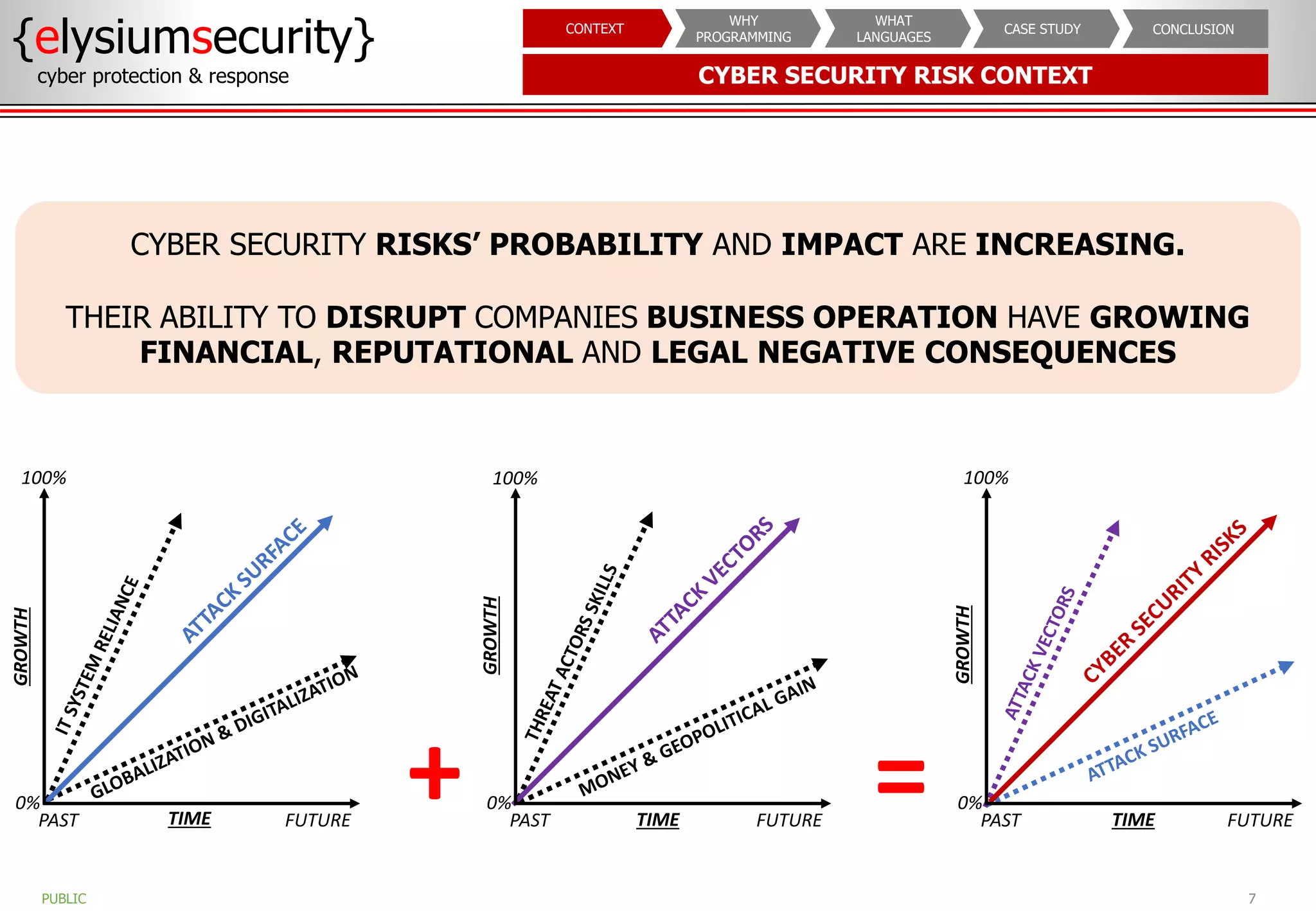
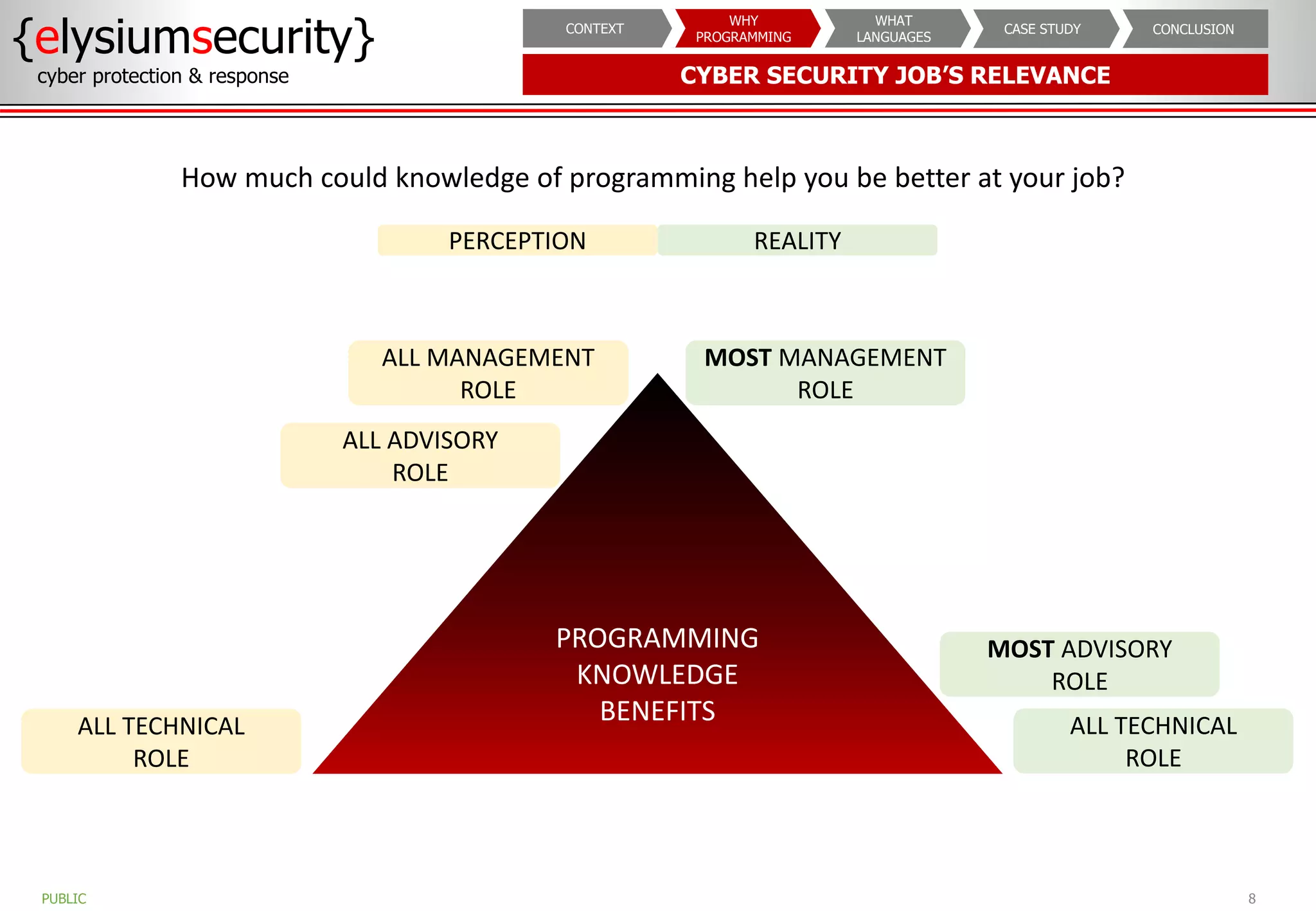
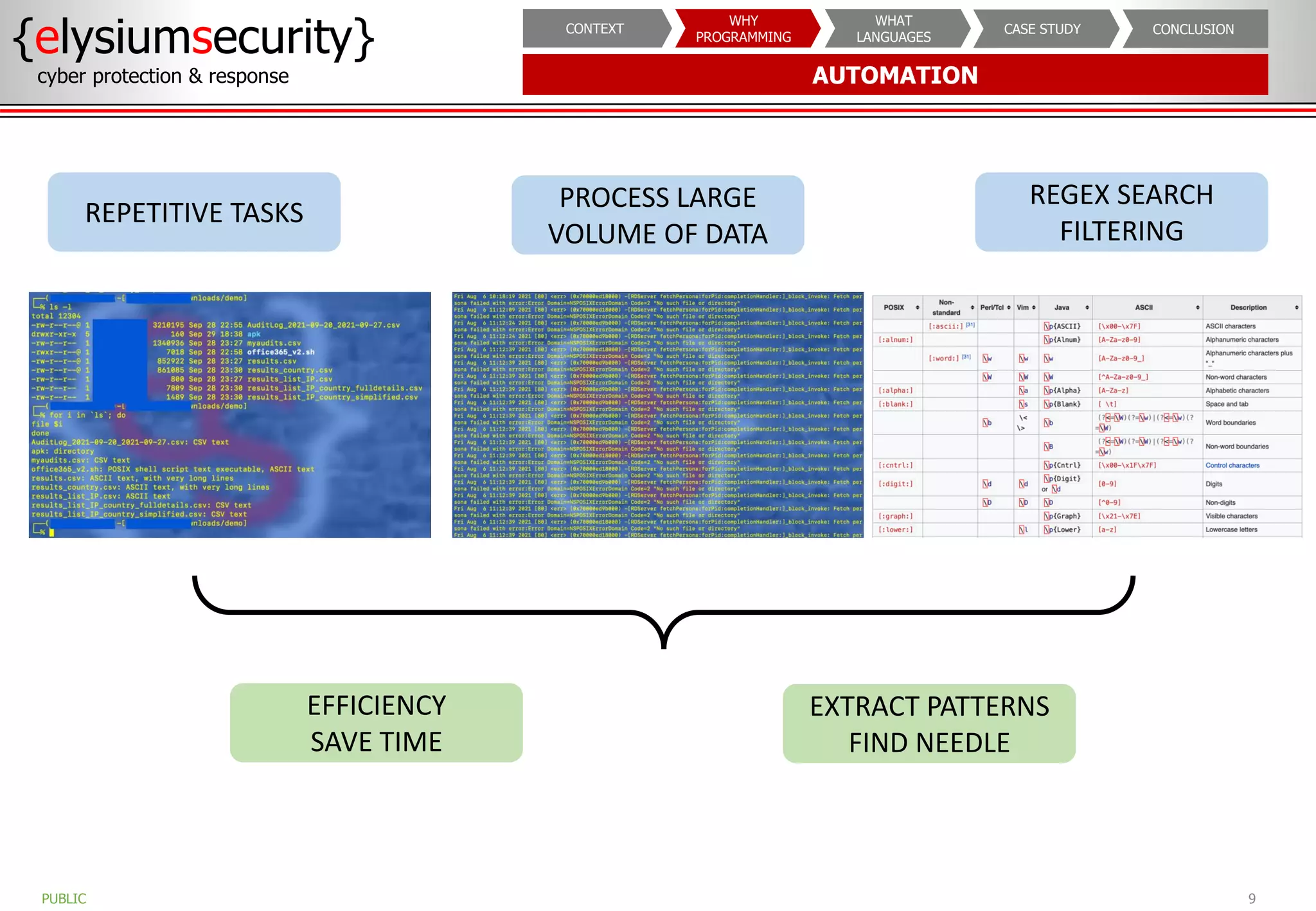
