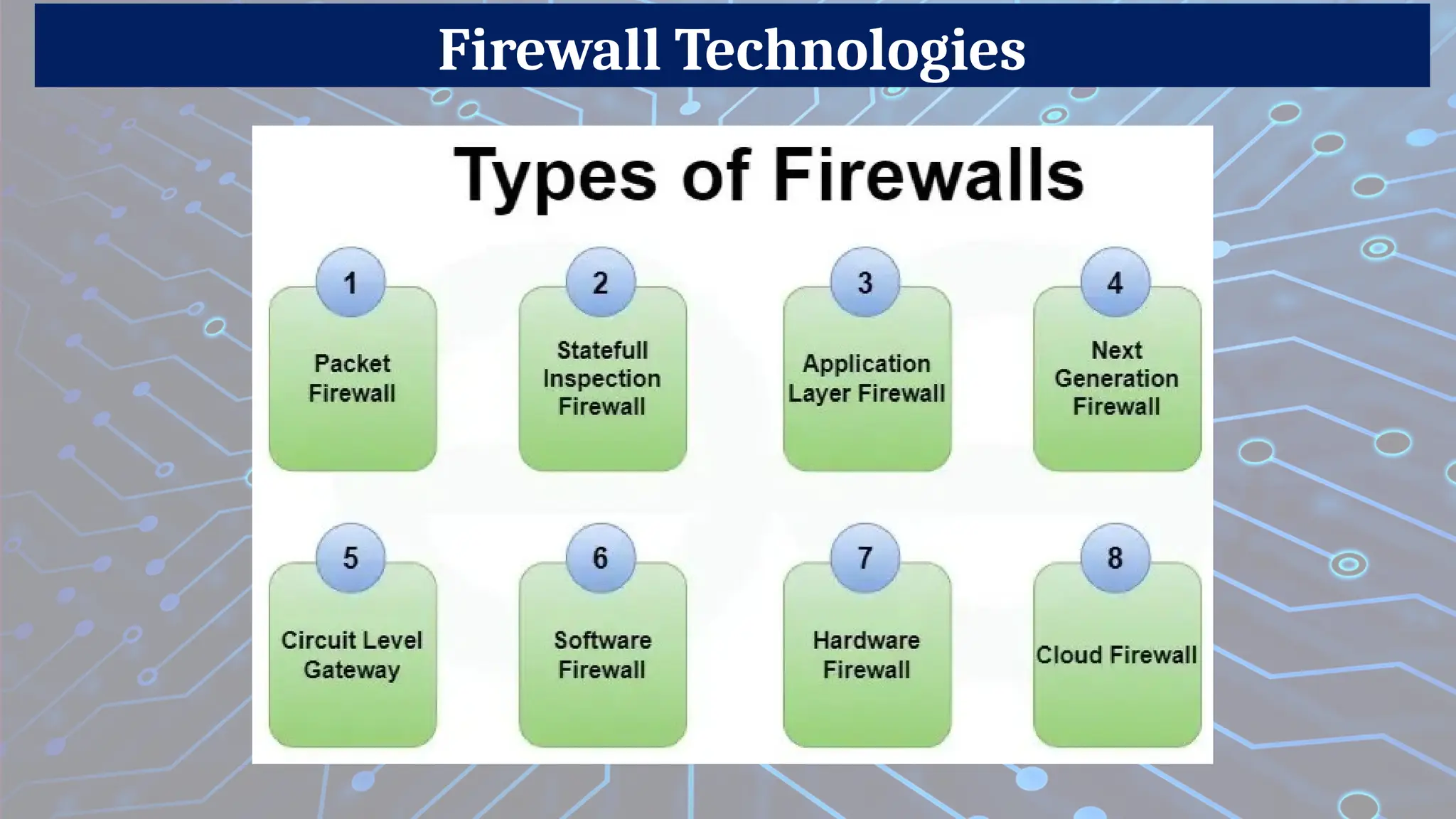
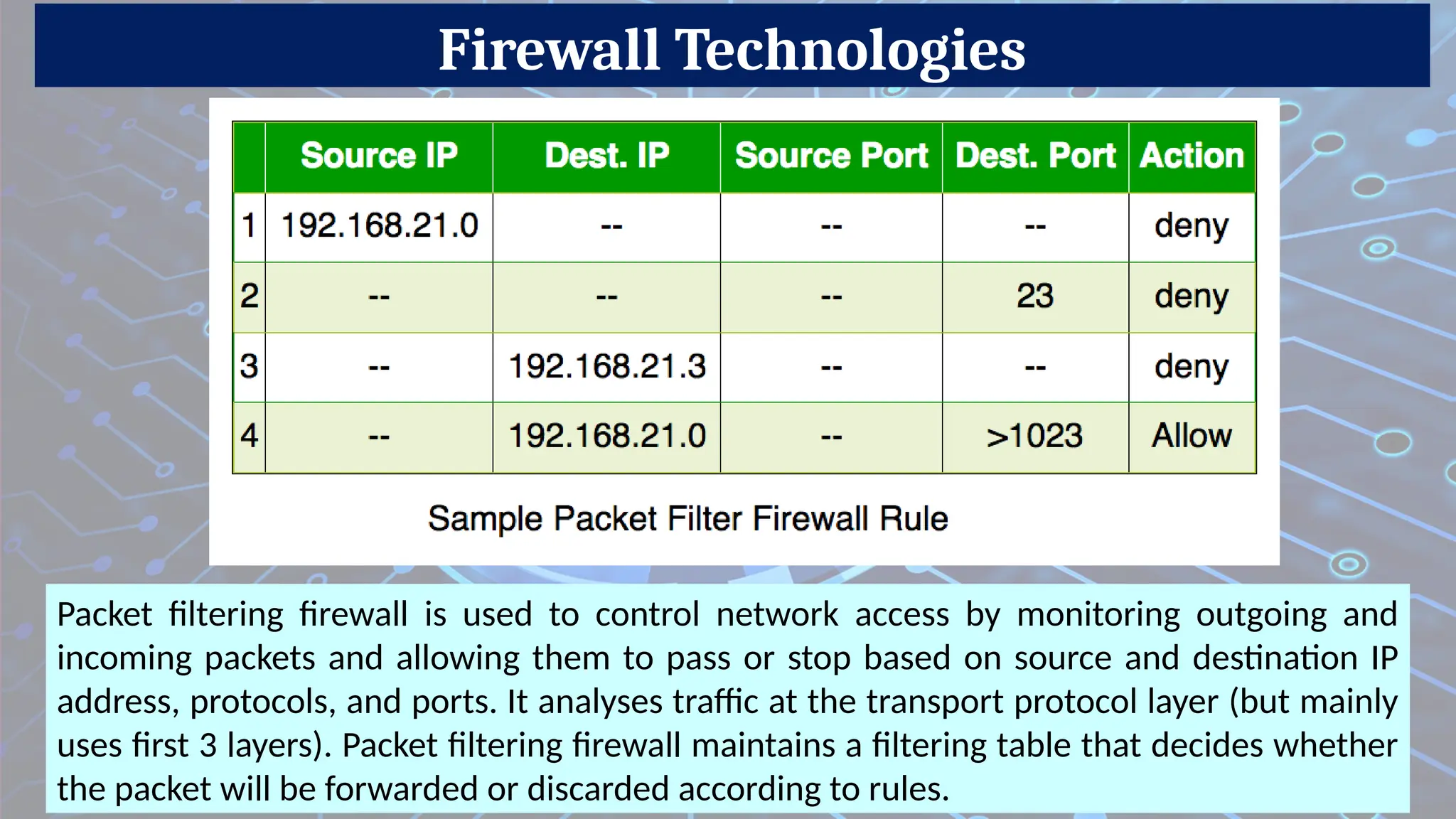
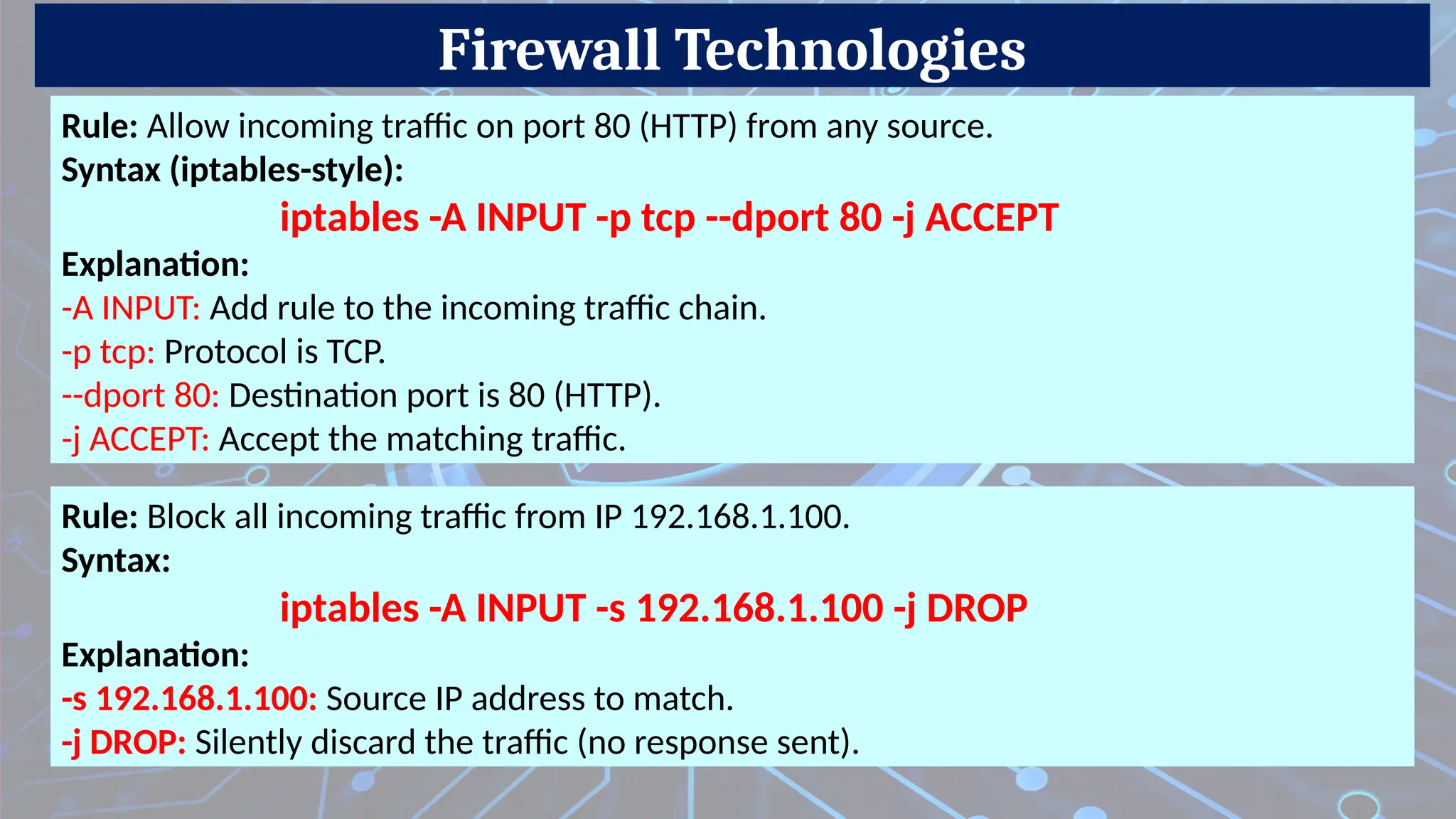
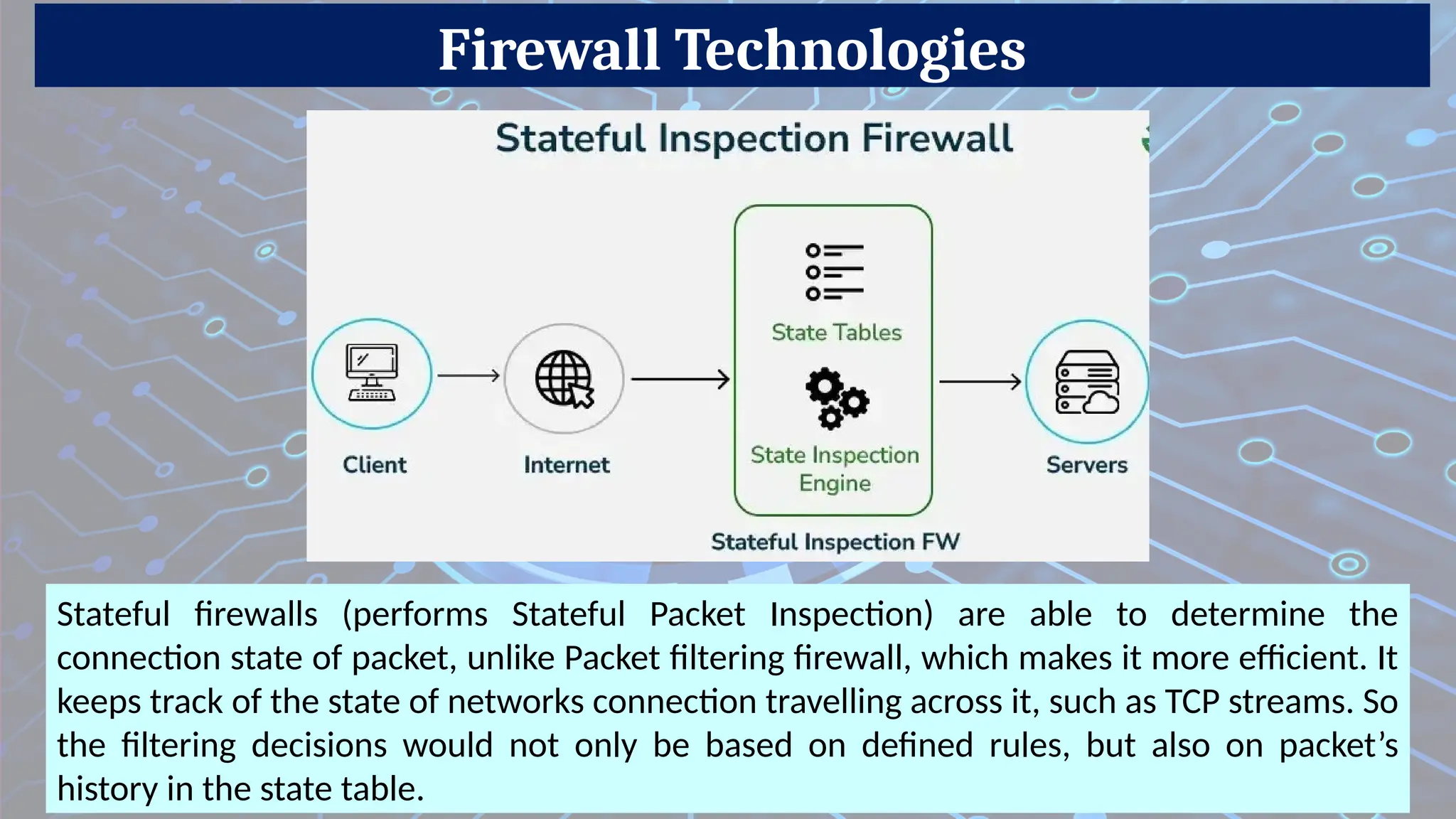
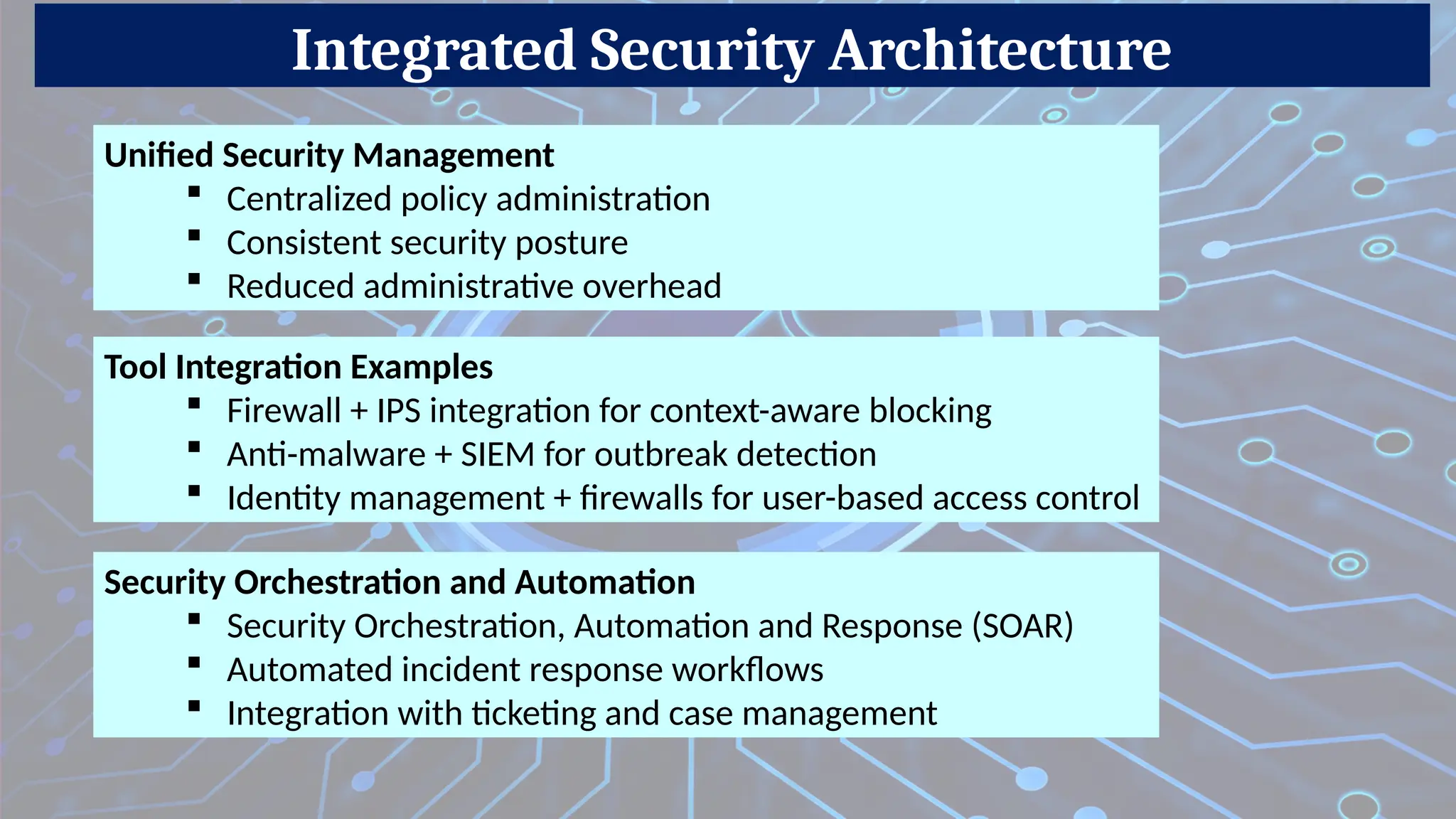
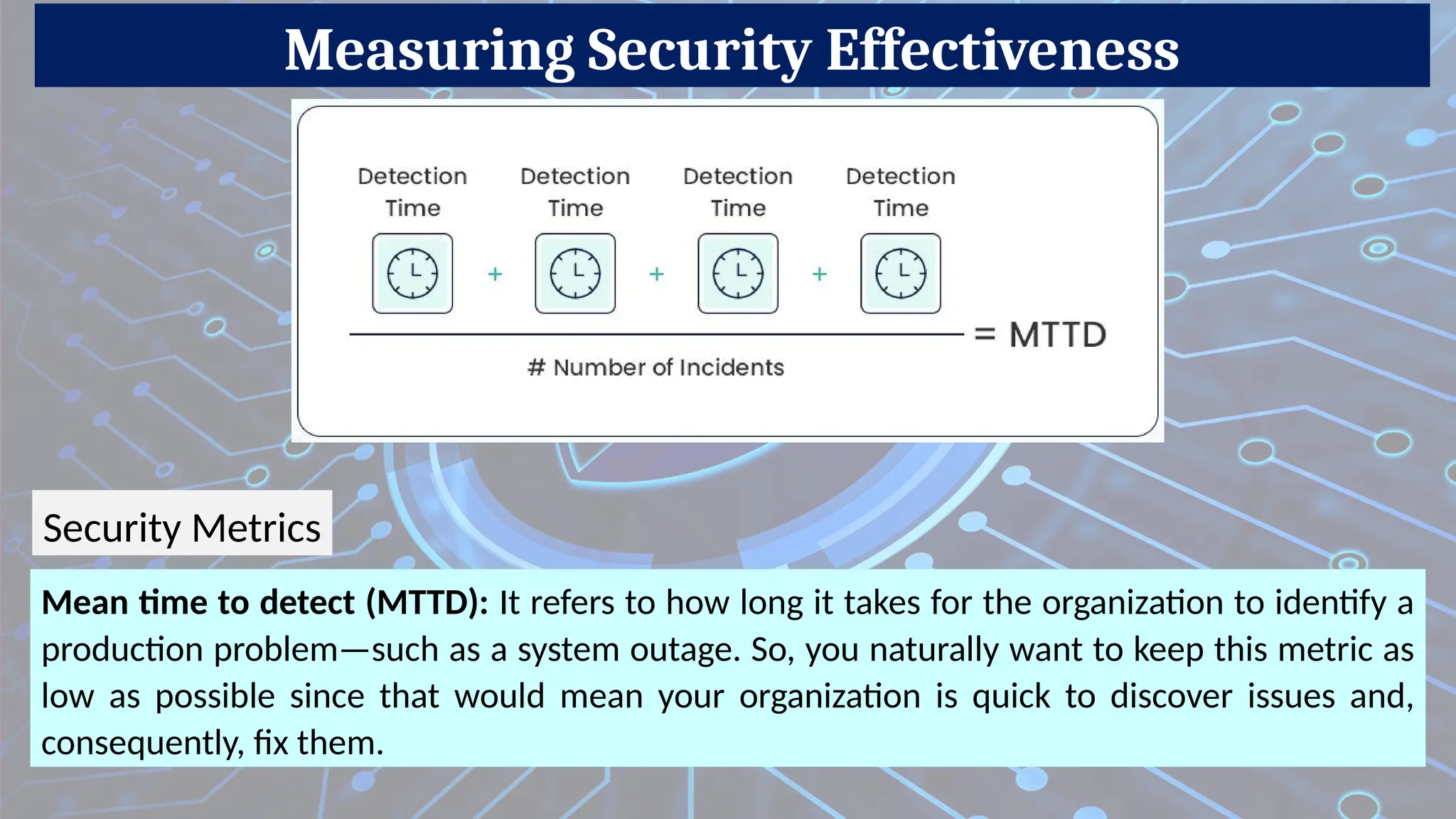
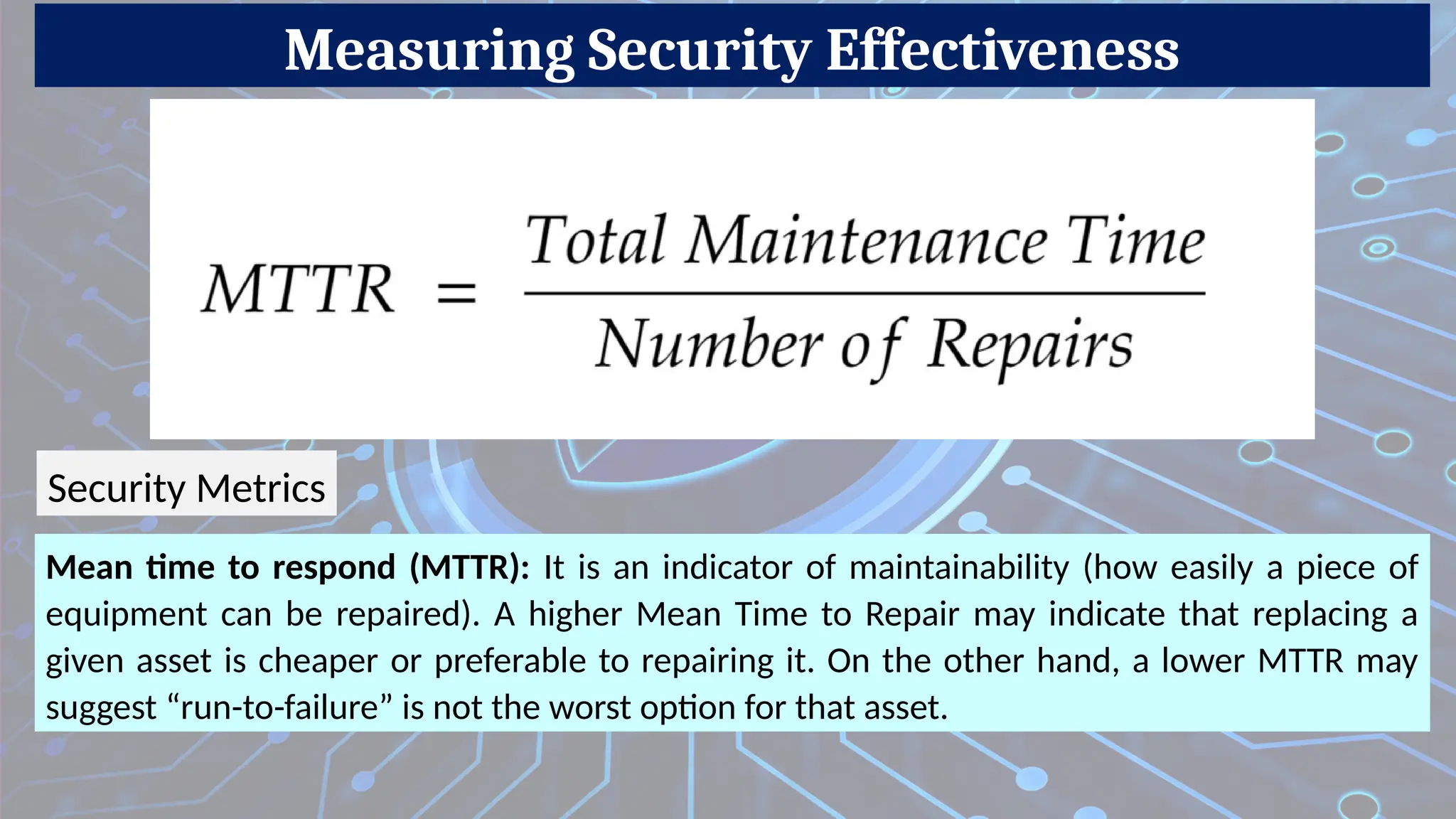
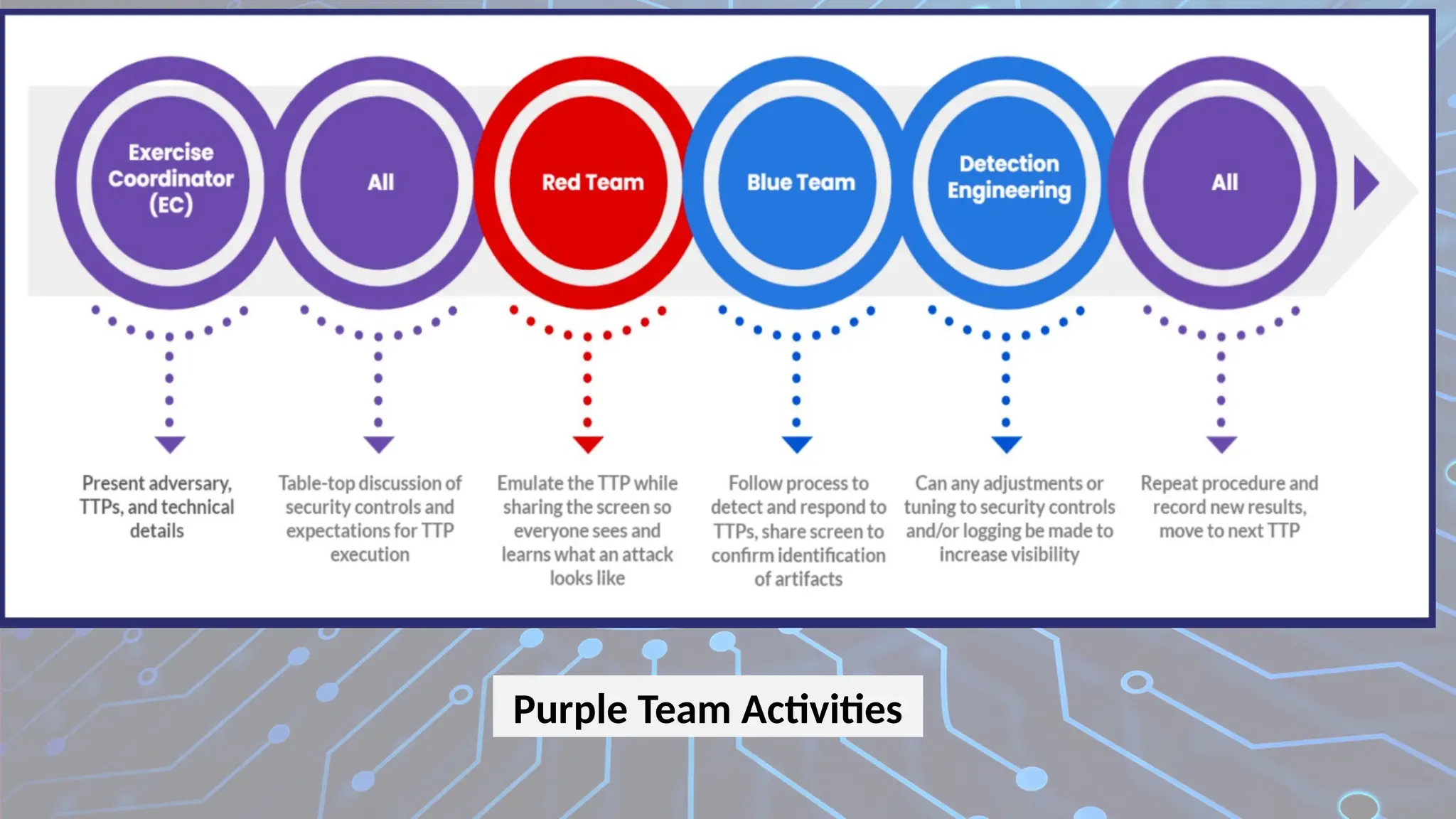
