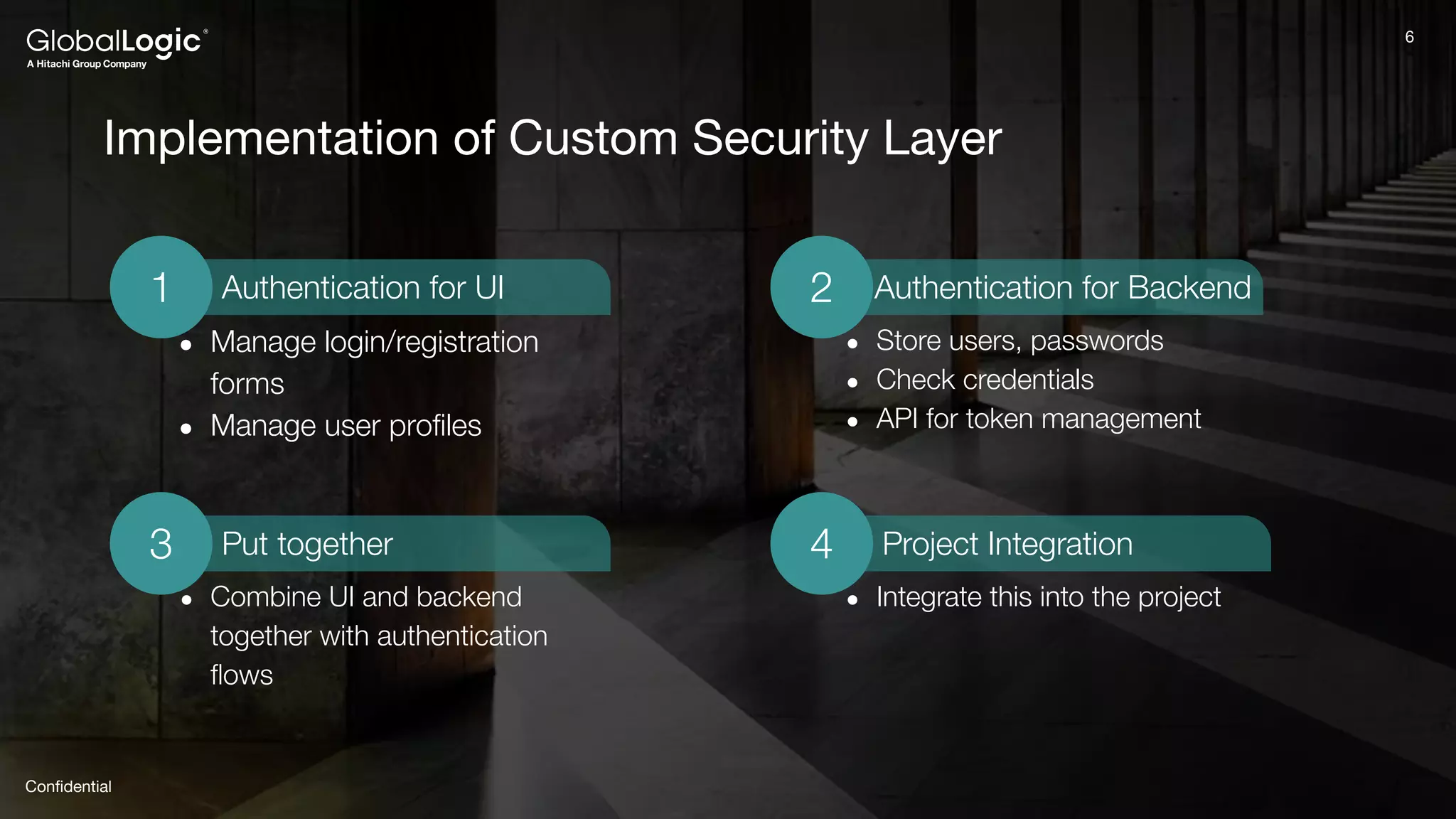
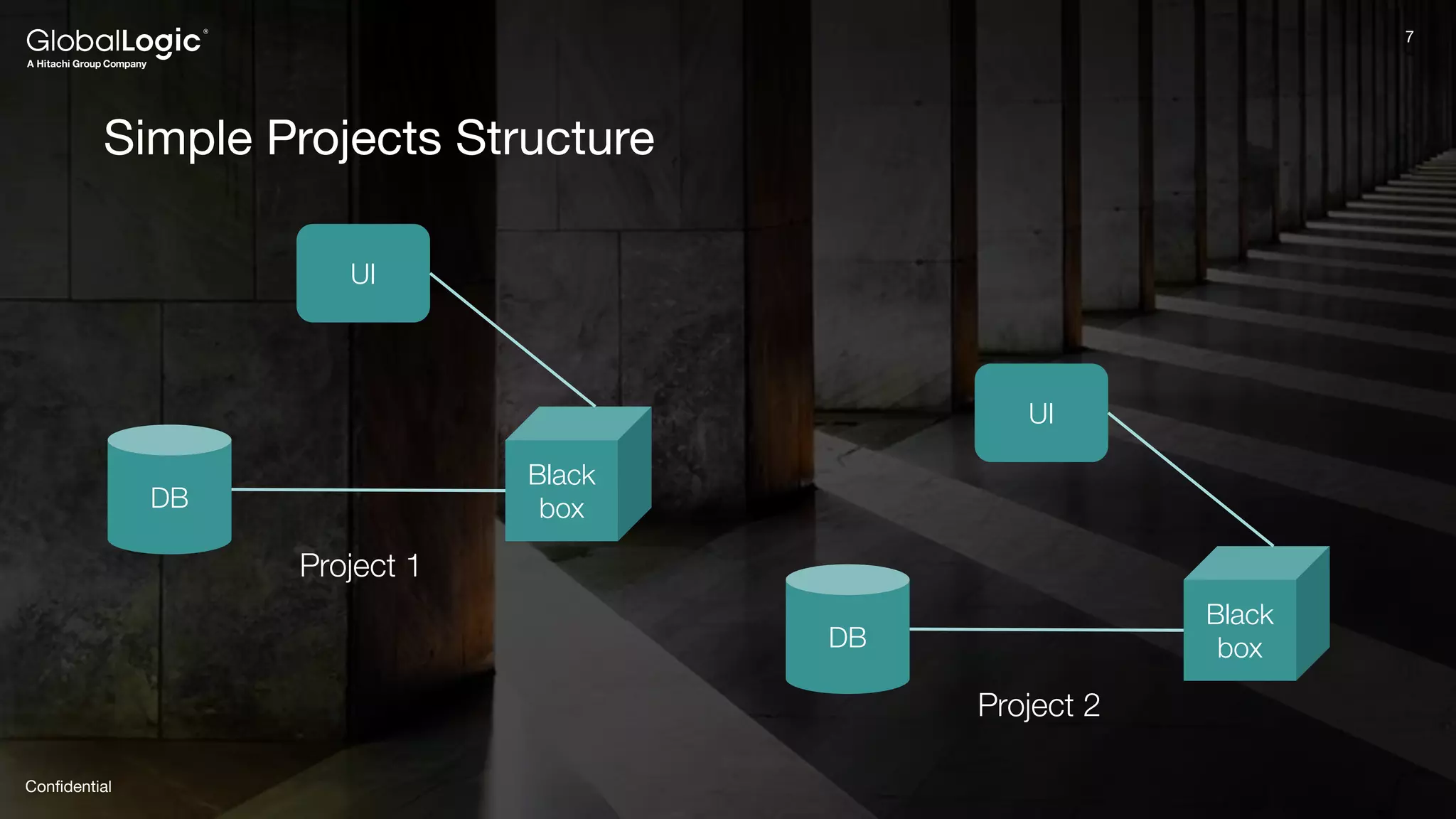
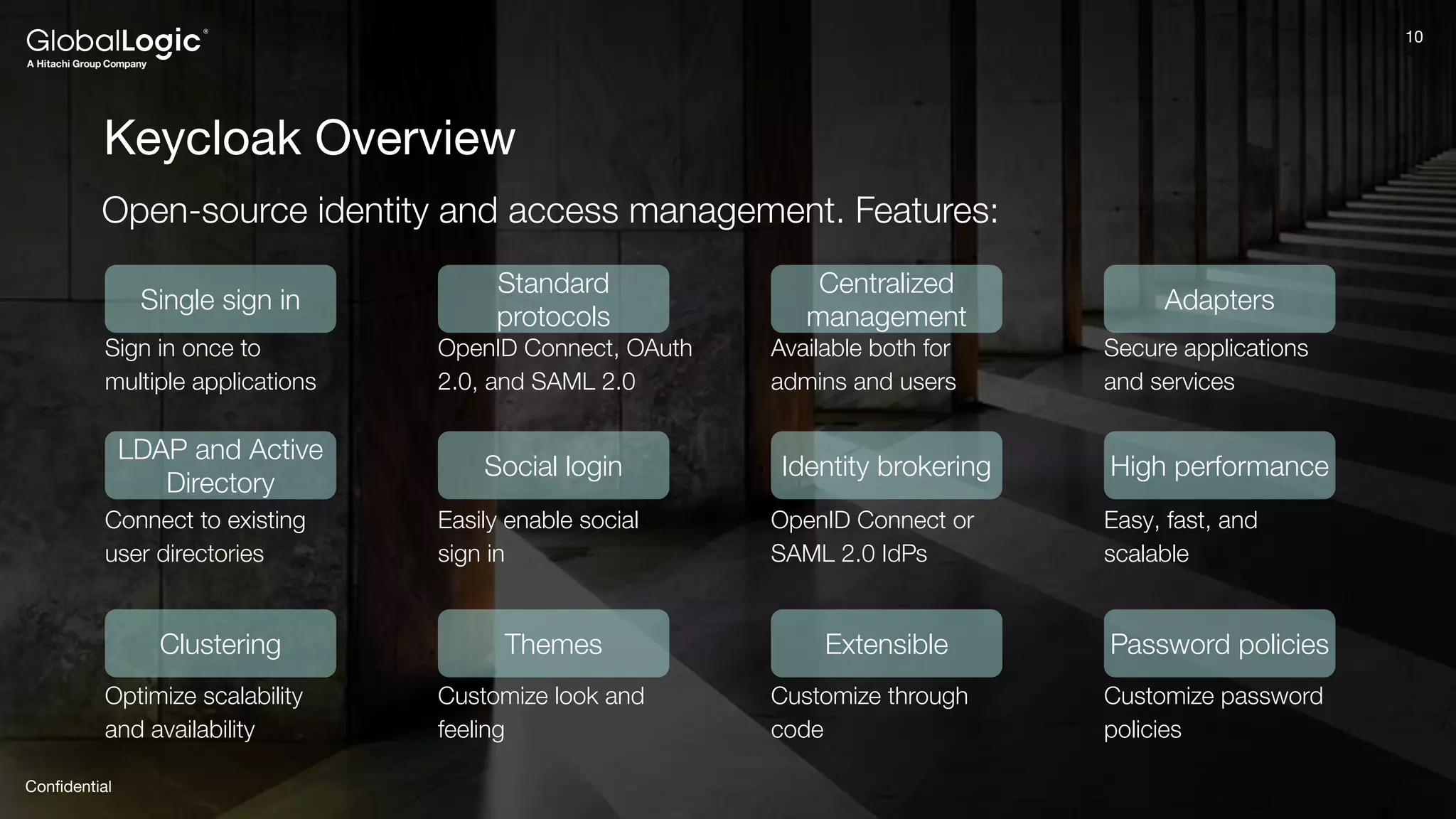