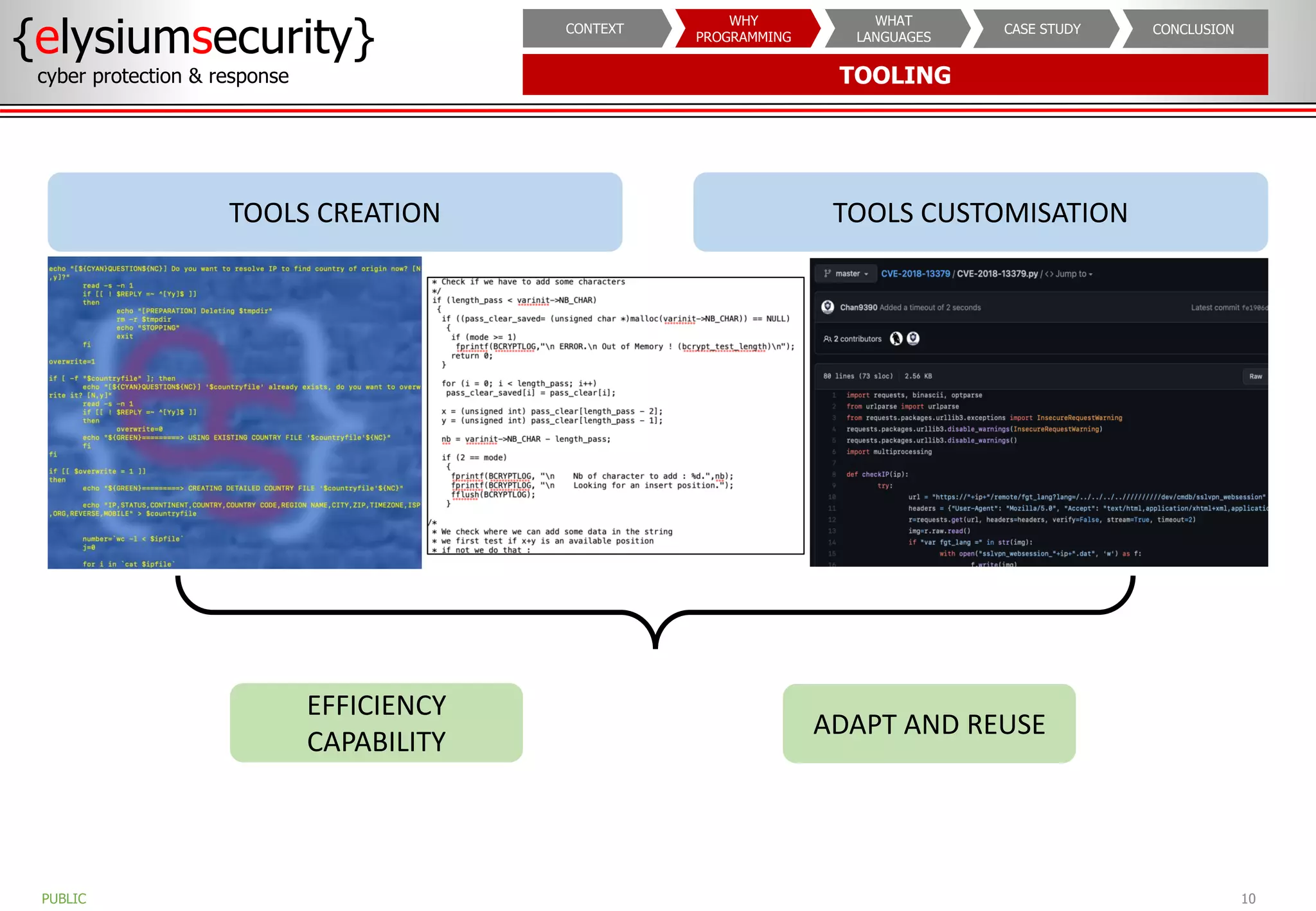
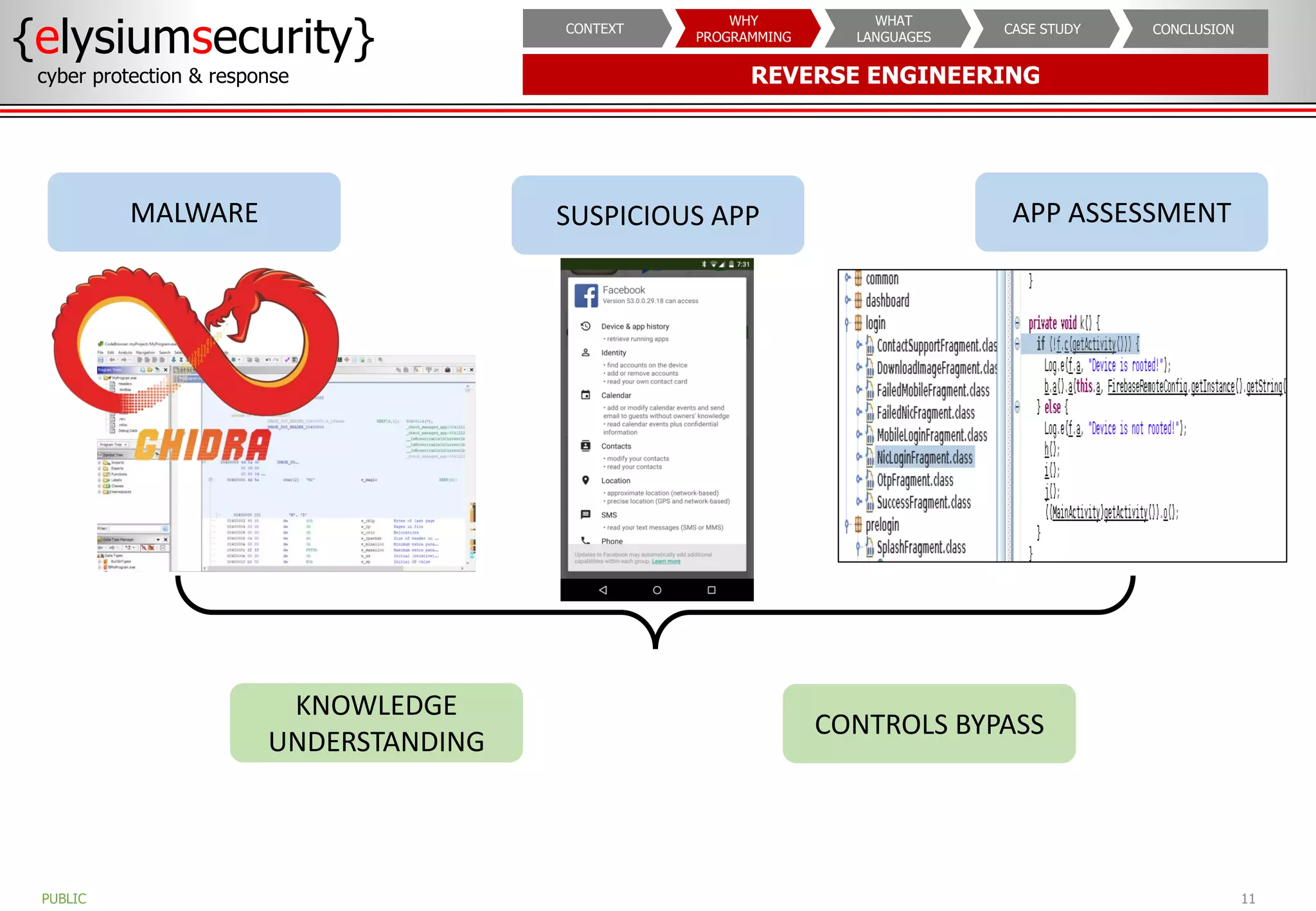
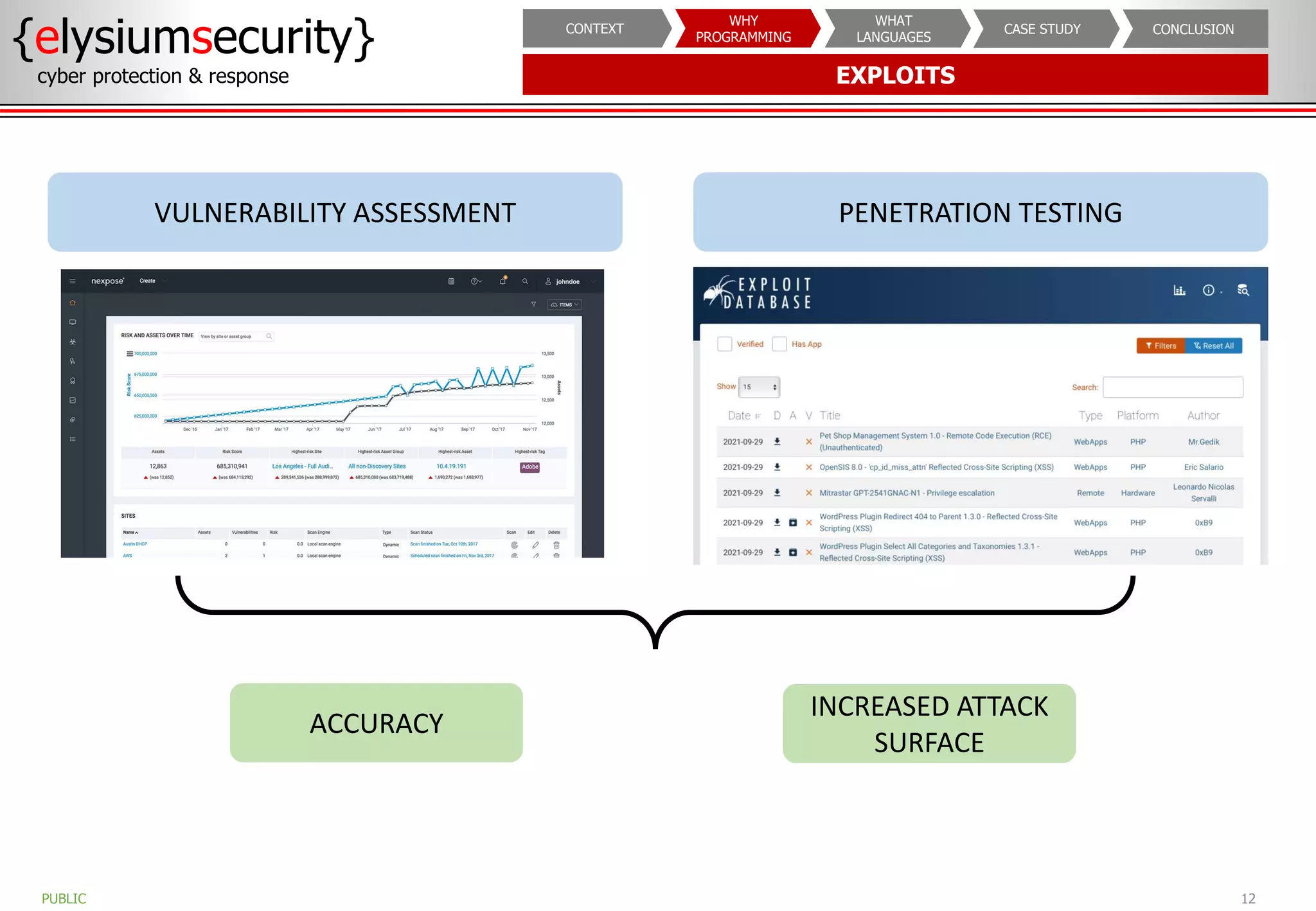
