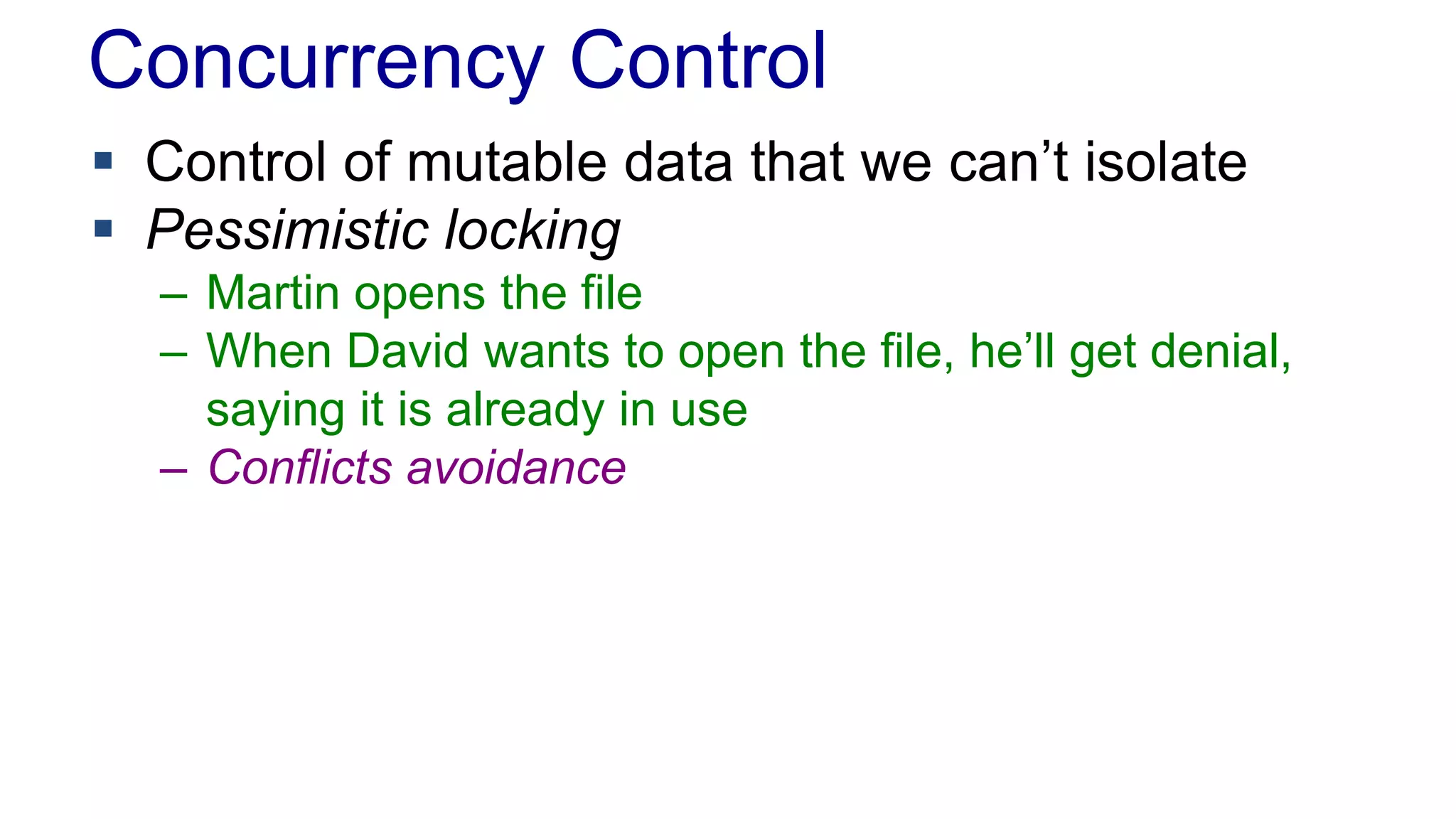
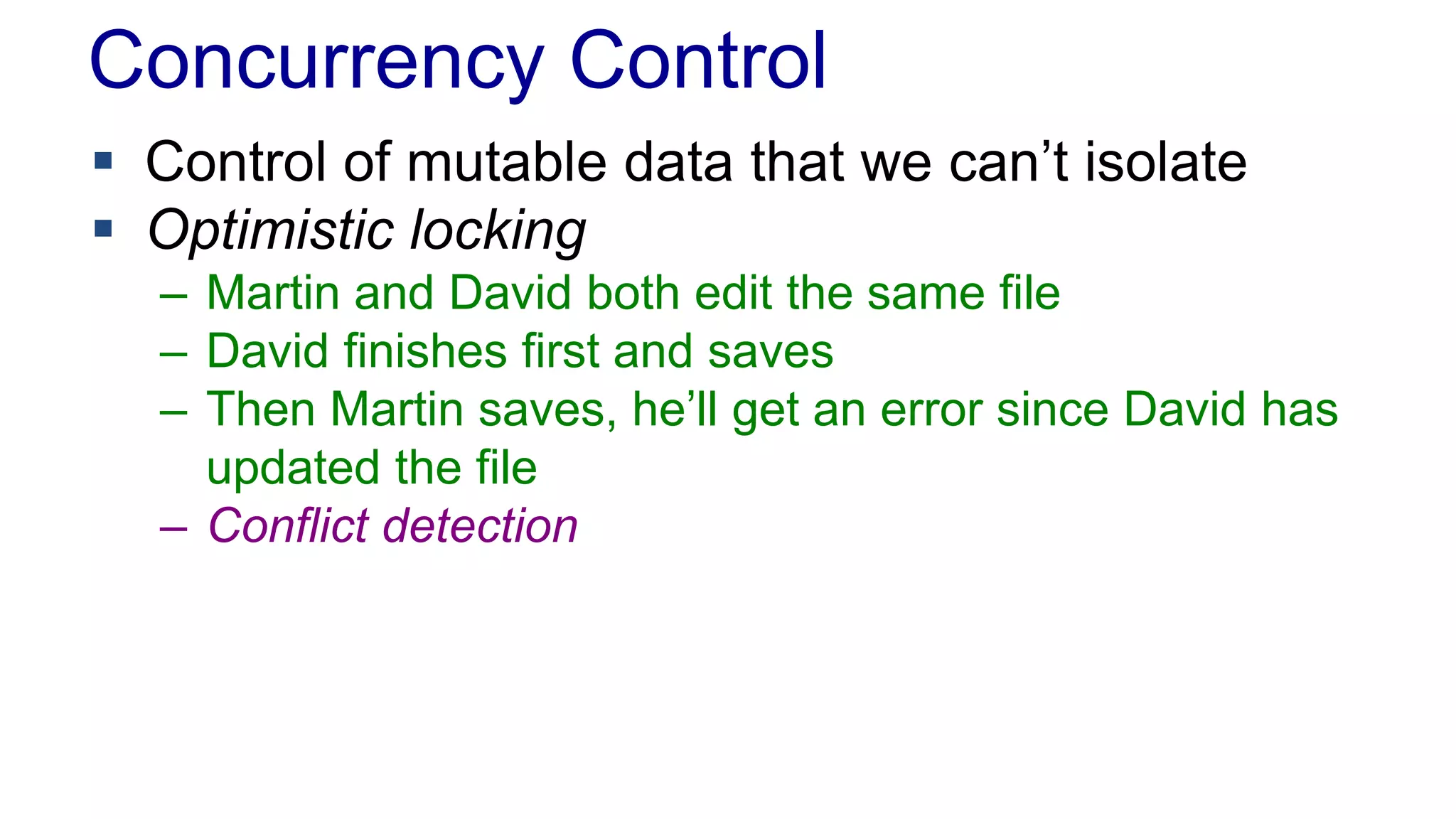
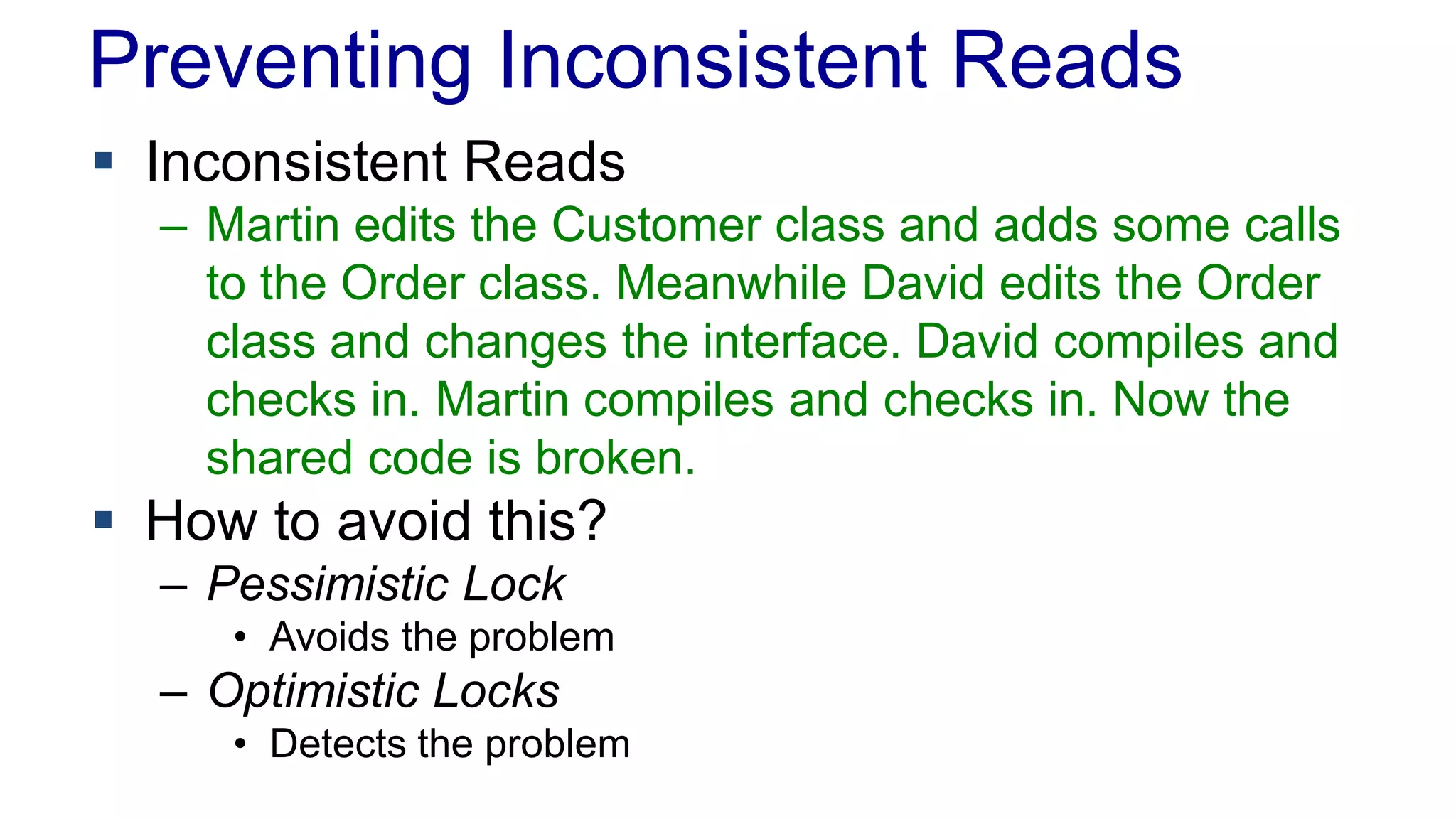
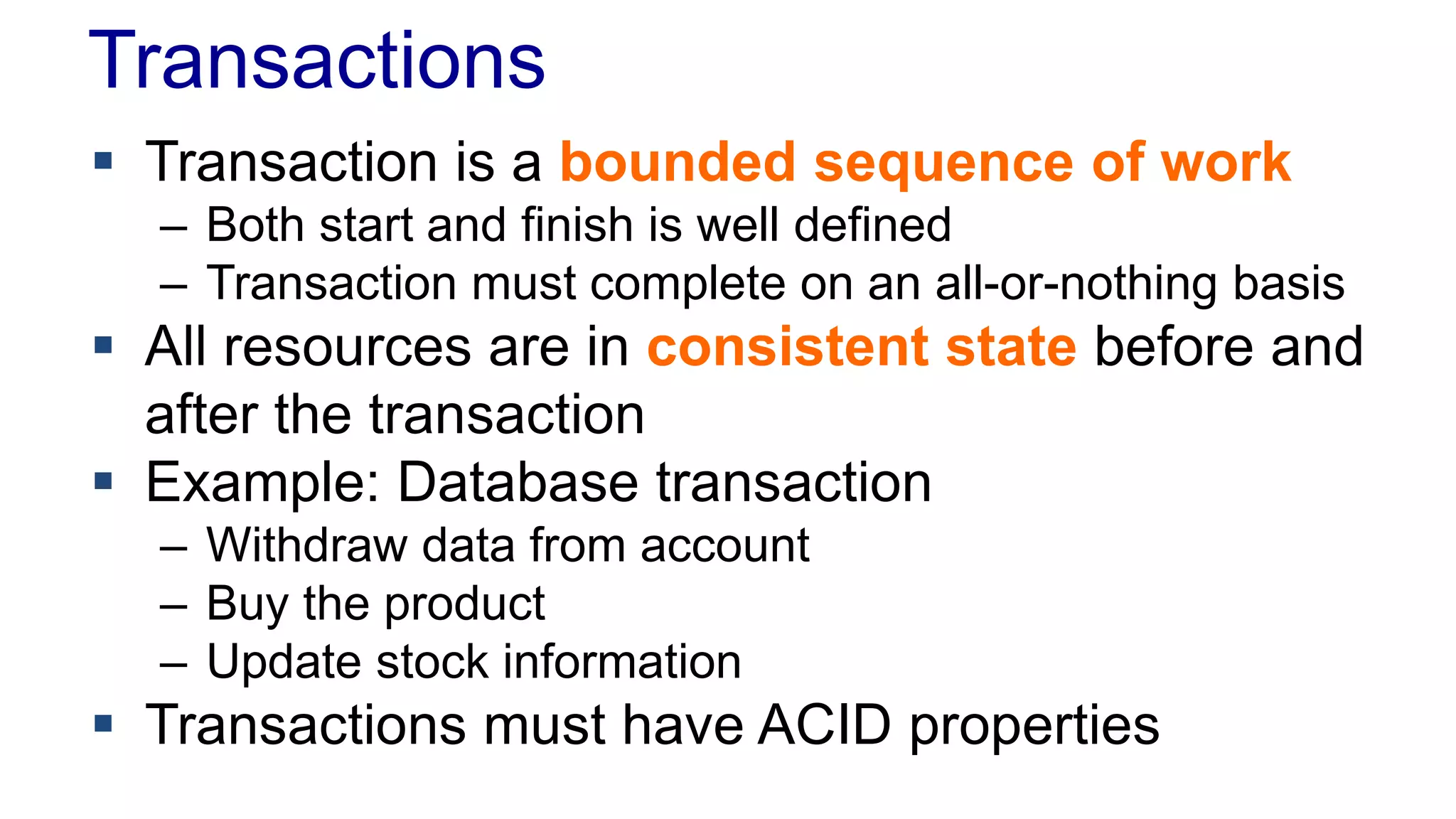
