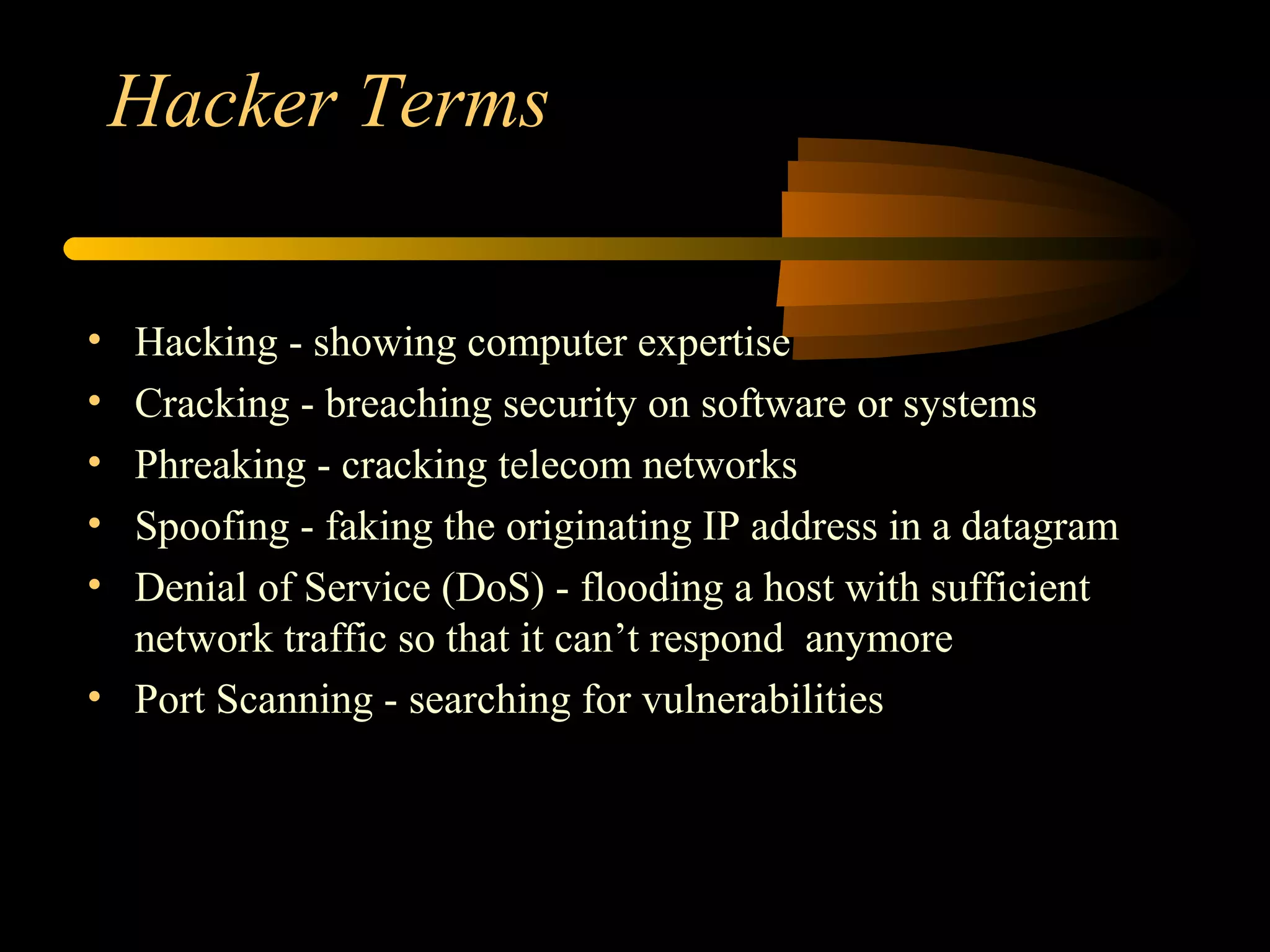
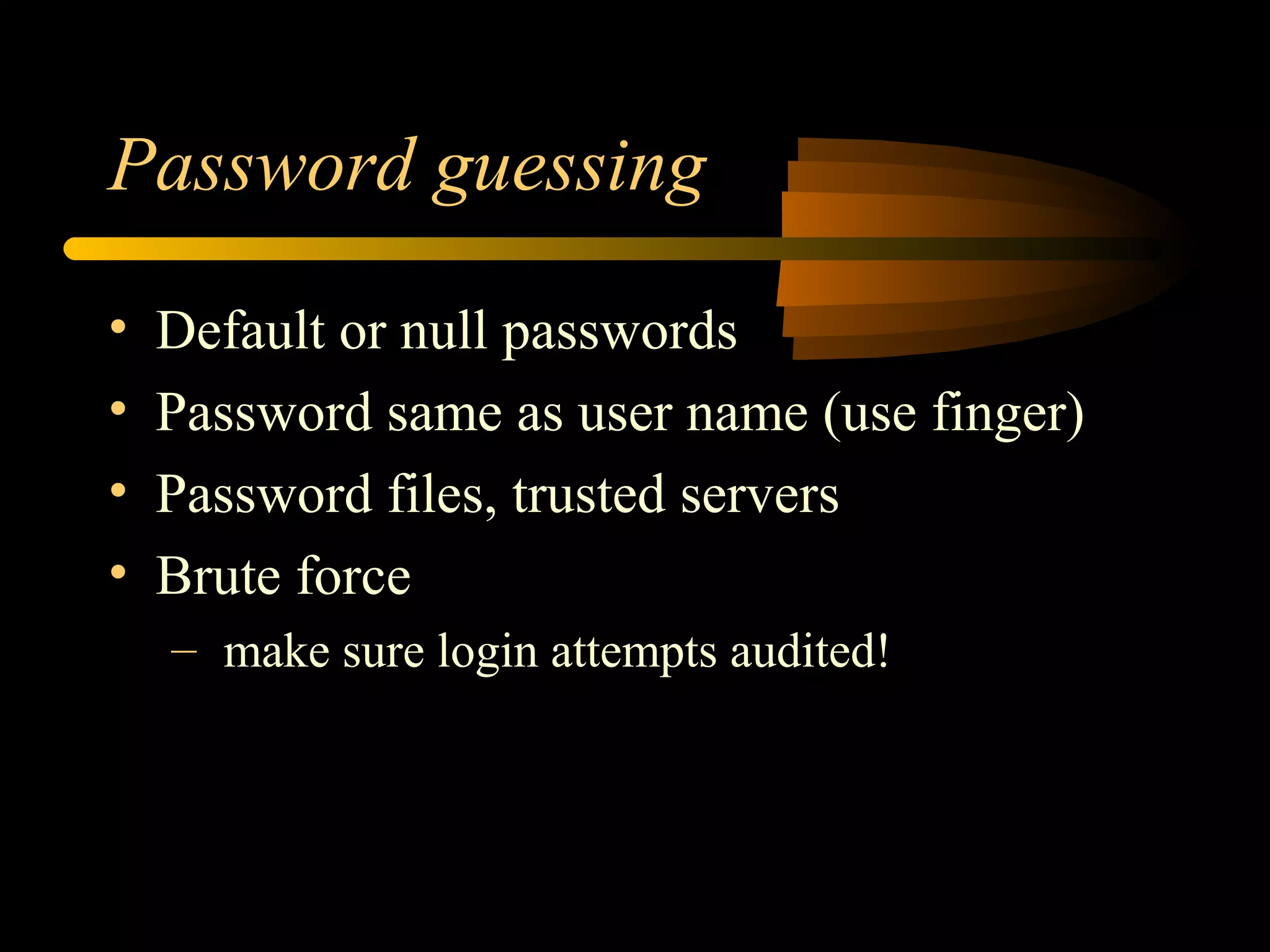
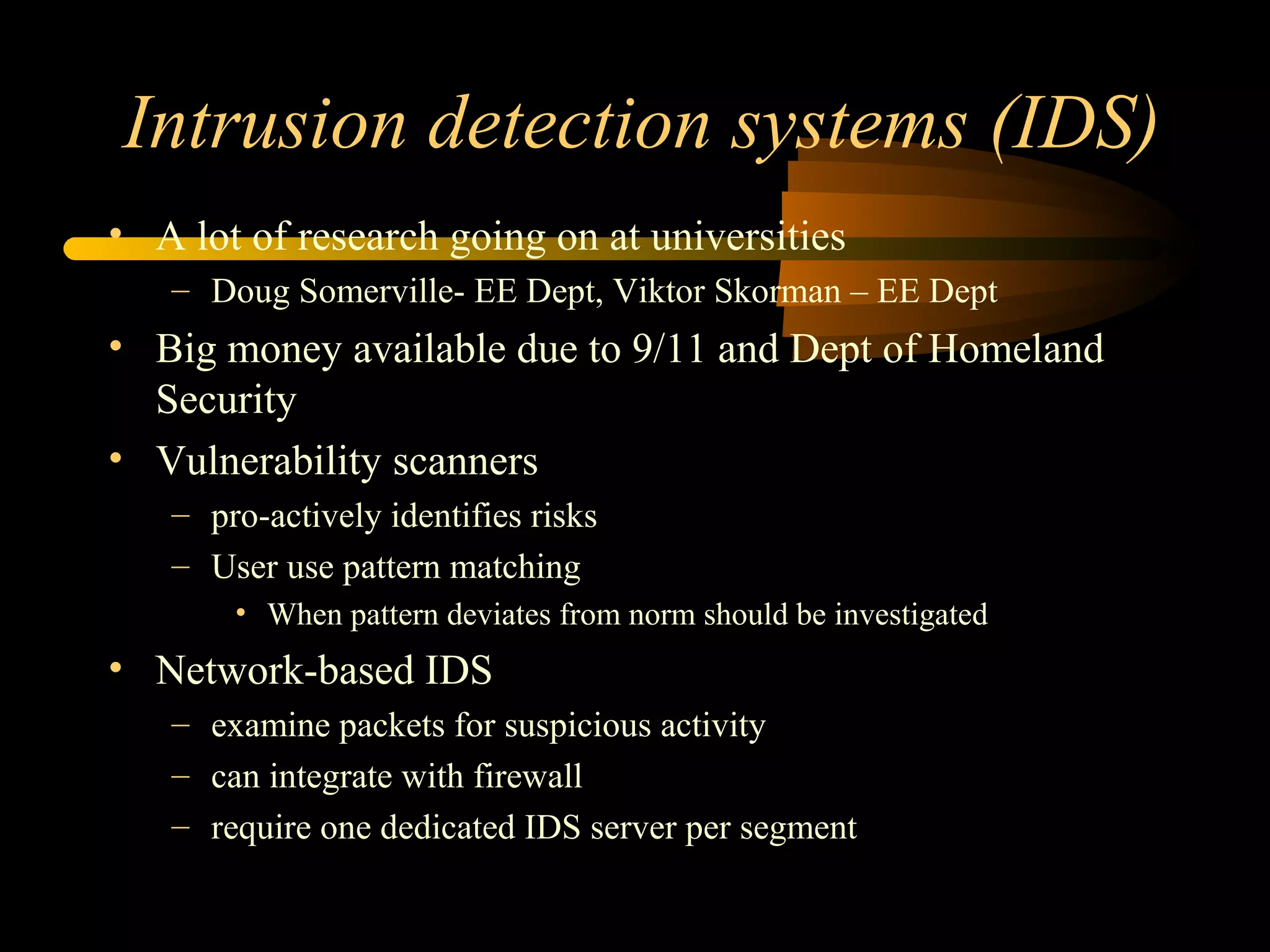
