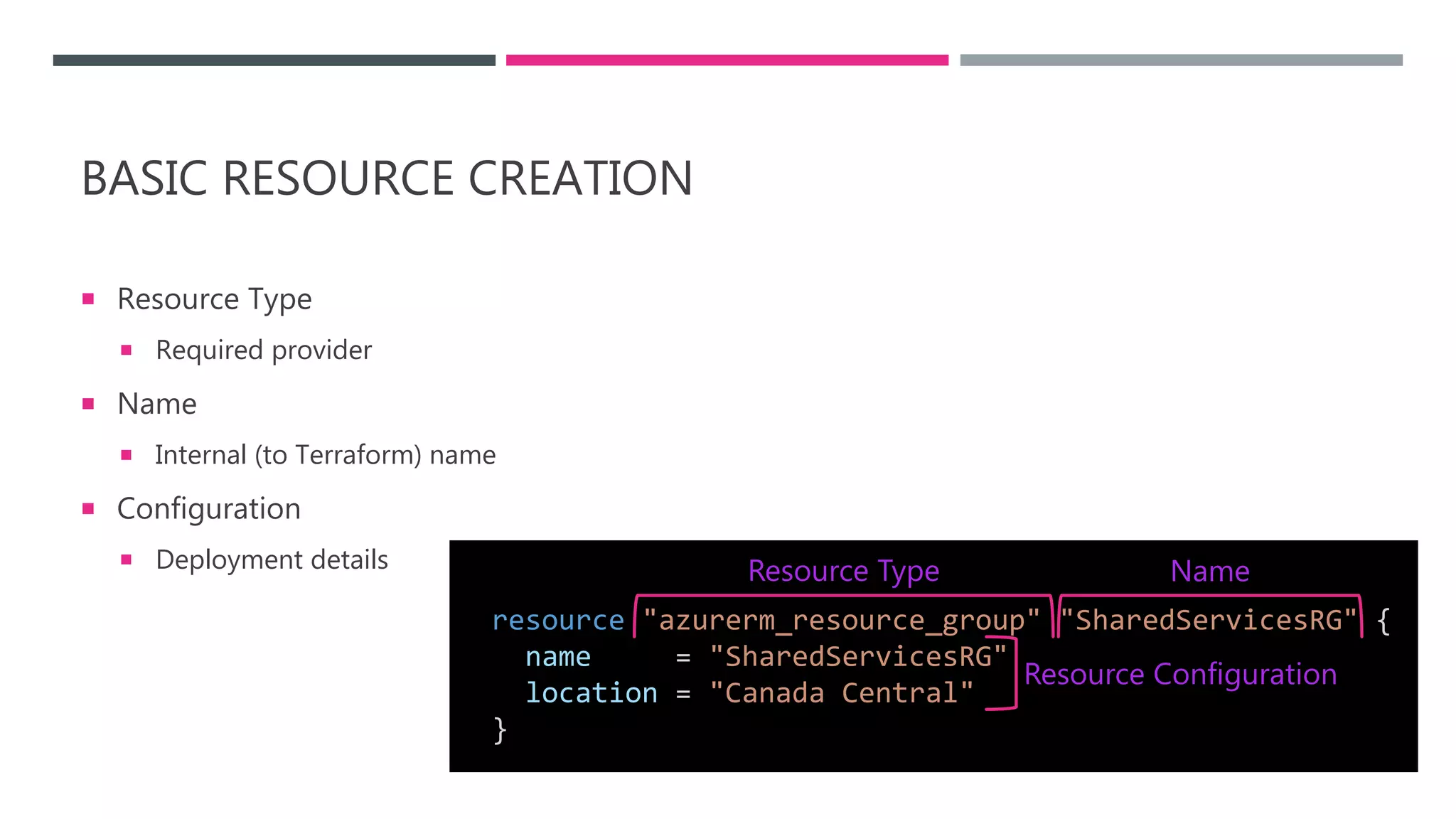
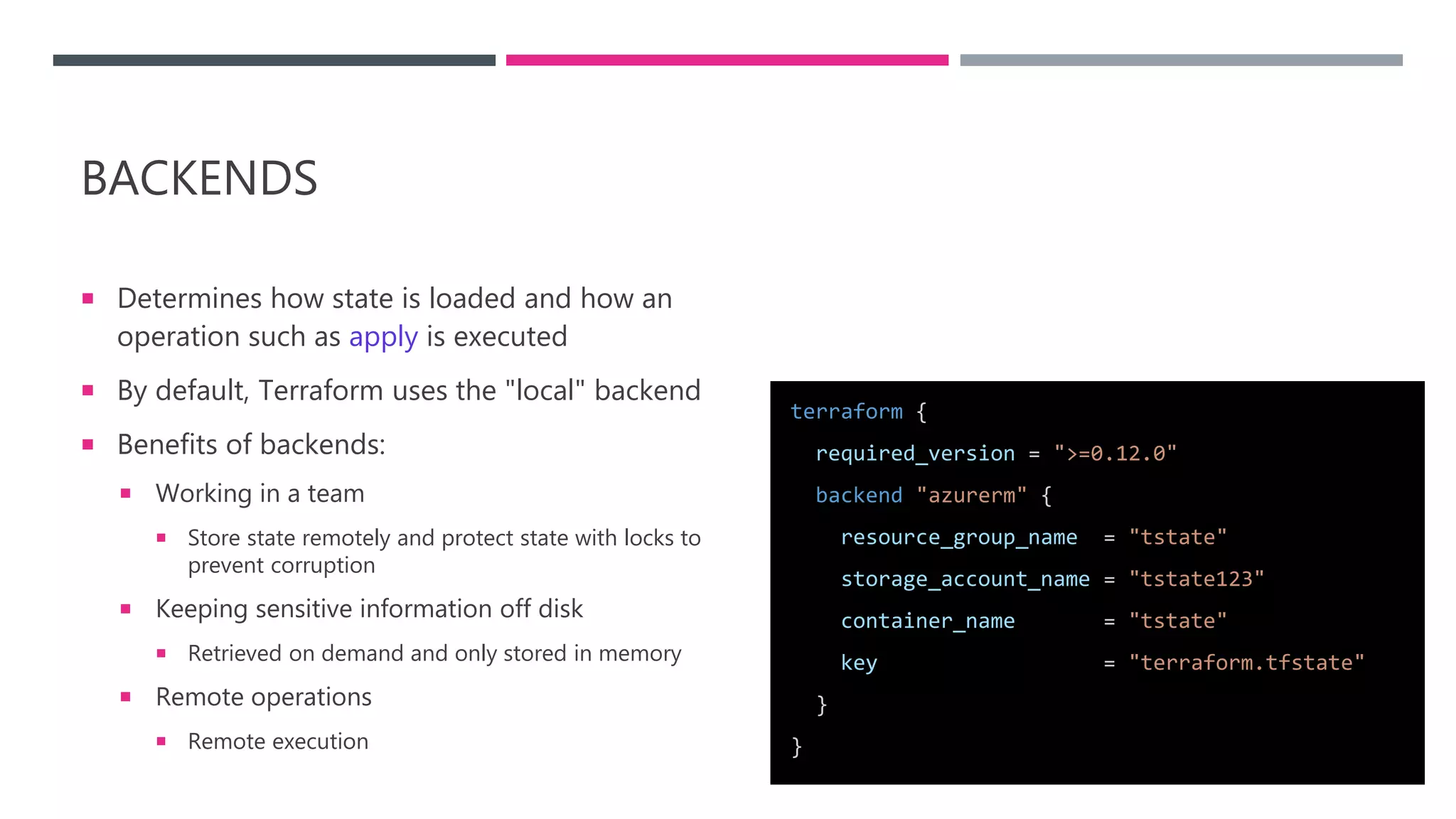
