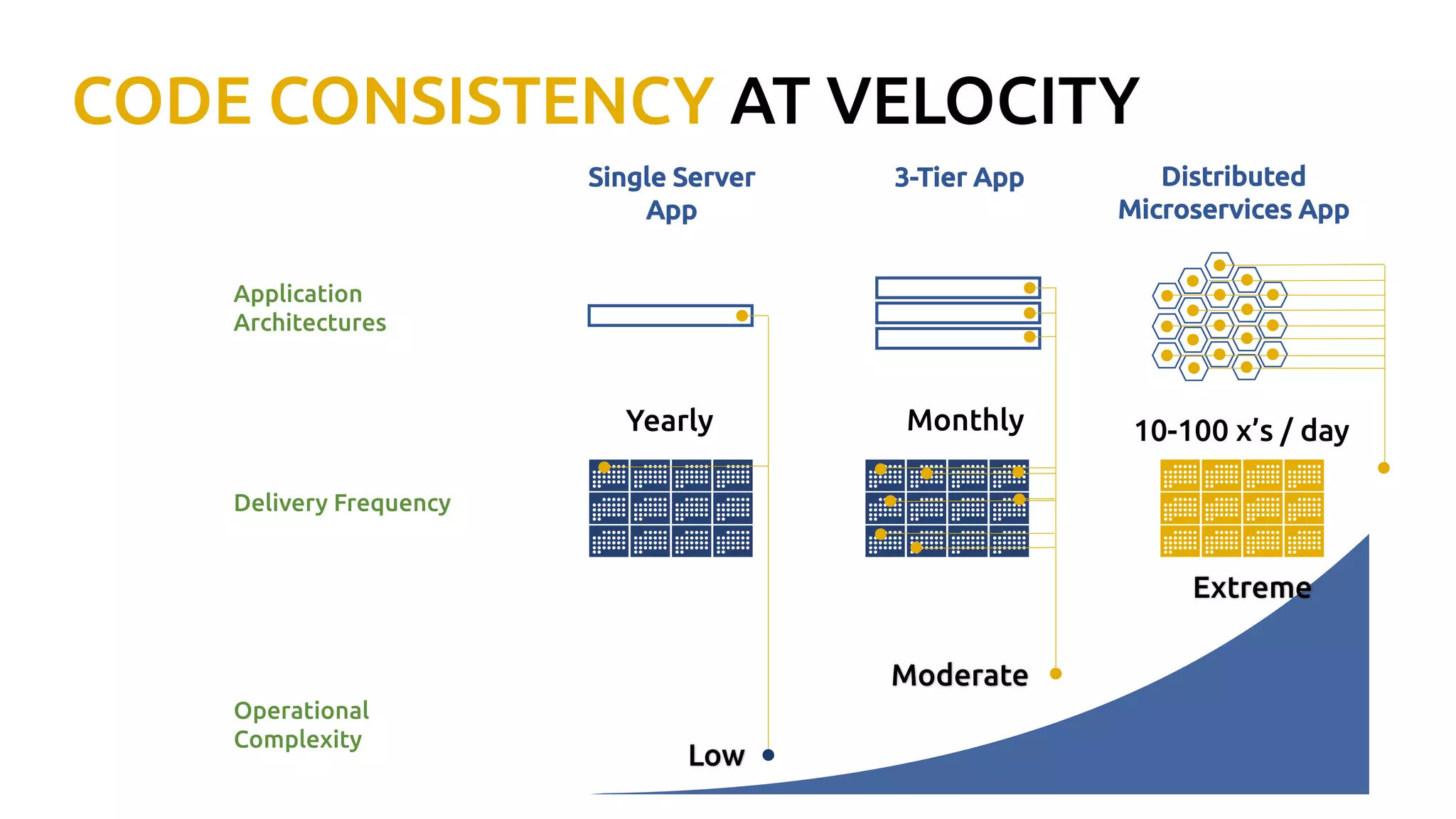
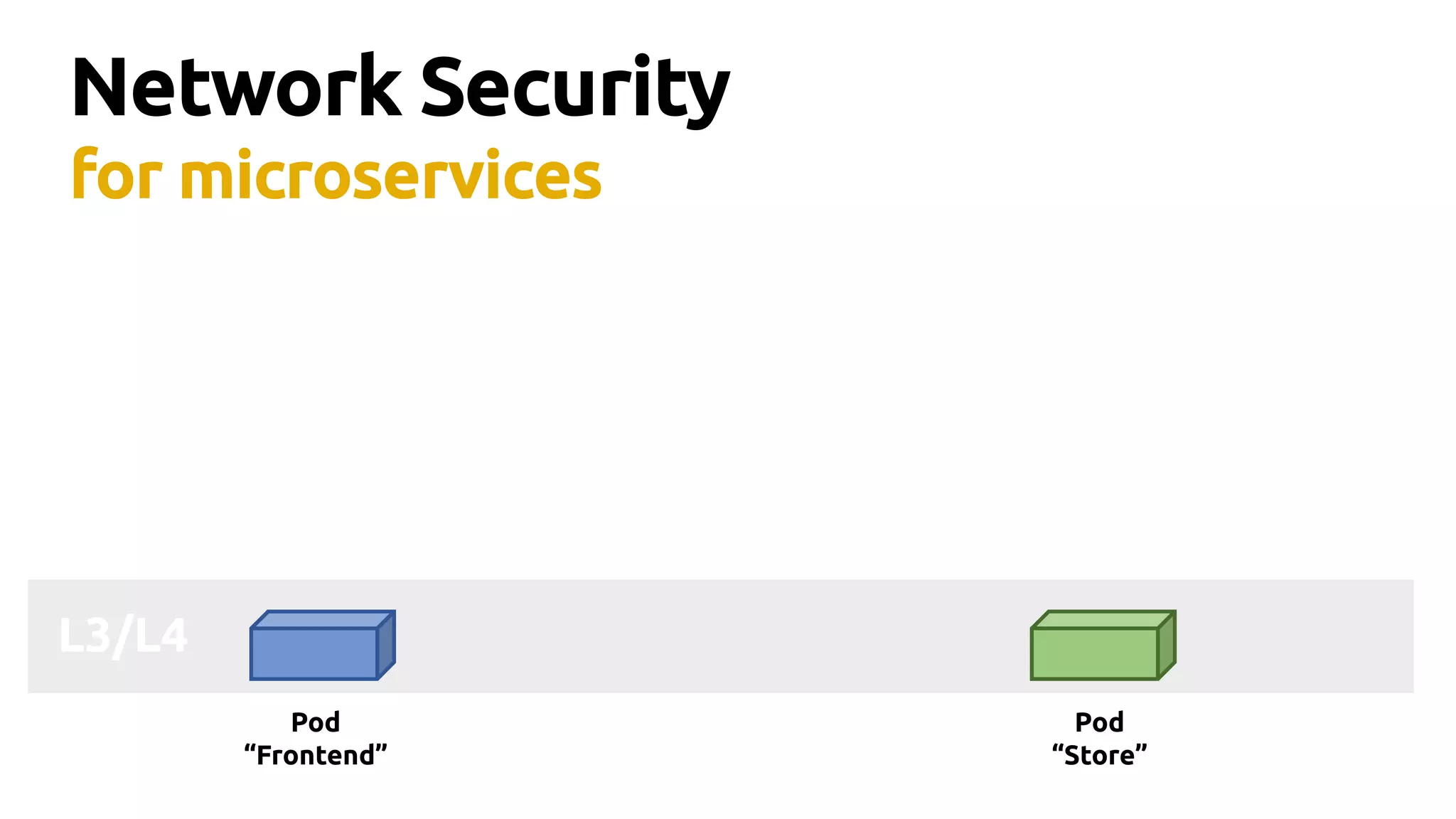
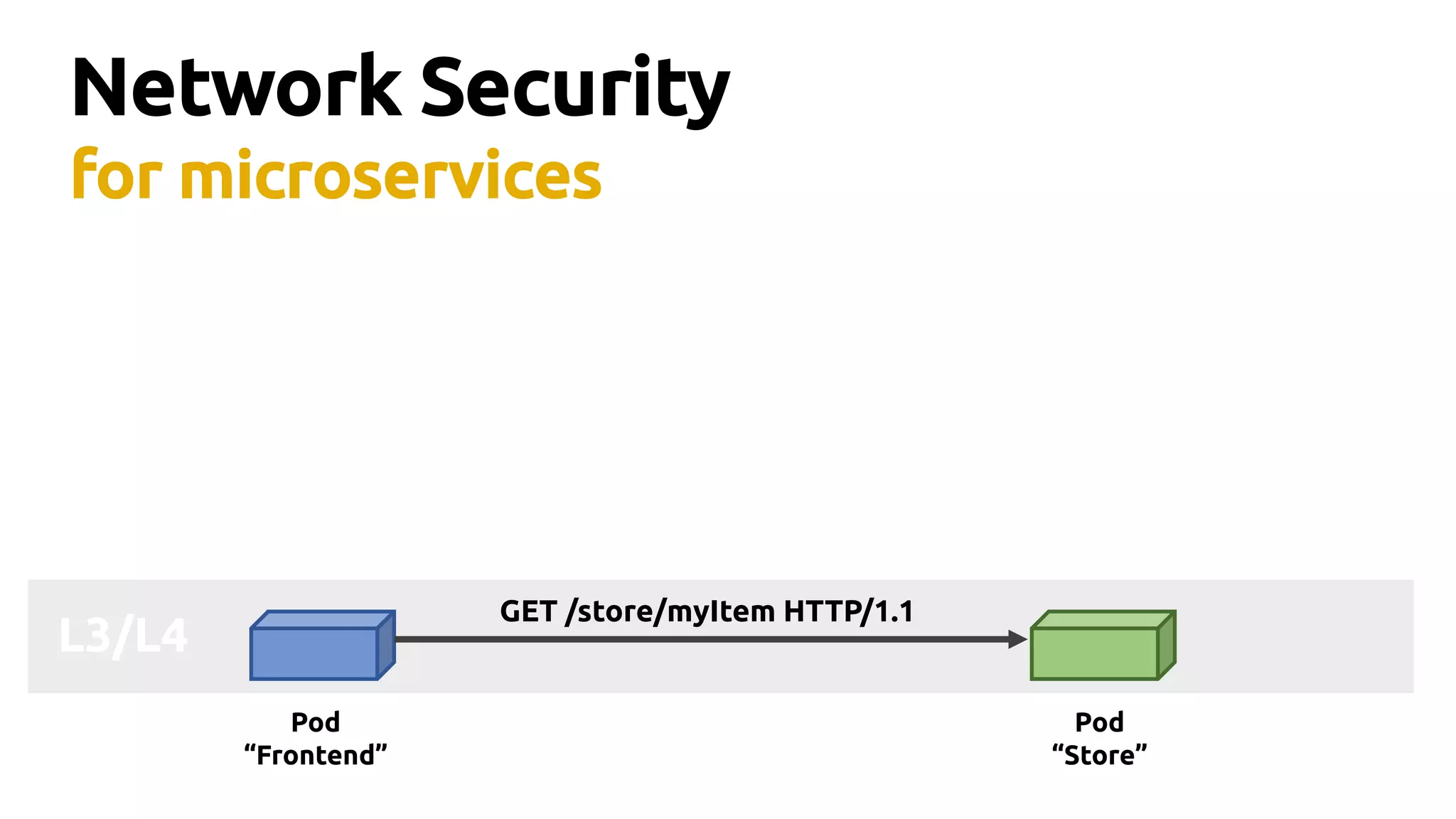
