This document provides an overview of the tcpdump network traffic analysis tool. It discusses how tcpdump can be used to capture and filter network packets, highlights some common workflows and options, describes the underlying Berkeley Packet Filter (BPF) architecture, and addresses some common issues and questions. The key points are:
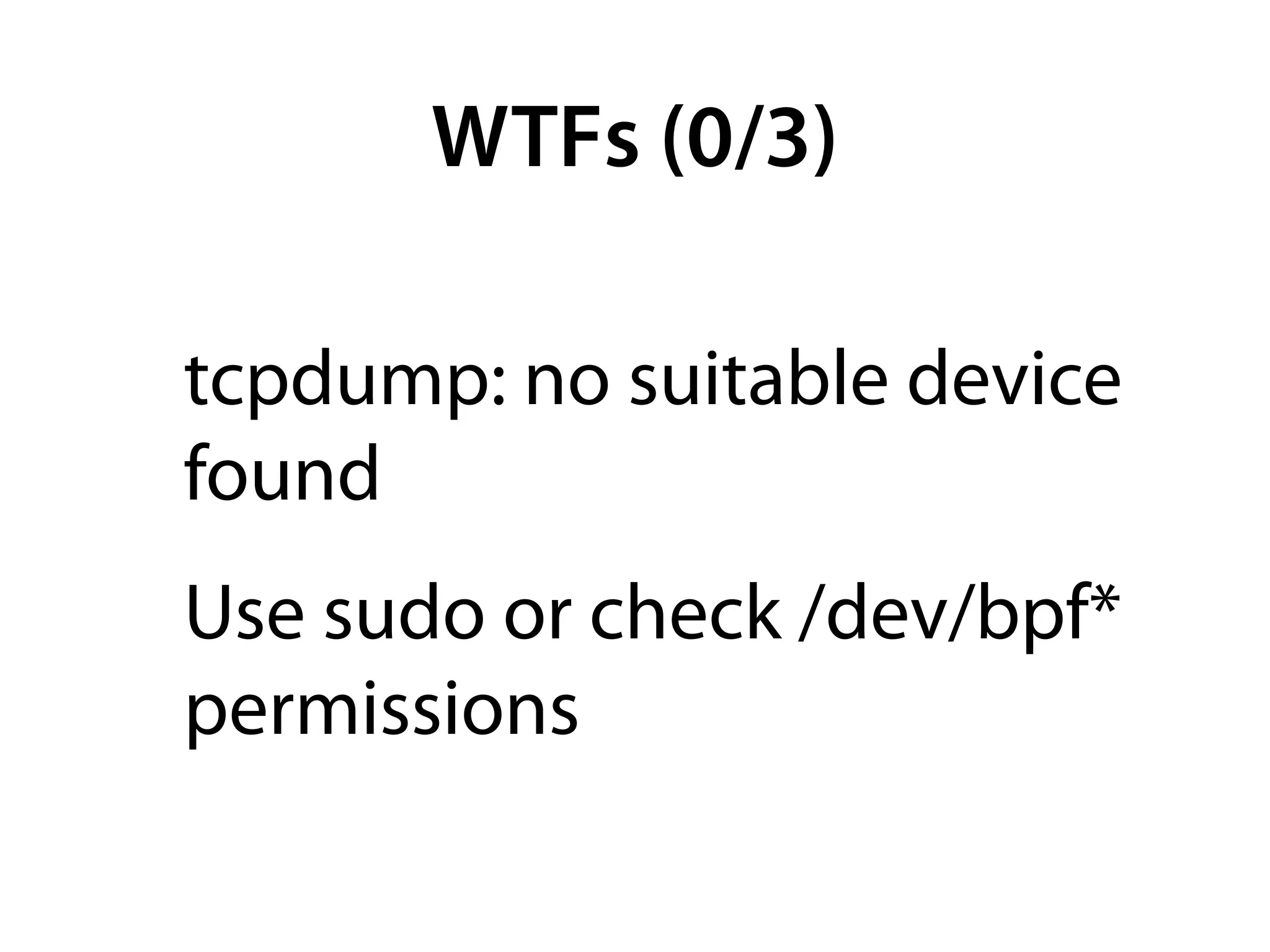
- Tcpdump allows users to capture and filter live network traffic or read from saved packet capture (pcap) files.
