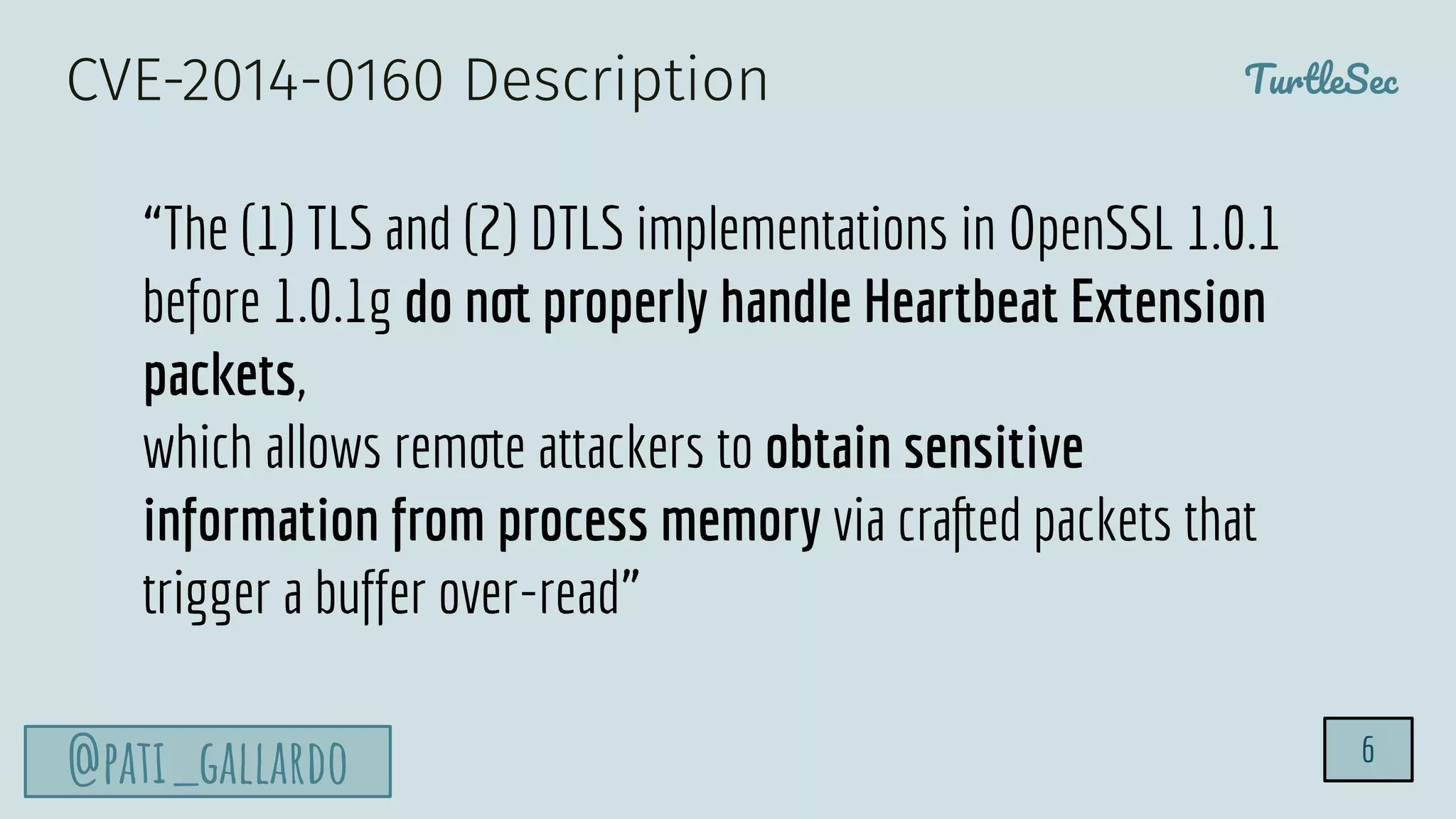
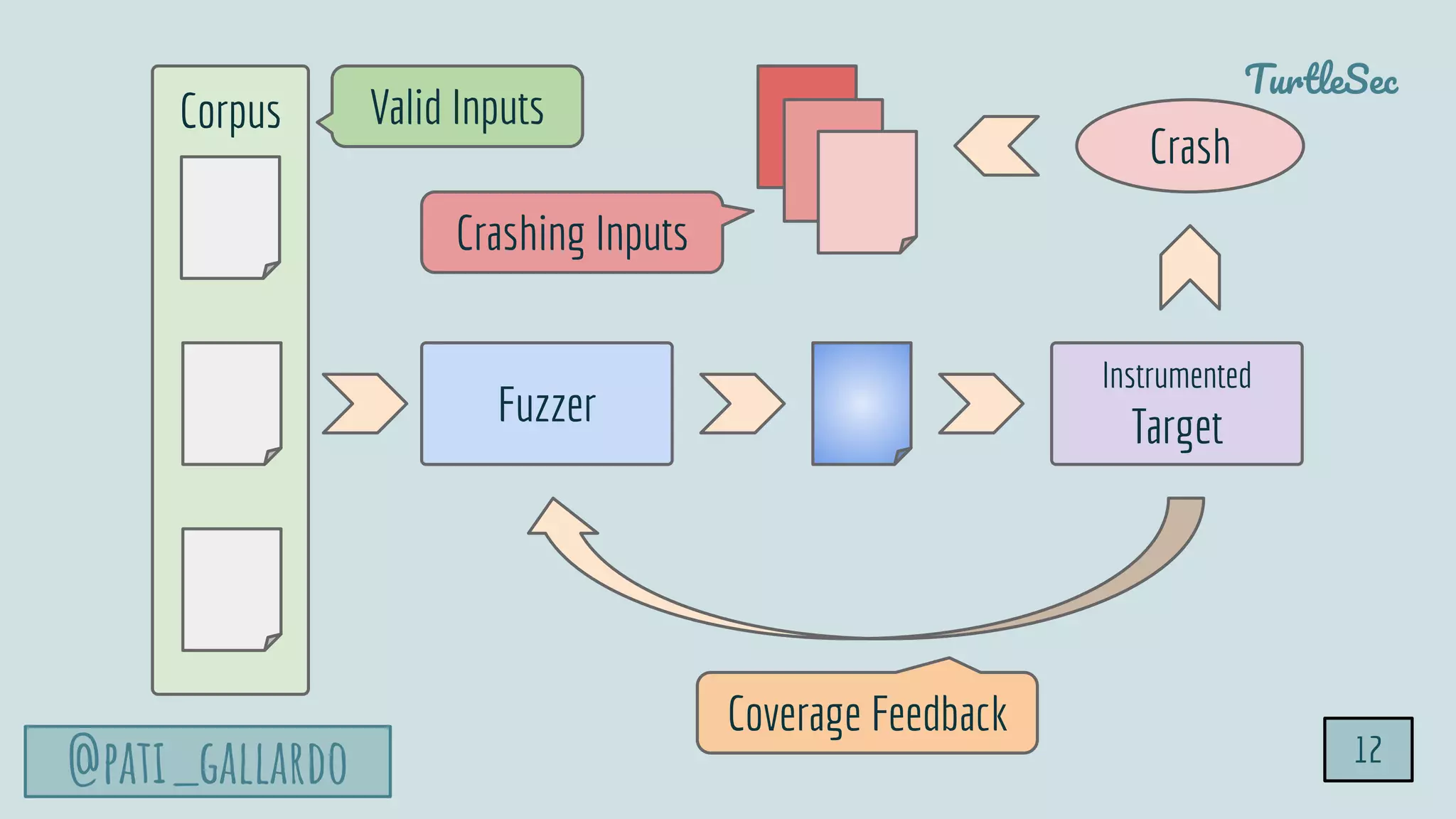
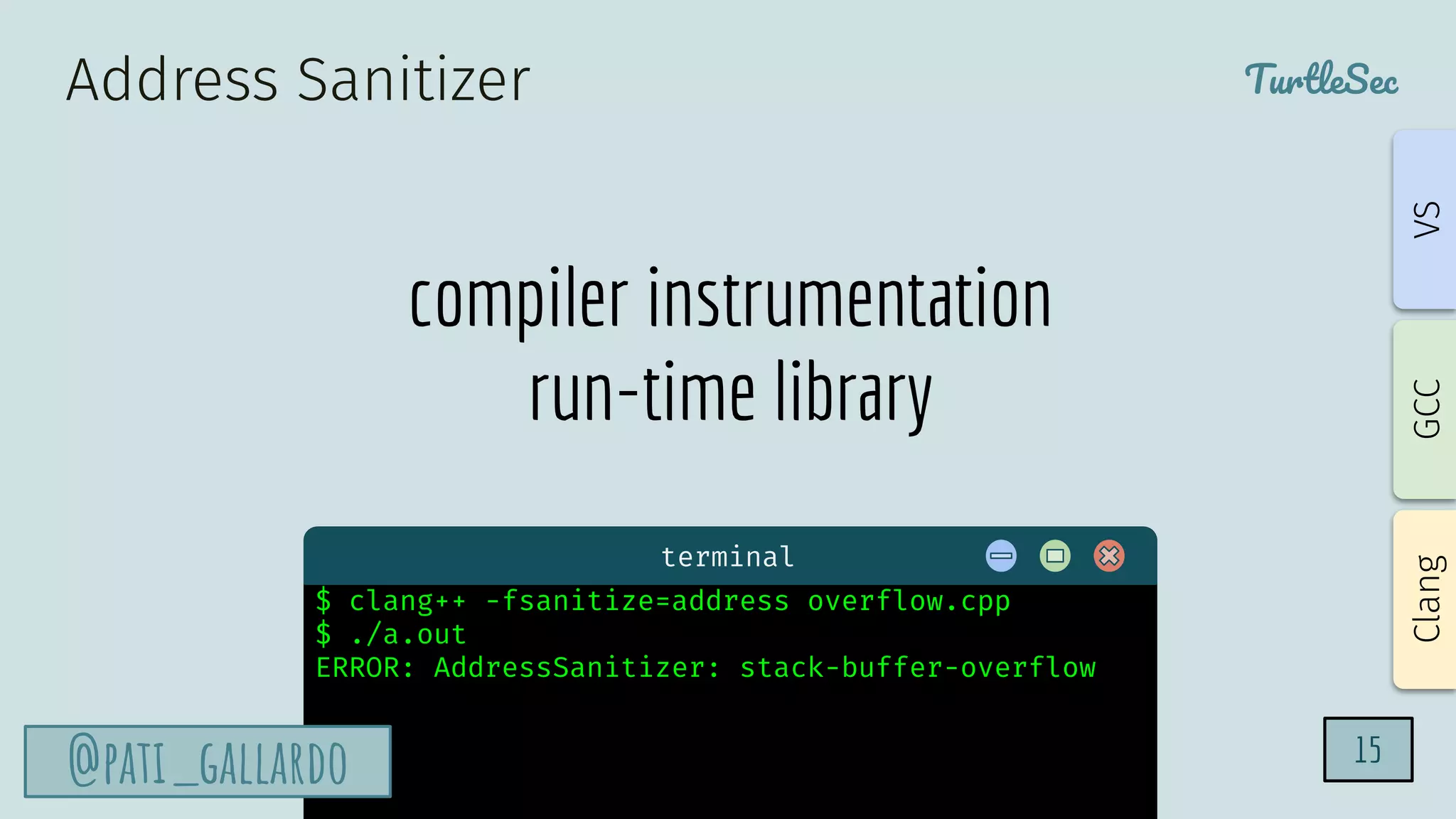
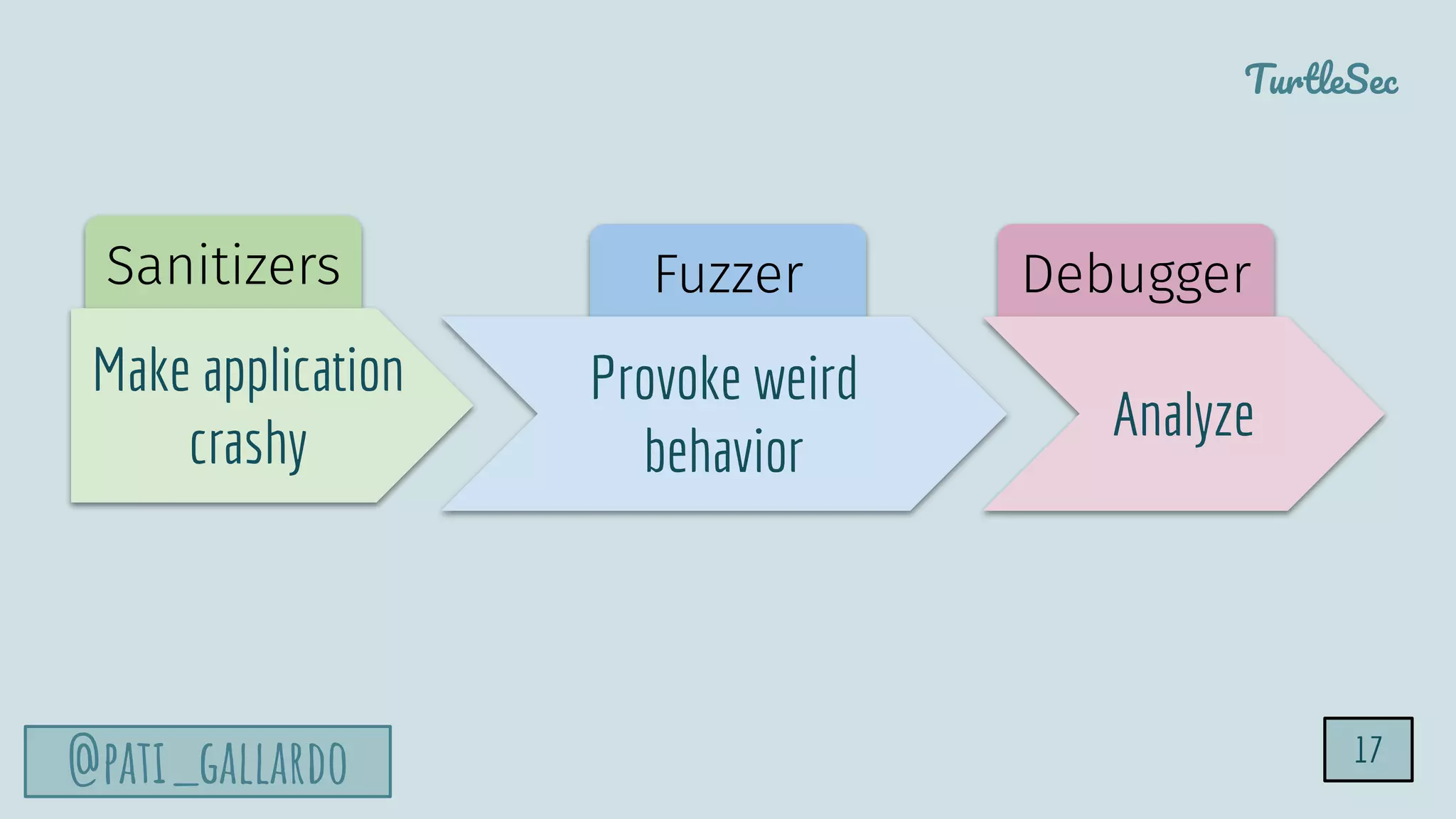
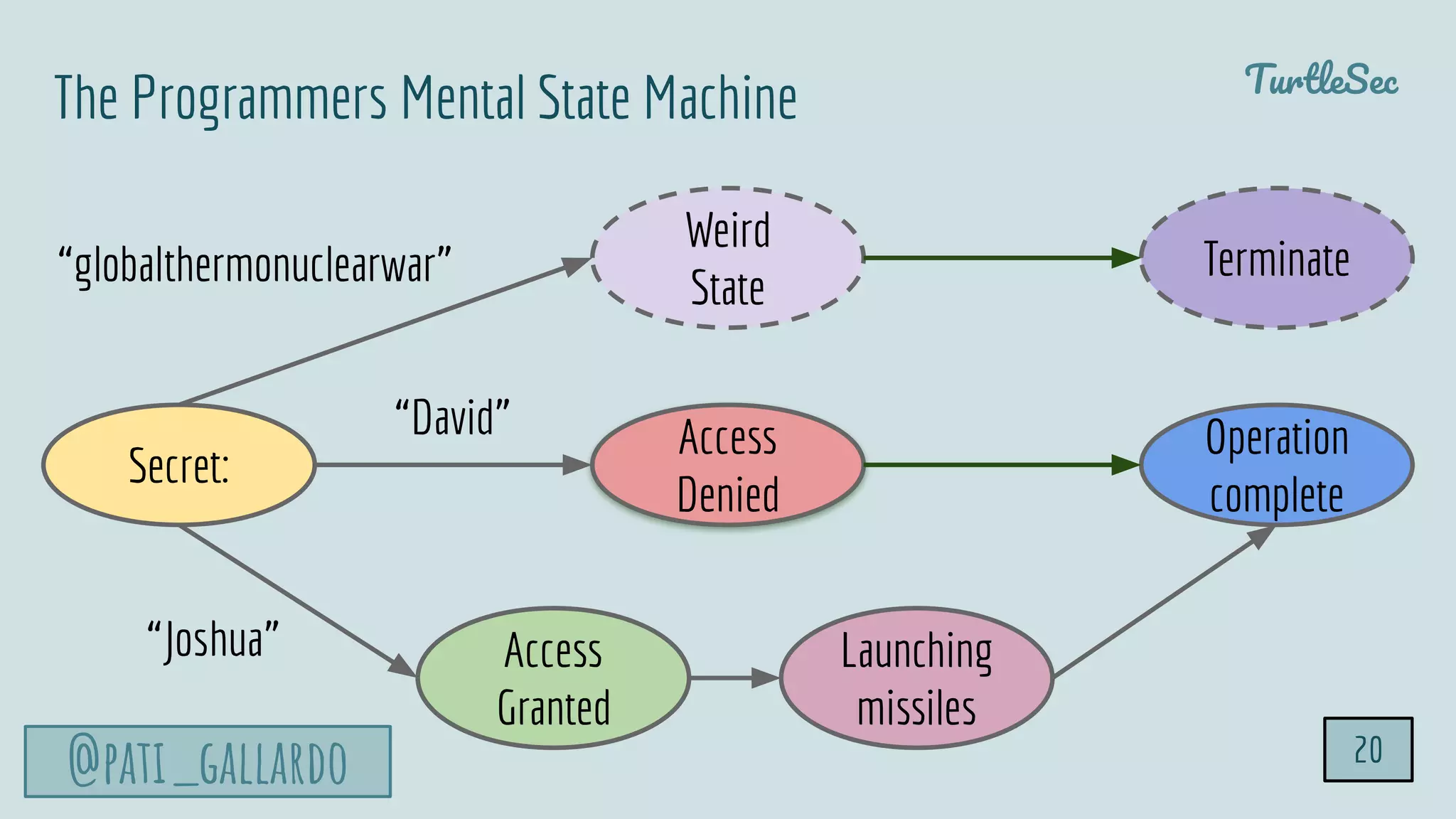
