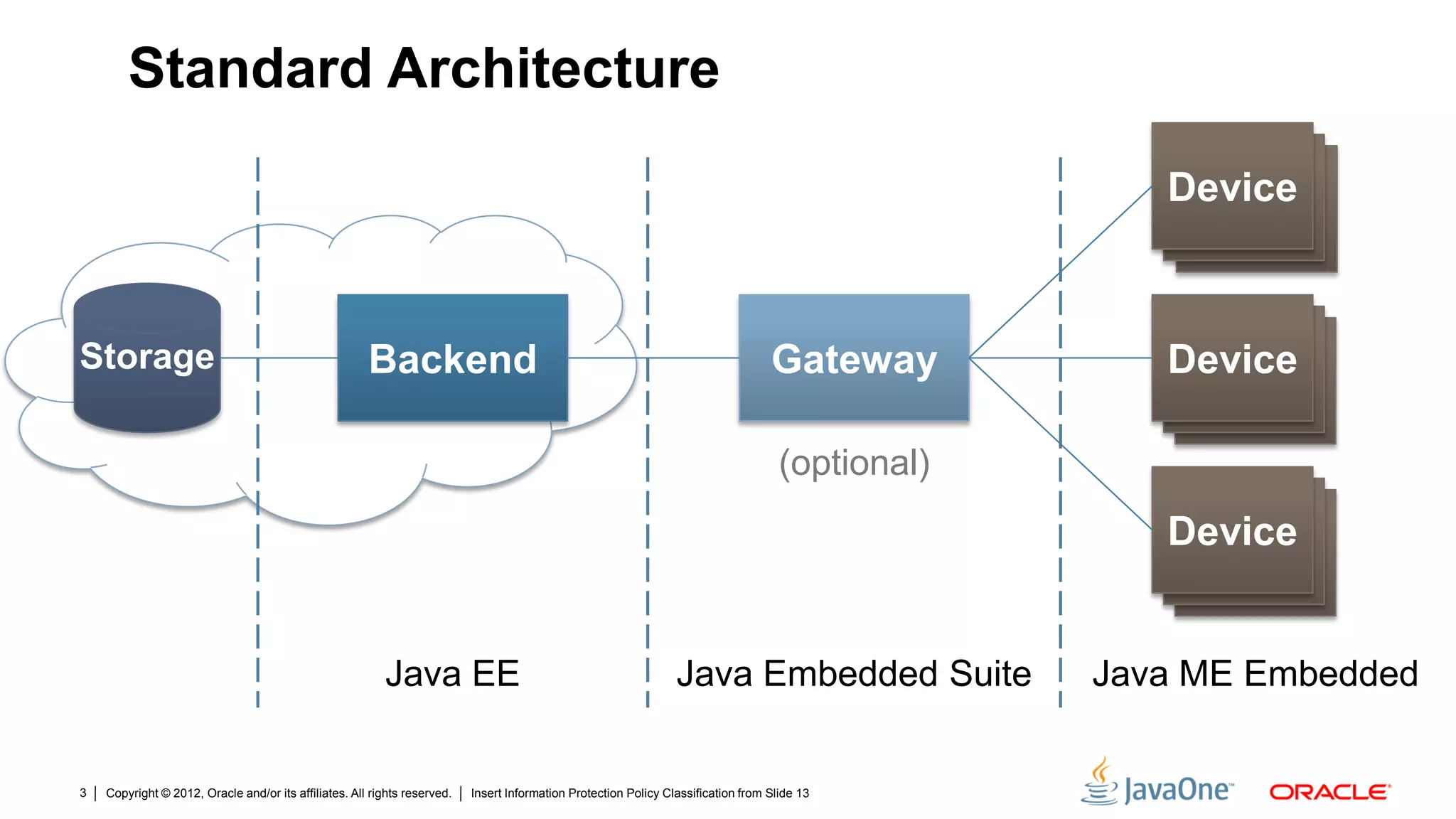
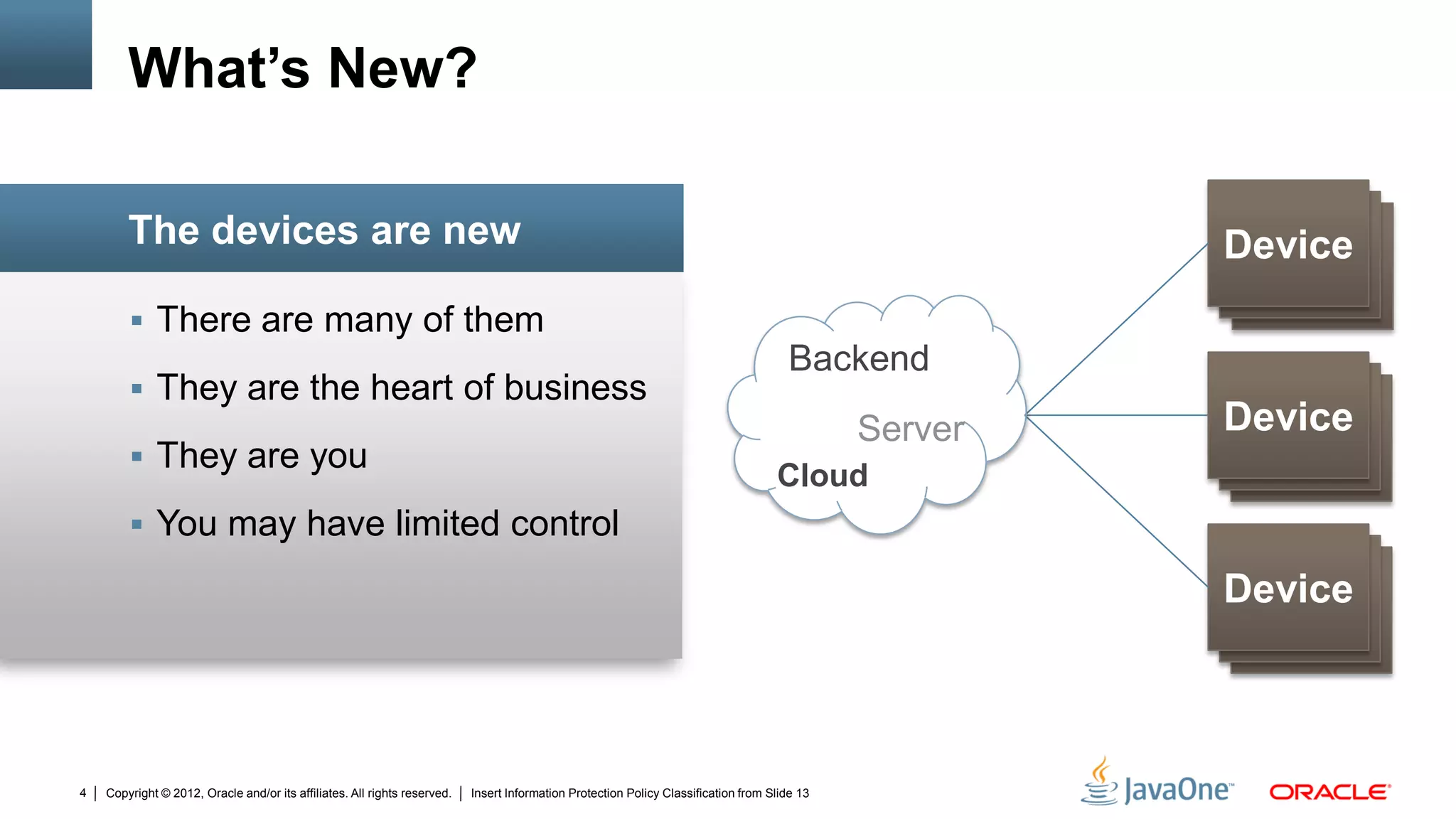
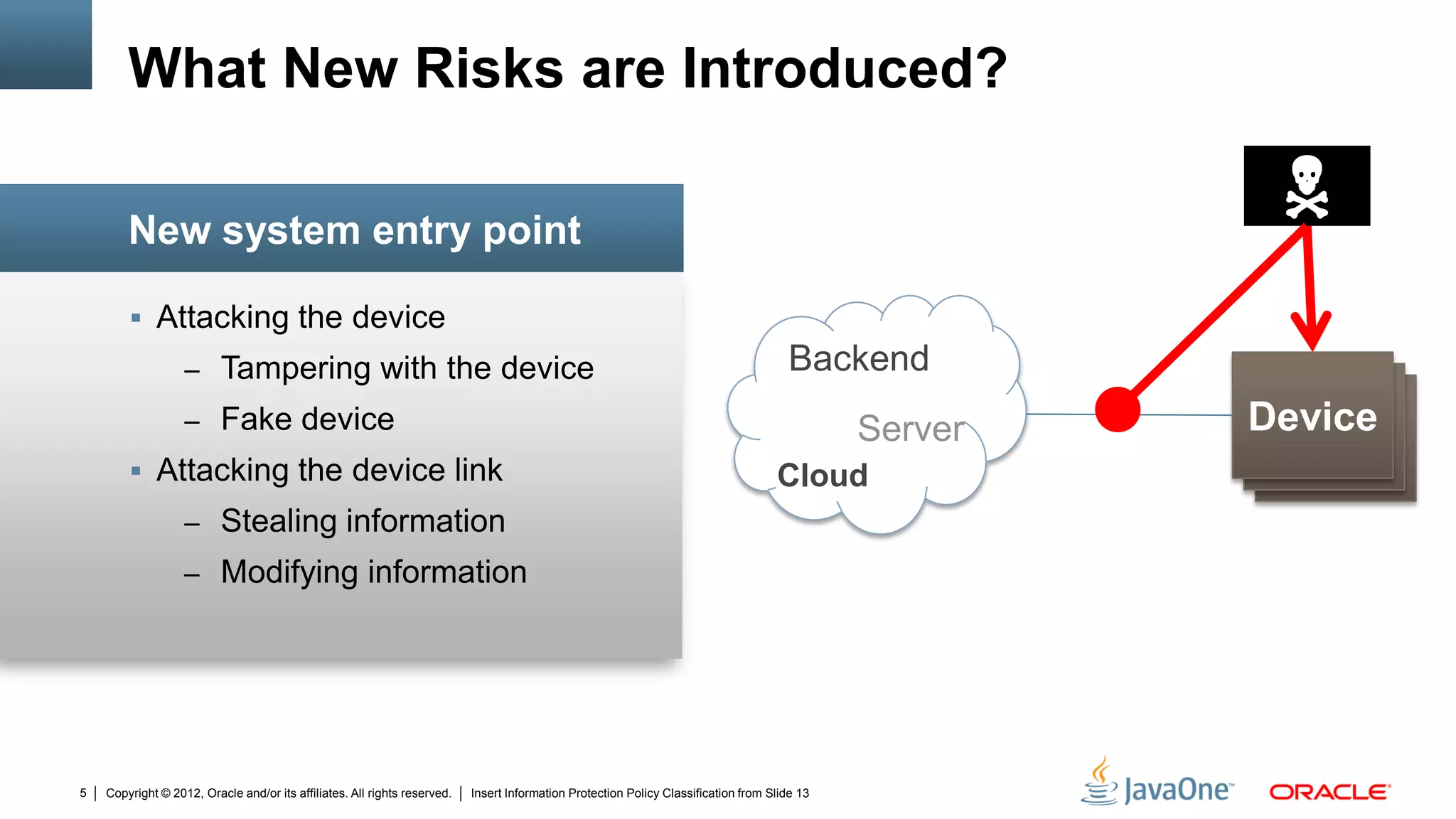
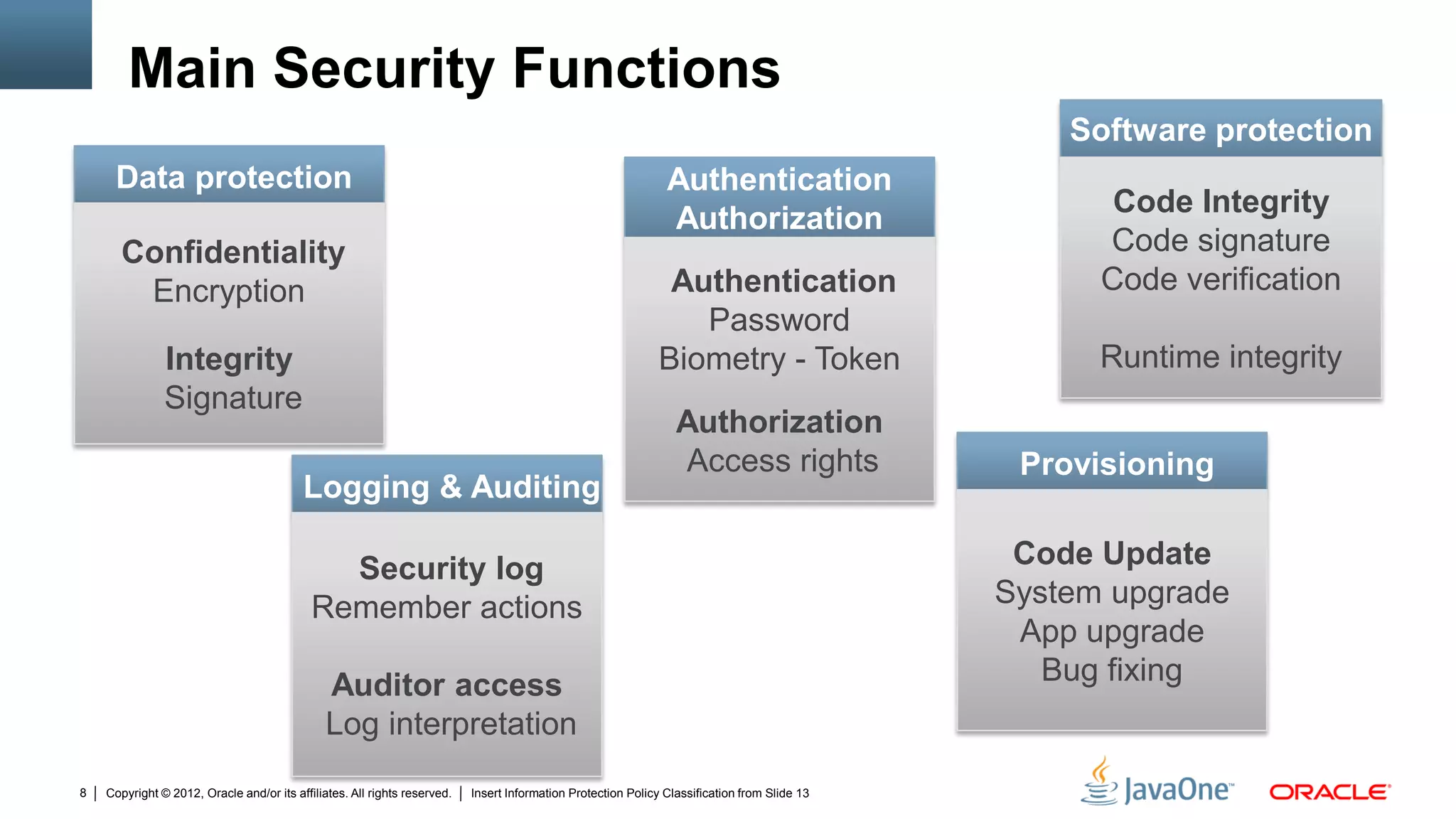