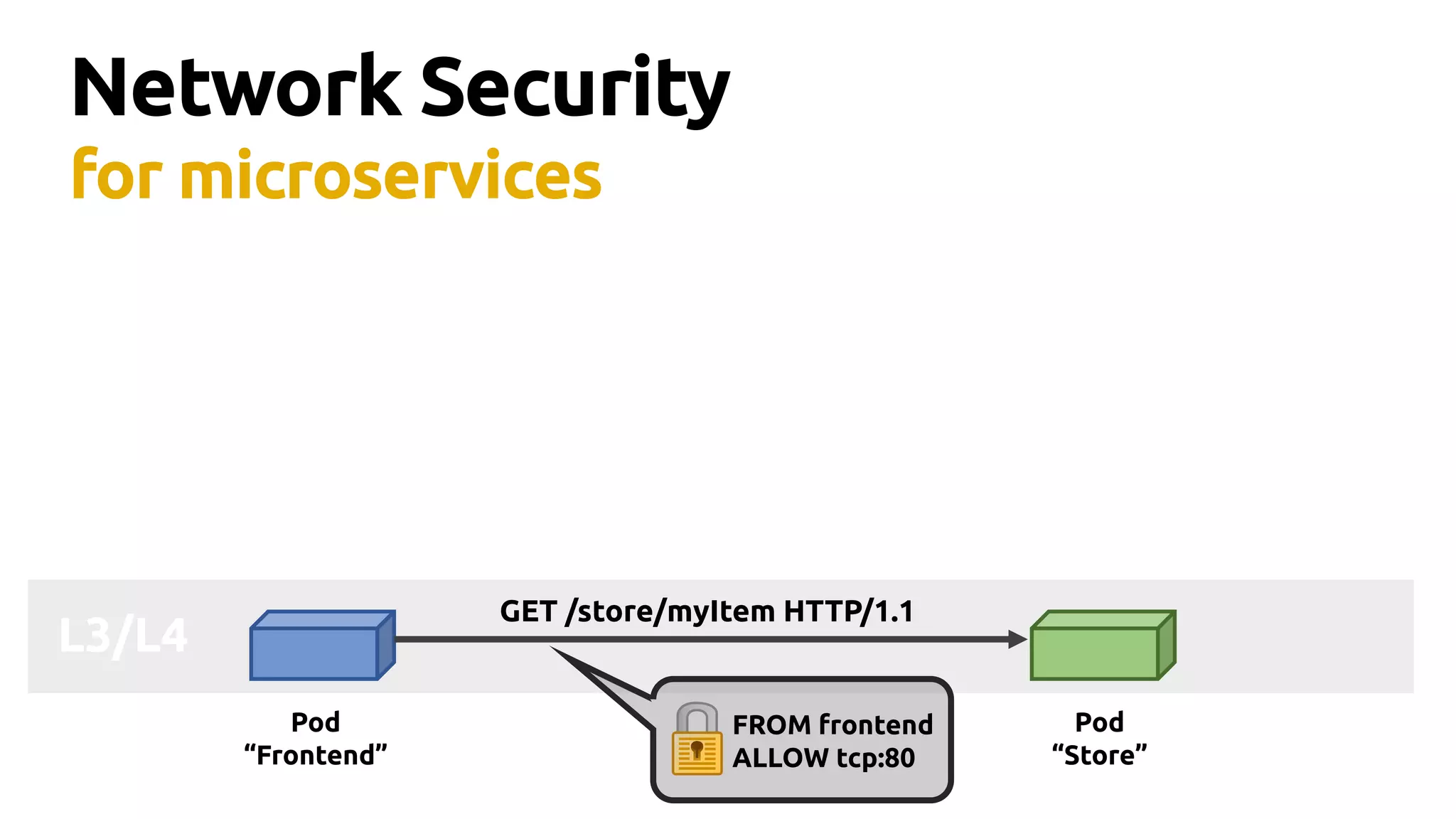
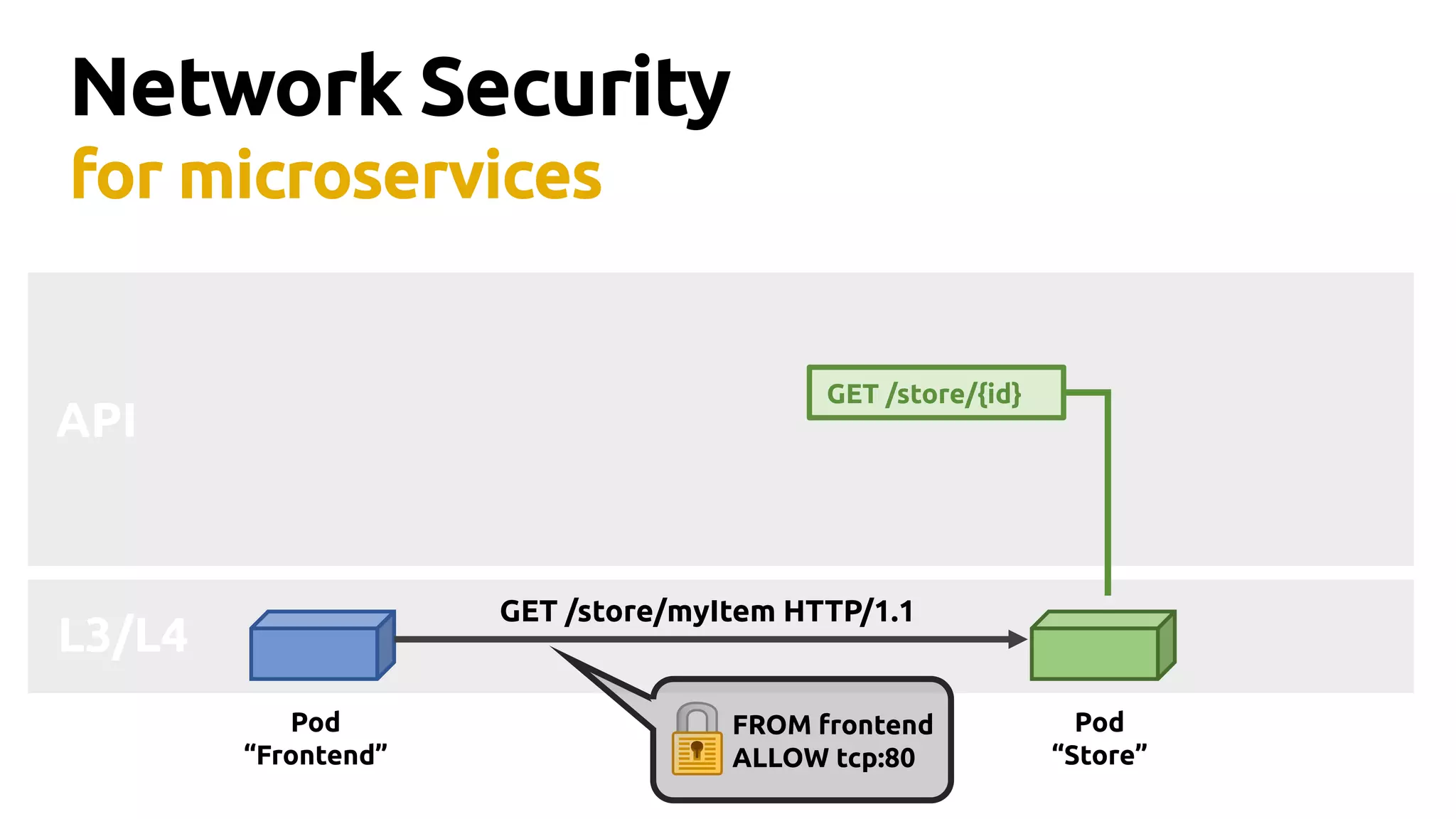
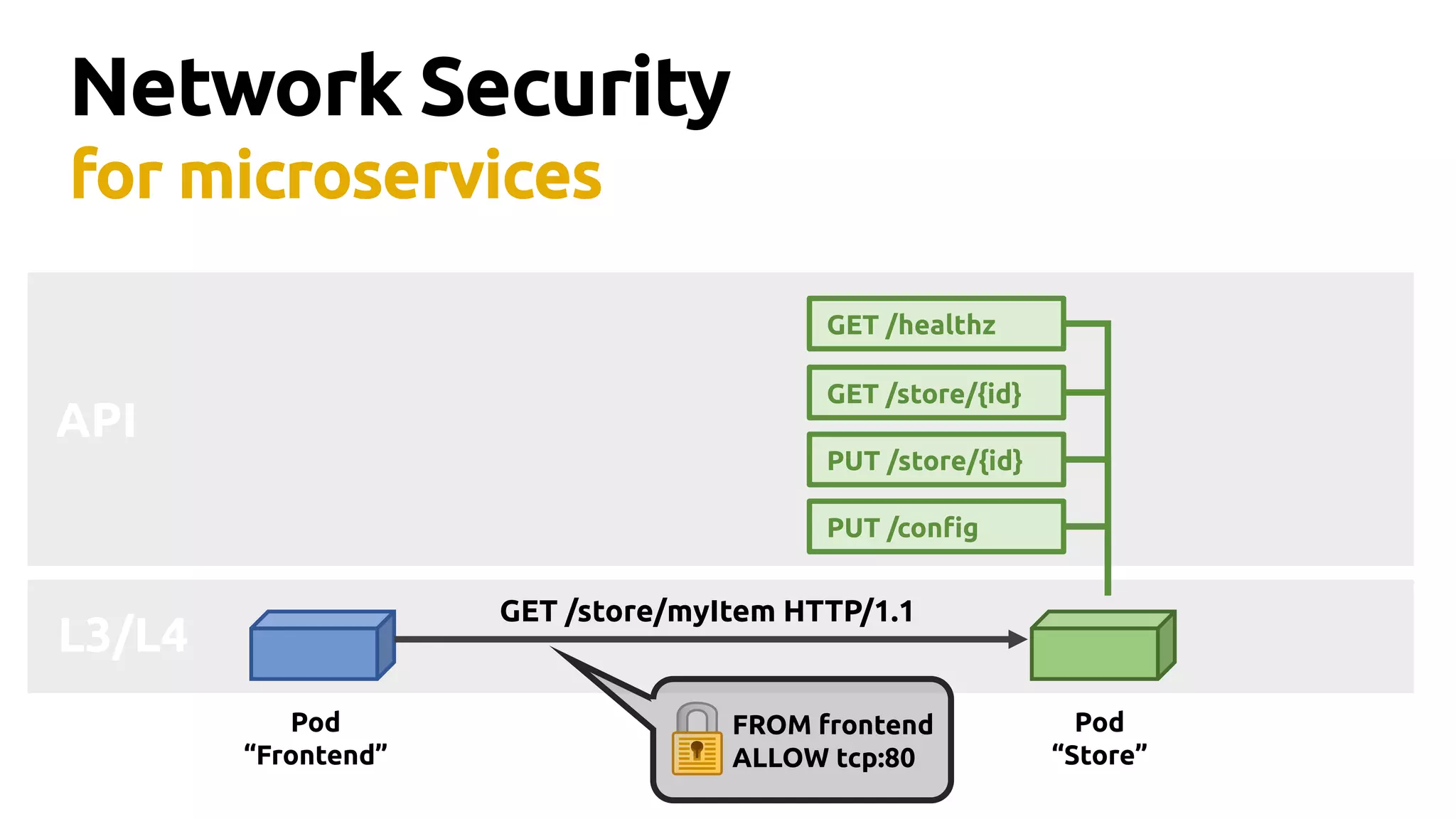
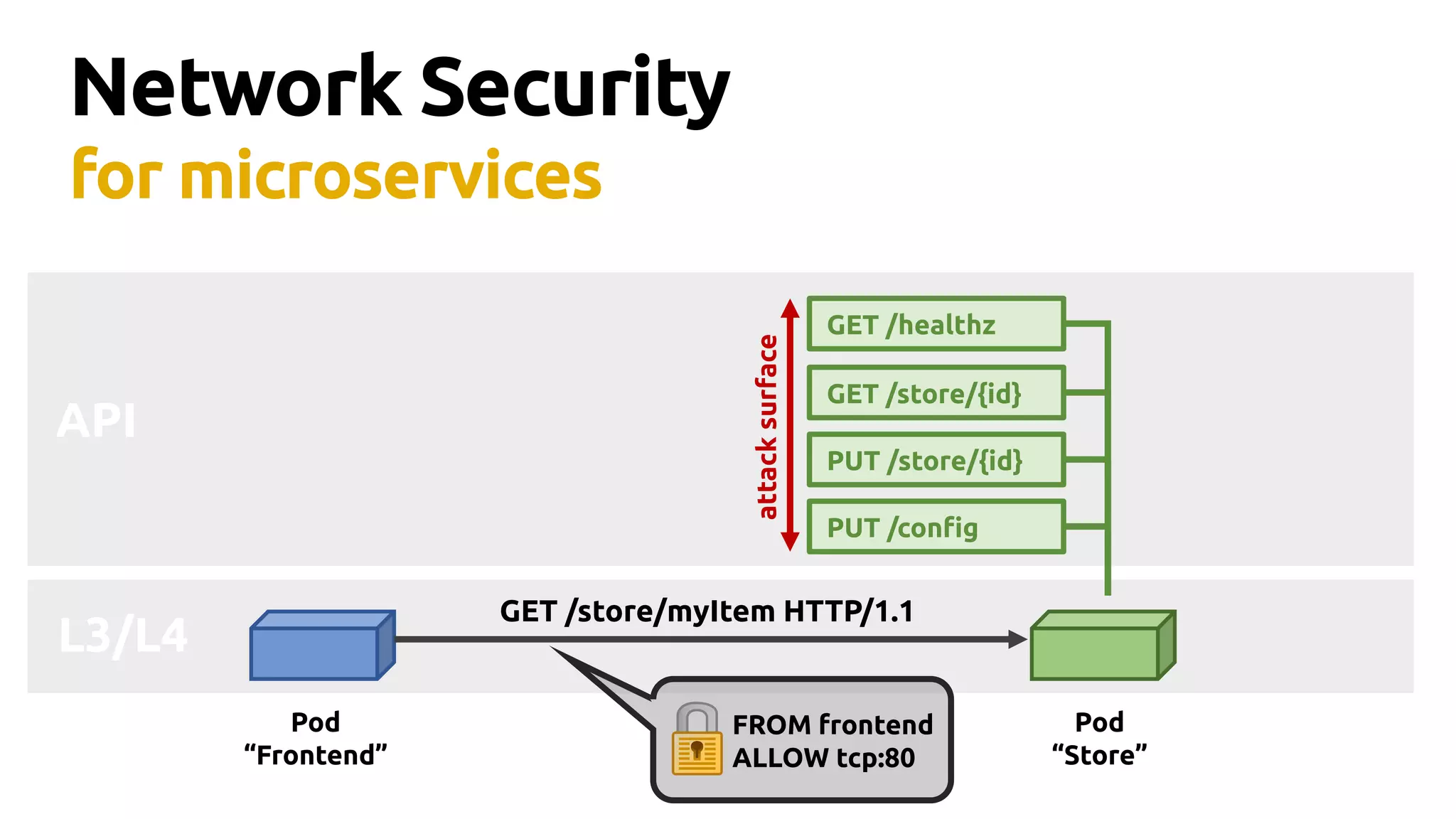