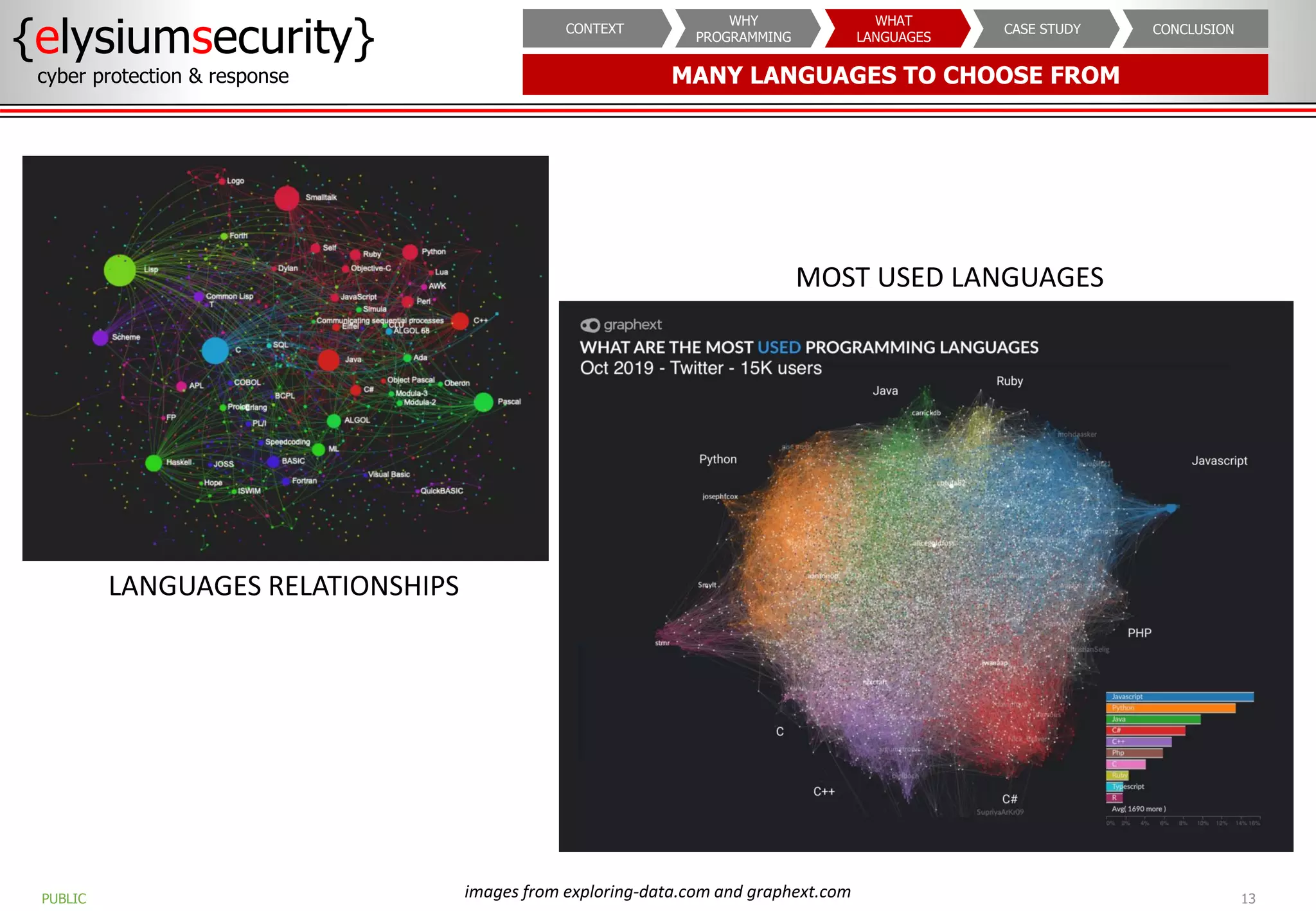
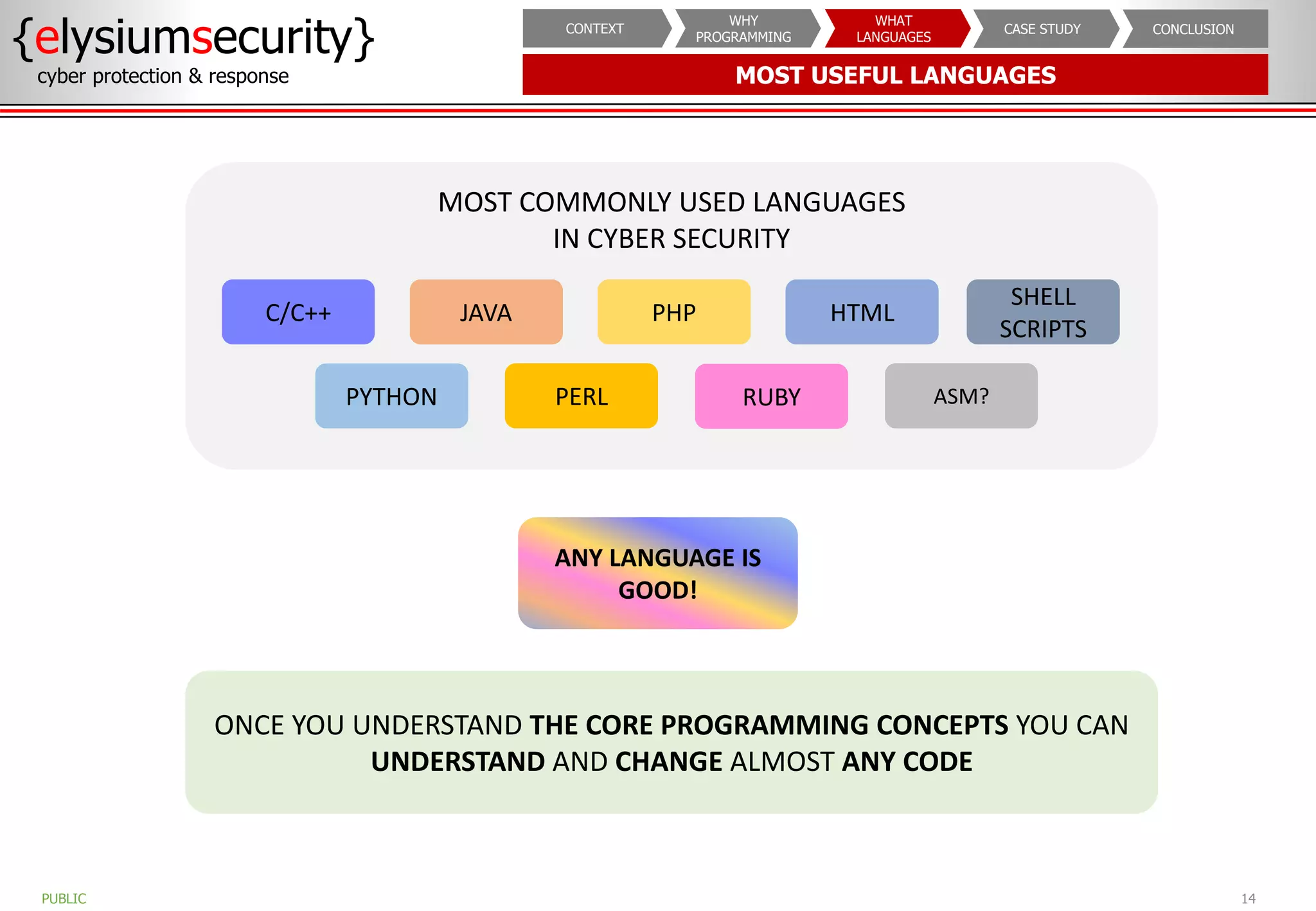
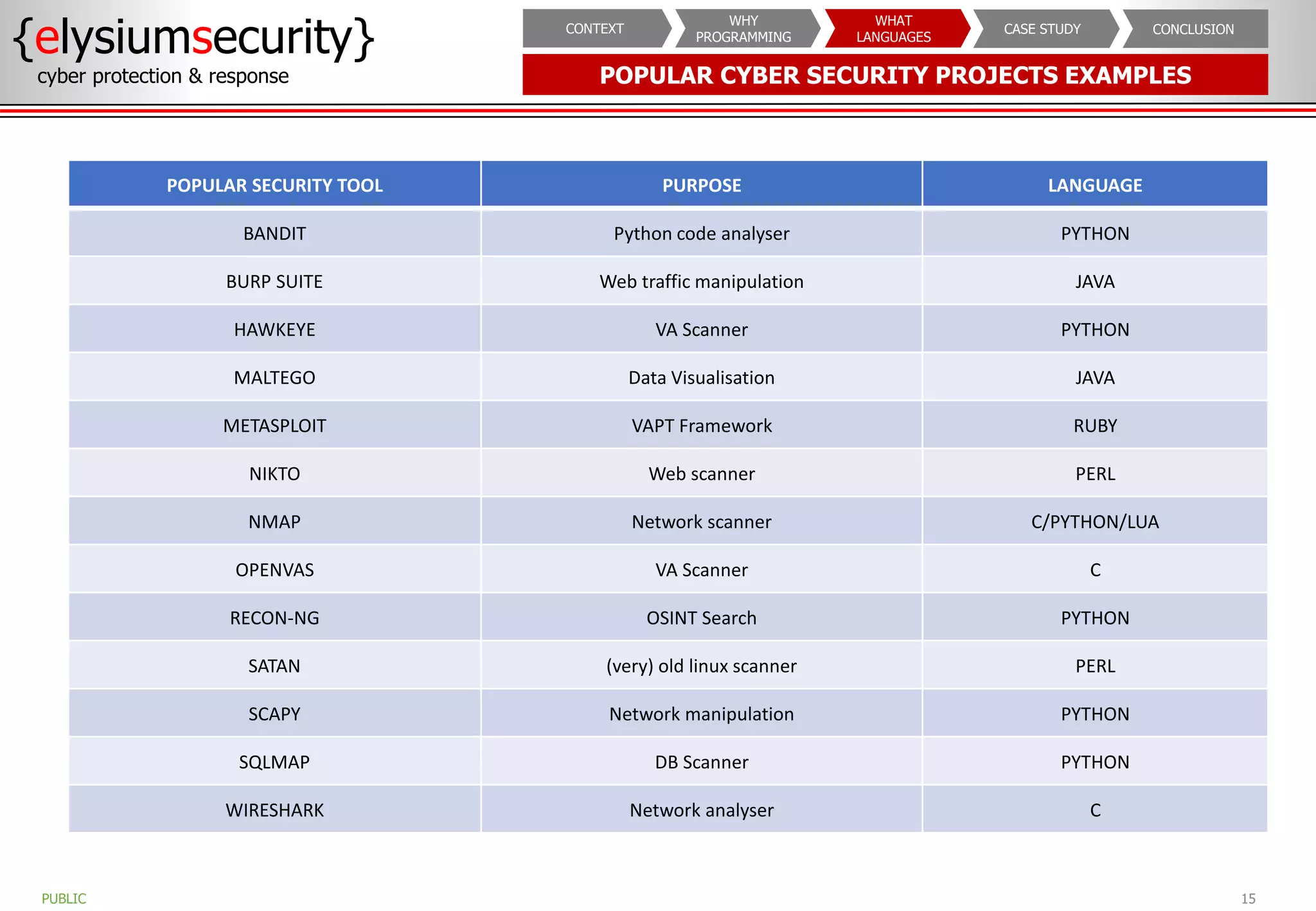