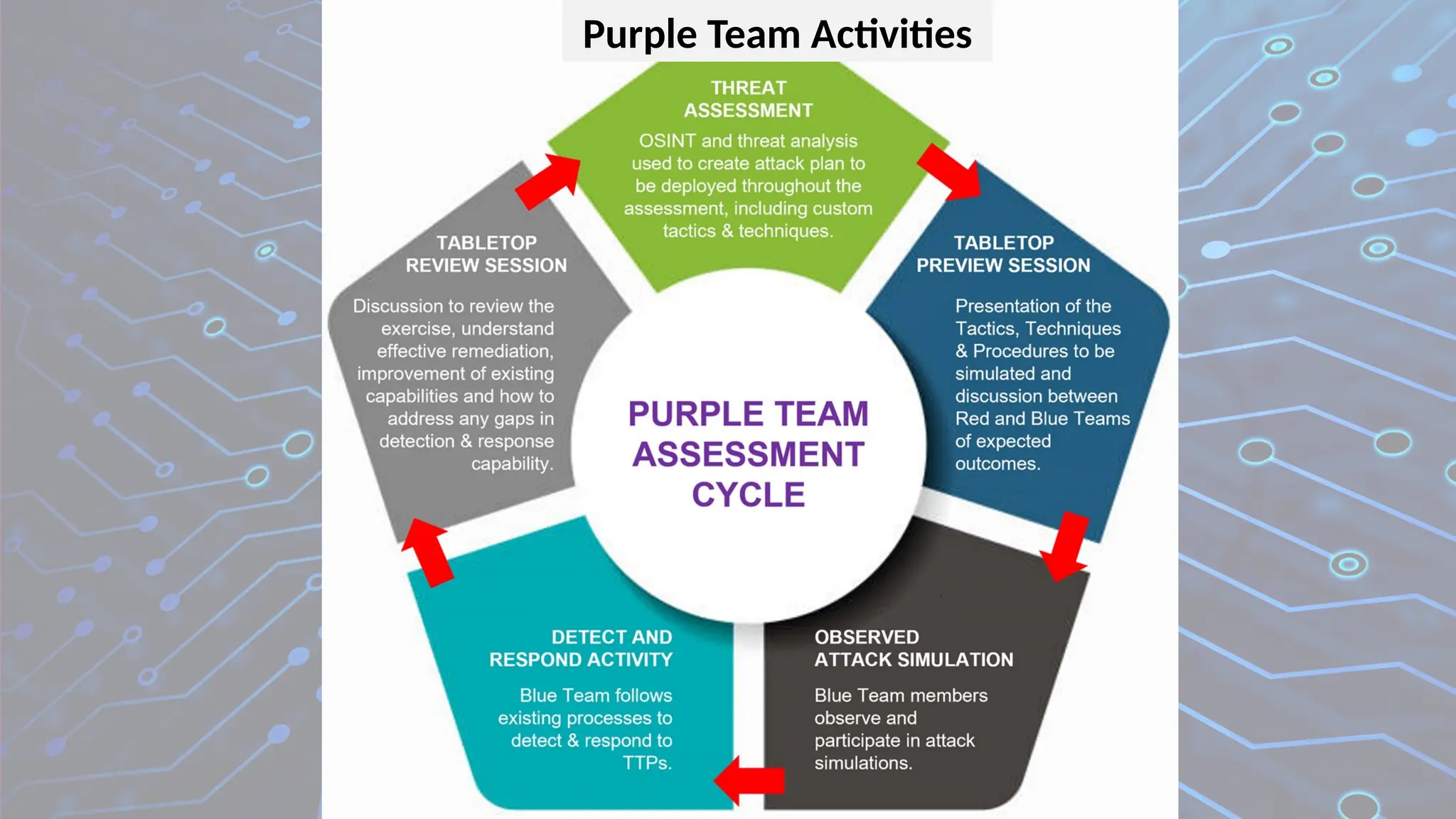
Firewalls are network security devices that monitor and control incoming and outgoing network traffic based on predefined security rules. There are several types of firewalls, each with different functionalities and use cases. Below are the main types of firewalls along with examples:
1. Packet-Filtering Firewall