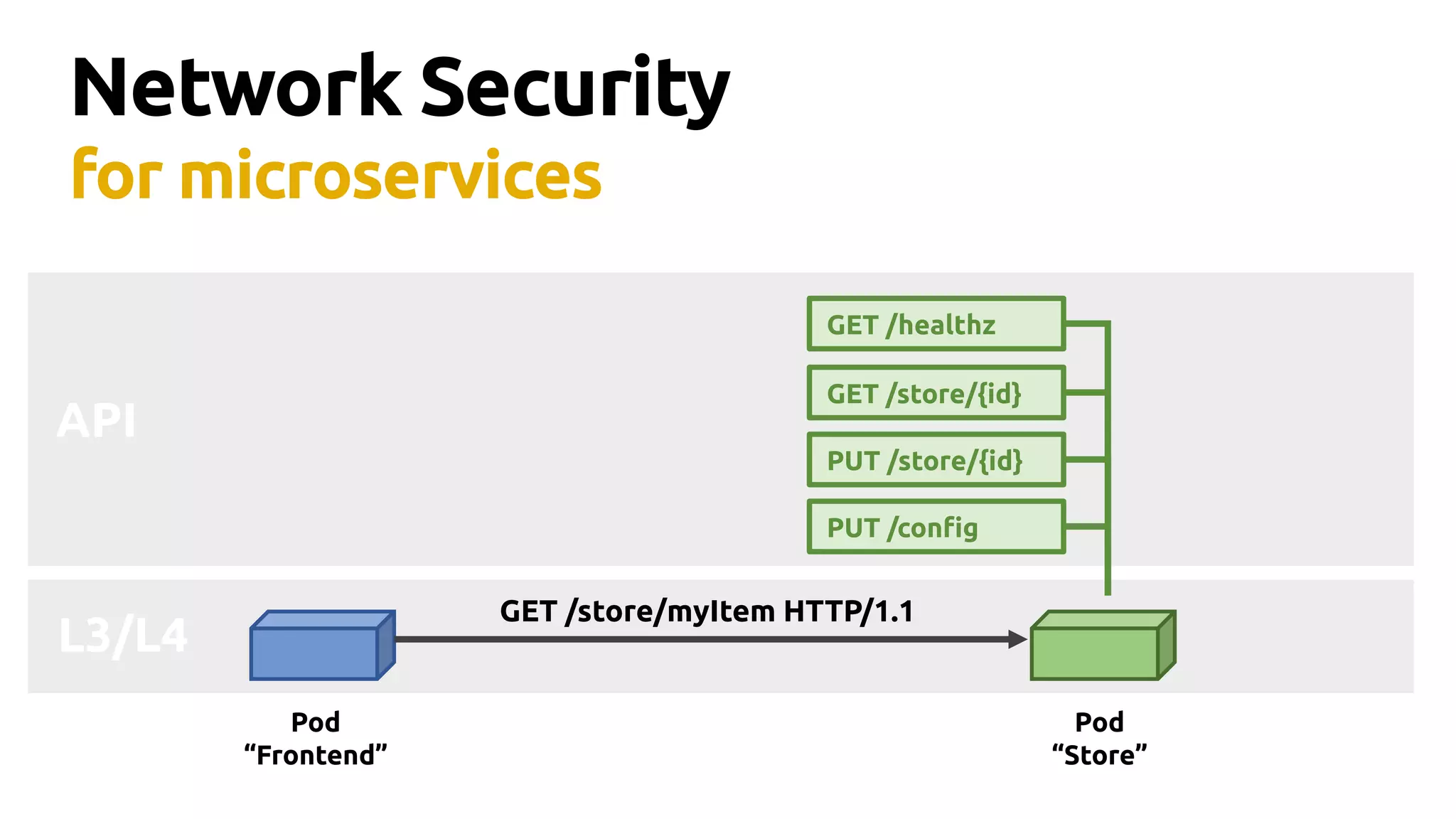
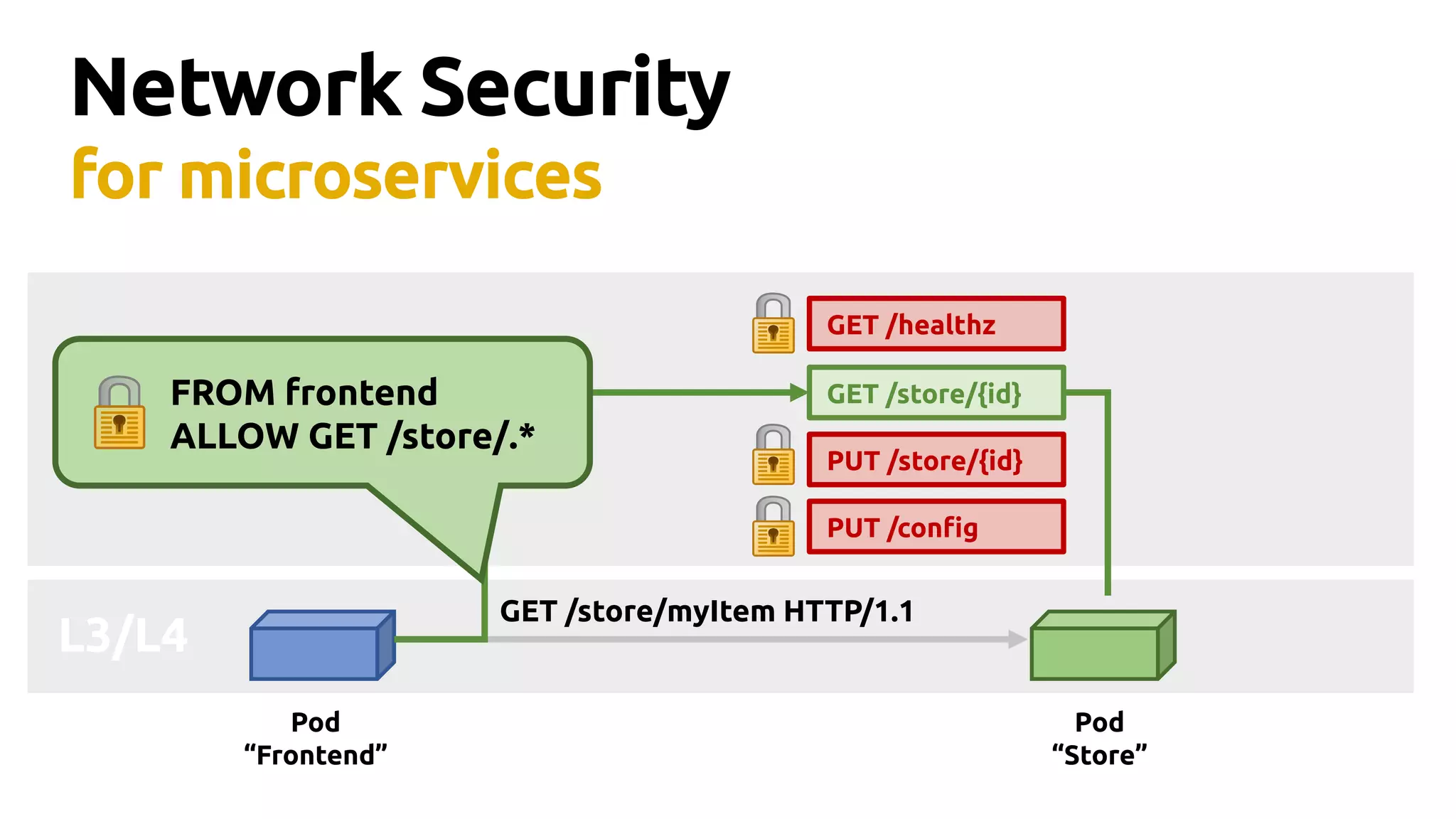
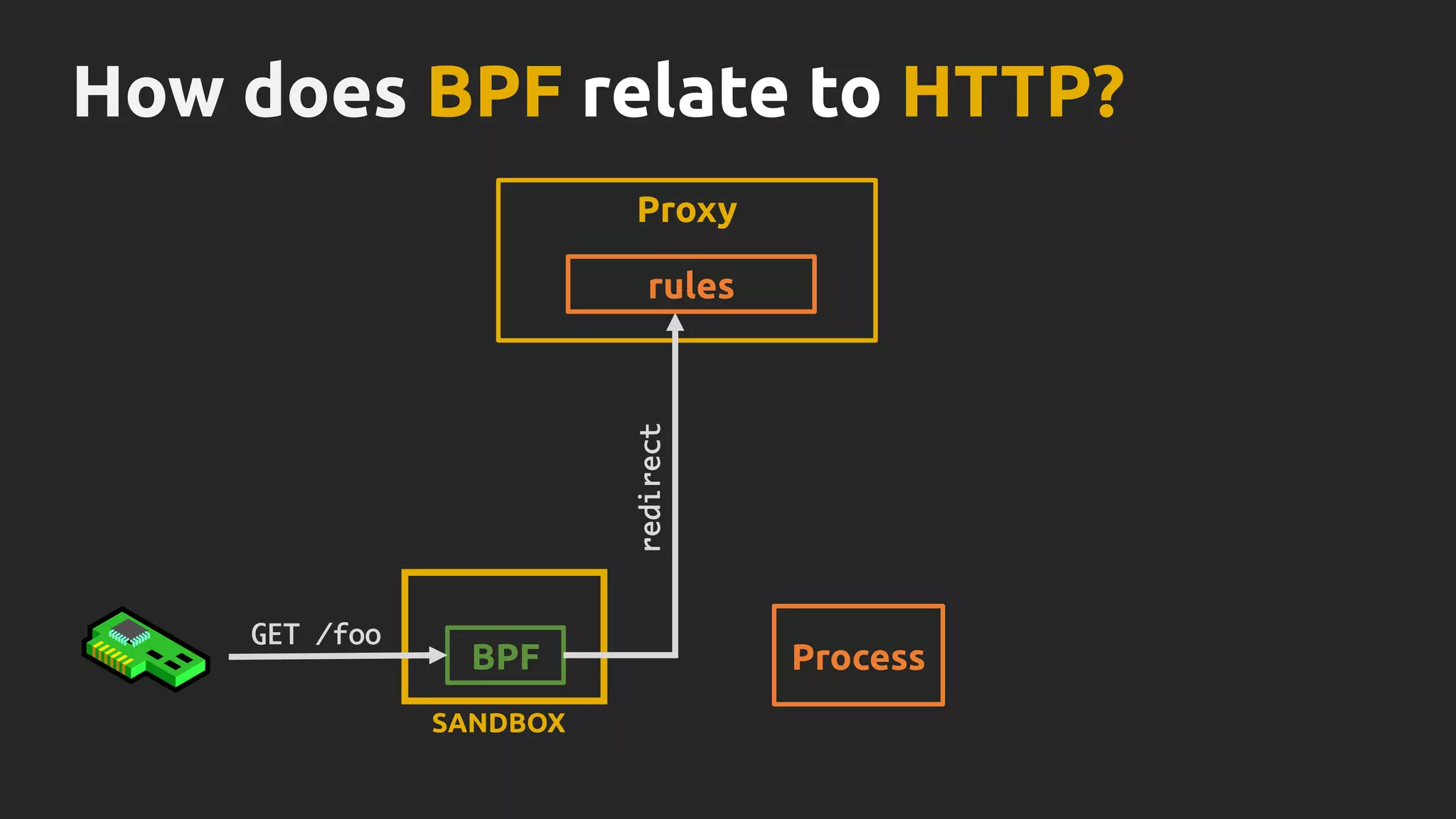