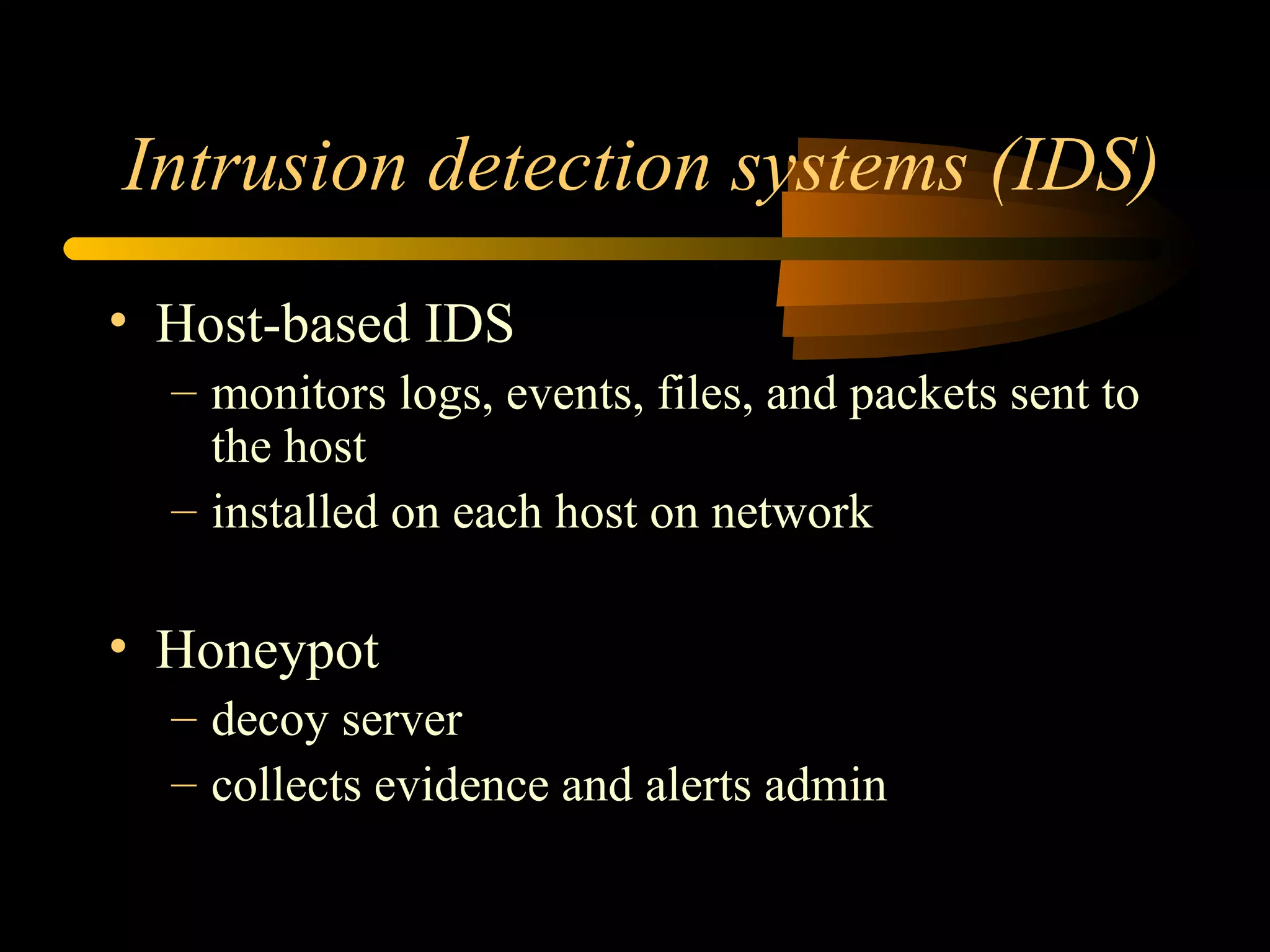
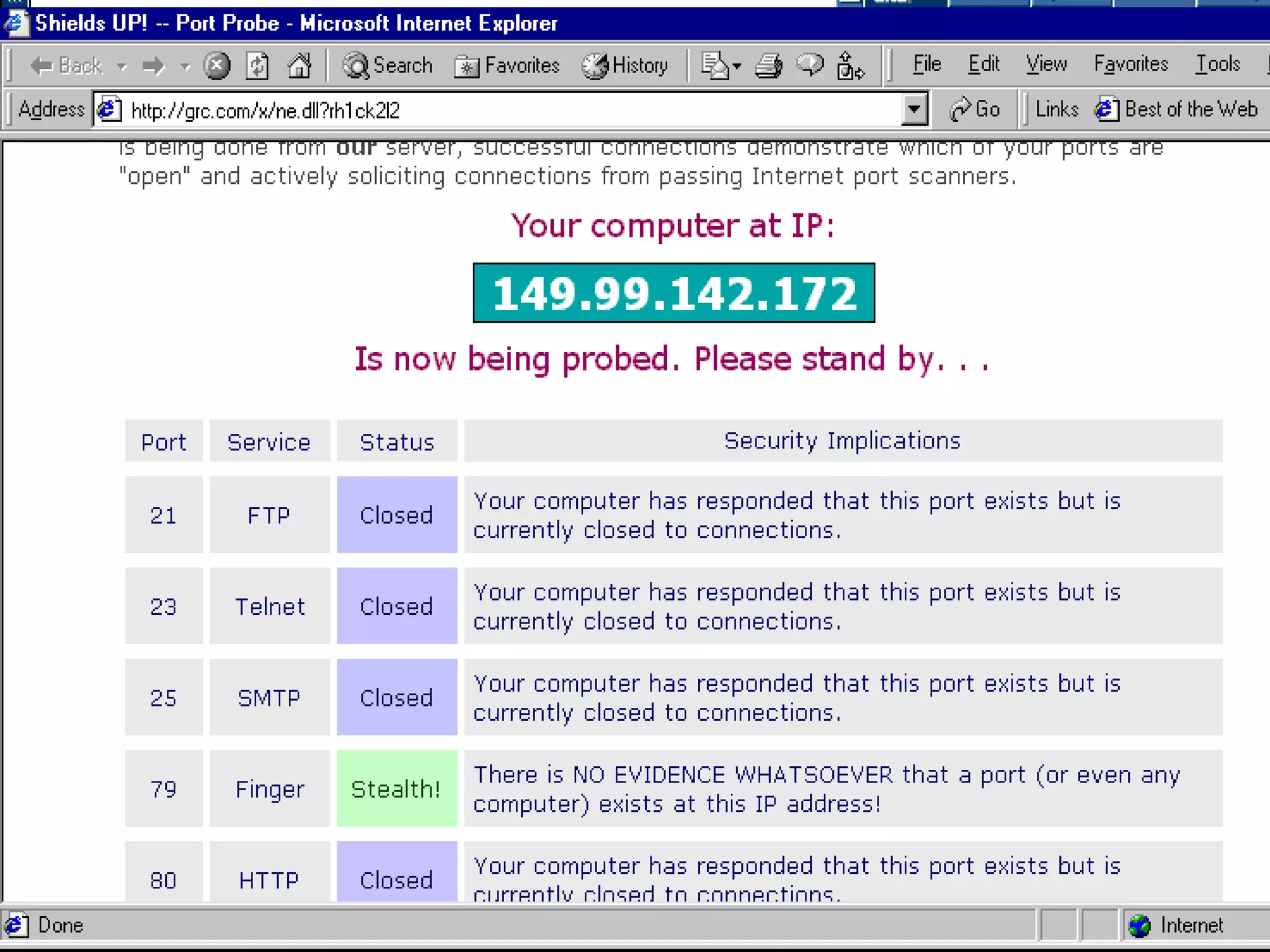
The document discusses various aspects of hacking, including definitions, types of hackers, intrusion techniques, and associated threats. It also covers the evolution of hacking incidents, legal and ethical questions regarding hacking practices, and the importance of intrusion detection and prevention systems. Additionally, it outlines computer crimes, relevant federal statutes, and the ramifications of hacking activities.