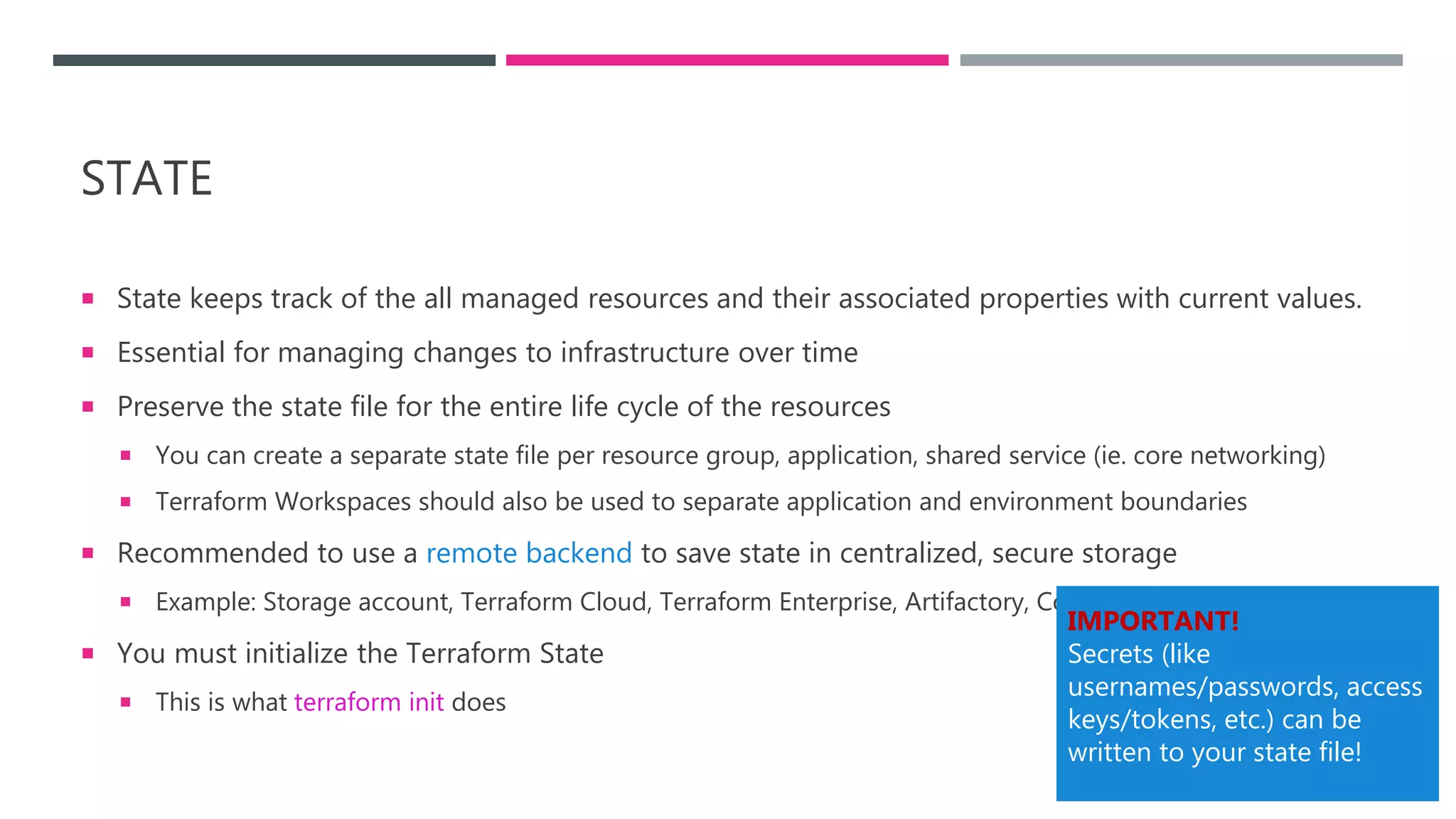
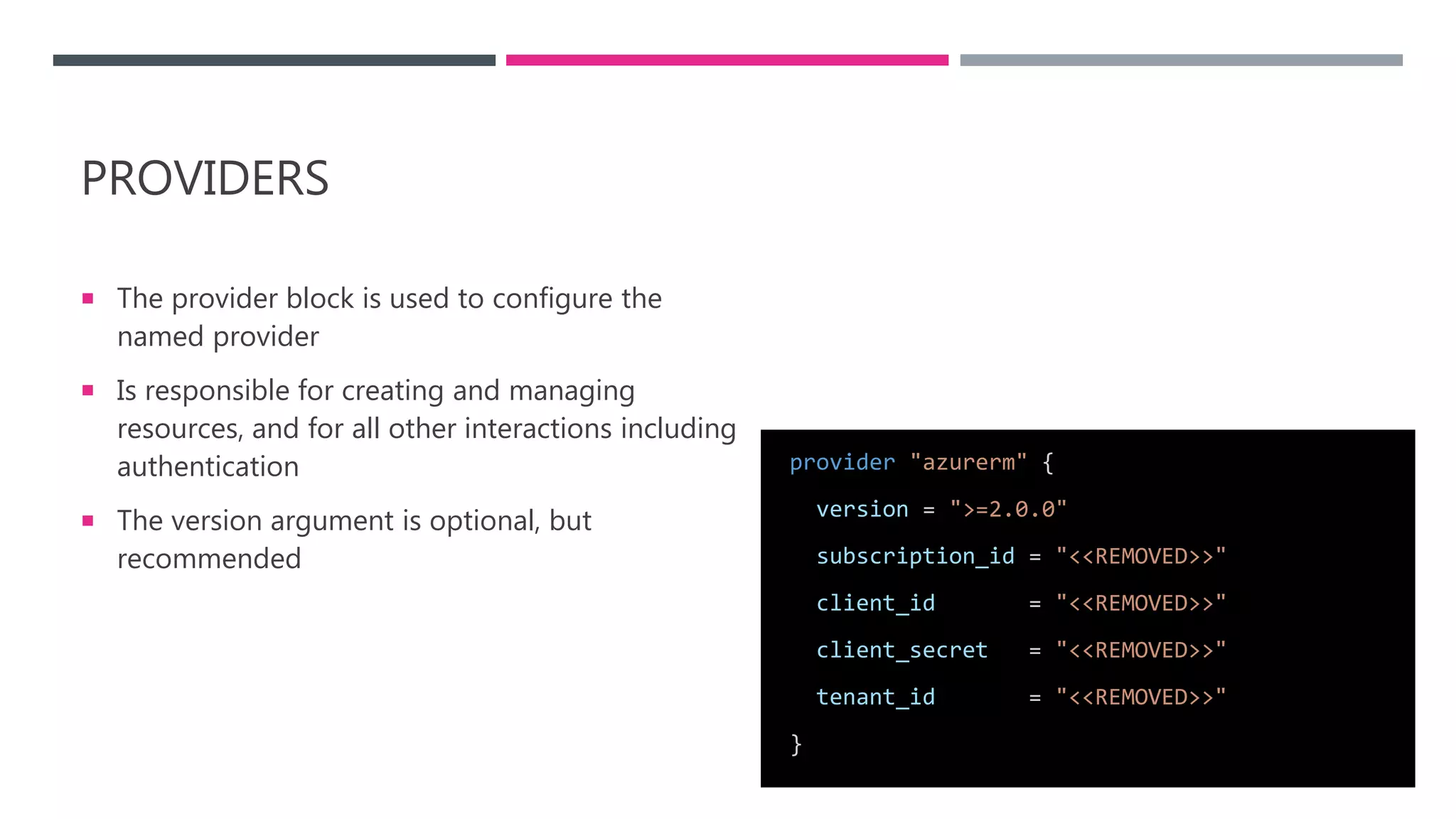
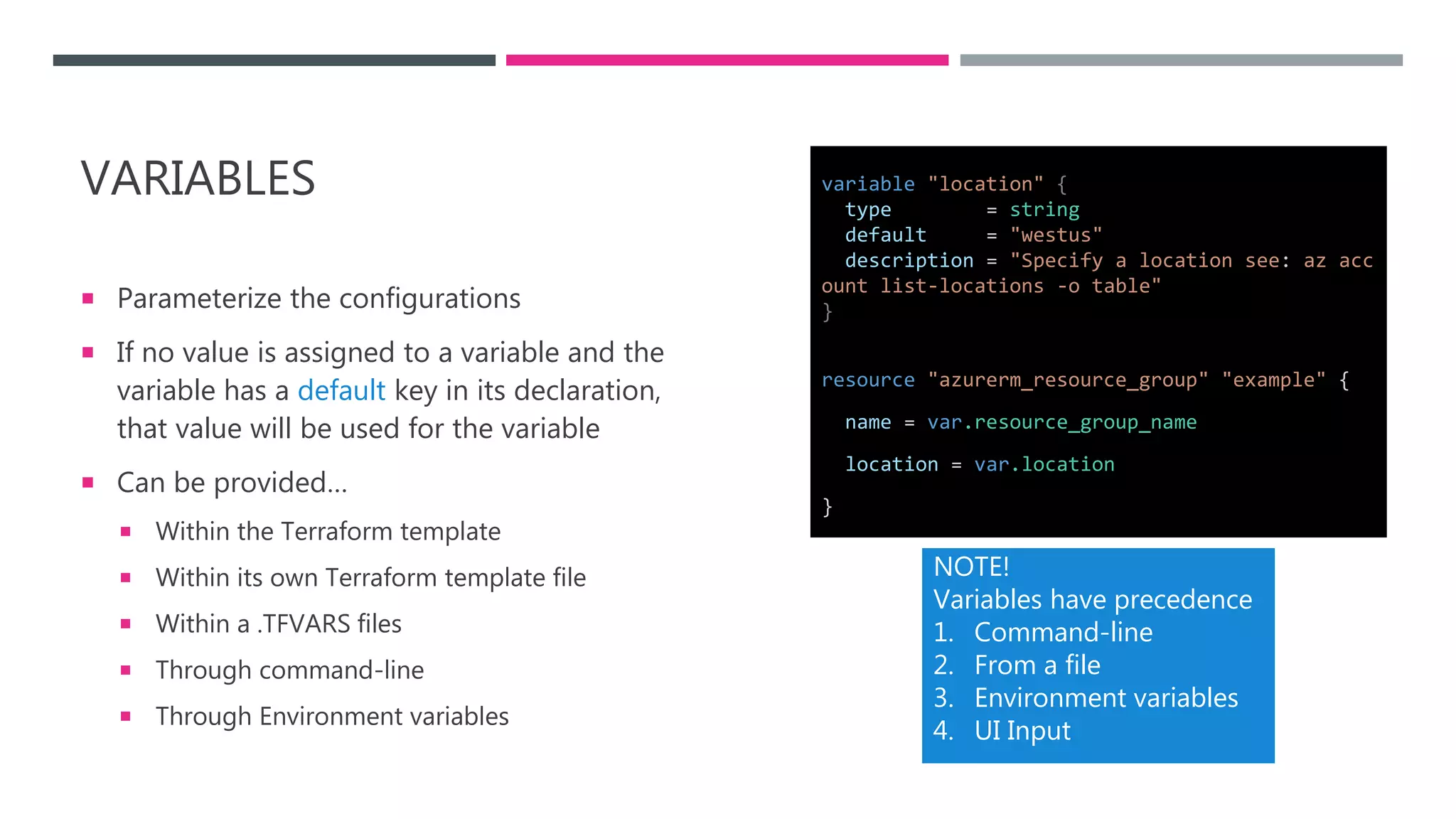