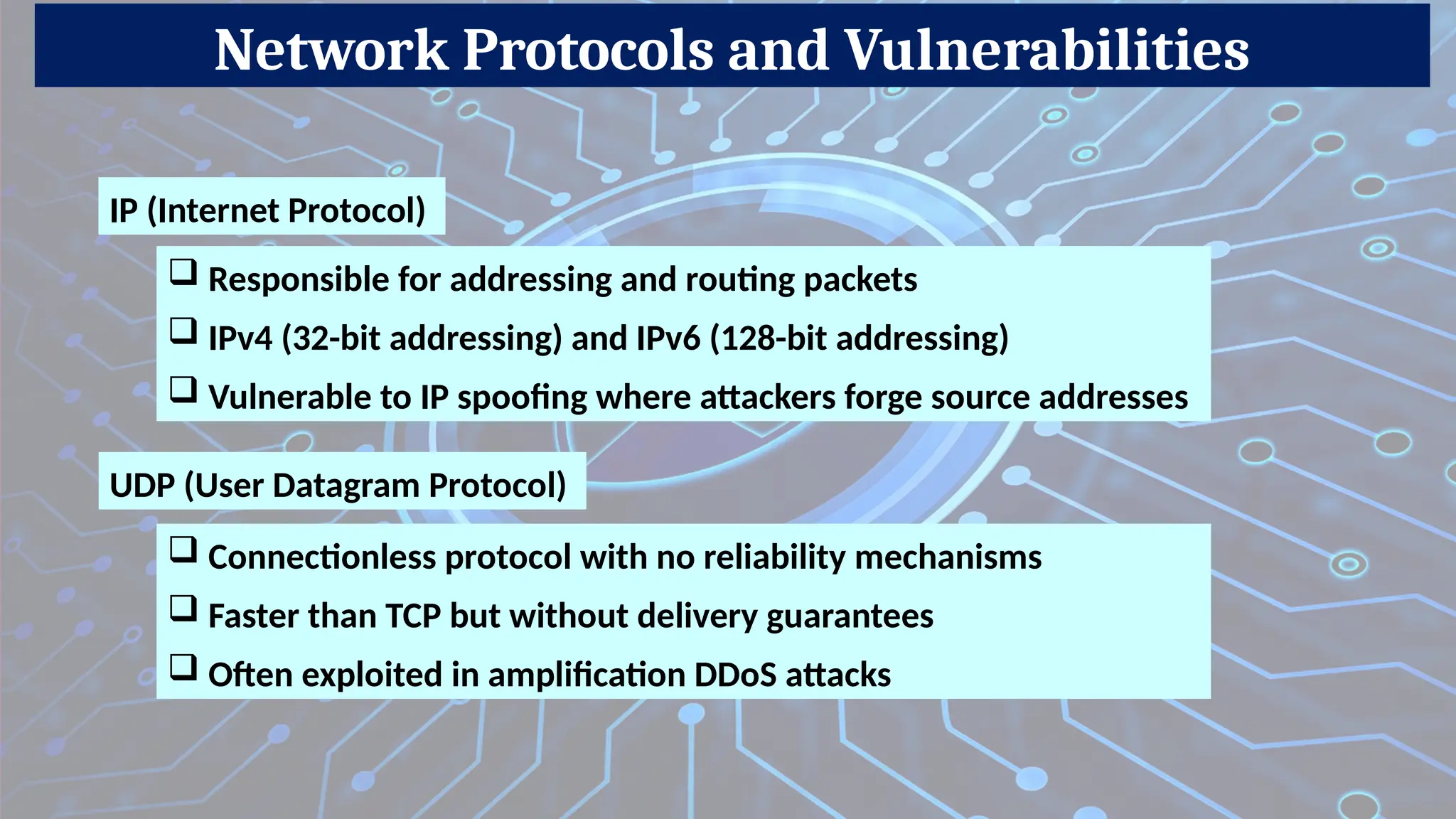
Description: Examines packets (data chunks) and allows or blocks them based on source/destination IP, port, and protocol.
Pros: Fast, low resource usage.
Cons: No deep inspection, vulnerable to IP spoofing.
Examples:
Cisco ASA (Adaptive Security Appliance)
iptables (Linux-based firewall)