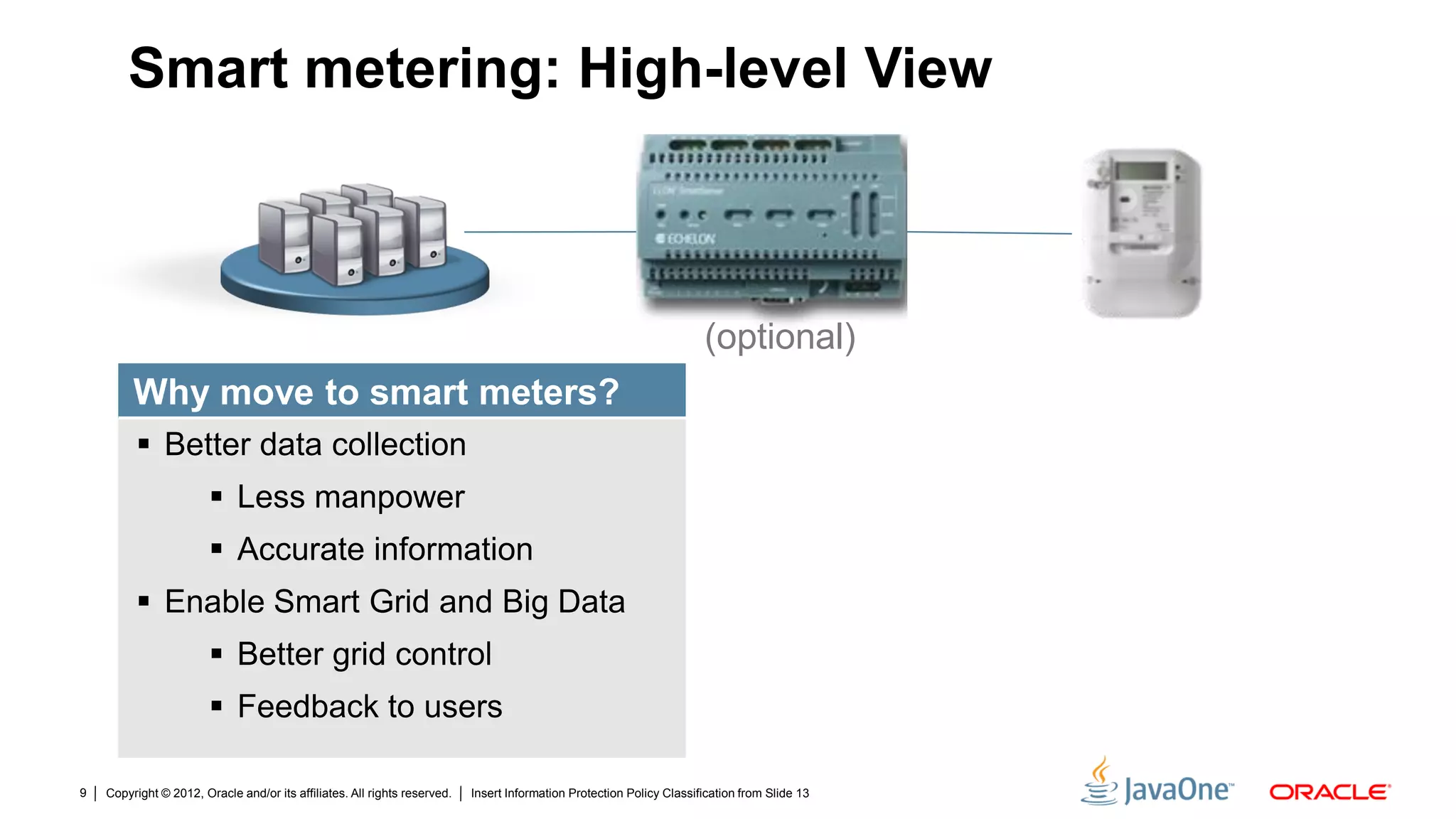
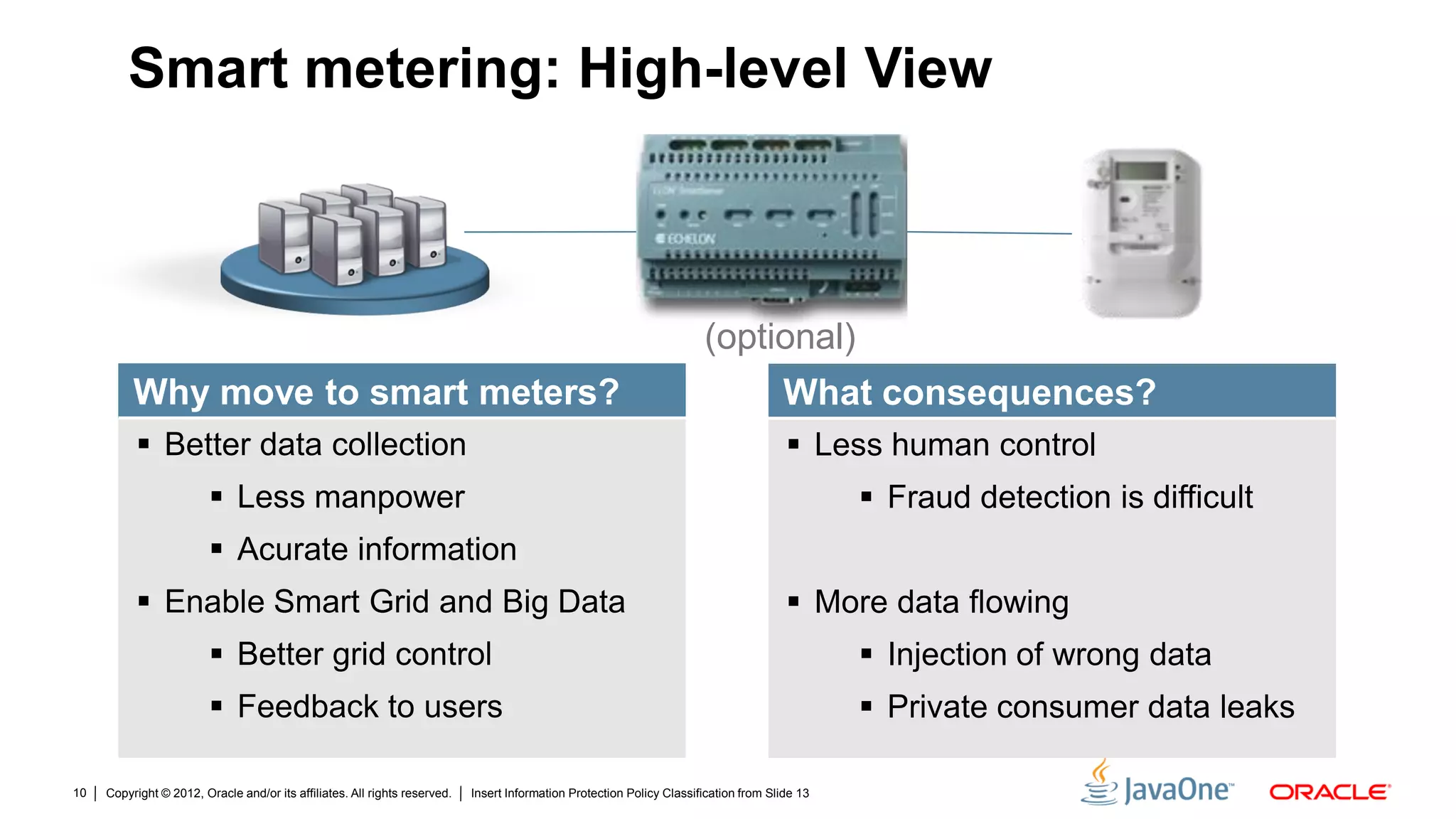
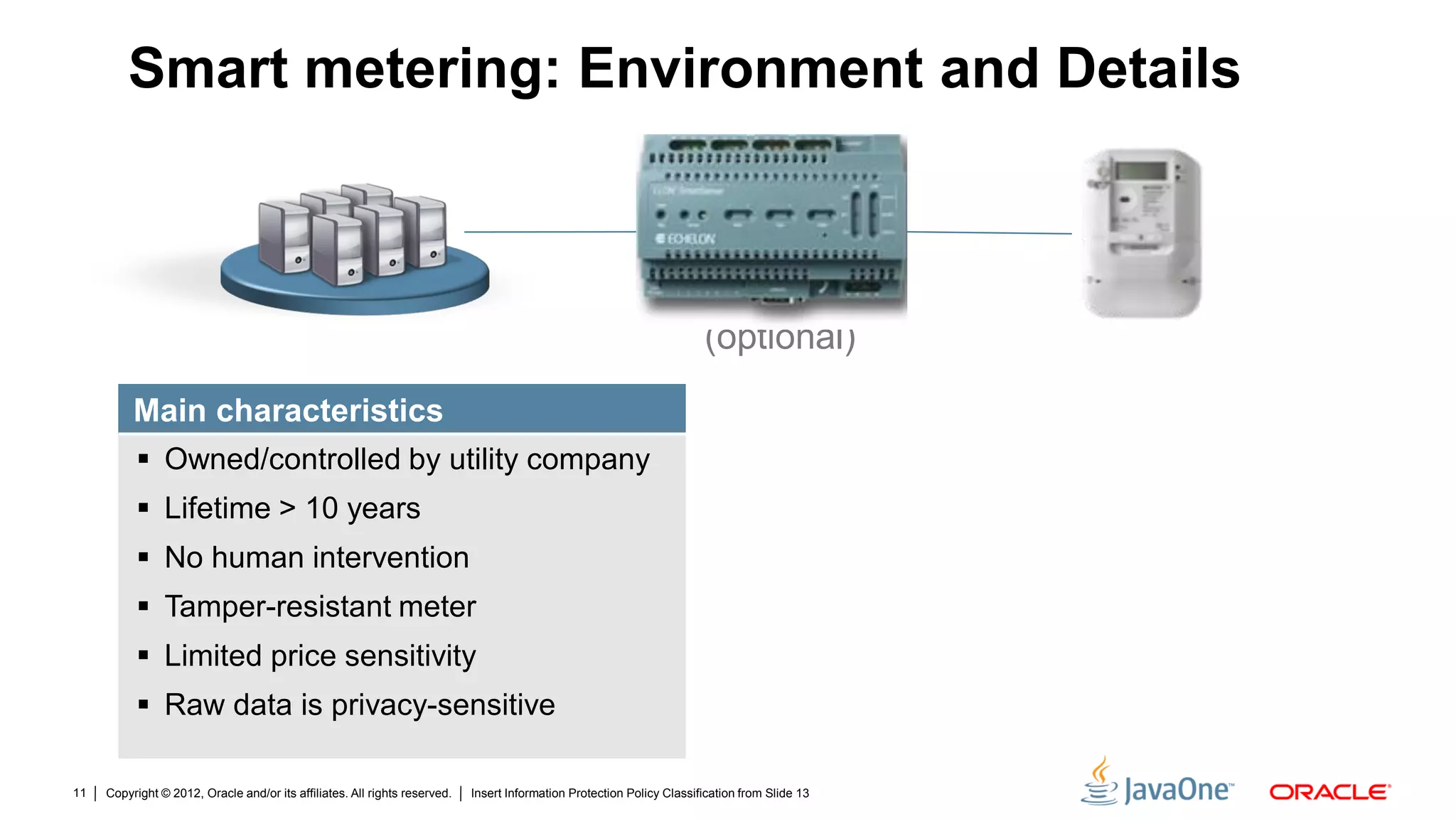
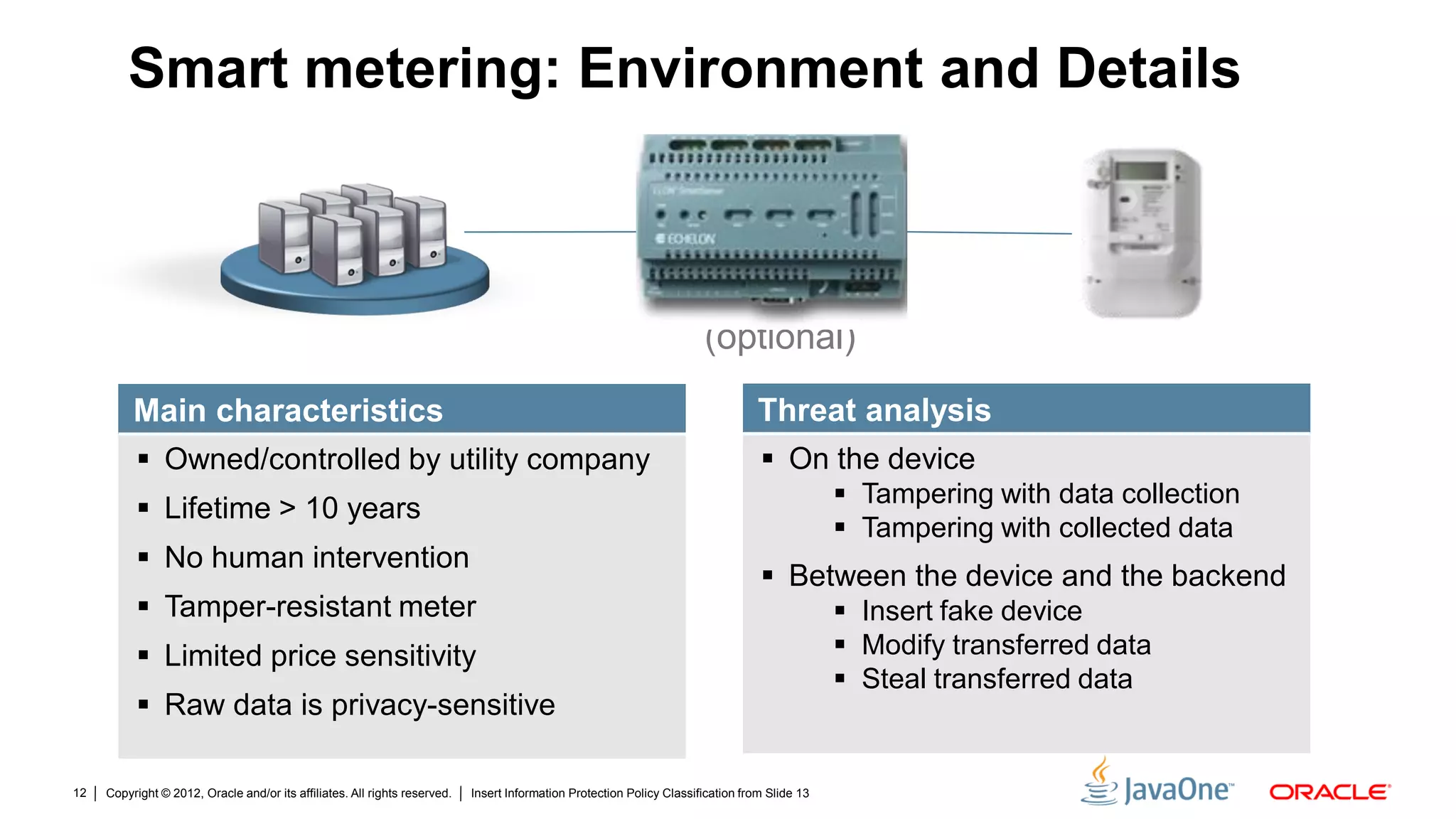
