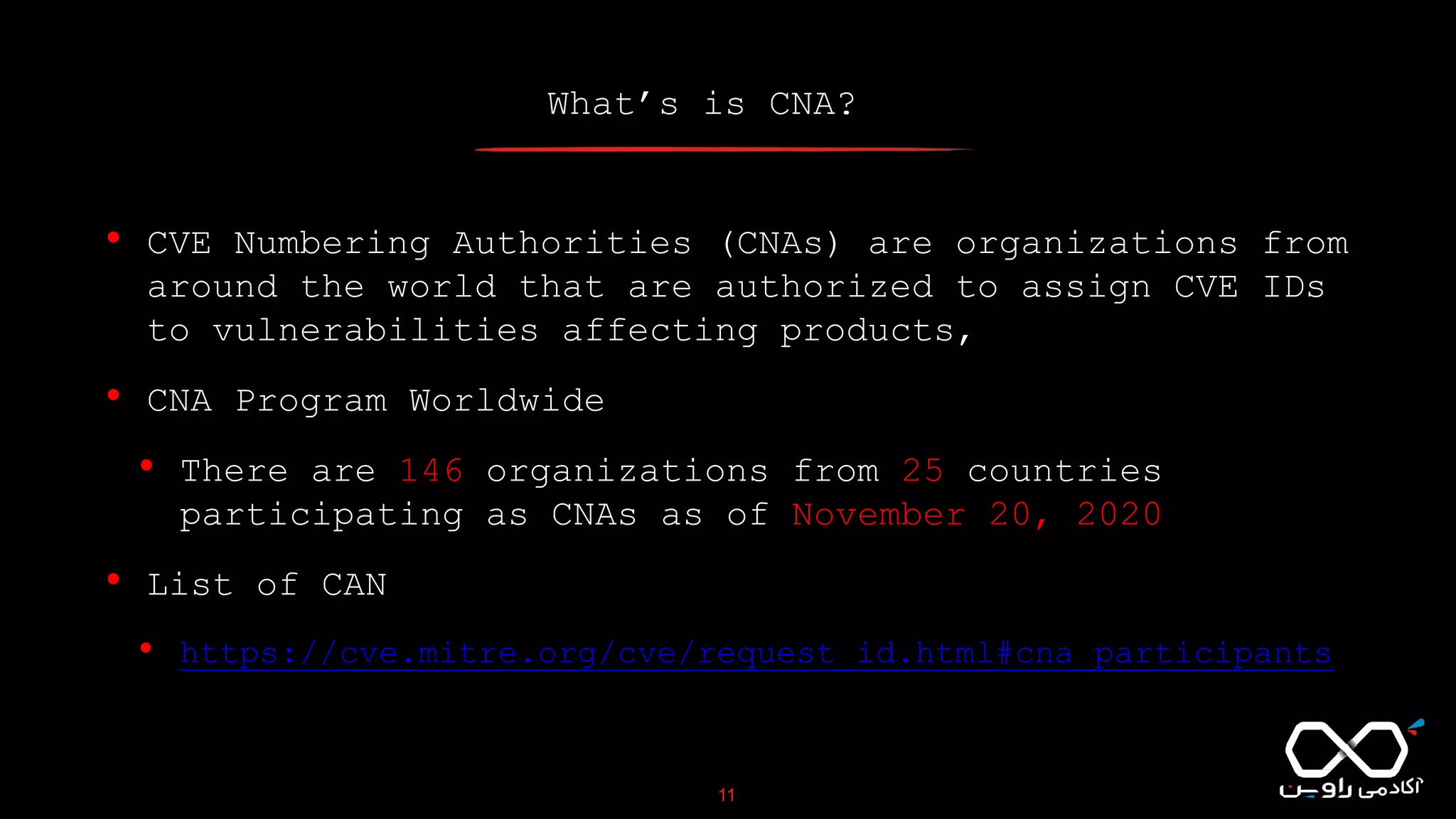
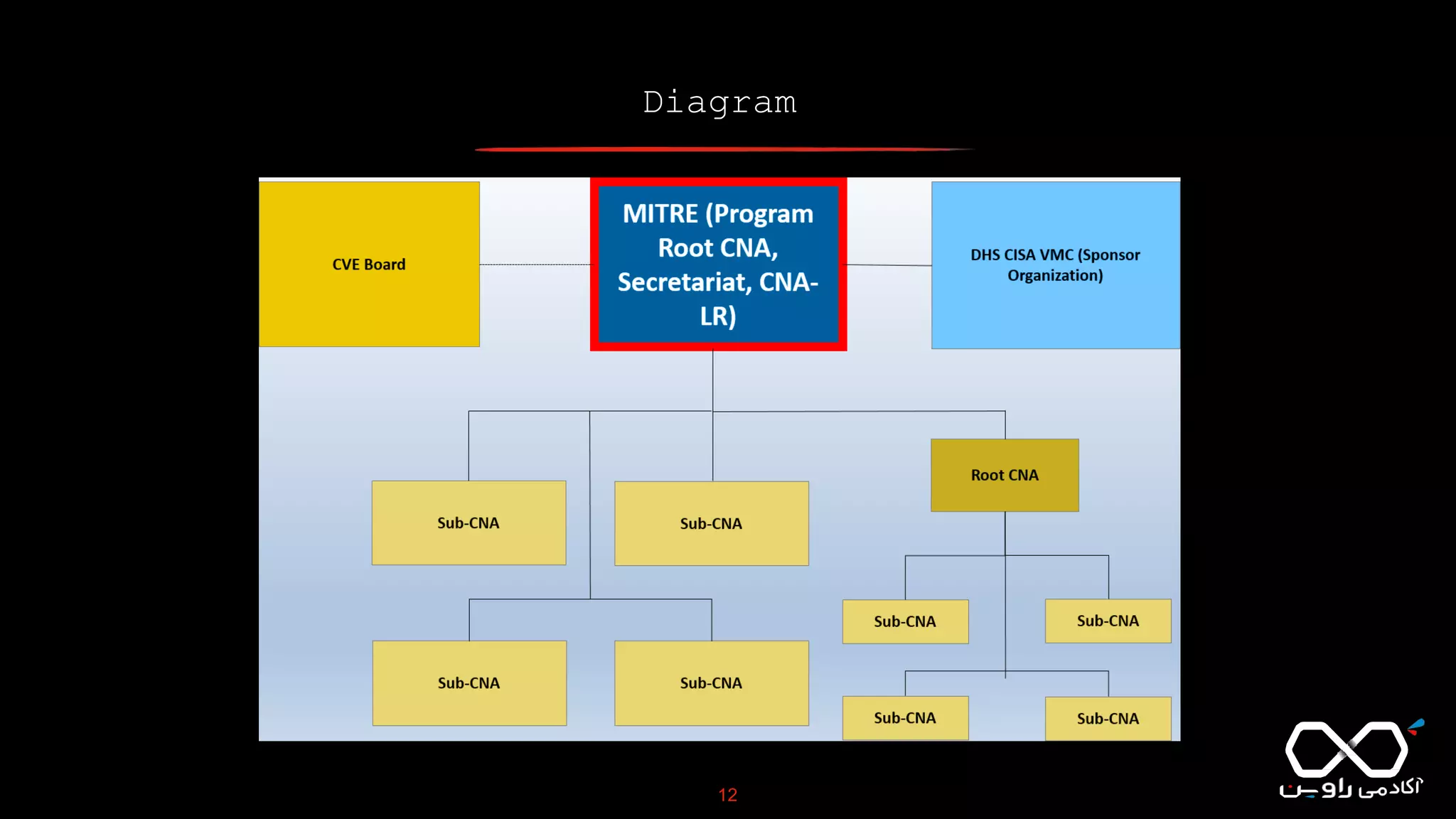
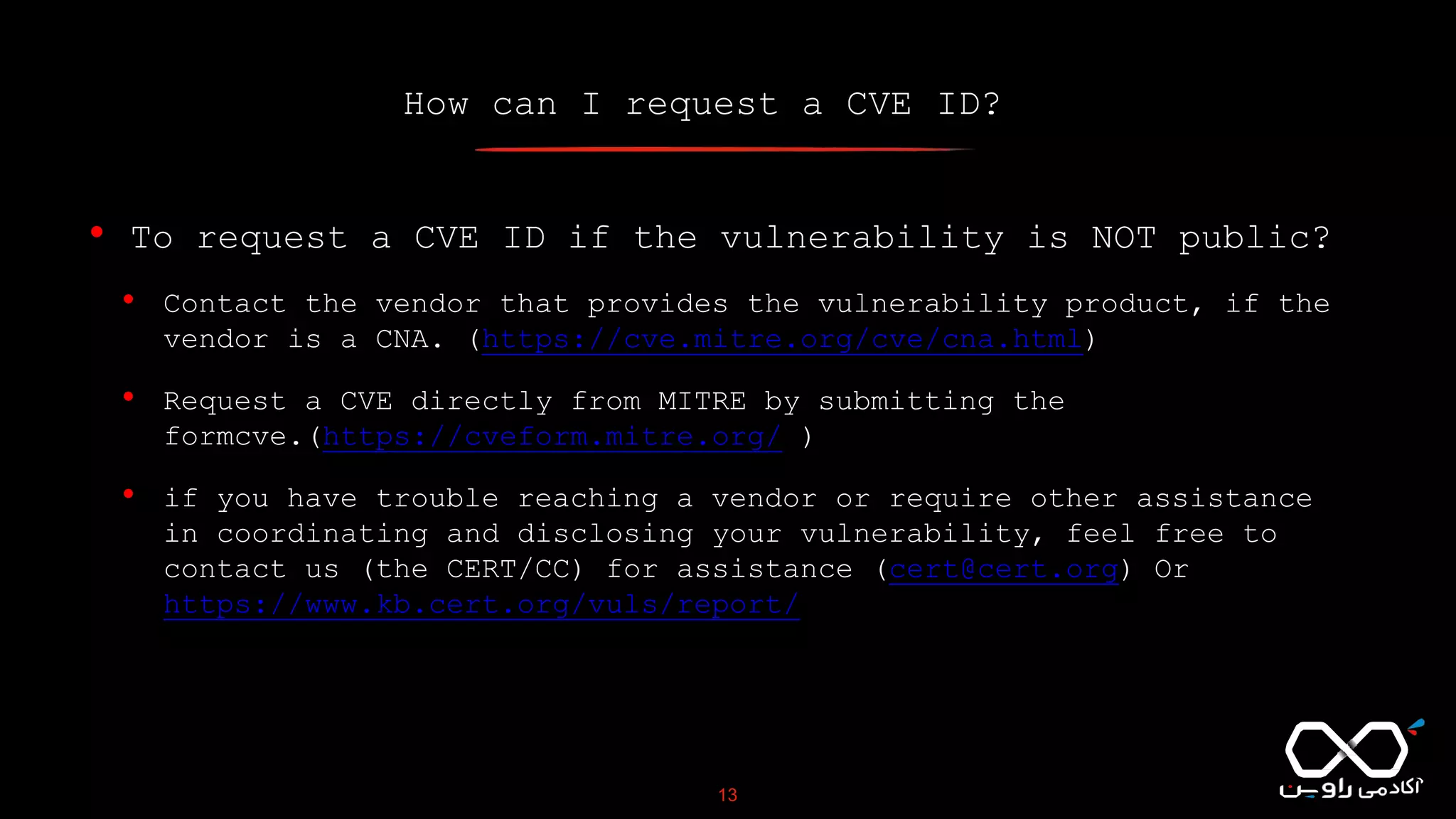