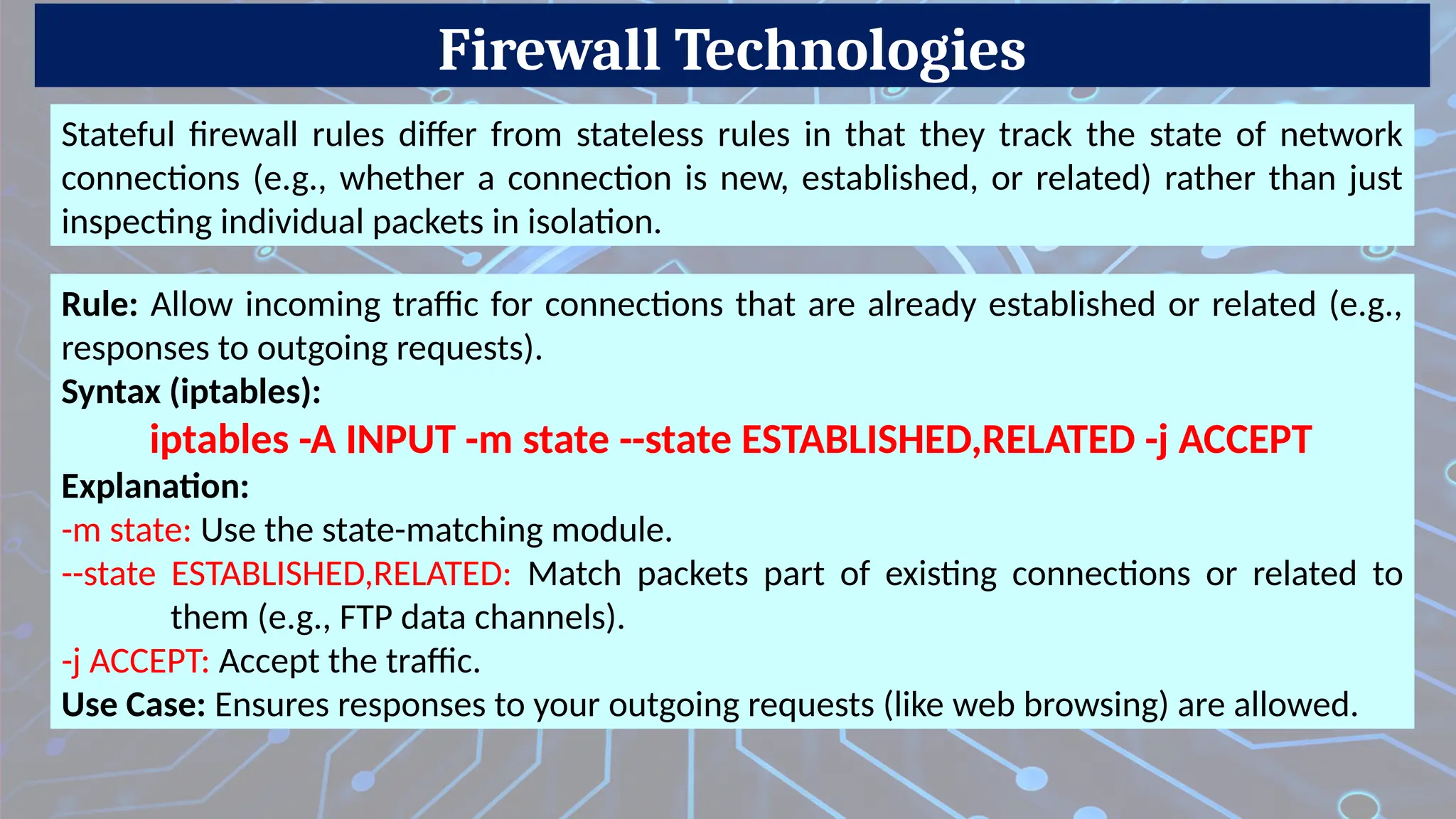
2. Stateful Inspection Firewall (Dynamic Packet Filtering)
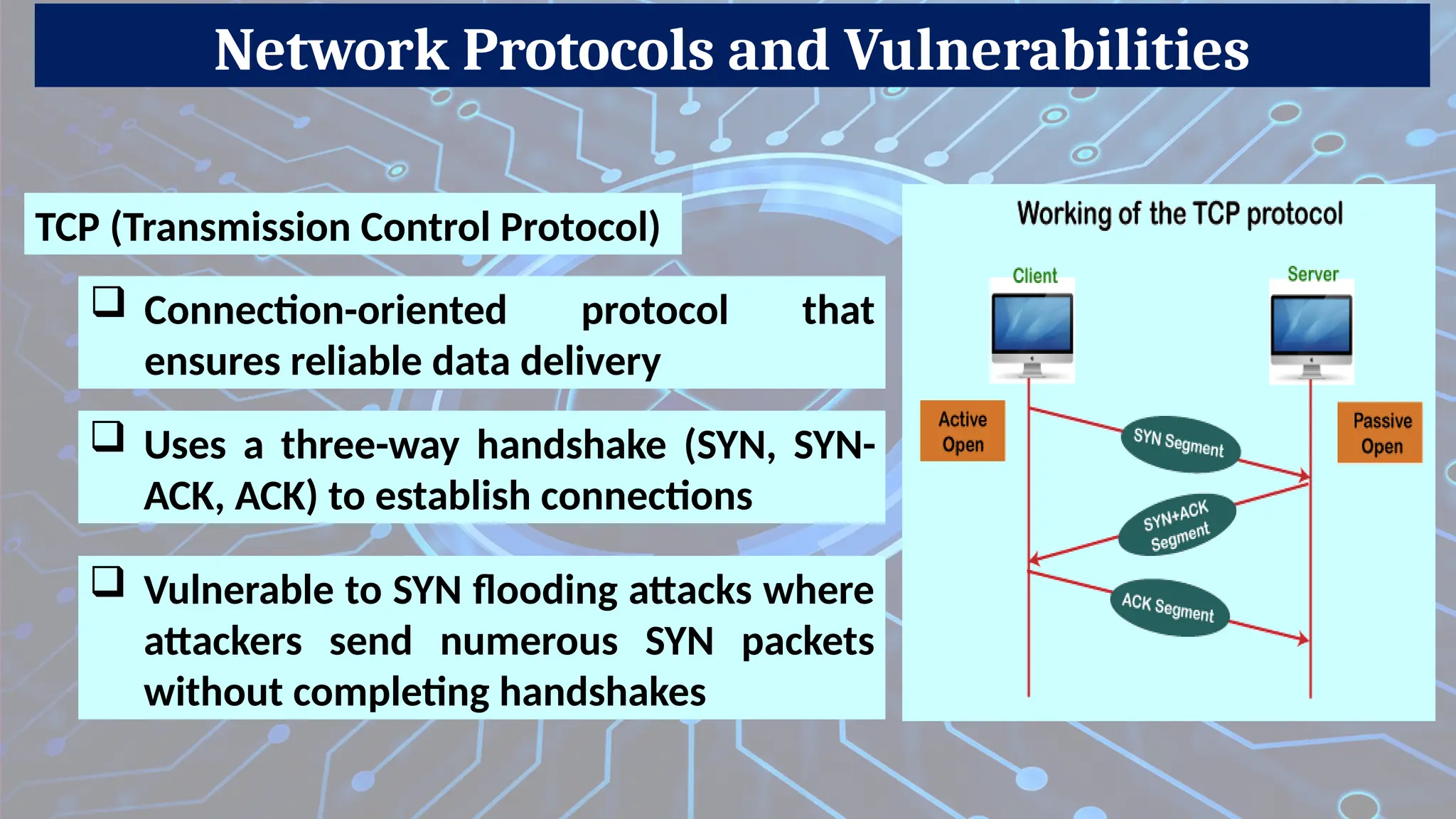
Description: Tracks active connections and makes decisions based on the state of the connection (e.g., TCP handshake).
Pros: More secure than basic packet filtering.
Cons: Higher resource usage.
Examples:
Check Point Firewall
Juniper SRX Series
3. Proxy Firewall (Application-Level Gateway)
Description: Acts as an intermediary between users and the internet, inspecting traffic at the application layer (e.g., HTTP, FTP).
Pros: Deep inspection, hides internal networks.
Cons: Slower, may not support all applications.
Examples:
Squid Proxy (Open-source)
Microsoft Forefront Threat Management Gateway (TMG) (Discontinued but still in use)
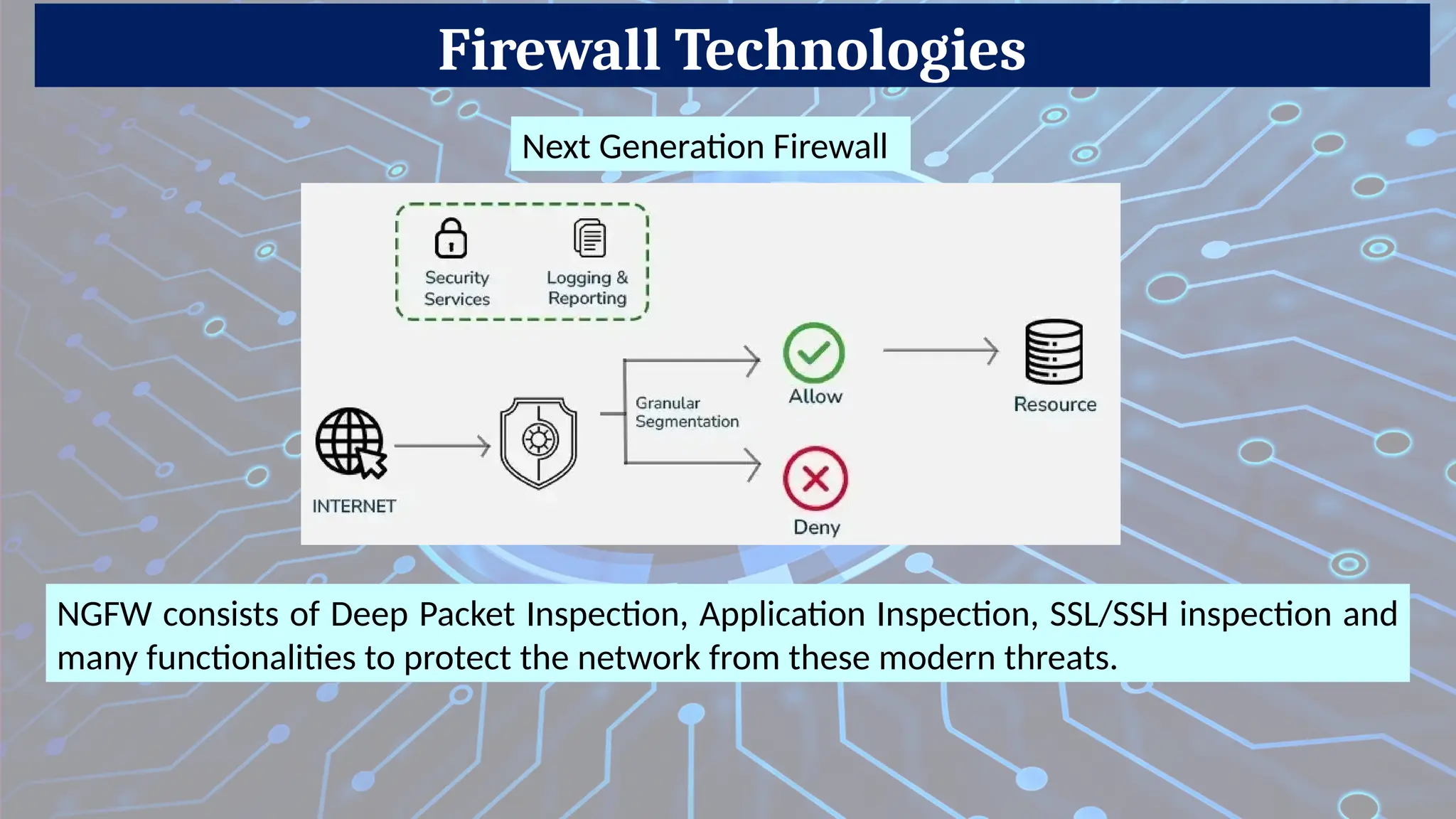
4. Next-Generation Firewall (NGFW)
Description: Combines traditional firewall features with advanced capabilities like deep packet inspection (DPI), intrusion prevention (IPS), and application awareness.