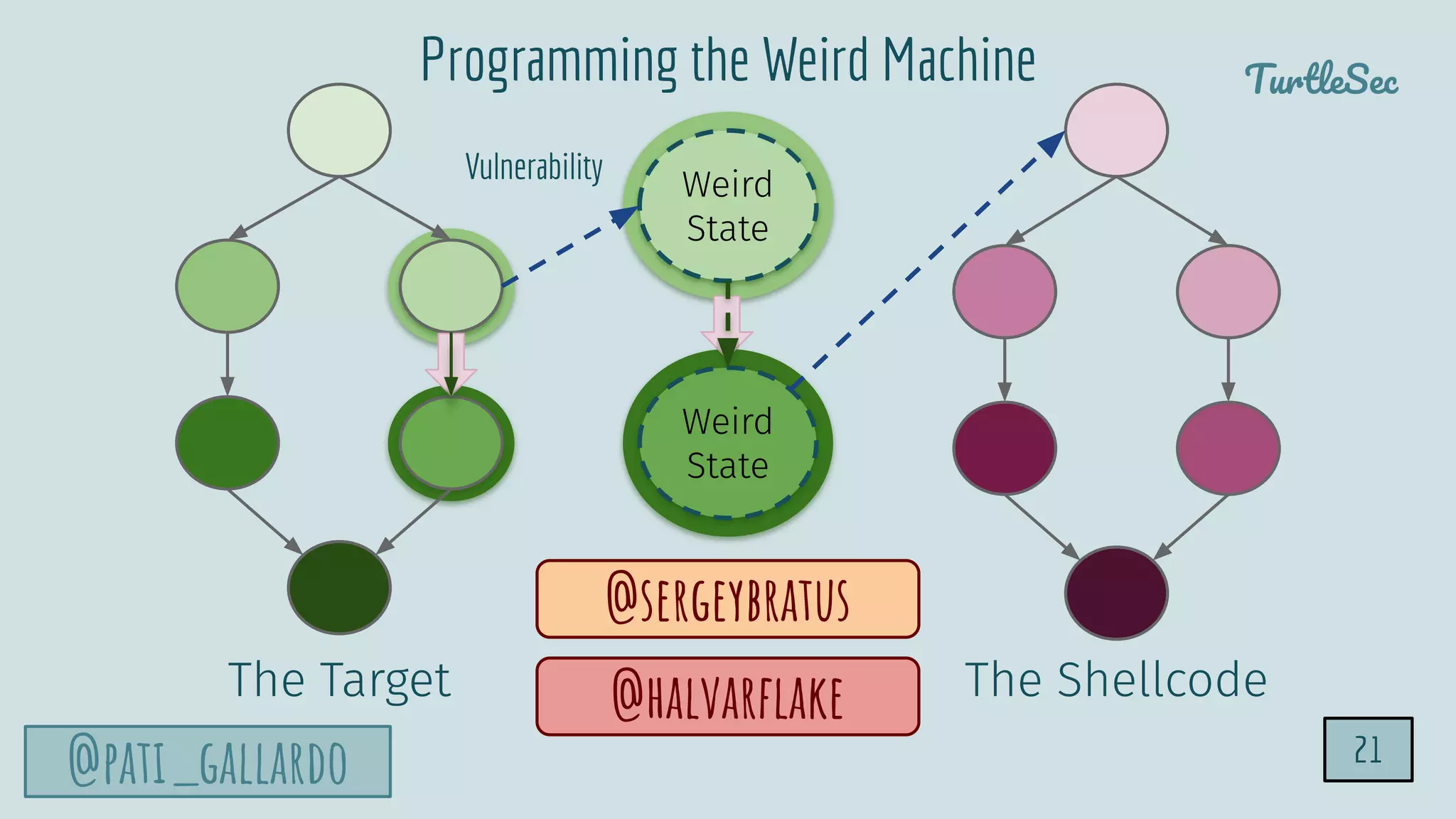
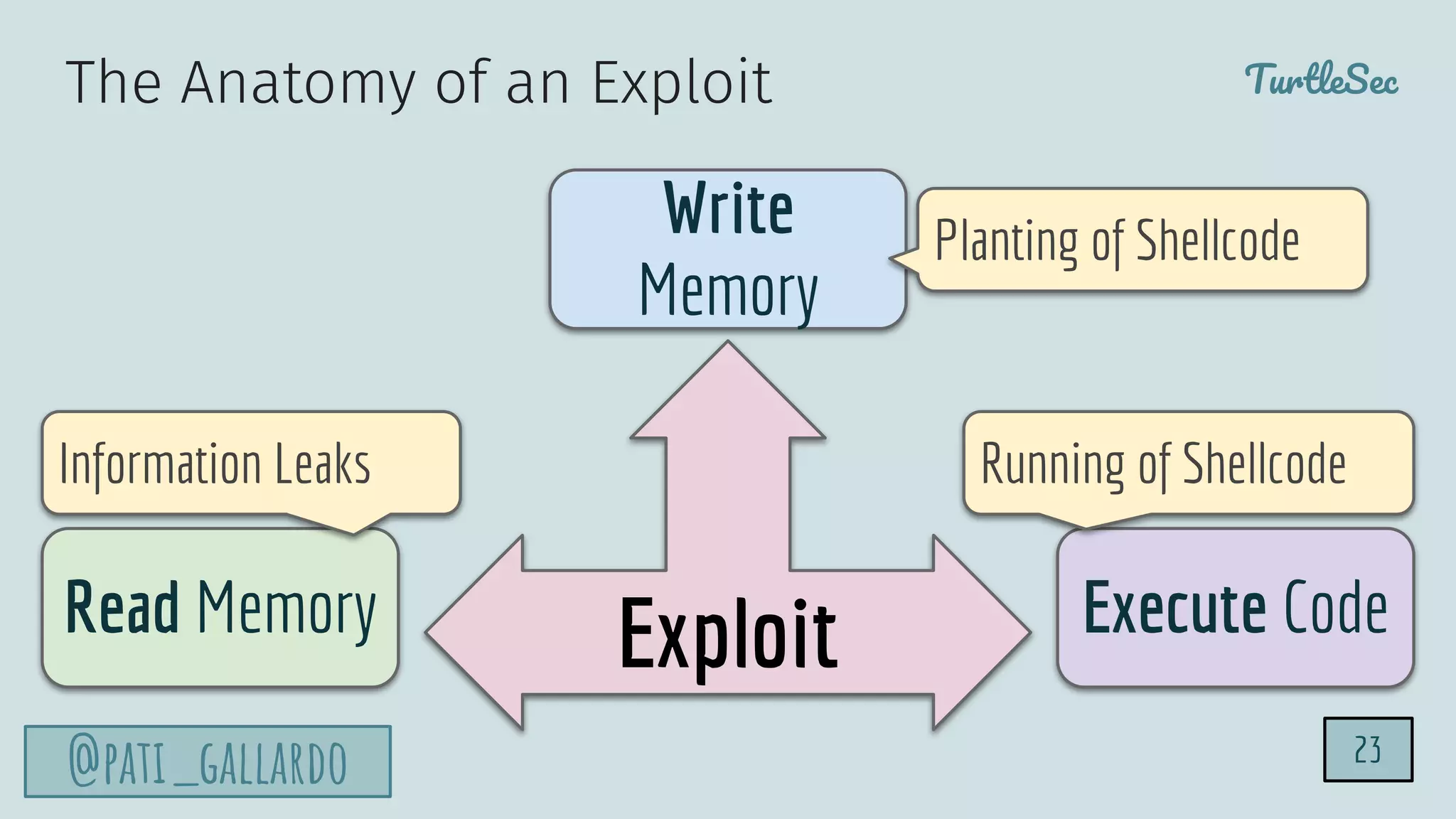
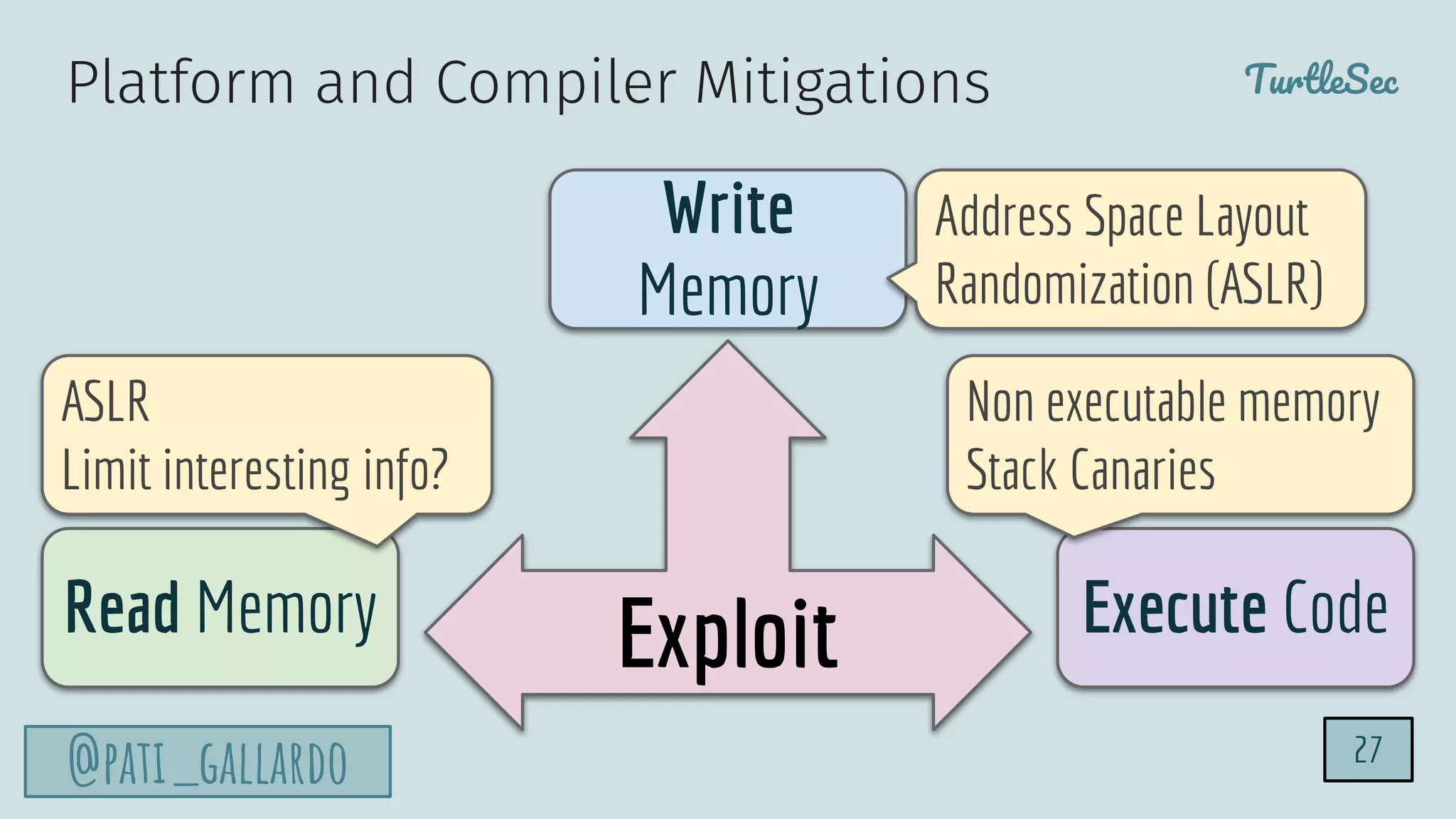
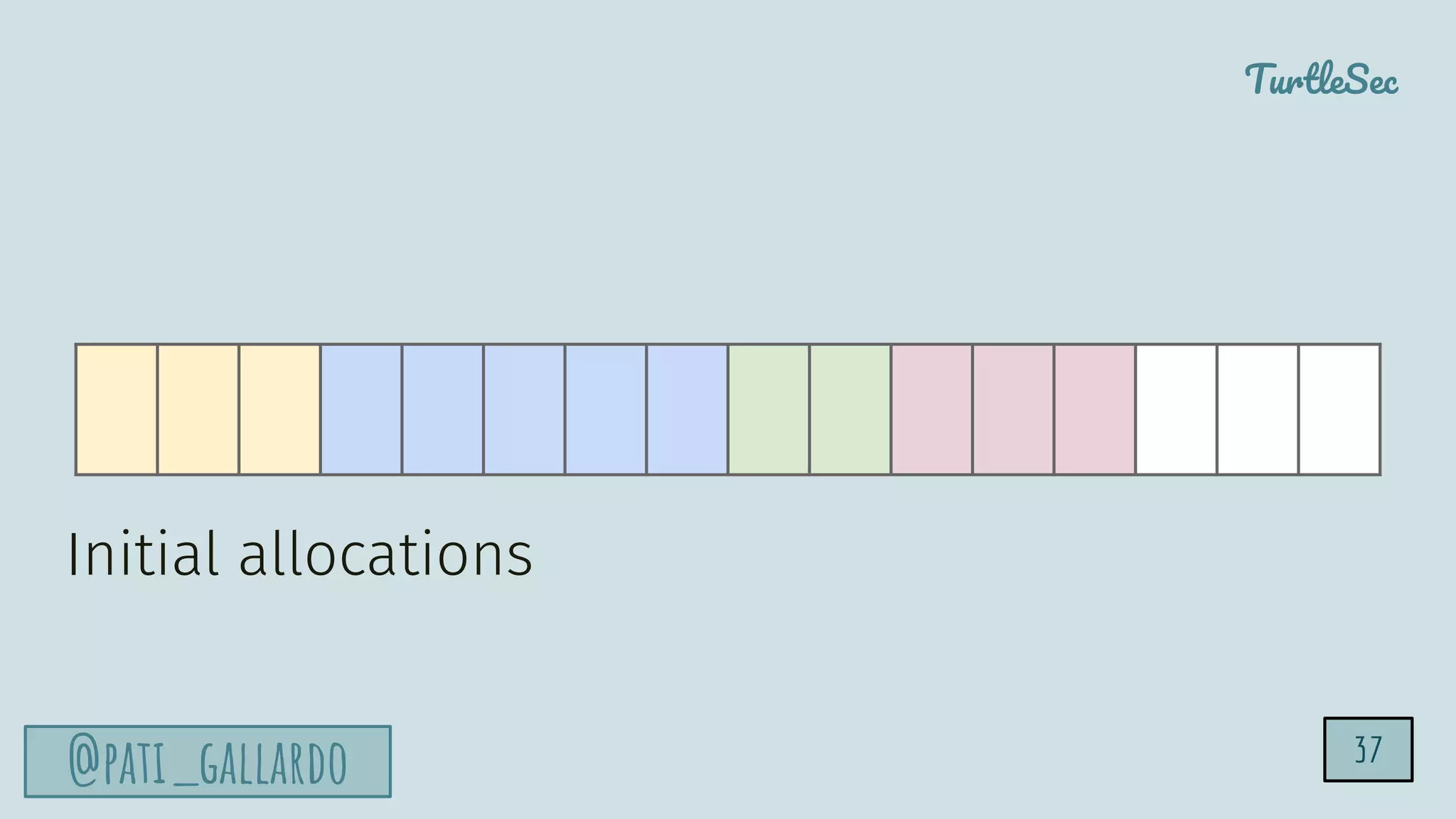