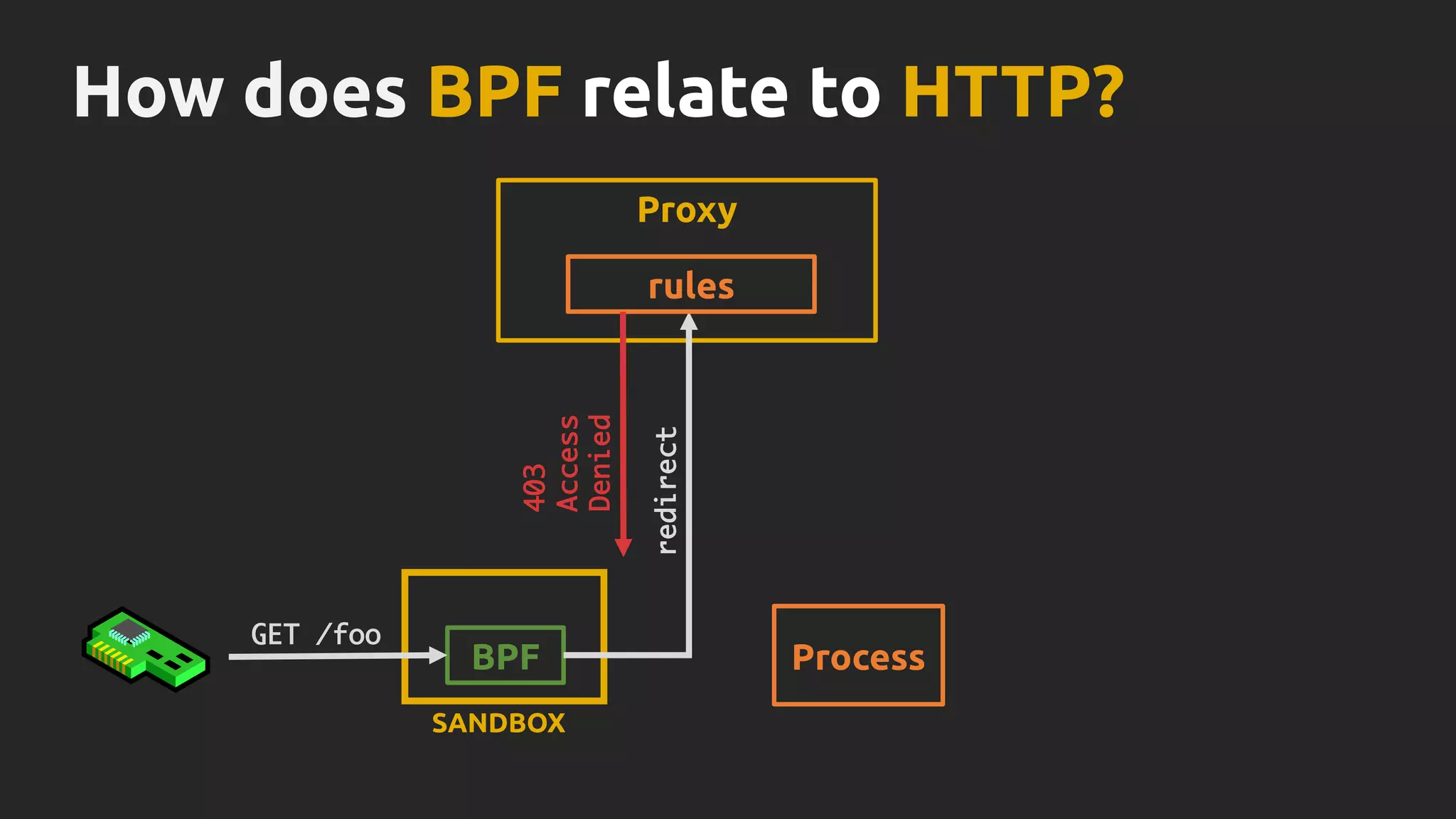
Thomas Graf, CTO and co-founder of Covalent, discusses the challenges of network security in a microservices