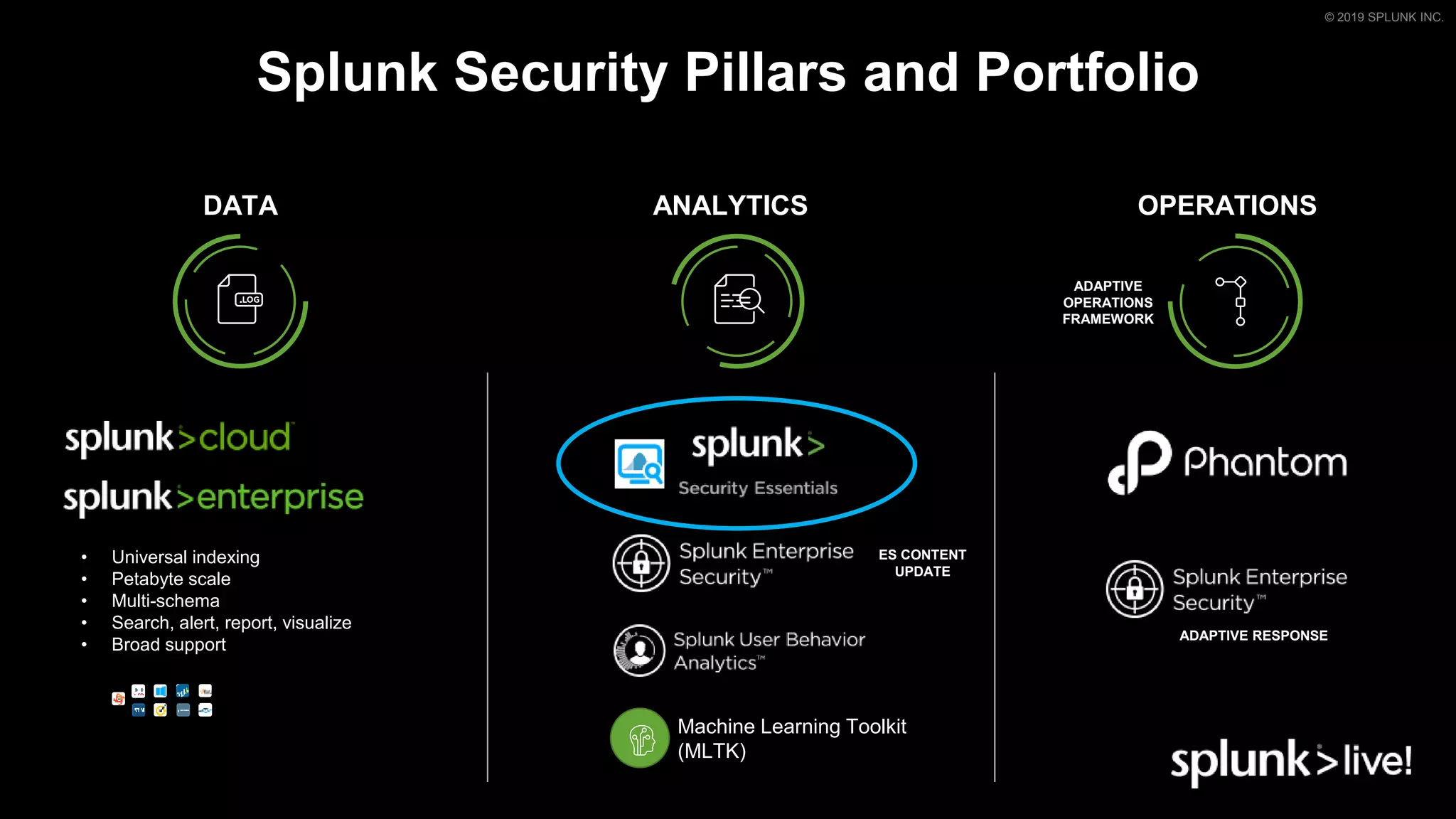
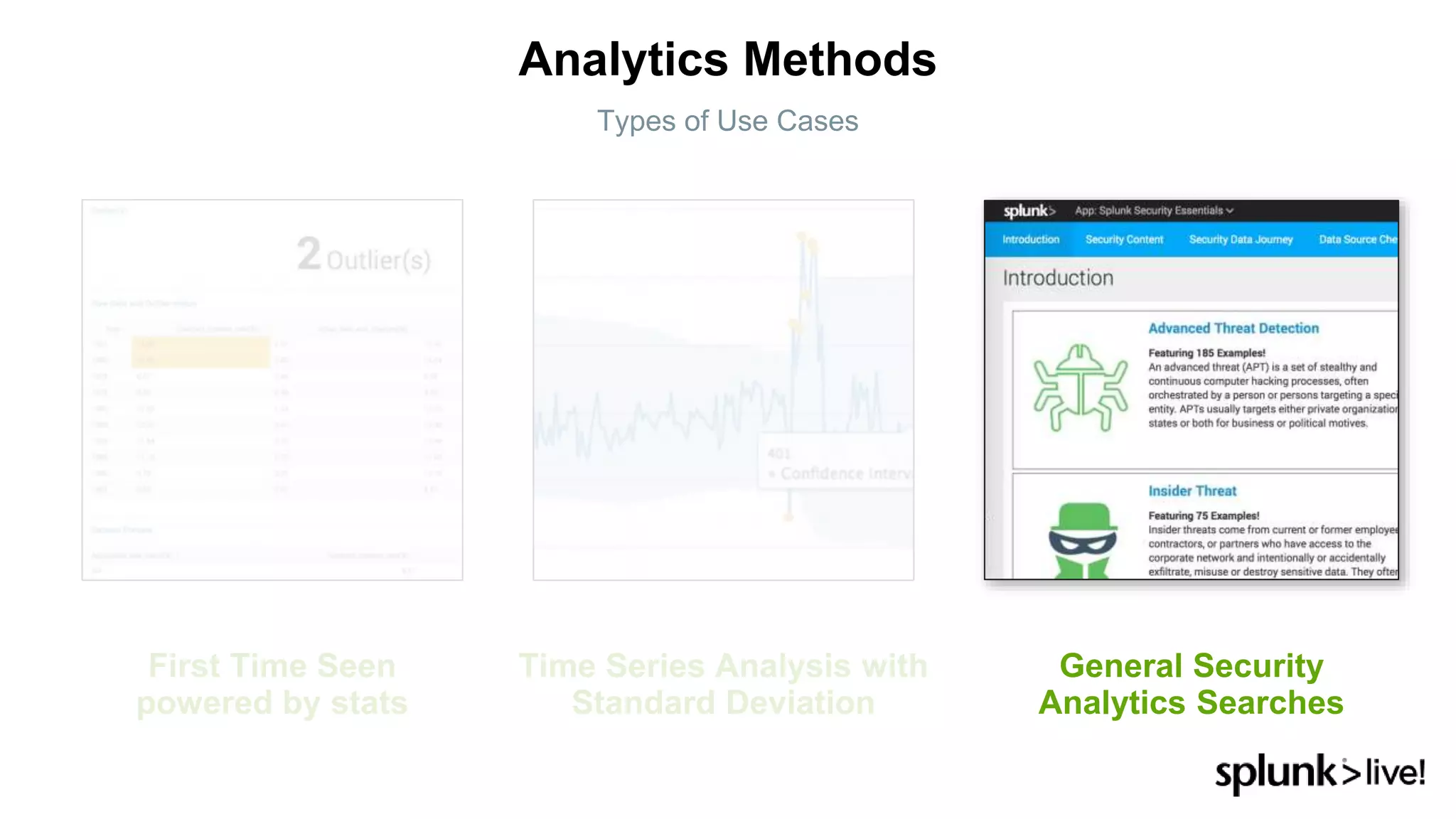
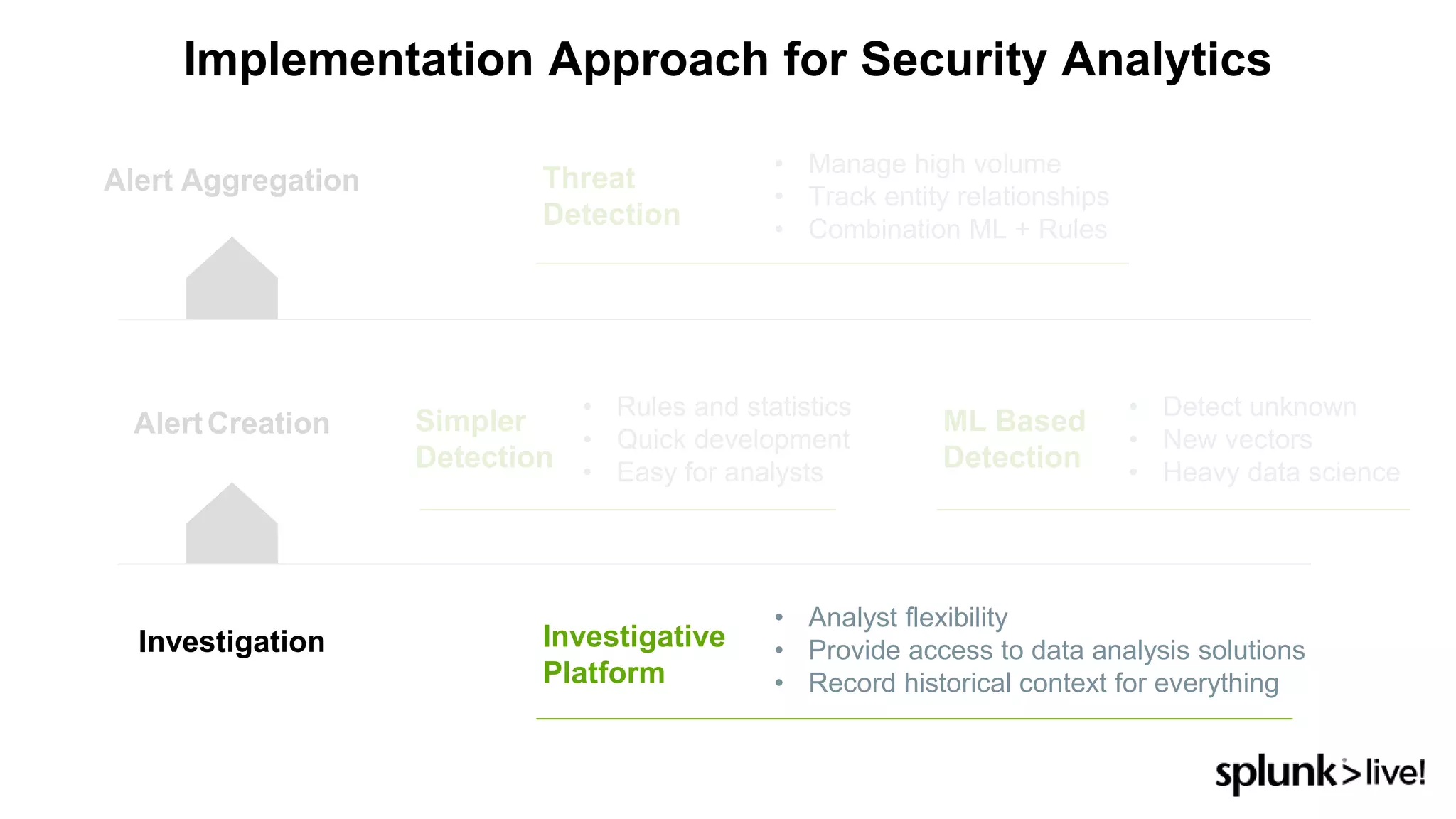
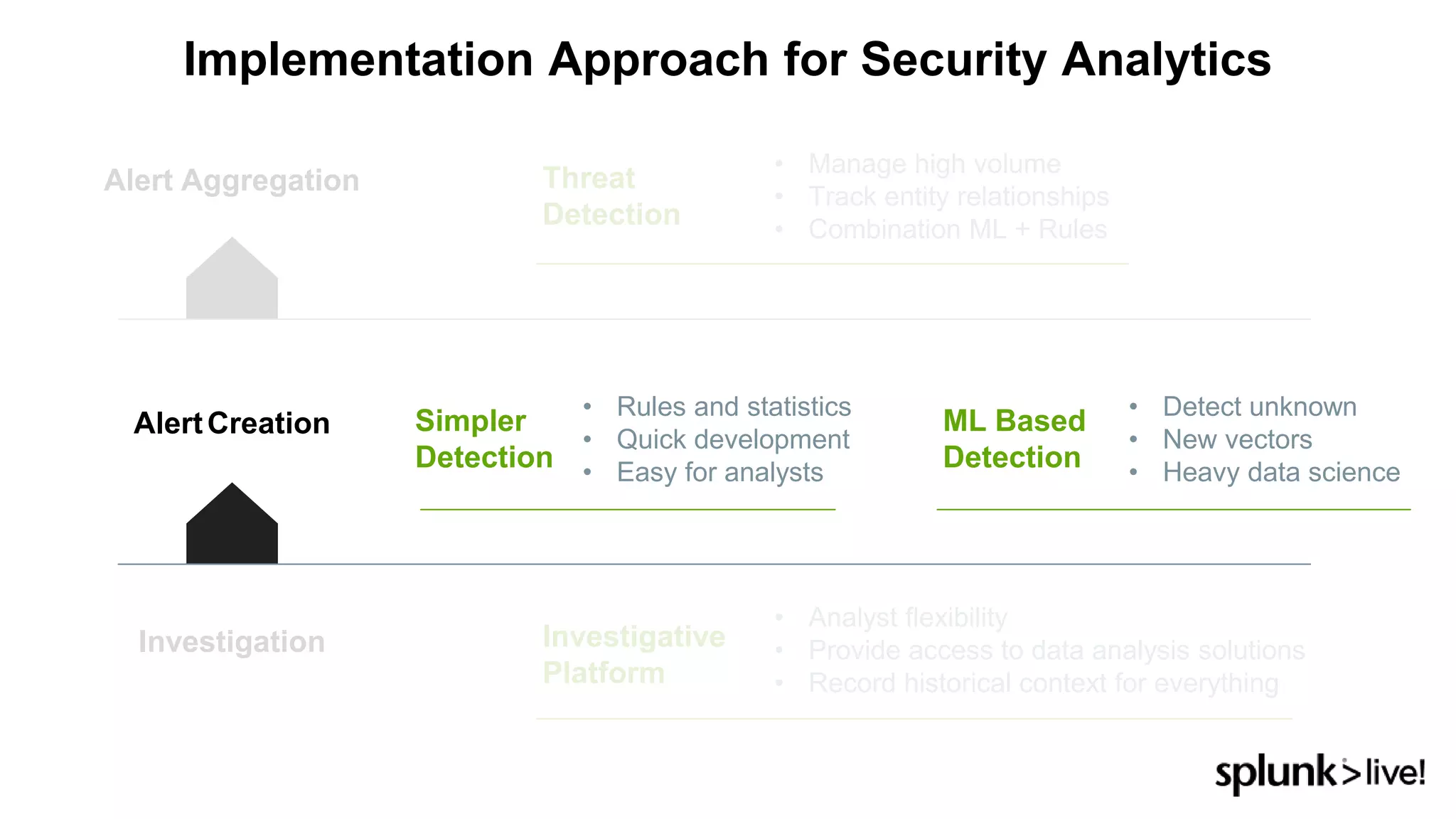
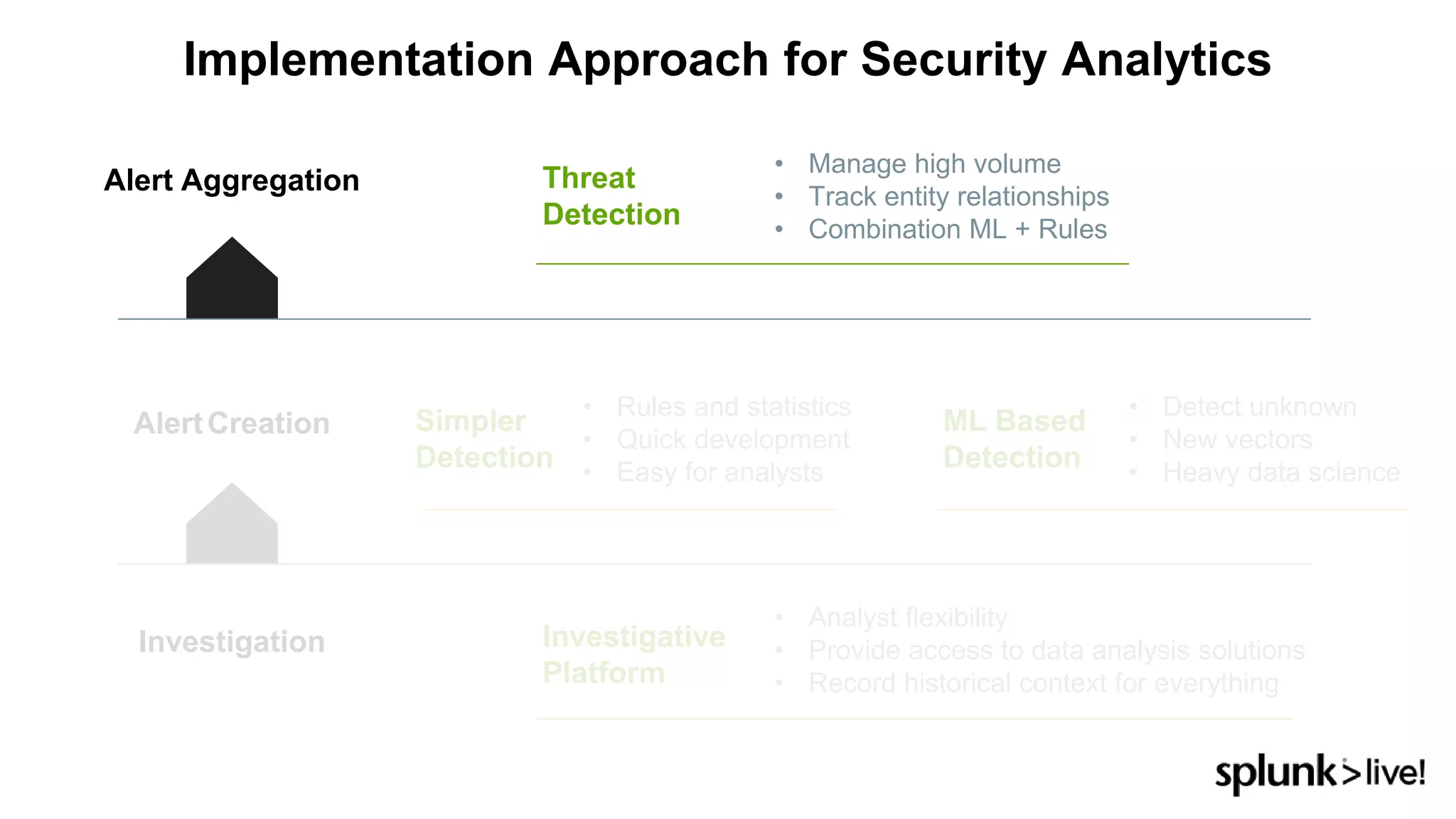
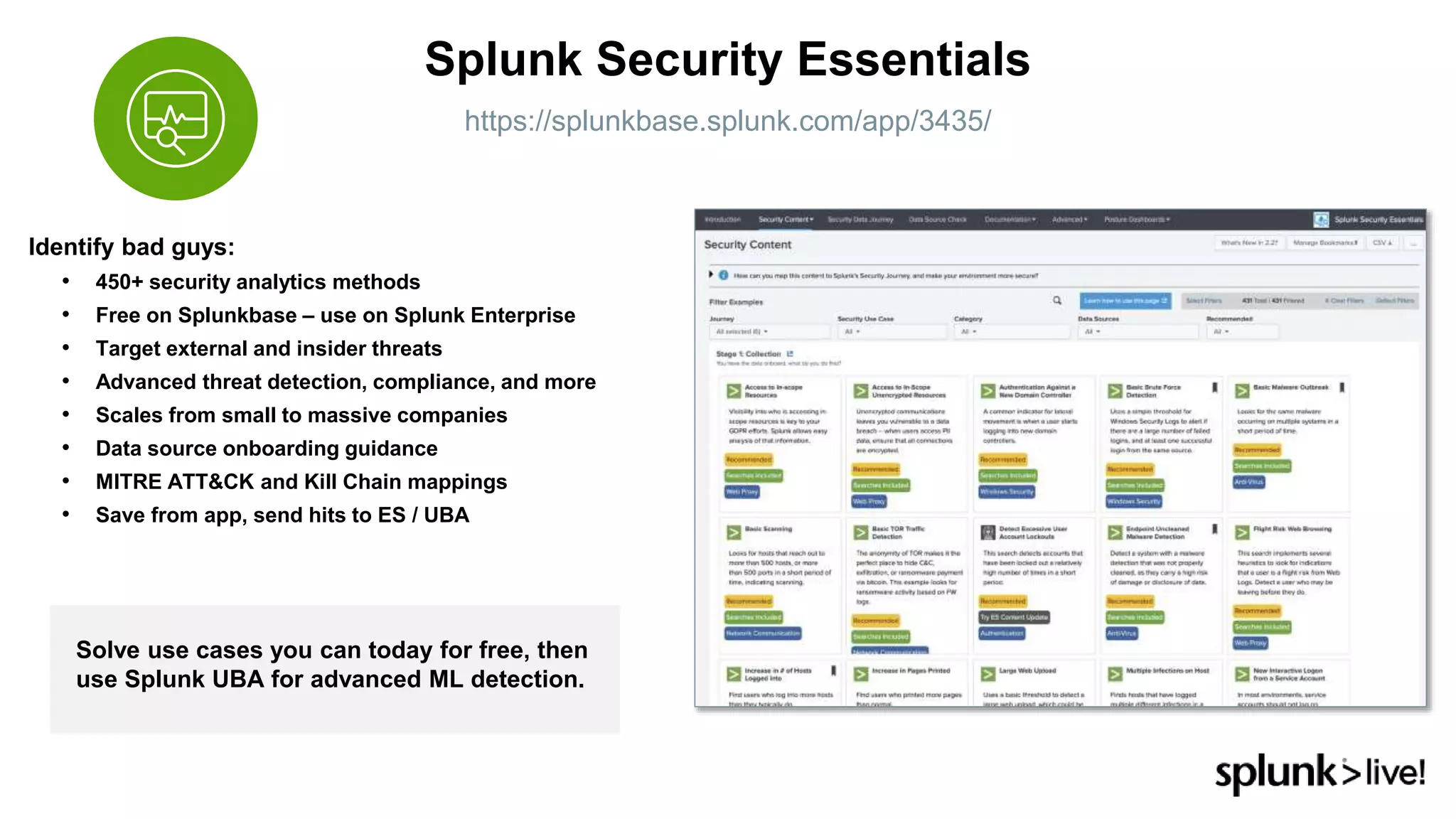
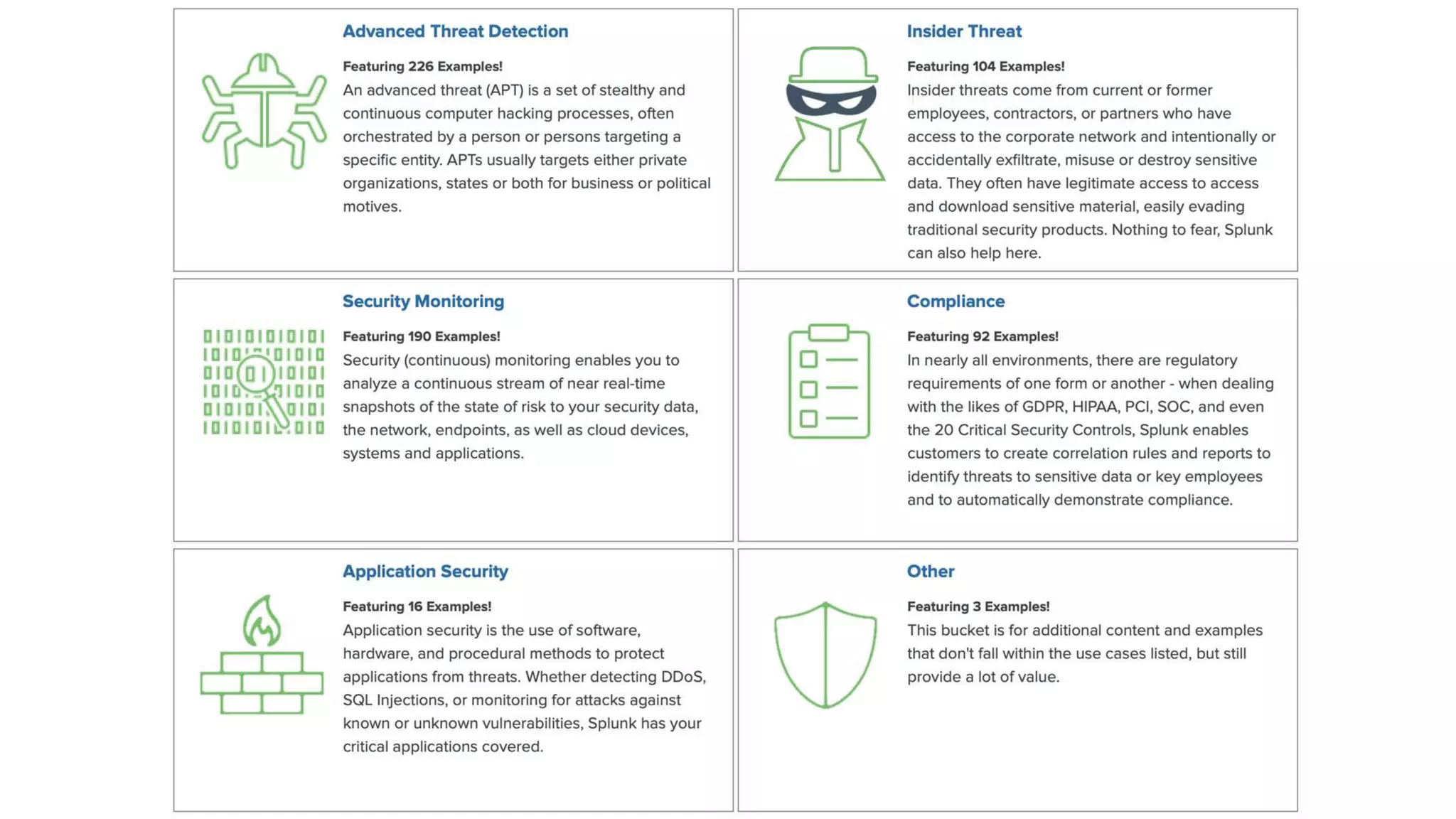