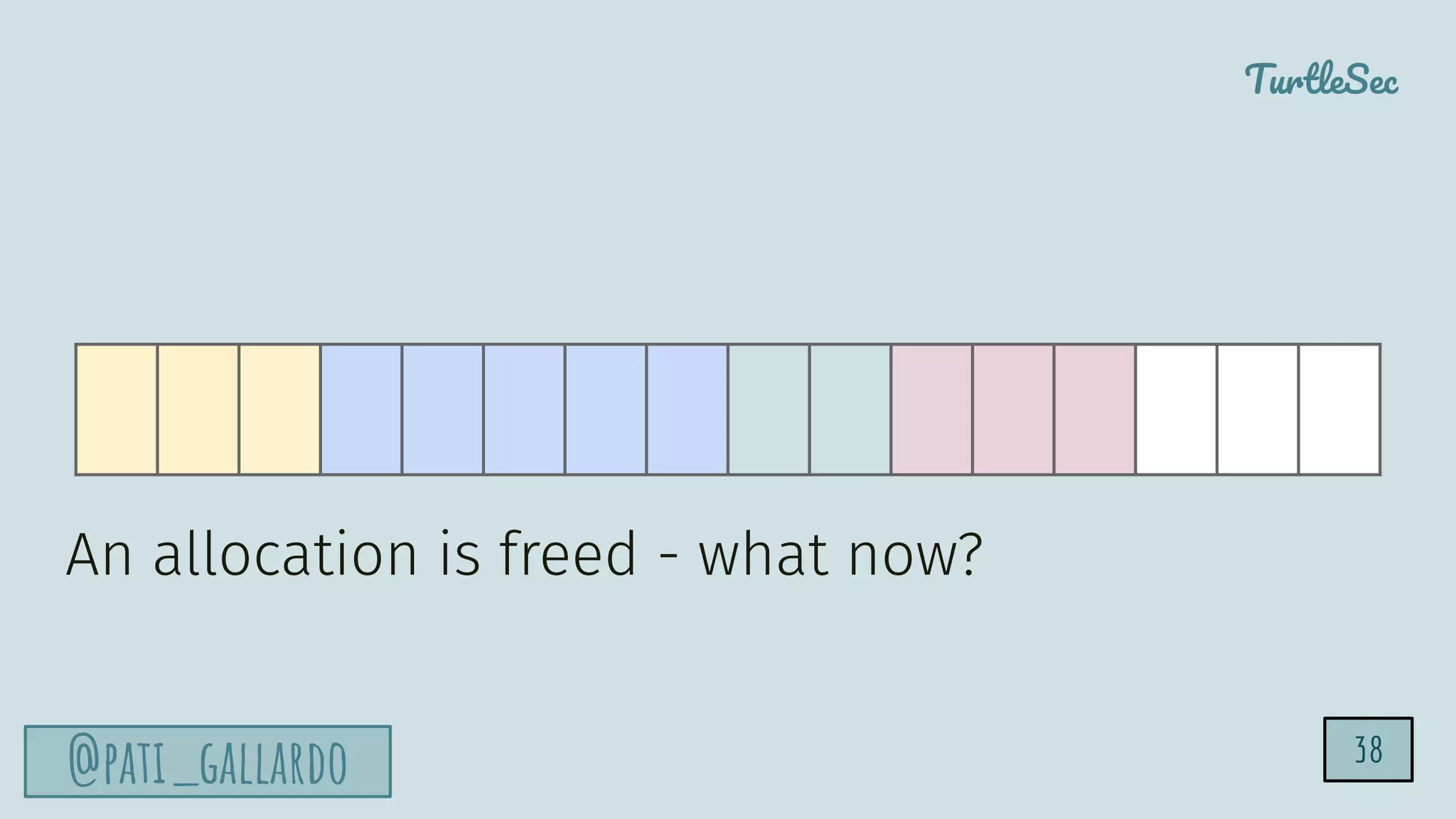
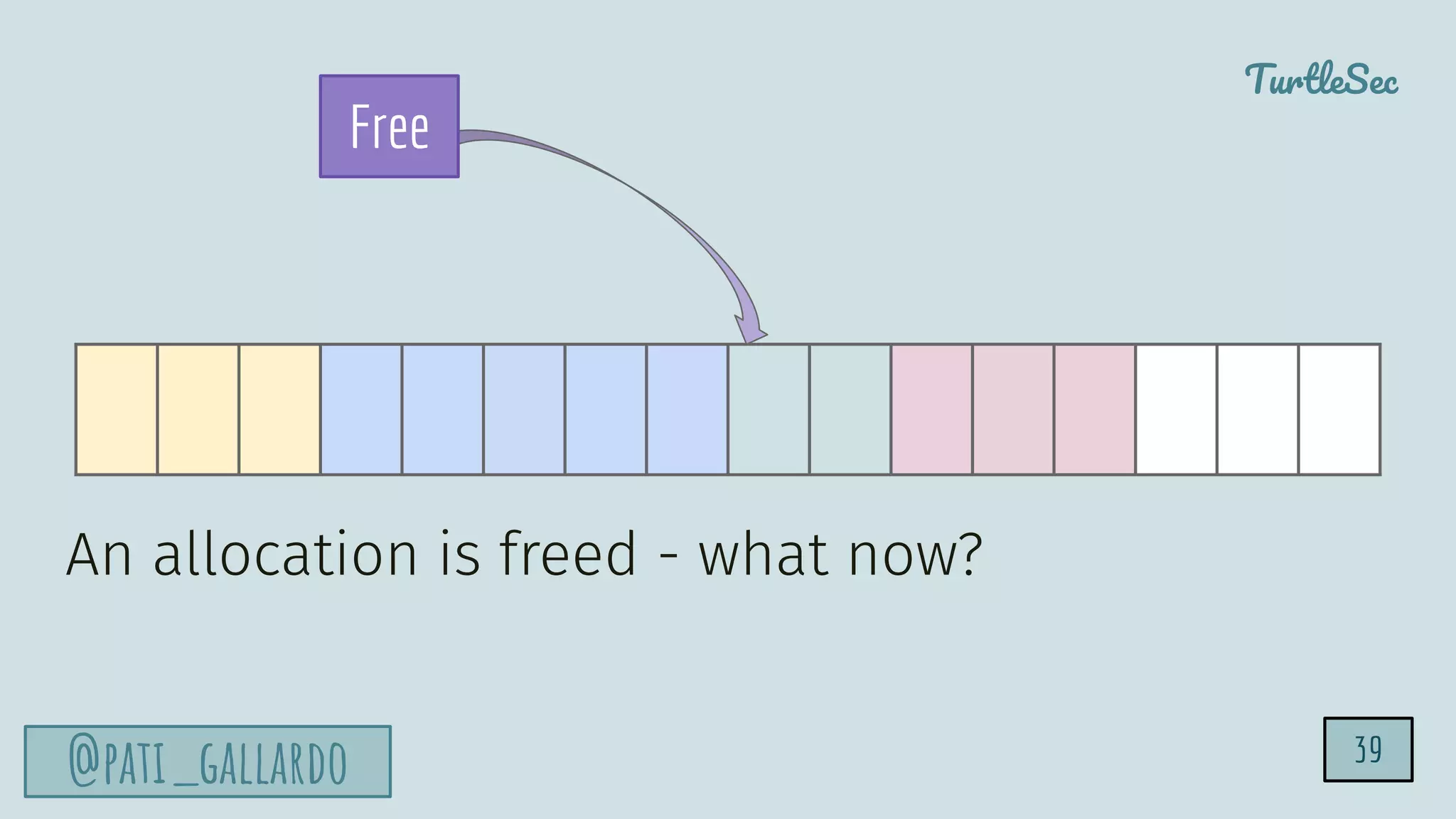
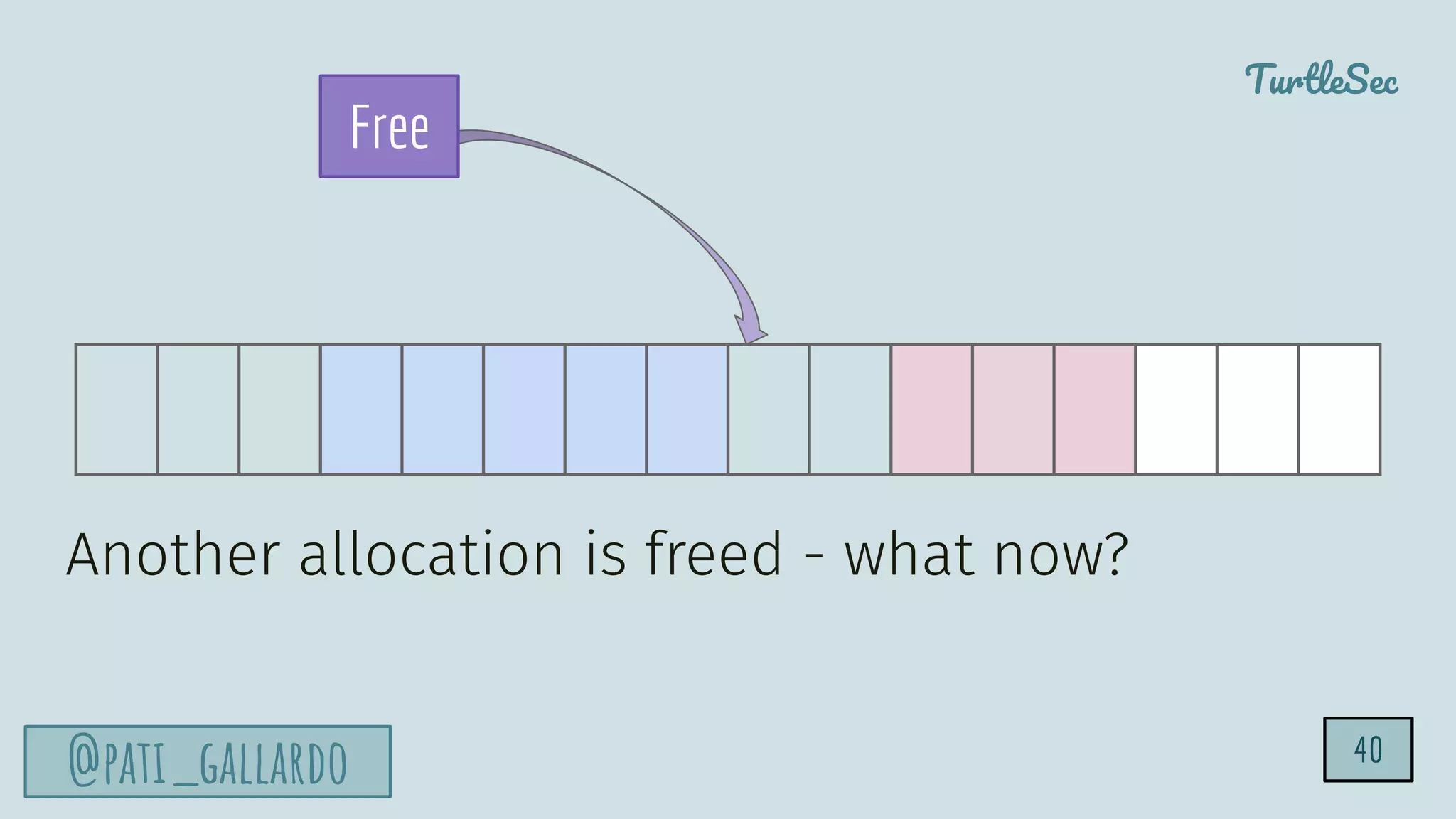
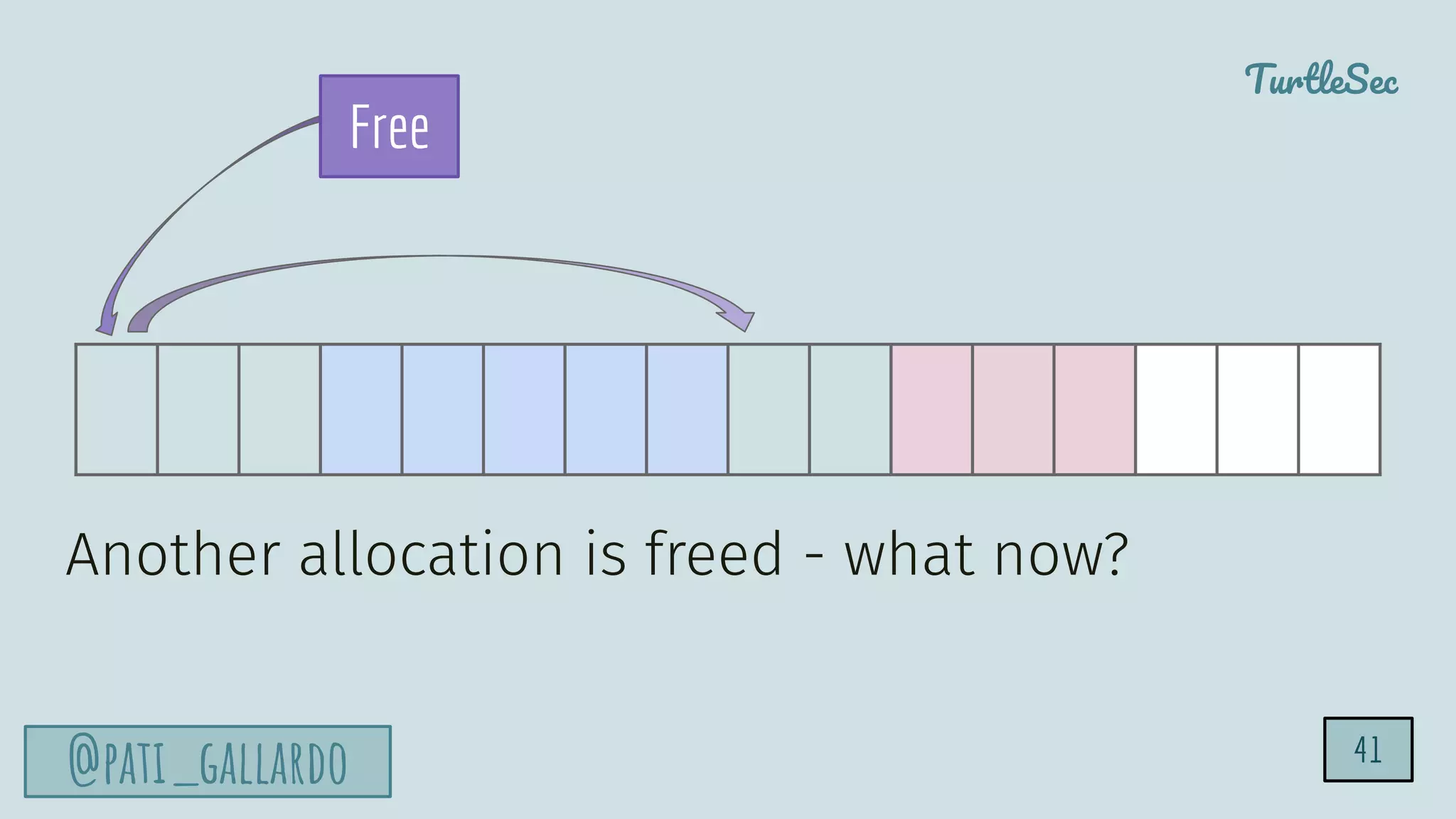
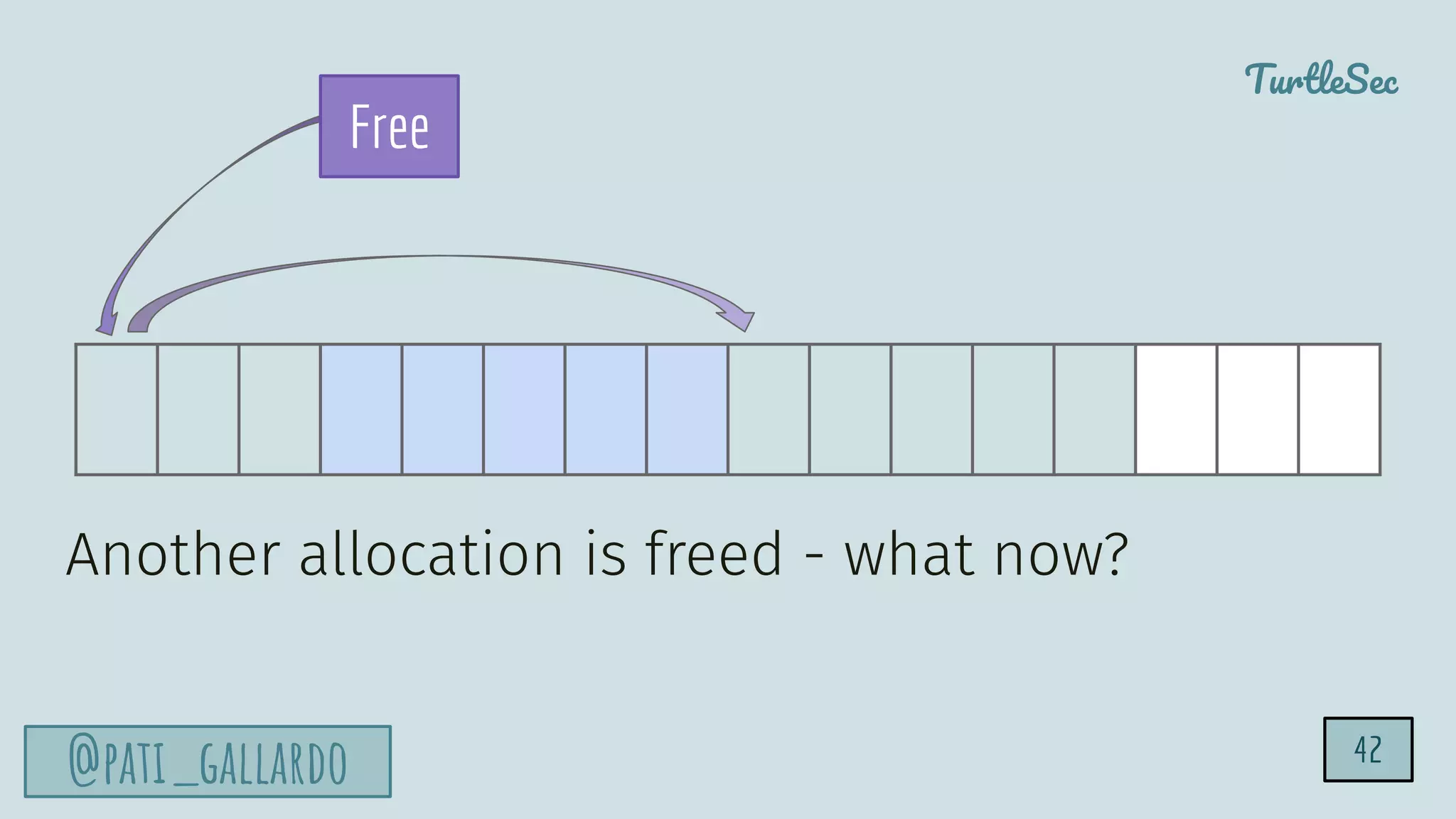