architecture, highlighting the limitations of traditional methods like iptables. He emphasizes the need for modern approaches using BPF (Berkeley Packet Filter) to enhance security and optimize performance in dynamic environments. The document also briefly touches on Cilium, a project that utilizes BPF for improved container networking and security policies.







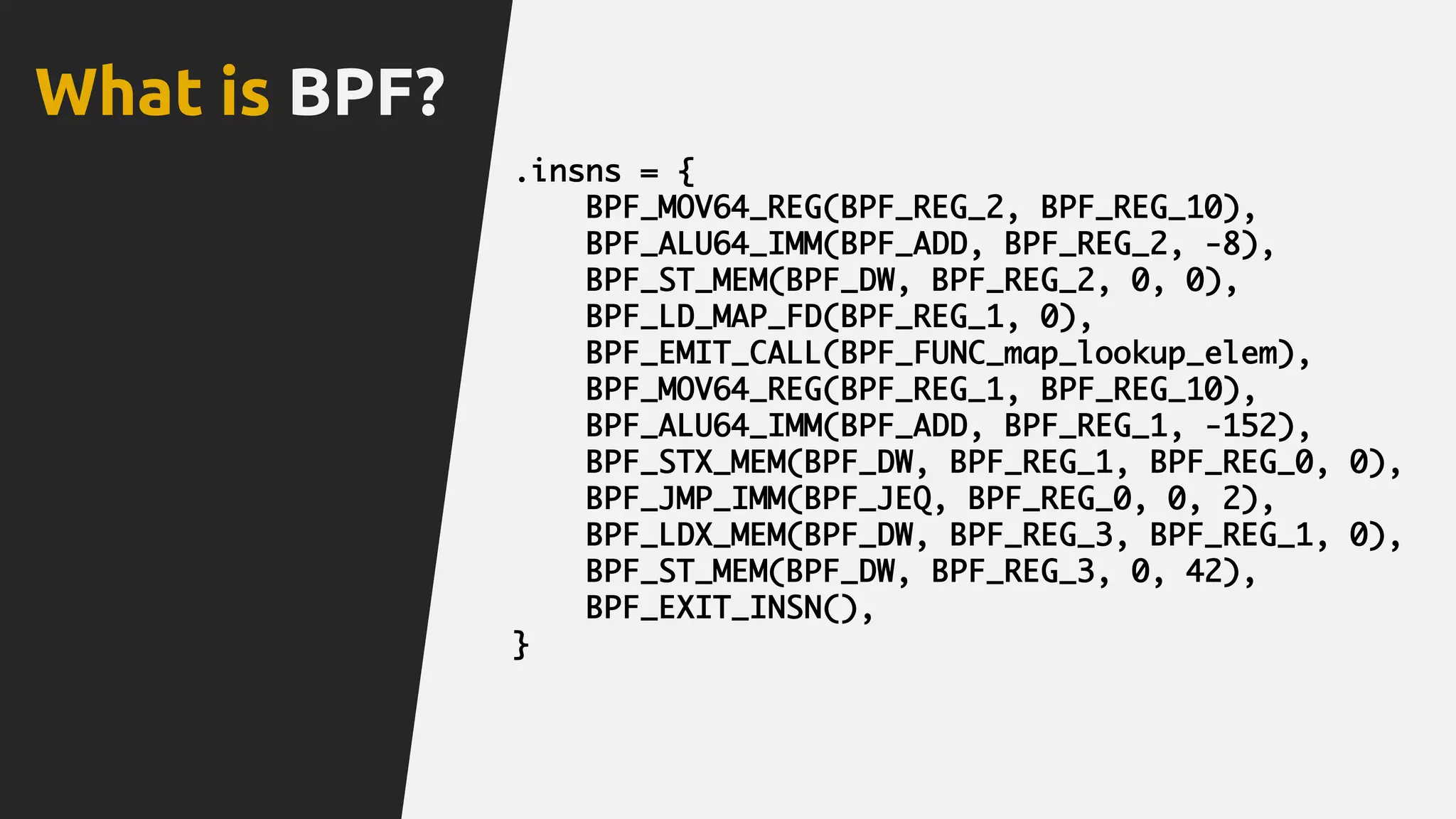
![What is BPF?