Pros: Highly secure, granular control.
Cons: Expensive, complex to configure.
Examples:
Palo Alto Networks Firewalls
Fortinet FortiGate
5. Unified Threat Management (UTM) Firewall
Description: All-in-one security solution combining firewall, antivirus, anti-spam, VPN, and intrusion detection/prevention.
Pros: Simplified management, cost-effective for small businesses.
Cons: Performance overhead.
Examples:
Sophos UTM
WatchGuard Firebox
6. Cloud Firewall (Firewall-as-a-Service - FaaS)
Description: Hosted in the cloud to protect cloud-based or hybrid network infrastructures.
Pros: Scalable, no hardware needed.
Cons: Dependent on cloud provider.
Examples:
AWS Network Firewall
Zscaler Cloud Firewall
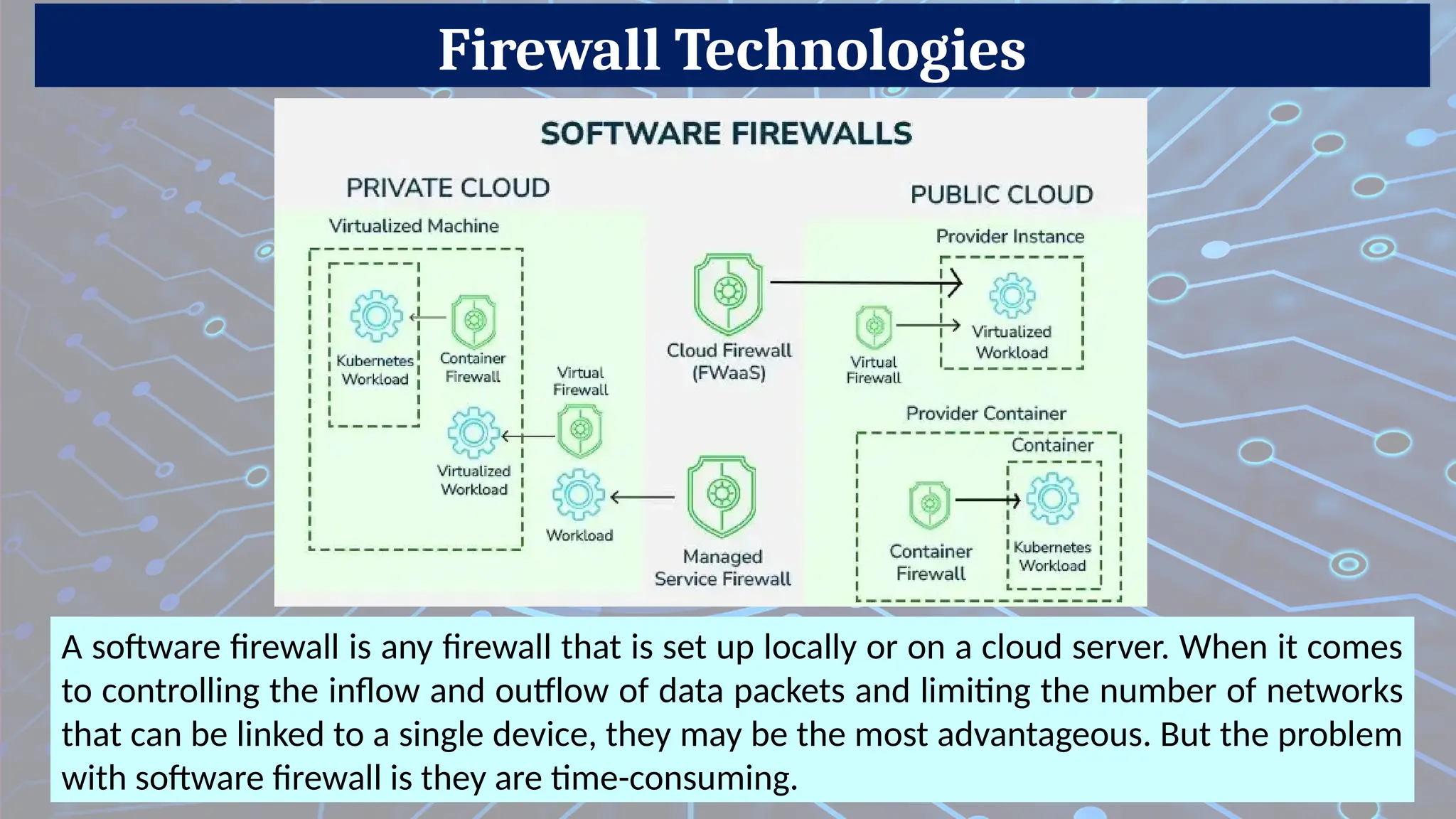
7. Software Firewall
Description: Installed on individual devices (e.g., PCs, servers) to control traffic.
Pros: Granular per-device control.
Cons: Requires installation on each device.
Examples:
Windows Defender Firewall
GlassWire (User-friendly firewall for PCs)
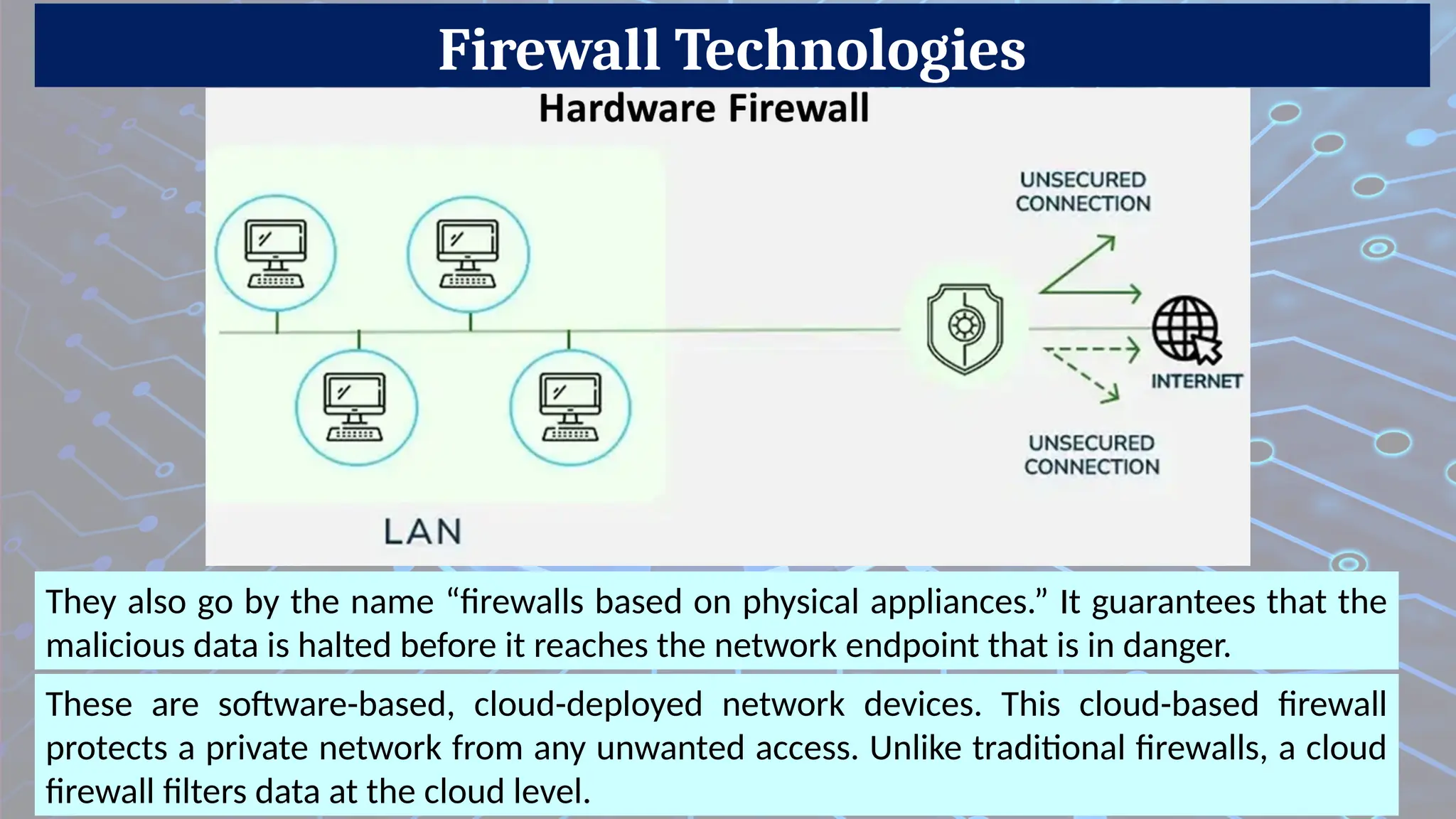
8. Hardware Firewall
Description: Physical device placed between a network and gateway to filter traffic.