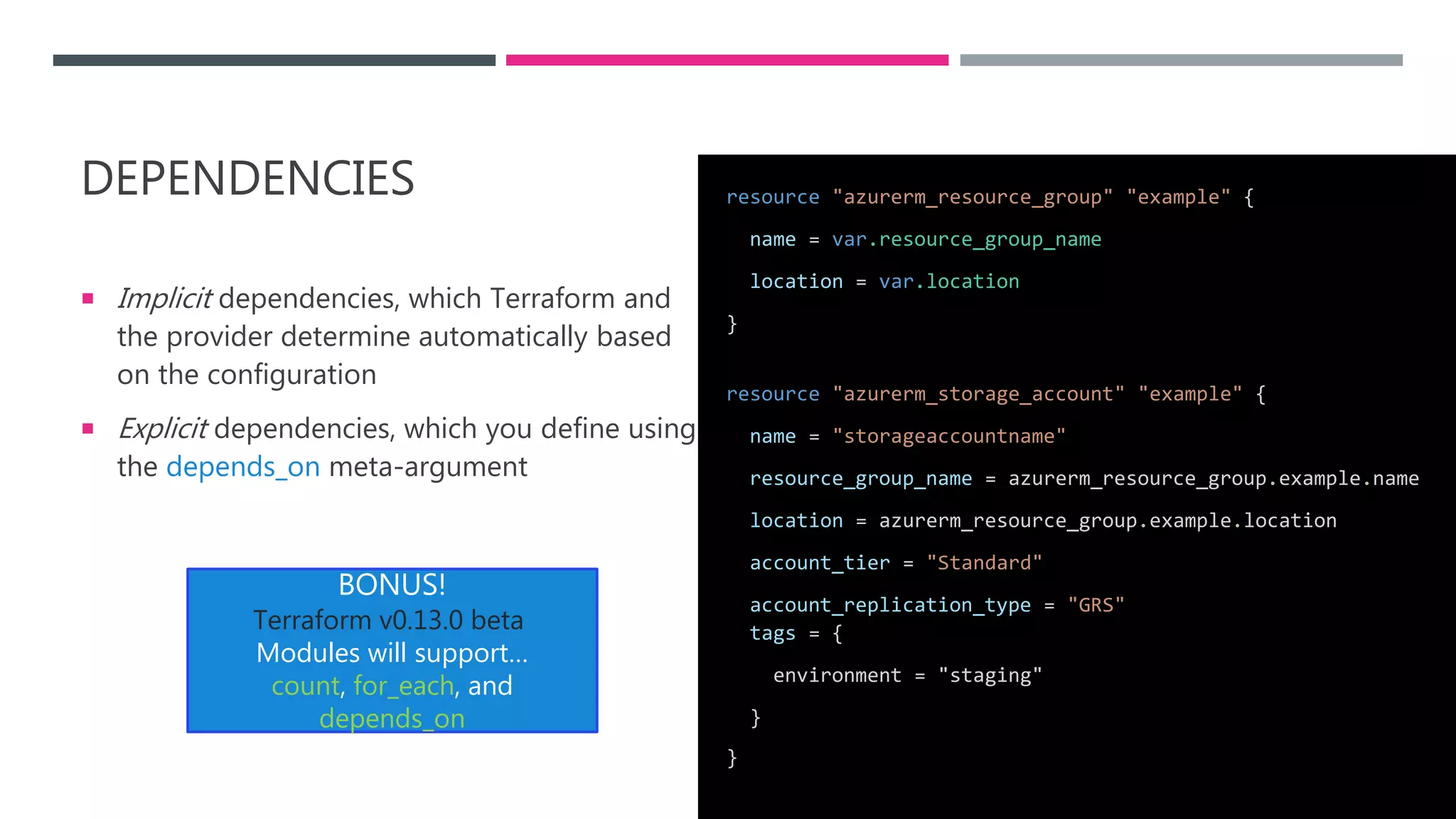
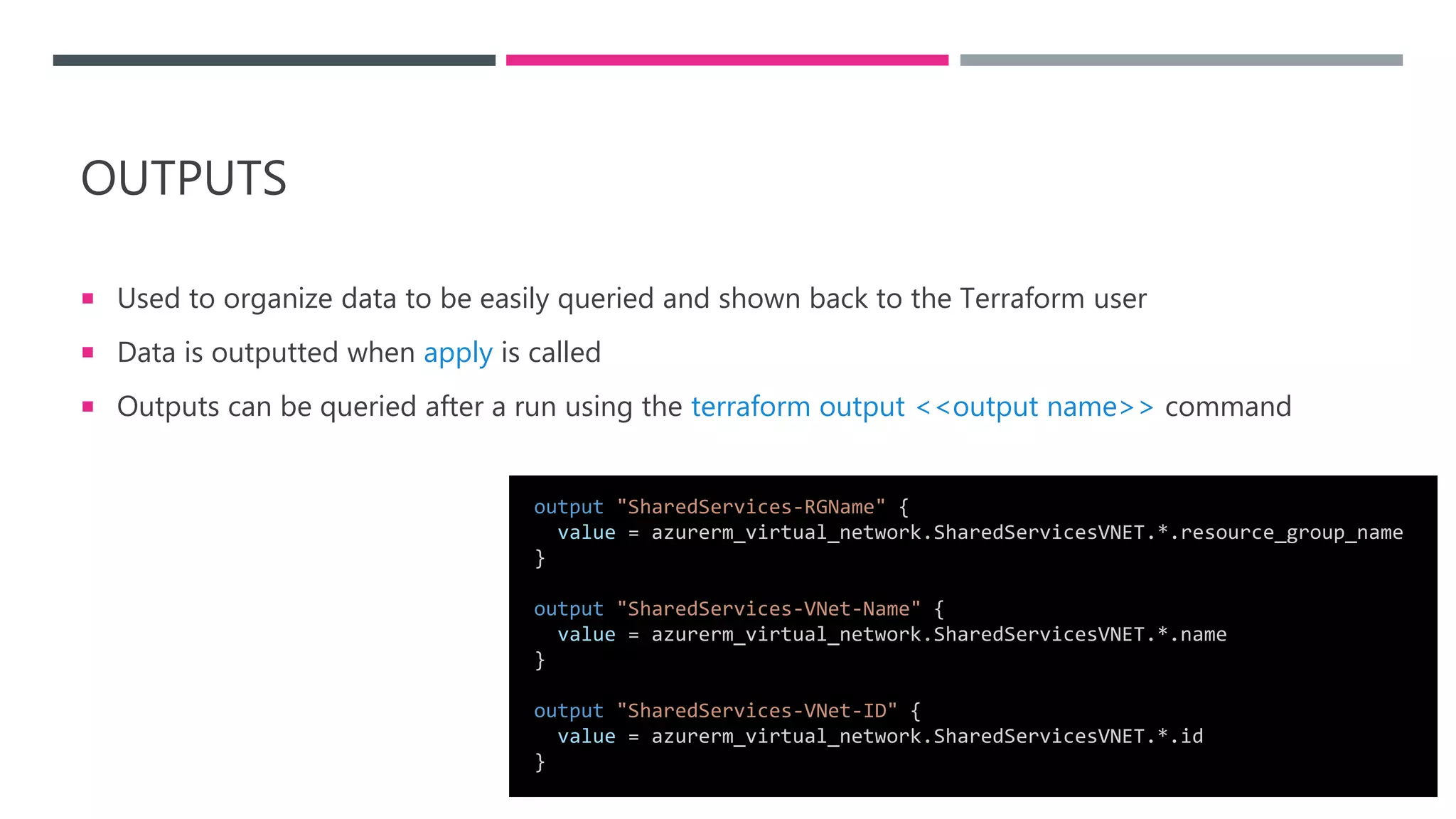