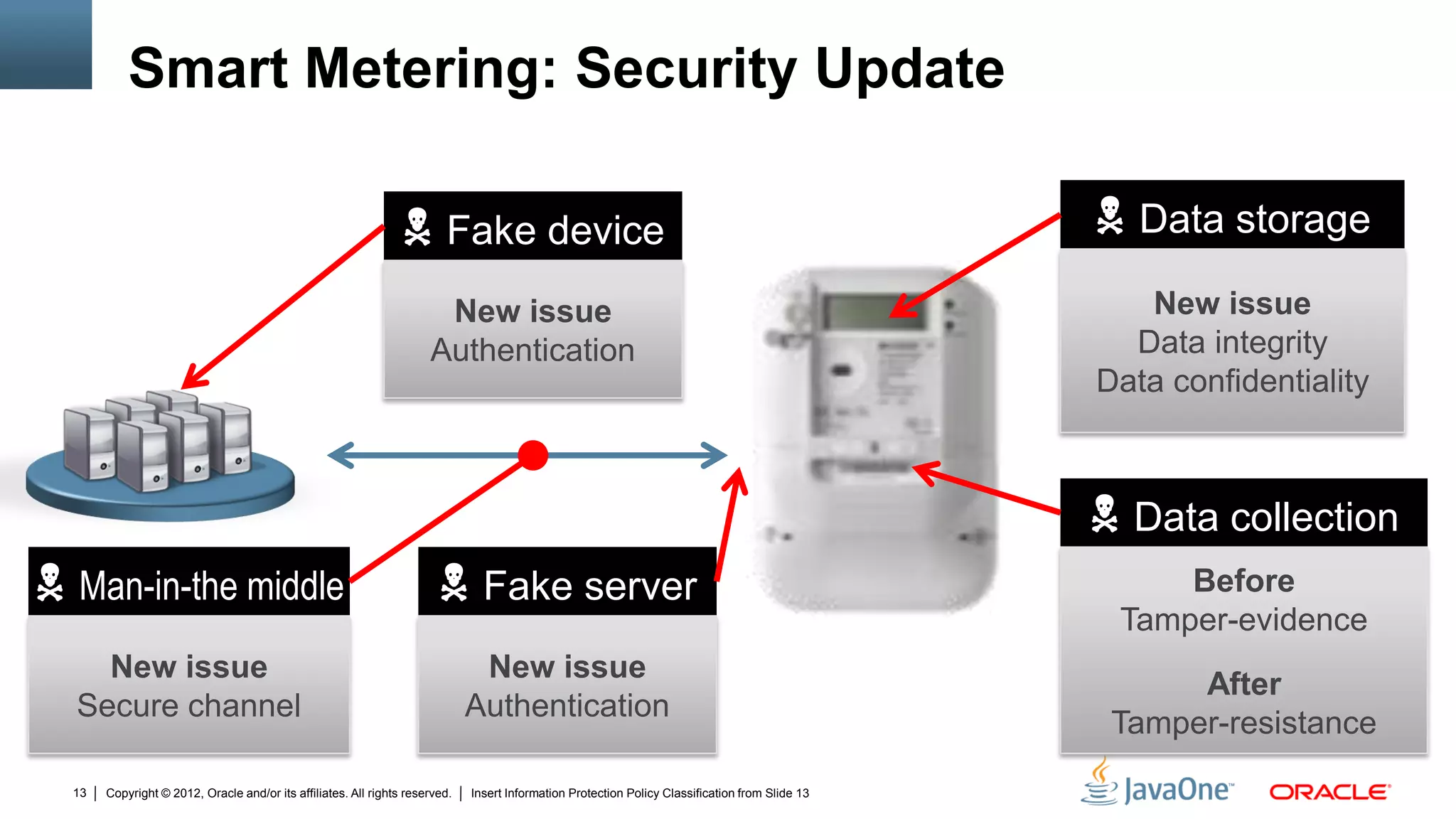
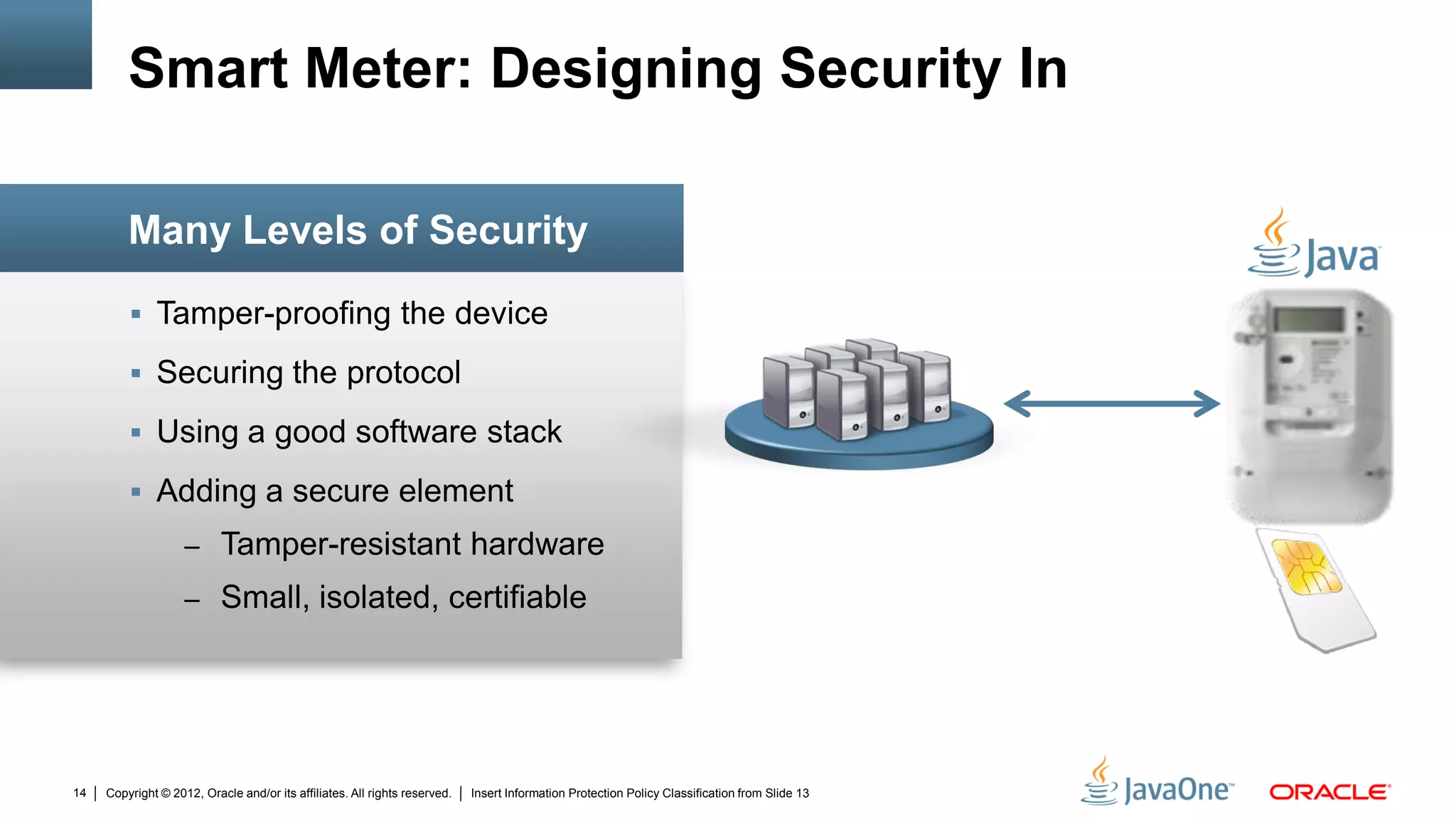
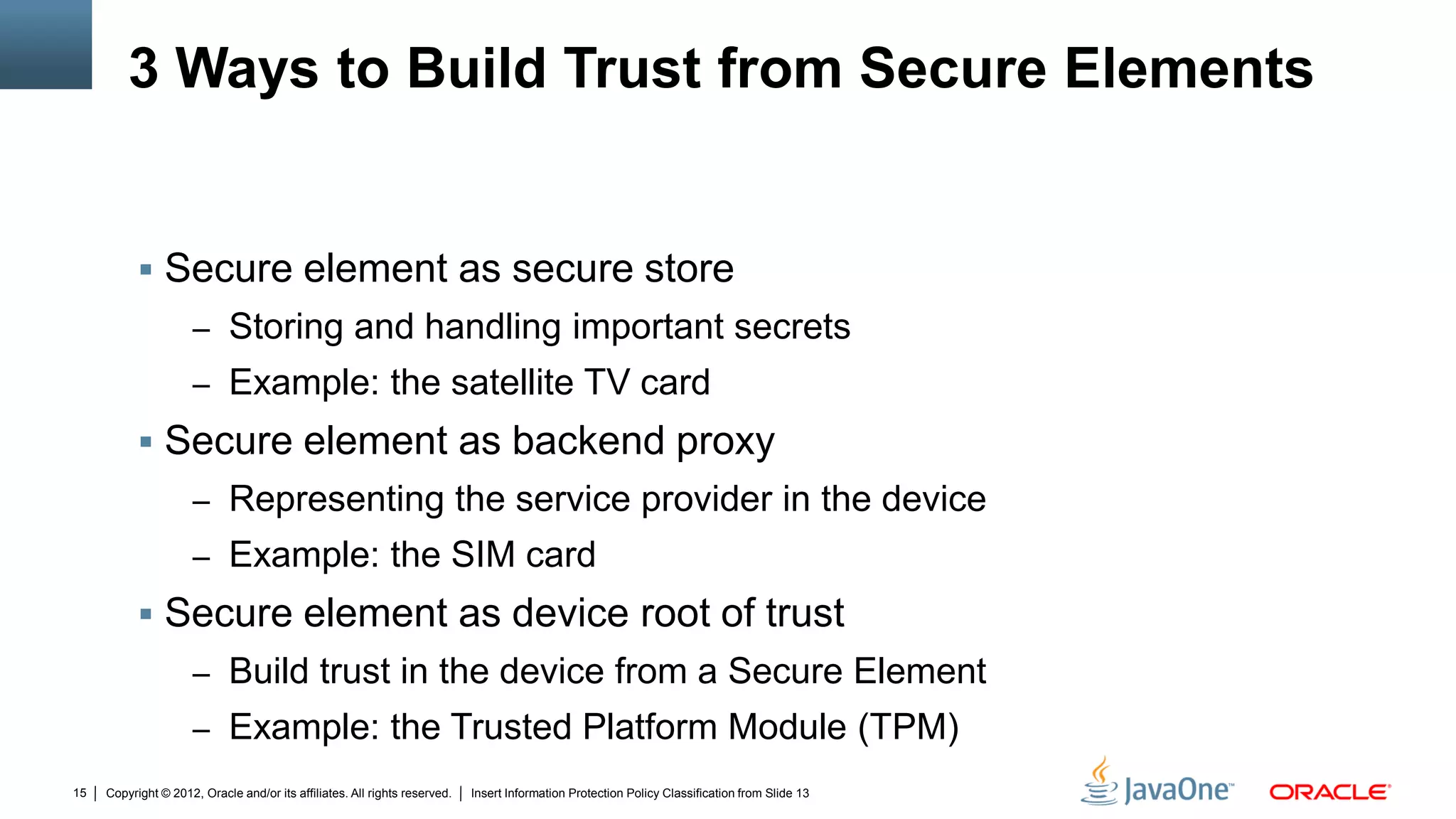
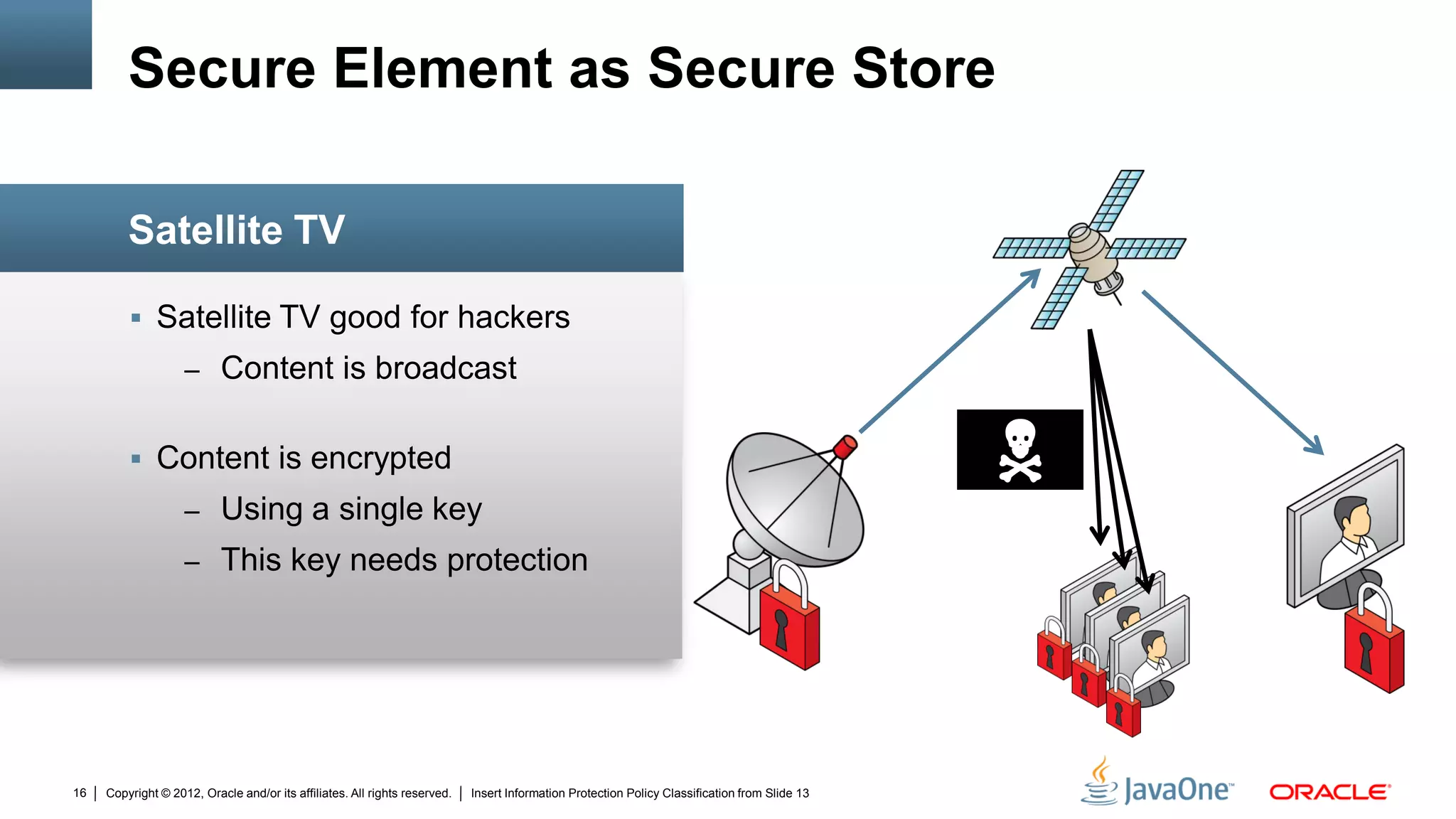