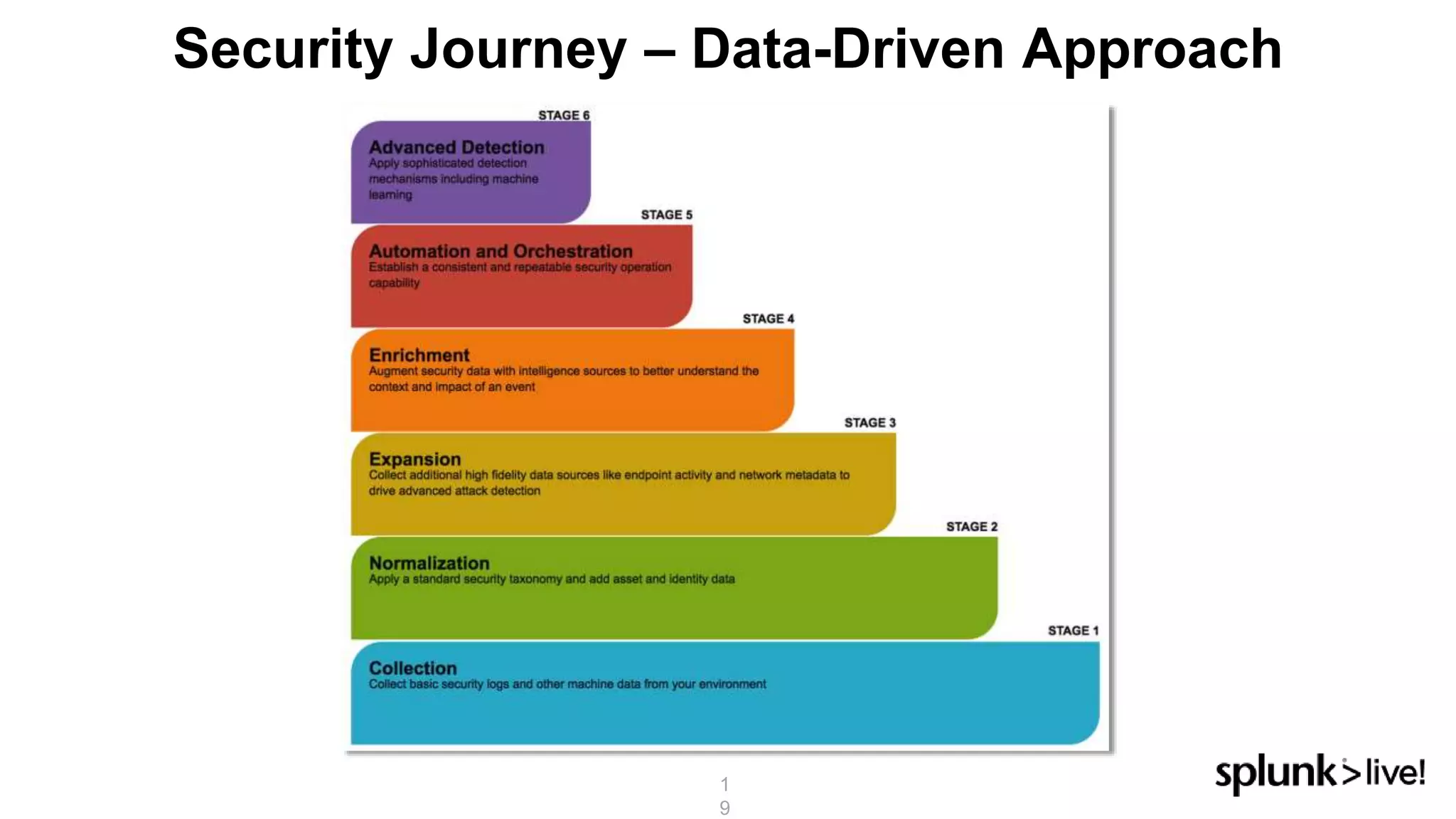
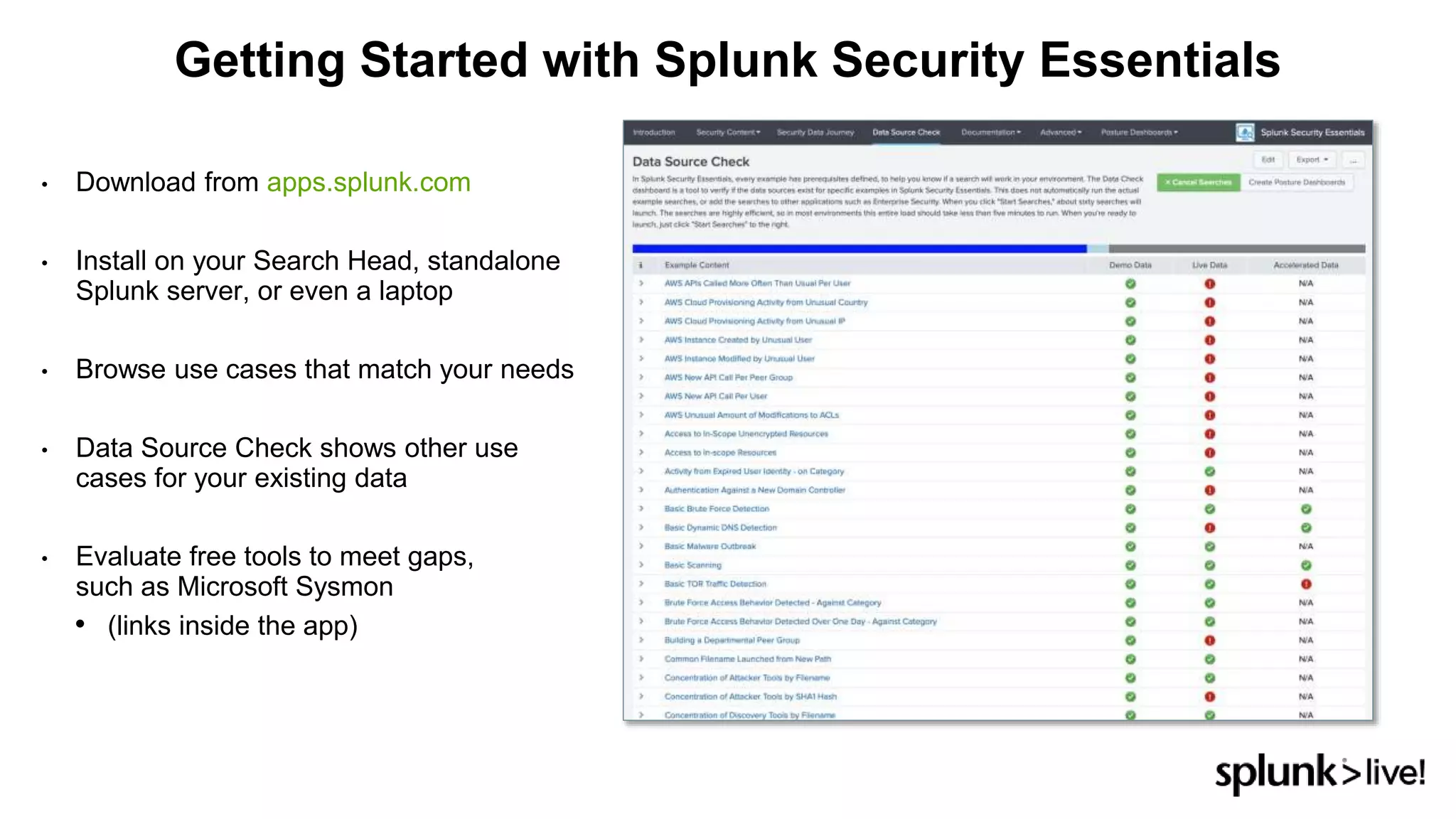
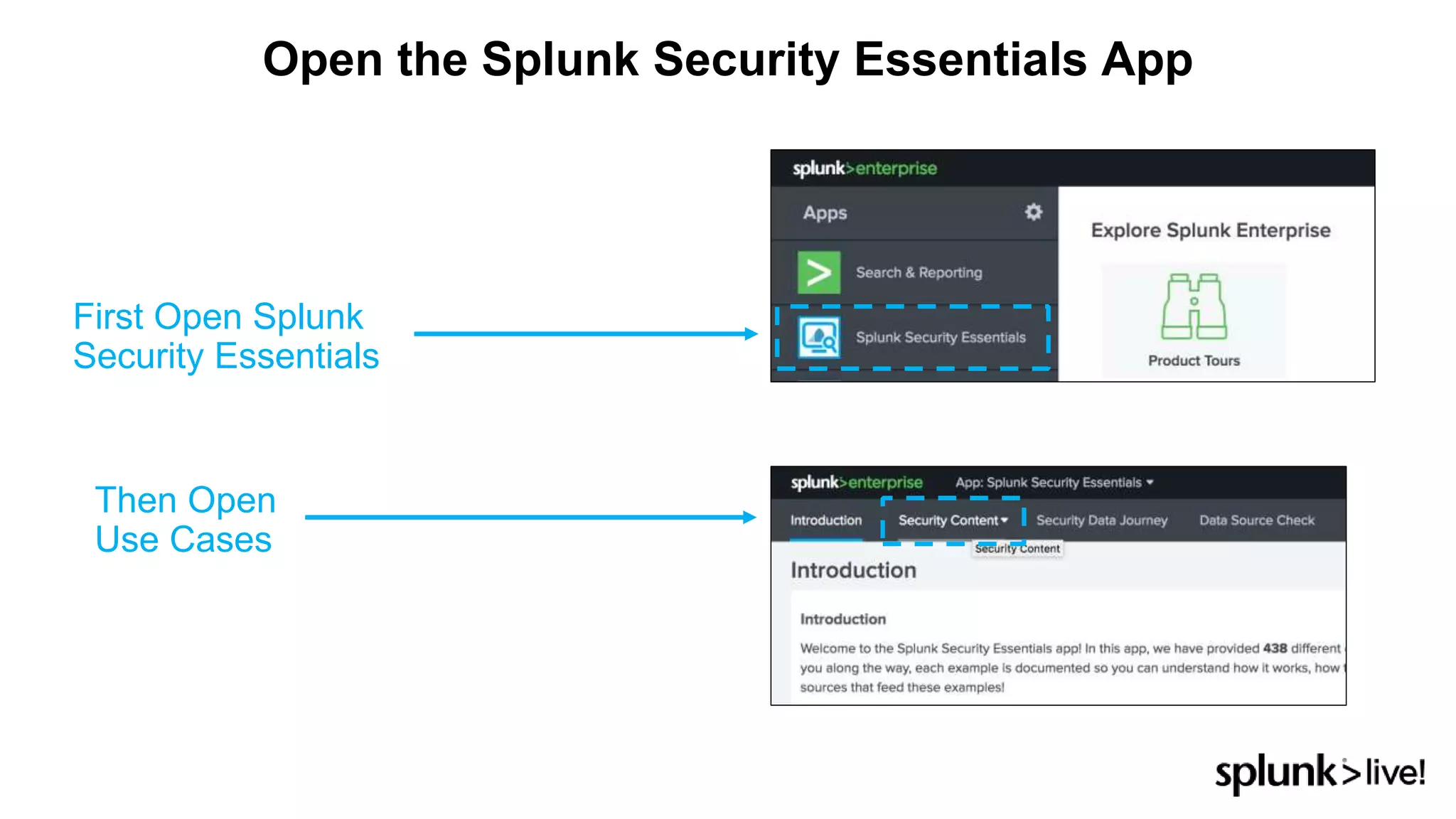
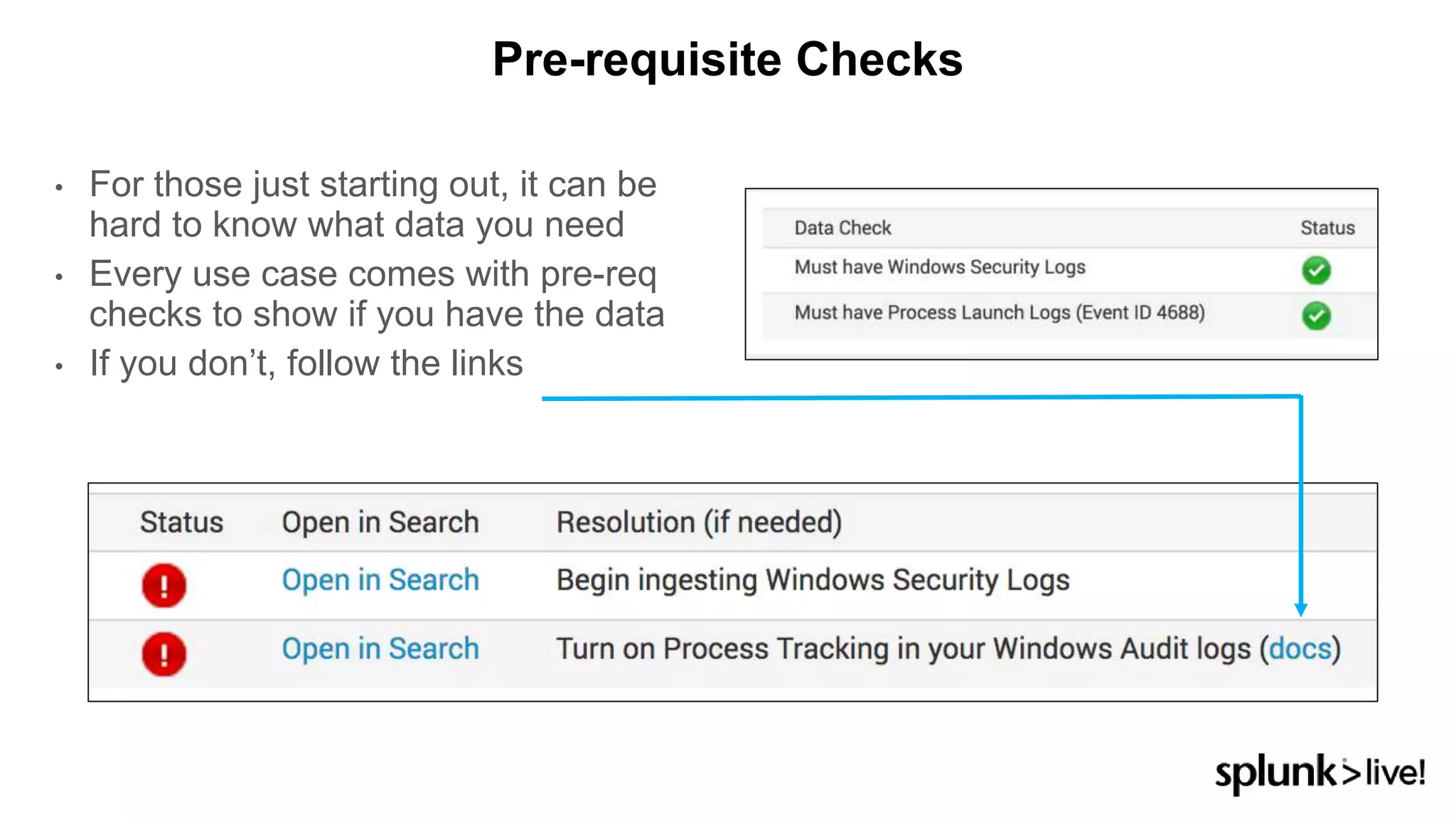
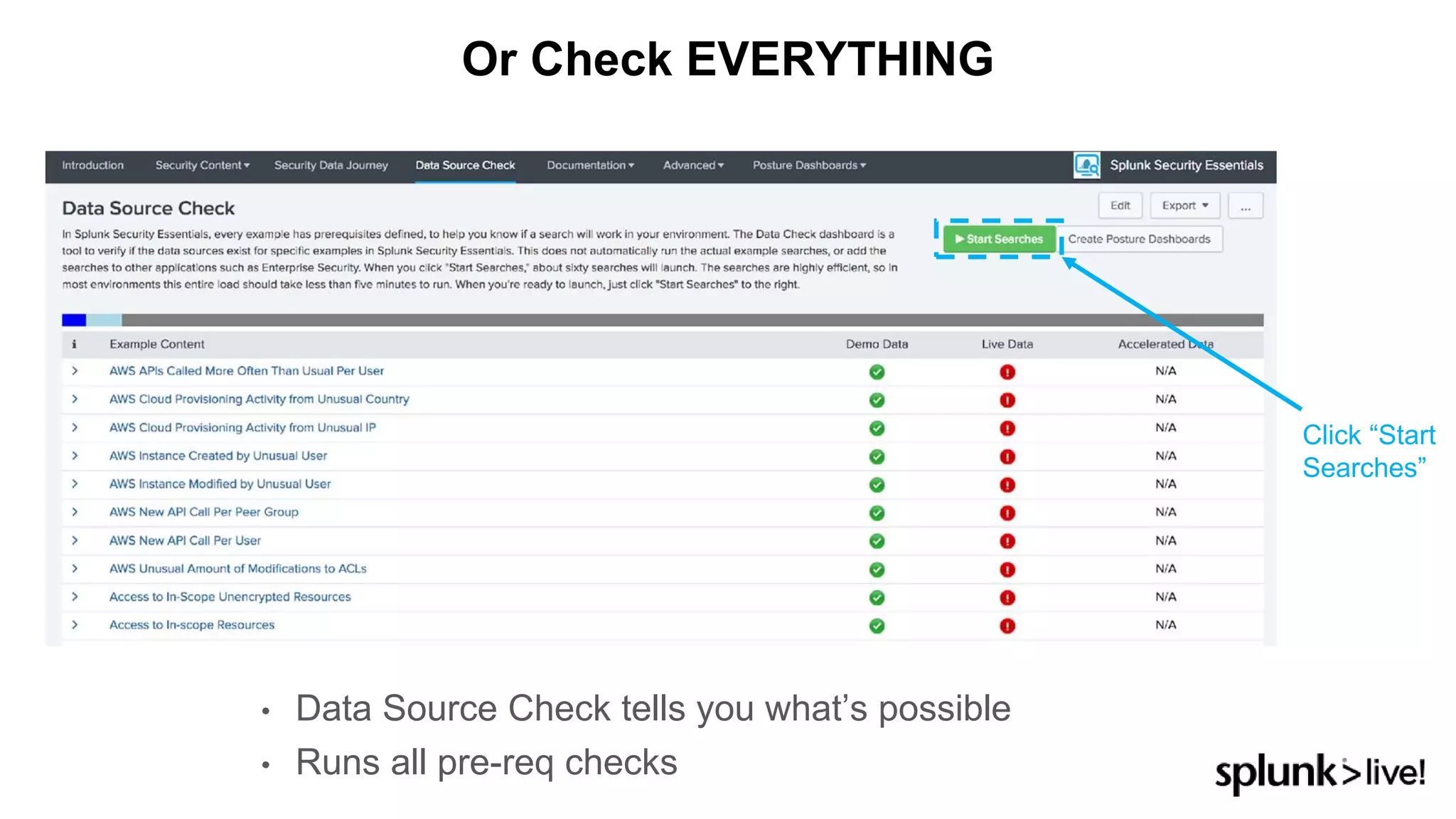
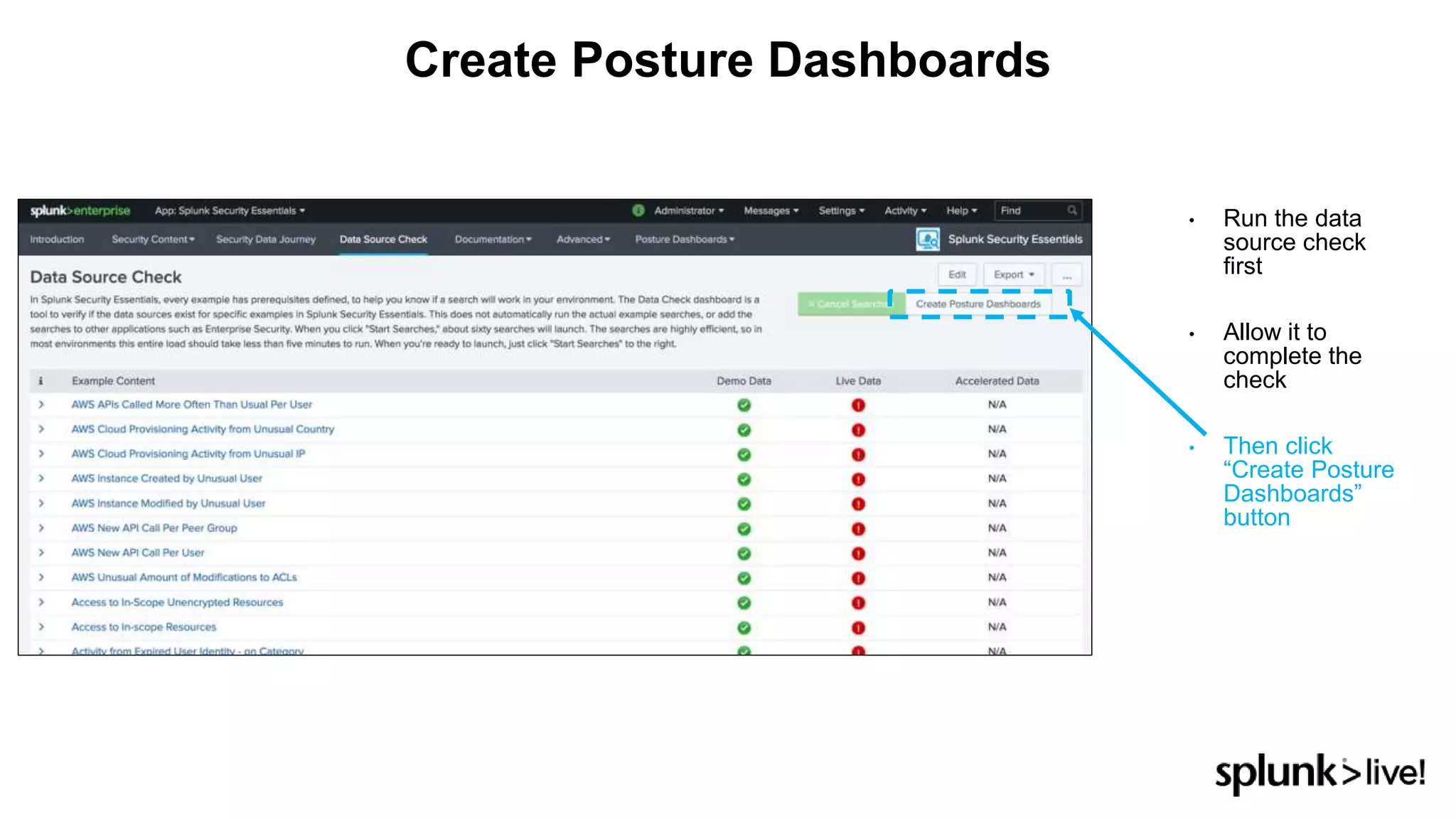