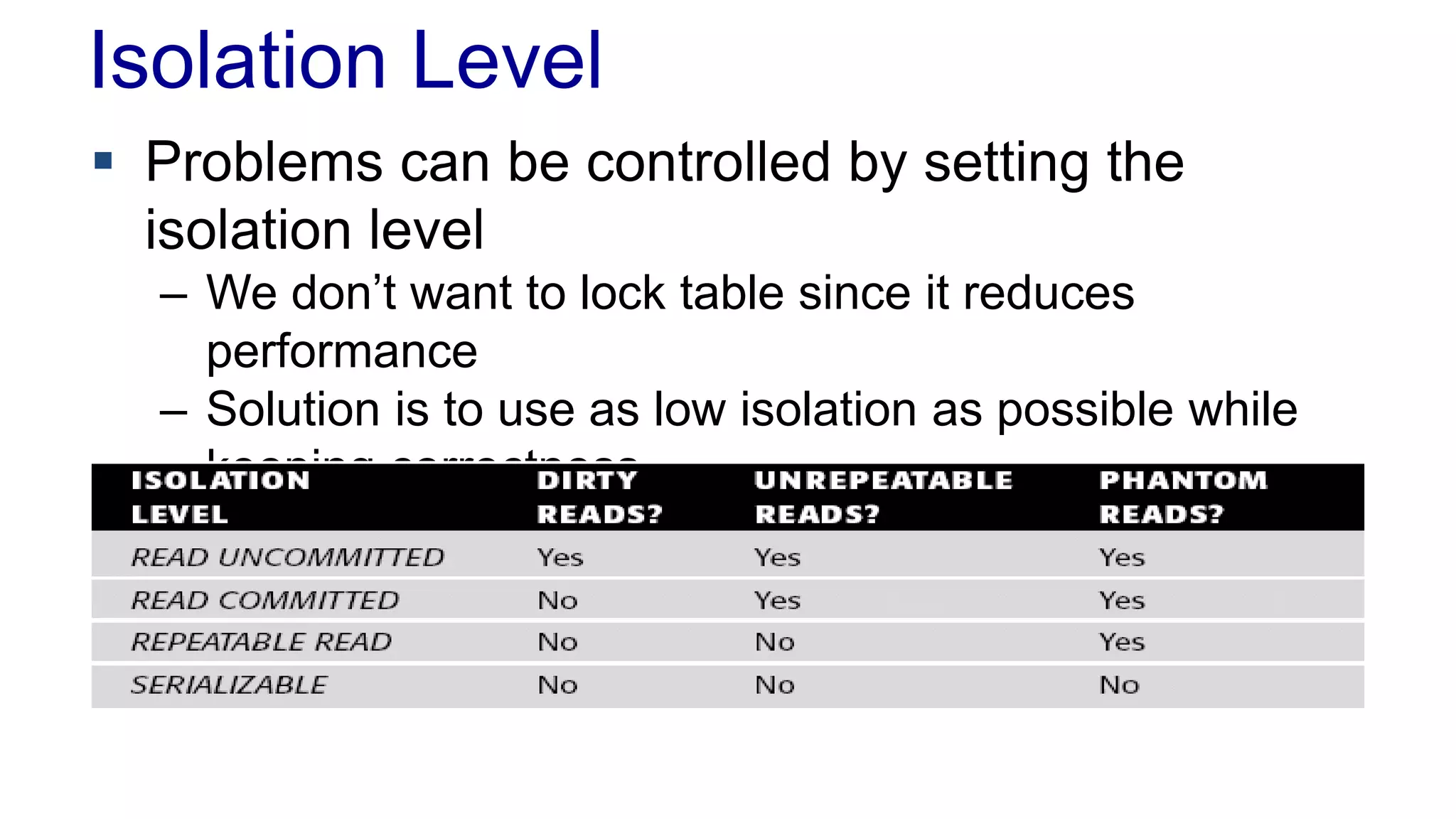
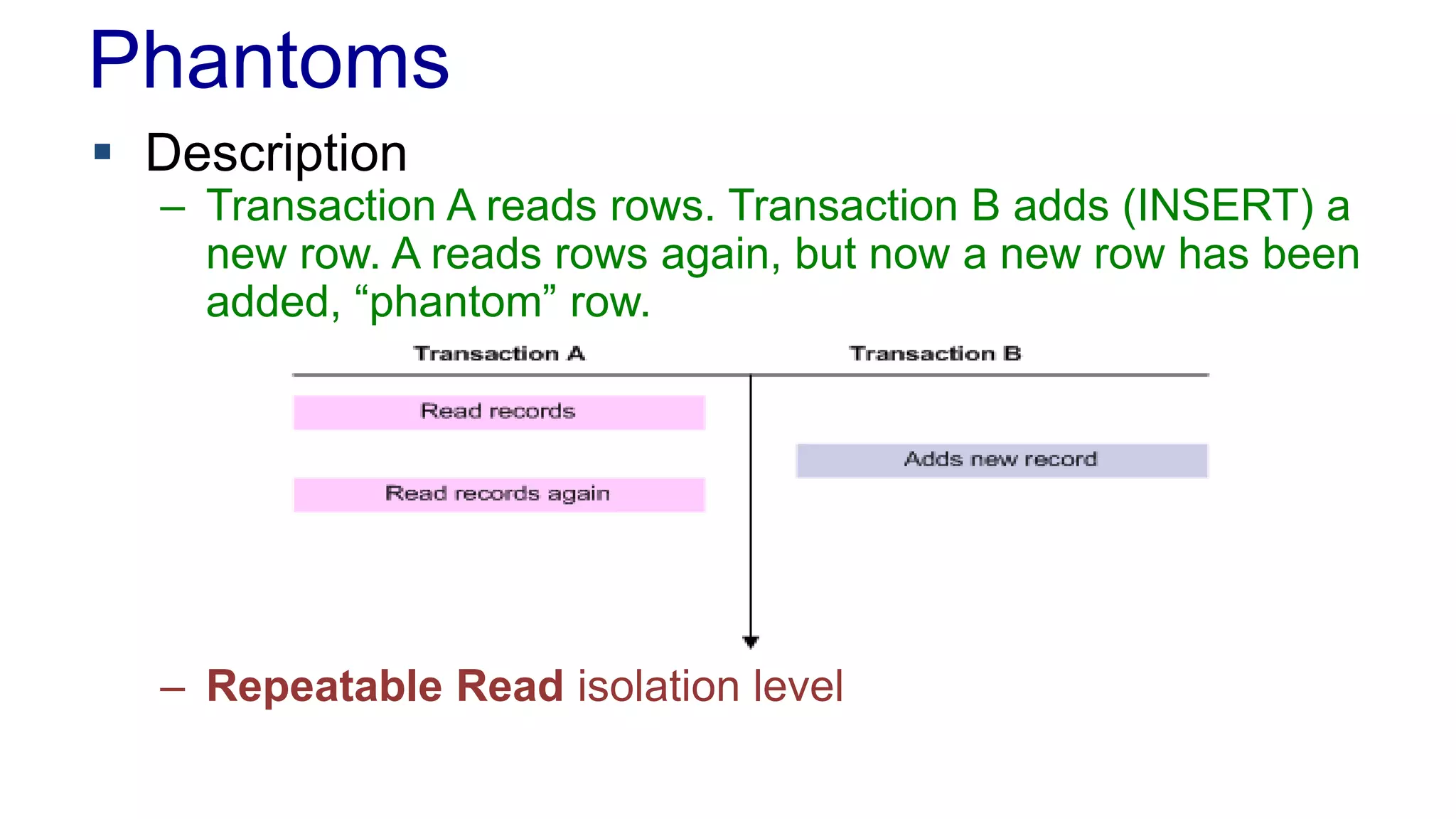
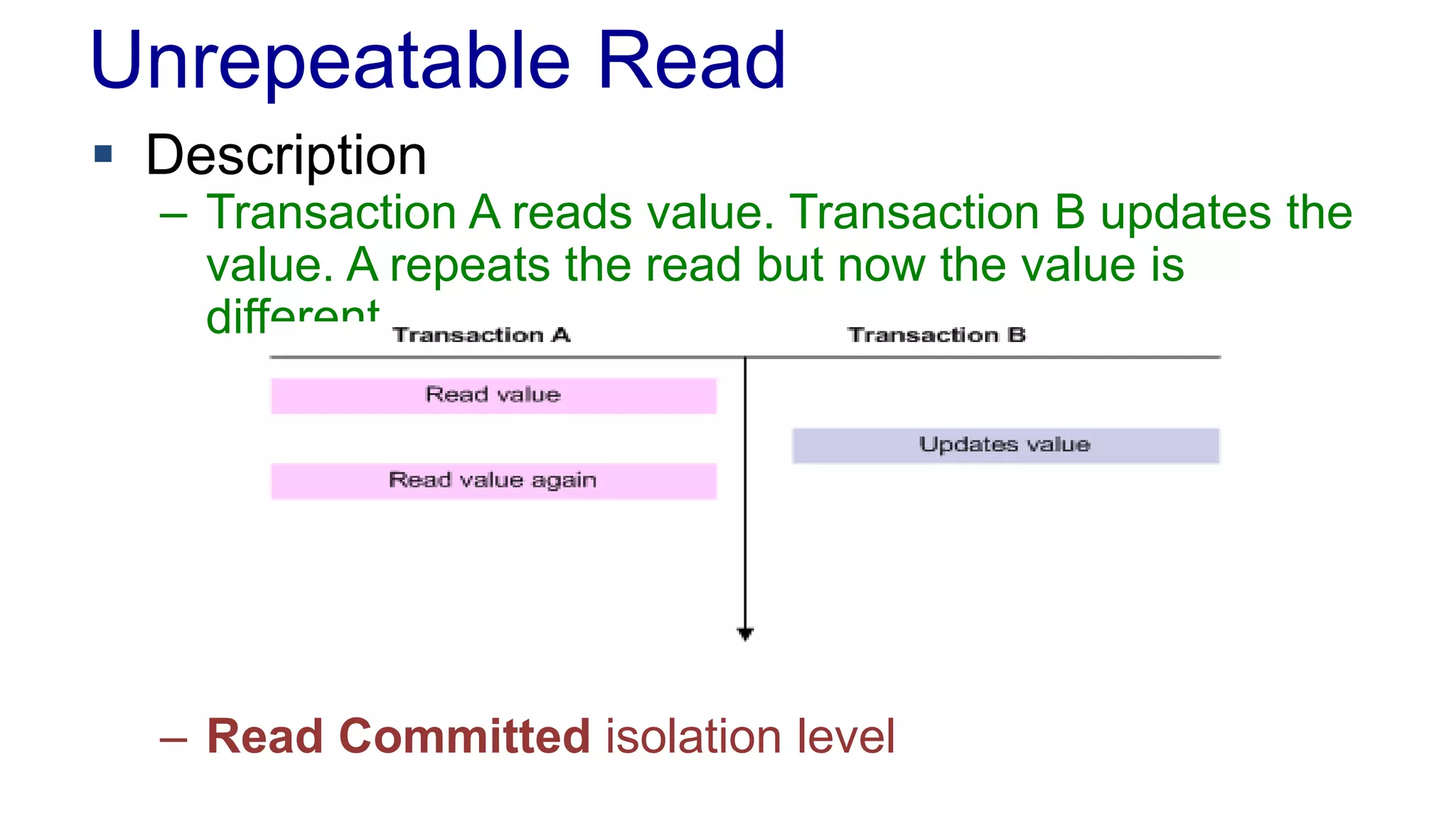