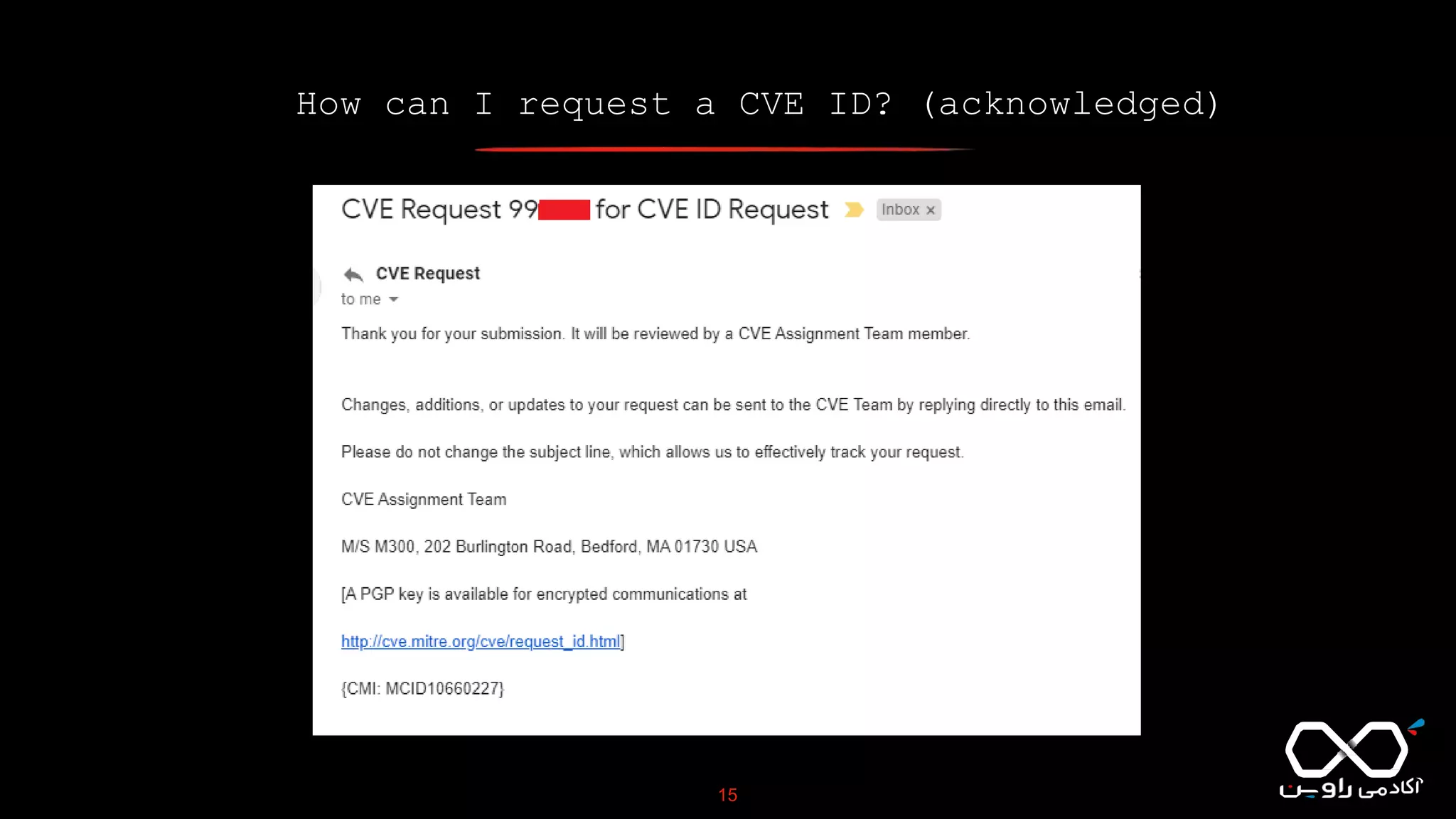
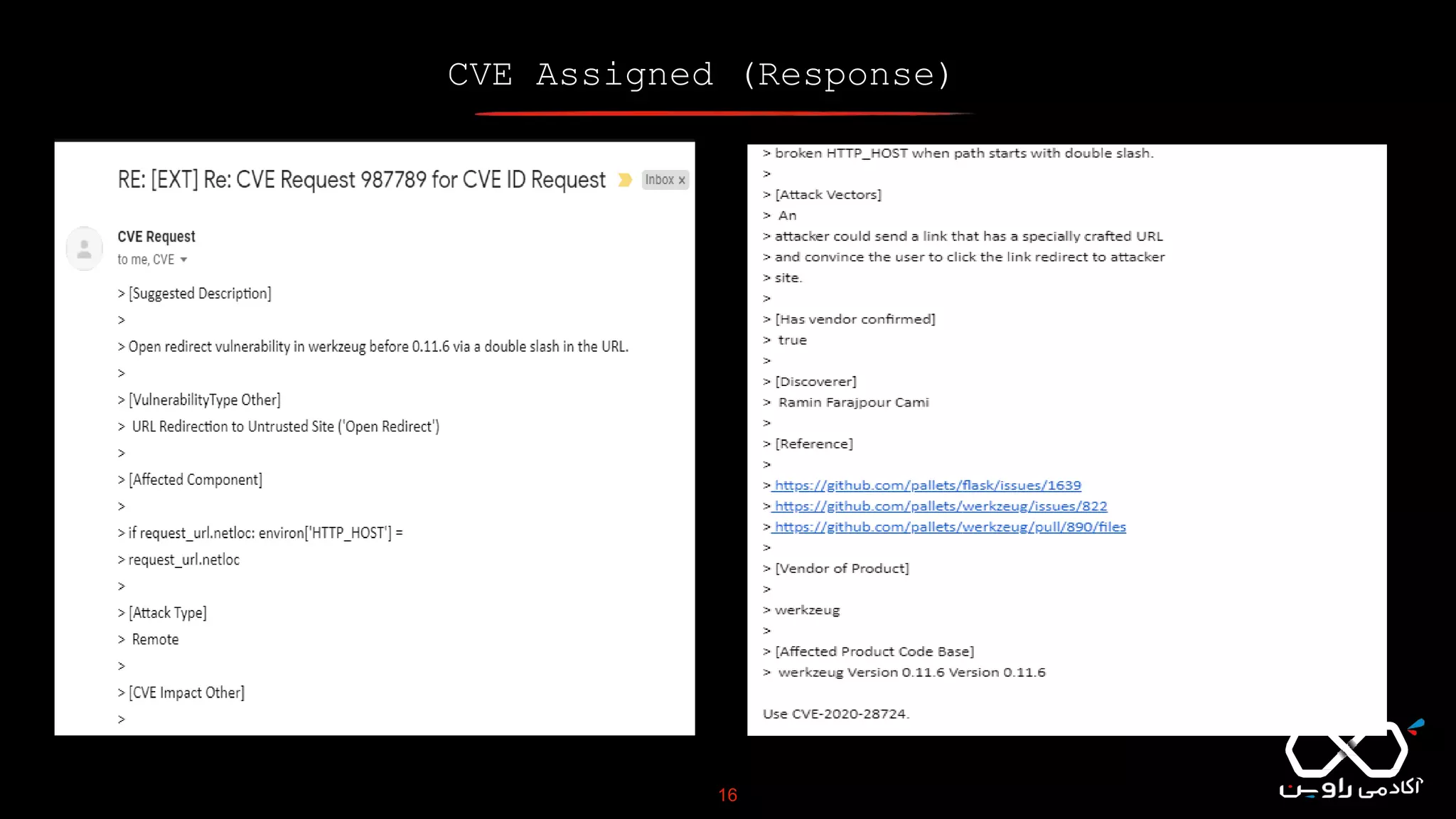
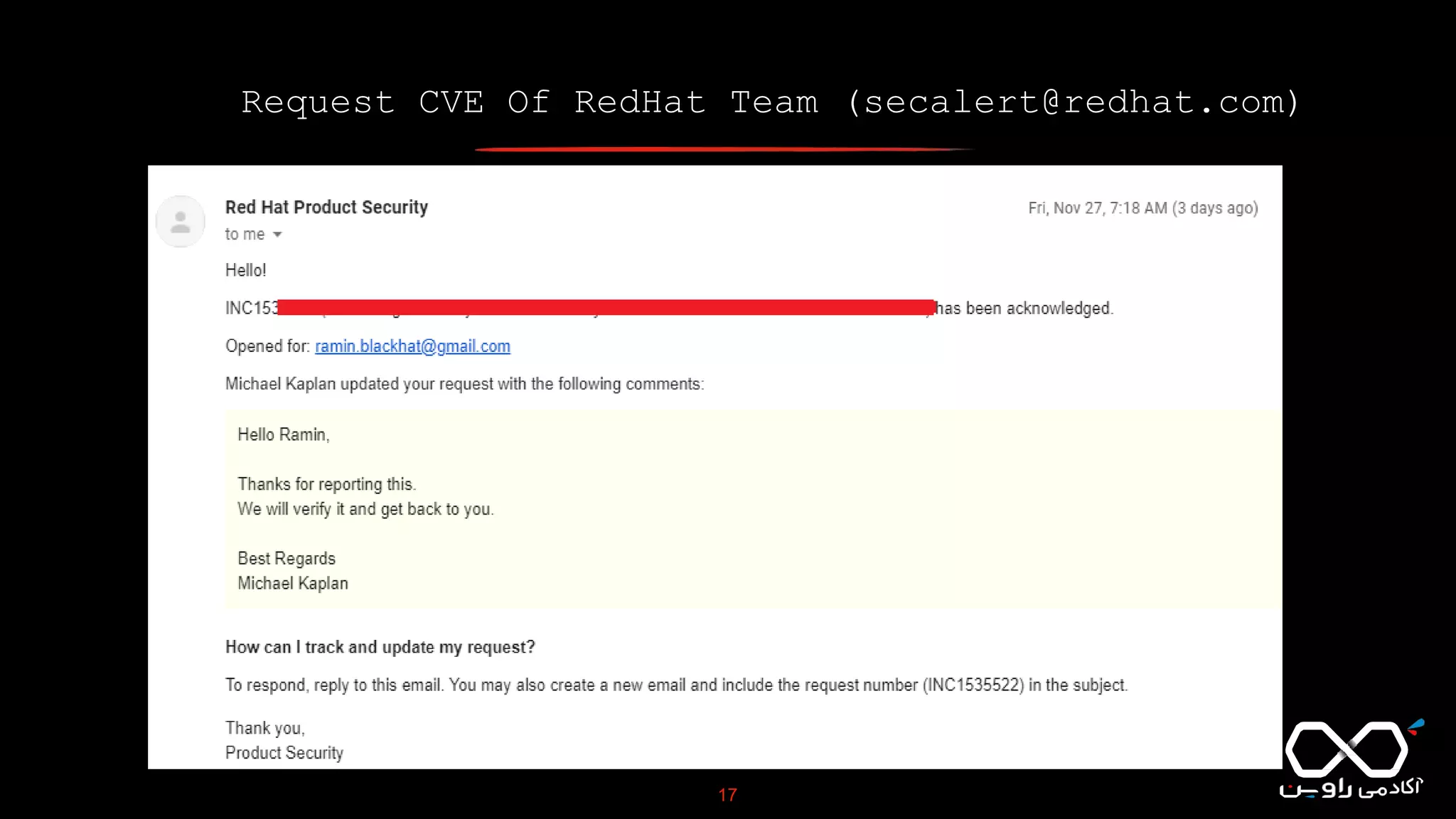