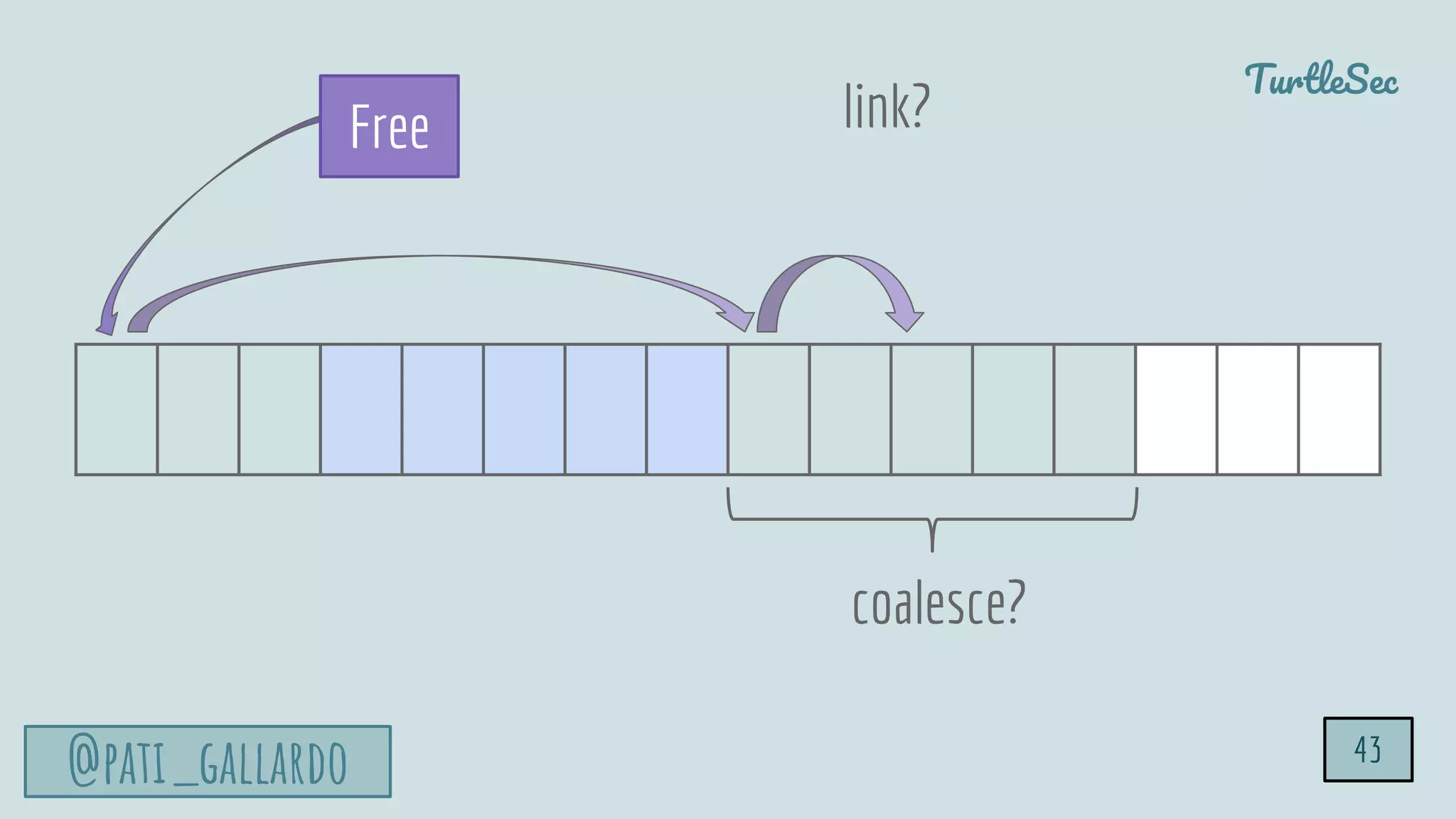
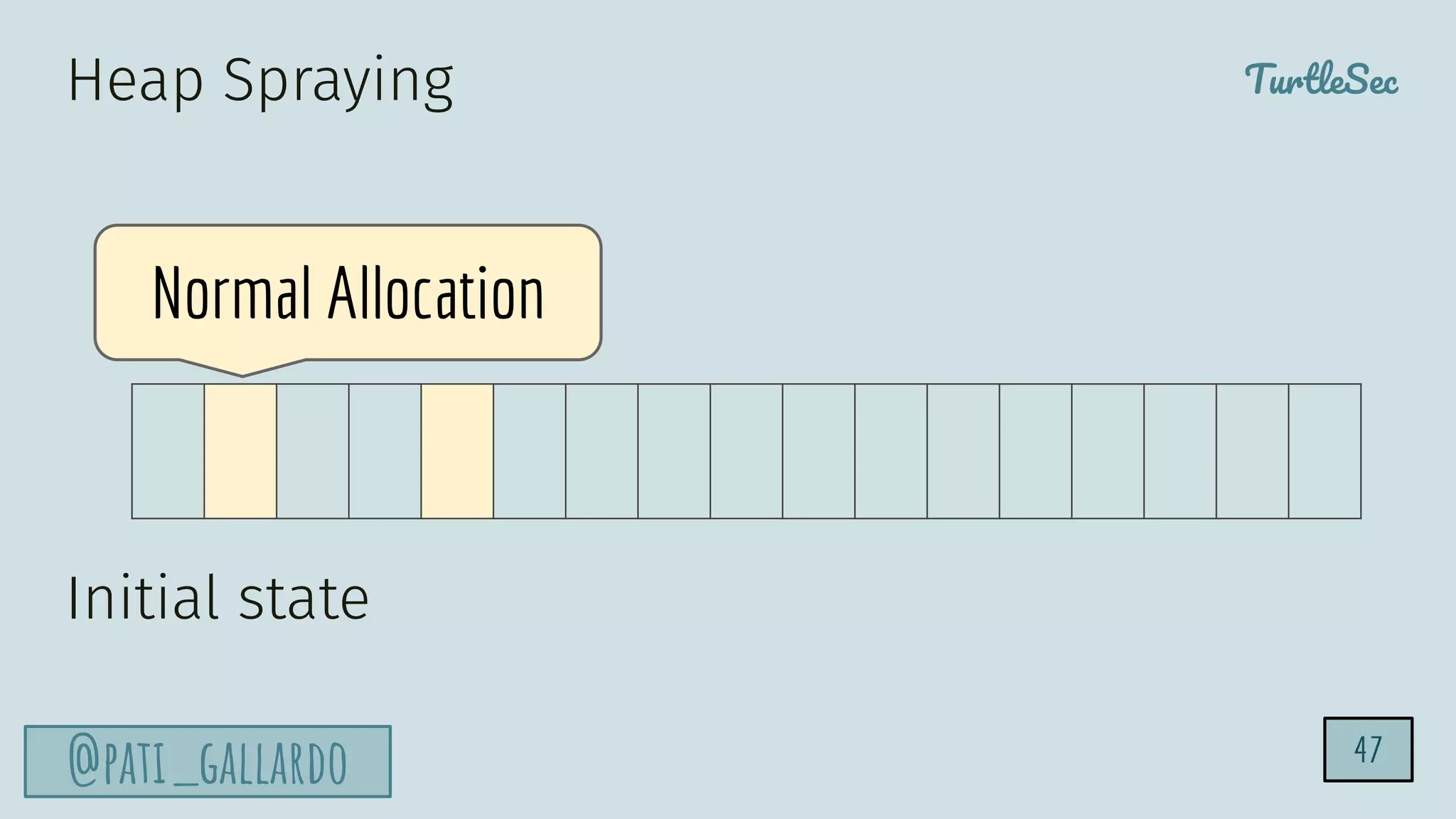
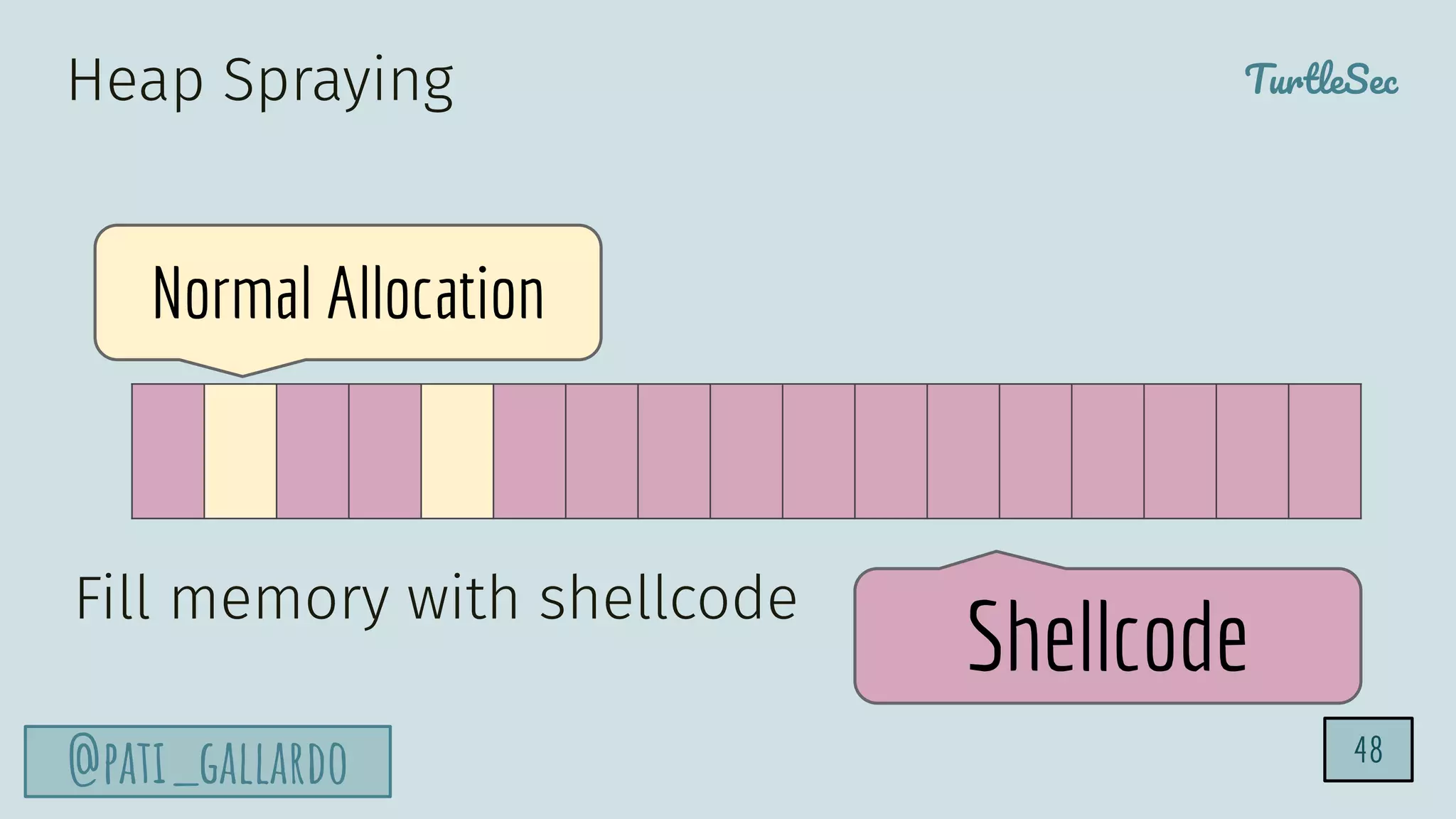
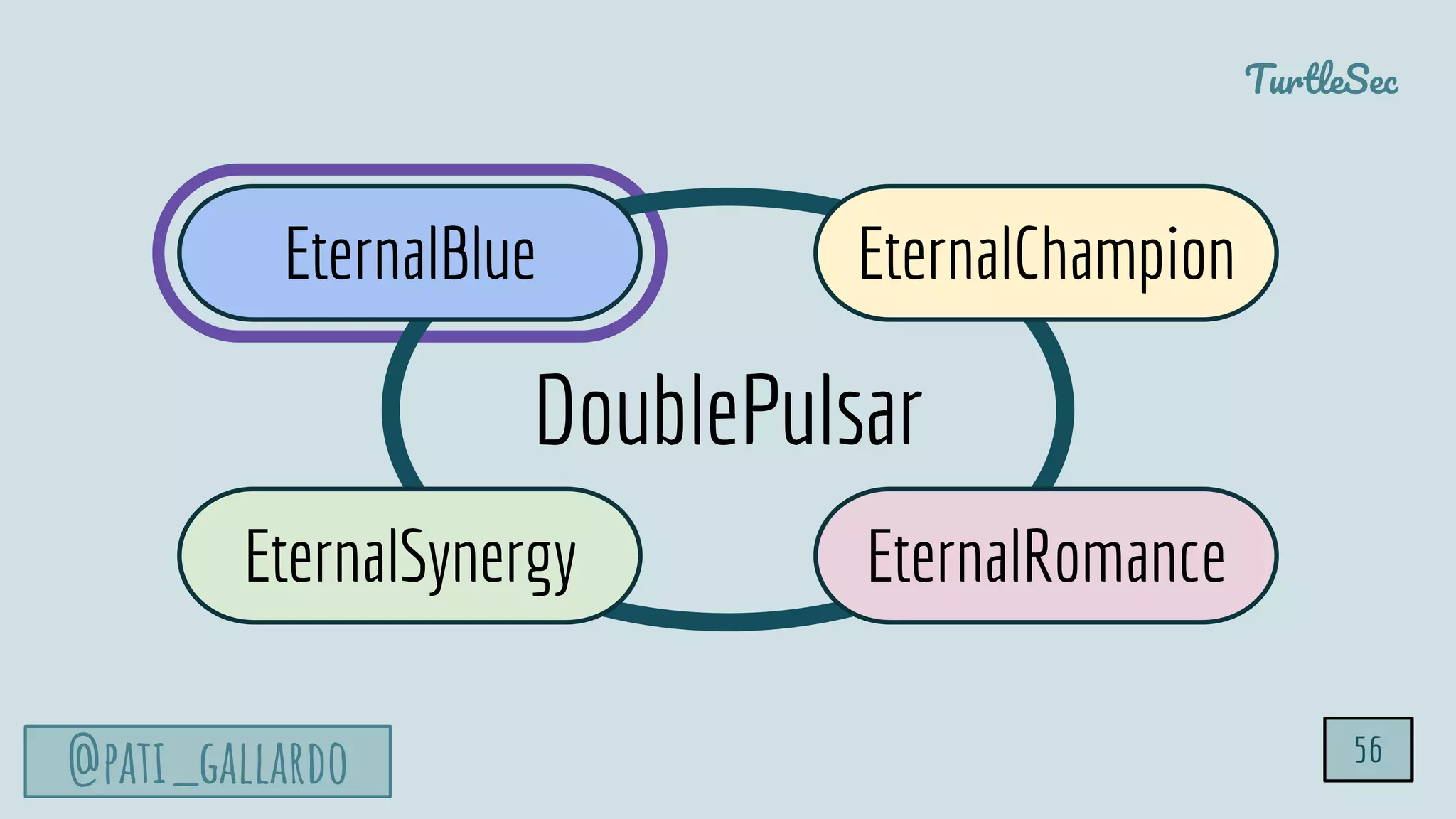