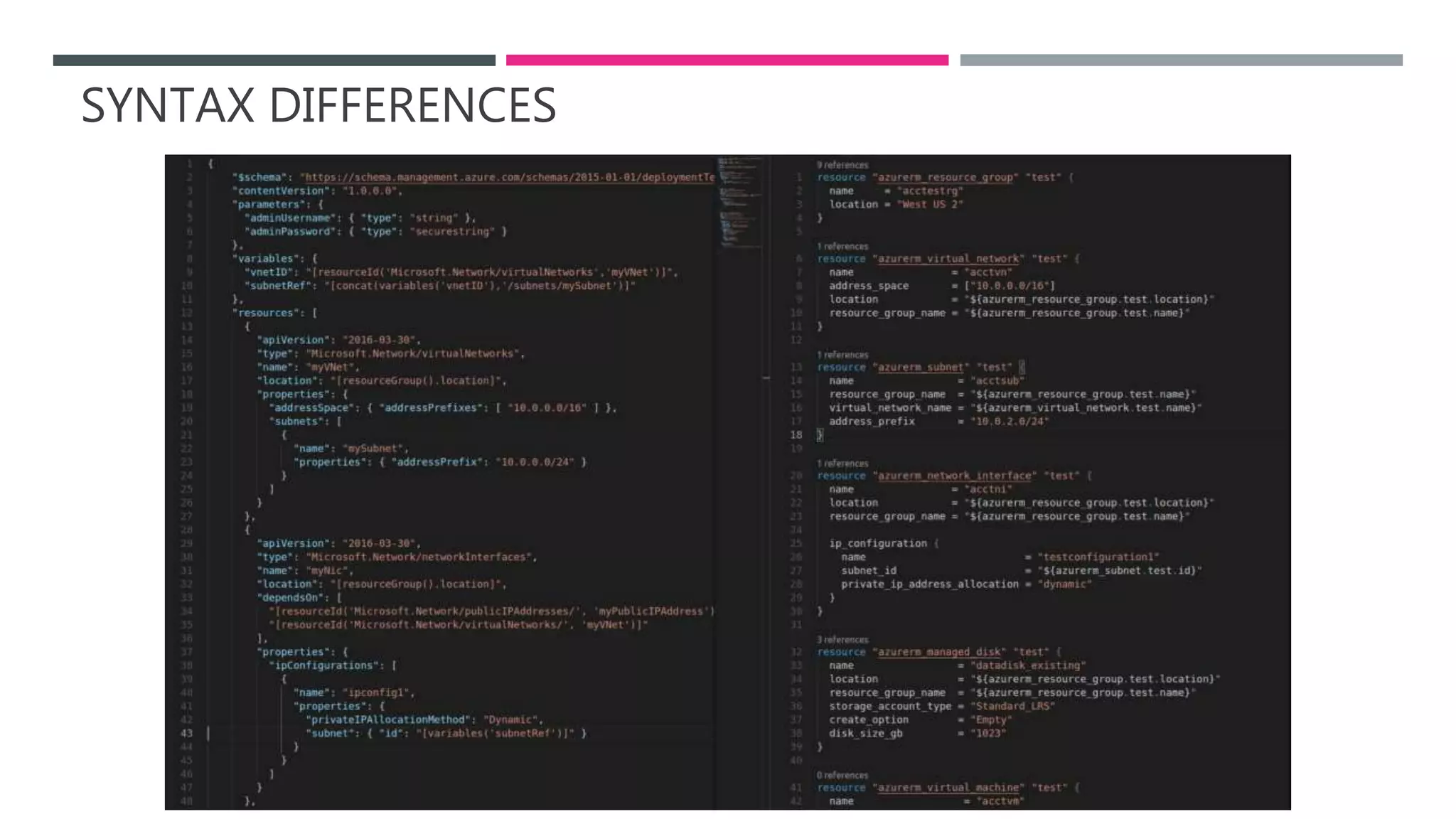
The document provides an introduction to Infrastructure as Code (IaC) using Terraform, highlighting its benefits like reproducible environments and automation. It covers the basics of Terraform, including commands, state management, resource configuration, and best practices for using Terraform with Azure. Additionally, it offers learning resources, certification guidance, and comparisons between Terraform and Azure Resource Manager (ARM).