Pros: High performance, dedicated security.
Cons: Expensive, requires maintenance.
Examples:
Cisco Firepower
Barracuda CloudGen Firewall
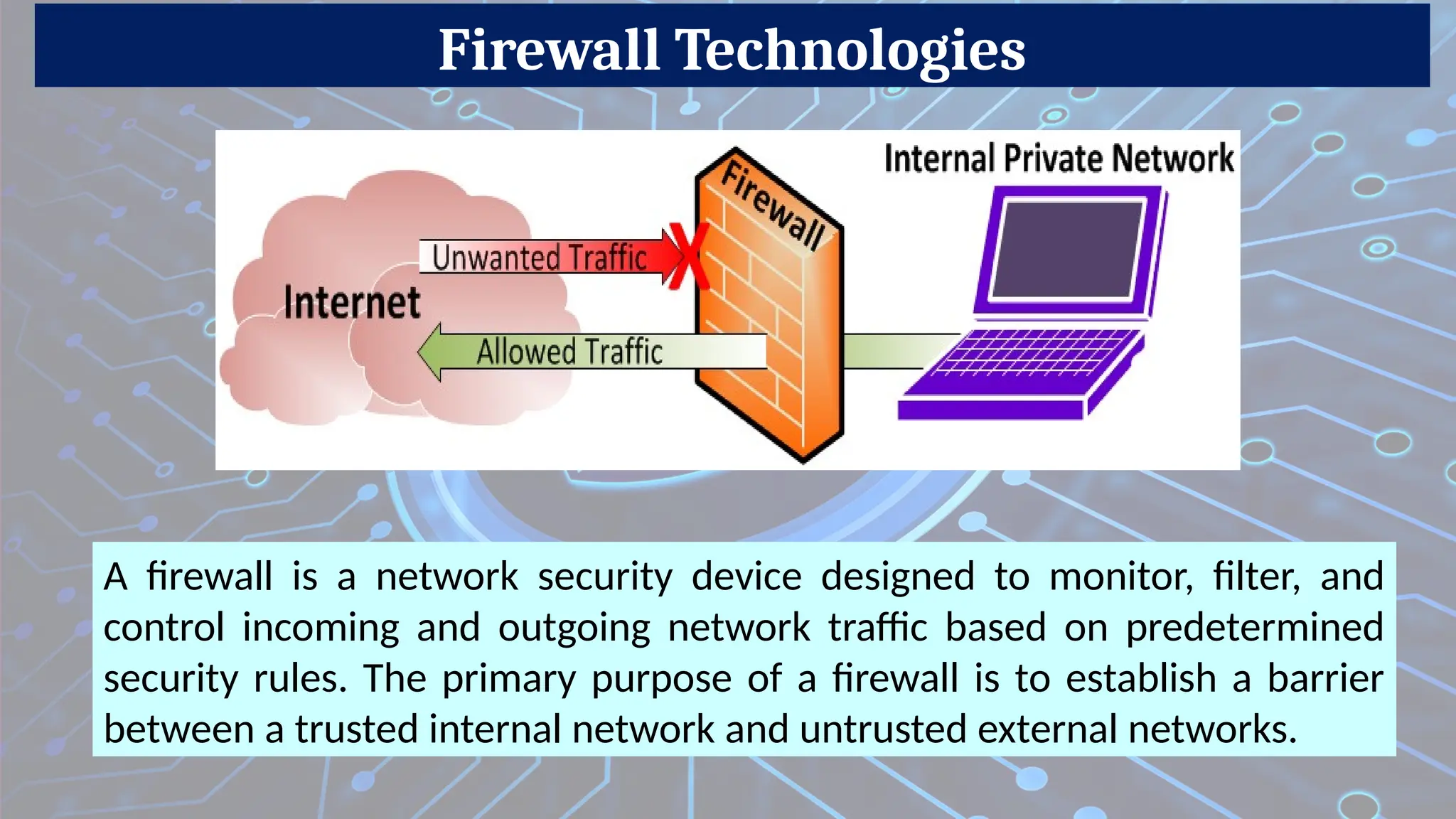
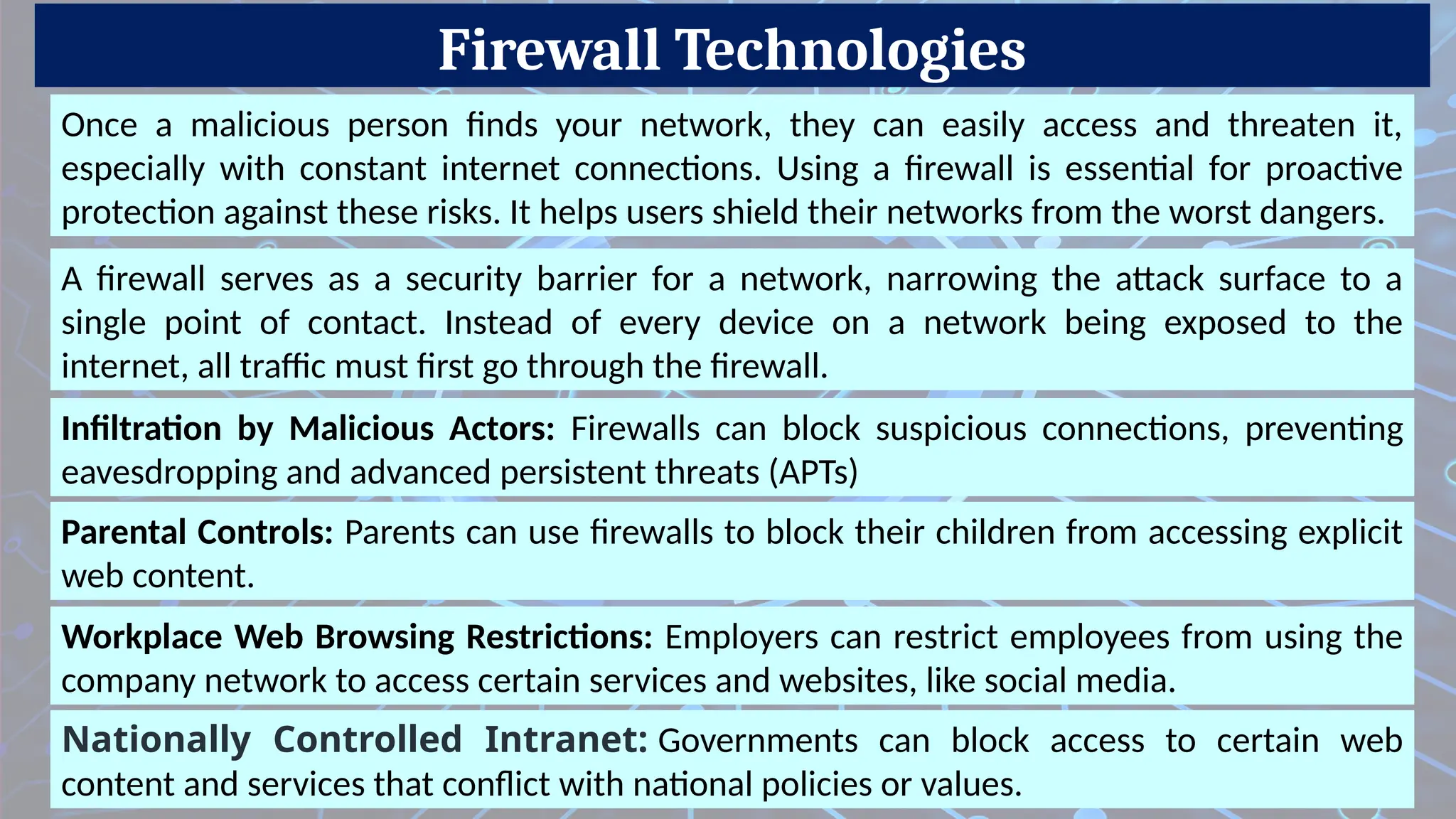
How to Prevent Network Traffic?
A network firewall applies a certain set of rules on the incoming and outgoing network traffic to examine whether they align with those rules or not.