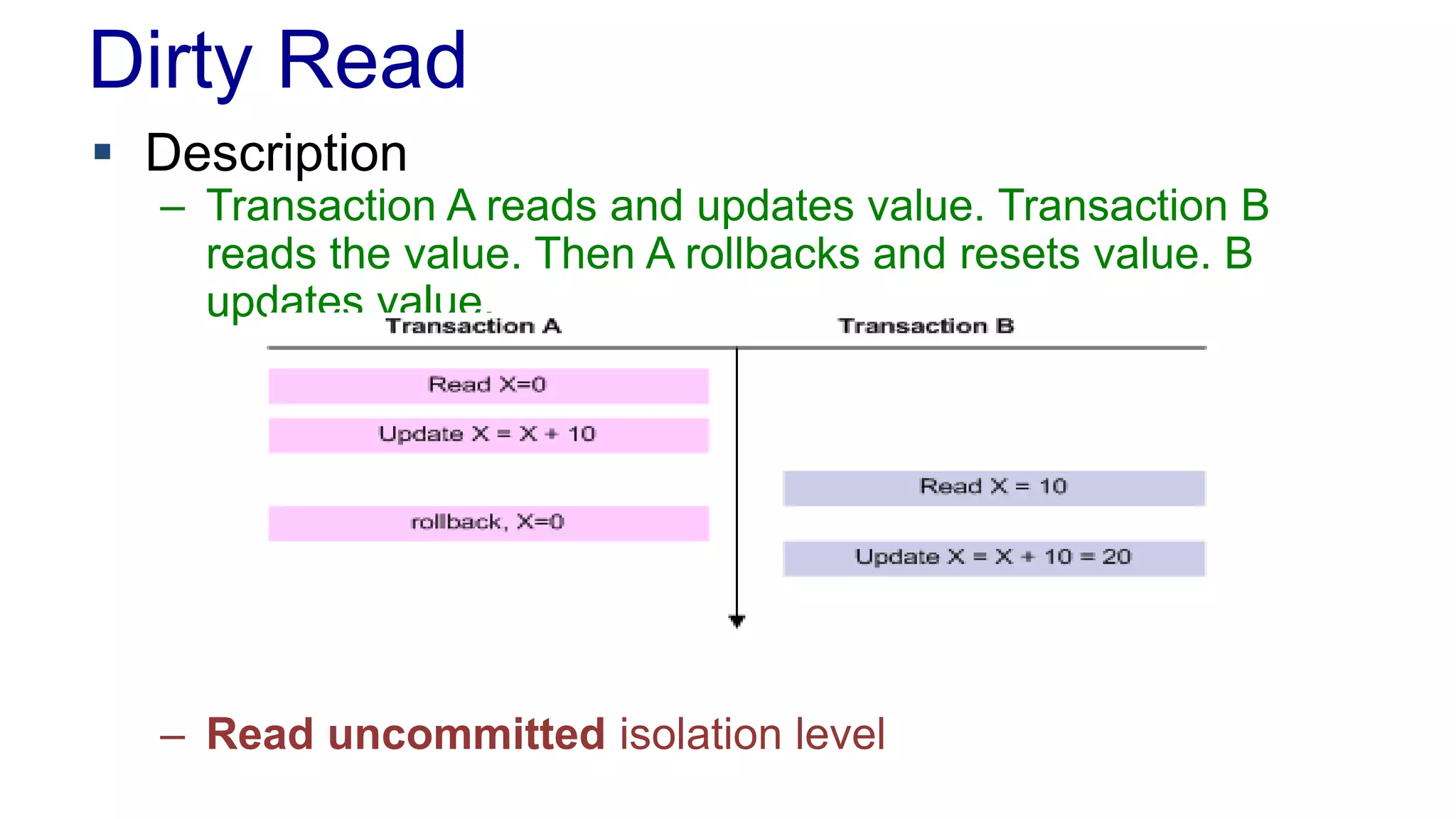
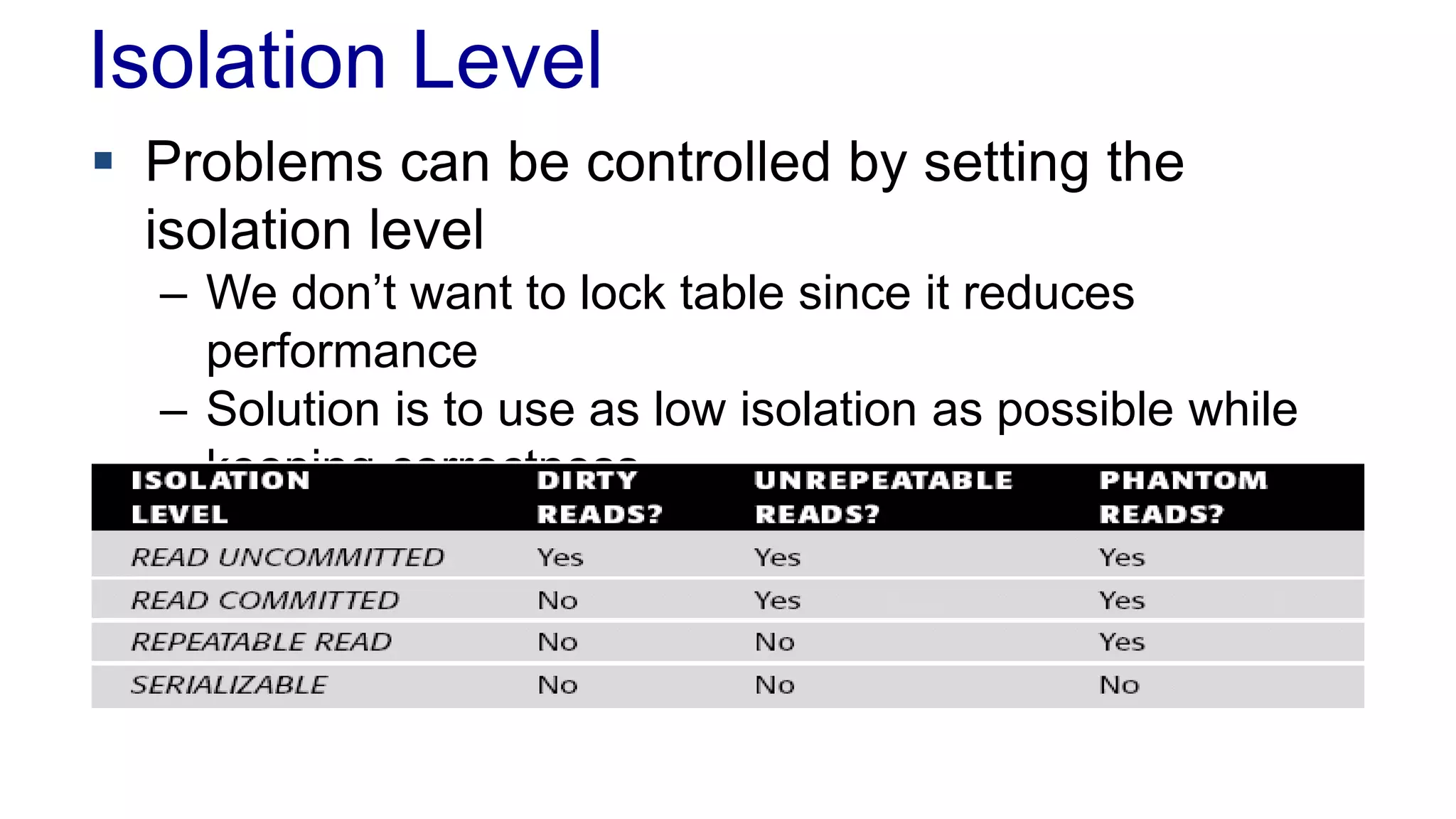
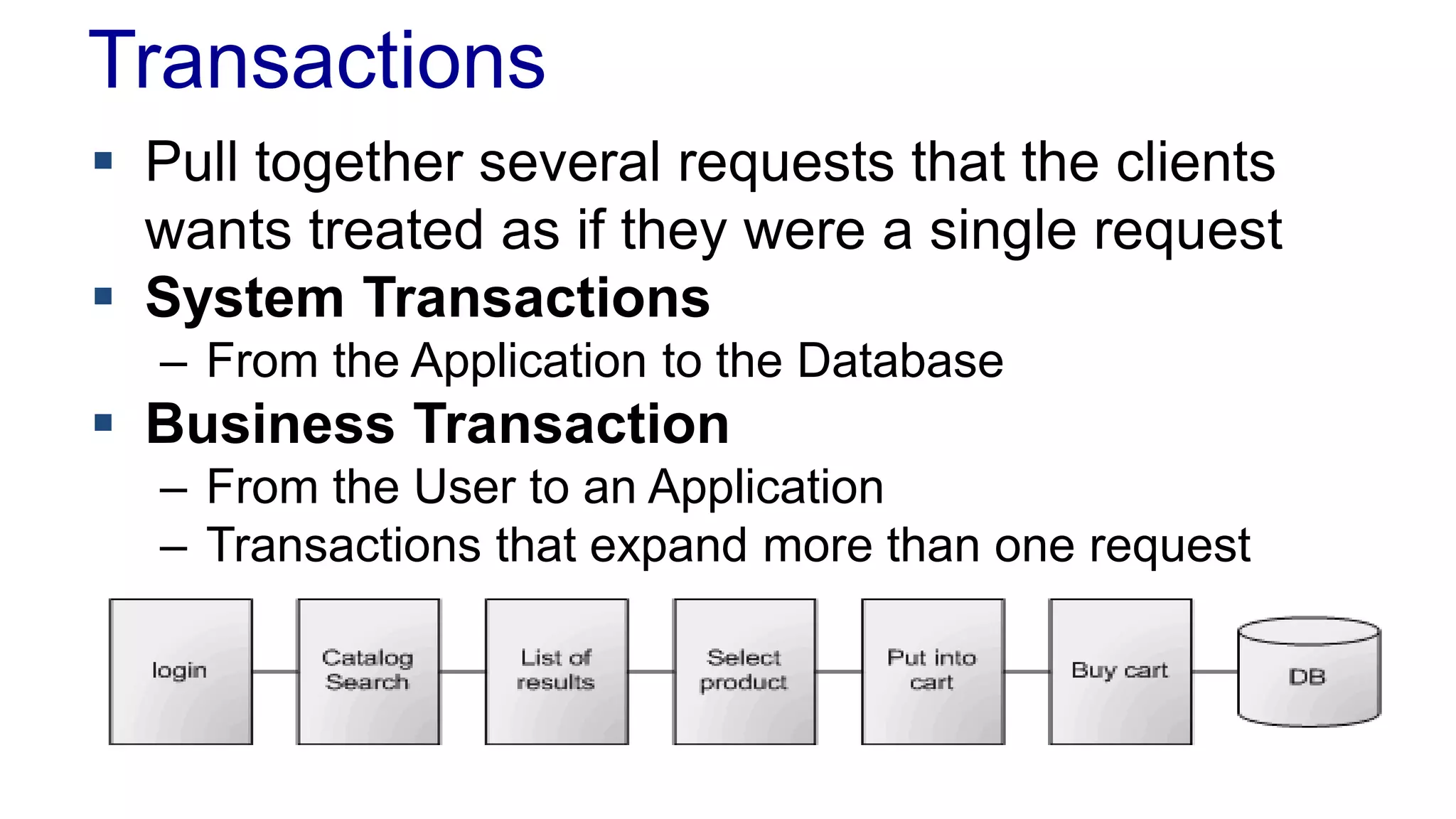
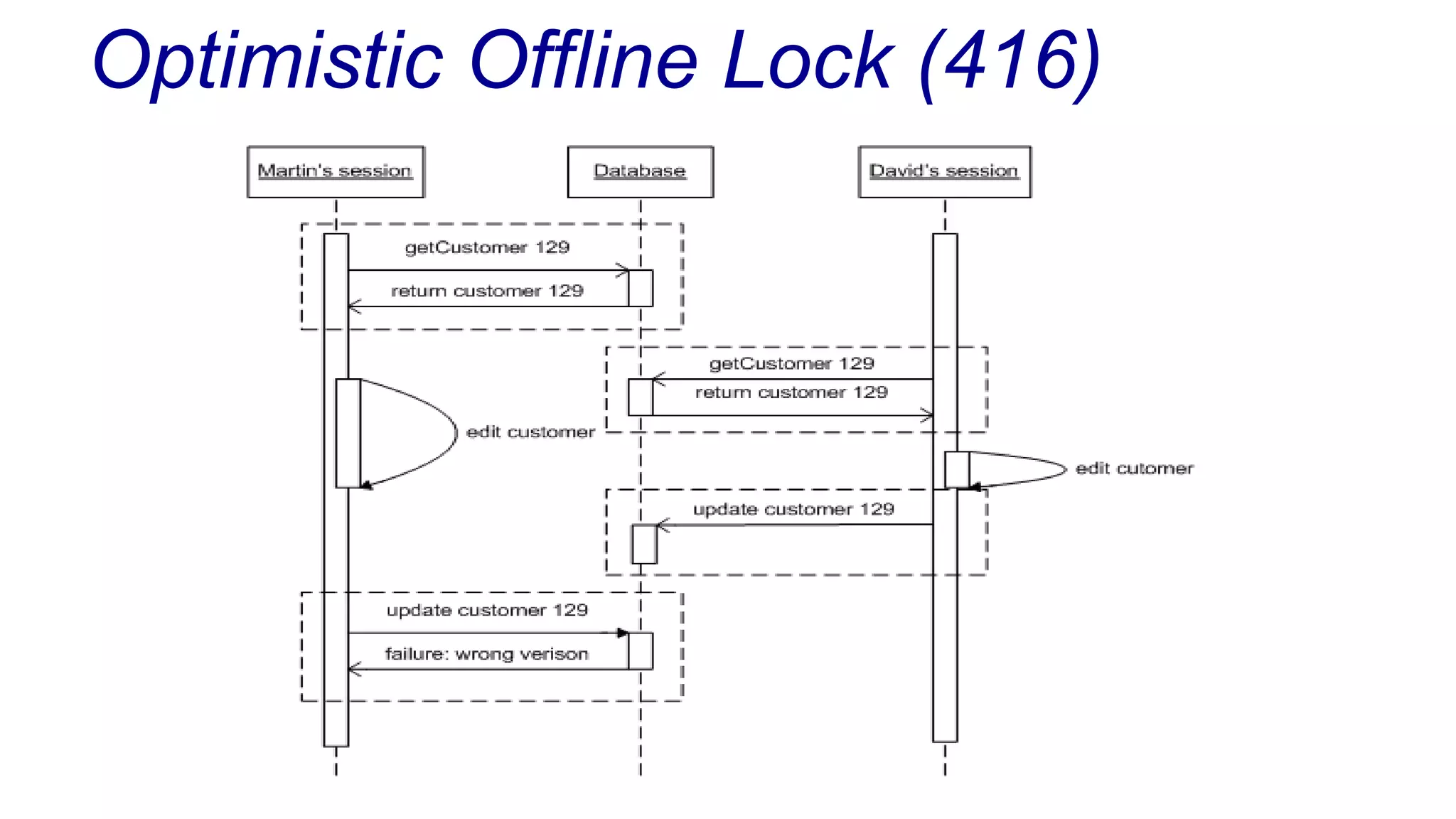