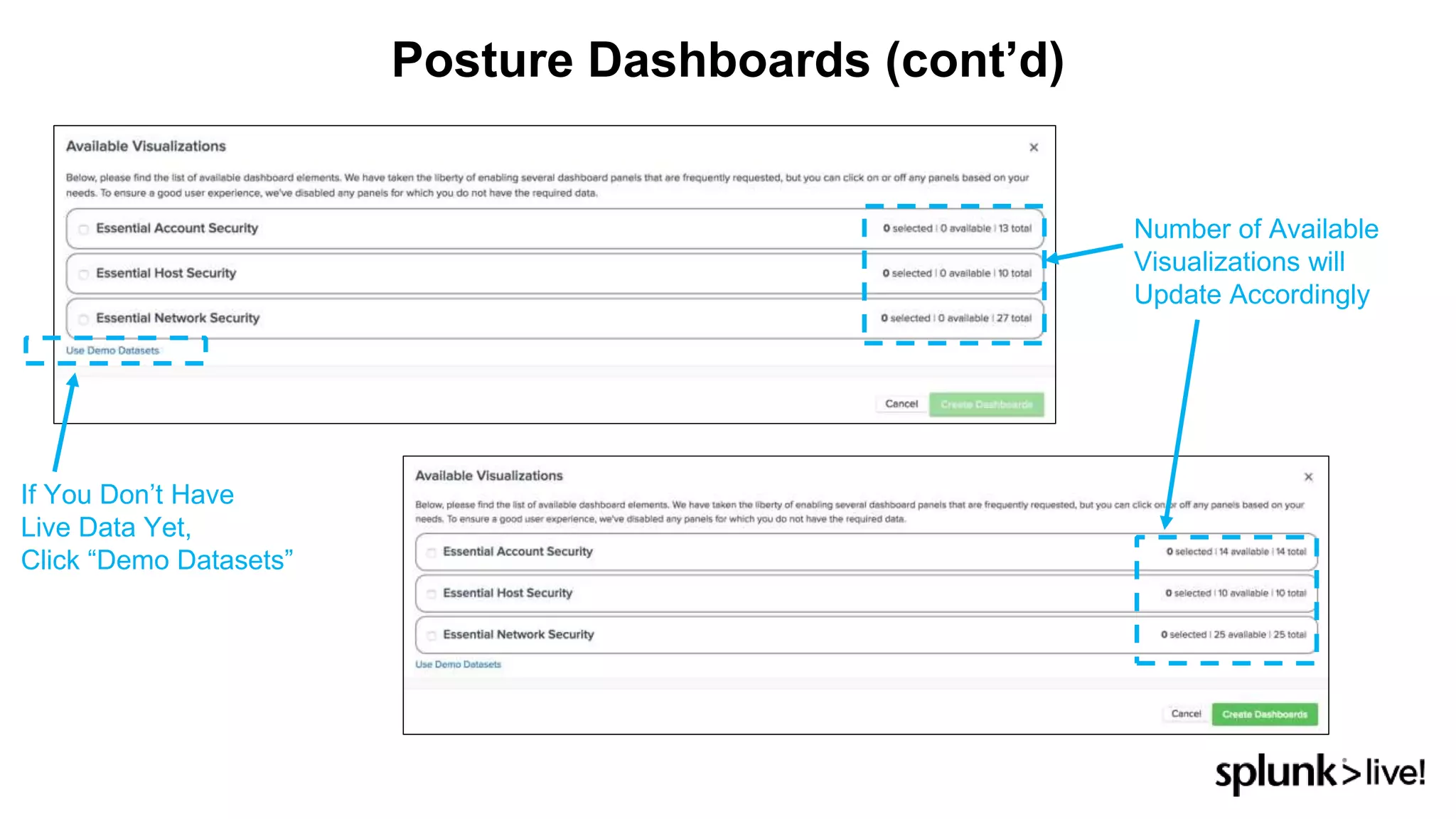
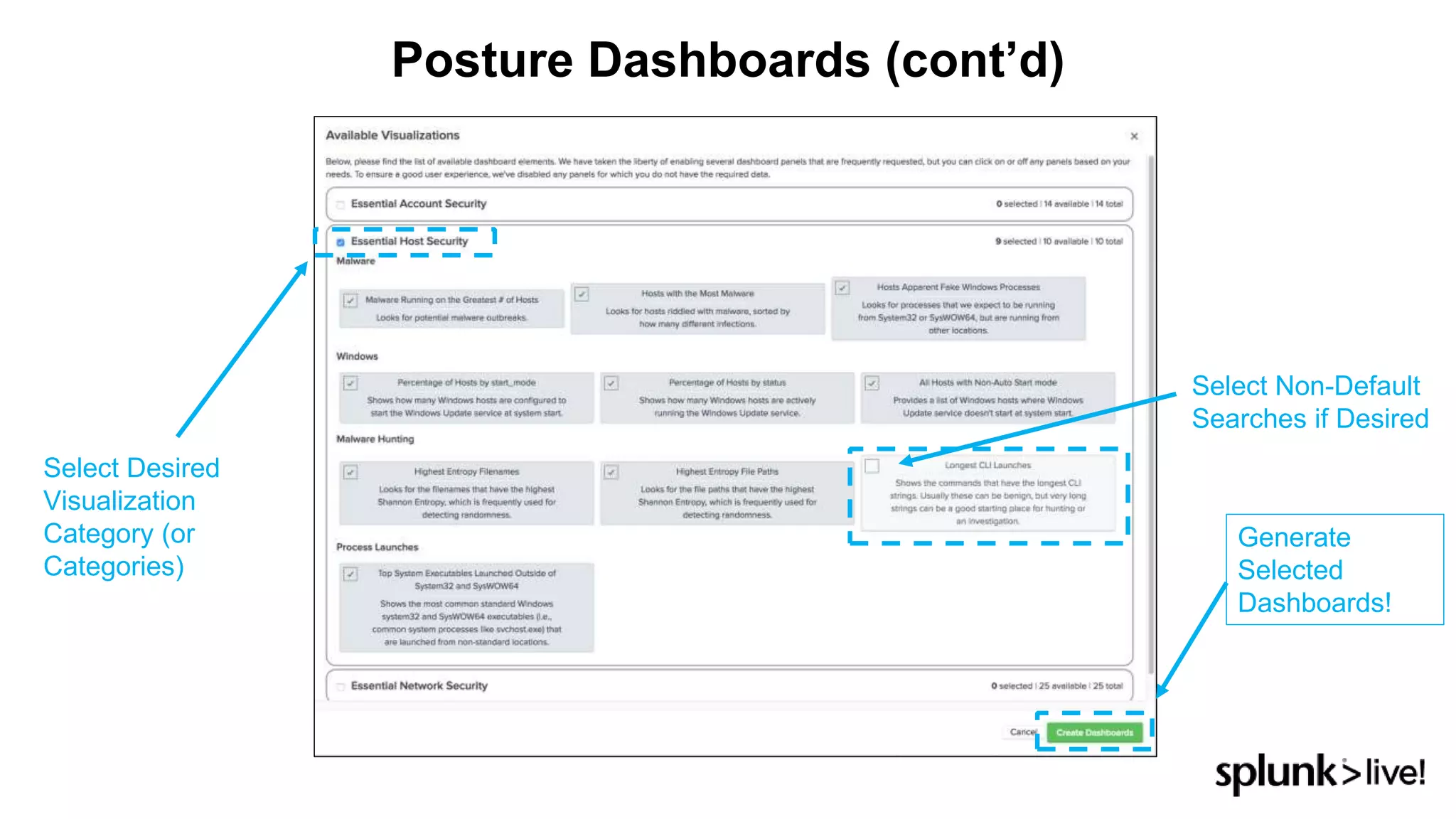
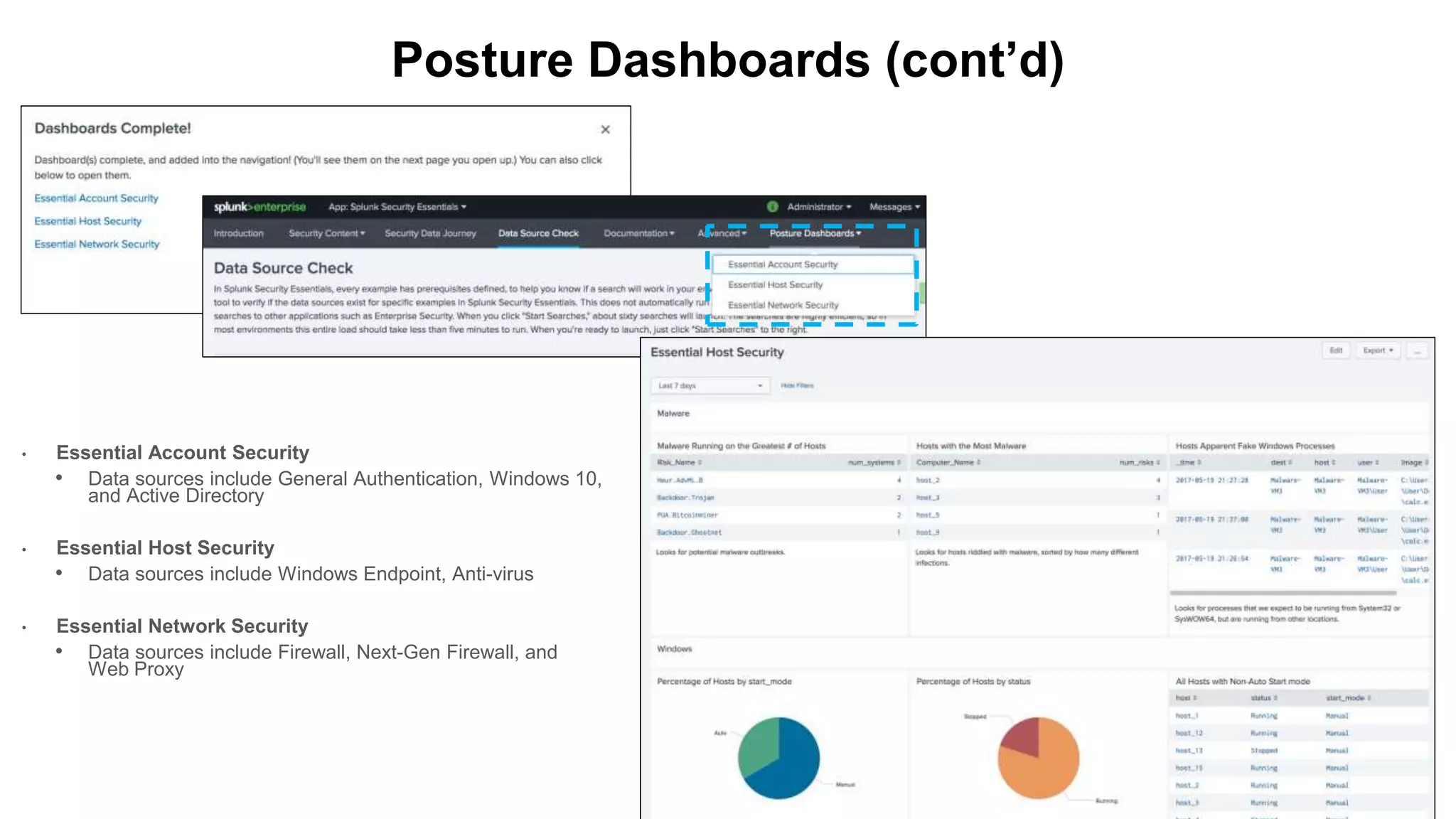
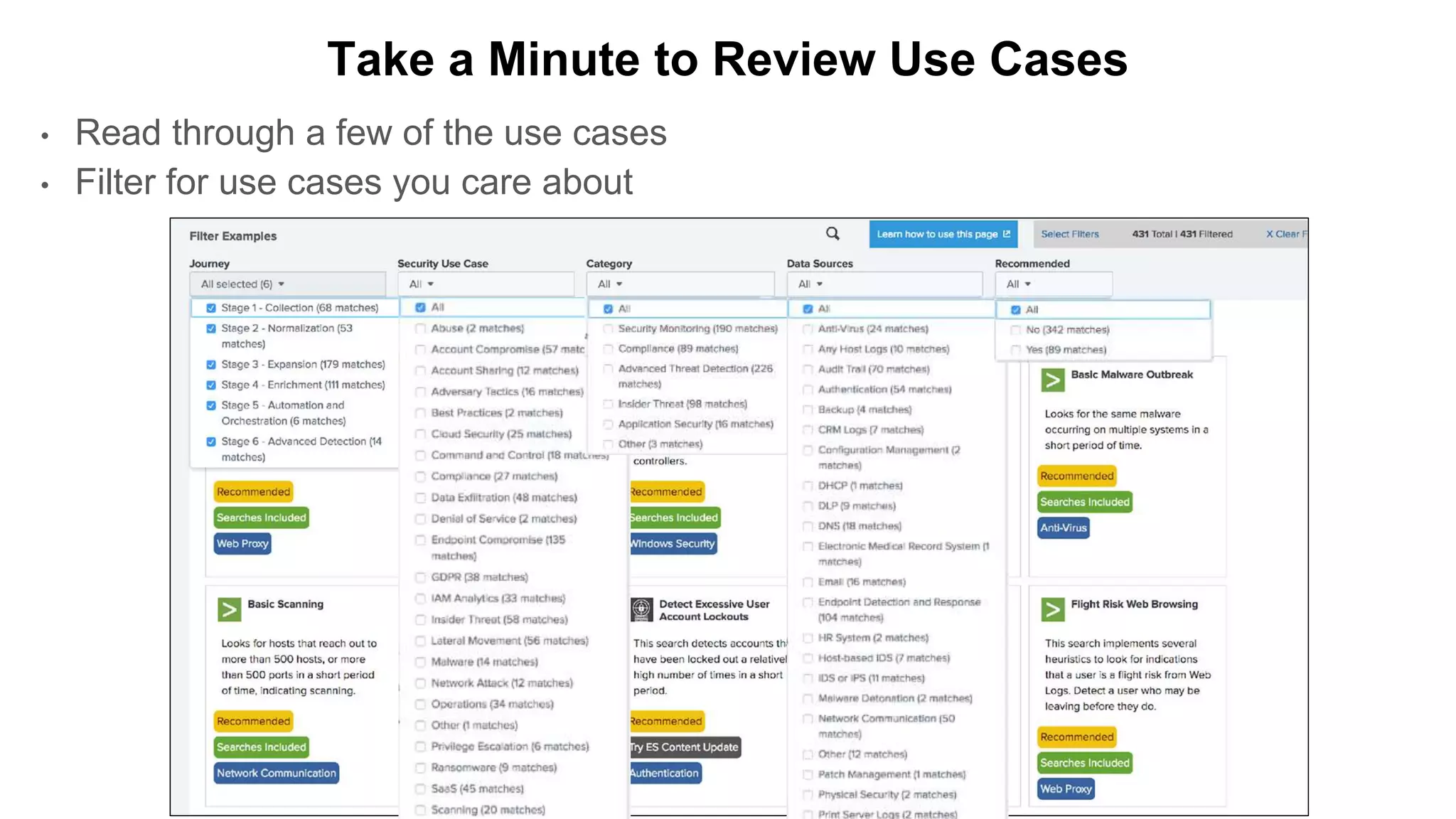
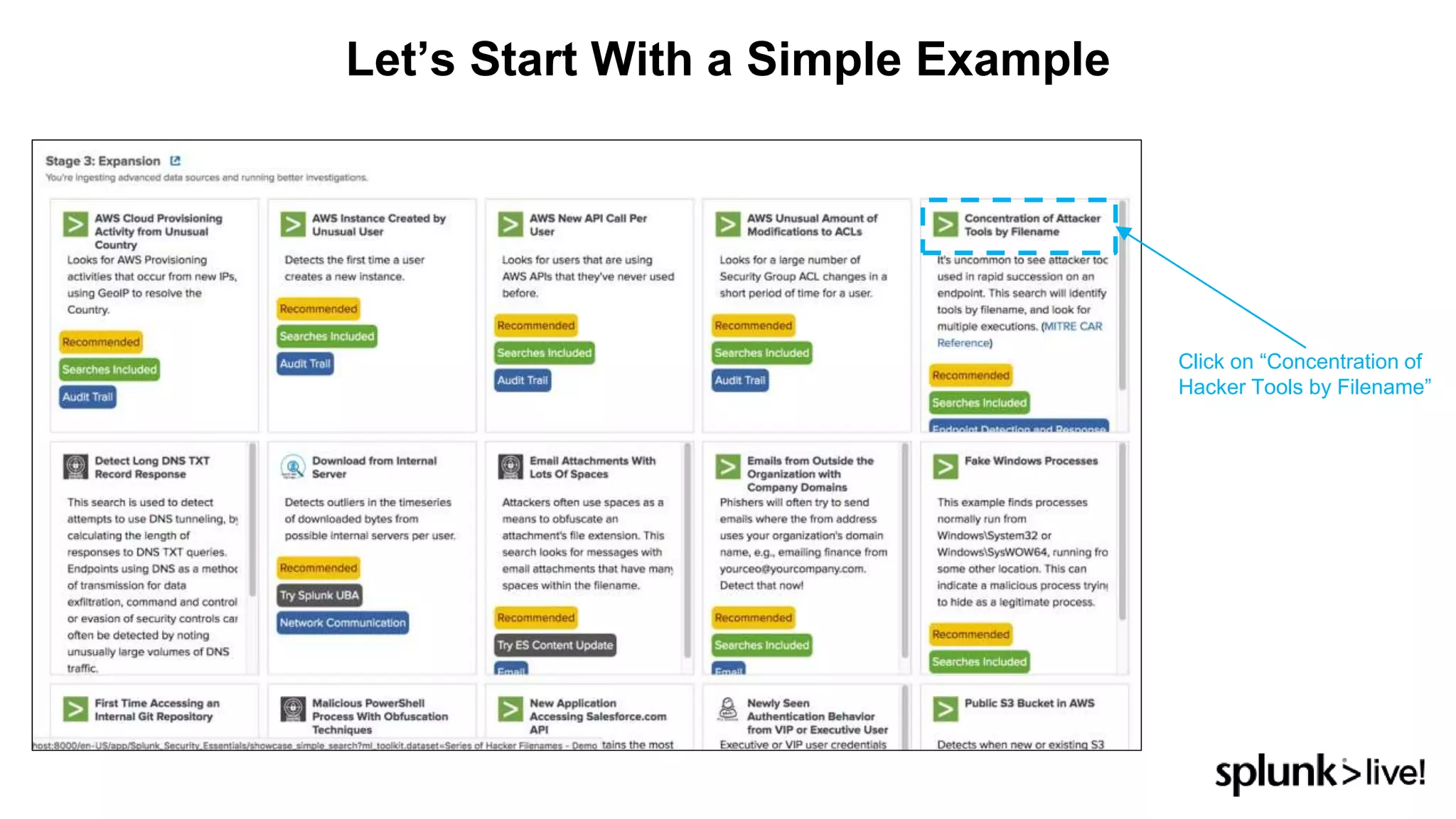
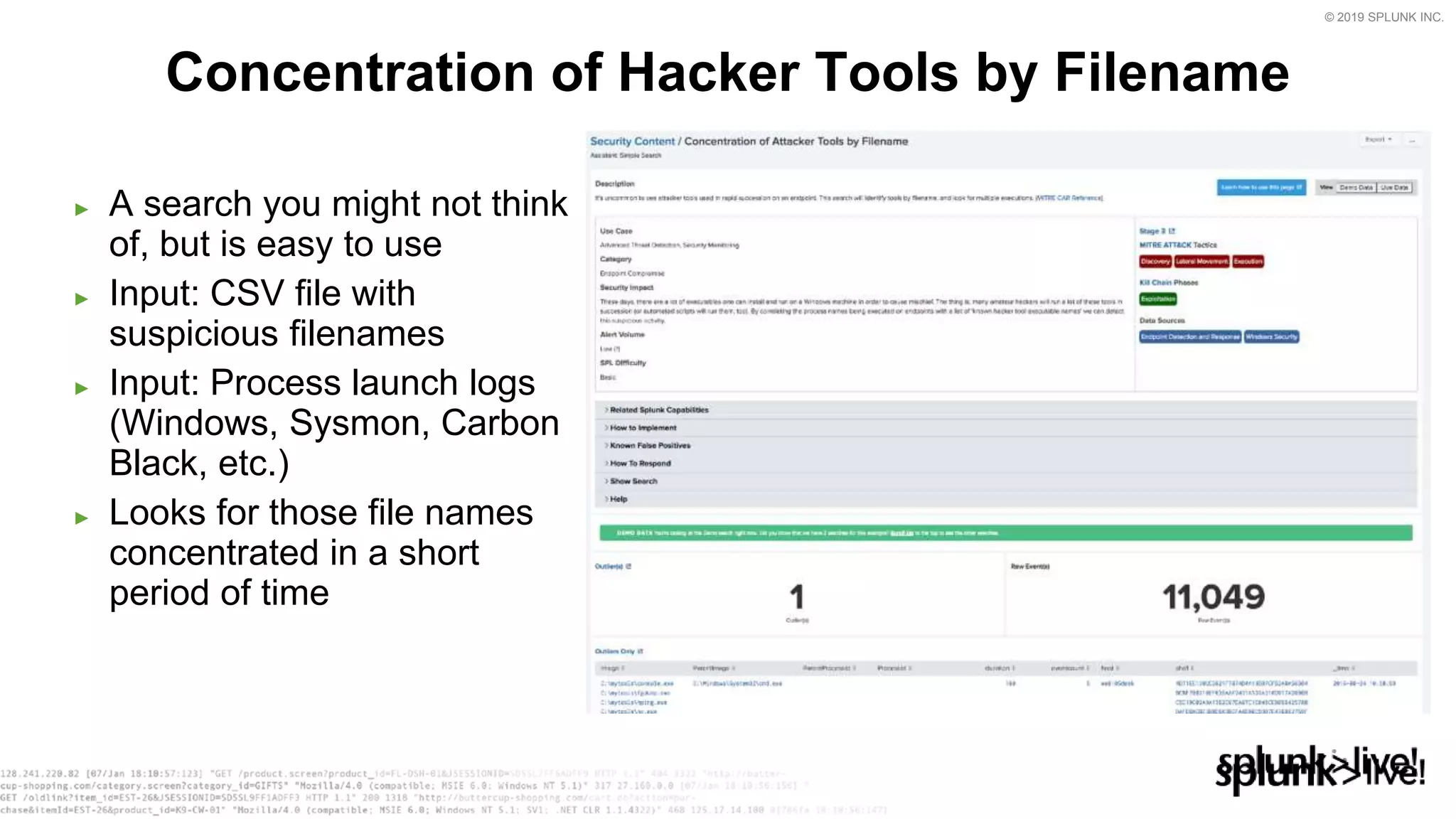
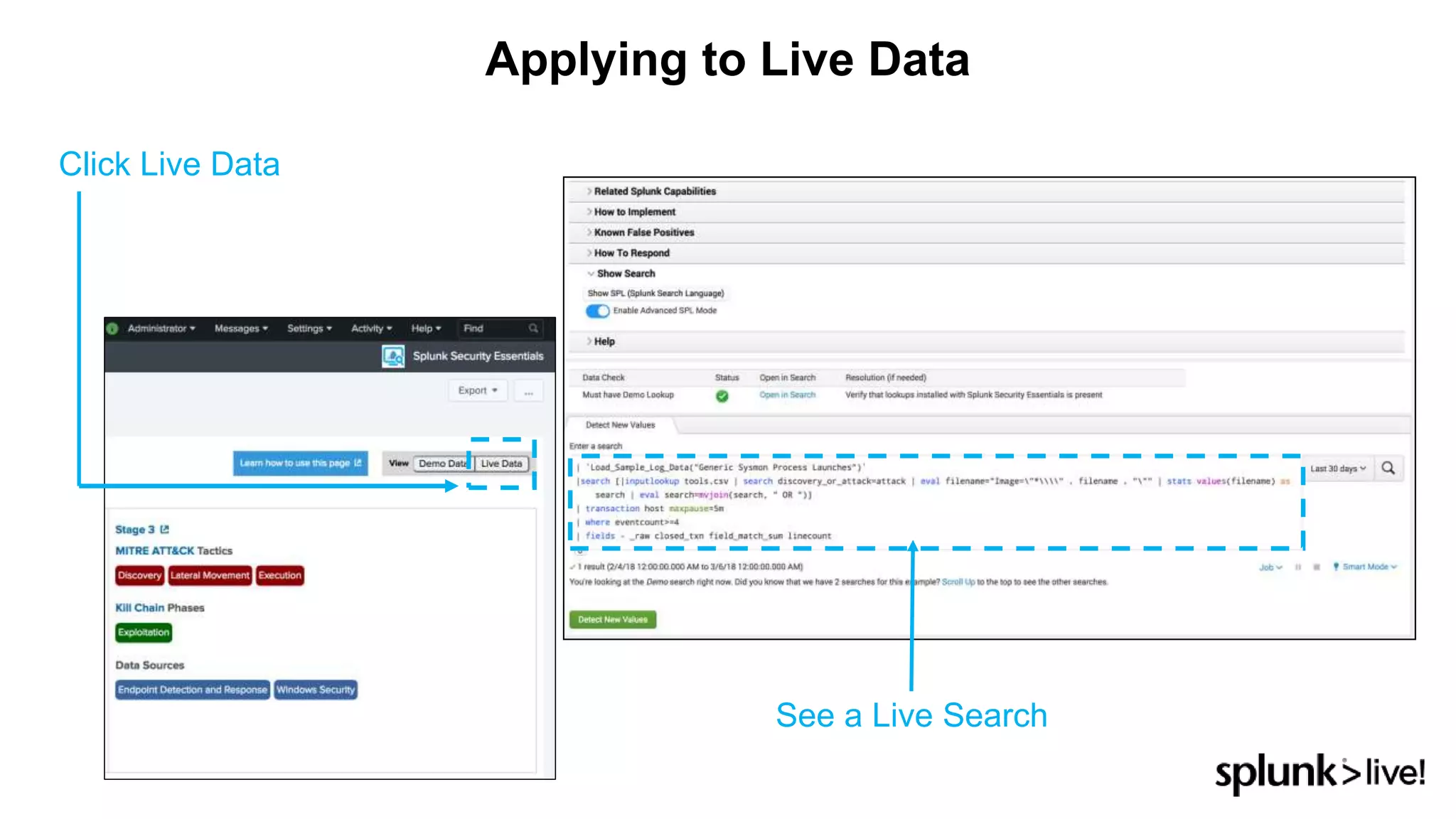