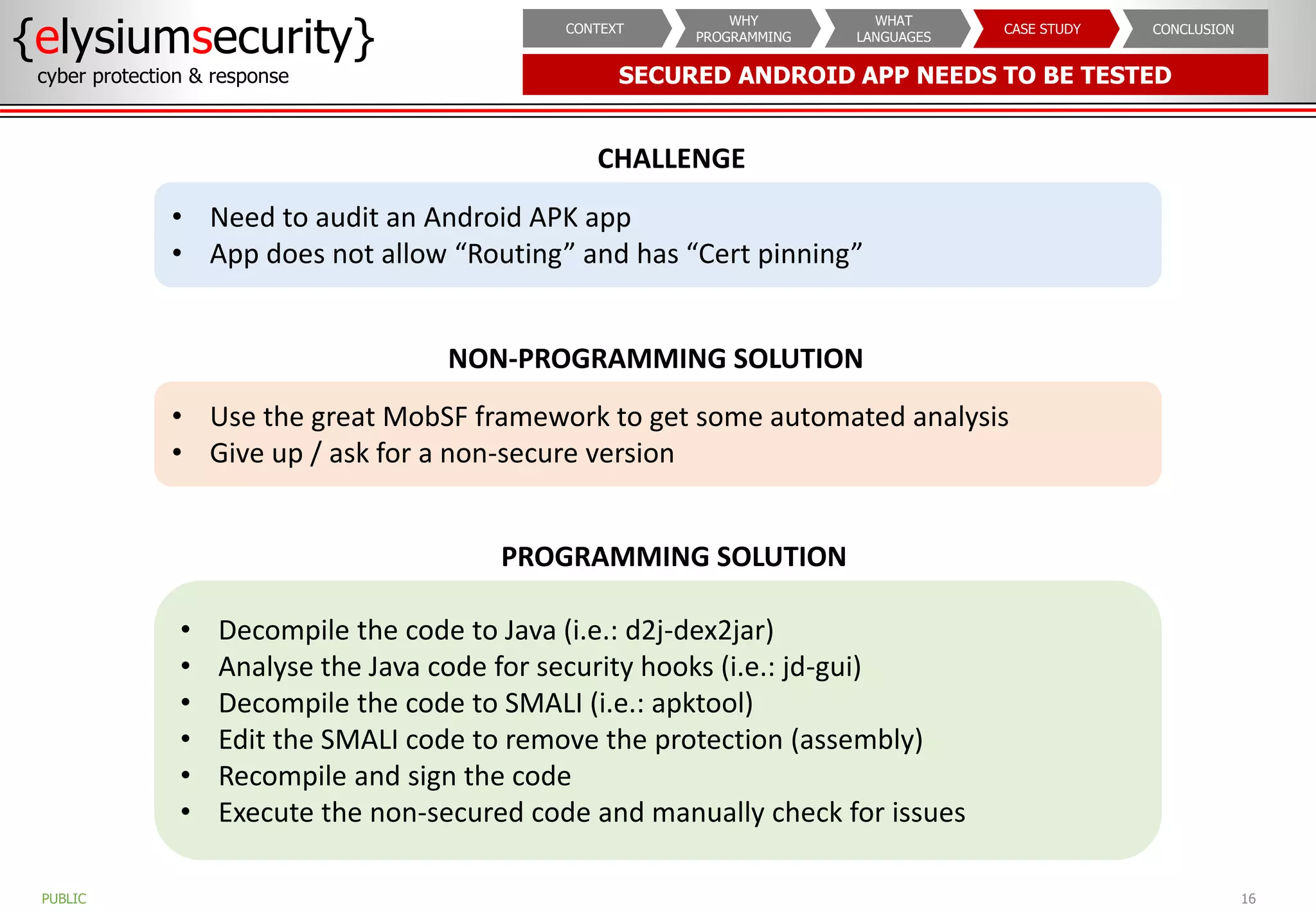
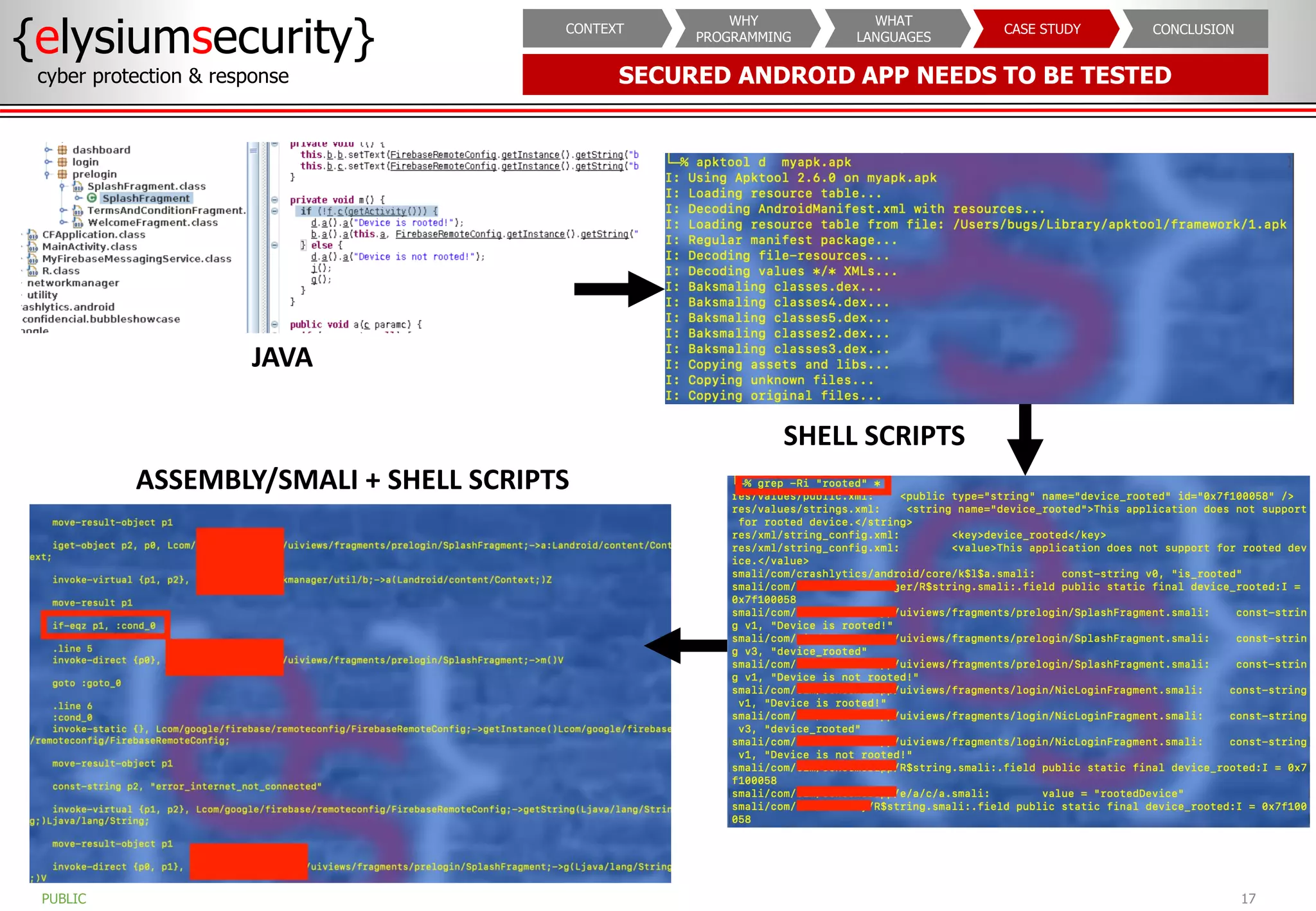
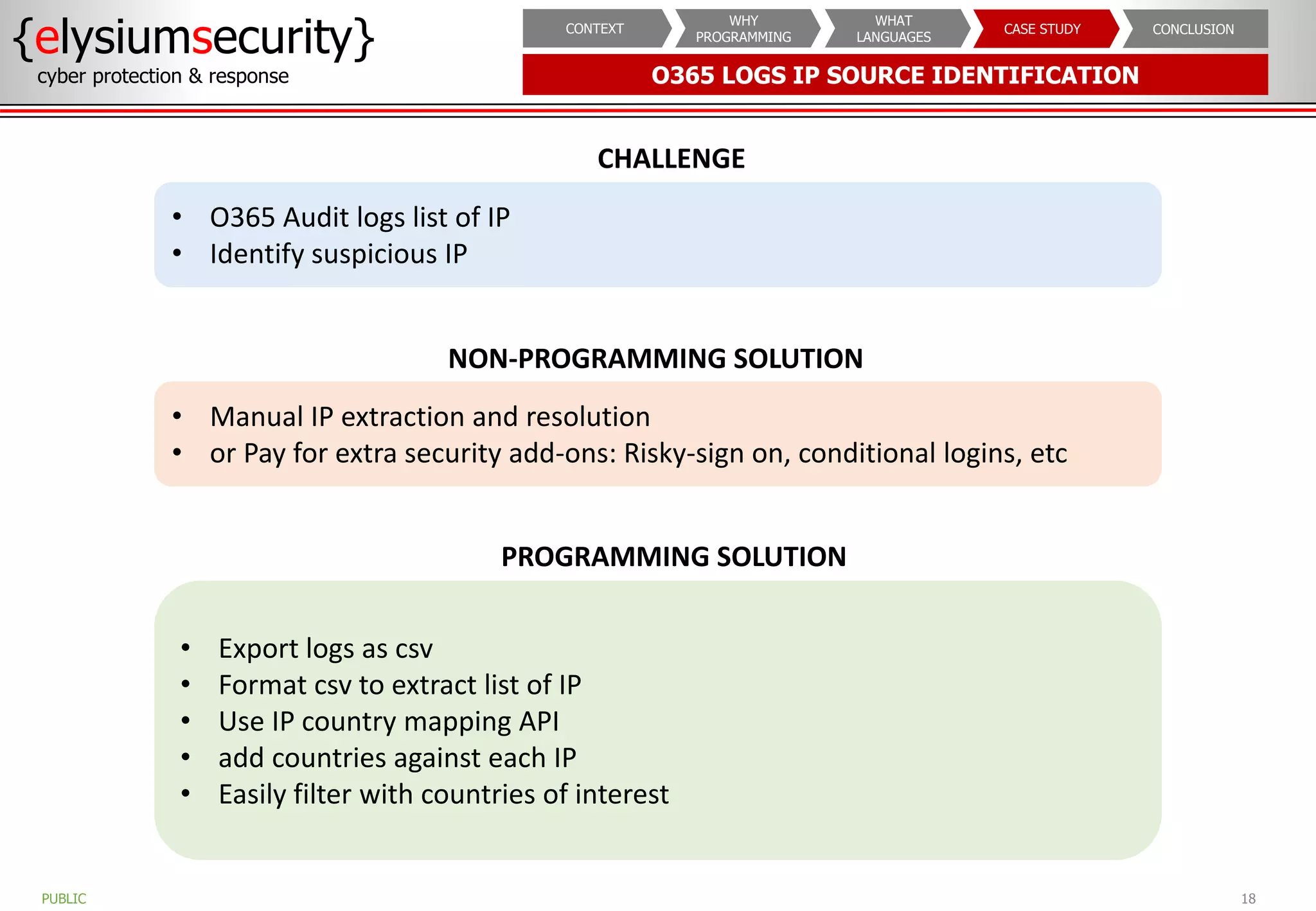