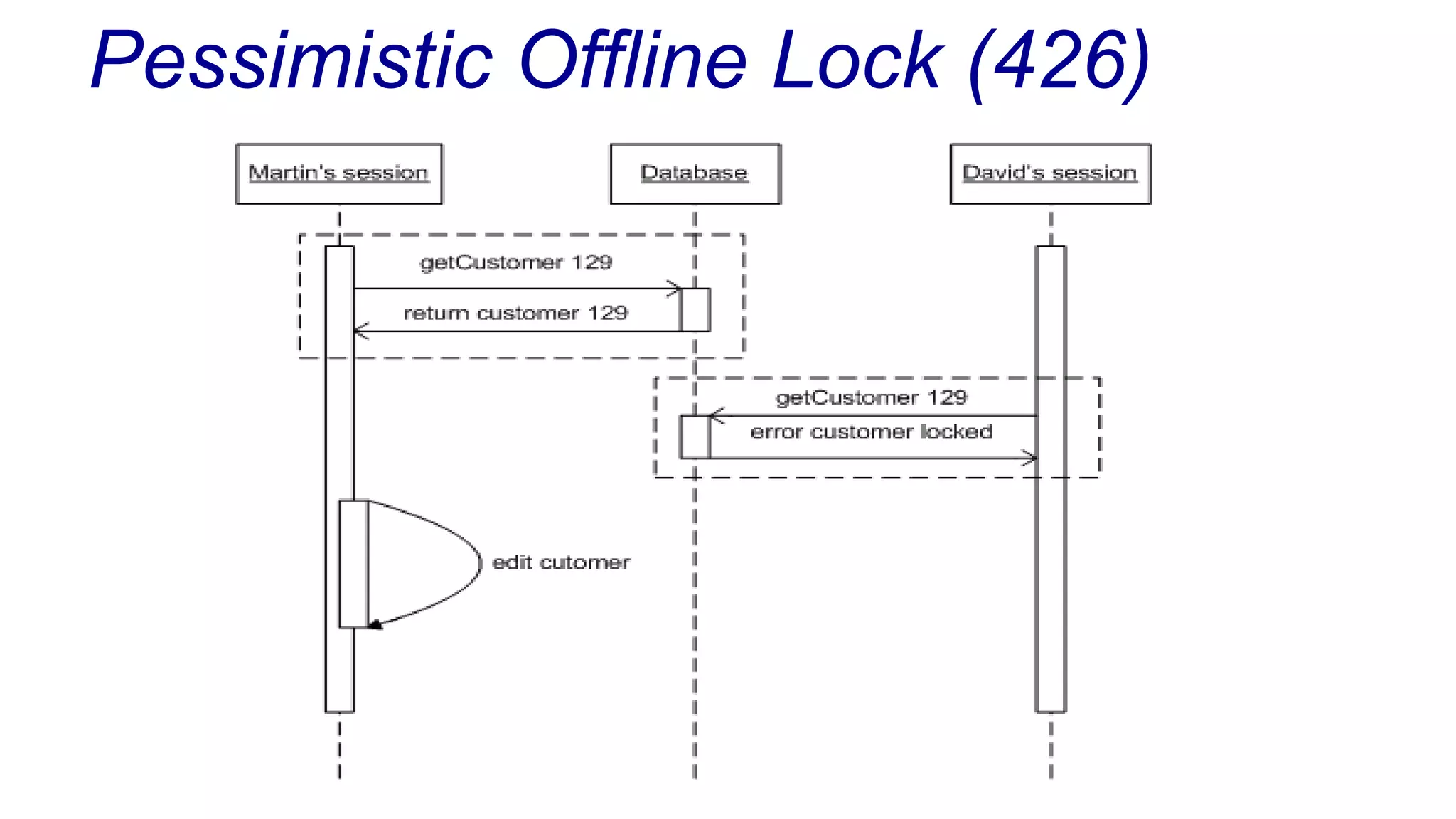
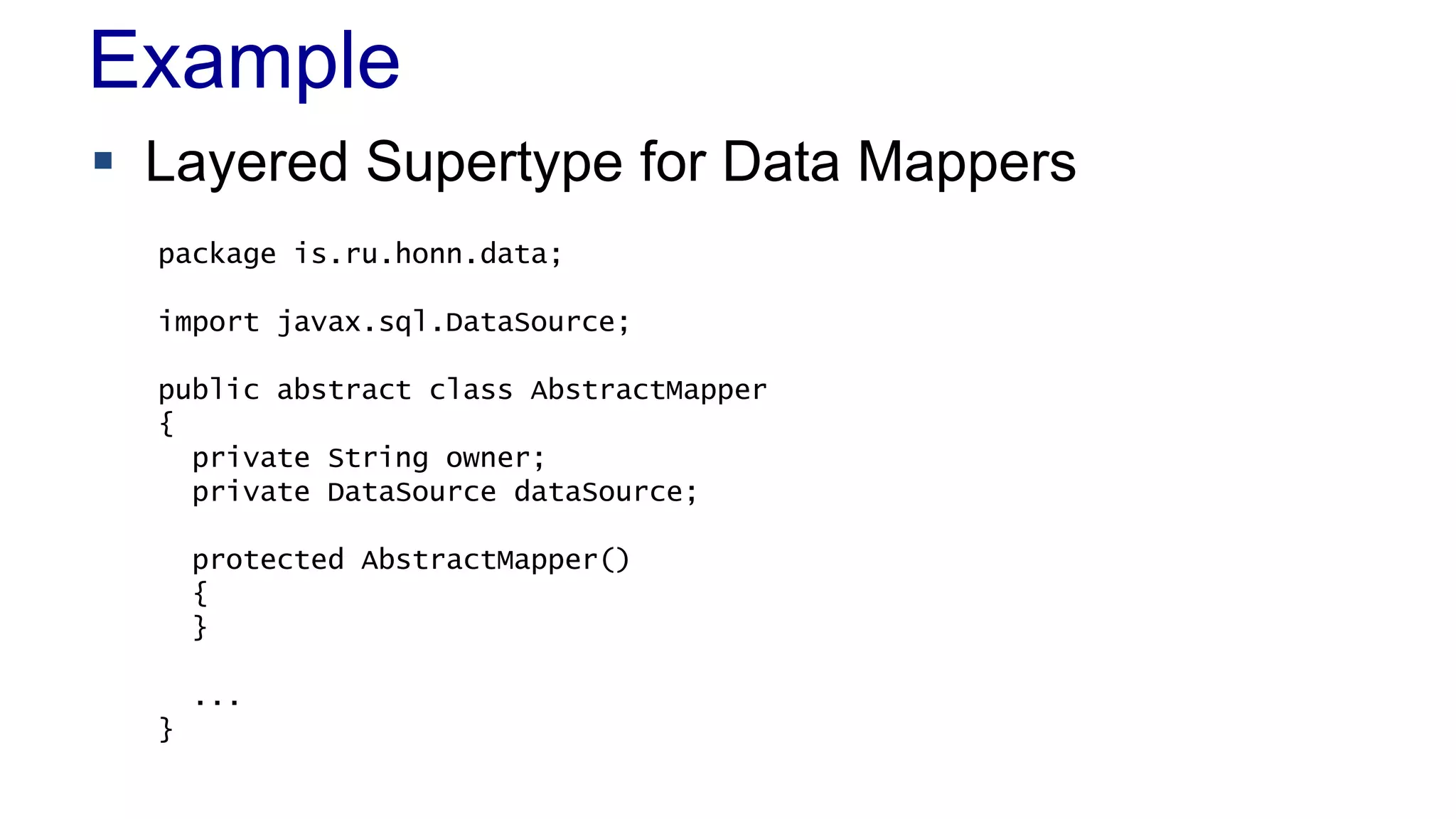
The document discusses concurrency in programming, highlighting various issues such as race conditions, deadlocks, and inconsistent reads, and elaborates on solutions like optimistic and pessimistic locking. It emphasizes the importance of transactions maintaining ACID properties and presents strategies to control concurrent access to data effectively. Additionally, it provides practical examples of implementing locking mechanisms and explores the implications of different isolation levels on performance and correctness.





