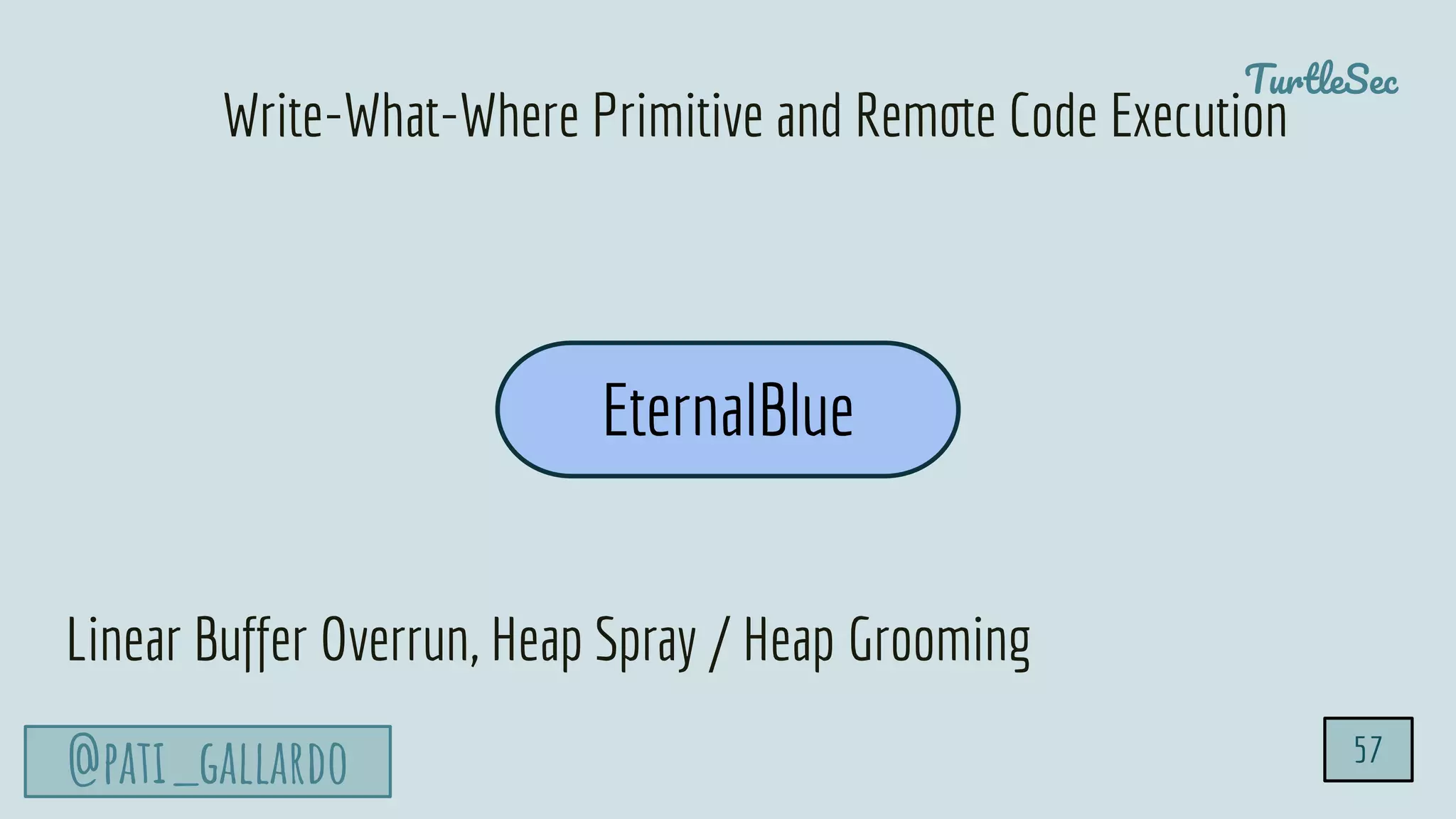
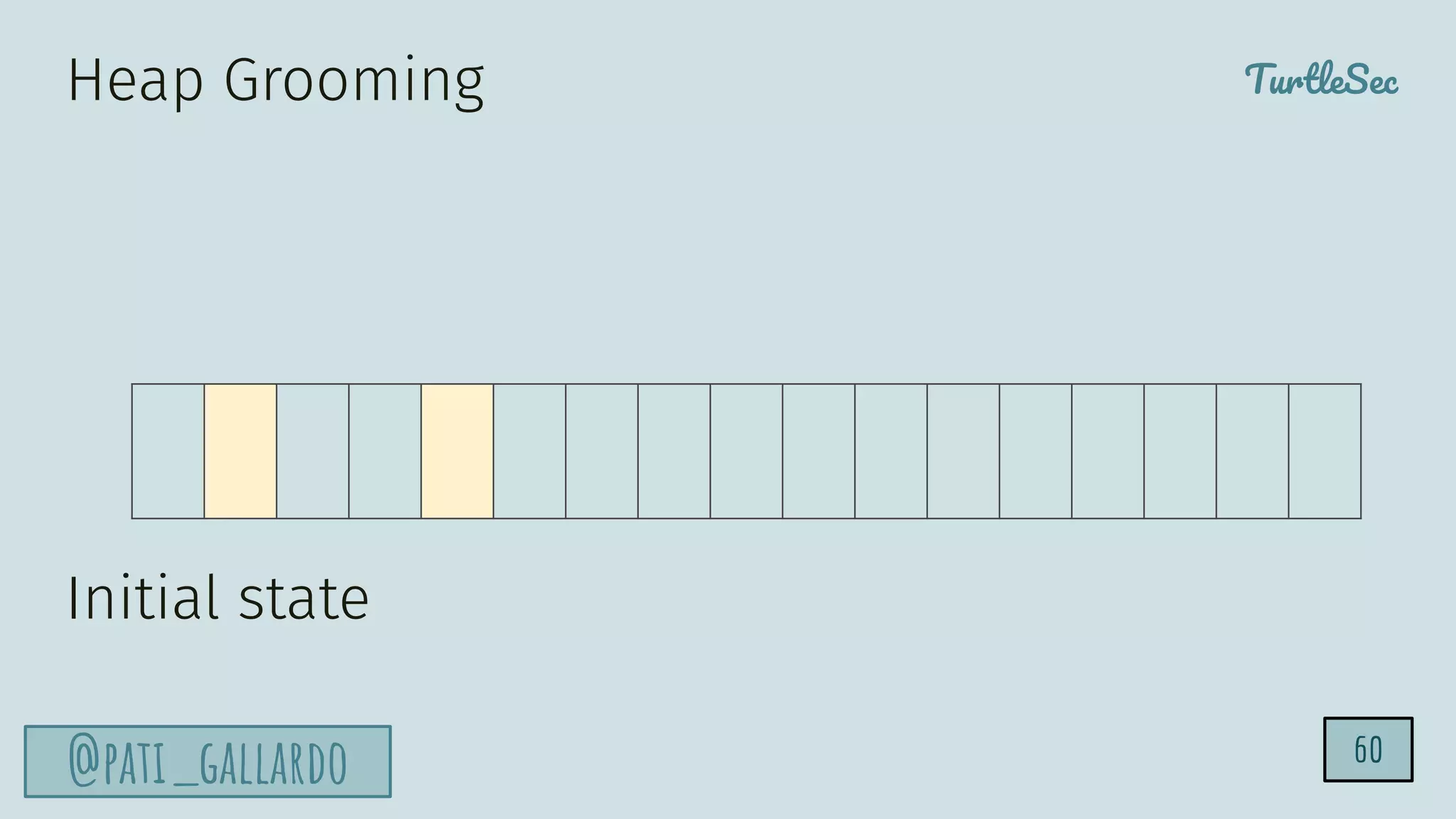
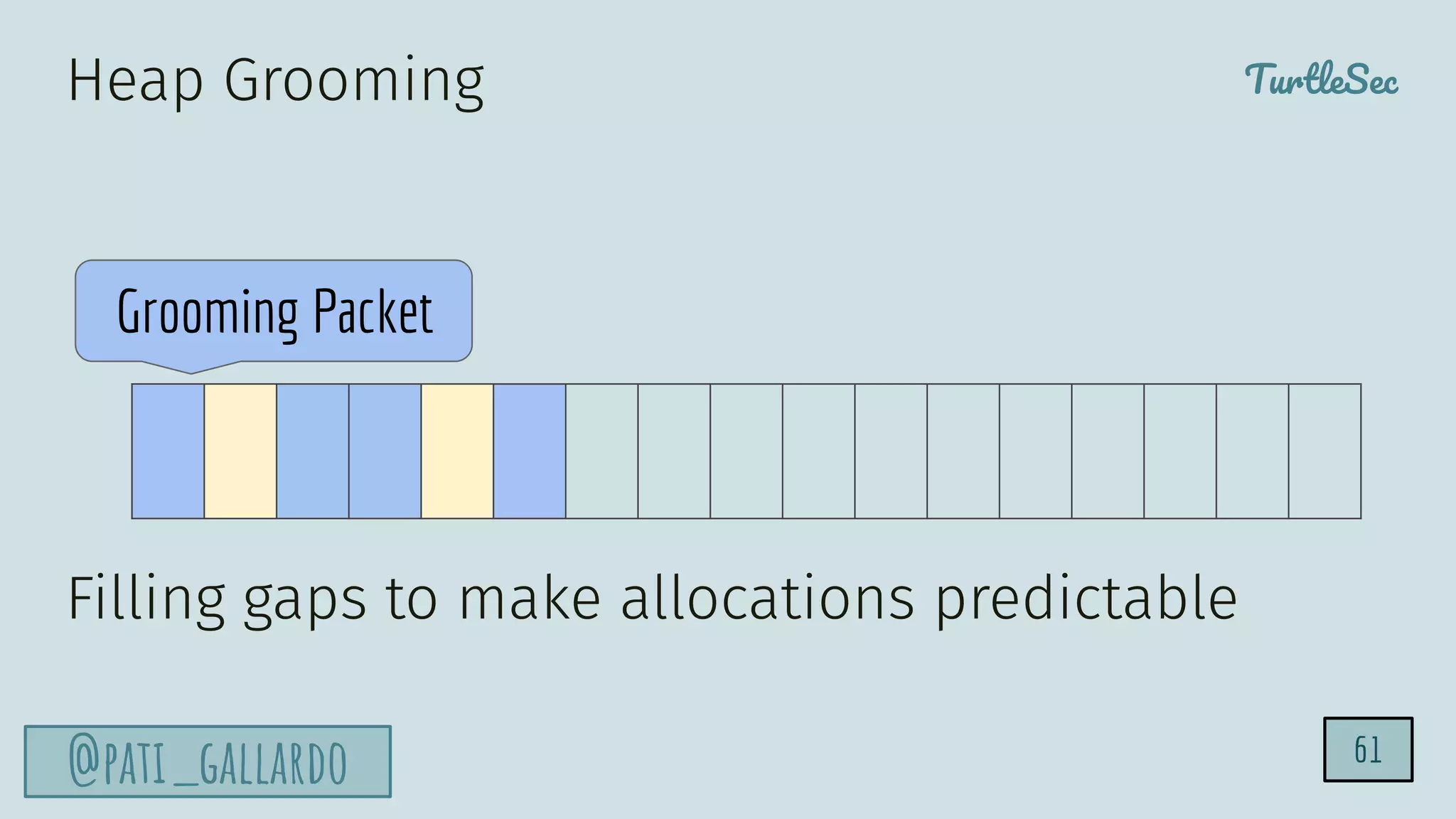
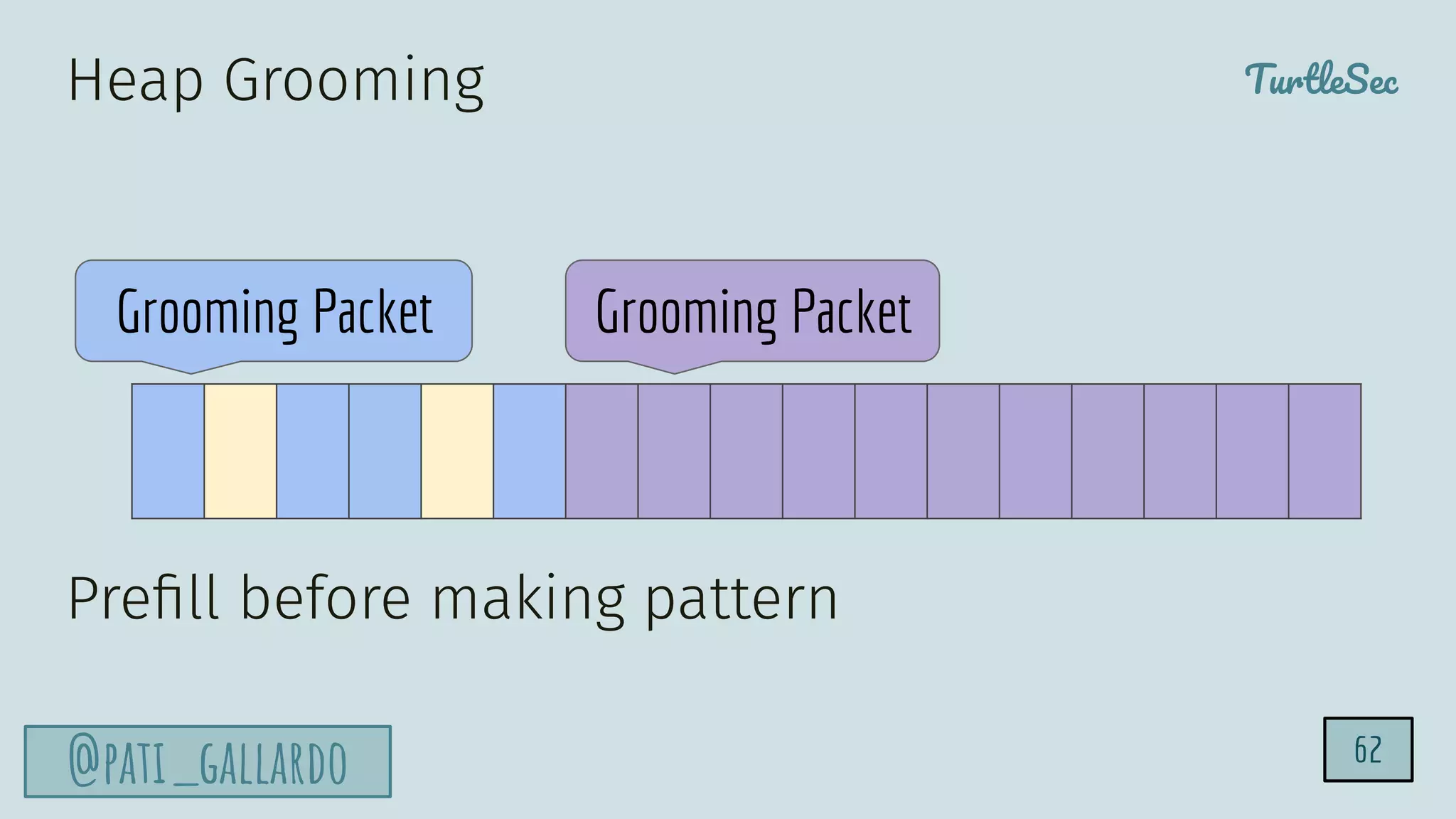
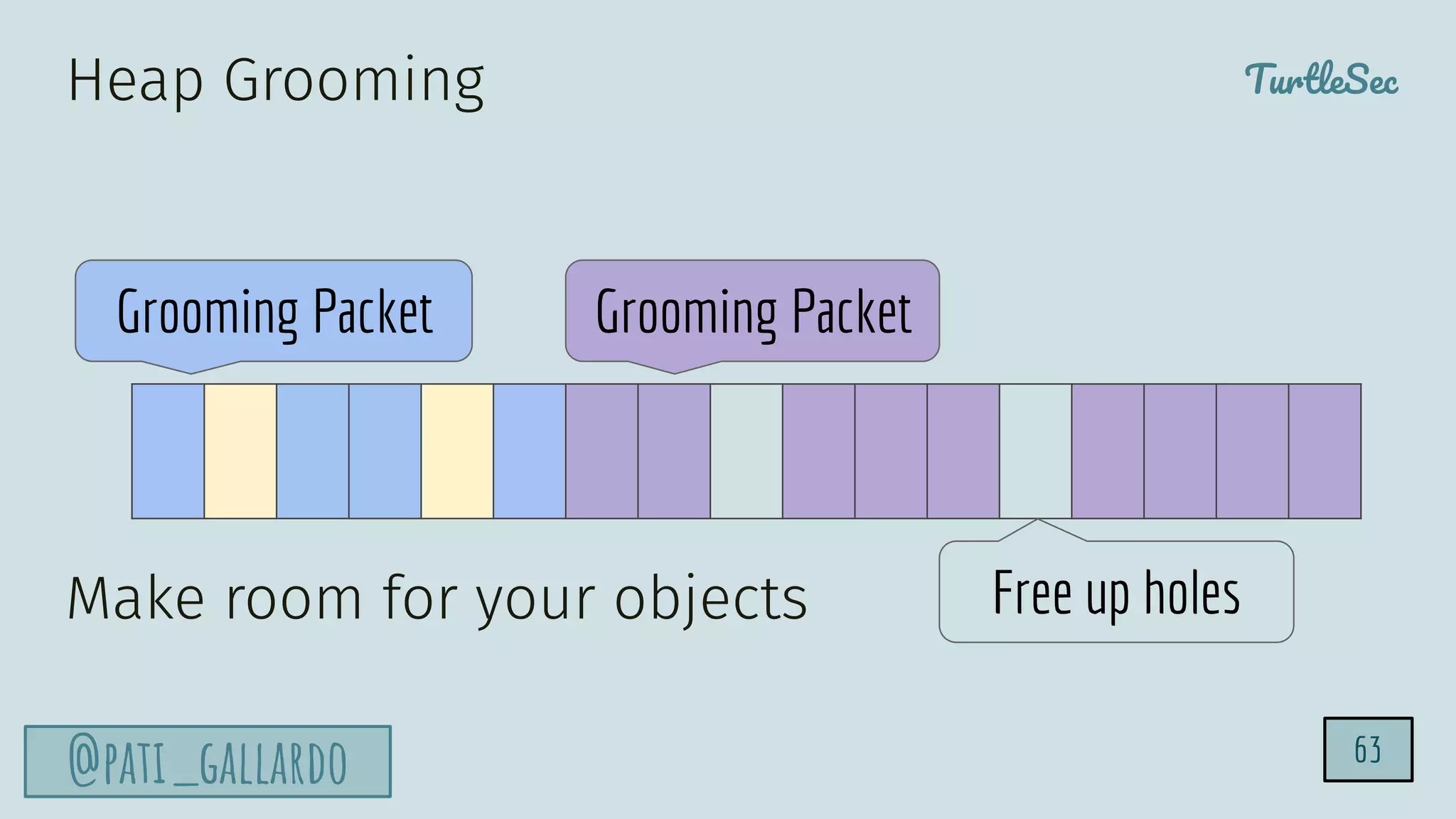