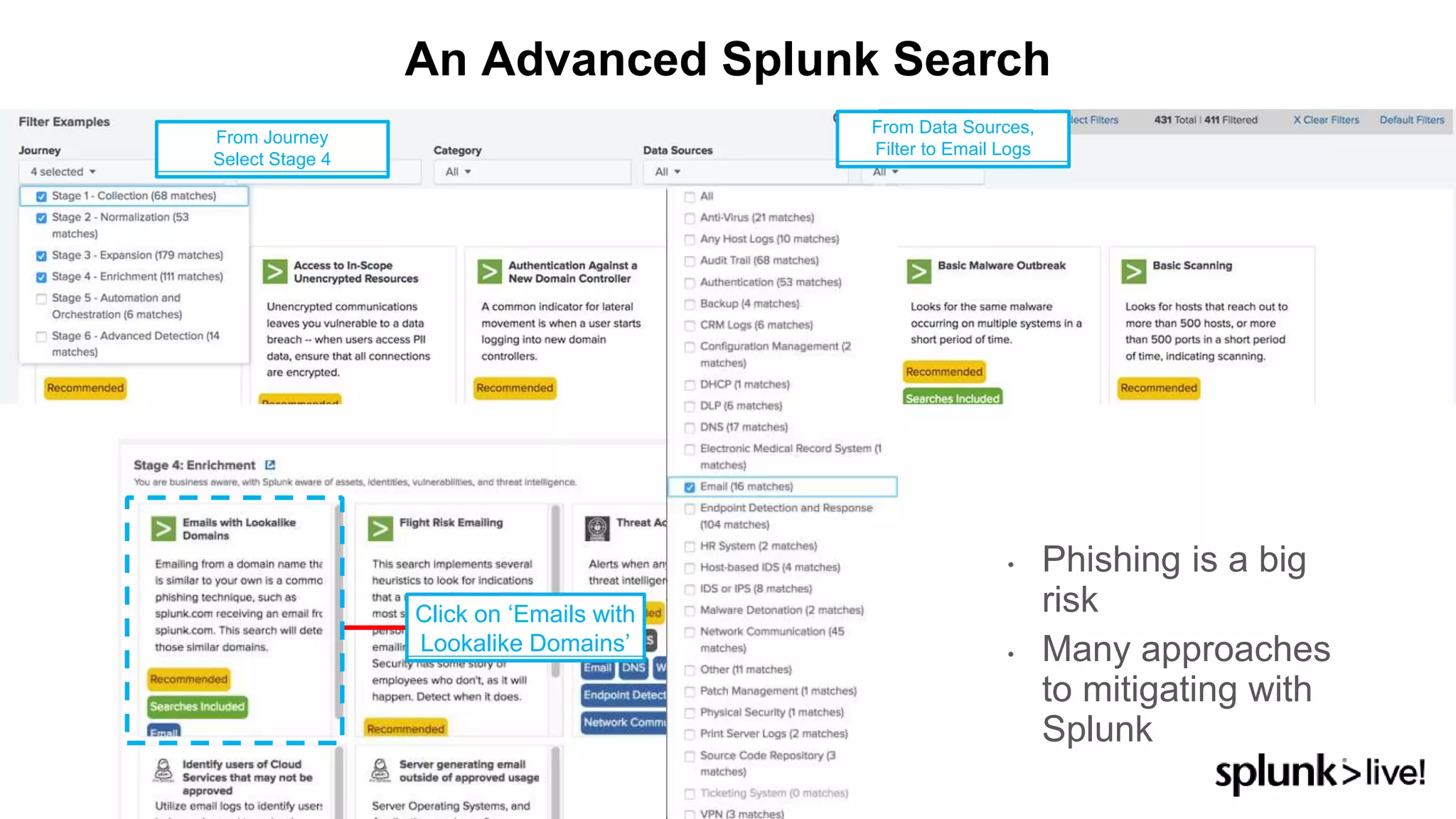
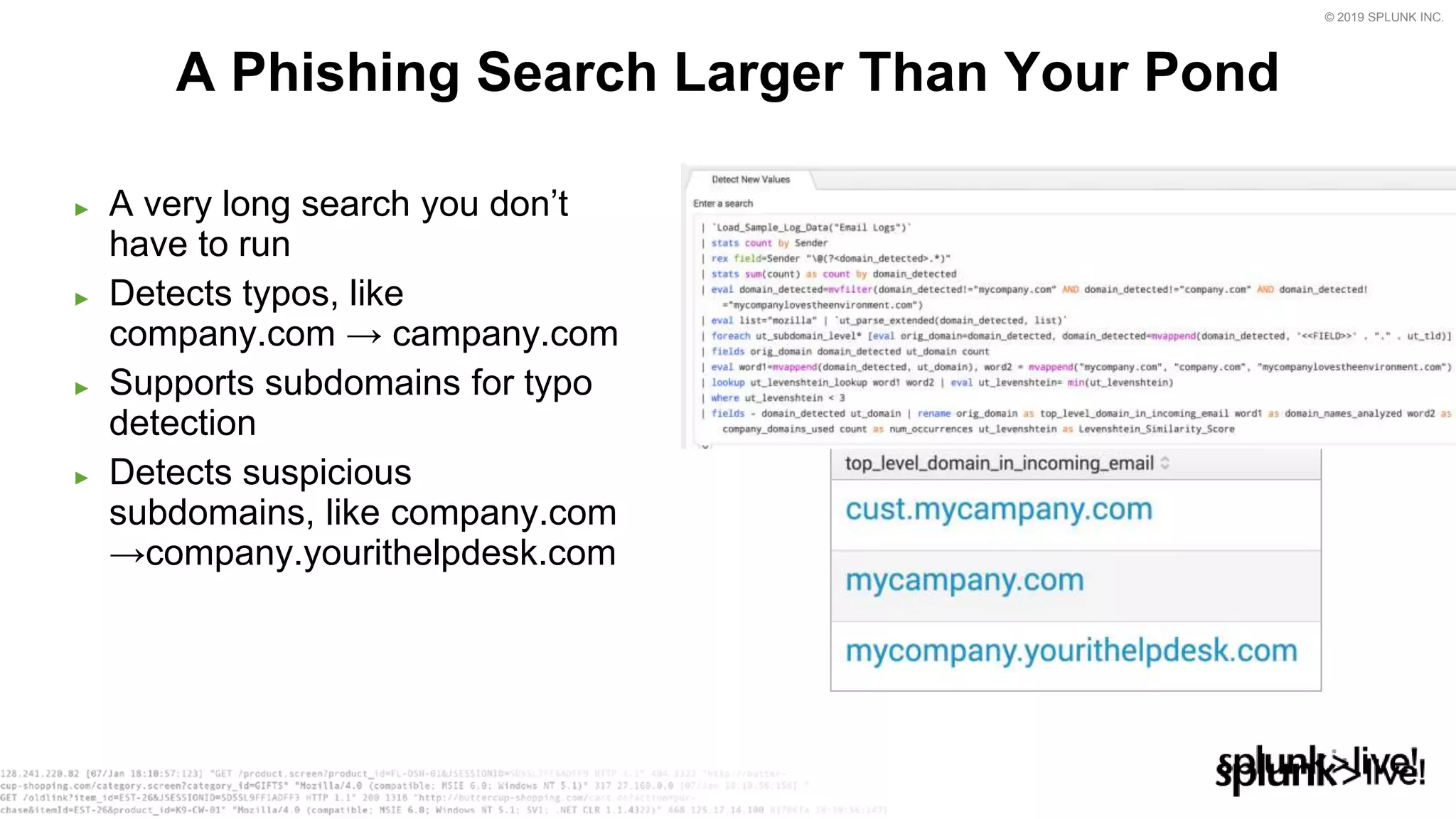
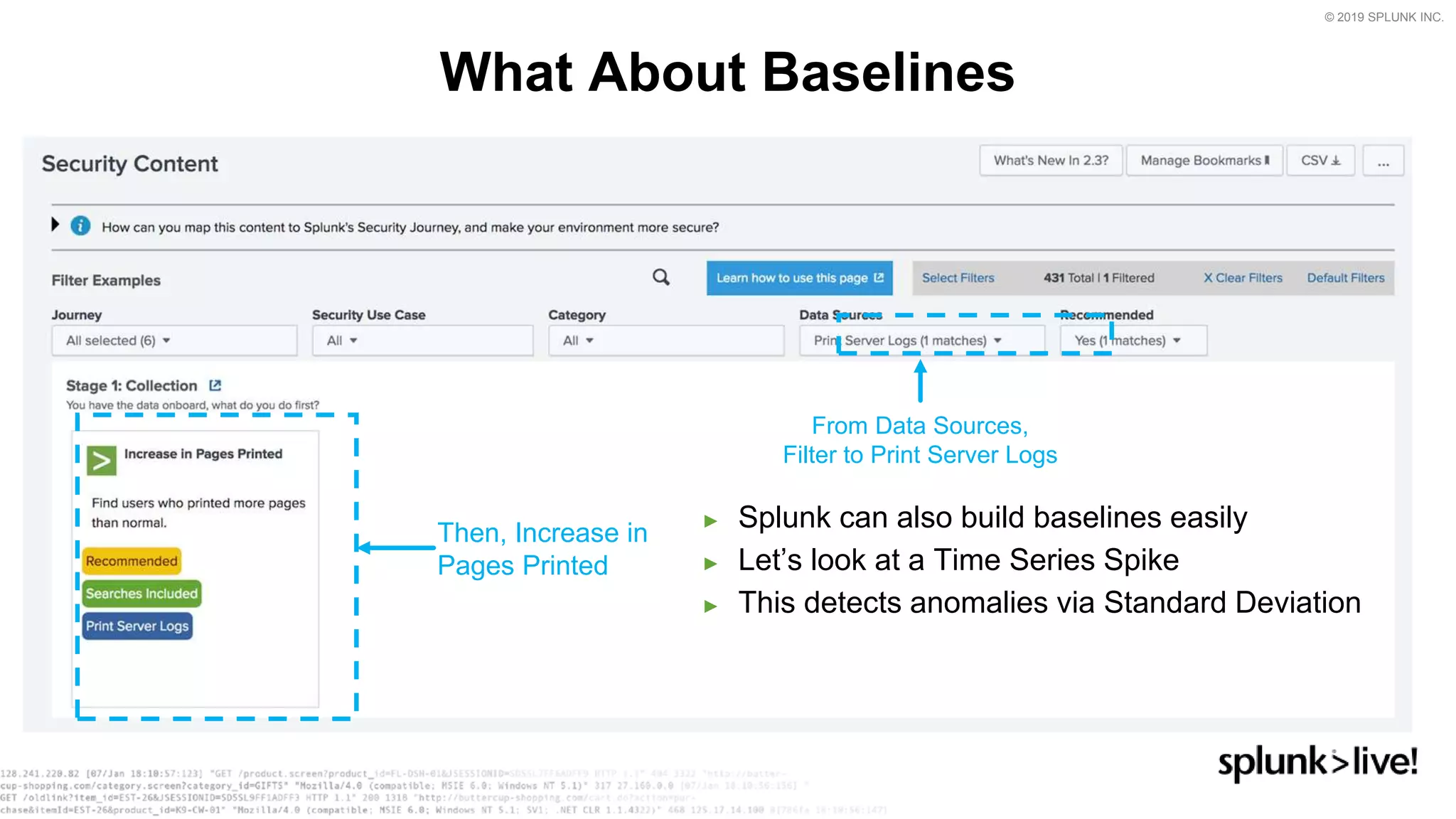
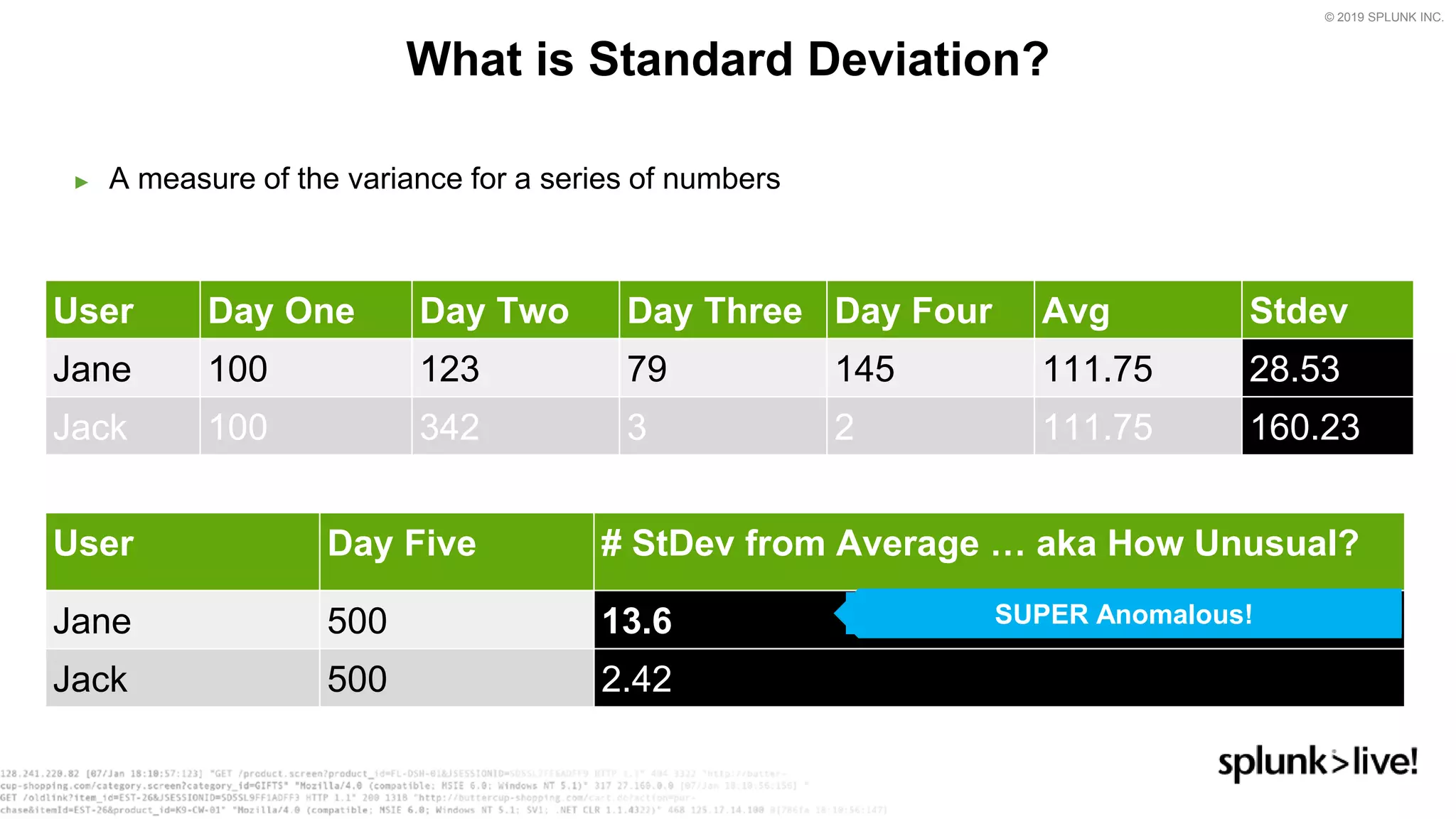
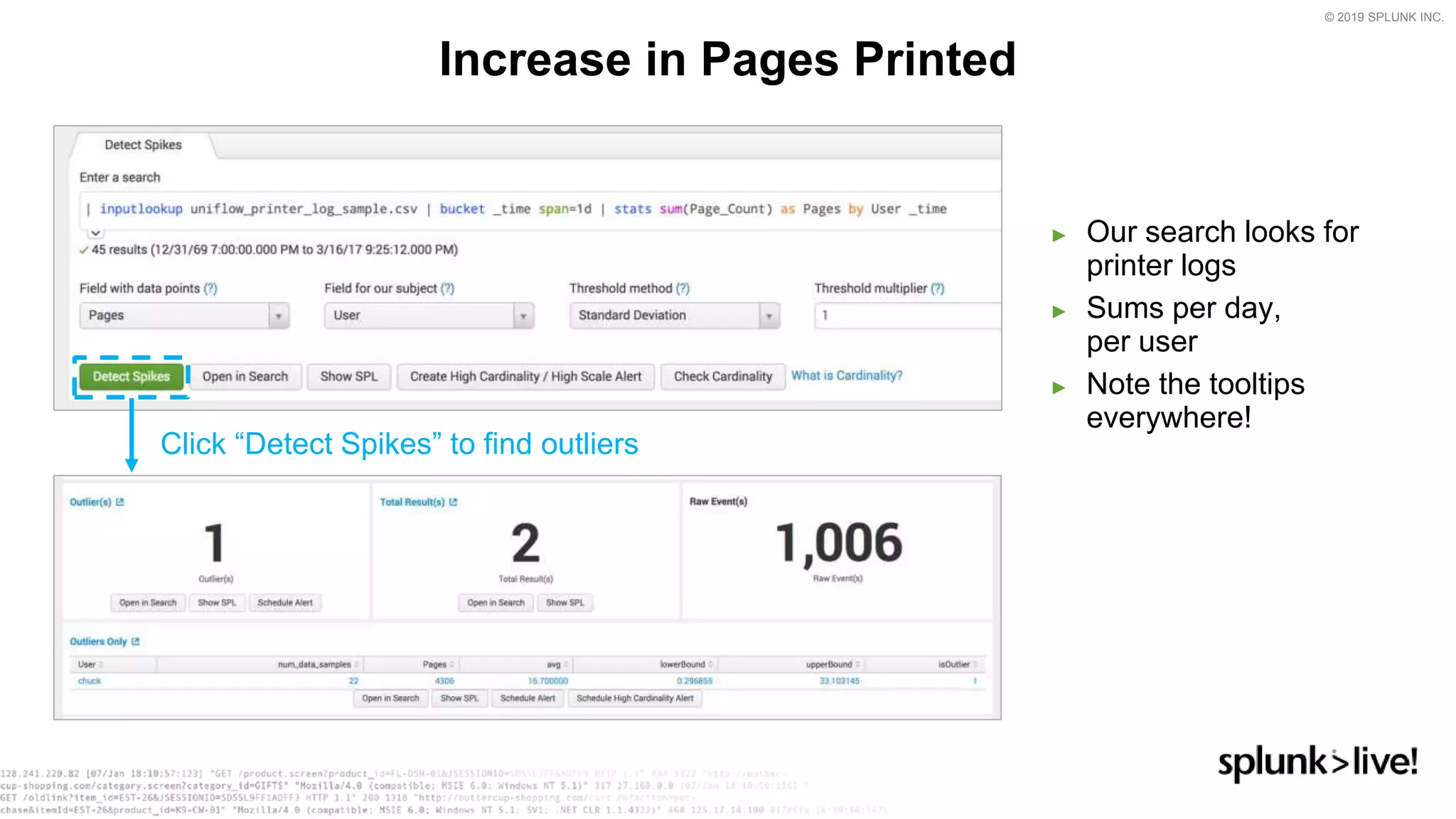
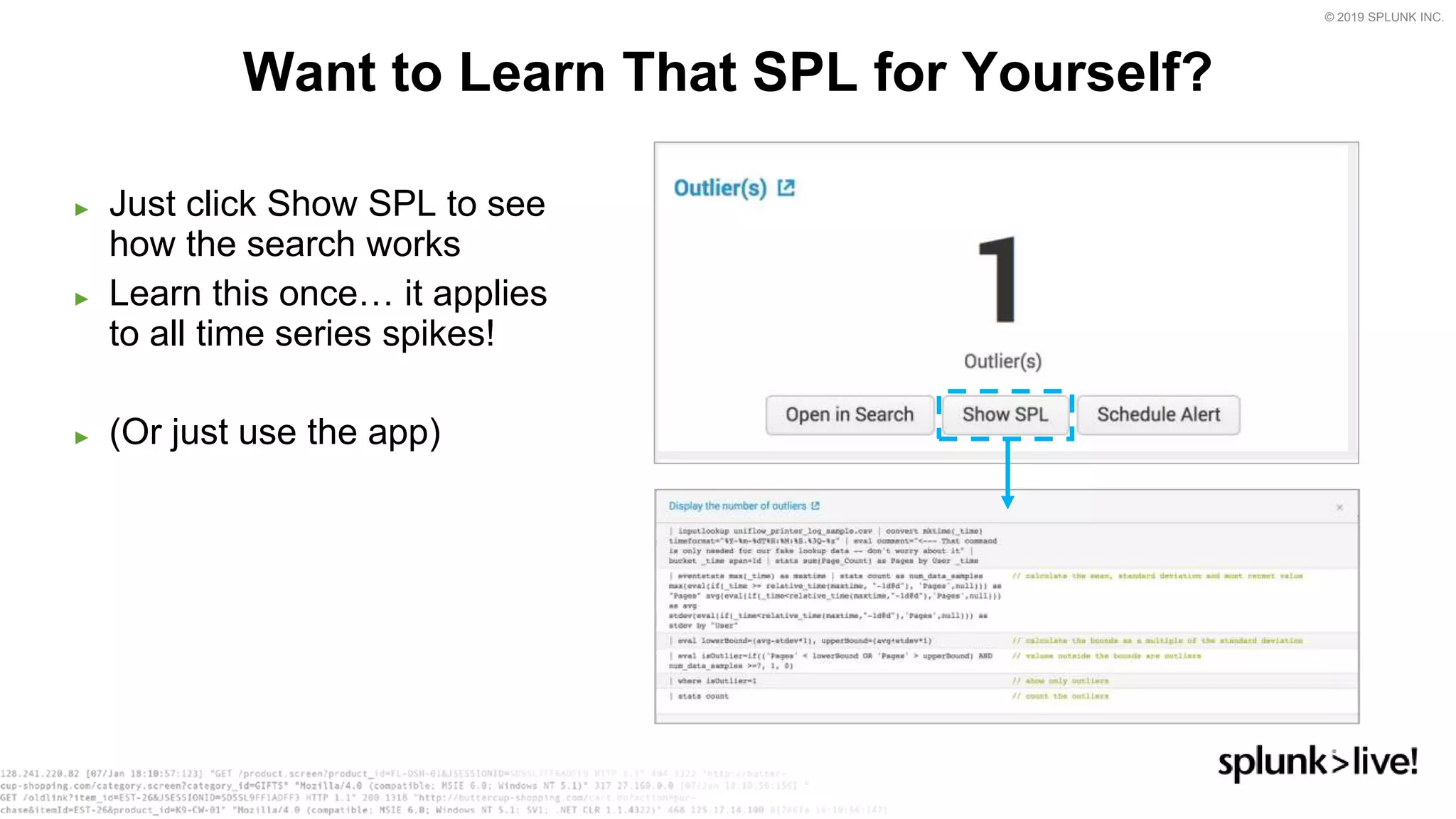
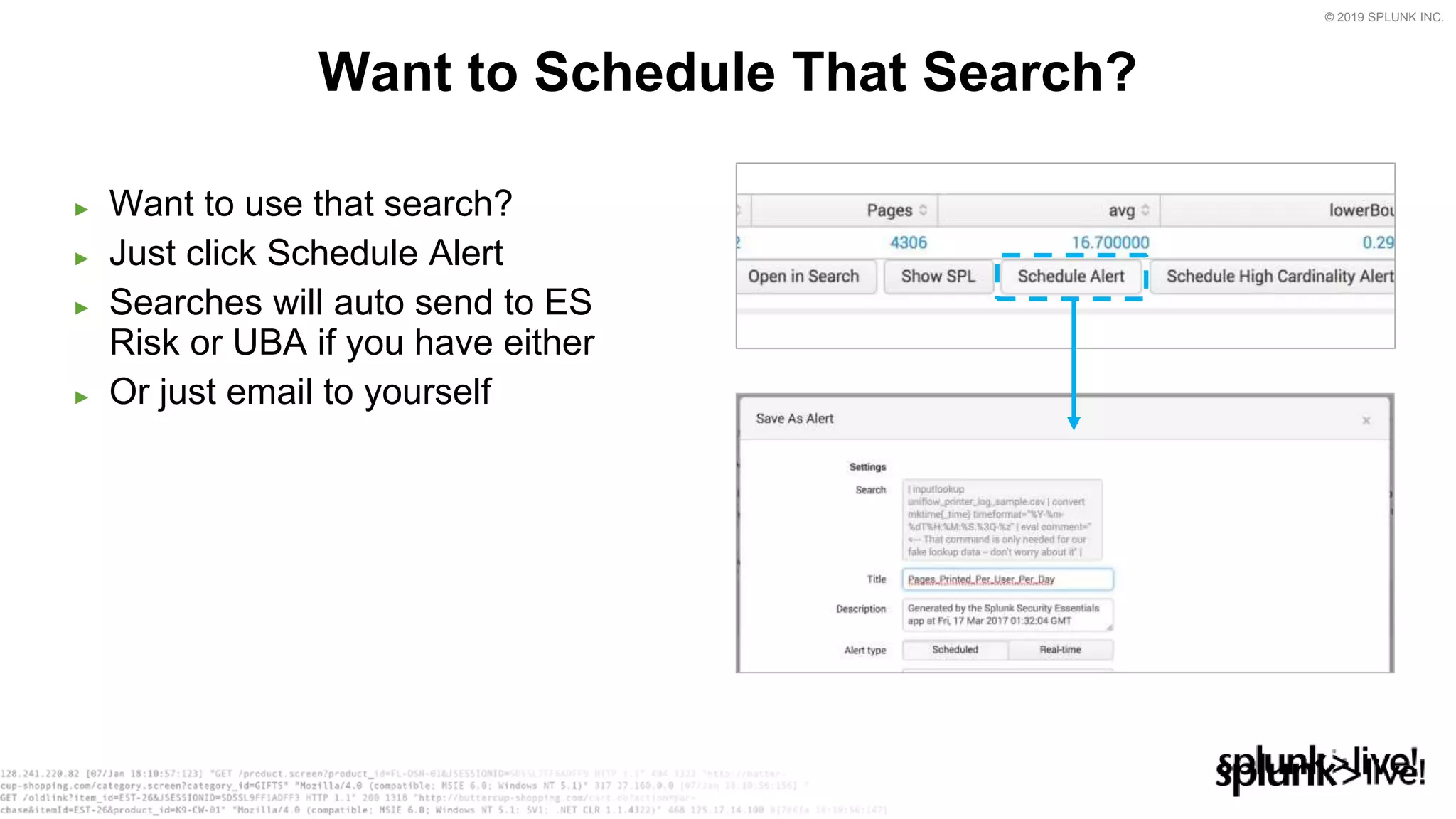