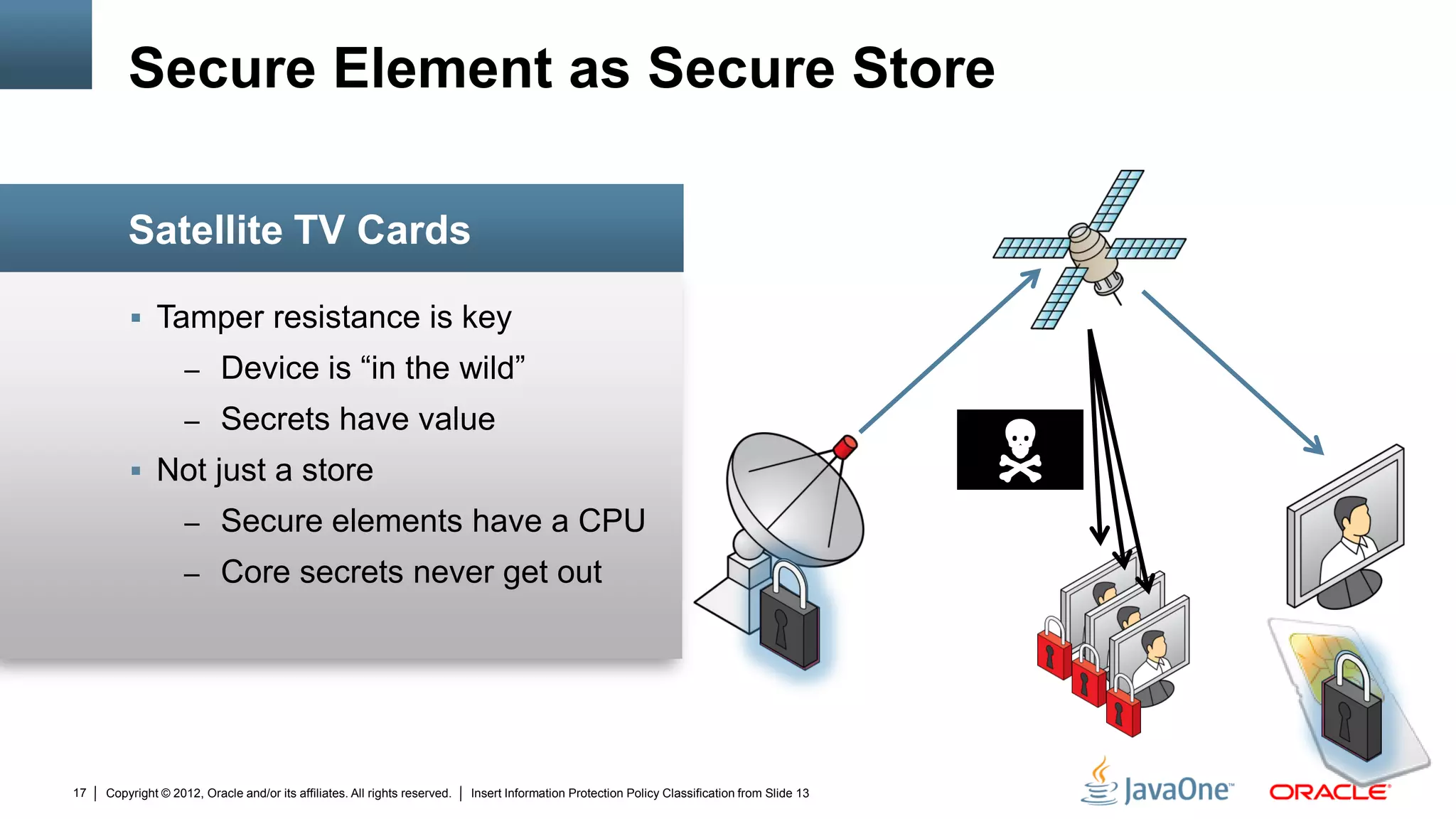
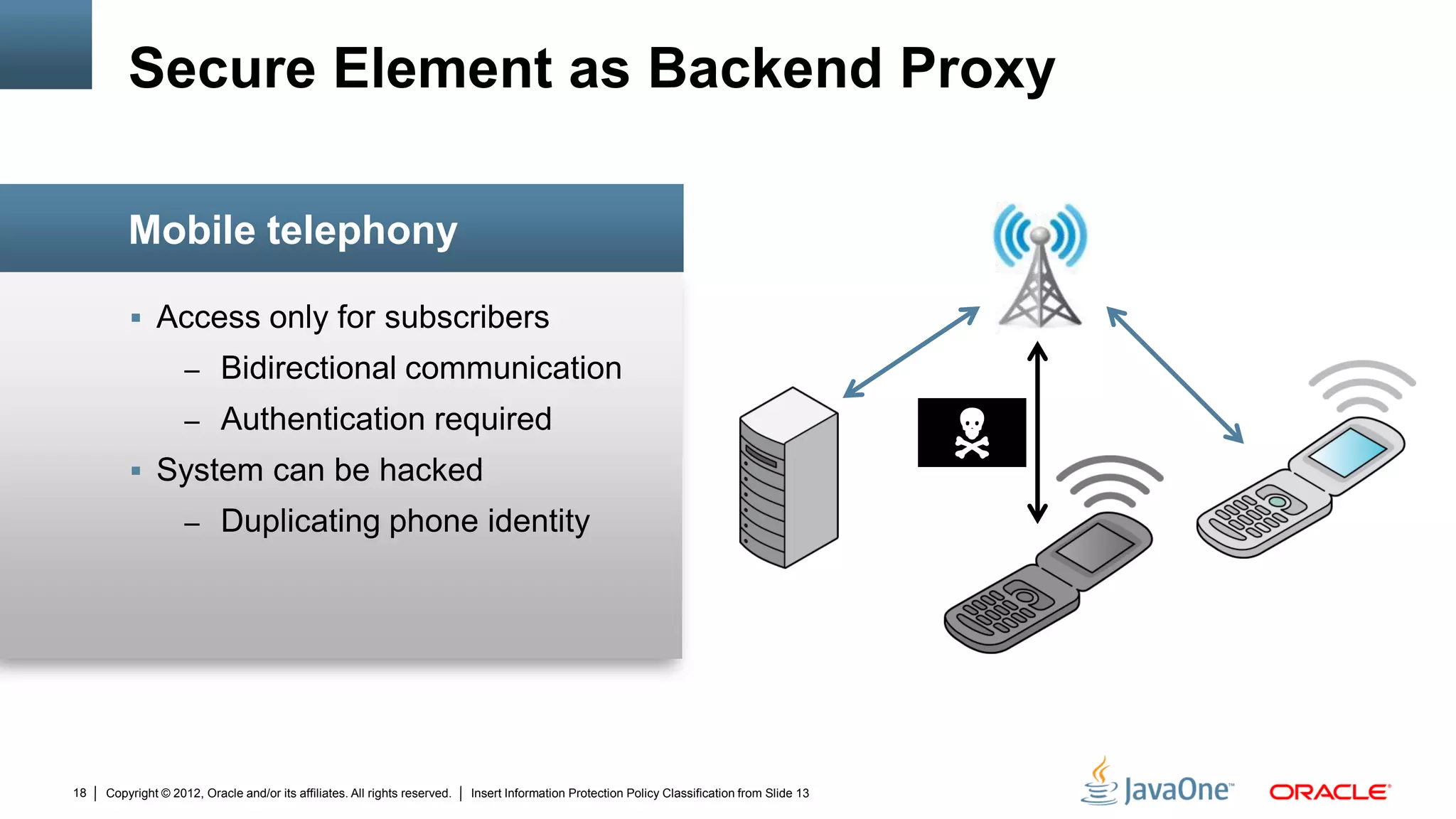
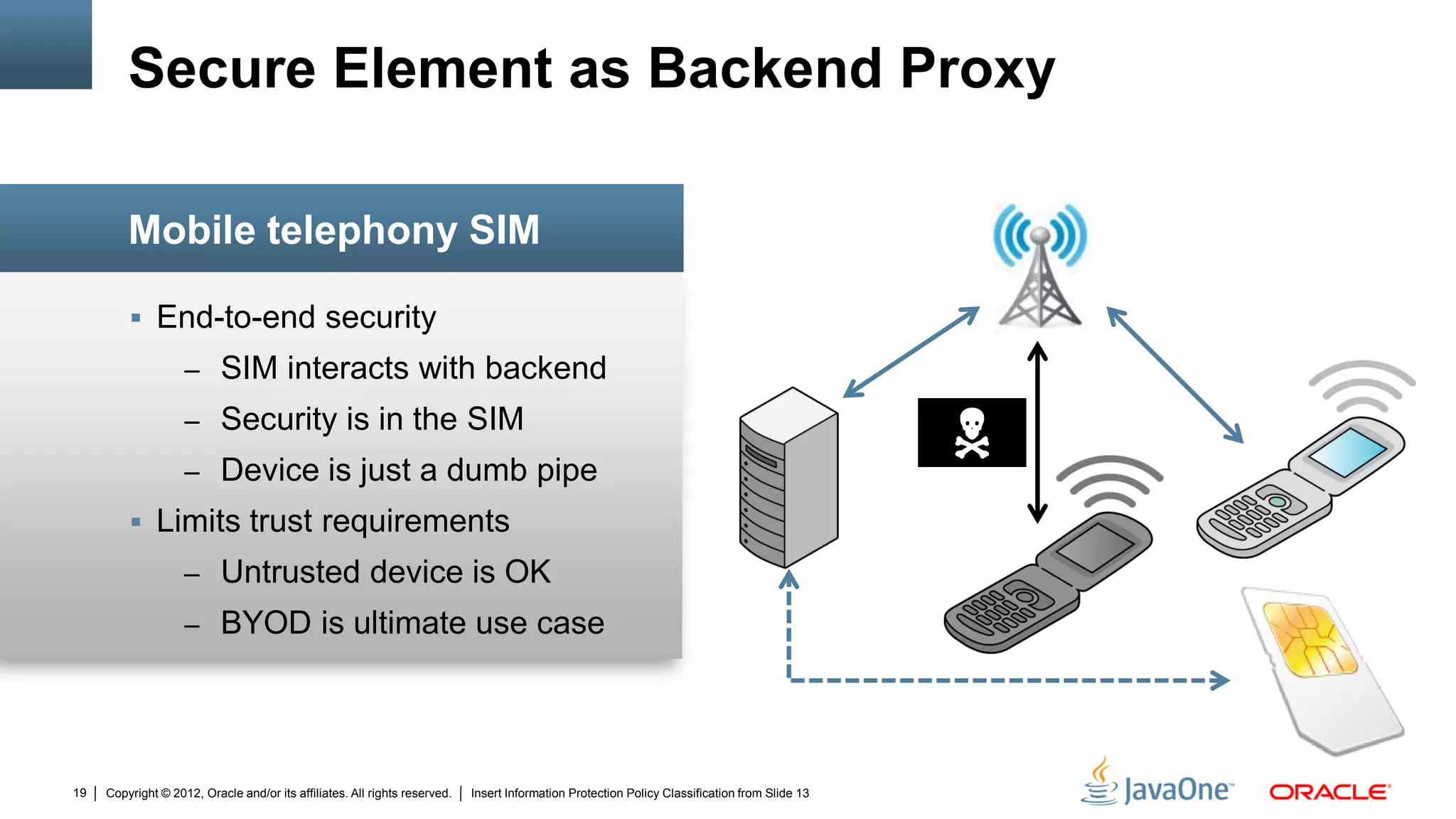
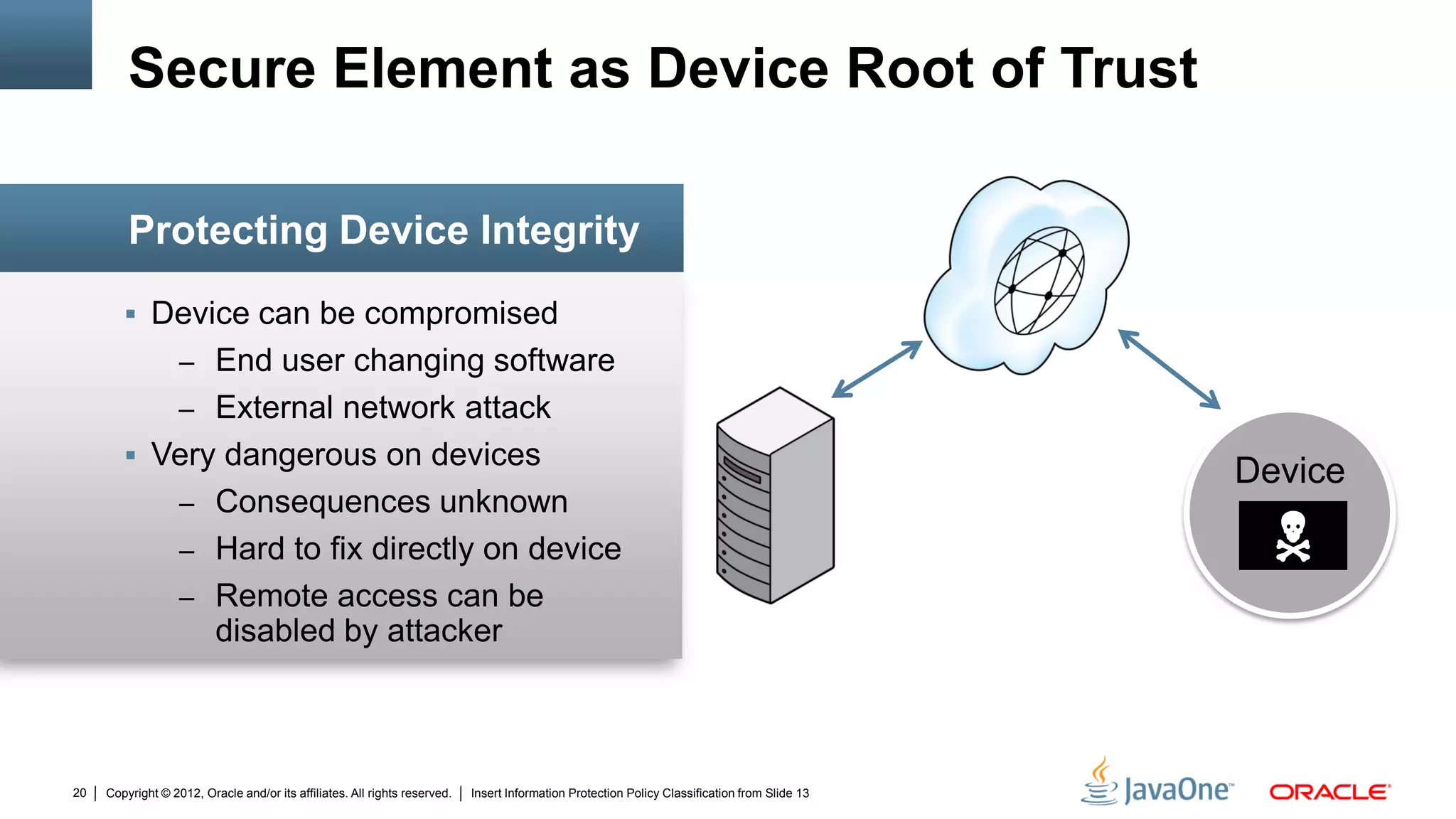