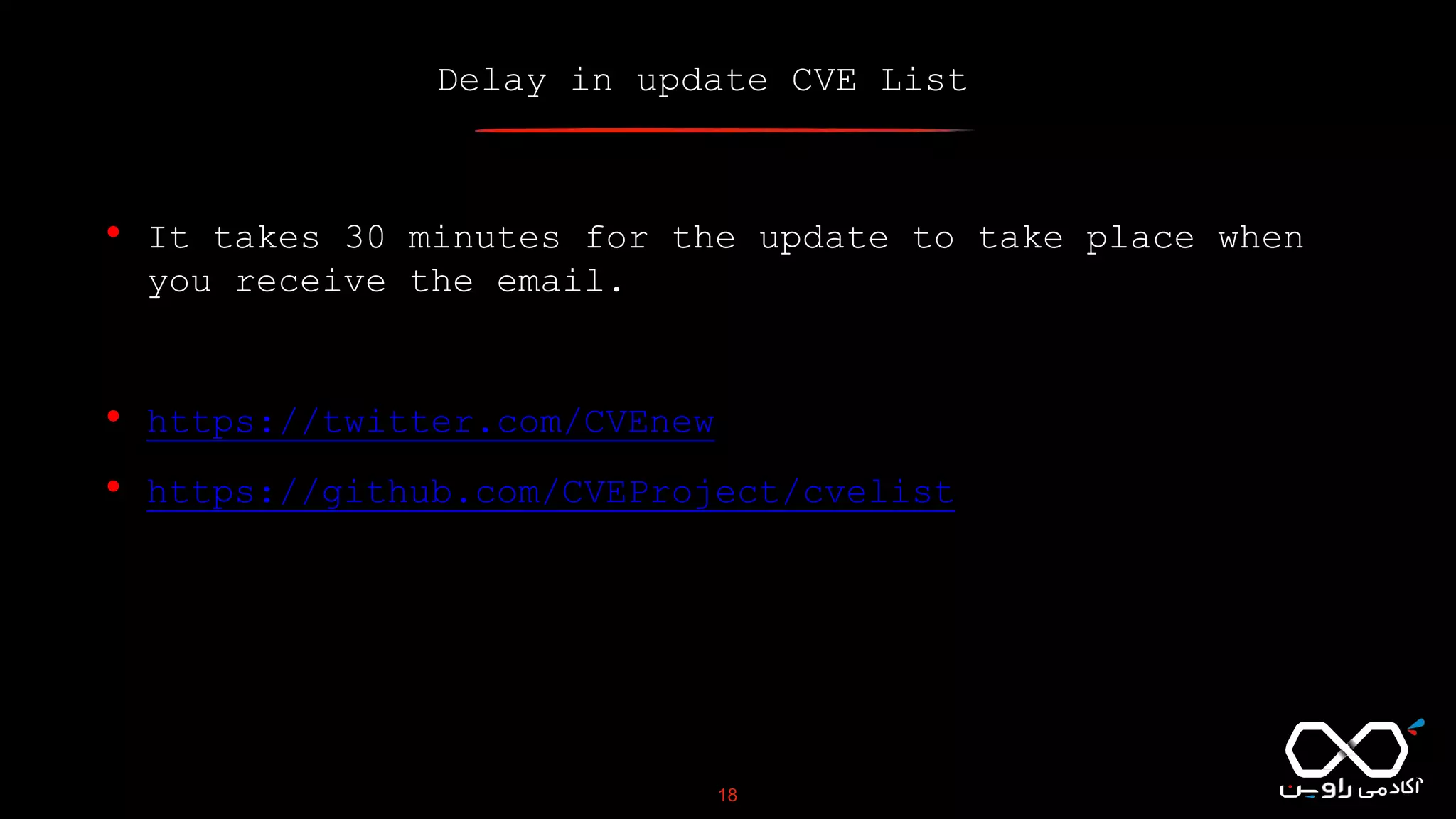
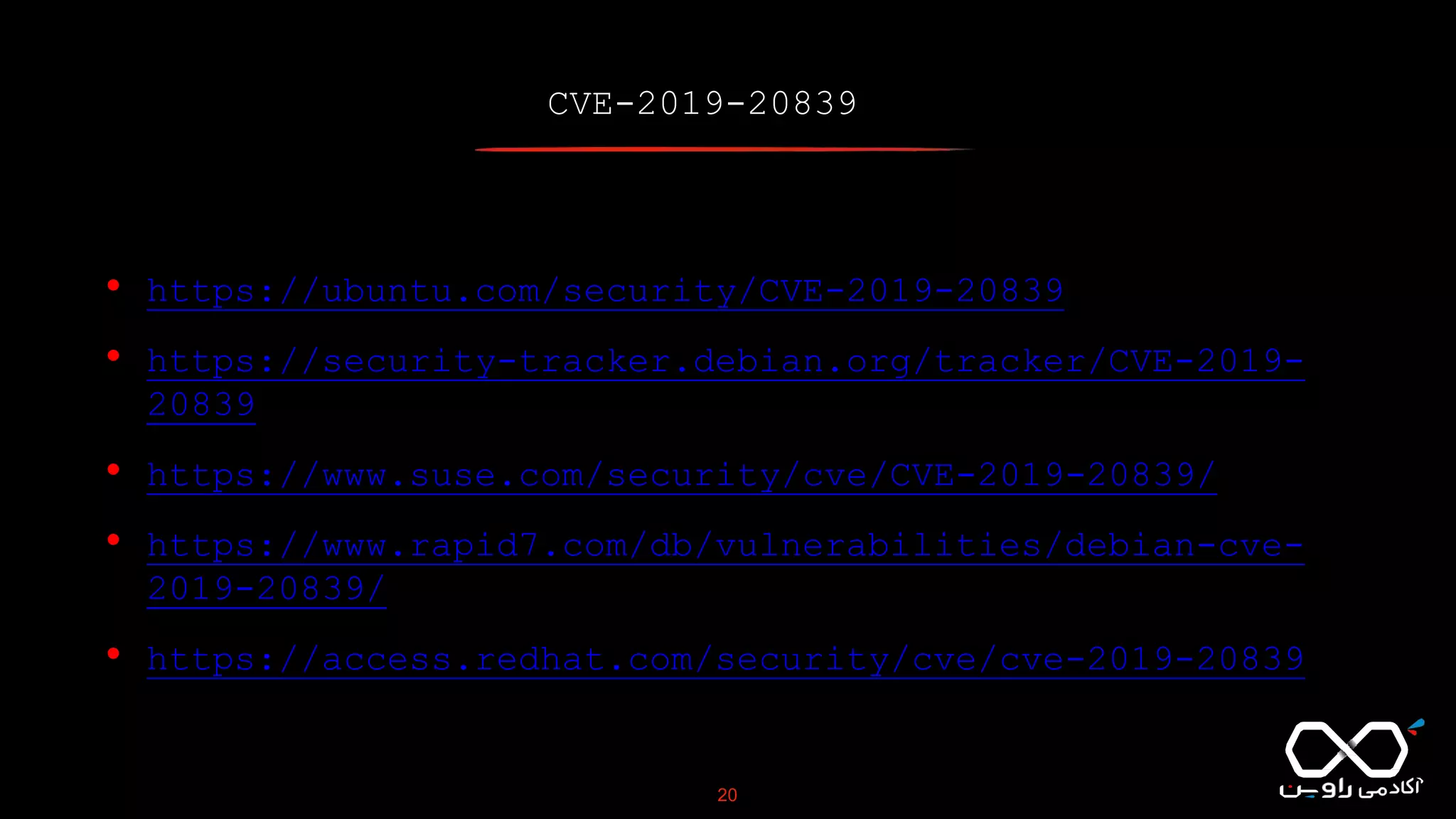
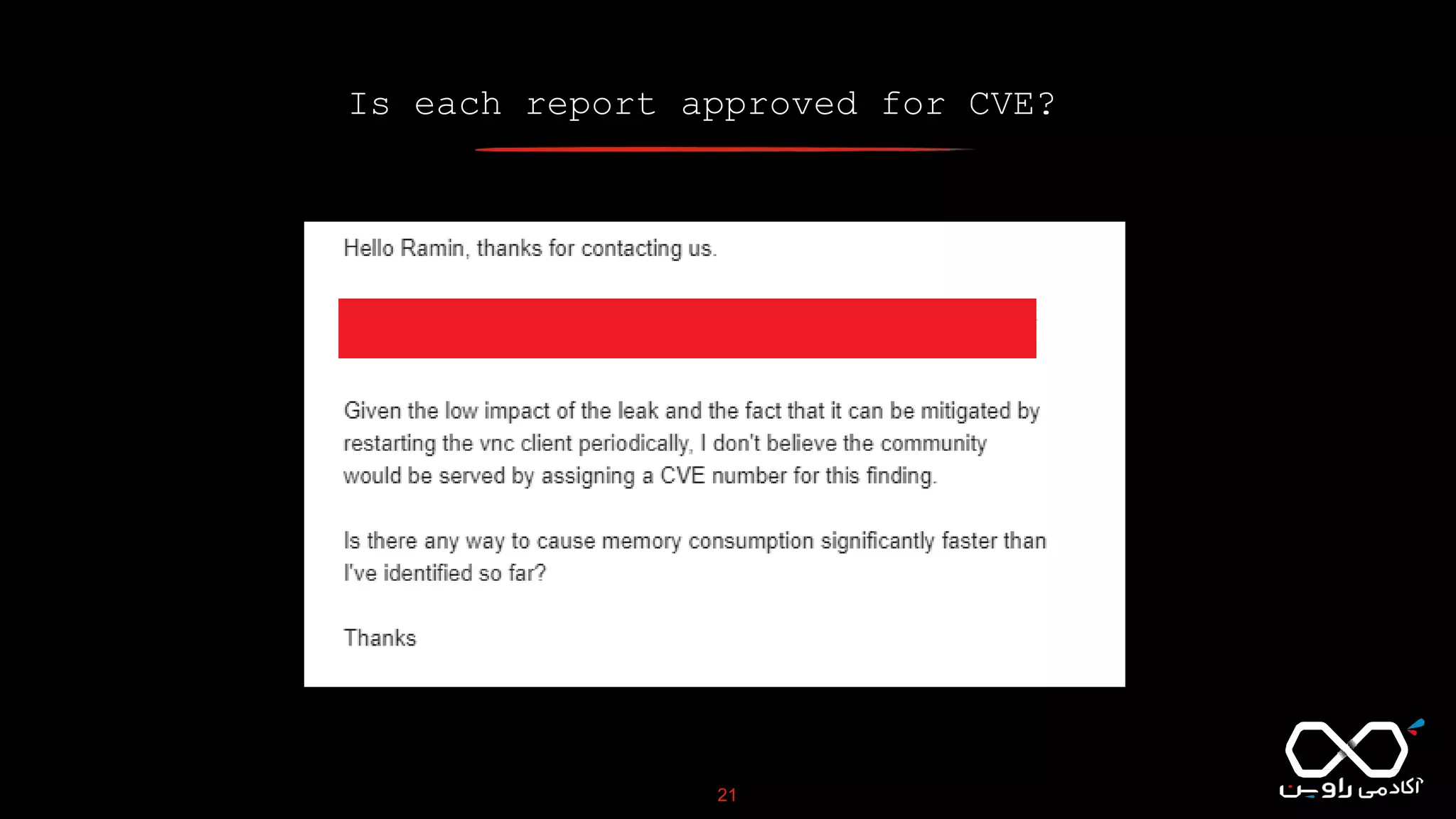