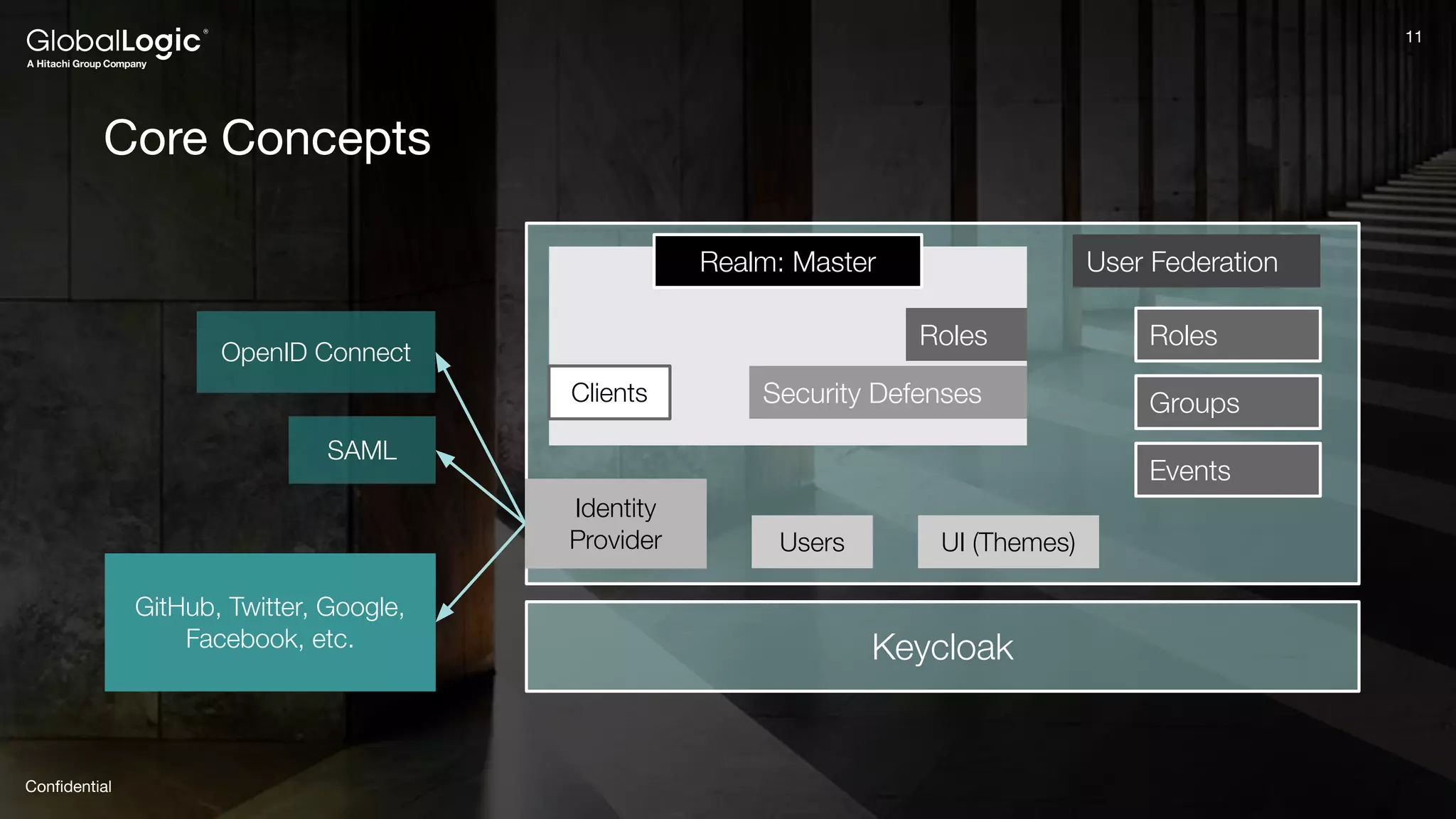
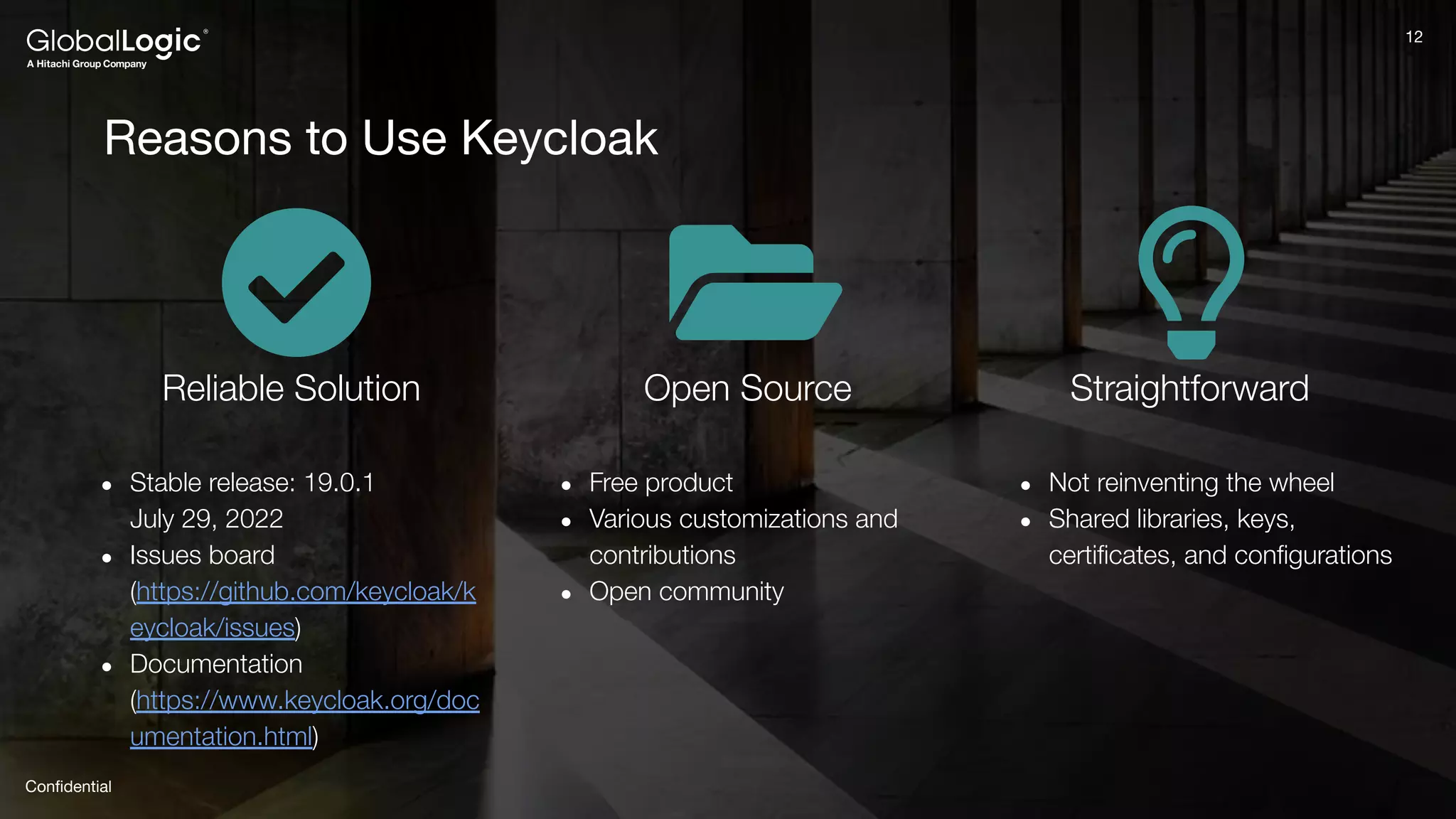
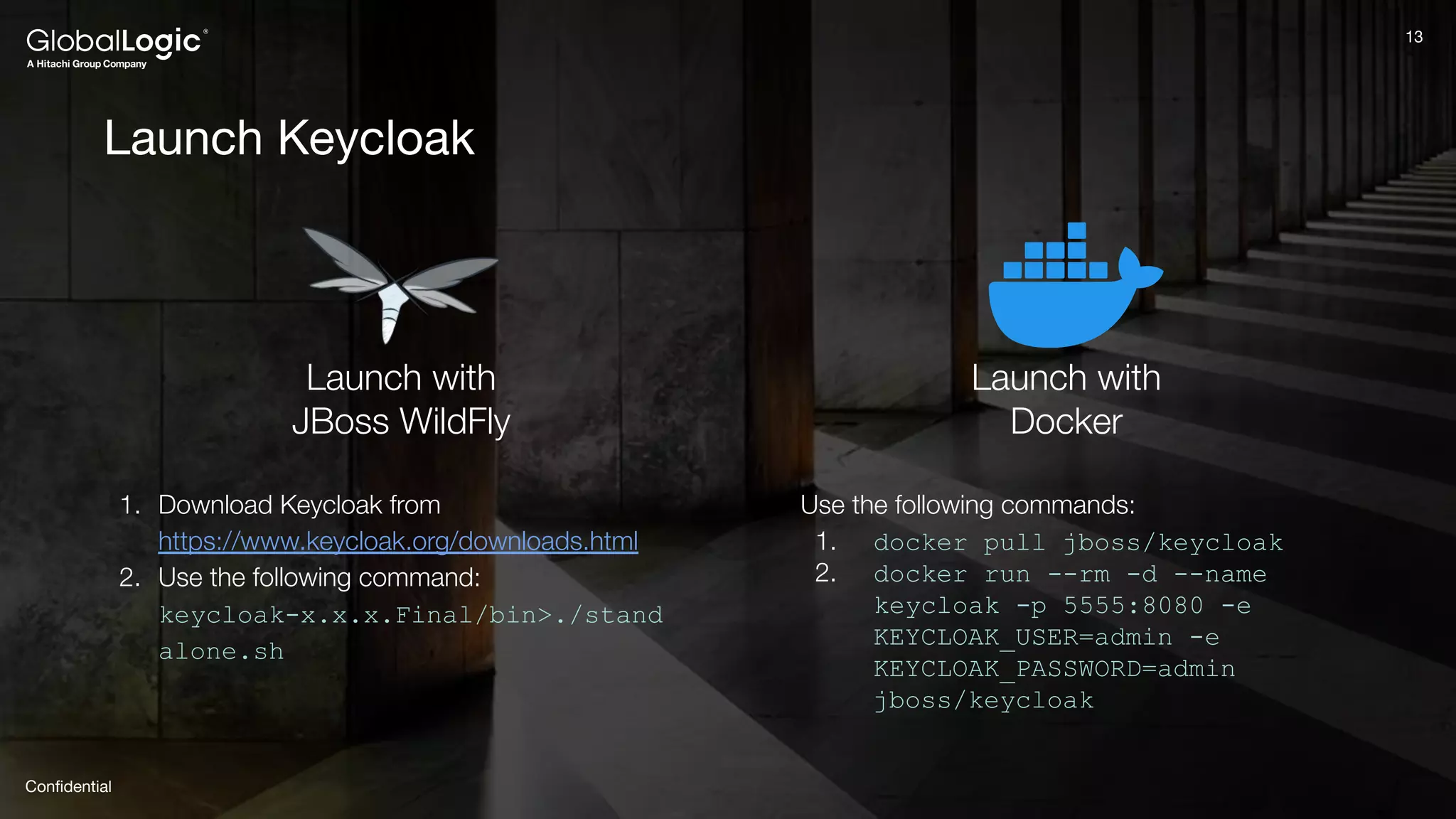
The document provides an overview of Keycloak, an open-source identity and access management solution, detailing its features such as single sign-on and integration capabilities. It outlines fundamental security principles and the process of implementing Keycloak in applications, highlighting its reliability and ease of use. Additionally, it emphasizes the importance of having a secure application framework and provides guidance on setting up Keycloak for various development environments.