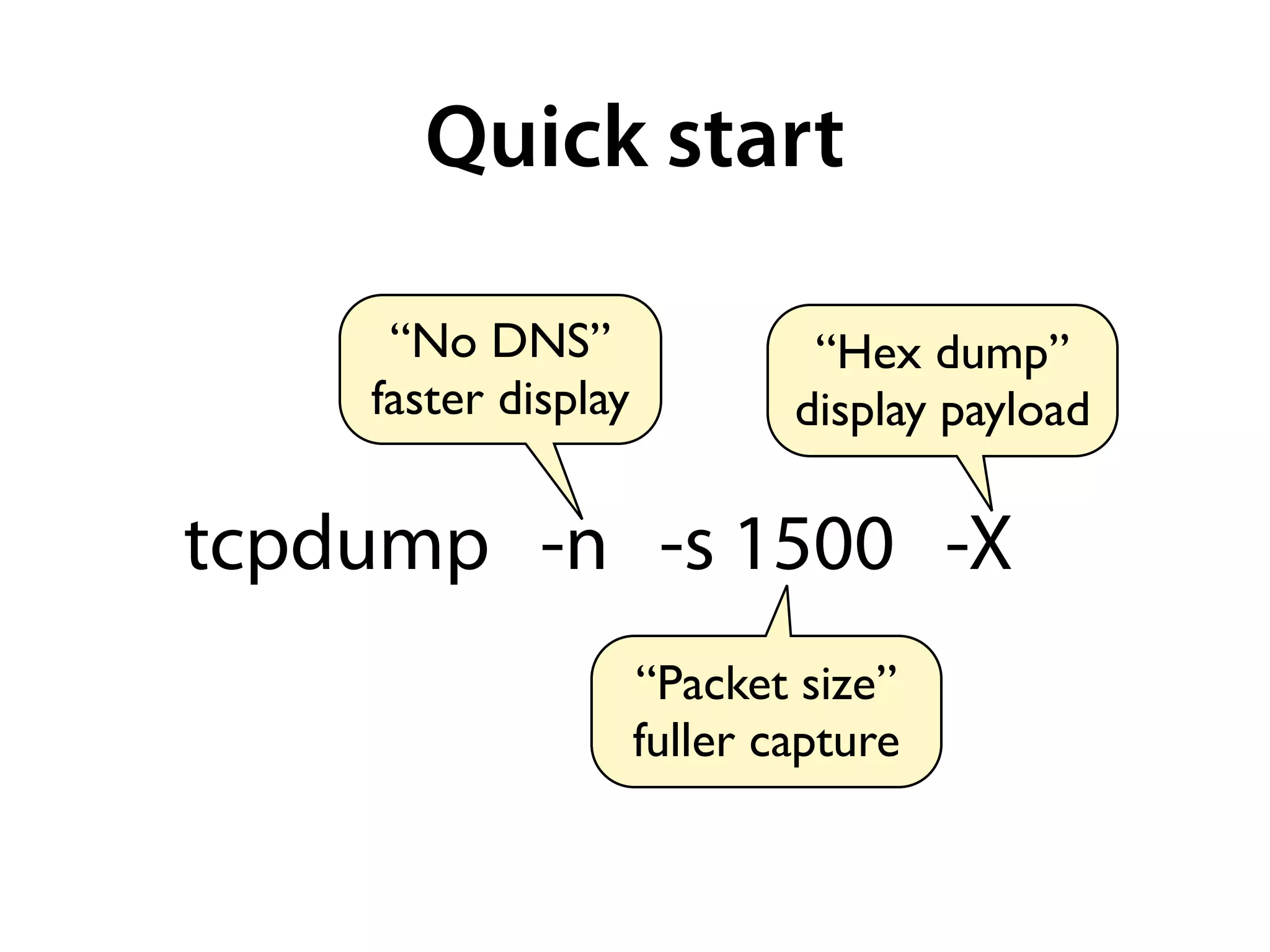
- Common options include -n to disable DNS resolution for faster display, -s1500 to set the snapshot length, -X to print packets in hex/ascii, and various filters like port 80.
- Workflows include online analysis of live traffic or offline analysis of saved captures

![What is tcpdump?