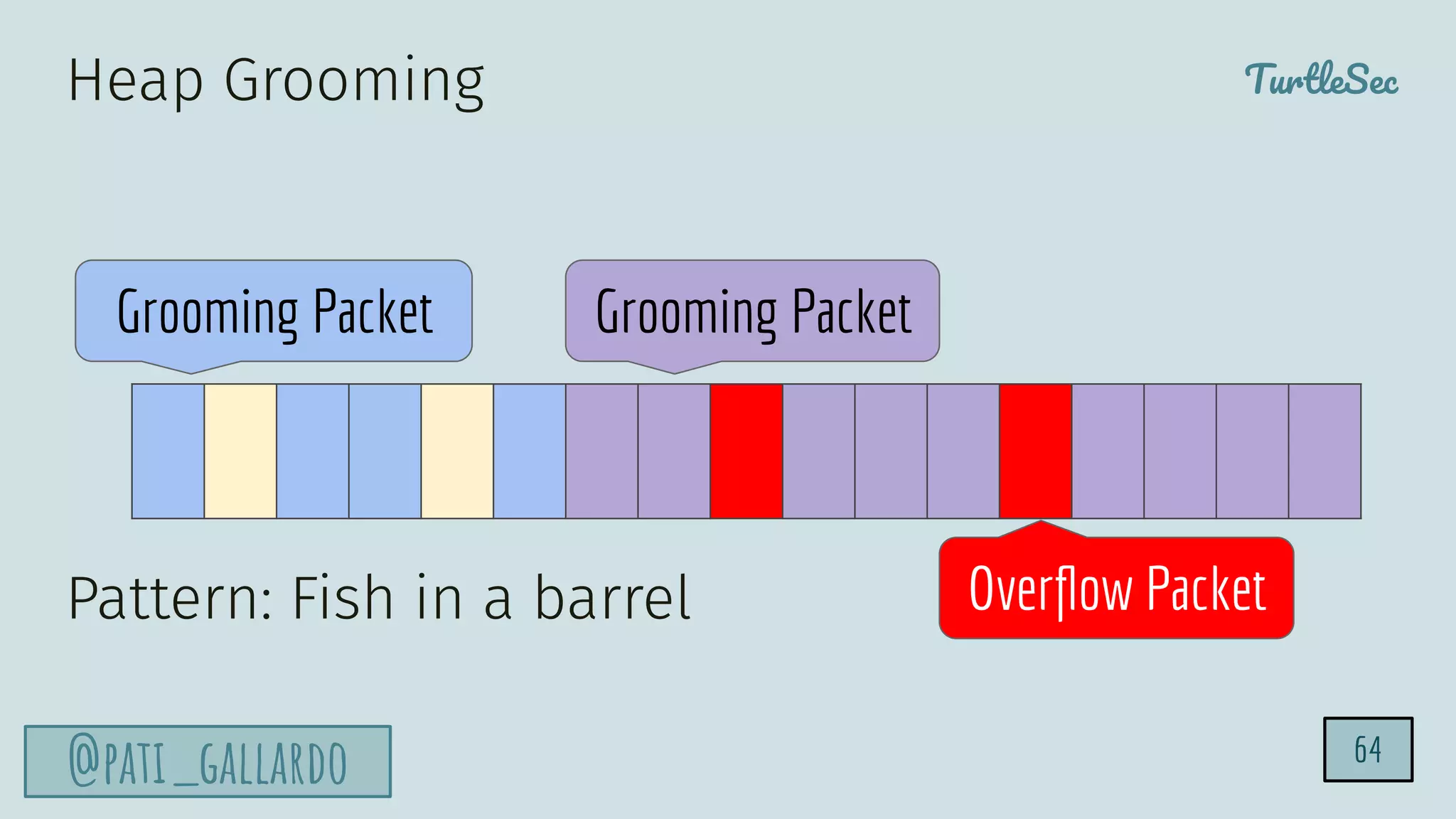
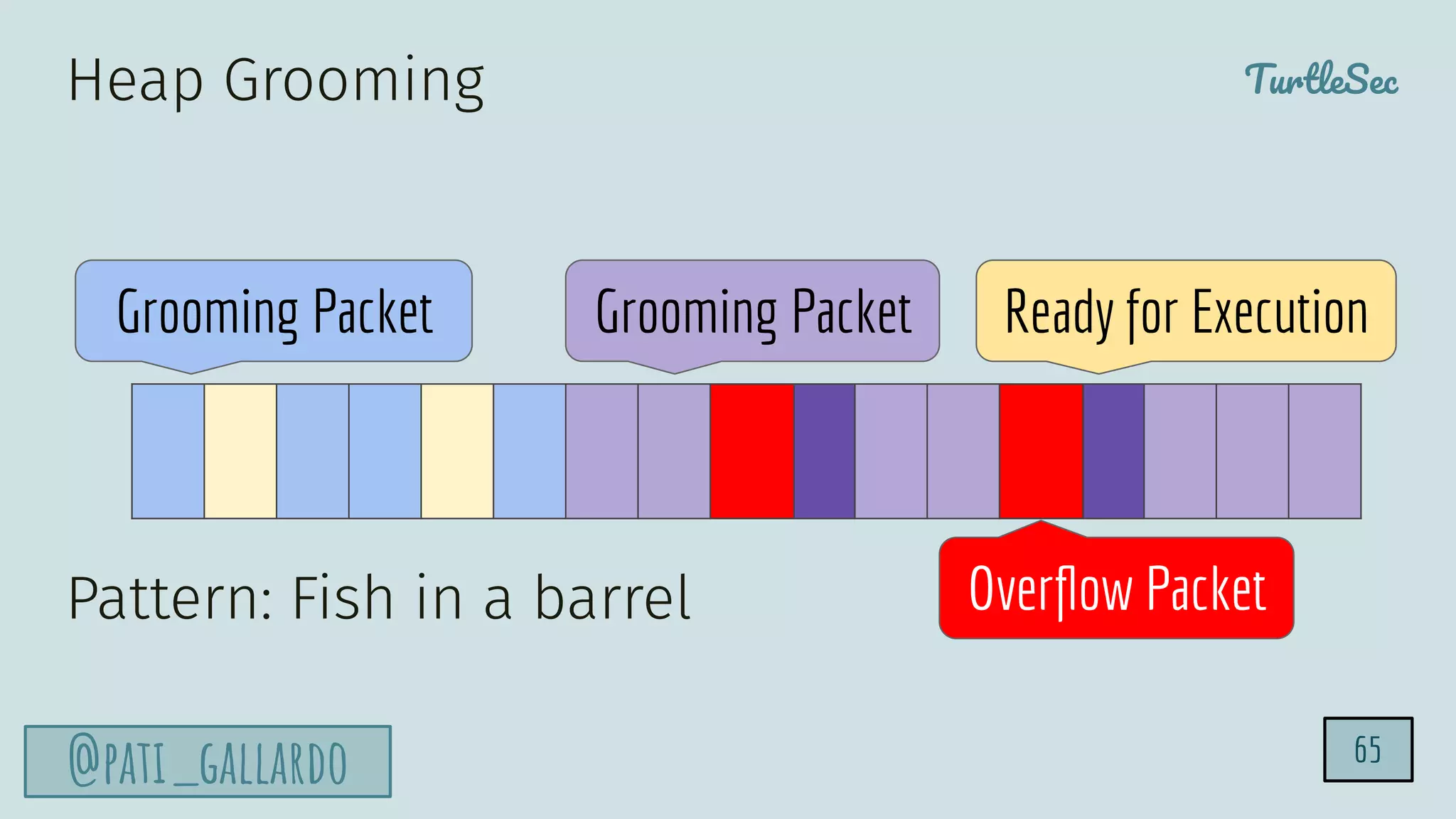
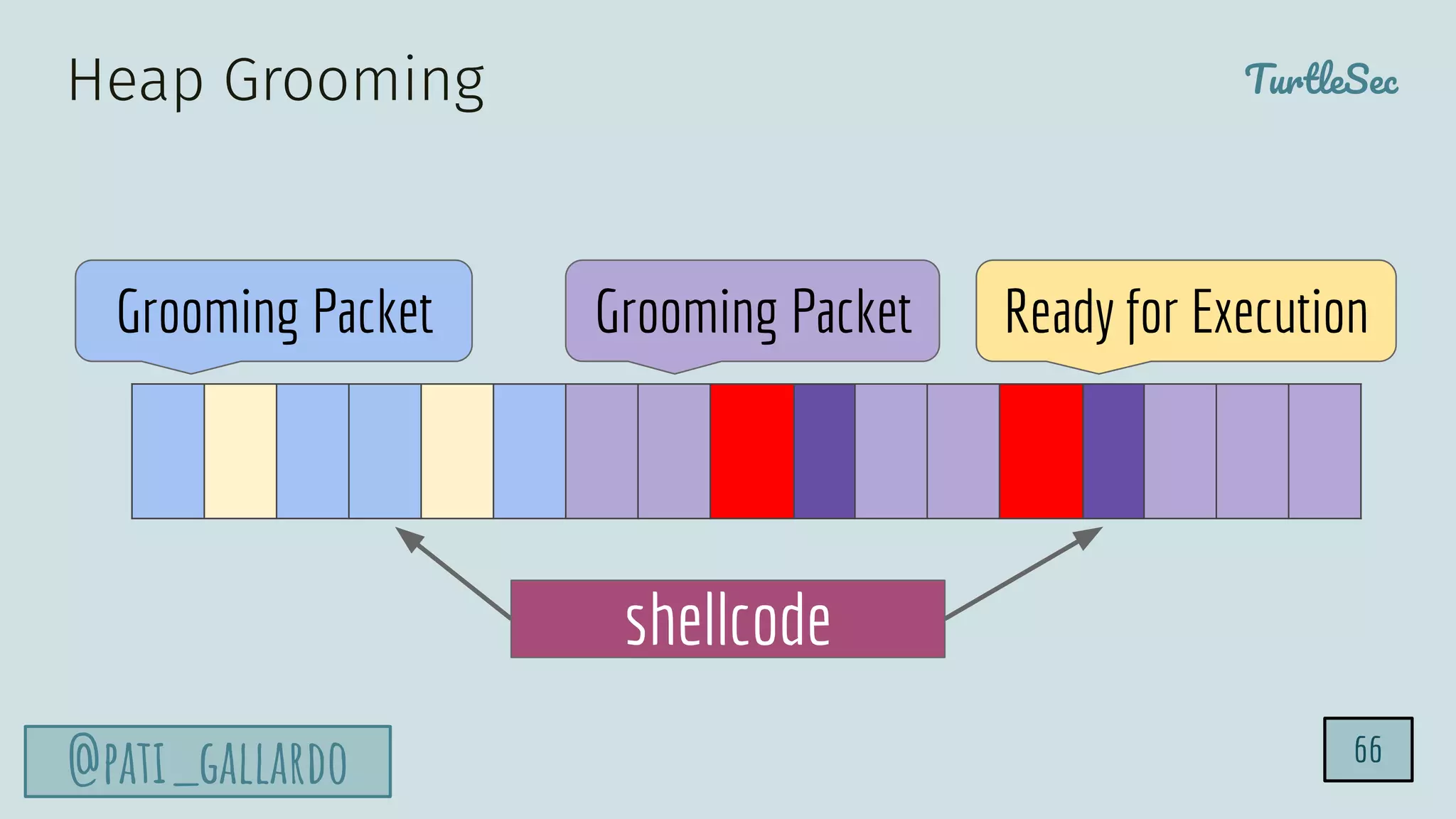
The document discusses the Heartbleed vulnerability, a severe memory exploit that allows attackers to access sensitive information from server memory without leaving traces. It outlines the attack's implications, the mechanisms behind the exploit, and the use of techniques like fuzzing and heap grooming to exploit memory errors. Furthermore, it emphasizes the importance of fixing vulnerabilities to mitigate risks associated with such exploits.