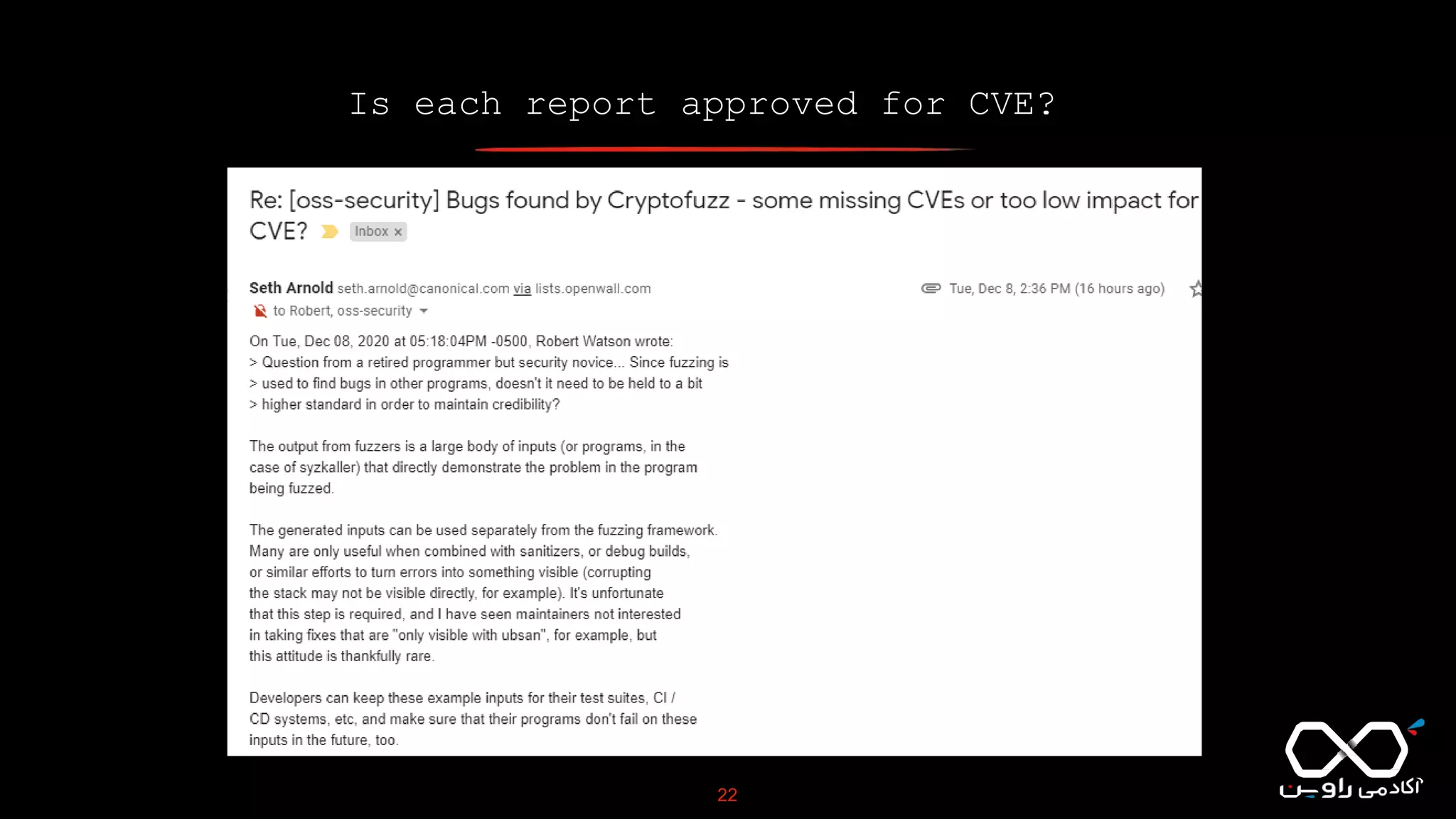
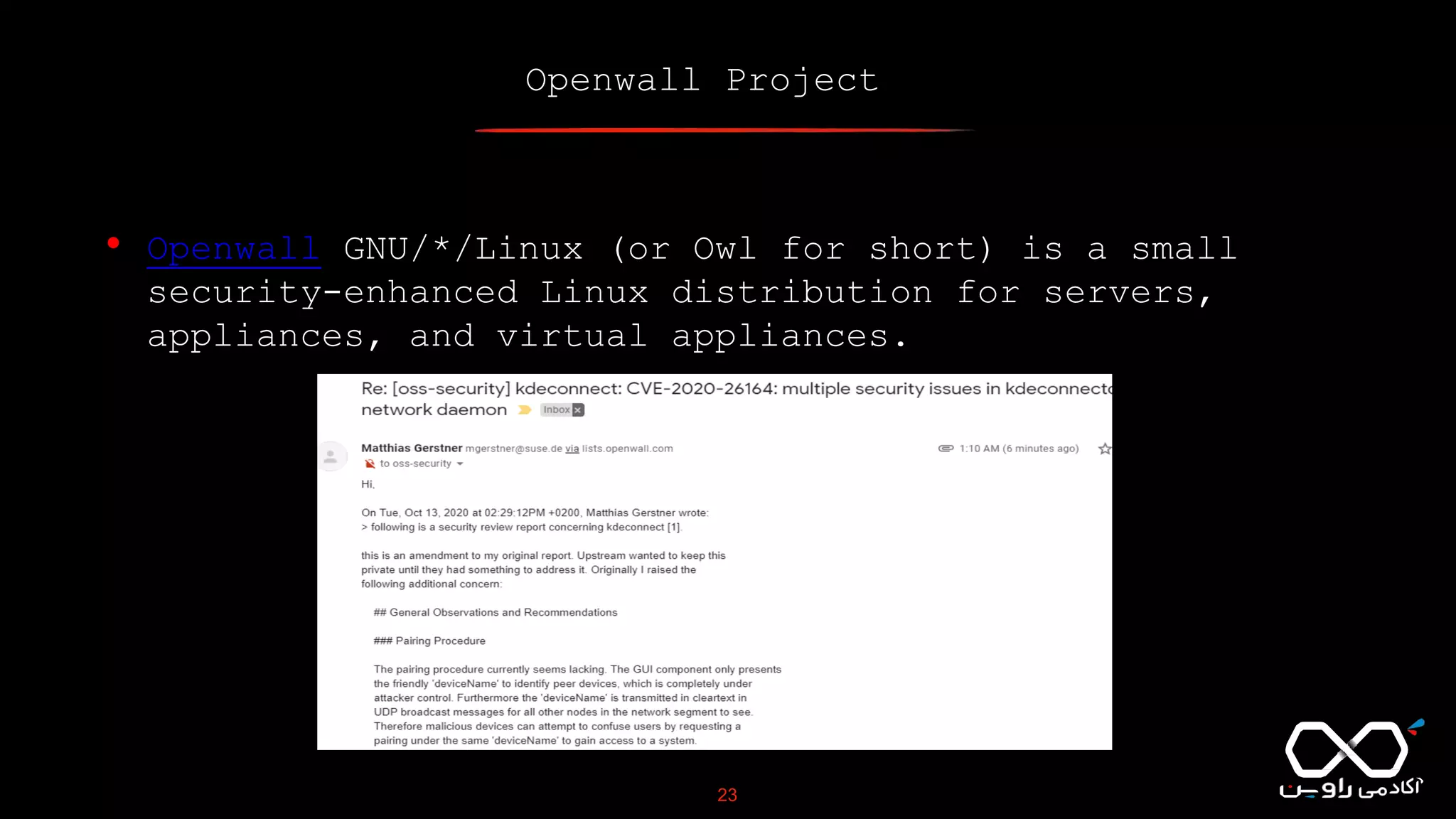
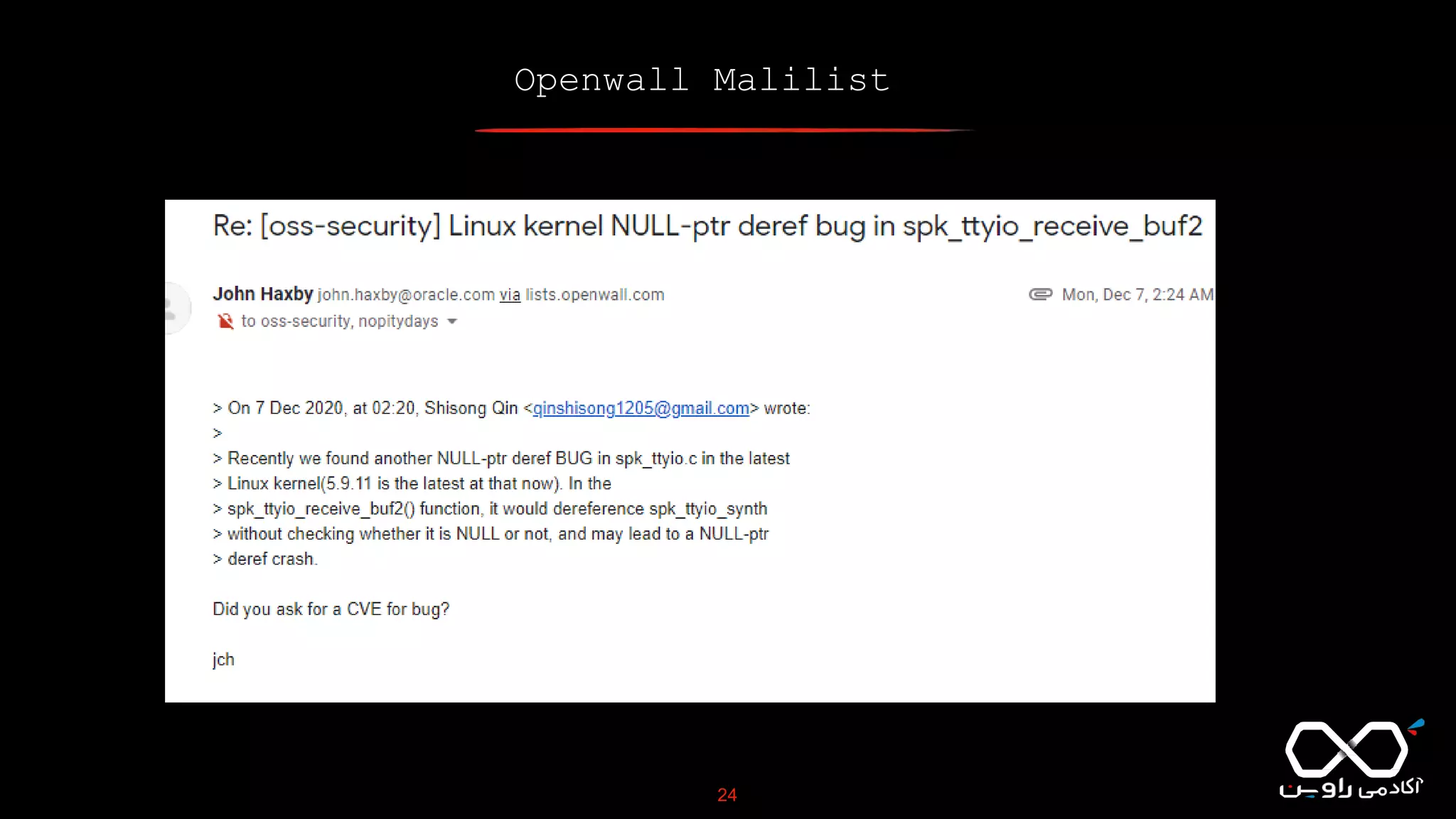
This document discusses Common Vulnerabilities and Exposures (CVE), which is a list of publicly disclosed computer security flaws identified by CVE IDs. It describes how CVE IDs are assigned by MITRE and partner organizations to vulnerabilities to help coordinate security efforts. The document also provides information on how individuals can request CVE IDs and outlines the goal of the CVE system to help address vulnerabilities in software and products.