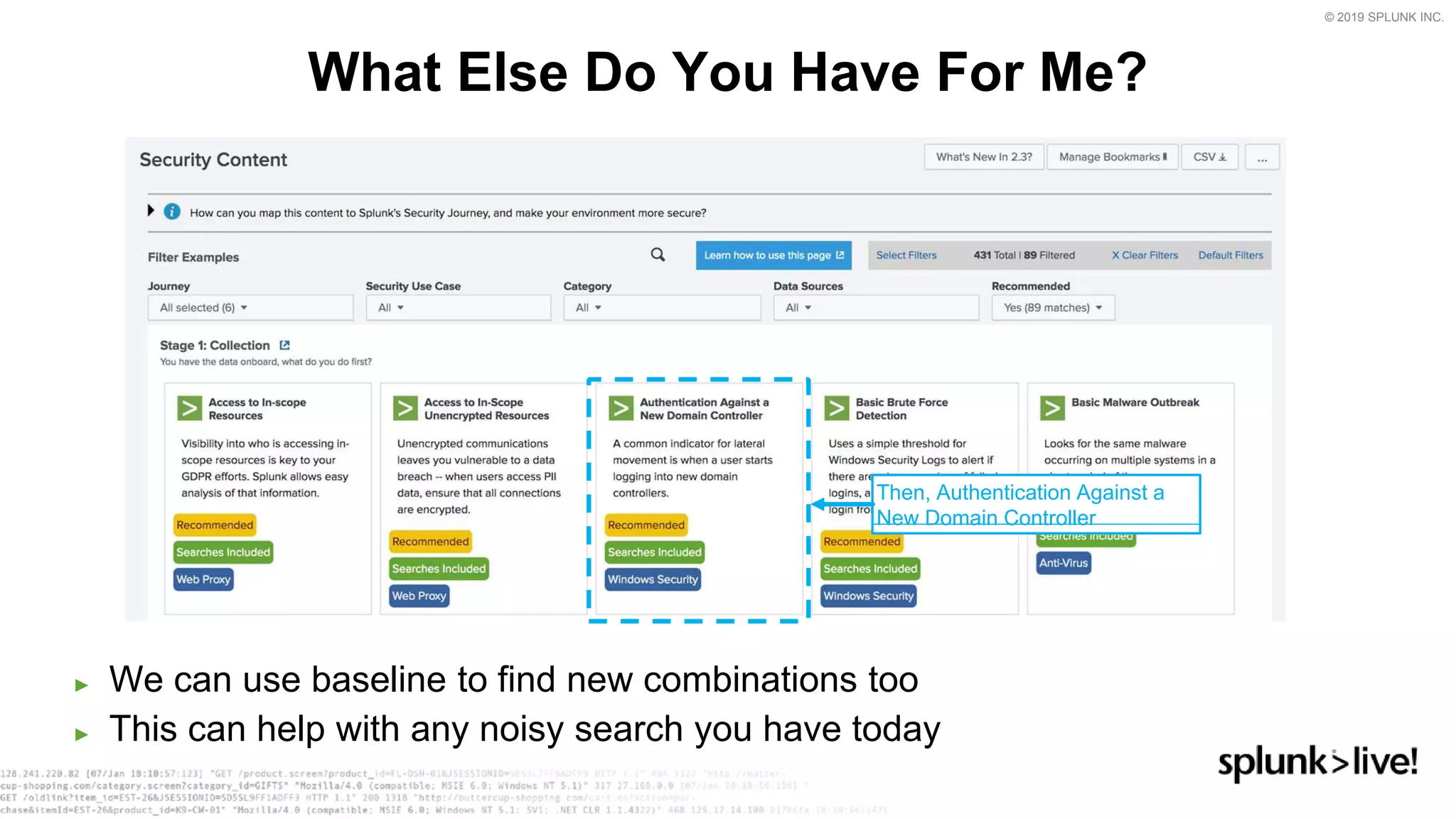
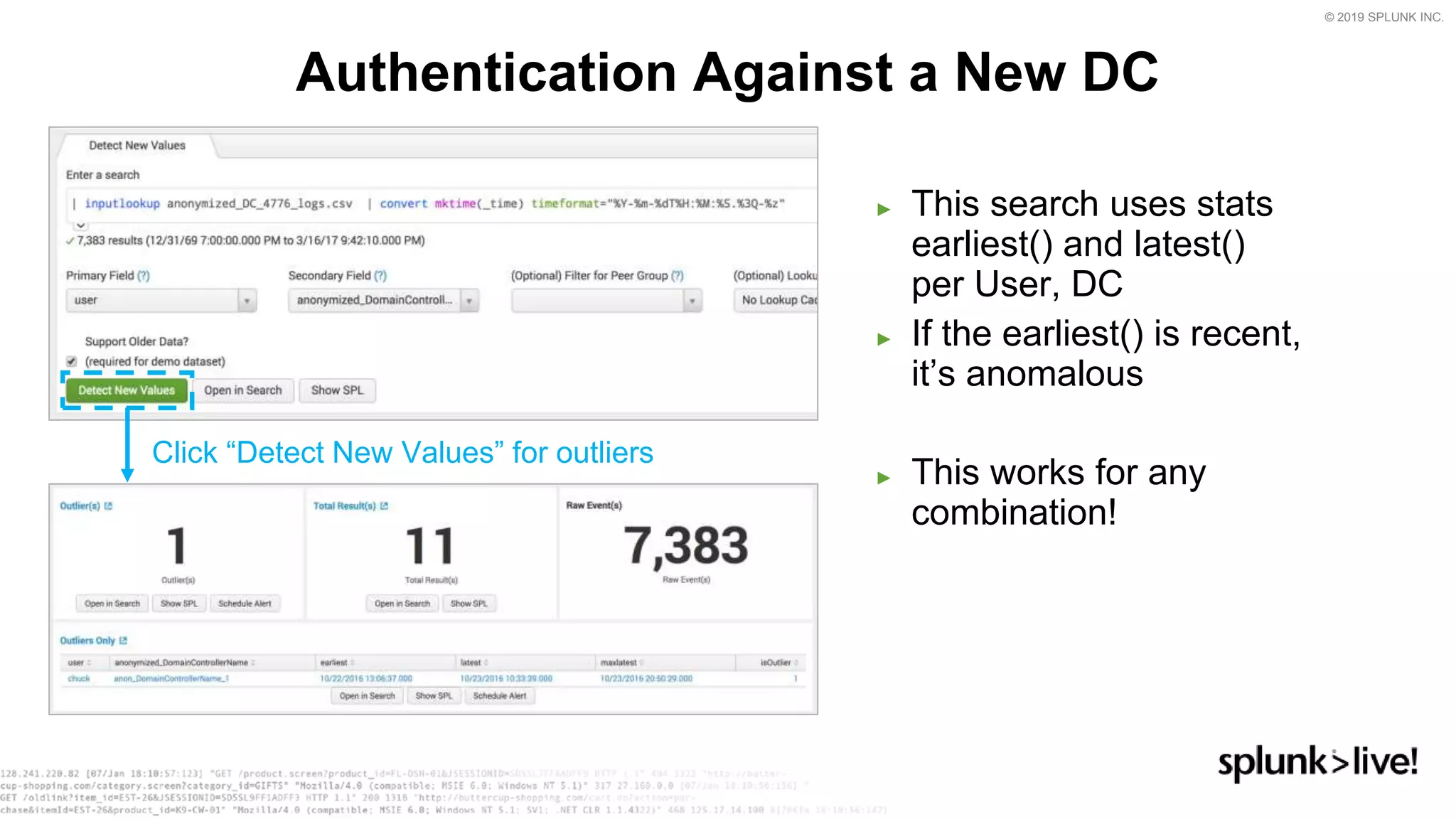
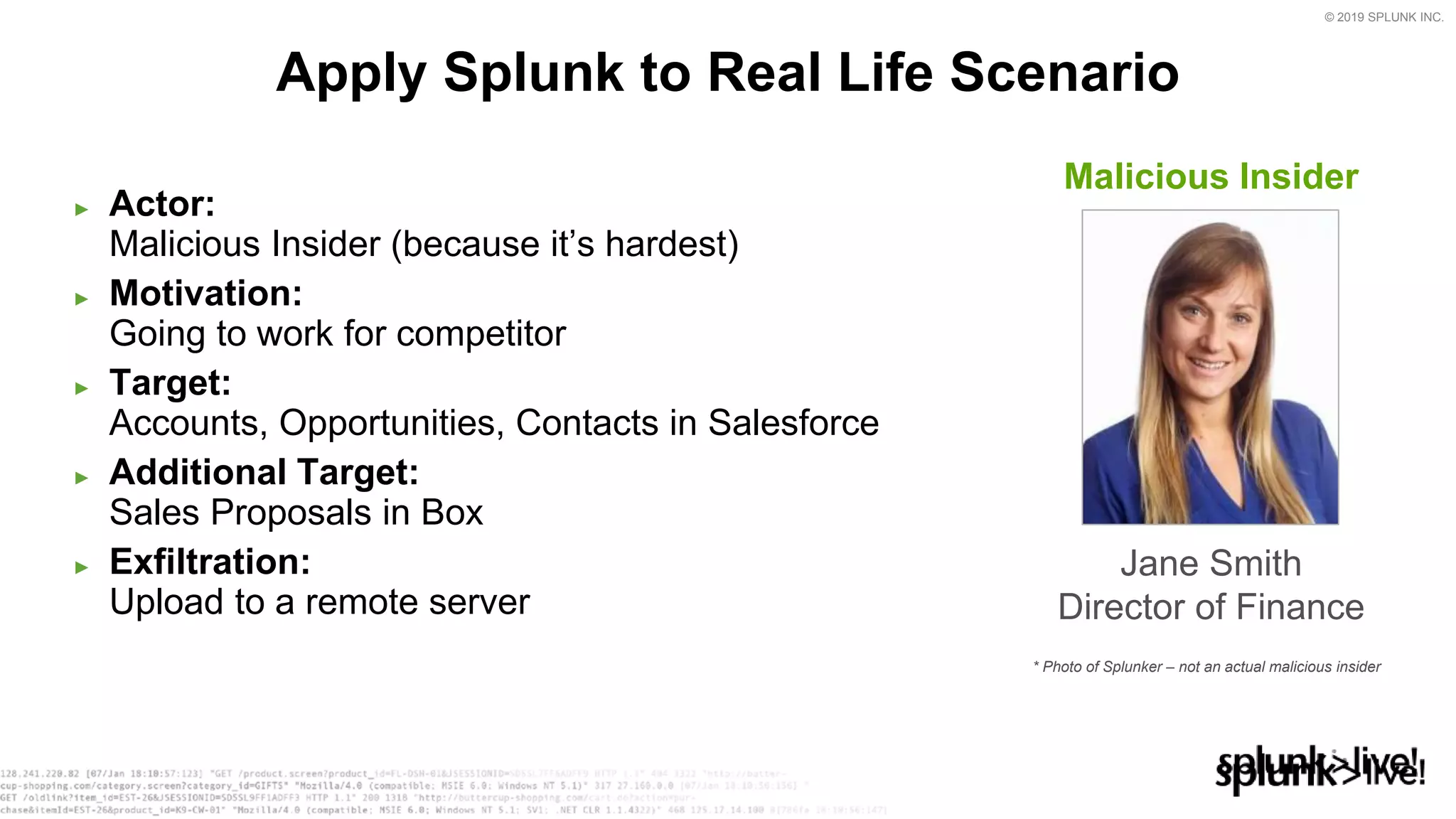
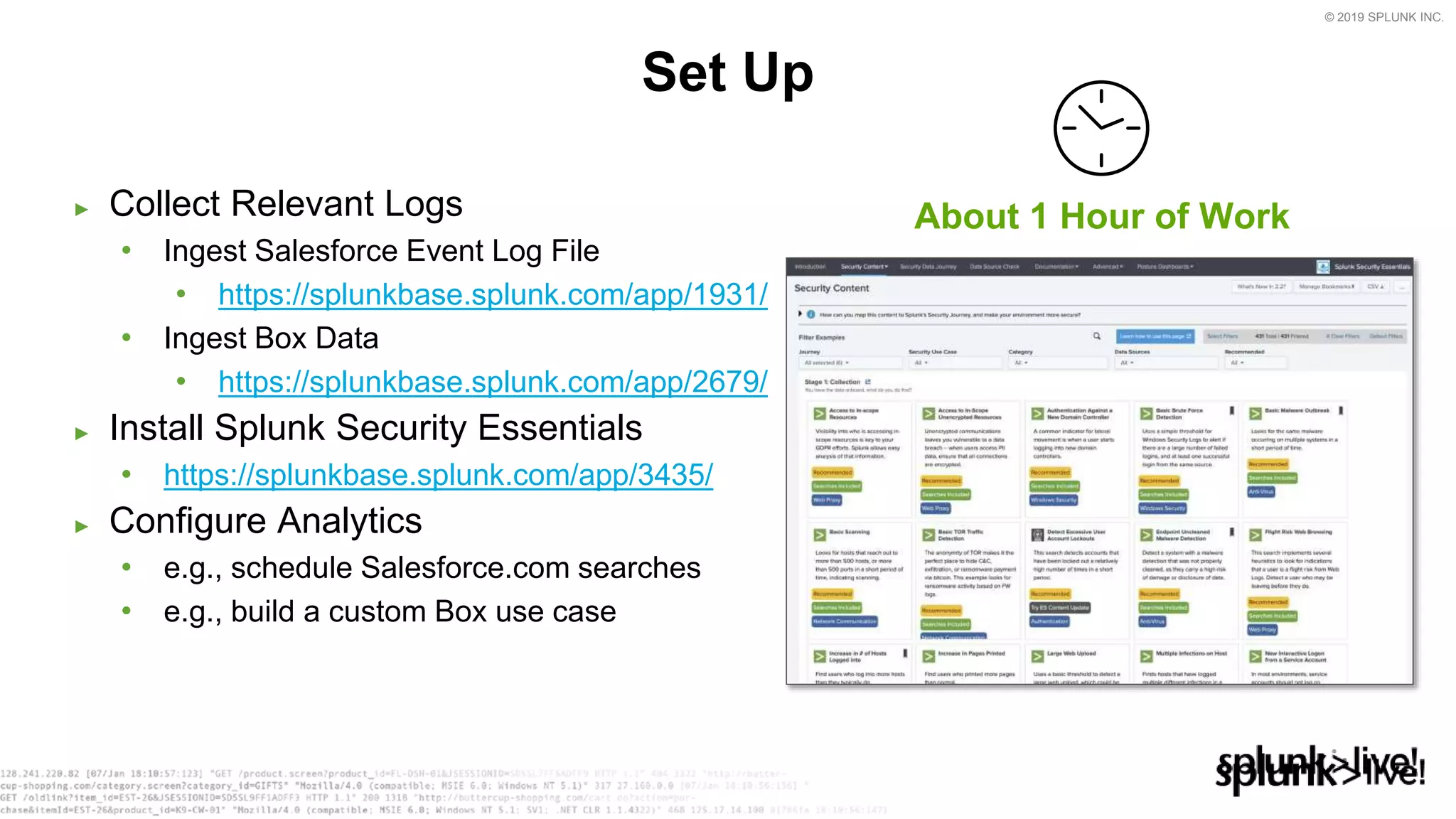
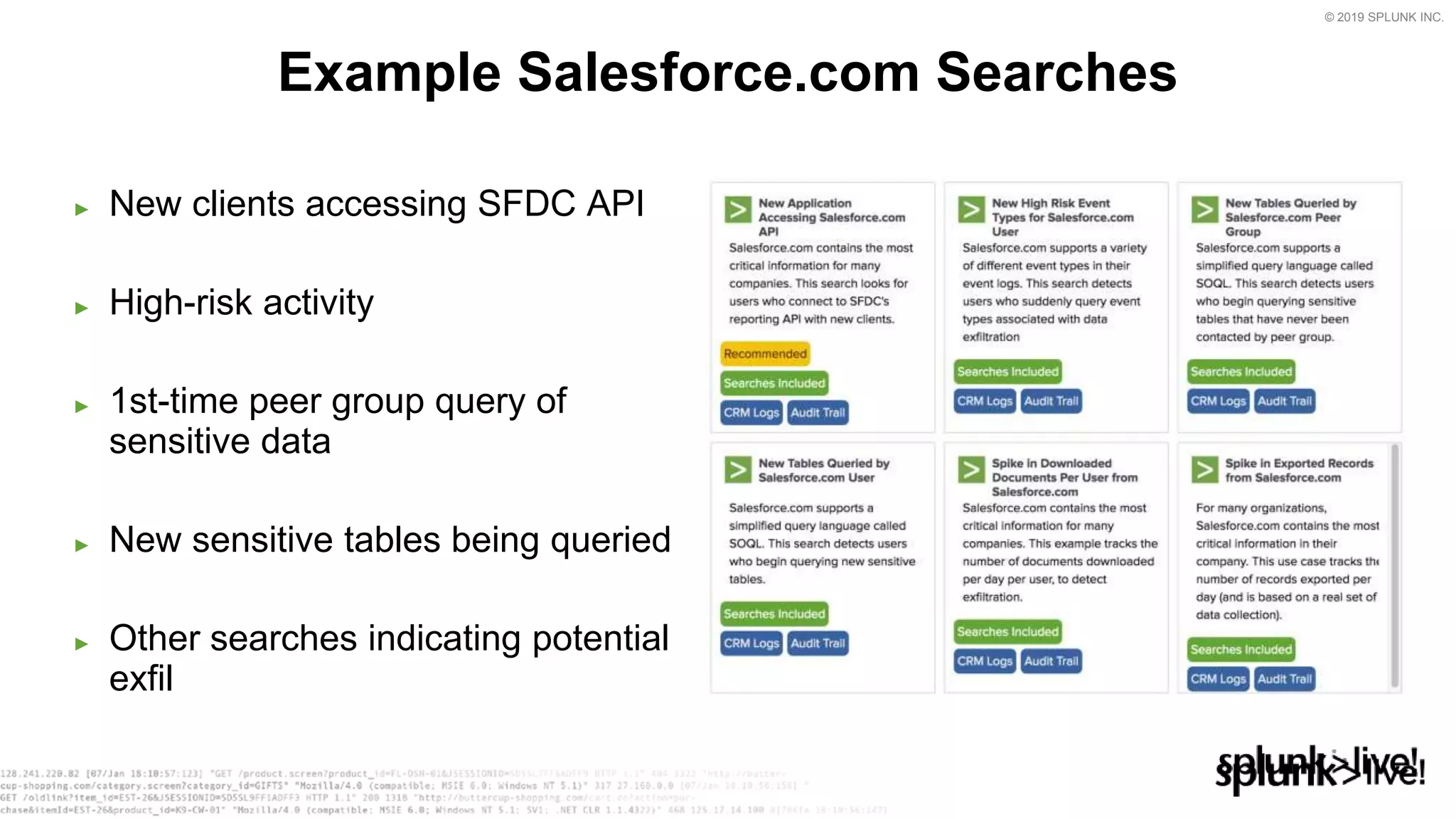
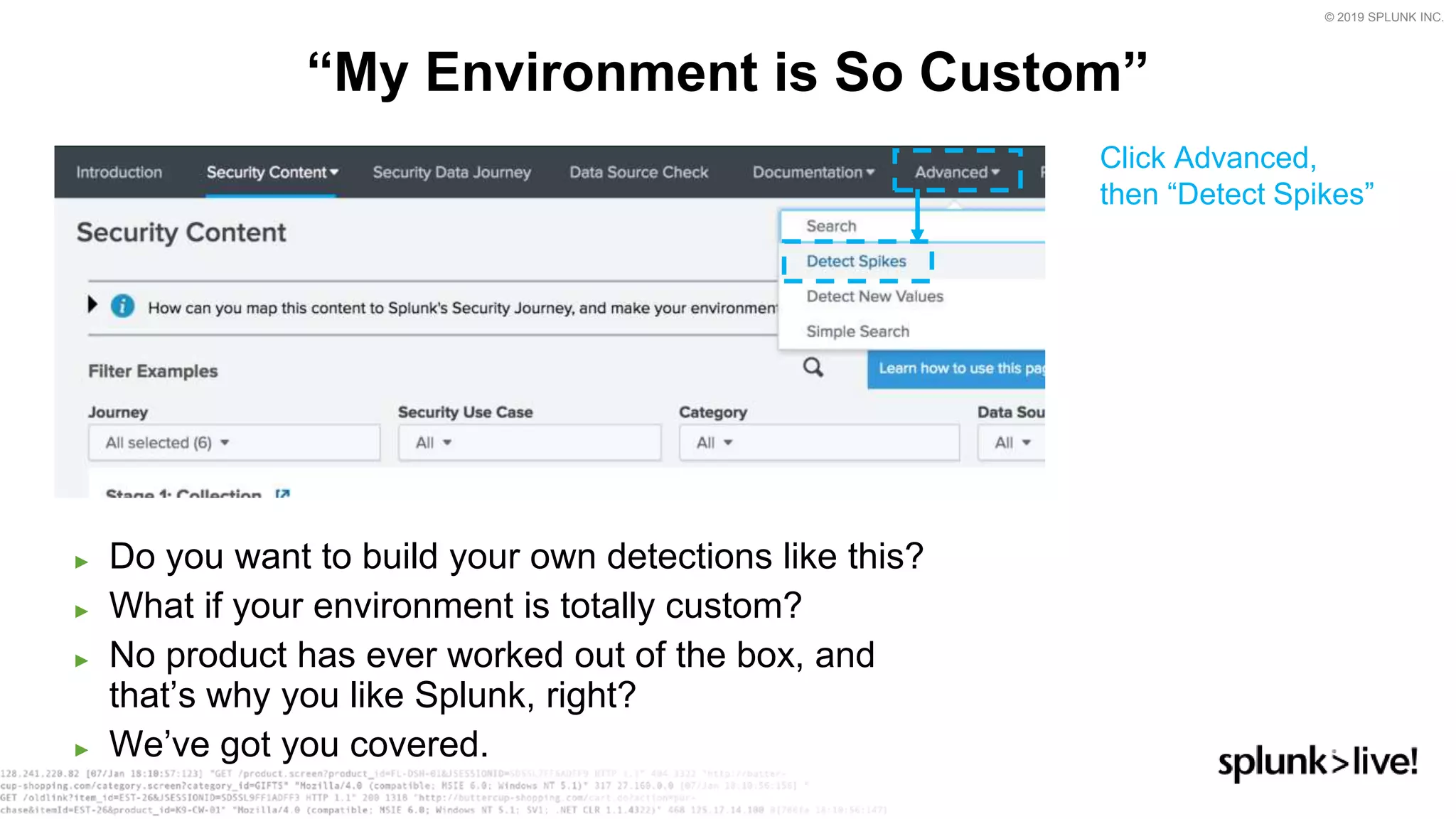
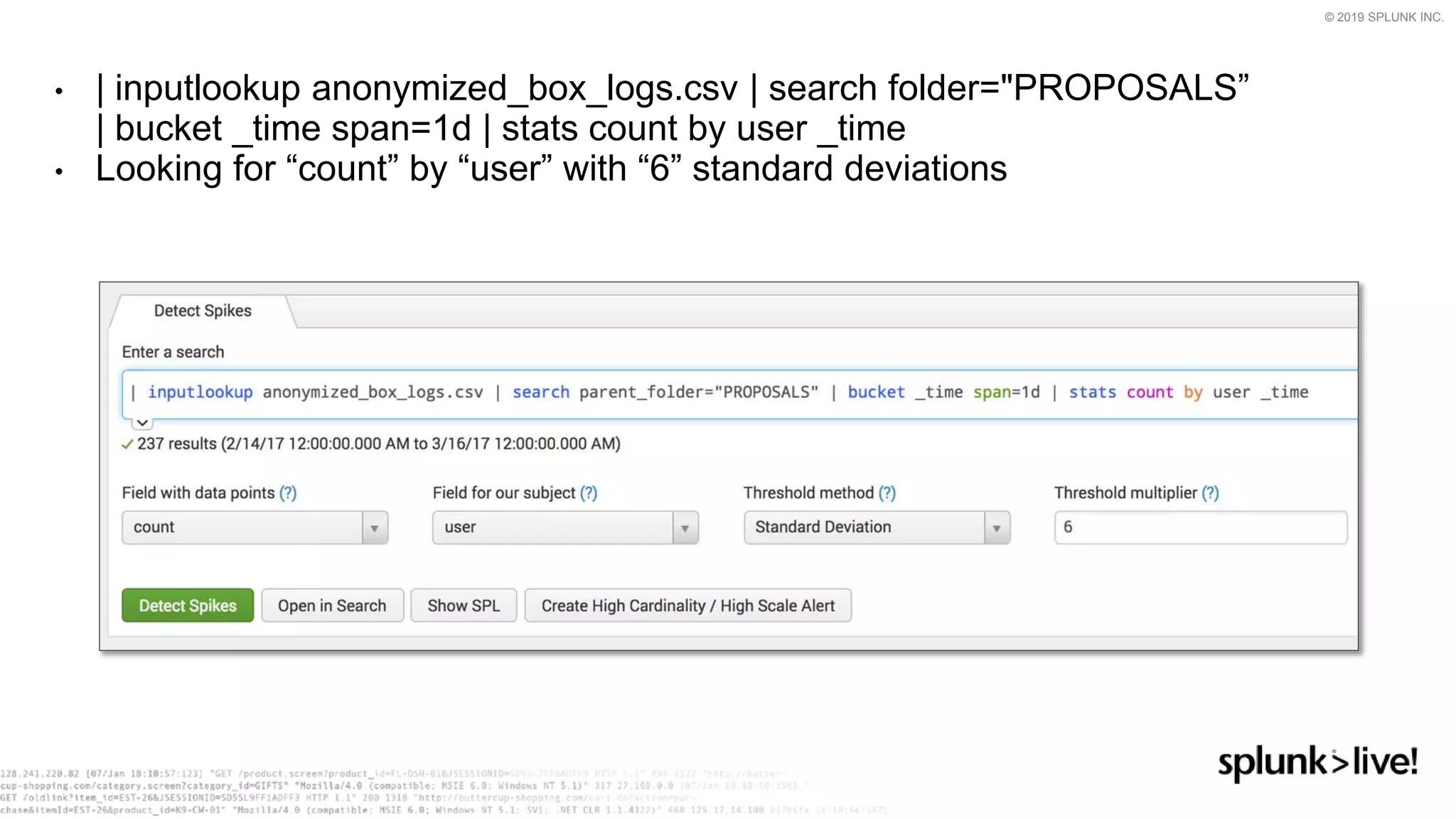