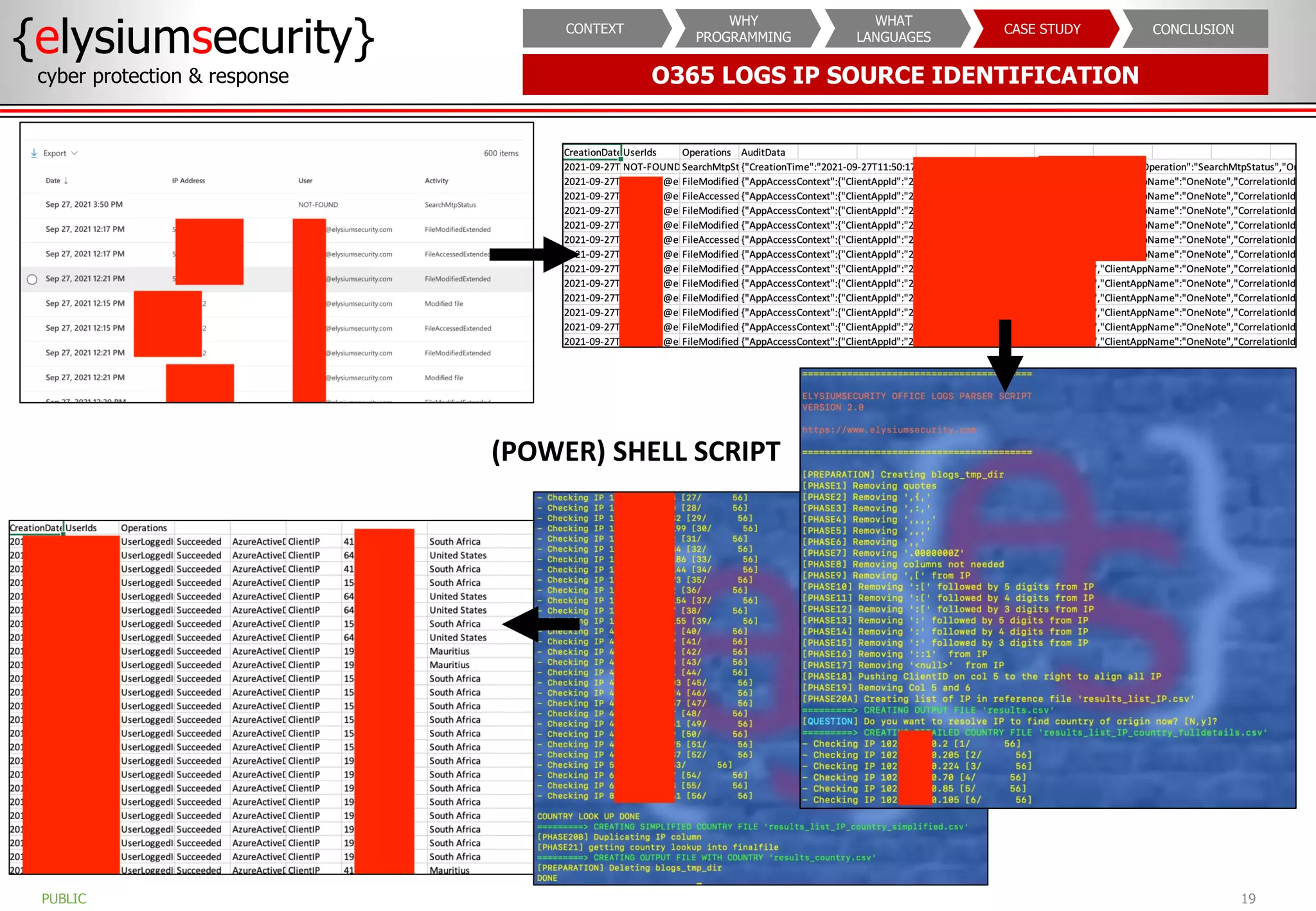
The document outlines the importance of programming knowledge in cybersecurity, highlighting how it aids in various roles from management to technical positions. It presents common programming languages used in the field, such as Python and Java, and emphasizes their utility in tasks like vulnerability assessments and automation of repetitive processes. Additionally, the document provides case studies illustrating programming applications in real-world cybersecurity scenarios.