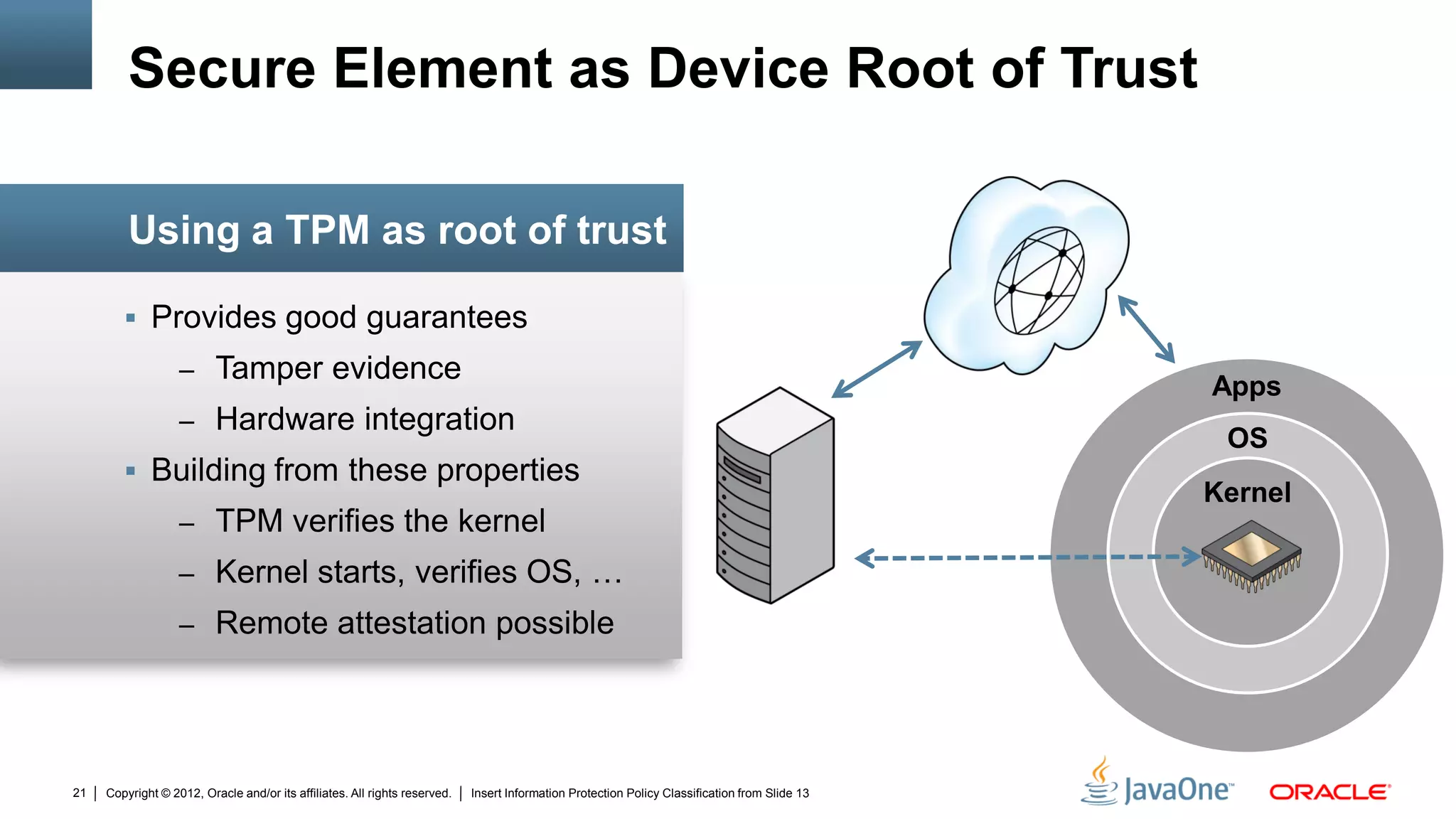
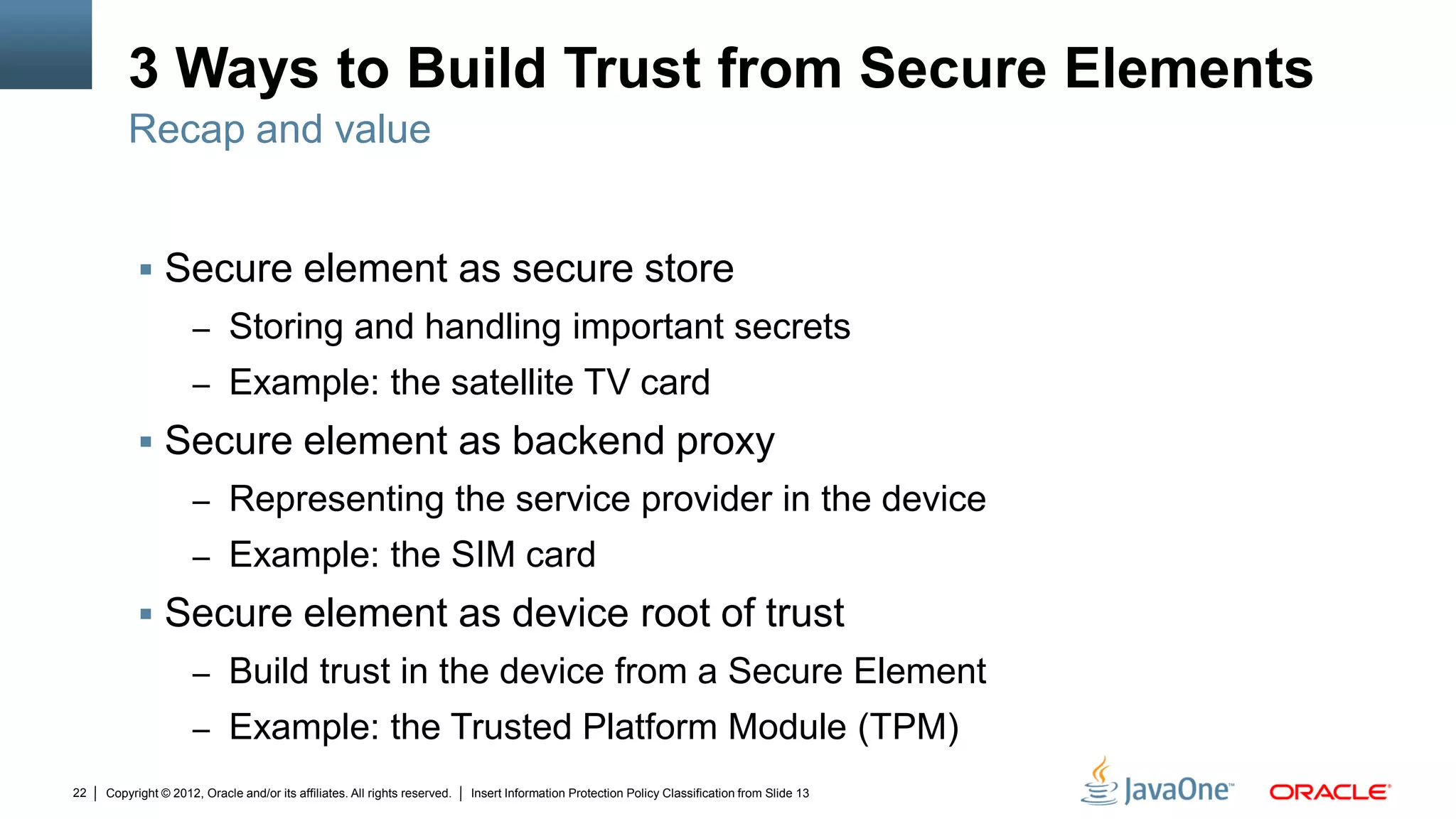
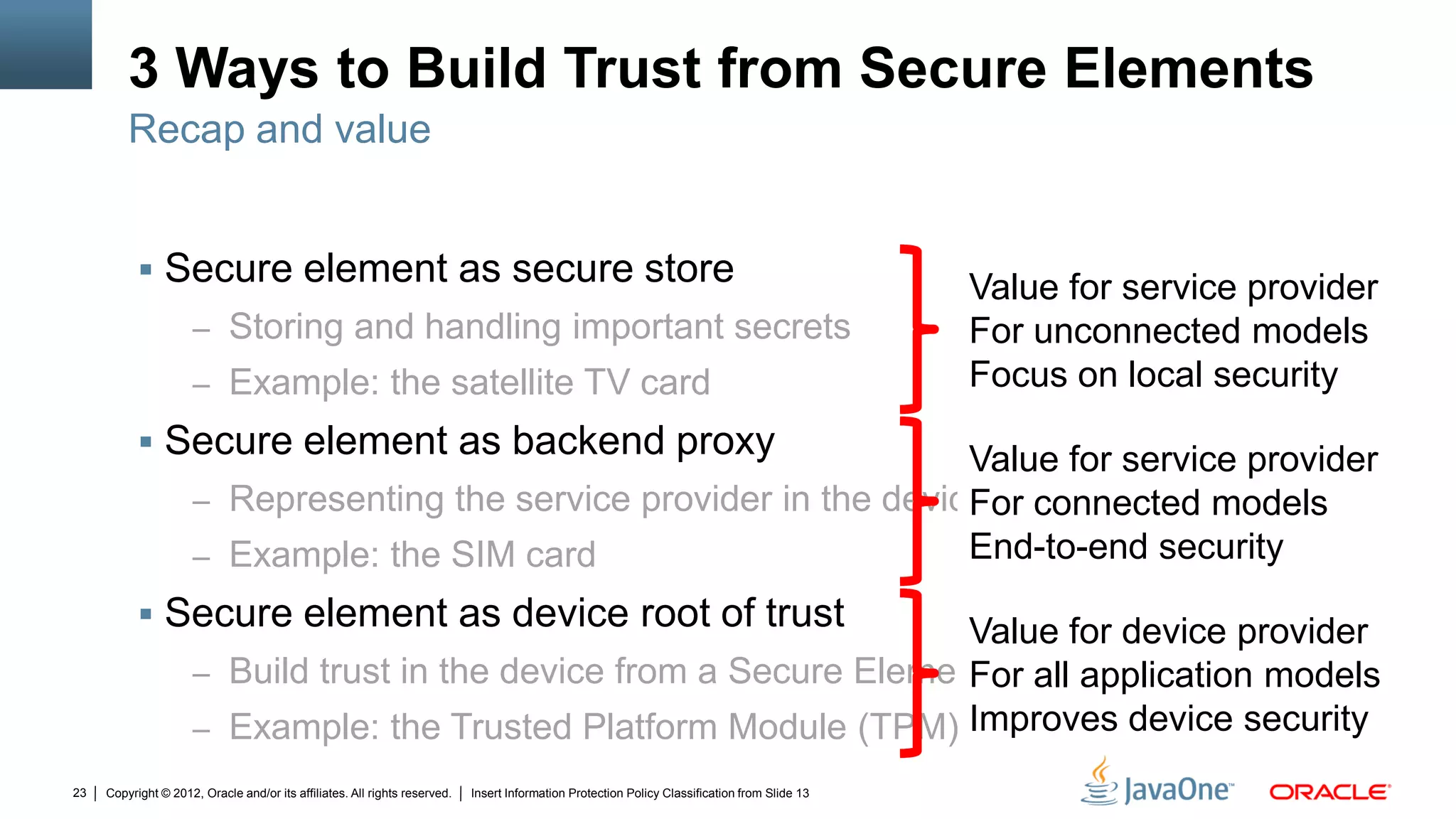
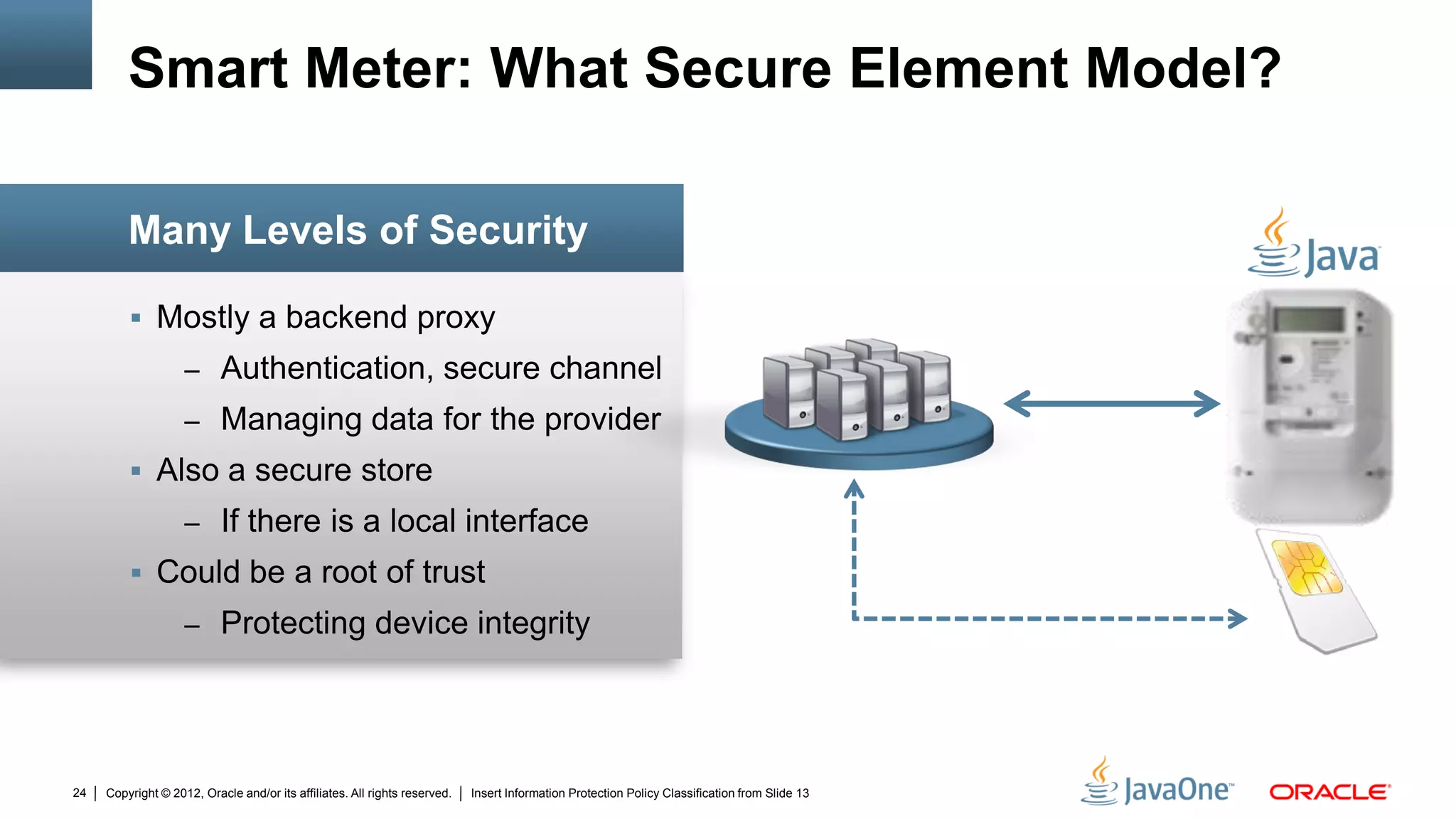
The document discusses security challenges and strategies for embedded systems, particularly smart meters, highlighting the importance of secure elements in building trust and protecting against attacks. It outlines main security requirements, functions, and the necessity for integrating security measures during device development. Additionally, it emphasizes the role of Java Card technology in programming secure elements to enhance overall security in edge-to-enterprise environments.