Capture
[Save]
Filter
Show and explain](https://image.slidesharecdn.com/echo-tcpdump-120814224838-phpapp02/75/Introduction-to-tcpdump-2-2048.jpg)
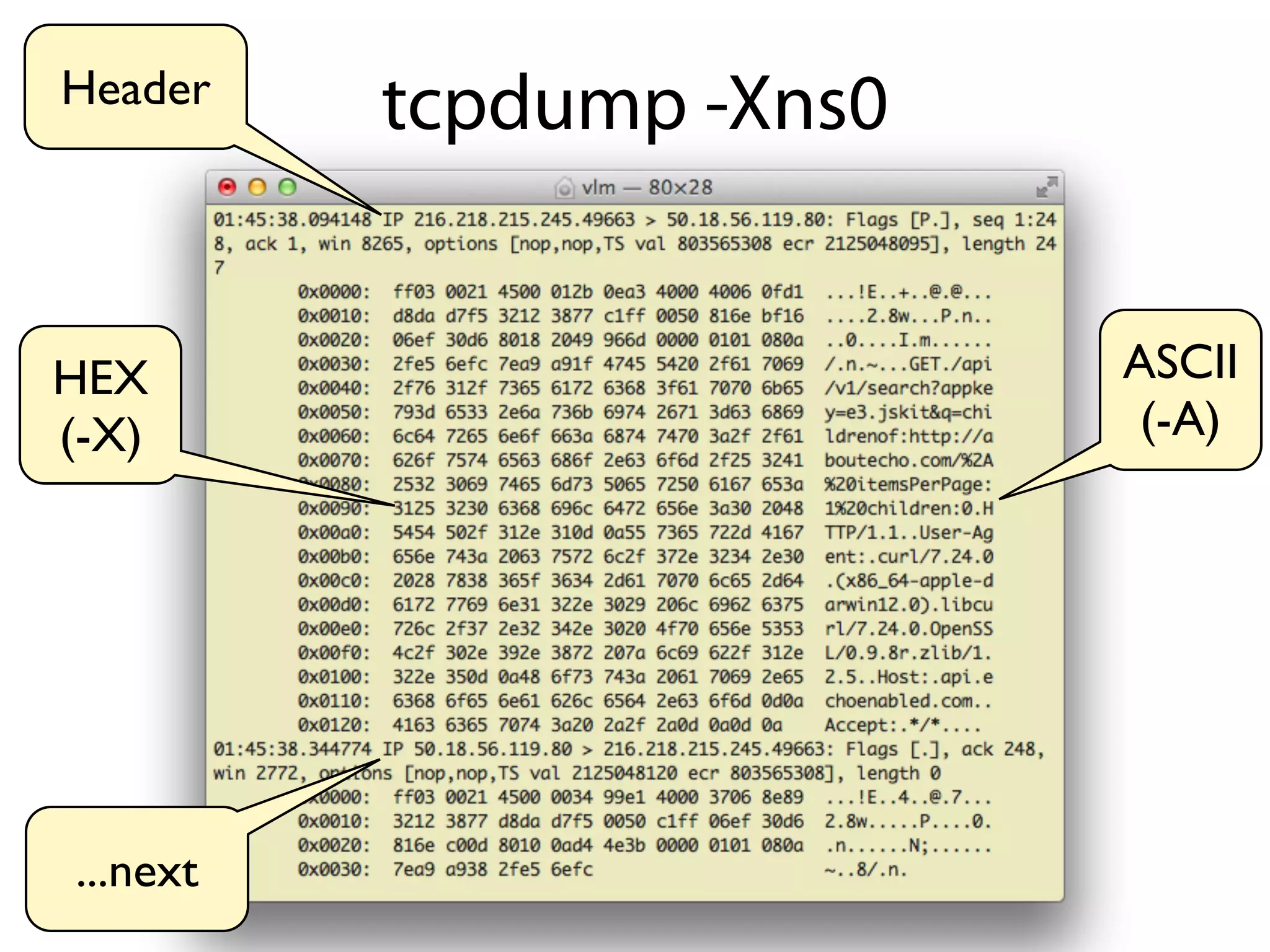




![Timestamp L3 protocol
(-tt, -ttt, -tttt) Output (IP, GRE, etc)
Relative TCP
ack number
src host src port dst host & port
TCP Flags Relative TCP Advertised TCP
(S, F, R) sequence number
1343949078.196214 IP window size
216.218.215.245.61966 > 50.18.0.102.80:
Flags [P.], seq 1:473, ack 1, win 8265,
options [nop,nop,TS val 808617737 ecr
1091126708], length 472
List of TCP Payload length
options (e.g. wscale)](https://image.slidesharecdn.com/echo-tcpdump-120814224838-phpapp02/75/Introduction-to-tcpdump-11-2048.jpg)