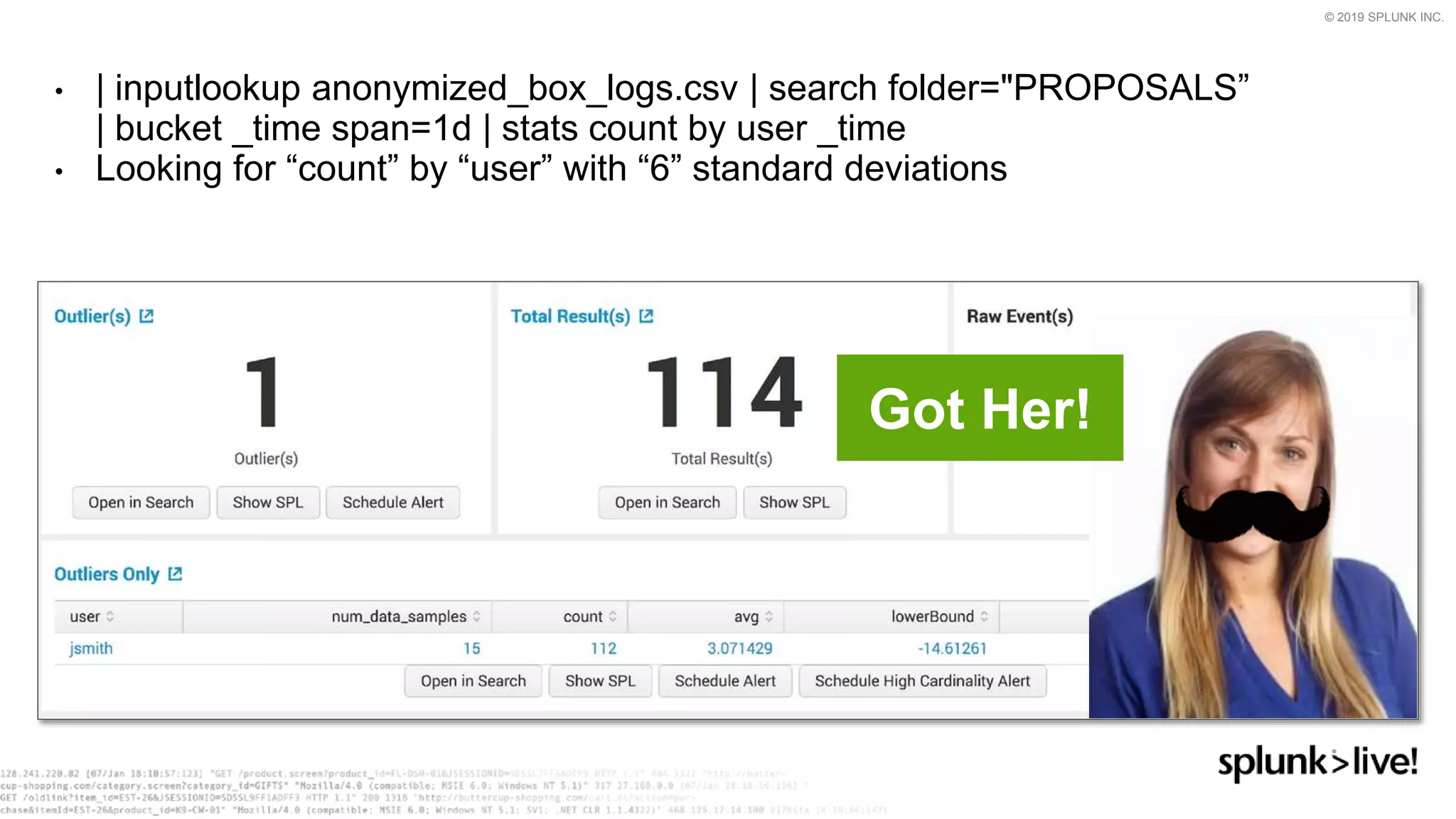
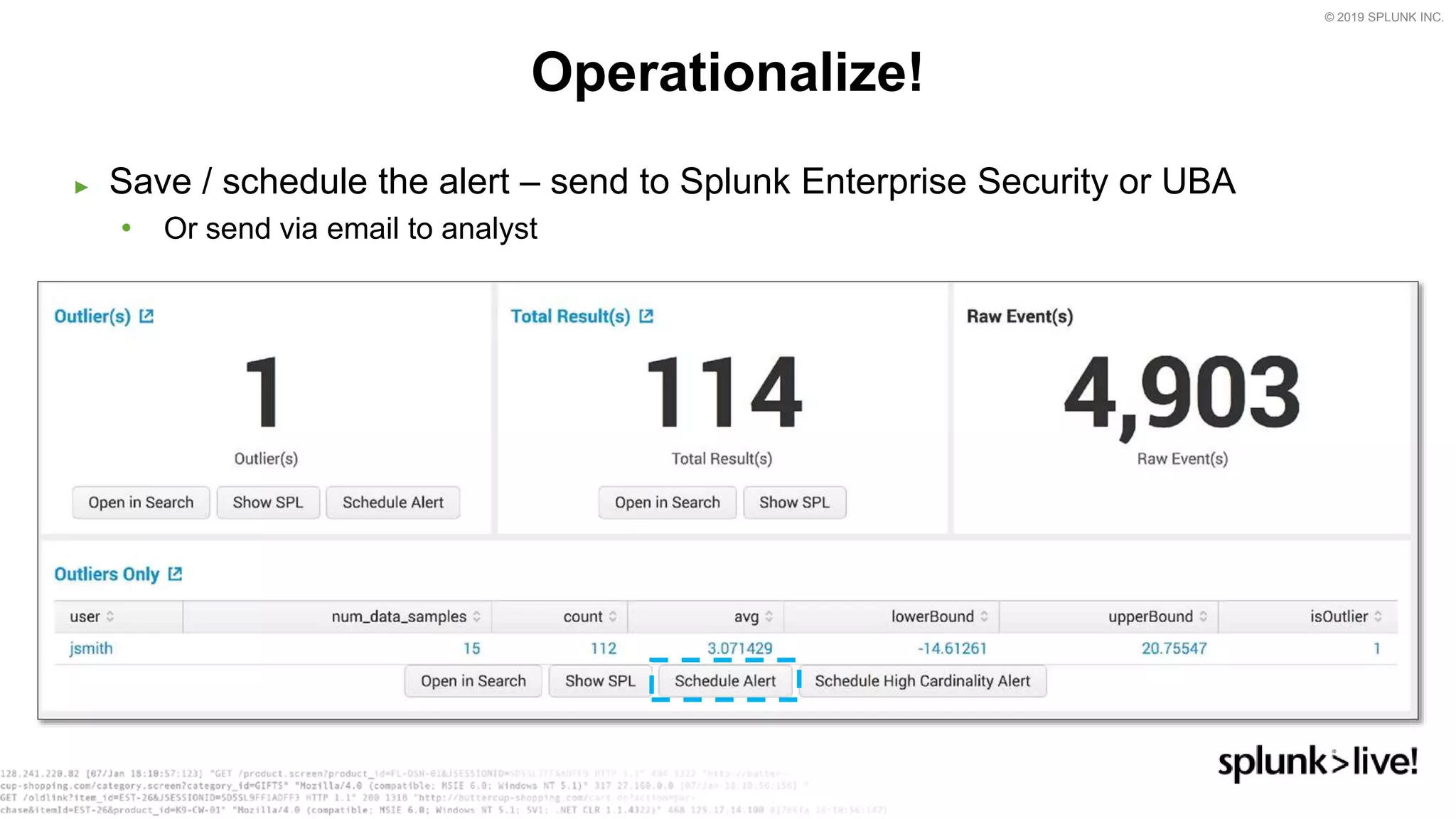
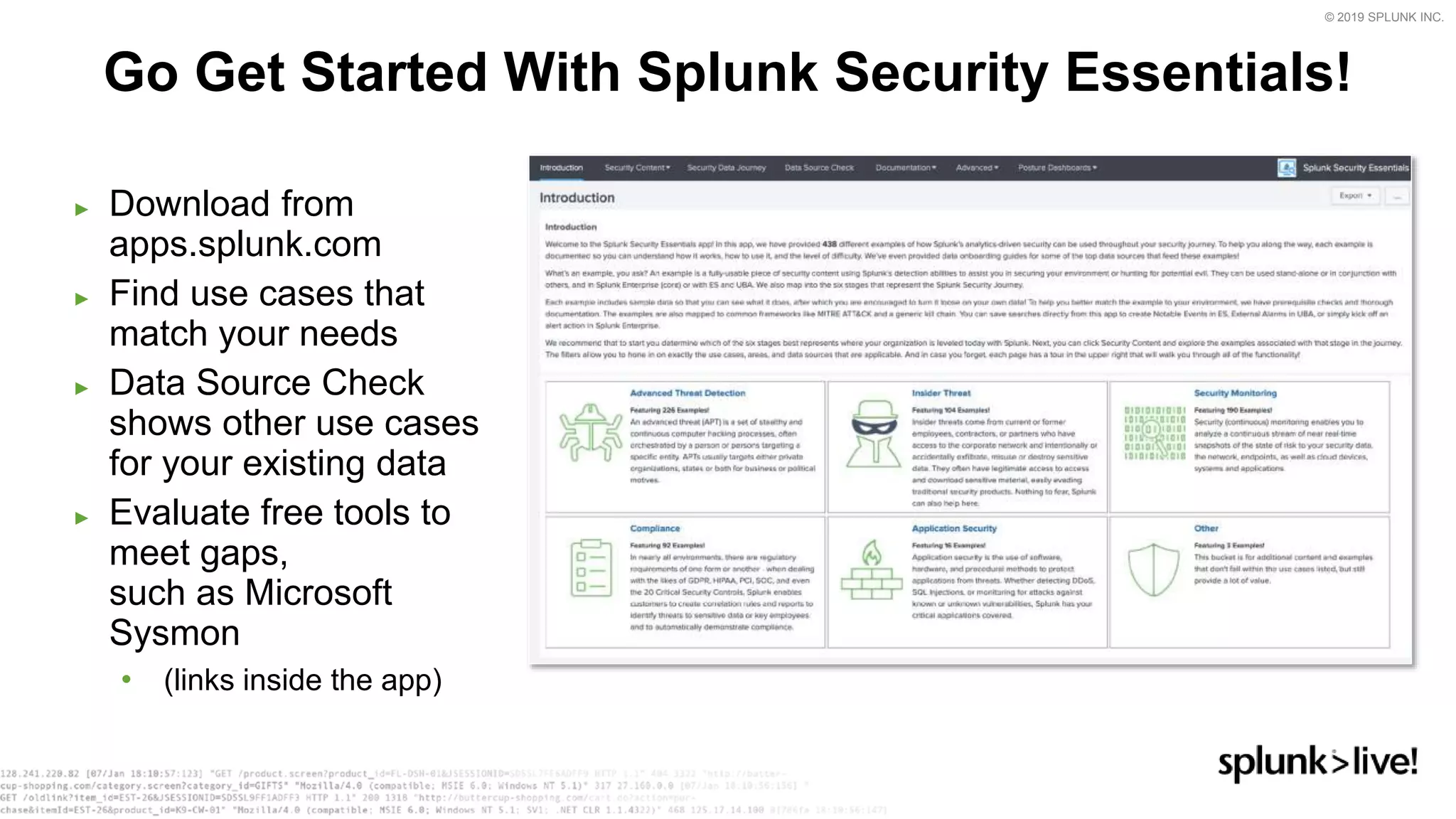
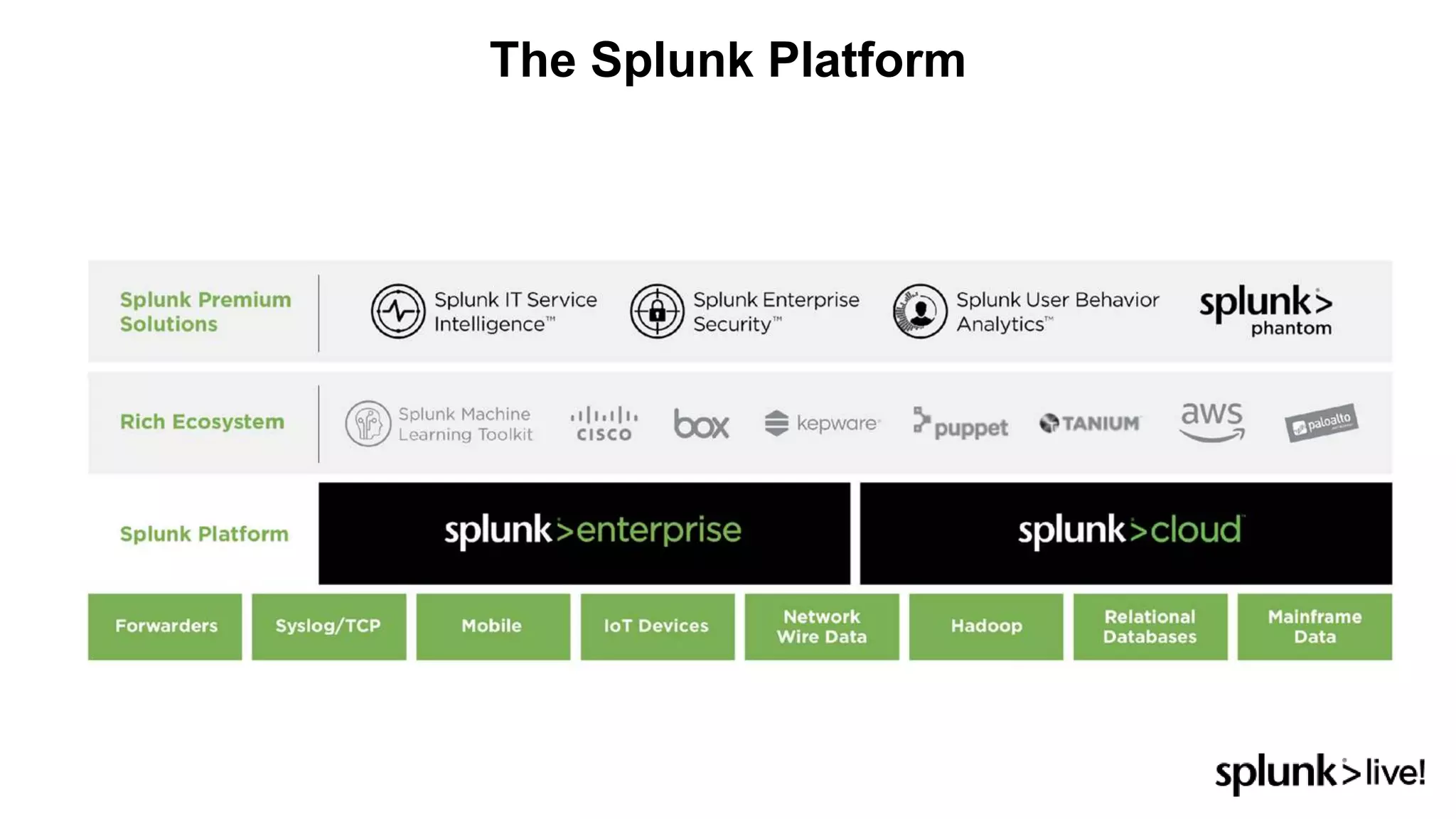
This document provides an overview and demo of Splunk Security Essentials. It begins with an introduction to the app and its capabilities for detecting threats both external and internal. It then demonstrates how to install and navigate the app to evaluate security use cases and review analytics methods. A scenario of a malicious insider exfiltrating data is presented and it shows how the app's searches could be used to detect anomalous activity related to Salesforce and Box downloads. The summary concludes by emphasizing how the app teaches detection use cases that can then be customized and integrated with Splunk's security products.