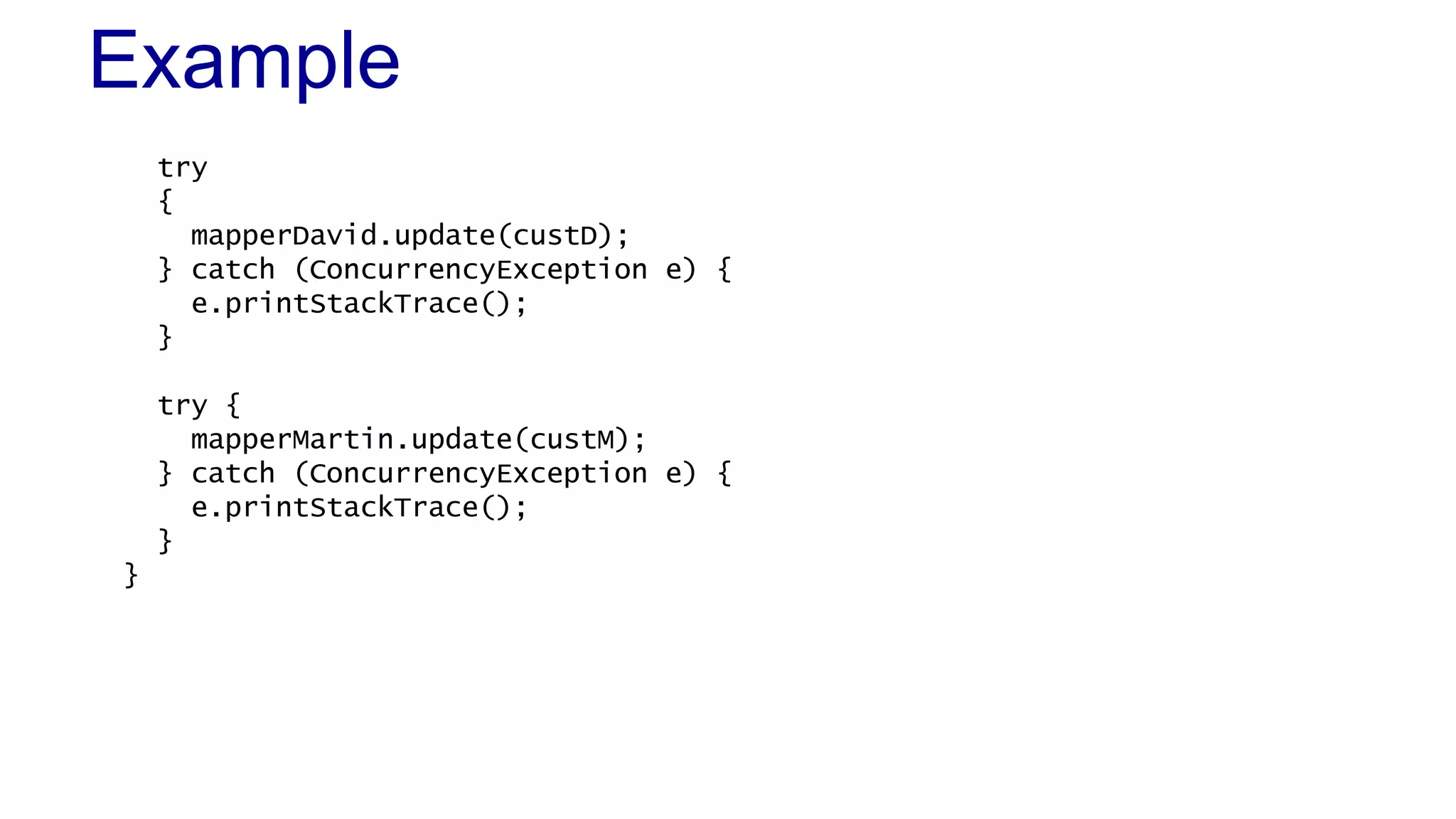
![Example
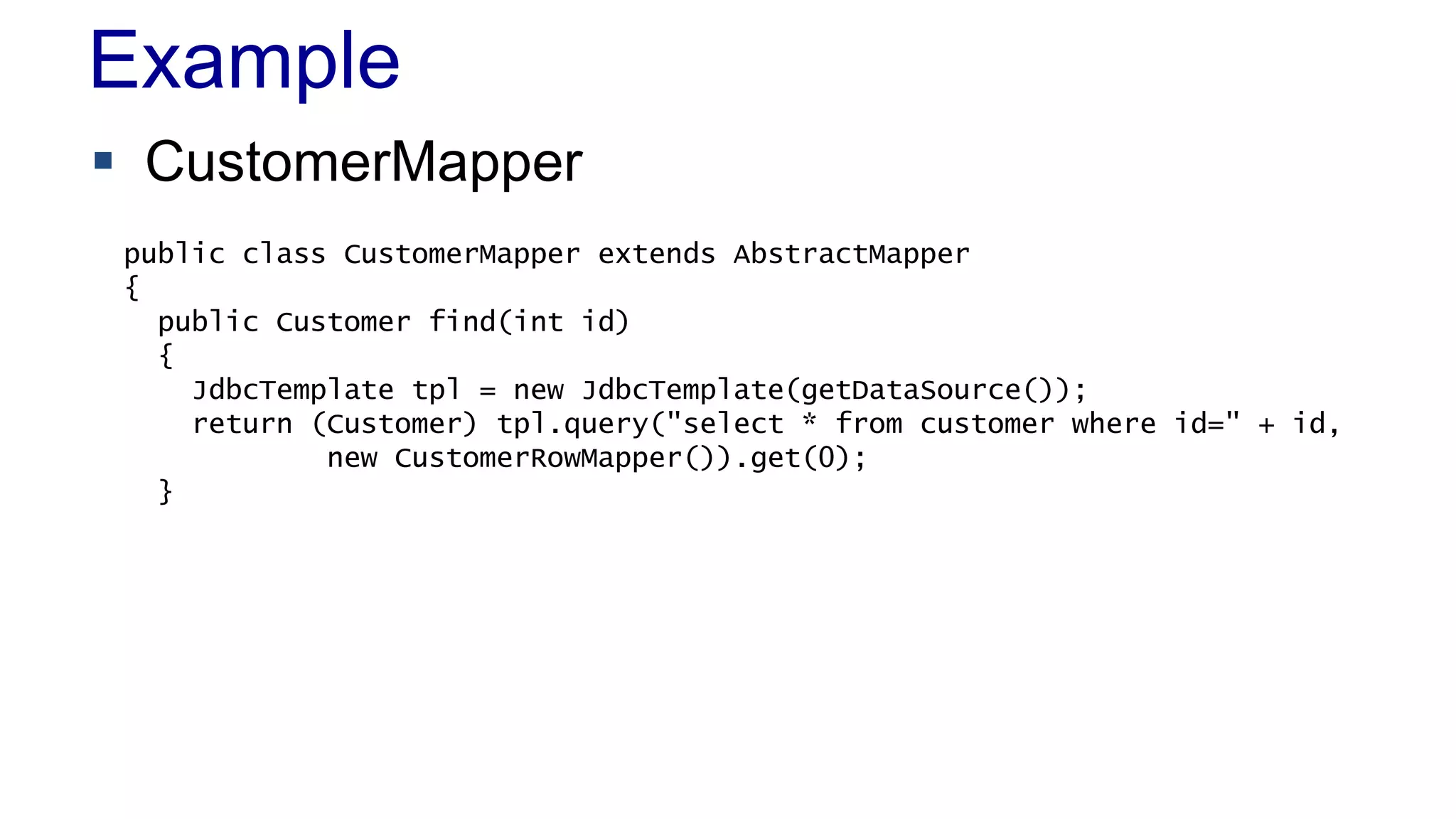
CustomerMapper
public void update(Customer customer) throws ConcurrencyException
{
Customer current = find(customer.getId());
if (current.getVersion() > customer.getVersion())
throw new ConcurrencyException("Customer has been changed by " +
current.getModifiedBy() + " at " +
current.getModified() + " (version: " + customer.getVersion() + ")");
JdbcTemplate tpl = new JdbcTemplate(getDataSource());
tpl.update("update customer set name=?, modifiedby=?, modified=?, " +
"version=? where id=?",
new Object[]
{
customer.getName(),
this.getOwner(),
new Date(),
customer.getVersion() + 1,](https://image.slidesharecdn.com/l12concurrentprogramming-131112130603-phpapp02/75/L12-Concurrent-Programming-39-2048.jpg)
![Example
public static void main(String[] args)
{
Resource resource = new FileSystemResource("data.xml");
BeanFactory beanfactory = new XmlBeanFactory(resource);
CustomerMapper mapperMartin = (CustomerMapper)beanfactory.getBean("customerMa
mapperMartin.setOwner("Martin");
CustomerMapper mapperDavid = (CustomerMapper)beanfactory.getBean("customerMap
mapperDavid.setOwner("David");
Customer custM = mapperMartin.find(1);
custM.setName("Mr. Stimpson J. Cat");
Customer custD = mapperDavid.find(1);
custD.setName("Ren Hoek");](https://image.slidesharecdn.com/l12concurrentprogramming-131112130603-phpapp02/75/L12-Concurrent-Programming-40-2048.jpg)