SOURCE CODE [C]
</>
USER SPACE](https://image.slidesharecdn.com/ciliumcncfv0-170330100102/75/Linux-Native-HTTP-Aware-Network-Security-18-2048.jpg)
![What is BPF?
SOURCE CODE [C]
</>
BYTE CODE [BPF]
USER SPACE
</>](https://image.slidesharecdn.com/ciliumcncfv0-170330100102/75/Linux-Native-HTTP-Aware-Network-Security-19-2048.jpg)
![What is BPF?
SOURCE CODE [C]
</>
BYTE CODE [BPF]
VERIFIER
+ JIT
USER SPACE
KERNEL
</>](https://image.slidesharecdn.com/ciliumcncfv0-170330100102/75/Linux-Native-HTTP-Aware-Network-Security-20-2048.jpg)
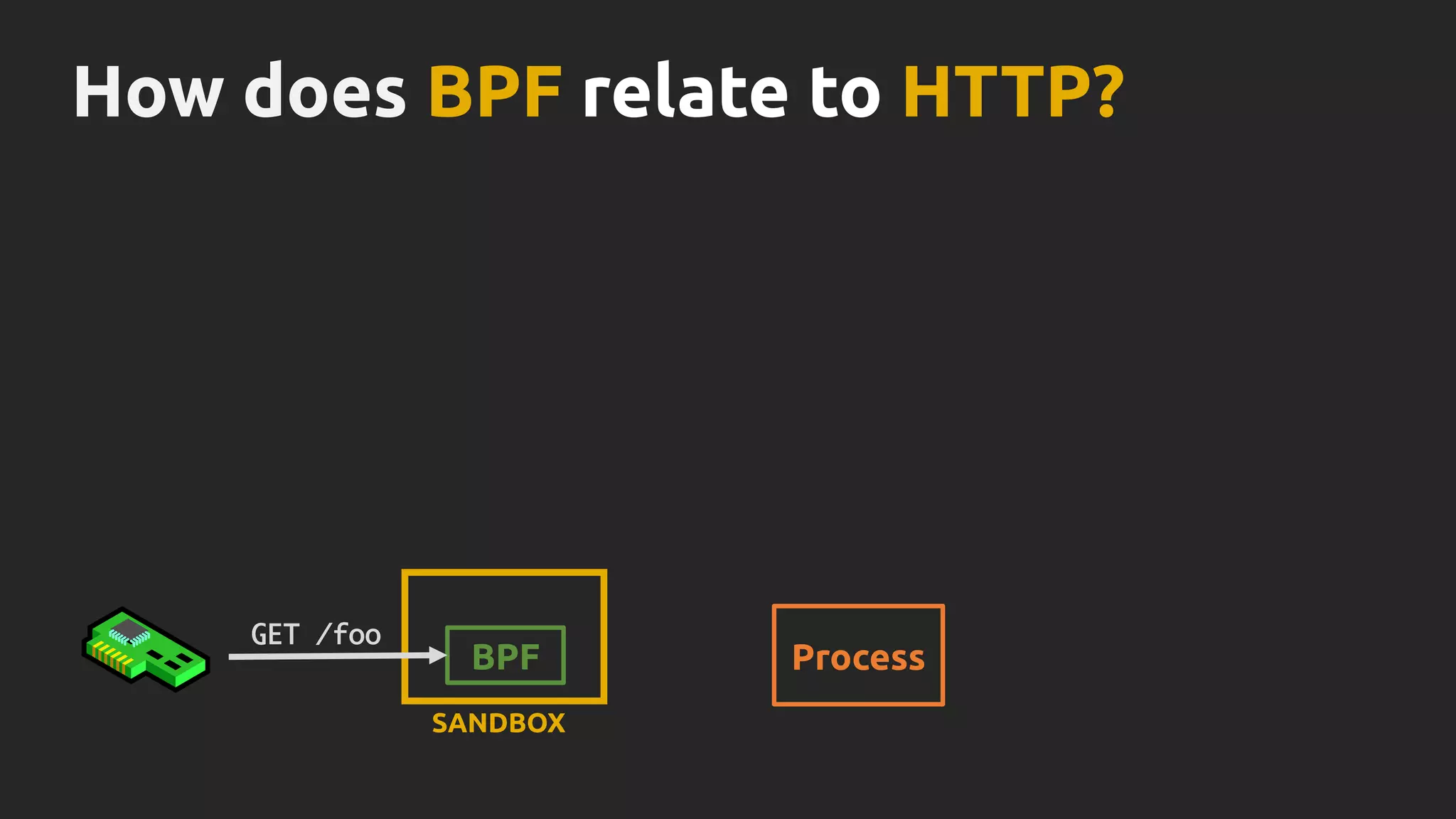
![What is BPF?
SOURCE CODE [C]
</>
BYTE CODE [BPF]
VERIFIER
+ JIT
USER SPACE
KERNEL
</>
SANDBOX
BPF](https://image.slidesharecdn.com/ciliumcncfv0-170330100102/75/Linux-Native-HTTP-Aware-Network-Security-21-2048.jpg)
![What is BPF?
SOURCE CODE [C]
</>
BYTE CODE [BPF]
VERIFIER
+ JIT
USER SPACE
KERNEL
</>
SANDBOX
BPF
Process
Process](https://image.slidesharecdn.com/ciliumcncfv0-170330100102/75/Linux-Native-HTTP-Aware-Network-Security-22-2048.jpg)
![What is BPF?
SOURCE CODE [C]
</>
BYTE CODE [BPF]
VERIFIER
+ JIT
USER SPACE
KERNEL
</>
SANDBOX
BPF
Process
SANDBOX
BPF
write()
Process](https://image.slidesharecdn.com/ciliumcncfv0-170330100102/75/Linux-Native-HTTP-Aware-Network-Security-23-2048.jpg)
![What is BPF?
SOURCE CODE [C]
</>
BYTE CODE [BPF]
VERIFIER
+ JIT
USER SPACE
KERNEL
</>
SANDBOX
BPF
Process
SANDBOX
BPF
write()
Process
EACCESS](https://image.slidesharecdn.com/ciliumcncfv0-170330100102/75/Linux-Native-HTTP-Aware-Network-Security-24-2048.jpg)


![75
140
205
240
325
365 370 365
410 412 425
445 450 460 460
490 495 505 515 525
545
565
0
100
200
300
400
500
600
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22
BPF redirect() performance
[GBit per core]
Intel Xeon 3.5Ghz Sandy Bridge, 24 Cores,
1 TCP GSO flow per core, netperf -t TCP_SENDFILE, 10K Cilium policies](https://image.slidesharecdn.com/ciliumcncfv0-170330100102/75/Linux-Native-HTTP-Aware-Network-Security-32-2048.jpg)
